The Feed 2025-02-03

AI Generated Podcast
https://open.spotify.com/episode/3C1rDW1eOEu8f2lQhgveSo?si=N-XHN6NaSCmoaer1KPsYEQ
Summarized Sources
- Browser Syncjacking: How Any Browser Extension can Be Used to Takeover Your Device : A browser extension with basic read/write capabilities can be used to hijack a user’s browser profile, and potentially their device, by silently logging them into an attacker-controlled profile and syncing their data.
Original link: https://labs.sqrx.com/browser-syncjacking-cc602ea0cbd0
- ClickFix vs. traditional download in new DarkGate campaign : A malvertising campaign used both “ClickFix” social engineering, where users are tricked into running malicious code, and traditional downloads of signed executables to deliver the DarkGate malware loader.
Original link: https://www.malwarebytes.com/blog/cybercrime/2025/01/clickfix-vs-traditional-download-in-new-darkgate-campaign
- Lumma Stealer’s GitHub-Based Delivery Explored via Managed Detection and Response : Attackers are using compromised websites to redirect users to malicious files hosted on GitHub, which download information-stealing malware like Lumma Stealer and other threats, such as SectopRAT and Vidar.
Original link: https://www.trendmicro.com/en_us/research/25/a/lumma-stealers-github-based-delivery-via-mdr.html
- New TorNet backdoor seen in widespread campaign: A new .NET backdoor called TorNet is being spread through phishing emails using a multi-stage attack that involves downloading and decrypting an encrypted PureCrypter binary and loading the backdoor into a .NET runtime process.
Original link: https://blog.talosintelligence.com/new-tornet-backdoor-campaign/
- One policy to rule them all: Attackers can use group policies to modify configurations and spread malware by changing attributes like gPCFileSysPath, gPCMachineExtensionNames and gPCUserExtensionNames, requiring close monitoring and security of group policies.
Original link: https://securelist.com/group-policies-in-cyberattacks/115331/
Browser Syncjacking: How Any Browser Extension can Be Used to Takeover Your Device
Summary
A browser syncjacking attack can be executed through a malicious browser extension with basic read/write permissions. The attack unfolds in phases, starting with the attacker creating a Google Workspace account and a malicious extension. Social engineering tactics are used to trick the victim into installing the extension. The extension then silently logs the victim into an attacker-controlled profile and synchronizes the victim’s data, including passwords. This initial access can be escalated by enrolling the victim’s browser into a managed workspace controlled by the attacker via a malicious executable disguised as a Zoom update, granting full control of the browser. The attacker can also use Chrome’s Native Messaging protocol to establish communication with a local binary on the victim’s machine to execute arbitrary system commands. This can allow the attacker to access the file system, modify system settings, install malware, conduct surveillance, harvest credentials, and remotely control the device. The stealthy execution of this attack makes it difficult to detect unless the victim is extremely security conscious.
Technical Details
The attack unfolds across three stages: profile, browser, and device hijacking.
Profile Hijacking: The attacker starts by purchasing a domain and creating a Google Workspace account. They then create multiple user profiles under the Google Workspace account and disable security features such as MFA. A malicious browser extension is developed and published on the Chrome Store, designed to communicate with the attacker’s server. The victim is then socially engineered into installing the extension, which often appears legitimate by offering useful features and requesting standard read/write permissions. Once installed, the extension runs silently in the background, connecting to the attacker’s domain to fetch user credentials and complete the necessary OAuth steps to log the victim into one of the attacker’s user accounts. The victim’s profile is synced to the attacker-controlled profile, exfiltrating locally stored passwords, browsing history, and other data.
Browser Hijacking: In this stage, the attacker aims to convert the whole browser into a managed browser. The attacker generates an enrollment token that is embedded in an executable disguised as a Zoom installer. When the victim tries to join a Zoom meeting, the malicious extension redirects them to a fake update page that downloads this malicious executable. When the victim executes the file, their browser is enrolled into the attacker’s managed workspace, giving the attacker full control. The attacker can then enforce policies to make the victim’s Chrome less secure and can install malicious extensions, redirect users to phishing sites, and monitor and modify file downloads.
Device Hijacking: The attacker can use Chrome’s Native Messaging protocol to communicate with local binaries on the victim’s machine. This is accomplished using a registry entry that is part of the browser hijacking “Zoom” package, or through a subsequent download that is initiated by the attacker once the browser has been hijacked. The malicious extension acts as a middleman, forwarding commands from the attacker to the compromised binary. Using a WebSocket connection, the attacker can send commands to perform malicious activities including accessing directories, manipulating files, and executing arbitrary system commands. This allows for full control over the device, including accessing file systems, modifying systems, surveillance, credential harvesting, and remote control.
