The Feed 2025-01-24

AI Generated Podcast
https://open.spotify.com/episode/1OZqCTRDkQHIUnw7AfDsY0?si=IAAUUfyqTNWHHyjgWz5-Yw
Summarized Sources
-
Beware: New XWorm Variant Spreading Fast Through Windows Script Files: Microsoft observed two large-scale email phishing campaigns in late 2024 distributing the Xworm remote access trojan through job recruitment lures and the ClickFix social engineering technique. URL: https://cyberpress.org/xworm-variant-spreading-fast-through-windows-script-files/
-
Fortinet Zero-Day CVE-2024-55591 Exposed: Super-Admin Access Risk: A critical authentication bypass vulnerability (CVE-2024-55591) in Fortinet’s FortiOS and FortiProxy products allows attackers to gain super-admin privileges and is being actively exploited. URL: https://cyble.com/blog/cve-2024-55591-the-fortinet-flaw-putting-critical-systems-at-risk/
-
Sliver Implant Targets German Entities With DLL Sideloading: A cyberattack targeting German organizations uses a deceptive LNK file to trigger DLL sideloading of a malicious Sliver implant, which establishes remote access. URL: https://cyble.com/blog/sliver-implant-targets-german-entities-with-dll-sideloading-and-proxying-techniques/
-
Tangerine Turkey mines cryptocurrency in global campaign: The Tangerine Turkey campaign is a VBS worm delivered via USB that uses a printui DLL hijack to deliver cryptomining malware and is connected to a large cryptocurrency mining operation. URL: https://redcanary.com/blog/threat-intelligence/tangerine-turkey/
-
Unveiling Silent Lynx APT: Targeting Central Asian Entities with Malicious Campaigns: The Silent Lynx APT group is targeting Central Asian entities, particularly in Kyrgyzstan, with multi-stage attacks involving malicious ISO files, C++ loaders, PowerShell scripts, and Golang implants, using Telegram bots for command and control. URL: https://www.seqrite.com/blog/silent-lynx-apt-targeting-central-asian-entities/
Beware: New XWorm Variant Spreading Fast Through Windows Script Files
Summary
Microsoft observed two large-scale email phishing campaigns in late 2024 distributing the Xworm remote access trojan. The first campaign used job recruitment lures with Prometheus TDS and a custom CAPTCHA. The second campaign used phishing emails with HTML attachments or URLs using the ClickFix technique to install Xworm. The Xworm RAT is used for remote access, data theft, and ransomware activities.
Technical Details
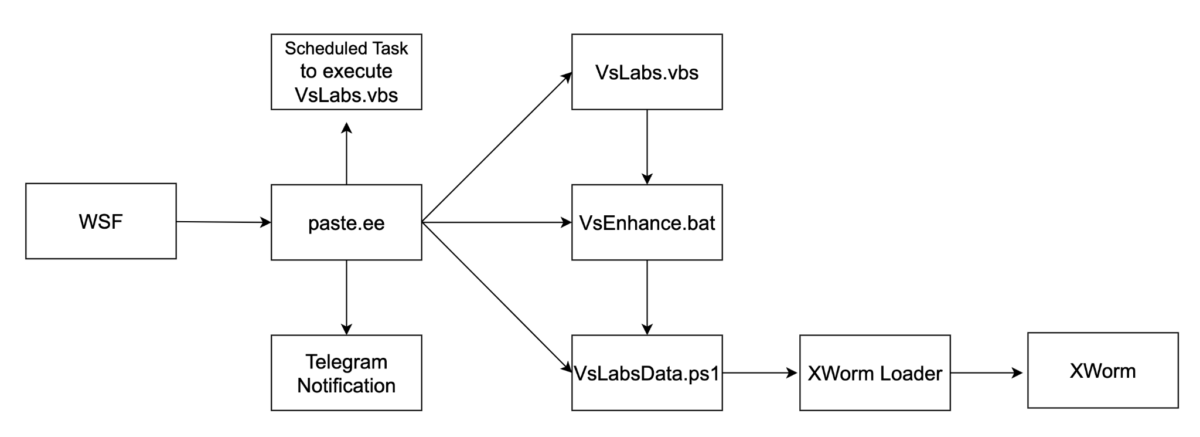 The initial access for the first campaign was through job recruitment lure emails with URLs that redirect to a site requiring a CAPTCHA. Once the CAPTCHA is solved a zip file containing a Javascript (.js) file is downloaded. The JavaScript runs PowerShell commands that download Xworm. The second campaign uses the ClickFix technique, which includes pop-up errors prompting users to copy and paste a command in the Windows Run dialog box. This command downloads and launches an HTA script that installs Xworm. The Xworm RAT enables remote access, data theft, and follow-on ransomware.
