The Feed 2025-02-05

AI Generated Podcast
https://open.spotify.com/episode/54nB0hiPimW1l6c00bAj1U?si=SgezrKmNSJ2x899ECOR-6w
Summarized Sources
-
CVE-2023-6080: A Case Study on Third-Party Installer Abuse: Mandiant discovered a privilege escalation vulnerability in the SysTrack installer that could be exploited by a low-privilege user due to insecure file handling during the repair process.
Original link: https://cloud.google.com/blog/topics/threat-intelligence/cve-2023-6080-third-party-installer-abuse/ -
CVE-2025-0411: Ukrainian Organizations Targeted in Zero-Day Campaign and Homoglyph Attacks: A zero-day vulnerability in 7-Zip (CVE-2025-0411) was exploited by Russian cybercrime groups to target Ukrainian organizations using double archiving and homoglyph attacks to bypass security measures.
Original link: https://www.trendmicro.com/en_us/research/25/a/cve-2025-0411-ukrainian-organizations-targeted.html -
Ongoing Email Bombing Campaigns leading to Remote Access and…: Threat actors are using email bombing, followed by Microsoft Teams messages, to gain remote access and deploy malware on victim systems.
Original link: https://www.esentire.com/security-advisories/ongoing-email-bombing-campaigns-leading-to-remote-access-and-post-exploitation -
Stealers on the Rise: A Closer Look at a Growing macOS Threat: Three prevalent macOS infostealers, Atomic, Poseidon, and Cthulhu, are being used to steal sensitive information from macOS systems, often leveraging AppleScript and social engineering tactics.
Original link: https://unit42.paloaltonetworks.com/macos-stealers-growing/ -
Uncovering Cyber Threat Networks: SmartApeSG & NetSupport RAT | Cymru: An investigation into the SmartApeSG FakeUpdate threat, which delivers NetSupport RAT, uncovered a complex network of interconnected infrastructure involving other RATs, cryptocurrency services, and illicit platforms, highlighting the importance of analyzing internet telemetry data.
Original link: https://www.team-cymru.com/post/tracing-the-path-from-smartapesg-to-netsupport-rat
CVE-2023-6080: A Case Study on Third-Party Installer Abuse
Summmary
Mandiant discovered a local privilege escalation vulnerability, CVE-2023-6080, in Lakeside Software’s SysTrack Agent version 10.7.8. An attacker with low-privilege access could exploit flaws in the Microsoft Software Installer (MSI) repair action of the SysTrack installer to achieve arbitrary code execution. The vulnerability stems from insecure coding practices in MSI Custom Actions, such as references to missing files or insecure folder permissions. During an MSI repair, operations can be triggered from an NT AUTHORITY\SYSTEM context, creating opportunities for privilege escalation. The SysTrack MSI performed file operations in the user’s %TEMP% folder, allowing a low-privilege user to alter files used in a high-privilege context. The software’s filename generation had a failover mechanism, allowing an attacker to force the application to use a predetermined filename. This vulnerability was addressed in SysTrack version 11.0.
Technical Details
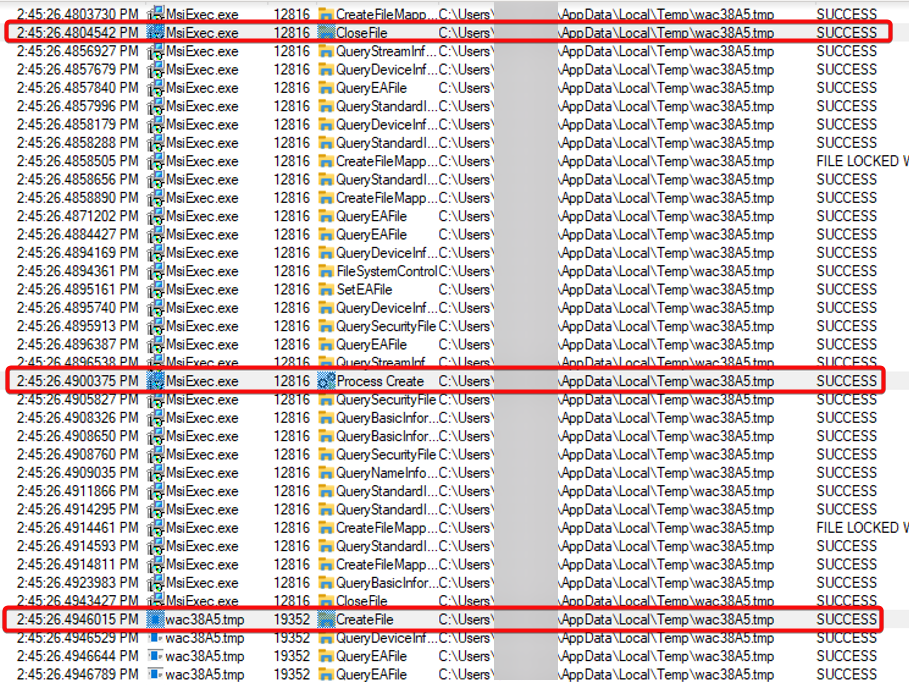
The attack leverages the MSI repair function, which is intended to fix issues with installed software, but can be exploited due to insecure coding practices in MSI Custom Actions. When software is installed using an MSI file, Windows caches it, allowing users to initiate the repair feature. During the repair process, several operations can be triggered from an NT AUTHORITY\SYSTEM context, even when initiated by a low-privilege user, creating a privilege escalation vulnerability.