Recommendations
The article recommends using a browser-native solution that understands the runtime behavior of each extension, citing SquareX’s Browser Detection and Response solution as an example. This solution includes a proprietary extension analysis engine with several components: * Highly granular extension-based policies, tracking extensions and elements listed on the Chrome Store, including user reviews, publisher, and number of downloads. * Advanced extension static analysis using AI and machine learning techniques to identify malicious intent. * Dynamic analysis that executes extensions in a controlled environment to observe their actual runtime behavior. * Browser extension policy library offering hundreds of policies based on best practices observed across their customers. * Extension risk scores based on multiple static and dynamic tests, public reviews, historical performance, and publisher reputation. * Shadow SaaS & OAuth Access Control to have full visibility of applications employees are using, and to block users from granting OAuth permissions to unauthorized enterprise applications.
Hunting methods
The source does not provide specific hunting queries but notes that the stealthy nature of the attack makes it difficult to detect. It also mentions that traditional methods of detecting malicious extensions, such as relying on permissions or involved sites, are not sufficient, and that a browser-native solution is required to monitor the runtime behavior of each extension.
Original link: https://labs.sqrx.com/browser-syncjacking-cc602ea0cbd0
ClickFix vs. traditional download in new DarkGate campaign
Summary
A recent malvertising campaign used a combination of “ClickFix” social engineering tactics and traditional malicious file downloads to distribute the DarkGate malware loader. The ClickFix method involves tricking users into copying and executing malicious code through a fake CAPTCHA or similar page. The traditional method relies on luring victims to download a malware-laden installer, sometimes with a digital signature to appear legitimate. The threat actors alternated between these two methods, likely to determine which approach yields more successful malware installs. This campaign targeted the Notion brand with malicious Google ads that redirected users to lookalike websites.
Technical Details
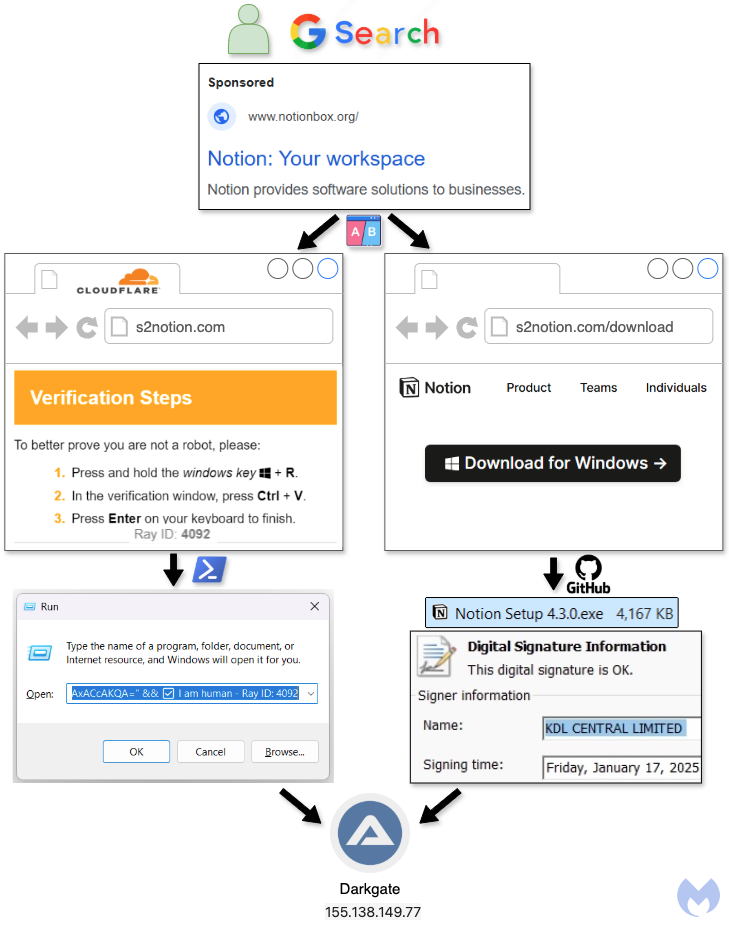 This campaign used two distinct methods to deliver the DarkGate malware loader.
This campaign used two distinct methods to deliver the DarkGate malware loader.
Delivery #1: ClickFix Technique
- Malicious Ad: The attack begins with a malicious Google ad for Notion, which redirects users to a fake Cloudflare Turnstile page, a common CAPTCHA-like verification step.
- Social Engineering: The fake Cloudflare page is actually a social engineering trick. The HTML source code is obfuscated with a Rot13 cipher and contains Russian comments, likely to obscure the malicious code from network rules and casual observation.
- Verification Steps: After checking the box, the victim sees new instructions that involve key combinations such as Windows key + R (to open the Run dialog) and Ctrl + V (to paste the clipboard’s contents). These actions are meant to trick the user into running malicious code.
- PowerShell Payload: The code pasted into the Run dialog is a command line that executes a Base64 encoded PowerShell script. This script fetches another piece of code from hxxps[:]//s2notion[.]com/in.php?action=1. This downloaded script in turn downloads a binary from hxxps[:]//s2notion[.]com/in.php?action=2 and executes it.