The MITRE ATT&CK Techniques observed were: Initial Access: Phishing (T1566), Execution: Command and Scripting Interpreter: JavaScript (T1059.007), Command and Scripting Interpreter: PowerShell (T1059.001), User Execution: Malicious File (T1204.002), Defense Evasion: Impair Defenses (T1562) and Command and Control: Dynamic Resolution (T1568).
The initial access for the first campaign was through job recruitment lure emails with URLs that redirect to a site requiring a CAPTCHA. Once the CAPTCHA is solved a zip file containing a Javascript (.js) file is downloaded. The JavaScript runs PowerShell commands that download Xworm. The second campaign uses the ClickFix technique, which includes pop-up errors prompting users to copy and paste a command in the Windows Run dialog box. This command downloads and launches an HTA script that installs Xworm. The Xworm RAT enables remote access, data theft, and follow-on ransomware.
The MITRE ATT&CK Techniques observed were: Initial Access: Phishing (T1566), Execution: Command and Scripting Interpreter: JavaScript (T1059.007), Command and Scripting Interpreter: PowerShell (T1059.001), User Execution: Malicious File (T1204.002), Defense Evasion: Impair Defenses (T1562) and Command and Control: Dynamic Resolution (T1568).
Recommendations
Microsoft recommends user education, using Zero-hour auto purge (ZAP) in Defender for Office 365, advanced anti-phishing solutions, Microsoft Edge with Defender SmartScreen, Conditional Access authentication, cloud-delivered protection in Microsoft Defender Antivirus, network protection, tamper protection, investigation and remediation in full automated mode, and EDR in block mode. They also recommend that Microsoft Defender XDR customers turn on attack surface reduction rules to prevent common attack techniques.
Hunting Methods
Microsoft for XDR Advanced Hunting query for suspicious URL clicks from emails:
UrlClickEvents
| where Timestamp between (start .. end) //Timestamp around time proximity of Risky signin by user
| where AccountUpn has "<Impacted user’s UPN or Email address>" and ActionType has "ClickAllowed"
| project Timestamp,Url,NetworkMessageId
IOC
URLs in campaigns:
https[:]//mideashop[.]es/translucid/egotistical/ovule/?
https[:]//abuc[.]cm/planning/contagious/?
https[:]//ilosalamos[.]cl/hamster/gelatinous/?
https[:]//adecco[.]com.working-with-adecco.findajob.profit-potential.top/adecco/ade.php?
http[:]//185.147.124[.]40/Capcha.html
JavaScript hosting:
https[:]//gwsmltd[.]com/bg/PM-DETAILS-STQRT5RX-102024.zip?
JavaScript running PowerScript commands to download:
http[:]//85.209.11[.]15/q/9.png
http[:]//85.209.11[.]15/q/45.png
SHA256s of payloads:
B09539cbda49c4c870bba07756eac1c7688e61efb8ea6e9bc2eac6eb53a7df7d
D08928d078d1b2ded79a527727839a0b302088e9934327a93d977e8a830af436
Hashes of downloaded scripts:
6182c88cd2881b3c9f44aadf3750d82f32e9ad19345d3aa7fd33b2bc363a884c
3bbdc10a48535df401713cbc1c29691a835258c8785fbcd58cf833398ddbd5e8
Xworm C2:
http[:]185.147.124[.]40
http[:]85.209.11[.]15
Original link: https://cyberpress.org/xworm-variant-spreading-fast-through-windows-script-files/
Fortinet Zero-Day CVE-2024-55591 Exposed: Super-Admin Access Risk
Summary
A critical authentication bypass vulnerability, CVE-2024-55591, has been identified in Fortinet’s FortiOS and FortiProxy products. This vulnerability, with a CVSSv3 score of 9.6, allows attackers to gain super-admin privileges by exploiting weaknesses in the Node.js WebSocket module. The vulnerability is actively being exploited in the wild. Attackers can craft malicious requests to bypass authentication and gain unauthorized access, leading to the creation of administrative accounts, modification of firewall policies, and establishment of SSL VPN tunnels to access internal networks. Affected versions of FortiOS are 7.0.0 through 7.0.16, and affected versions of FortiProxy are 7.0.0 through 7.0.19 and 7.2.0 through 7.2.12. Upgrading to FortiOS version 7.0.17 or later, and FortiProxy to versions 7.0.20 or 7.2.13 or later is recommended.