Mandiant used Microsoft’s Process Monitor (ProcMon) to analyze file operations during the SysTrack MSI repair process. They observed that MSIExec.exe wrote a new .tmp file to the user’s %TEMP% folder and executed it. The filename was generated using a formula, starting with “wac” followed by four random hexadecimal characters, resulting in 65,535 possible filenames. Since the %TEMP% folder is writable by low-privilege users, Mandiant tested the repair tool’s behavior after creating all possible .tmp files. They used a PowerShell script to copy a test executable to all possible filenames (wac0000.tmp to wacFFFF.tmp) in the %TEMP% folder. When all possible names were used, the application would failover to an incrementing filename pattern starting with wac1.tmp.
Mandiant then observed a delay between file creation and execution. By creating wac1.tmp and wac2.tmp, they forced the repair function to use wac3.tmp. This predictable filename pattern was leveraged using a PowerShell script to win the race condition by copying a test executable to wac3.tmp between the file write and execution by MSIExec.exe, overwriting the file created by MSIExec.exe. This resulted in the test.exe file being executed by MSIExec.exe, opening cmd.exe as NT AUTHORITY\SYSTEM.
Recommendations
Software developers should follow secure coding practices and review their implemented Custom Actions to prevent attackers from exploiting high-privilege operations triggered by the MSI repair functionality. Folder permissions should be carefully managed to ensure privileged file operations are performed from secured folders, such as C:\Program Files or C:\Program Files (x86). When using randomized filenames, developers should use a sufficiently large length to prevent attackers from exhausting all possibilities and forcing the application into unexpected behavior. Companies should audit the security of their endpoints to ensure defense in depth is maintained. Monitor the spawning of administrative shells such as cmd.exe and powershell.exe in an elevated context to alert on possible privilege escalation attempts.
Original link: https://cloud.google.com/blog/topics/threat-intelligence/cve-2023-6080-third-party-installer-abuse/
CVE-2025-0411: Ukrainian Organizations Targeted in Zero-Day Campaign and Homoglyph Attacks
Summmary
A zero-day vulnerability, CVE-2025-0411, in the 7-Zip archiver was exploited in a campaign targeting Ukrainian organizations. The vulnerability allows attackers to bypass Windows Mark-of-the-Web (MoTW) protections by double archiving files. This bypass enables the execution of malicious content without the usual security checks. Russian cybercrime groups actively exploited this vulnerability using spear-phishing emails with homoglyph attacks to disguise malicious file extensions. The attacks were aimed at both Ukrainian government and civilian organizations as part of the ongoing Russo-Ukraine conflict. The vulnerability was patched in 7-Zip version 24.09. The exploitation of CVE-2025-0411 represents the first known instance where a homoglyph attack was integrated into a zero-day exploit chain. This campaign also targeted smaller local Ukrainian government bodies that are often under cyber pressure and lack comprehensive cyber security resources.
Technical Details
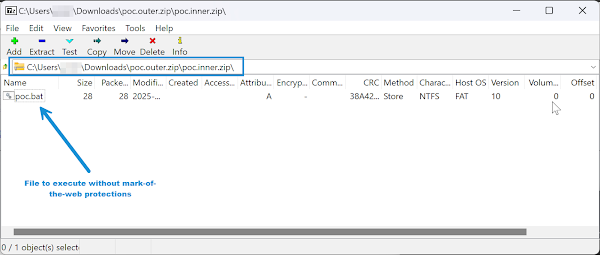
The vulnerability, CVE-2025-0411, allows attackers to bypass the Windows MoTW security feature. MoTW flags files downloaded from untrusted sources, such as the internet, by adding an Alternate Data Stream (ADS) named Zone.Identifier to the file. This stream contains the text ZoneId=3, indicating the file came from the internet and should be treated with caution. This security measure helps prevent automatic execution of harmful scripts and allows Windows to perform extra security checks via Microsoft Defender SmartScreen.