- AutoIt Script: The binary downloads an AutoIt script that is executed and it delivers the DarkGate malware.
- DarkGate Configuration: The AutoIt script extracts the DarkGate configuration.
Delivery #2: Traditional File Download
- Malicious Ad: In this method, the same malicious Google ad for Notion redirects users to a webpage with a “Download for Windows” button. The URL path includes “/download/”.
- Decoy Site: The decoy site mimics a legitimate download page for the Notion application.
- Malicious Executable: The downloaded executable is hosted on GitHub under the user profile herawtisabela1992. The file is named “Notion Setup 4.3.0.exe”.
- Digital Signature: This executable is digitally signed by KDL CENTRAL LIMITED, although this signature has since been revoked.
- AutoIt Payload: Like the ClickFix method, the downloaded executable extracts and runs an AutoIt payload which then installs the DarkGate malware. The configuration of DarkGate is the same as in the ClickFix delivery method.
Recommendations
The source recommends using a product that is capable of detecting the malware, and specifically mentions Malwarebytes as a solution.
IOC
Domains:
notionbox[.]org
s2notion[.]com
File Hashes:
6b6676267c70fbeb3257f0bb9bce1587f0bdec621238eb32dd9f84b2bcd7e3ea
4fe8bbc88d7a8cc0eec24bd74951f1f00b5127e3899ae53de8dabd6ff417e6db
Original link: https://www.malwarebytes.com/blog/cybercrime/2025/01/clickfix-vs-traditional-download-in-new-darkgate-campaign
Lumma Stealer’s GitHub-Based Delivery Explored via Managed Detection and Response
Summary
This article details a campaign where Lumma Stealer malware was distributed through GitHub’s release infrastructure. Attackers used GitHub to host malicious files, which included SectopRAT, Vidar, and Cobeacon. The initial access was gained by users downloading these files from GitHub URLs. The downloaded files then executed additional malware and exfiltrated sensitive data. The tactics used are similar to those of the Stargazer Goblin group. The attackers compromised legitimate websites to redirect victims to GitHub-hosted malware. The malware uses techniques to avoid detection and establish persistence, such as PowerShell scripts and shell commands. The campaign used multiple malware families, indicating an attempt to maximize operational impact.
Technical Details
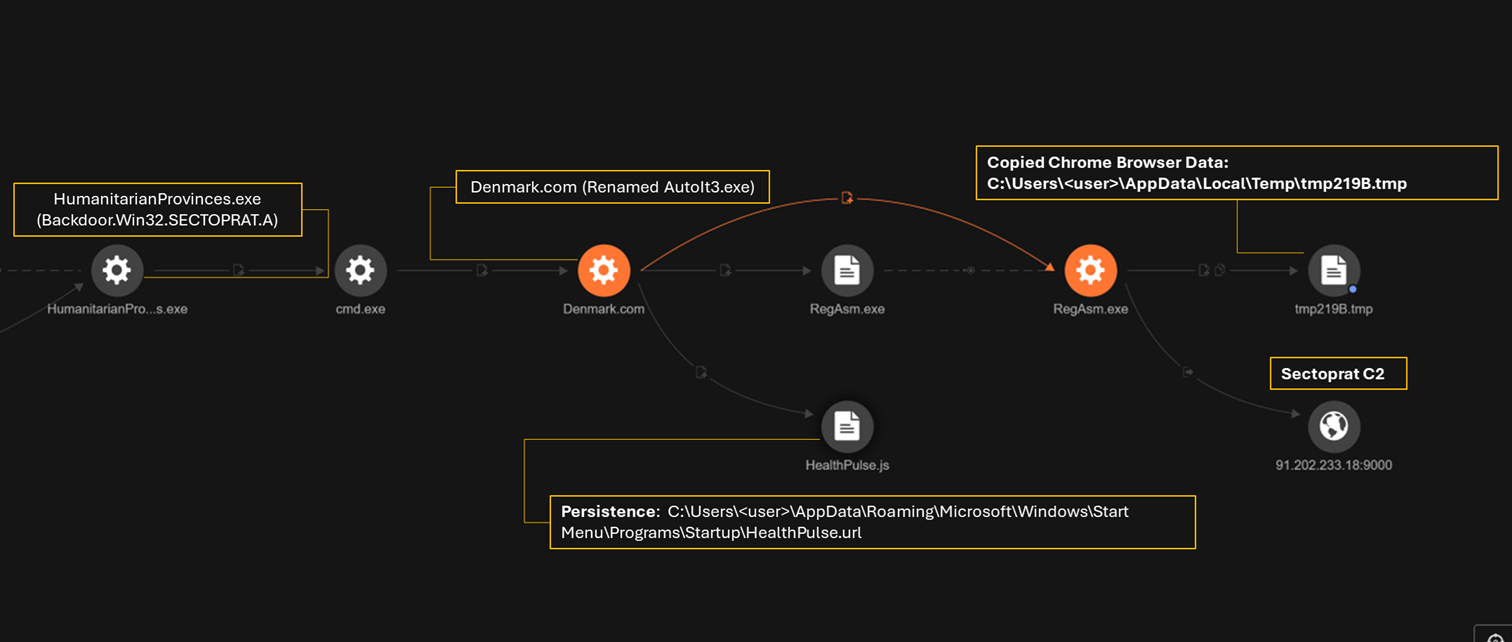 The attack begins with users downloading malicious files such as Pictore.exe and App_aeIGCY3g.exe from GitHub. These files are Lumma Stealer variants, an information-stealing malware. These executables, originally signed by ConsolHQ LTD and Verandah Green Limited, had their certificates revoked. The files use 7zip to extract further malware components. These components include nsis7z.dll and a 7zip archive app-64.7z, which contains the Lumma Stealer and associated files. The files are extracted to a temporary directory and include Chromium resources, which indicate the malware is built using the Electron framework.