Technical Details
The vulnerability stems from an “Authentication Bypass Using an Alternate Path or Channel” issue (CWE-288). Attackers send malicious WebSocket requests to bypass authentication controls. They may target administrative accounts by guessing or brute-forcing usernames. After gaining access, they create random user accounts, such as "Gujhmk" or "M4ix9f", and add these accounts to administrative or VPN groups, using SSL VPN connections to infiltrate internal networks. The malicious actions include creating administrative or local user accounts, modifying firewall policies, addresses, or system settings, and establishing Secure Sockets Layer Virtual Private Network (SSL VPN) tunnels to access internal networks.
The MITRE ATT&CK techniques include: Initial Access: Exploit Public-Facing Application (T1190), Privilege Escalation: Abuse Elevation Control Mechanism (T1548), Account Creation: Local Account (T1136.001) and Remote Access: VPN (T1021.003)
Recommendations
Upgrade FortiOS to version 7.0.17 or later. Upgrade FortiProxy to versions 7.0.20 or 7.2.13 or later. If an immediate upgrade is not possible, mitigate risk by disabling HTTP/HTTPS administrative interfaces, restricting access with local-in policies, and using non-standard admin usernames. Continuously monitor system logs for any unauthorized administrative activity, suspicious configuration changes, or unexpected VPN connections. Conduct regular vulnerability scans. Adopt a zero-trust approach, limit user privileges, and enforce strict access controls. Implement multi-factor authentication (MFA). Educate IT and security teams about this vulnerability.
Hunting Methods
Monitor logs for suspicious entries including successful admin logins from “jsconsole,” and any unauthorized configuration changes with “jsconsole” in the ui field. Look for the following types of log entries in your system:
type=”event” subtype=”system” level=”information” logdesc=”Admin login successful”
user=”admin” ui=”jsconsole” srcip=1.1.1.1 dstip=1.1.1.1 action=”login” status=”success”
msg=”Administrator admin logged in successfully from jsconsole”
type=”event” subtype=”system” level=”information” logdesc=”Object attribute configured”
user=”admin” ui=”jsconsole(127.0.0.1)” action=”Add”
msg=”Add system.admin vOcep”
IOC
Suspicious IP Addresses:
45.55.158.47
87.249.138.47
155.133.4.175
37.19.196.65
149.22.94.37
Original link: https://cyble.com/blog/cve-2024-55591-the-fortinet-flaw-putting-critical-systems-at-risk/
Sliver Implant Targets German Entities With DLL Sideloading
Summary
Cyble Research and Intelligence Labs (CRIL) has identified an ongoing cyberattack campaign targeting organizations in Germany using a Sliver implant. The attack uses a deceptive LNK file within an archive to initiate a multi-stage infection process. The LNK file executes a legitimate executable which then sideloads a malicious DLL. This DLL decrypts and executes shellcode, ultimately deploying the Sliver framework for command and control. The Sliver implant allows the threat actors to establish communication with the compromised system and conduct further malicious operations. The campaign uses a lure document disguised as a home office agreement in German, suggesting that the campaign is designed to target individuals or organizations in Germany. The initial .7z file was observed to have been uploaded to VirusTotal from a German location.
