The Feed 2025-02-10

AI Generated Podcast
https://open.spotify.com/episode/2D7U3Rj1XU7MztZxmqUFBq?si=lPxvgBNNQSqGH4KetJGM2Q
Summarized Sources
- Coyote Banking Trojan: A Stealthy Attack via LNK Files: The Coyote Banking Trojan uses LNK files to deliver multi-stage attacks, targeting over 70 Brazilian financial applications and websites to steal sensitive information.
Original link: https://www.fortinet.com/blog/threat-research/coyote-banking-trojan-a-stealthy-attack-via-lnk-files
- Operation Phantom Circuit: North Korea’s Global Data Exfiltration Campaign: The Lazarus Group, based in North Korea, infiltrated trusted development tools to compromise cryptocurrency and technology developers worldwide, using sophisticated methods to steal data.
Original link: https://securityscorecard.com/blog/operation-phantom-circuit-north-koreas-global-data-exfiltration-campaign/
- Persistent Threats from the Kimsuky Group Using RDP Wrapper - ASEC: The Kimsuky group employs spear-phishing attacks using LNK files to distribute malware such as PebbleDash and RDP Wrapper, enabling remote control of infected systems.
Original link: https://asec.ahnlab.com/en/86098/
-
**Technical Analysis of Xloader Versions 6 and 7 Part 1**: Xloader malware establishes persistence, injects code into multiple processes, and uses complex obfuscation techniques to evade detection.
Original link: https://www.zscaler.com/blogs/security-research/technical-analysis-xloader-versions-6-and-7-part-1
- Unmasking SparkRAT: Detection & macOS Campaign Insights: The SparkRAT malware, known for its cross-platform support and web-based interface, is used in cyber espionage campaigns, including those linked to North Korea, targeting macOS users.
Original link: https://hunt.io/blog/sparkrat-server-detection-macos-activity-and-malicious-connections
Coyote Banking Trojan: A Stealthy Attack via LNK Files
Summary
The Coyote Banking Trojan is delivered through multi-stage attacks initiated by LNK files, primarily targeting users in Brazil to harvest sensitive information from financial applications and websites. Once deployed, the Trojan performs keylogging, captures screenshots, and displays phishing overlays to steal credentials. The malware modifies the registry to establish persistence and gathers system information to send to a remote server. The Trojan expands its target list to include numerous sites and financial agents and monitors active windows.
Technical Details
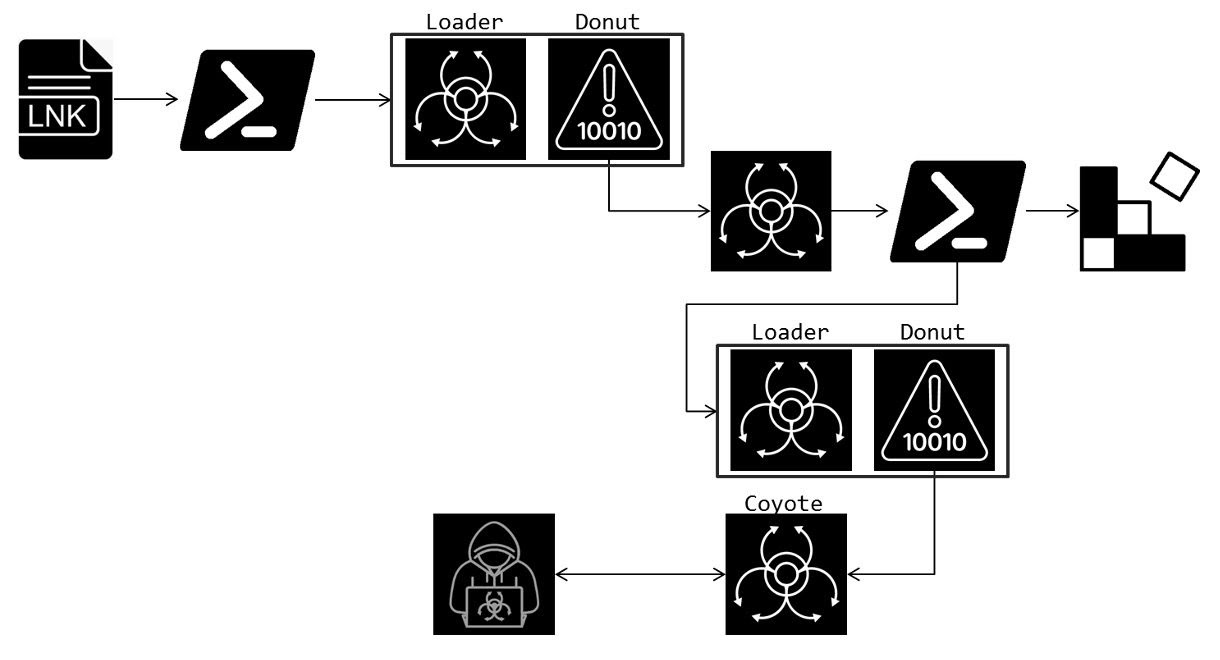 The attack begins with a malicious LNK file containing a PowerShell command that connects to a remote server. This command initiates the next stage by running a script from a URL such as hxxps://tbet[.]geontrigame[.]com/zxchzzmism. The downloaded content contains encoded data segments which are decoded and executed using PowerShell scripts.