The attack begins with users downloading malicious files such as Pictore.exe and App_aeIGCY3g.exe from GitHub. These files are Lumma Stealer variants, an information-stealing malware. These executables, originally signed by ConsolHQ LTD and Verandah Green Limited, had their certificates revoked. The files use 7zip to extract further malware components. These components include nsis7z.dll and a 7zip archive app-64.7z, which contains the Lumma Stealer and associated files. The files are extracted to a temporary directory and include Chromium resources, which indicate the malware is built using the Electron framework.
Lumma Stealer connects to external C&C servers. Pictore.exe connects to 192[.]142[.]10[.]246:80 and 192[.]178[.]54[.]36:443, while App_aeIGCY3g.exe connects to 84[.]200[.]24[.]26:80. The malware exfiltrates system information including RAM size, display adapter, OS version, hostname, uptime, user directory paths, and temporary directory content to the C&C servers. This data is sent via HTTP requests to the C&C servers’ /login.php endpoints. The malware uses shell commands to gather information about GPU and network configurations. It also uses PowerShell for malicious activities and reconnaissance via the command line, such as searching the setupact.log file for boot environment details, gathering the computer’s domain name, and setting the active code page number.
The initial Lumma Stealer files drop additional malware such as SectopRAT, Vidar and another Lumma Stealer variant. SectopRAT files are created in randomly-named folders in the temp directory and executed via cmd.exe. SectopRAT renames the file Signup to Signup.cmd. The script concatenates multiple files, creates directories, introduces delays, and performs reconnaissance. It searches for the presence of security software. The malware also uses AutoIt3.exe, which is renamed to Denmark.com, to execute malicious files. The malware then copies Chrome browser data and uses RegAsm.exe to connect to the C&C server at 91[.]202[.]233[.]18:9000. Persistence is achieved by creating a shortcut file (HealthPulse.url) in the Startup folder which executes HealthPulse.js, then HealthPulse.scr. On some machines, SectopRAT creates a scheduled task named Lodging to execute Quantifyr.js every five minutes.
Vidar malware is also dropped via the file DesignersCrawford.exe, and uses Privilege.com (renamed AutoIt3.exe), as a facilitator. Vidar launches Chrome with a specific remote debugging port and default user profile. It copies data from Discord, Chrome, Edge, Firefox, and OneDrive to C:\ProgramData\S2VKXL68GLN7<6 random char>, then connects to 5[.]75[.]212[.]196:443. It also connects to the domain ikores[.]sbs. After data exfiltration, it deletes the folder containing the copied data. A variant of Lumma Stealer is also dropped via the file ResetEngaging.exe, which uses Fabric.com (AutoIt3.exe) and connects to lumdukekiy[.]shop. This variant creates a PowerShell script that contacts external domains and downloads and extracts a zip file.
The campaign redirects users to malicious GitHub release links by compromising legitimate websites using injected PHP scripts and basic image files. The analysis of downloaded files reveals a consistent URL pattern containing the string page, indicating a naming convention. The compromised websites were previously legitimate, with some dating back to 1999. The GitHub accounts used were newly created and had minimal activity. The repository names and Readme.md content often mirrored each other.
Recommendations
The article recommends the following to prevent infections:
- Validate URLs and files before downloading, especially from platforms such as GitHub.
- Inspect links and attachments in unsolicited emails.
- Regularly check the validity of digital certificates for executables.
- Use endpoint security solutions to detect unauthorized shell commands.
- Block communication with known malicious IP addresses and enforce strict firewall rules.
- Train employees to recognize phishing emails and malicious websites.
- Partner with an MDR provider to gain access to specialized expertise and real-time threat detection.
- Incorporate threat intelligence into your security posture using tools such as Trend Vision One.
- Regularly patch operating systems, browsers, and third-party applications.
- Enable Multi-Factor Authentication (MFA) on all accounts.
- Adopt a zero-trust approach.