Technical Details
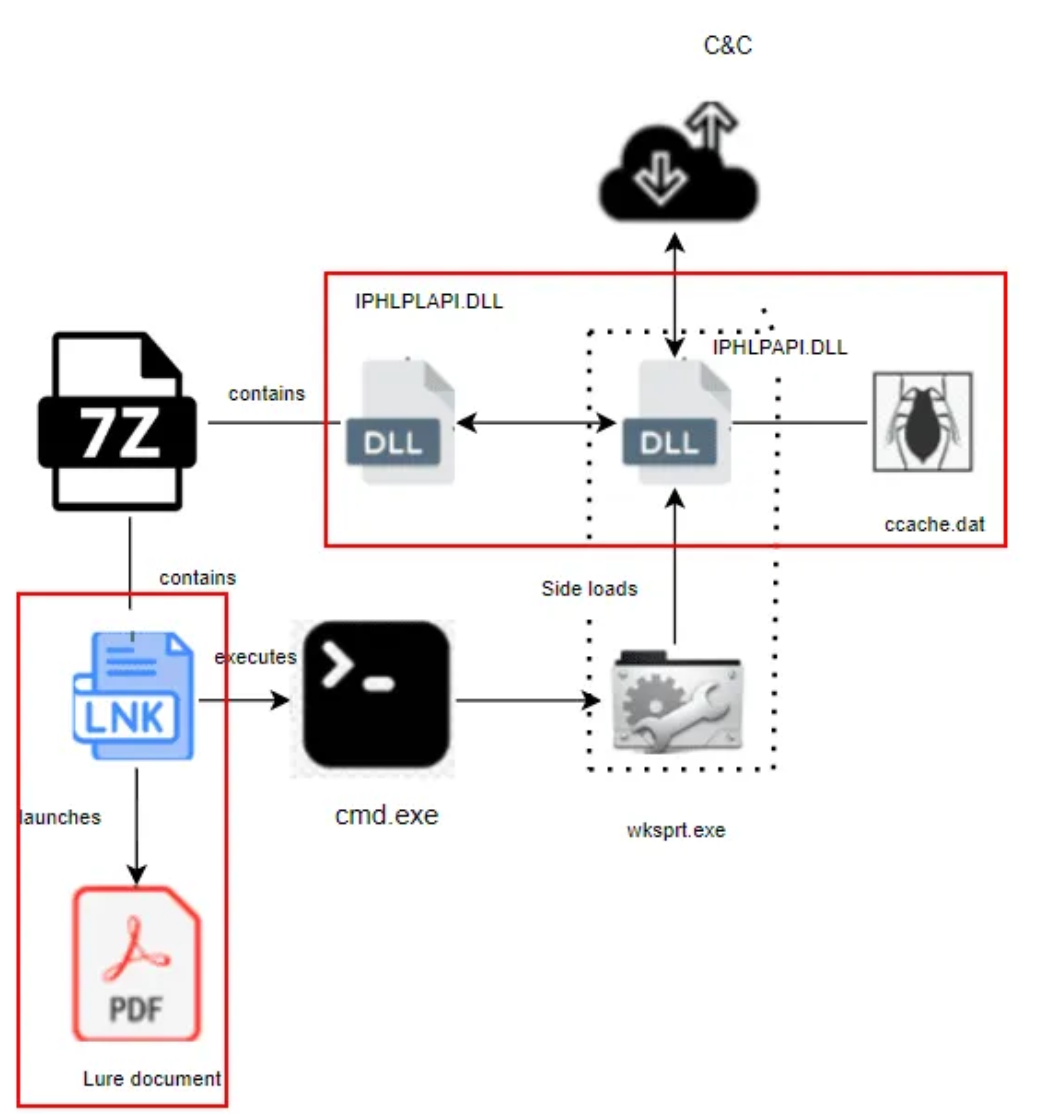 The attack begins when a user extracts a .7z archive file, likely delivered via spear phishing email, which contains a malicious LNK file disguised as a PDF document along with other files including legitimate executables (DLL and EXE files), a malicious DLL, an encrypted DAT file, and a decoy PDF. When the LNK file is executed, it launches a decoy PDF document to deceive the user, and simultaneously executes a legitimate file,
The attack begins when a user extracts a .7z archive file, likely delivered via spear phishing email, which contains a malicious LNK file disguised as a PDF document along with other files including legitimate executables (DLL and EXE files), a malicious DLL, an encrypted DAT file, and a decoy PDF. When the LNK file is executed, it launches a decoy PDF document to deceive the user, and simultaneously executes a legitimate file, cmd.exe, to copy files to specific directories and perform other tasks. A directory named “InteI” is created within the user’s local app data folder, and a legitimate Windows file, wksprt.exe, is copied into this directory. The malicious files IPHLPAPI.dll, IPHLPLAPI.dll, and ccache.dat are also copied into this directory with their hidden attributes preserved. The wksprt.exe executable then sideloads the malicious DLL, IPHLPAPI.dll, which in turn loads a legitimate DLL renamed IPHLPLAPI.dll. This malicious DLL uses DLL proxying to intercept function calls and forward them to the legitimate DLL, allowing the malicious DLL to execute its code while maintaining normal application behavior. The malicious DLL spawns a new thread to read the encrypted shellcode from ccache.dat and decrypt it using cryptographic APIs. The decrypted shellcode decrypts another layer of payload, which is the Sliver implant, an open-source red teaming and command and control framework. The implant then establishes connections to remote servers for further malicious activities. To establish persistence, a shortcut (wksprt.lnk) is copied to the Startup folder to automatically execute wksprt.exe on system startup.
The MITRE ATT&CK techniques observed include: Initial Access: Phishing (T1566), Execution: Command and Scripting Interpreter (T1059), Persistence: Registry Run Keys / Startup Folder (T1547.001), Privilege Escalation: Hijack Execution Flow: DLL Side-Loading (T1574.002), Defense Evasion: Obfuscated Files or Information (T1027.002), Command and Control: Application Layer Protocol: Web Protocols (T1071.001). The Sliver framework has capabilities for Privilege Escalation: Access Token Manipulation (T1134), Defense Evasion: Process Injection (T1055) and Obfuscated Files or Information (T1027), Discovery: File and Directory Discovery (T1083), System Network Configuration Discovery (T1016), System Network Connections Discovery (T1049), Command and Control: Application Layer Protocol (T1071), Data Encoding: Standard Encoding (T1132.001), Encrypted Channel (T1573.001, T1573.002), and Ingress Tool Transfer (T1105), as well as Exfiltration: Exfiltration Over C2 Channel (T1041).