The vulnerability is exploited by double-archiving files using 7-Zip. This involves encapsulating an archive within another archive. The root cause of the vulnerability is that prior to version 24.09, 7-Zip did not properly propagate MoTW protections to the contents of double-encapsulated archives. This enables the creation of archives containing malicious scripts or executables that will not receive MoTW protections, leaving Windows users vulnerable to attacks.
Attackers used spear-phishing campaigns with compromised Ukrainian email accounts to deliver malicious 7-Zip attachments. These attachments contained a nested archive structure. For instance, an outer archive named Документи та платежи.7z (Documents and payments) contained an inner archive named Спiсок.doс (List). The inner archive used a homoglyph attack where the “c” in the “.doc” extension was replaced with the Cyrillic character “Es,” which visually looks identical to the Latin letter “c”. This tricks the user and Windows into thinking the file is a .doc file. Inside the inner archive was a .url file that pointed to an attacker-controlled server hosting another ZIP archive. Once the user opens the .url file the final payload, a SmokeLoader executable, is downloaded and executed leading to a full system compromise.
Homoglyph attacks are a type of attack using similar-looking characters to trick users into clicking suspicious files or visiting malicious websites. This attack technique is commonly used in phishing campaigns to spoof legitimate websites or files. For example, an attacker might use the Cyrillic letter Es in a domain name to spoof a legitimate domain.
Countries
Ukraine
Industries
Ukrainian government and civilian organizations
Recommendations
Organizations should update 7-Zip to version 24.09 or later. Strict email security measures, including filtering and anti-spam technologies, should be implemented to block spear-phishing attacks. Employee training is essential to recognize phishing attempts, including homoglyph attacks on files and filetypes. Users should be educated on zero-day and n-day vulnerabilities, and the importance of MoTW, which helps prevent the automatic execution of potentially harmful scripts. The automatic execution of files from untrusted sources should be disabled, and systems should prompt users for verification before opening such files. Domain filtering and monitoring should be used to detect and block homoglyph-based phishing attacks. URL filtering should be used to block access to known malicious domains, and blacklists should be regularly updated.
Hunting methods
Trend Vision One customers can use the following query to identify related events: malName:*SMOKELOADER* AND eventName:MALWARE_DETECTION AND LogType: detection. More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
IOC
File Hashes:
- ba74ecae43adc78efaee227a0d7170829b9036e5e7f602cf38f32715efa51826
- 84ab6c3e1f2dc98cf4d5b8b739237570416bb82e2edaf078e9868663553c5412
- 7786501e3666c1a5071c9c5e5a019e2bc86a1f169d469cc4bfef2fe339aaf384
- 2e33c2010f95cbda8bf0817f1b5c69b51c860c536064182b67261f695f54e1d5
Original link: https://www.trendmicro.com/en_us/research/25/a/cve-2025-0411-ukrainian-organizations-targeted.html
Ongoing Email Bombing Campaigns leading to Remote Access and…
Summmary
eSentire has observed ongoing Email Bombing attacks where threat actors use phishing techniques to gain remote access to a host and install malware. These attacks involve overwhelming a user’s inbox with spam emails, followed by a Microsoft Teams message from a threat actor posing as IT support requesting a remote session. Once connected, the threat actor downloads malicious payloads for persistence, reconnaissance, credential theft, data exfiltration, and malware or ransomware deployment. These attacks are linked to ransomware campaigns. The threat actors use Microsoft remote control tools such as Quick Assist or Teams screen sharing to gain control of the target’s machine.