Hunting methods
The article provides the following hunting query for Trend Vision One customers:
malName:LUMMASTEALER* AND eventName:MALWARE_DETECTION AND LogType: detection*
IOC
IP Addresses:
192[.]142[.]10[.]246
192[.]178[.]54[.]36
84[.]200[.]24[.]26
91[.]202[.]233[.]18
5[.]75[.]212[.]196
Domains:
ikores[.]sbs
lumdukekiy[.]shop
File Hashes:
de6fcdf58b22a51d26eacb0e2c992d9a894c1894b3c8d70f4db80044dacb7430
afdc1a1e1e934f18be28465315704a12b2cd43c186fbee94f7464392849a5ad0
b87ff3da811a598c284997222e0b5a9b60b7f79206f8d795781db7b2abd41439
cd207b81505f13d46d94b08fb5130ddae52bd1748856e6b474688e590933a718
823d37f852a655088bb4a81d2f3a8bfd18ea4f31e7117e5713aeb9e0443ccd99
380920dfcdec5d7704ad1af1ce35feba7c3af1b68ffa4588b734647f28eeabb7
d8ae7fbb8db3b027a832be6f1acc44c7f5aebfdcb306cd297f7c30f1594d9c45
15b195152a07bb22fec82aa5c90c7ff44a10c0303446ce11f683094311a8916b
800c5cd5ec75d552f00d0aca42bdaede317f12aa797103b9357d44962e8bcd37a
5550ea265b105b843f6b094979bfa0d04e1ee2d1607b2e0d210cd0dea8aab942
3e8ef8ab691f2d5b820aa7ac805044e5c945d8adcfc51ee79d875e169f925455
feed69653299522cfbee13895dc259300da62293
0dcc5779743a2e744c6d5efd92f2444a4c309c59293928453a5c907fd68cd
61722dbacb774466d62c014e67a1e1348e
Original link: https://www.trendmicro.com/en_us/research/25/a/lumma-stealers-github-based-delivery-via-mdr.html
New TorNet backdoor seen in widespread campaign
Summary
This article details a financially motivated threat actor targeting users, primarily in Poland and Germany, since July 2024. The threat actor uses phishing emails with attachments to deliver various payloads, including Agent Tesla, Snake Keylogger, and a new backdoor called TorNet. The phishing emails impersonate financial institutions and manufacturing and logistics companies. The actor compresses the malicious attachment files using GZIP to disguise their content and evade email detections. The actor uses a .NET loader executable to download encrypted PureCrypter malware from compromised staging servers. PureCrypter then drops and runs the TorNet backdoor, which connects to a command and control (C2) server and the TOR network. The actor also disconnects and reconnects the victim machine from the network to avoid cloud antimalware detections and uses a Windows scheduled task for persistence, even when the device is on low battery. The TorNet backdoor can receive and run arbitrary .NET assemblies from the C2 server, which increases the attack surface for further intrusions.
Technical Details
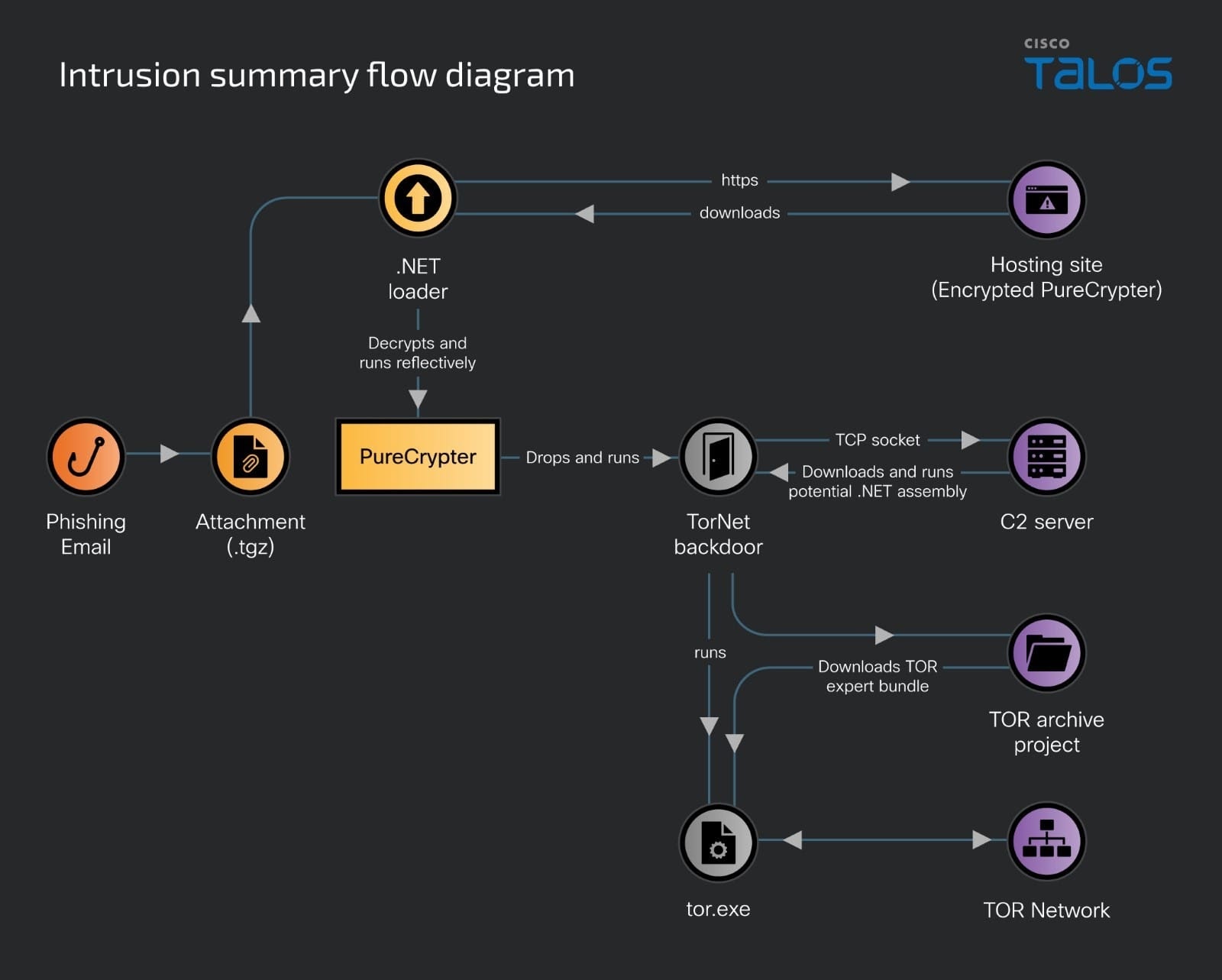