Countries
Germany
Industries
Not specified in the article, though the lure document suggests the campaign is designed to target individuals or organizations that may have remote working agreements.
Recommendations
The article recommends deploying strong email filtering systems to prevent the delivery of harmful attachments. Exercise caution when handling email attachments or links, particularly from unknown senders. Verify the sender’s identity and implement application whitelisting to prevent unauthorized execution of LNK files and other suspicious components. It’s also recommended to deploy Endpoint Detection and Response (EDR) solutions to identify and block malicious behaviors such as DLL sideloading and shellcode injection, and to monitor for anomalous network activity to detect Sliver framework activity. Enable network protection to prevent applications or users from accessing malicious domains and other content on the internet. Use Microsoft Defender Firewall to prevent RPC and SMB communication to limit lateral movement, and use cloud-delivered protection and automatic sample submission on Microsoft Defender Antivirus to identify new threats. Additionally, educate users about good credential hygiene. Microsoft 365 Defender customers should turn on tamper protection features, run EDR in block mode, enable investigation and remediation in full automated mode, and use device discovery. Attack surface reduction rules should be enabled to prevent common attack techniques including blocking process creations originating from PsExec and WMI commands, blocking executable files from running unless they meet a prevalence, age, or trusted list criterion, and blocking credential stealing. It is also recommended to assess rule impact before deployment.
Hunting Methods
Microsoft for XDR Advanced Hunting queries include:
- GetSystem: This query finds potential launch of the built-in GetSystem command by looking for
SeDebugprivileges added to a process, followed by that process creating a remote thread inspoolsv.exewithin 30 seconds. The KQL query is:let SeDebugPriv = 1048576; DeviceEvents | where FileName == 'spoolsv.exe' | where ActionType == 'CreateRemoteThreadApiCall' | where InitiatingProcessFileName !~ 'csrss.exe' | project InitiatingProcessId, DeviceId, CreateTime=Timestamp, FileName | join kind=inner ( DeviceEvents | where ActionType == 'ProcessPrimaryTokenModified' | extend TokenModTime = Timestamp ) on DeviceId, InitiatingProcessId | where TokenModTime between ((CreateTime - 30s) .. CreateTime) | extend JSON=parse_json(AdditionalFields) | where binary_xor(tolong(JSON.OriginalTokenPrivEnabled),tolong(JSON.CurrentTokenPrivEnabled)) == SeDebugPriv //| where binary_and(tolong(JSON.OriginalTokenPrivEnabled), SeDebugPriv) == 0 | where binary_and(tolong(JSON.CurrentTokenPrivEnabled), SeDebugPriv) != 0 | extend TargetProcessFileName=FileName | project-reorder DeviceName, InitiatingProcessFileName, TargetProcessFileName, InitiatingProcessId - Shell: This query finds the default PowerShell command used when Sliver creates an interactive shell. The KQL query is:
DeviceProcessEvents | where ProcessCommandLine == 'powershell.exe -NoExit -Command [Console]::OutputEncoding=[Text.UTF8Encoding]::UTF8' - Sideload/SpawnDll/Execute-Assembly: This query finds process creation events where the same process creates and injects into
notepad.exewithin 10 seconds. The KQL query is:DeviceProcessEvents | where ActionType == 'ProcessCreated' | where ProcessCommandLine =~ 'notepad.exe' | distinct InitiatingProcessId, DeviceId | join kind=inner ( DeviceEvents | where ActionType == 'CreateRemoteThreadApiCall' | where ProcessCommandLine == 'notepad.exe' | where Timestamp between (ProcessCreationTime .. (ProcessCreationTime+10s)) ) on DeviceId, InitiatingProcessId - PsExec: This query finds default values for
ImagePath,DisplayName, andDescriptionof the service installed on the remote system when using Sliver’s PsExec command. The KQL query is:DeviceRegistryEvents | where ActionType == 'RegistryValueSet' | where (RegistryValueName == 'ImagePath' and RegistryValueData matches regex @'^[a-zA-z]:\\windows\\temp\\[a-zA-Z0-9]{10}\.exe') or (RegistryValueName == 'DisplayName' and RegistryValueData == 'Sliver') or (RegistryValueName == 'Description' and RegistryValueData == 'Sliver implant')An alternative query searches for the same service properties within service installation events:
DeviceEvents | where ActionType == 'ServiceInstalled' | extend JSON = parse_json(AdditionalFields) | where (FolderPath endswith_cs @':\windows\temp' and FileName matches regex @'^[a-zA-Z0-9]{10}\.exe') or (JSON.ServiceName == 'Sliver')A Sigma rule for detecting DLL sideloading using
wksprt.exeis provided. The Sigma rule is: ``` title: Detects DLL SideLoading using wksprt.exe id: cff15cc1-8d5c-455d-a0d3-c19b48911433 status: experimental description: Detects DLL SideLoading using wksprt.exe author: Cyble date: 2025/01/16 logsource: category: image_load product: windows tags: - attack.defense_evasion
- attack.t1574.001
- attack.t1574.002 detection: selection: Image|endswith: ‘\wksprt.exe’ ImageLoaded|endswith: ‘\iphlpapi.dll’ filter_main_legit_path: Image|startswith:
- ‘C:\Windows\System32' filter_main_is_signed: Signed: ‘true’ condition: selection and not 1 of filter_main_* falsepositives:
- Unknown
level: Medium
```
Yara and Sigma rules to detect this campaign are also available for download from the linked Github repository.
