Funding Cuts Threaten Foundational Cybersecurity Infrastructure
The latest news about potential budget cuts might affect global Cybersecurity efforts. We are at risk to lose the Common Vulnerabilities and Exposures (CVE) database, maintained by the federally funded, non-profit research and development organization MITRE. This has been reported and verified by U.S. based Cybersecurity reporter Brian Krebs1
U.S. institutions, notably the Cybersecurity and Infrastructure Security Agency (CISA) and MITRE, serve as indispensable hubs for coordinating cybersecurity efforts on an international scale. The CVE list, in particular, provides a universal dictionary for identifying and tracking vulnerabilities, forming the bedrock for effective communication and response among defenders worldwide. While these platforms foster crucial global cooperation, it is undeniable that the foremost beneficiaries of this public-private coordination are the major U.S.-based technology and cybersecurity corporations. Companies such as Google, Microsoft, Palo Alto Networks, CrowdStrike, SentinelOne, Cybereason, and countless others heavily rely on this shared intelligence infrastructure to secure their products, services, and customers.
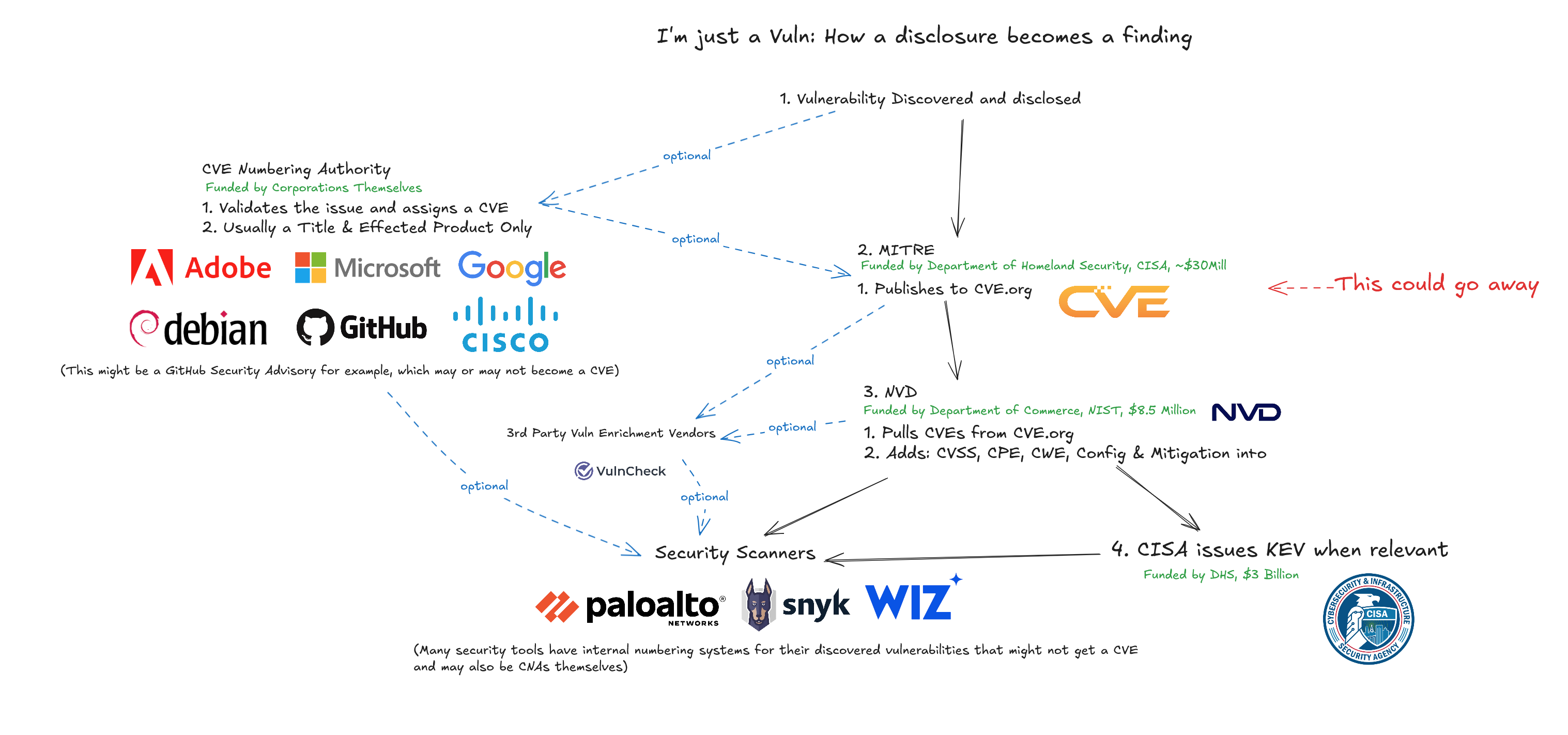 CVE Interplay between public and private organizations2
CVE Interplay between public and private organizations2
The cuts made to the publicly funded programs at CISA and MITRE are potentially seen by the current U.S. administration as cutting tax payer funded program that benefit disproportionately organizations outside the U.S., who are not contributing towards them, but another argument might be that this is going to disproportionally affect U.S. based companies who are global industry leaders in the field of Cybersecurity.
This could mean that global cybersecurity effort is going to be weakened, while at the same time - putting significant economic value within the U.S at risk. Furthermore, such targeted cuts often fail to make a substantial impact on overall budget deficits, making the strategic cost disproportionately high compared to any potential fiscal savings. Investing in shared cybersecurity infrastructure is not simply expenditure; it is a critical investment in national security, global stability, and the continued prosperity of the U.S. digital economy.
Update 2025-04-16 13:25:00 UTC
News about global politics has accelerated to a breakneck pace for the past few months (years, really) and this is reflected as well in the Cybersecurity industry. The following exert is from an update that James Berthoty shared on LinkedIn and I am publishing without any changes :
Latest updates on hashtag #MITREMELTDOWN (it needs a thunderdome name if it’s going to be a major cybersecurity event):
-
CISA has extended the MITRE contract, so crisis averted for now - https://lnkd.in/euzY5syu (bluesky quote from this: https://lnkd.in/eDZtPhZR)
-
Patrick Garrity 👾🛹💙 pointed out that the CVE printer is still working - https://lnkd.in/eSJMNFiZ
-
Tib3rius pointed out the formation of the CVE Foundation, which is apparently made up of some CVE board members, but there’s no information really at this point - https://lnkd.in/evCGr3Nk
-
Others have pointed to a global effort - https://gcve.eu, as well as Tom Alrich with OWASP - https://lnkd.in/epYsgwd9
-
The latest Brian Krebs update seems to suggest that CVE publications from CNAs will still work (which is the vast majority of them), we just don’t know for how long and what the long term plan is
I tried to call out in my video (linked below) that the main issue here is one of coordination and adoption, not the technical difficulty of creating a database. Almost every vendor has their own vulnerability database to host NVD and their own discovered vulnerabilities.
Instead, the challenge is CNA adoption of some new process and standards. There are over 450 CNAs who do most of the daily work, and no vendor is jumping at the opportunity to help all their competitors, inherit all of the drama of managing the CVE ecosystem, try to coordinate the daily work, and not make any money in the process.
I’ve been talking to a ton of vendors all of which are willing and wanting to help, but none of which can do it alone - most are hoping the best positioned like GitHub, Microsoft, or Google steps in to save the day.
Video: https://lnkd.in/eFFEh-qr