The attack begins with a phishing email that contains a .tgz attachment. When a user opens the attachment and runs a .NET loader executable, it downloads encrypted PureCrypter malware. The .NET loader may download the malware from a remote staging server or load an embedded malicious binary. The loader decrypts the PureCrypter malware using the AES algorithm and loads it into the system memory. PureCrypter is a Windows dynamic-link library obfuscated with Eziriz’s .NET Reactor obfuscator. It contains encrypted binaries of legitimate DLLs and the TorNet backdoor. PureCrypter creates a mutex on the victim machine and releases the DHCP IP address before establishing persistence, performing anti-analysis and detection tasks, and then drops and runs the payload. It then renews the IP address of the victim machine. This is likely a technique to evade detection from cloud-based anti-malware programs.
PureCrypter performs various checks, including anti-debugger checks using the “CheckRemoteDebuggerPresent” function. It also checks for the presence of Sandboxie and Cuckoo sandbox environments. It checks for virtual environments by executing WMI queries and searching for specific strings and checks for the “vmGuestLib.dll”. It checks for specific usernames and searches for strings related to “amsi.dll” and “amsiscanbuffer”. It also checks if Event Tracing for Windows (ETW) is configured by looking for processes that point to “EtwEventWrite”. It modifies Windows Defender settings by adding its process and the path of the dropped backdoor to the exclusion lists.
After the evasion checks, PureCrypter decrypts and drops the TorNet backdoor in the user profile application temporary folder with a random file name. PureCrypter establishes persistence in the Run registry key and creates a Windows task that executes the loader every two to four minutes. This task is designed to run even if the machine is on battery power. A Visual Basic script is dropped in the Windows startup folder to load and execute the backdoor. The backdoor is loaded by accessing it through a URL scheme “file[://]
The TorNet backdoor is also obfuscated with Eziriz’s .NET Reactor obfuscator. It decodes a base64-encoded string to obtain the C2 domain, port number, and a 16-character alphanumeric string. TorNet performs similar anti-debugging, anti-malware, anti-VM, and sandbox evasion checks as PureCrypter. It establishes a TCP socket connection to the C2 server by resolving the IP address of the C2 domain. The C2 communication uses ports 8194, 7890, or 8410. It sends the decoded 16-character string to the C2 server after compressing it using the GzipStream function and encrypting it with the triple DES algorithm, using an MD5 hash of the same string as a key. The C2 server may respond with an arbitrary encrypted .NET assembly, which TorNet decrypts and runs reflectively. TorNet also connects the victim machine to the TOR network by downloading the TOR expert bundle and running “tor[.]exe”. It routes all traffic from the backdoor process through the TOR network to anonymize C2 communication.