IOC
File Hashes (SHA-256):
83a70162ec391fde57a9943b5270c217d63d050aae94ae3efb75de45df5298be - Archive File
f778825b254682ab5746d7b547df848406bb6357a74e2966b39a5fa5eae006c2 - LNK file
9b613f6942c378a447c7b75874a8fff0ef7d7fd37785fdb81b45d4e4e2d9e63d - Malicious DLL
86f8a979bd887955f0491a0ed5e00de2f3fe53e6eb5856fb823115ce43b7c0ca - Encrypted .dat file
URLs:
hxxp://www.technikzwerg[.]de/auth/auth/authenticate/samples.html
hxxp://www.technikzwerg[.]de/auth/auth/authenticate/samples.php
Original link: https://cyble.com/blog/sliver-implant-targets-german-entities-with-dll-sideloading-and-proxying-techniques/
Tangerine Turkey mines cryptocurrency in global campaign
Summary
Tangerine Turkey is the name given to a visual basic script (VBS) worm that delivers cryptomining malware. The worm is delivered via USB and uses a printui dynamic link library (DLL) hijack. Red Canary first observed this activity in November 2024. In December 2024, the threat was ranked #8 in their top 10 threat rankings. The activity is part of a wider cryptocurrency mining campaign. The threat has been observed to drop XMRig mining software. A similar operation called “Universal Mining” was discovered by the Azerbaijan CERT, which had infected 270,741 computers in 135 countries. Security researcher Will Thomas created YARA and Sigma rules for “UniversalMiner”. The Zephyr Miner Malware collection on VirusTotal has 178 files.
Technical Details
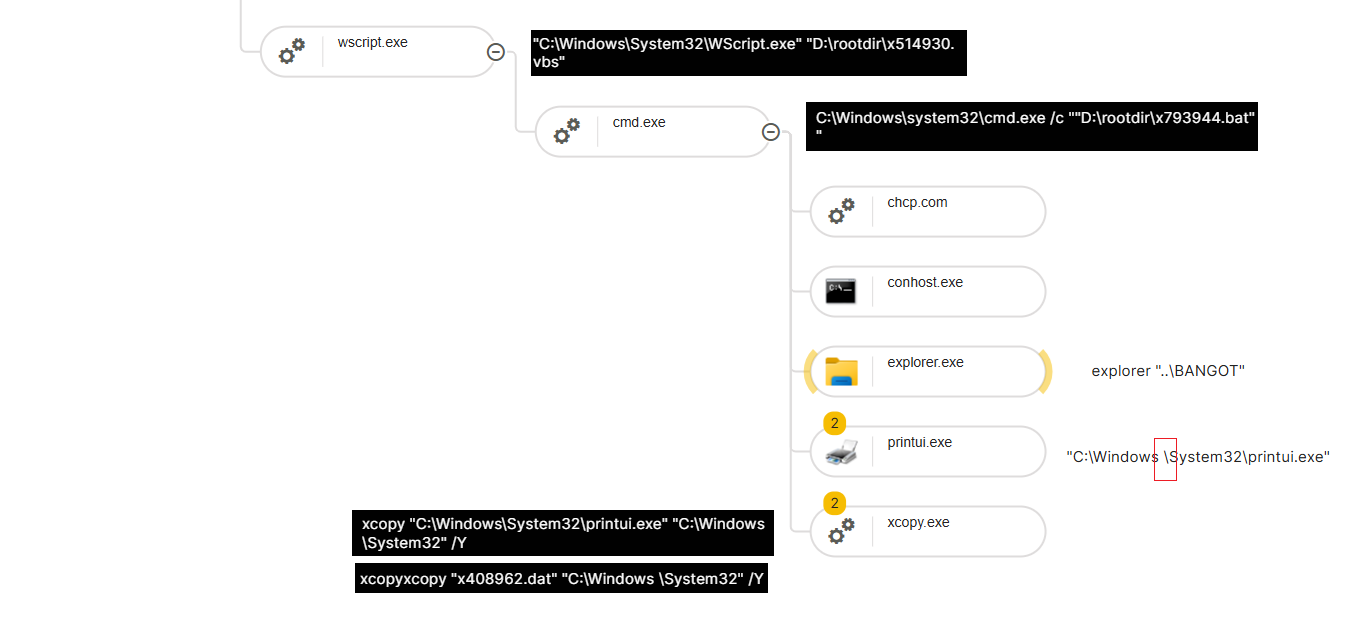 The execution chain starts with a VBS file executed from a folder named rootdir on a USB drive. The VBS file has a filename that begins with an “x” followed by six random digits, for example, x644291.vbs. The VBS file executes a BAT file with a similar naming convention. The BAT file execution is via a CMD child process from wscript, for example: cmd.exe /c “D:\rootdir\x138621.bat”. A folder named C:\Windows \System32 (note the trailing space after \Windows ) is created. The legitimate printui.exe binary is copied from C:\Windows\System32 to the newly created malicious C:\Windows \System32 directory using xcopy. DAT and printui.dll files are created in C:\Windows \System32 to be used for DLL side-loading. The printui.dll file eventually drops XMRig mining software. The malware uses a database to store information about the infected computer and to obtain the information needed to configure the miner. The malware connects to a PostgreSQL database on a remote server.