Technical Details
The attack begins with an email bombing campaign to overwhelm a user’s inbox. The threat actors then send a Microsoft Teams message, posing as the organization’s IT support, to the victim. This message requests a remote session to resolve the email issue. This is made possible by Microsoft Teams settings that allow external domains to initiate chats or meetings with internal users. During the remote session, the threat actor uses tools like Quick Assist or Teams screen sharing to gain control of the target’s machine. Once in control, the threat actor downloads malicious files. In one instance, the threat actor downloaded two files via the Microsoft Edge web browser, ‘kb052117-01.bpx’ and ‘kb052123-02.bpx’, from the domain ‘hxxps[://]filters6[.]s3[.]us-east-2[.]amazonaws[.]com/gtjs.html?t=drivers’. These files were then combined to create ‘pack.zip’. The threat actor extracted this file using ‘tar.exe’ and created ‘%TEMP%\arch1271.cab’, which was then copied to ‘%LOCALAPPDATA%\Microsoft\ODBC’. The ‘arch1271.cab’ file contained the malicious ‘wscapi.dll’ file that was executed via ‘odbcconf.exe’. Similar actions were performed in the ‘%LOCALAPPDATA%\Microsoft\OneDrive’ directory. The script also created a legitimate ‘OneDriveStandaloneUpdater.exe’ process in this directory. After these steps, the script prints ‘Filters installed successfully!’ to conceal the activity.
A registry key was added under ‘HKCU\SOFTWARE\TitanPlus’ containing C2 IPs. The script then deletes the ‘kb052117-01.bpx’, ‘kb052117-02.bpx’, and ‘pack.zip’ files. In other instances, PowerShell was used to download additional payloads and establish persistence, such as TeamViewer for persistence, XenArmor password recovery tool for credential theft, and a .NET DLL for command-and-control (C2) connections. The .NET DLL also loaded SharpShares in memory for network share discovery, and used Nltest for Domain Controller enumeration.
Recommendations
Organizations should restrict access to external Microsoft tenants unless necessary. The principle of least privilege should be followed to limit the impact of a security breach. Microsoft Teams messages and calls from external organizations should be restricted unless necessary, and if required, only allow messages and calls from trusted business partners. Remote access tools should be restricted via policy unless needed for normal operations. Anti-spam policies should be configured within Exchange Online to block malicious emails. User awareness training should be conducted to educate users about these attacks. Users should only grant remote access to verified tech support teams, and login credentials must be kept secure. Users should verify any request for access, especially those with a sense of urgency, and they should be aware of how to report potential security incidents.
Hunting methods
eSentire’s Threat Response Unit is performing threat hunts for known Indicators of Compromise across customer environments. eSentire MDR for Log has detections in place to identify Microsoft Teams messages originating from external accounts from high-risk sources. eSentire MDR for Endpoint has detections in place to identify domain reconnaissance, application control bypass attempts, as well as for malware and ransomware being deployed on an endpoint.
IOC
IP Addresses:
38[.]180[.]25[.]3
45[.]8[.]157[.]199
5[.]181[.]3[.]164
67[.]43[.]234[.]113
File Hashes:
0041E492A07AAC0B64AD907D44E6242BCA8A2193D492B8DD44EFC14170391E0F
26B16D28C42F3853D9AA571BD864E419B56B30A54BB5A8E596F70B2D227386402
2B3D230A76368B7B940BD069DD63C8FCD16E4DBFC888B127427062EE39BDD3CA
4F77EA80FF9ACA5752A6CF01A0C0FF070563E286659AB86F43EAC889341B0E13
2010A4701A0819B61579F916149AE0A5FE3D37D6939B3F66102717C925289B9C
73F3ED20F03168D25E658B0603E533CDB566B402
Domains:
hxxps[://]filters6[.]s3[.]us-east-2[.]amazonaws[.]com/gtjs.html?t=drivers
hxxps[://]filters6[.]s3[.]us-east-2[.]amazonaws[.]com/js/kb052117-01[.]bpx
hxxps[://]filters6[.]s3[.]us-east-2[.]amazonaws[.]com/js/kb052123-02[.]bpx
hxxps[://]filters6[.]s3[.]us-east-2[.]amazonaws[.]com/gtjs[.]html?t=drivers
hxxps[://]onedrive[.]live[.]com/download?resid=886E7DEE31E60678!116&authkey=!AFpMOei32rZTc4M
hxxps[://]drive[.]usercontent[.]google[.]com/u/0/uc?id=1xXbgBiLuM_D-Ak-J7bgRJefFvlfGY-fx
hxxps[://]drive[.]usercontent[.]google[.]com/u/0/uc?id=1IdT91pPHyRsDSQMyM7qXFlbVHG0F3a3r
hxxps[://]hatua[.]tech/mspsek/x
hxxps[://]hatua[.]tech/mspsek/7
hatua[.]tech
hxxps[://]ensol[.]co/wp-content/themes/twen/a[.]zip
ensol[.]co
Original link: https://www.esentire.com/security-advisories/ongoing-email-bombing-campaigns-leading-to-remote-access-and-post-exploitation
Stealers on the Rise: A Closer Look at a Growing macOS Threat
Summmary
This article discusses a rise in macOS infostealers, which are a type of malware designed to steal sensitive information such as financial data, credentials, and files. The article focuses on three prevalent infostealers: Atomic Stealer (AMOS), Poseidon Stealer, and Cthulhu Stealer. These stealers are often distributed through malicious installers and exploit the AppleScript framework, which can trick users into giving up credentials or disabling security controls. The infostealers are sold as Malware-as-a-Service (MaaS) and are used to collect a wide range of data, including browser data, cryptocurrency wallets, instant messaging data, and files. Infostealers can lead to data breaches, financial losses, and reputational damage. The article emphasizes that a proactive, multi-layered defense strategy is essential to protect assets. Palo Alto Networks products, such as Cortex XDR and XSIAM, offer protections against these threats.