Countries
Poland and Germany
Industries
Financial institutions, manufacturing and logistics companies
Recommendations
Cisco Secure Endpoint is recommended to prevent the execution of the malware. Cisco Secure Web Appliance web scanning prevents access to malicious websites. Cisco Secure Email can block malicious emails. Cisco Secure Firewall appliances can detect malicious activity. Cisco Secure Malware Analytics identifies malicious binaries. Umbrella blocks users from connecting to malicious domains, IPs, and URLs. Cisco Secure Web Appliance automatically blocks dangerous sites and tests suspicious sites. Additional protections with context to specific environments are available from the Firewall Management Center. Cisco Duo provides multi-factor authentication for users. Open-source Snort Subscriber Rule Set customers can download the latest rule pack.
Hunting methods
Snort SIDs: 64440, 64439, 64437, 64438, and 301115
ClamAV detections:
Win.Backdoor.TorNet-10041435-0
Win.Downloader.TorNet-10041463-0
Win.Malware.TorNet-10041565-0
Win.Malware.TorNet-10041601-0
Win.Trojan.TorNet-10041734-0
IOC
IP Addresses:
104[.]168[.]7[.]37
Domains:
italzformingdinggallores[.]duckdns[.]org
Original link: https://blog.talosintelligence.com/new-tornet-backdoor-campaign/
One policy to rule them all
Summary
This article discusses the use of Windows group policies as a powerful management tool that can be exploited by attackers to distribute malware, execute hidden scripts, and deploy ransomware. The article examines how cybercriminals exploit group policies as an attack vector, the risks associated with these attacks, and measures to protect against potential threats. Group Policy Objects (GPOs) consist of a Group Policy Container (GPC) and a Group Policy Template (GPT). The GPC is an Active Directory container holding information about the GPO, while the GPT is a collection of files and folders on the SYSVOL system volume, containing settings, scripts, and presets. Attackers exploit vulnerabilities in group policies to gain control over networks, create local users/administrators, create malicious scheduled tasks, run tasks on behalf of the system or user, and change the registry configuration. Attackers need WriteProperty permissions on the gPCFileSysPath attribute within the GPO to modify policies. The article also highlights that attackers may modify the gPCFileSysPath attribute to point to a network resource under their control, allowing them to distribute malicious policies. Detection methods using event 5136 are detailed to monitor changes to group policy attributes, including gPCMachineExtensionNames, gPCUserExtensionNames, and gPCFileSysPath. The article concludes that group policies, while useful, require close monitoring and constant security to prevent exploitation by malicious actors.
Technical Details
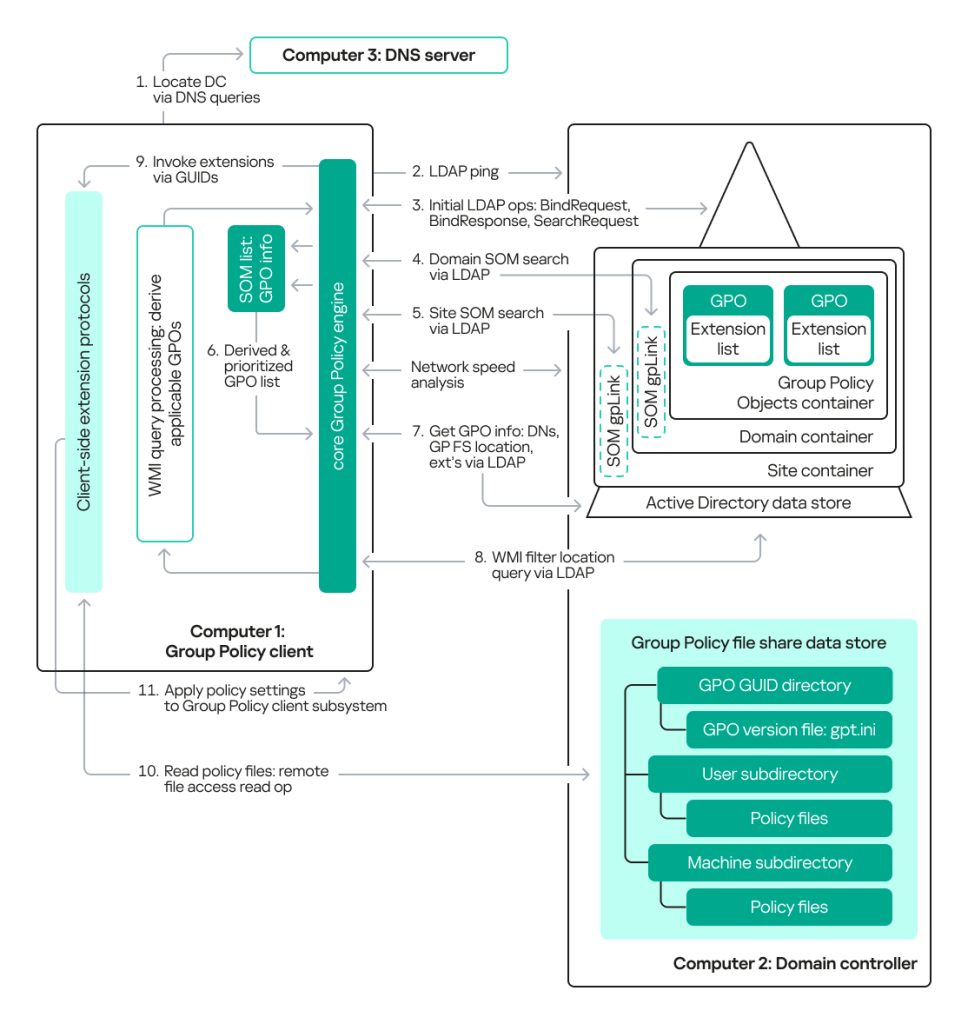 Group Policy Objects (GPOs) are composed of a Group Policy Container (GPC) and a Group Policy Template (GPT). A GPC is an Active Directory container that stores information about the GPO version and status. A GPT is a collection of files and folders stored on the SYSVOL system volume of each domain controller. These files contain settings, scripts, and presets for users and computers. The path to each template is stored in the gPCFileSysPath attribute of the group policy container. The attributes gPCMachineExtensionNames and gPCUserExtensionNames contain GUIDs for Client Side Extensions (CSE) that are distributed to user and/or computer settings. These extensions are implemented using libraries containing functions for applying settings, with the GUID providing information about which library needs to be loaded.