The attack begins with a malicious LNK file containing a PowerShell command that connects to a remote server. This command initiates the next stage by running a script from a URL such as hxxps://tbet[.]geontrigame[.]com/zxchzzmism. The downloaded content contains encoded data segments which are decoded and executed using PowerShell scripts.
- The decoded data leads to the injection of a DLL file (“bmwiMcDec”) that acts as a loader, using VirtualAllocEx and WriteProcessMemory to inject a payload (“npuGDec”). It then uses CreateRemoteThread to execute the injected code.
- The injected code uses Donut to decrypt and execute MSIL payloads.
- Persistence is achieved by modifying the registry at “HCKU\Software\Microsoft\Windows\CurrentVersion\Run”. The malware removes any existing PowerShell commands and creates a new one with a randomly generated name, pointing to a Base64-encoded URL.
- The malware gathers system information (machine name, username, OS) and installed antivirus products, encodes it in Base64, reverses the string, and sends it to a remote server.
- The Trojan checks for specific usernames and virtual machine-related files/folders to identify test/sandbox environments.
- Coyote monitors active windows, and if a target site is accessed, it communicates with a C2 server via port 443 using domains like geraatualiza[.]com, masterdow[.]com, and geraupdate[.]com. It can receive commands to perform actions such as taking screenshots, keylogging, or displaying fake images.
Countries
- Brazil
Industries
- Financial
Recommendations
- Utilize FortiGuard Antivirus, FortiGate, FortiMail, FortiClient, and FortiEDR with up-to-date protections.
- Block the identified C2 server using FortiGuard Web Filtering Service.
- Complete Fortinet’s free cybersecurity training module: Fortinet Certified Fundamentals (FCF) in Cybersecurity to help identify and protect against phishing attacks.
- Contact the Global FortiGuard Incident Response Team if an impact is suspected.
Hunting methods
- Analyze LNK files for unusual PowerShell commands.
- Monitor registry modifications at “HCKU\Software\Microsoft\Windows\CurrentVersion\Run” for new or altered PowerShell commands.
- Inspect network traffic for connections to the listed URLs and hosts.
- Examine processes for the use of Donut to decrypt and execute MSIL payloads.