Technical Details
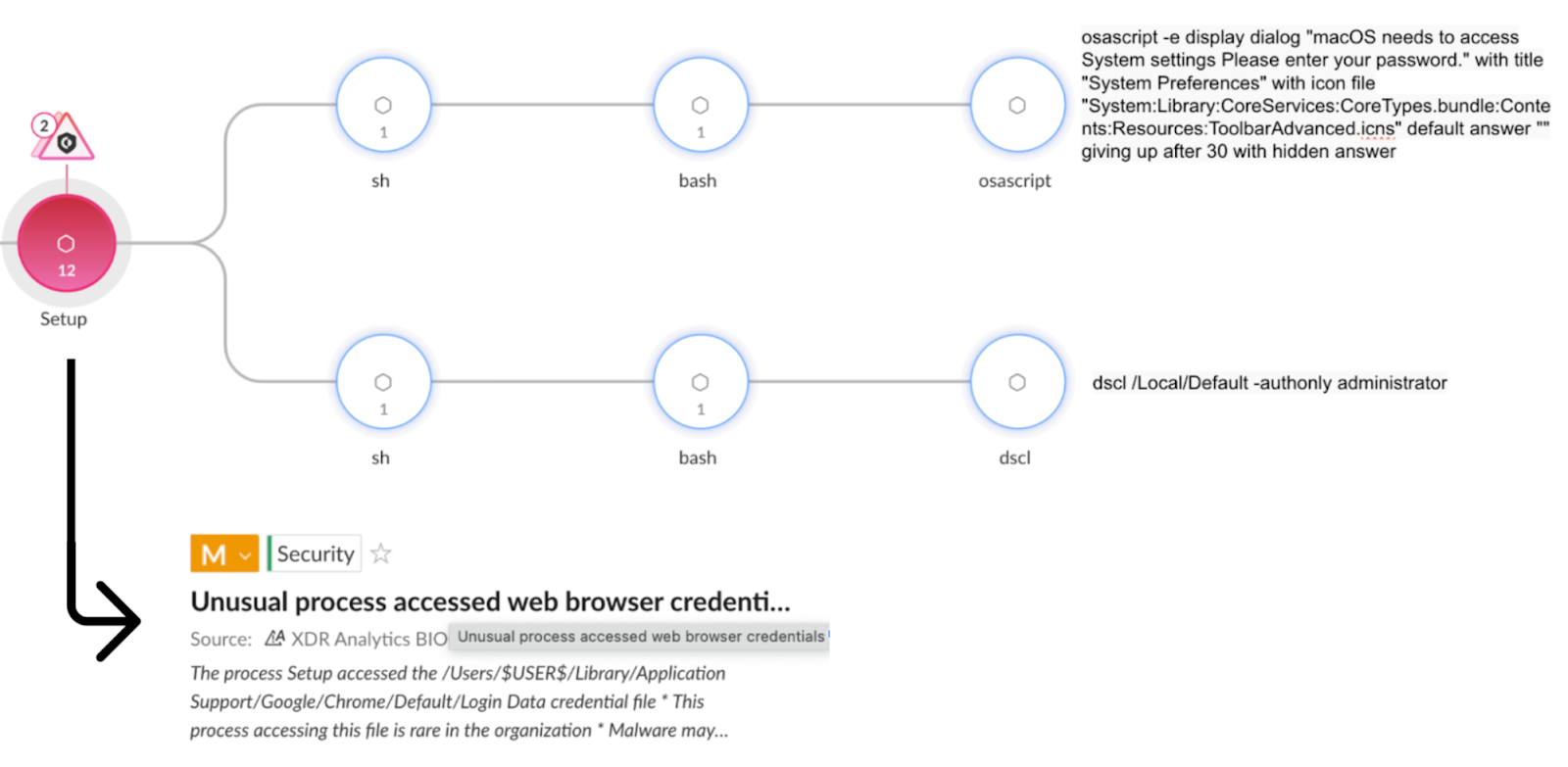
 The three infostealers discussed in the article are distributed through different methods, often using social engineering tactics.