Group Policy Objects (GPOs) are composed of a Group Policy Container (GPC) and a Group Policy Template (GPT). A GPC is an Active Directory container that stores information about the GPO version and status. A GPT is a collection of files and folders stored on the SYSVOL system volume of each domain controller. These files contain settings, scripts, and presets for users and computers. The path to each template is stored in the gPCFileSysPath attribute of the group policy container. The attributes gPCMachineExtensionNames and gPCUserExtensionNames contain GUIDs for Client Side Extensions (CSE) that are distributed to user and/or computer settings. These extensions are implemented using libraries containing functions for applying settings, with the GUID providing information about which library needs to be loaded.
A client determines which policies to apply by making an LDAP query to the domain controller, which returns a set of policies called the Scope of Management (SOM). The gpLink attribute connects organizational units (OUs) to the GPOs that apply to them. To modify policies, attackers need WriteProperty permissions on the gPCFileSysPath attribute within the GPO. Attackers use tools such as SharpGPOAbuse to modify GPOs. During GPO modification, a new task is added to the GPT on SYSVOL as an XML file. The versionNumber attribute and the version number in the GPT.ini file are then changed, so the client can detect a newer version of the policy. Event 5136 is generated whenever an Active Directory object is modified, which can be used to track these changes. When creating a custom policy, the gPCUserExtensionNames attribute is modified to include CSE GUID values.
Attackers can also modify the gPCFileSysPath attribute to specify a path to a network resource they control. This forces clients to retrieve templates from this attacker-controlled resource, which is a technique used in a GPOddity attack. The tool spins up an SMB server, creates malicious policies, changes the path to the GPT, and then restores it to its original state after applying the modified policies. The ability to store GPTs outside of the SYSVOL system folder is considered a feature by Microsoft, though they do not recommend it because it can break certain Windows mechanisms. To detect this, event 5136 is monitored for modifications to the gPCFileSysPath attribute. A filter can be added to exclude events generated when creating a new GPO with a standard GPT path.
Compromise Assessment projects involve searching for compromises via group policies using tools such as Group3r, which identifies suspicious policies and vulnerabilities. A script can be used to identify GPOs that have had their gPCFileSysPath attribute changed. SharpHound is another tool that can identify GPO configuration errors and potential attack vectors. The GCNet tool, based on Microsoft’s PoC, is used to monitor directory service changes by connecting to the LDAP database and subscribing to changes in the CN=Policies attribute. When a policy change notification is received, detailed information about the corresponding GPO, including GPC and GPT data, is requested. Detected events are run through detection rules to identify malicious policies, while also analyzing attributes such as GPLink options and policy flags to provide more context to the threat. Group policies update every 90 minutes (+/- 30 minutes) on client machines, and every 5 minutes on the domain controller.
Recommendations
The article recommends that group policies must be closely monitored and constantly secured. It also suggests tracking changes in group policies and responding to detected threats as part of a Managed Detection and Response (MDR) service.
Hunting methods
The article provides several detection rules based on modifications to GPO attributes:
- Detecting the addition of new privileges through GPOs by monitoring event 5136 for changes to gPCMachineExtensionNames with specific GUID values.
- Detecting the addition of new autorun scripts through GPOs by monitoring event 5136 for changes to gPCMachineExtensionNames or gPCUserExtensionNames with specific GUID values.
- Detecting the addition of new scheduled tasks using GPOs by monitoring event 5136 for changes to gPCMachineExtensionNames or gPCUserExtensionNames with specific GUID values.
- Detecting changes to the gPCFileSysPath attribute by monitoring event 5136 for modifications to this attribute, excluding the standard path when creating new GPOs.
Original link: https://securelist.com/group-policies-in-cyberattacks/115331/