IOC
URLs:
hxxps://btee[.]geontrigame[.]com/mvkrouhawm
hxxps://qmnw[.]daowsistem[.]com/fayikyeund
hxxps://bhju[.]daowsistem[.]com/iwywybzqxk
hxxps://lgfd[.]daowsistem[.]com/riqojhyvnr
hxxps://leme[.]daowsistem[.]com/omzowcicwp
hxxps://igow[.]scortma[.]com/fqieghffbm
hxxps://quit[.]scortma[.]com/xzcpnnfhxi
hxxps://llue[.]geontrigame[.]com/byyyfydxyf
hxxps://cxmp[.]scortma[.]com/qfutdbtqqu
hxxps://xrxw[.]scortma[.]com/gmdroacyvi
hxxps://qfab[.]geontrigame[.]com/vfofnzihsm
hxxps://tbet[.]geontrigame[.]com/zxchzzmism
hxxps://yezh[.]geontrigame[.]com/vxewhcacbfqnsw
Hosts:
geraatualiza[.]com
masterdow[.]com
geraupdate[.]com
Files:
362af8118f437f9139556c59437544ae1489376dc4118027c24c8d5ce4d84e48
330dffe834ebbe4042747bbe00b4575629ba8f2507bccf746763cacf63d655bb
33cba89eeeaf139a798b7fa07ff6919dd0c4c6cf4106b659e4e56f15b5809287
552d53f473096c55a3937c8512a06863133a97c3478ad6b1535e1976d1e0d45f
64209e2348e6d503ee518459d0487d636639fa5e5298d28093a5ad41390ef6b0
67f371a683b2be4c8002f89492cd29d96dceabdbfd36641a27be761ee64605b1
73ad6be67691b65cee251d098f2541eef3cab2853ad509dac72d8eff5bd85bc0
7cbfbce482071c6df823f09d83c6868d0b1208e8ceb70147b64c52bb8b48bdb8
839de445f714a32f36670b590eba7fc68b1115b885ac8d689d7b344189521012
bea4f75370eba4088e8a51818d9de8e9ad0138495338402f05c5c7a800695a6
f3c37b1de5983b30b9ae70c525f97727a56d3874533db1a6e3dc1355bfbf37ec
fd0ef425d34b56d0bc08bd93e6ecb11541bd834b9d4d417187373b17055c862e
*Original link:** https://www.fortinet.com/blog/threat-research/coyote-banking-trojan-a-stealthy-attack-via-lnk-files
Operation Phantom Circuit: North Korea’s Global Data Exfiltration Campaign
Summary
The Lazarus Group, based in North Korea, conducted a sophisticated campaign called “Phantom Circuit,” compromising over 1,500 systems worldwide. The attackers infiltrated trusted development tools by embedding malware directly into them. They targeted cryptocurrency and technology developers, exfiltrating sensitive development credentials, authentication tokens, browser-stored passwords, and system configuration details. The stolen data was transferred to Dropbox after collection by command-and-control (C2) servers. The infrastructure included command-and-control servers, spoofed domains, and persistent remote management sessions. The operation was active from November 2024 to January 2025, with major victim hotspots in Europe, India, and Brazil. The attackers used Russian proxy servers to obfuscate their origin.
Technical Details
The Lazarus Group employed a complex, multi-layered infrastructure to conduct “Operation Phantom Circuit”:
- Initial Access: The operation started from North Korean IP addresses.
- VPN Obfuscation: These IPs connected to Astrill VPN endpoints to conceal their origin.
- Proxy Relay: Traffic was routed through the Oculus Proxy network in Hasan, Russia, adding an extra layer of anonymity. These proxies are registered to Sky Freight Limited.
- Command and Control (C2) Servers: The proxied connections reached C2 infrastructure hosted on Stark Industries servers, which managed communications with compromised systems and exfiltrated data. The C2 servers used ports 1224 for communication with infected systems and 1245 for a hidden administrative platform.
- Data Exfiltration: Stolen data was uploaded to Dropbox. Some servers maintained active sessions for over five hours.
- Malware Embedding: The attackers embedded malware into trusted development tools, ensuring widespread compromise while maintaining stealth.
- Administrative Platform: The C2 servers included an administrative platform for managing compromised systems worldwide. This platform, built on Node.js with a React frontend, featured multiple API endpoints for granular operational control. It allowed operators to search, filter, and organize exfiltrated information.
- Persistence: Attackers maintained persistent RDP sessions, some lasting up to 10 days, to retain direct access to compromised systems.
The administrative platform had key features for system tracking, credential management, and activity logs:
- System Tracking: Monitored device details, including PC names, operating systems, and configurations.
- Credential Management: Collected URLs, browser-stored credentials, and authentication tokens.
- Activity Logs: Tracked timestamps for victim interactions.
The platform included hidden pages and access points, secured behind a login wall, to facilitate control over compromised systems. The Info page retrieved and displayed exfiltrated victim data, including PC names, URLs, passwords, credentials, and system configuration details. The backend extracted and filtered data from implants via the /keys API endpoint.