The three infostealers discussed in the article are distributed through different methods, often using social engineering tactics.
Atomic Stealer (AMOS): This stealer, also known as AMOS, was discovered in April 2023. It is sold as MaaS on hacker forums and Telegram. The malware is capable of stealing notes, documents, browser data (passwords, cookies), cryptocurrency wallets, and instant messaging data (Discord, Telegram). Atomic Stealer is distributed via malvertising and has been observed in different versions, including those written in Go, C++, and using Python scripts or Mach-O binaries. The execution flow of Atomic Stealer involves accessing files that store Google Chrome login credentials.
Poseidon Stealer: This stealer is considered a fork or direct competitor of Atomic Stealer, and it is advertised in hacker forums by someone known as “Rodrigo4”. Poseidon Stealer is also sold as MaaS. It is distributed through Trojanized installers disguised as legitimate applications, often via Google ads and malicious spam emails. The malicious installer contains an encoded AppleScript file which decodes and executes during the installation process. It prompts users to enter their password via a dialog box, and the stolen data is sent to a command and control server. Poseidon uses AppleScript to gather system information, steal browser passwords, cookies, cryptocurrency wallets, user credentials, notes from the macOS Notes app, Telegram data, and passwords from BitWarden and KeePassXC.
Cthulhu Stealer: This infostealer is also sold as MaaS through Telegram by “Cthulhu Team”. Cthulhu Stealer is written in Go, and its operators distribute it via malicious application installers. Upon execution, the installer shows fake dialog boxes requesting system and MetaMask passwords. Cthulhu targets sensitive data from major browsers (Google Chrome, Microsoft Edge, Firefox), cryptocurrency wallets, FileZilla configuration files, Telegram data, note files from the macOS Notes app, Keychain and SafeStorage passwords, and files with specific extensions (e.g., .png, .jpg, .doc, .pdf). It also targets data related to the Battle[.]net gaming platform and Minecraft. Cthulhu Stealer saves stolen data in a directory at /Users/Shared/NW and uploads it to a command-and-control server.
All three stealers leverage the AppleScript framework, which allows extensive OS access and simplifies execution with natural language syntax. This allows threat actors to trick victims into providing credentials or disabling security controls. The execution of these threats is shown in Cortex XDR as unusual process that access credential or crypto wallet files.
Recommendations
The article recommends implementing advanced macOS detection modules to identify and counter these threats. Palo Alto Networks has developed Cortex XDR macOS Analytics suites, which include detection suites for:
- Credentials grabbing
- Sensitive information stealing
- Malicious AppleScript usage
These suites monitor sensitive file access and unusual AppleScript executions to identify malicious activities. In addition, the article notes that Cortex XDR and XSIAM can prevent the execution of known malware, prevent unknown malware using Behavioral Threat Protection, protect against credential gathering techniques, and detect infostealer threats by analyzing anomalous file access, AppleScript execution, and user activity. The article also mentions that the Advanced WildFire cloud-delivered malware analysis service can identify samples of these stealers, and that Advanced URL Filtering and Advanced DNS Security can identify malicious domains. Organizations should adopt a proactive and multi-layered defense strategy.
Hunting methods
The article does not explicitly mention hunting methods in the form of queries. However, it mentions that the Cortex XDR macOS Analytics suites are used for detecting malicious activities associated with the stealers. The suites are designed to detect techniques used to acquire credentials and to steal sensitive data, as well as monitor malicious AppleScript execution. The product analyzes anomalous file access, AppleScript execution and user activity from multiple data sources.