The execution chain starts with a VBS file executed from a folder named rootdir on a USB drive. The VBS file has a filename that begins with an “x” followed by six random digits, for example, x644291.vbs. The VBS file executes a BAT file with a similar naming convention. The BAT file execution is via a CMD child process from wscript, for example: cmd.exe /c “D:\rootdir\x138621.bat”. A folder named C:\Windows \System32 (note the trailing space after \Windows ) is created. The legitimate printui.exe binary is copied from C:\Windows\System32 to the newly created malicious C:\Windows \System32 directory using xcopy. DAT and printui.dll files are created in C:\Windows \System32 to be used for DLL side-loading. The printui.dll file eventually drops XMRig mining software. The malware uses a database to store information about the infected computer and to obtain the information needed to configure the miner. The malware connects to a PostgreSQL database on a remote server.
Countries
The Universal Mining operation had infected 270,741 computers in 135 countries.
Industries
No specific industries were identified in the sources.
Recommendations
Monitor for printui.exe being relocated outside of Windows\System32. Profile System32 binaries, collect and store their expected metadata to build detection analytics.
Hunting methods
YARA and Sigma rules for “UniversalMiner” have been created by Will Thomas.
process_path_is_unexpected == (printui)
IOC
Domains:
rootunvdwl[.]com
Original link: https://redcanary.com/blog/threat-intelligence/tangerine-turkey/
Unveiling Silent Lynx APT: Targeting Central Asian Entities with Malicious Campaigns
Summary
The Silent Lynx APT group has been identified in two recent campaigns targeting government entities in Central Asia, specifically Kyrgyzstan. The first campaign targeted the National Bank of the Kyrgyz Republic, while the second targeted the Ministry of Finance of Kyrgyzstan. Both campaigns used spear phishing emails with RAR attachments, which contained either malicious ISO files or password-protected RAR files. These attachments included decoy documents designed to appear legitimate. The attacks leverage a compromised email account. The threat actor uses a Telegram bot for command and control, and for data exfiltration. The actor has been observed downloading additional payloads from remote servers and using Google Drive. The group has been linked to a Kazakhstan-based threat actor known as YoroTrooper, due to overlaps in tooling, techniques, and targeting.