The Lazarus Group used a commercial proxy service (Oculus Proxy) to add a layer of legitimacy to their operations. Some of the Astrill VPNs used in this operation could be traced back to Pyongyang. STRIKE applied the CIA’s Analysis of Competing Hypotheses (ACH) methodology and concluded that the Lazarus Group was responsible for the campaign.
Countries
- Targeted: Primarily European technology sectors.
- Victim Hotspots: India, Brazil.
- Origin: North Korea.
- Proxy: Russia.
Industries
- Cryptocurrency
- Technology Development.
Recommendations
- Package Verification: Validate the integrity of software updates using cryptographic checksums or signatures.
- Network Monitoring: Analyze connections to uncommon ports, such as 1224 and 1245.
- Proxy Detection: Identify and block suspicious proxy usage, particularly from commercial services linked to malicious campaigns.
- Development Tool Audits: Regularly review and update development tools to identify and mitigate vulnerabilities.
- Remote Access Scrutiny: Monitor for persistent Remote Desktop Protocol (RDP) sessions that could indicate unauthorized access.
- Incident Response: Contact the STRIKE Incident Response team.
- Supply Chain Security: Use SecurityScorecard’s Supply Chain Detection and Response (SCDR) solution to monitor and assess the software supply chain.
Hunting methods
- Analyze network connections for traffic through Astrill VPNs and Oculus Proxy IPs to C2 servers.
- Monitor for connections to ports 1224 and 1245.
- Examine applications and systems for unexpected modifications or embedded malicious code.
- Review system logs for persistent RDP sessions.
IOC
Server IPs:
94.131.9.32
185.153.182.241
86.104.74.51
5.253.43.122
North Korean IPs:
175.45.178.130
175.45.176.27
175.45.178.14
175.45.178.9
175.45.178.11
175.45.178.10
Astrill VPN Endpoints:
70.39.70.196
204.188.233.68
45.58.143.196
70.39.70.197
199.115.99.62
Oculus Proxy IPs:
83.234.227.49
83.234.227.50
83.234.227.51
83.234.227.53
Spoofed domain: sageskills-uk[.]com
Original link: https://securityscorecard.com/blog/operation-phantom-circuit-north-koreas-global-data-exfiltration-campaign/
Persistent Threats from the Kimsuky Group Using RDP Wrapper - ASEC
Summary
The Kimsuky group is actively launching attacks using spear-phishing emails with malicious shortcut files disguised as Office documents. When executed, these files use PowerShell or Mshta to download and execute payloads like PebbleDash and RDP Wrapper. They use these tools, along with others such as Proxy, KeyLogger, and infostealers, to control infected systems and steal information. The group has been modifying its tactics, such as using RDP Wrapper and Proxy tools for remote control rather than relying solely on backdoors. To avoid detection, they also extract key values from web browsers instead of directly stealing credentials.
Technical Details
The Kimsuky group employs a range of techniques and tools in their attacks:
- Spear-Phishing: Uses shortcut files (*.LNK) disguised as Office documents delivered via spear-phishing emails to specific targets.
- Initial Payload Delivery: Executes PowerShell or Mshta to download additional payloads from external sources.
- RDP Wrapper: Installs a custom-made RDP Wrapper to enable remote desktop functionality on systems where it is not supported by default, creating export functions to bypass file detection.
- Proxy: Uses proxy malware to enable external access to systems located on private networks, creating mutexes for operation.
- Keylogging: Uses PowerShell scripts and executable keyloggers to record user keystrokes, storing the data in specific file paths.
- Credential Theft: Employs tools like “forceCopy” to steal user credentials from web browsers, using the NTFS Parser library to read files and bypass security products.
- Loaders and Injectors: Uses Loader and Injector malware, along with ReflectiveLoader PowerShell scripts, to load files into memory and inject code into target processes.
- Persistence: Uses tools like RDP Wrapper and Proxy to maintain remote control over infected systems.
Countries
- Targeted: South Korea
Industries
- Not mentioned in the source.
Recommendations
- Carefully check the sender of emails and avoid opening files from unknown sources.