IOC
SHA256 Hashes for Examples of Atomic Stealer:
599e6358503a0569d998f09ccfbdeaa629d8910f410e26df0ffbd68112e77b05
a33705df80d2a7c2deeb192c3de9e7f06c7bfd14b84f782cf86099c52a8b0178
cfa8173e681bf6866e06b1a971dab03954b28d3626d96ac0827c5f261e7997cd
831f80f6e6f7be8352aba0b54b3e55ade63f8719c7e6f8cfa19ee34af5a07deb
a9fe32498f6132b9c39ae16524bdb3d71b451017a2d3acf117416a0dc9a89ce5
3eac9c66a712f74d9e93e24751220a74b2c7e5320c74f1f7b4931d8181c7f26c
IP Addresses for Atomic Stealer C2 Servers:
94.142.138[.]177
194.169.175[.]117
SHA256 Hashes for Examples of Poseidon Stealer:
9f4f286e5e40b252512540cc186727abfb0ad15a76f91855b1e72efb006b854c
5880430d86d092ac56bfa4aec7e245e3d9084e996165d64549ccb66b626d8c56
0bb4ba056d64fff21d13b53b5c1bd5ccb89bed27e66e2b7ff60ddcf47c1342b4
1b9b929e63be771393b6a4e526930eedb78f279174711bd2f19dfa8545f6e714
c4e7320945caf9dc4dca11f6ad0170bc6fc2148de0cdc8aa15a236b248165d39
a8aa1d7f940f0a8ccd516e52232b103d343826e13df9e4d9567f75e996683886
09852c1f67939efad0f0baeead5d23dc9cd53eec0f1f6069f041dfd4e0e83c3f
b94067535123dd236a075d54afa34fef80324f7d1375f55c29ca70393e6492b2
9390108ca021b5f5c8c25849c1d6903c8a30568e822ce22e01e96381ea2df3b5
IP Addresses for Poseidon Stealer C2 Servers:
194.59.183[.]241
70.34.213[.]27
SHA256 Hashes for Examples of Cthulhu Stealer:
2d232bd6a6b6140a06b3cf59343e3e2113235adcf3fb93e78fa3746d9679cfc3
d8d29c2906145771e1c12d6520a826c238d5672f256779326ba38859dfb9cf4c
6483094f7784c424891644a85d5535688c8969666e16a194d397dc66779b0b12
a772451ddd6897c00ce766949fc82e30cfb64a6b31b44bfd9068a76ab99dd188
ad32e638216b859855f78a856f8f4e3aea66add550619a4bde08754e2c218186
dd831c4aaaceb9f063642ae729956a716e29e0c5452526996e92959cca820914
57ece6ae15a8d16a24bad097b4455dc6aec4a24c139d62d05c59330620c3e90e
93f33e76c57240dda2b80b0270ad867a4c77ee7ad4ac135d086398e789e4dbc9
Original link: https://unit42.paloaltonetworks.com/macos-stealers-growing/
Uncovering Cyber Threat Networks: SmartApeSG & NetSupport RAT | Cymru
Summmary
This article details an investigation into a cyber threat network, starting with the analysis of SmartApeSG, a FakeUpdate threat that delivers NetSupport RAT. The investigation used internet telemetry data to uncover related C2 infrastructure, active NetSupport RAT servers, and connections to other suspicious activity. The findings suggest a link between SmartApeSG and NetSupport RAT clusters, as well as connections to Quasar RAT and cryptocurrency services. The threat actors used Moldovan IPs for C2 management, and updated their infrastructure with new IPs and domains. Despite reporting the malicious infrastructure, the threat actors have continued to evolve their operations. The investigation emphasizes how internet telemetry can help uncover interconnected threats and highlights the importance of reviewing older indicators for current utilization.
Technical Details
The investigation started by analyzing SmartApeSG C2 servers, a FakeUpdate threat that deceives users into installing a fake browser update and deploying NetSupport RAT. The C2 infrastructure was initially hosted on Stark Industries. Two hosts were observed connecting to the C2 servers over TCP/1500, and visiting one of these hosts revealed an ISPManager login page. This control panel software, popular among Russian-speaking users, is used for managing web servers. The default port for API authentication calls in ISPManager is the same as the one used by the C2s, indicating the hosts were likely used to manage the C2s using the API to perform automated tasks.
The investigation pivoted to two Moldovan IPs (5.181.156.16 and 5.181.157.69) that were connecting to the SmartApeSG C2 servers. Both IPs were hosted by MivoCloud, but had different open ports and hosted X.509 certificates. The first IP (5.181.156.16) used TCP/3389 (RDP) and TCP/5986, and its X.509 certificate had a subject and issuer of CN=55554rac. The second IP (5.181.157.69) used TCP/137, TCP/3389, and TCP/5985 and had a X.509 certificate subject and issuer as CN=MATRACHEDICIDGA. Internet telemetry data revealed that these two IPs were communicating with additional C2s over TCP/1500, with the first IP (5.181.156.16) interacting with SmartApeSG C2s more frequently. One day, the second IP (5.181.157.69) established a connection to 95.164.37.152:443, a known NetSupport RAT C2.