Technical Details
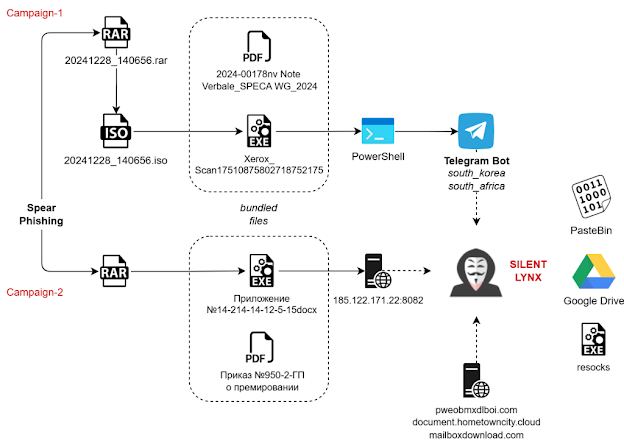
The Silent Lynx APT uses a multi-stage attack strategy involving spear phishing emails with malicious attachments.
Campaign 1:
- A spear phishing email contains an RAR attachment.
- The RAR file contains a malicious ISO file and a decoy document.
- The ISO file contains a malicious C++ executable and a decoy PDF.
- The C++ executable spawns a PowerShell process with an encoded script.
- The PowerShell script uses a Telegram bot for command execution and data exfiltration. The script includes functions to execute commands and exfiltrate data to a Telegram chat.
- The PowerShell script can execute commands such as /sleep, /cmd, and /download.
- The PowerShell script uses the getUpdates API endpoint to fetch messages and acts on them based on their content. It implements error handling to retry failed API calls.
Campaign 2:
- A spear phishing email contains a password-protected RAR attachment.
- The RAR file contains a malicious Golang executable and a decoy document.
- The Golang executable is a reverse shell that connects to a command and control server.
- The Golang reverse-shell uses packages like net_dial to connect to the command and control, and sleeps if the connection fails.
The threat actor uses a Telegram bot for command and control, and for data exfiltration. The actor also downloads additional payloads from remote servers using the curl command. The actor establishes persistence using a registry modification command which adds the downloaded payload to the Windows Run key. The threat actor uses a red-team open-source tool known as resocks. The actor also uses Google Drive to download further payloads. The threat actor has been observed to execute commands such as whoami and ipconfig to perform discovery on the target system. The group has been observed to use C++, MSIL implants, and PowerShell scripts.
The group uses the following techniques:
- T1589.002 Gather Victim Identity Information: Email Addresses
- T1204.002 User Execution: Malicious File
- T1078.002 Valid Accounts: Domain Accounts
- T1059.001 Command and Scripting Interpreter: PowerShell
- T1547.001 Registry Run Keys / Startup Folder
- T1056.001 Input Capture: Keylogging
- T1552.001 Unsecured Credentials: Credentials In Files
- T1087 Account Discovery
- T1083 File and Directory Discovery
- T1046 Network Service Discovery
- T1012 Query Registry
- T1018 Remote System Discovery
- T1016 System Network Configuration Discovery
- T1007 System Service Discovery
- T1560.001 Archive Collected Data: Archive via Utility
- T1567.002 Exfiltration to Cloud Storage
Countries
Kyrgyzstan, Turkmenistan
Industries
Embassies, Lawyers, Government Banks, Government Think-Tanks
Recommendations
The source material does not contain any specific recommendations for defending against this attack. However, it is important to note the use of a compromised email account and the use of a Telegram Bot for C2.
IOC
File Hashes:
efb700681713cd50a2addd1fea6b7ee80c084467d3e87668688b9f06642062ba
e6f76a73180b4f2947764f4de57b52d037b482ece1a88dab9d3290e76be8c098
3560660162f2268d52b69382c78192667a7eee5796d77418a8609b2f1709f834
297d1afa309cdf0c84f04994ffd59ee1e1175377c1a0a561eb25869909812c9c
c045344b23fc245f35a0ff4a6d6fa744d580cde45c8cd0849153dee7dce1d80c
1b76931775aa4de29df27a9de764b22f17ca117d6e5ae184f4ef617c970fc007
66294c9925ad454d5640f4fe753da9e7d6742f60b093ed97be88fcdd47b04445
99c6017c8658faf678f1b171c8eb5d5fa7e7d08e0a0901b984a8e3e1fab565cd
Domains/URLs:
hxxps:[//]pweobmxdlboi[.]com
hxxps:[//]document[.]hometowncity[.]cloud
hxxps:[//]mailboxdownload[.]com
hxxps[:]//api[.]telegram[.]org/bot8171872935:AAHLoudjpHz1bxA26bV5wPuOEL3LOHEl6Qk
hxxps[:]//api[.]telegram[.]org/bot7898508392:AAF5FPbJ1jlPQfqCIGnx-zNdw2R5tF_Xxt0
Original link: https://www.seqrite.com/blog/silent-lynx-apt-targeting-central-asian-entities/