- Apply the latest patches for programs, including the OS and web browsers.
- Update AhnLab V3 to the latest version to prevent malware infection.
Hunting methods
- Not mentioned in the source.
IOC
File Detections:
Backdoor/Win.PebbleDash.C5719351
Trojan/Win.Rdpwrap.C5704469
Trojan/Win.Rdpwrap.C5708551
Trojan/Win.Rdpwrap.C5710893
Trojan/Win.Rdpwrap.C5716647
Trojan/Win.Rdpwrap.C5719870
Trojan/Win.Rdpwrap.C5720371
Trojan/Win.KeyLogger.C5687683
Trojan/Win.KeyLogger.C5705213
Trojan/Win.KeyLogger.C5705571
Trojan/Win.Injecter.C5705214
Trojan/Win.UACMe.C5705215
Trojan/Win.Loader.C5716648
Infostealer/Win.Browser.R641029
Malware/Gen.Generic.C2950389
Trojan/Win.Agent.C5687684
Trojan/PowerShell.Loader
Trojan/PowerShell.Launcher
Trojan/PowerShell.KeyLogger
Original link: https://asec.ahnlab.com/en/86098/
Technical Analysis of Xloader Versions 6 and 7 | Part 1
Summary
This article provides a detailed analysis of Xloader versions 6 and 7, focusing on its behavior, obfuscation, and anti-analysis techniques. Xloader establishes persistence by copying itself into a subdirectory under %APPDATA% or %PROGRAMFILES% and adding an entry in the Windows registry. It uses process injection techniques to evade antivirus software, injecting code into processes like explorer.exe and executables in the SysWOW64 directory. The malware employs multiple layers of custom encryption and obfuscation to protect its code and data. These versions have added new encryption layers and dynamic key generation to complicate analysis and detection.
Technical Details
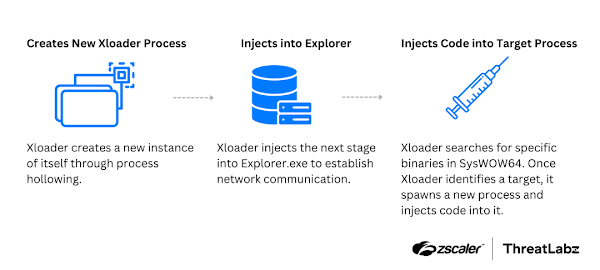
 Xloader uses a multi-stage process to inject malicious code and maintain persistence:
Xloader uses a multi-stage process to inject malicious code and maintain persistence:
- Persistence: Xloader copies itself to %APPDATA% or %PROGRAMFILES% under a randomly named directory and file. It then creates a registry entry under either
HKCUorHKLMin theRunorPolicieskey to ensure it runs on startup. The registry entry has a randomly generated name and points to the Xloader executable. - Process Injection:
- Process Hollowing: Xloader creates a new instance of itself via process hollowing.
- Explorer.exe Injection: It injects code into
explorer.exeto establish network communication, using the asynchronous procedure call (APC) queue technique with theNtQueueApcThreadAPI. - SysWOW64 Injection: Xloader launches and injects code into an executable file in the SysWOW64 directory using Windows API functions such as
CreateProcessInternal,NtCreateSection,NtMapViewOfSection, andNtResumeThread. - The specific executable filenames targeted in SysWOW64 vary across samples and versions.
- Code Obfuscation:
- Multiple Encryption Layers: Xloader uses custom encryption, including RC4 and adjacent byte subtraction, with additional layers in versions 6 and 7.