Further analysis of the NetSupport RAT C2 (95.164.37.152) revealed another Moldovan IP (5.181.158.15) connecting to it over TCP/443 for several months. This IP had open ports TCP/137, TCP/3389, and TCP/5985 and used a X.509 certificate with the subject and issuer CN=WIN-7FUHAU7D2HV, initially hosted on TCP/6778, but later updated to TCP/3389. This host was also communicating with seven other NetSupport RAT C2s over TCP/443 or TCP/447, with one C2 also showing connections over TCP/2552 for about a month. This IP was also connecting to derelay.rabby[.]io, a public relay for Rabby Wallet.
Most of the NetSupport RAT C2s had been publicly reported a year prior, but were still active. Some of the C2s also established connections to fex[.]net, a Russian-language file-sharing service. One C2 (194.31.109.74), that had a X.509 certificate with the subject and issuer CN=MATRACHEDICIDGA (matching the SmartApeSG management host), was communicating with 193.107.109.76, which was reported as a Lycantrox C2 in 2023 and later as a Quasar RAT C2 in August 2024. This communication occurred primarily over TCP/1488, and occasionally over TCP/54664. The investigation pivoted to the Quasar RAT C2, revealing around 15 hosts communicating with it. Many of these hosts used the X.509 certificate CN=DESKTOP-TCRDU4C. Some of the hosts were used for Tox, Telegram, and Jabber server communication. Other hosts appeared to be part of a proxy network, while some others were used in cryptocurrency scams and visited Russian-language marketplaces and forums. One of the hosts that communicated with the Quasar RAT C2 over TCP/54663 made SSH connections to cryptocurrency scam sites, and impersonated a legitimate investment bank.
Countries
Moldova
Industries
Financial services (indirectly, through cryptocurrency scams)
Recommendations
The article recommends using the shared Indicators of Compromise (IOCs) for hunting, and to review older indicators for current utilization.
Hunting methods
The article suggests that Pure Signal users can hunt for this activity by querying for the IOCs or based on characteristics such as X.509 certificate common names.
IOC
IP Addresses:
5.181.156.16
5.181.157.69
5.181.158.15
95.164.37.152
194.31.109.74
193.107.109.76
5.181.159.111
5.181.159.113
5.181.159.119
45.8.145.132
45.67.35.101
185.153.183.59
Domains:
derelay.rabby[.]io
fex[.]net
exploit[.]im
ubsglobalmarkets[.]com
k-trades[.]com
rivosgroup[.]com
23mtkro[.]cn
allenew1[.]com
asdgelvasd[.]icu
asdsrjhegrhj[.]xyz
comparegjs[.]com
dgdsrzzw45tg[.]cn
dsfygfnb3[.]icu
duvje6egvuas[.]com
dvtrstrhdbcvbxr[.]xyz
e3ubj753ifg[.]xyz
fdoshbjdo[.]icu
fufvnasie[.]icu
gfu6nfmgnm86gm[.]xyz
gjuauyfhjha[.]cn
gkdkr[.]icu
gsdgtruhu45[.]cn
huntaget[.]cn
isaydiuaysoidalkspw[.]com
jintsung[.]cn
jkhmzxvidfyidu[.]xyz
mgsubneu4hgba[.]xyz
mixuvvvjsurub[.]cn
moreeu[.]cn
msguguudfh4[.]xyz
nfdsnvuusds7d64jg[.]cn
recsfgsfxvdgr[.]xyz
ruhvsvya[.]icu
safvyhgdrsdfhd[.]xyz
sasfyvuaseyzzs[.]cn
sasygzsu4zusaty[.]cn
scheduleyaraupd2[.]cn
sdfojbeufibibsuu8u[.]cn
sdgn446yhd[.]cn
sdjbizirebz[.]cn
sertte56gzxes[.]cn
sevndgkhkidgr[.]xyz
sidfbuz8egozs[.]cn
ssdghgrehndx[.]cn
tojh5roh4[.]top
torpoa[.]cn
tripdsbeacgsa43wes[.]xyz
u4snvsrtvlrui[.]xyz
u55fbwiubyuere[.]xyz
usjnvovoo4[.]net
zjdhduv[.]com
zytjbgev[.]icu
X.509 Certificate Common Names:
CN=55554rac
CN=MATRACHEDICIDGA
CN=WIN-7FUHAU7D2HV
CN=WIN-J9D866ESIJ2
CN=DESKTOP-TCRDU4C
Original link: https://www.team-cymru.com/post/tracing-the-path-from-smartapesg-to-netsupport-rat