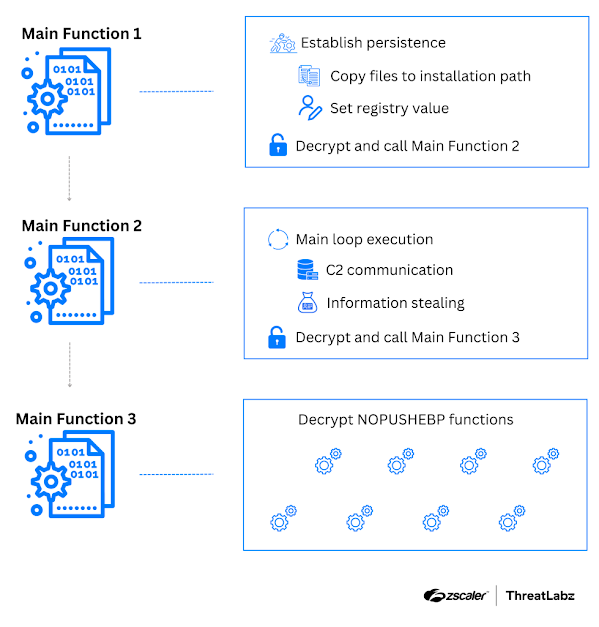
- Main Functions: Xloader executes three main functions, each responsible for decrypting subsequent encrypted functions.
- Main Function 1: Establishes persistence and decrypts/calls Main Function 2. It uses an egg-hunting technique to find the memory address range of encrypted code and XOR operations to evade static signature detection.
- Main Function 2: Executes the main loop for C2 communication and data theft, and decrypts/calls Main Function 3.
- Main Function 3: Decrypts a new encryption layer on top of NOPUSHEBP functions, using egg-hunting techniques to find encrypted blocks.
- NOPUSHEBP Functions: These functions have an additional encryption layer in versions 6 and 7. The decryption process involves dynamically calculated IDs and keys.
- PUSHEBP Functions: Similar to prior versions but with added complexities in version 7.5 that use XOR operations to derive the RC4 key.
- API Call Encryption: Xloader encrypts its code before calling critical APIs like
ZwSetThreadContextinvolved in process injection. After the API call, the original code is decrypted again.
- Data Obfuscation:
- Dynamic Value Construction: Instead of static encrypted data blocks, Xloader dynamically constructs strings, keys, seeds, and constants when needed.
- String Obfuscation: Dedicated functions build, decrypt, and return each string. Encrypted strings are pushed onto the stack, and a dynamically generated key is used to decrypt them with RC4 and subtraction.
- Stack Strings: Plaintext strings are built on the stack through NOPUSHEBP functions, which are themselves encrypted.
- API Obfuscation: CRC32 values for Windows API function names are created by specific code blocks instead of using static data blocks. These functions use XOR keys and RC4 with subtraction to decrypt the API function name’s CRC32 value.
- NTDLL Hook Evasion: Xloader loads a copy of ntdll and calls API functions from the copy to evade breakpoints or hooks on the original library.
Recommendations
The source does not explicitly list recommendations; however, based on the technical details, these actions can be considered:
- Monitor registry keys for unexpected entries in
HKCUorHKLMunder theRunorPolicieskeys. - Detect and block the injection of code into legitimate processes like
explorer.exeand executables within the SysWOW64 directory. - Implement detection mechanisms for RC4 and byte subtraction encryption algorithms.
- Monitor API calls such as
CreateProcessInternal,NtCreateSection,NtMapViewOfSection,NtResumeThread, andZwSetThreadContext. - Implement checks for processes loading their own copy of
ntdll.dll.
Hunting methods
The source does not explicitly list hunting methods; however, based on the technical details, these methods can be considered:
- Registry Monitoring: Monitor for new or modified registry entries in the
RunandPolicieskeys underHKCUandHKLMthat point to executables in the %APPDATA% or %PROGRAMFILES% directories. - Process Monitoring: Track process creation events, looking for instances of process hollowing where a new process is created, and the original process is immediately terminated.
- API Hooking: Implement API hooks or use existing EDR solutions to monitor calls to
NtQueueApcThread,CreateProcessInternal,NtCreateSection,NtMapViewOfSection, andNtResumeThread. - Memory Scanning: Scan process memory for decrypted code blocks, focusing on areas where code has been recently decrypted before API calls.
- NTDLL Analysis: Check for processes that load a separate copy of
ntdll.dll. Compare the loaded copy’s hash with the known good hash of the system’sntdll.dll. - CRC32 Monitoring: Monitor API calls and check if the CRC32 values are calculated dynamically instead of loaded from a static table.
IOC
The source does not list explicit IOCs such as IPs, domains, or specific file hashes. However, indicators can be derived from the malware’s behavior:
File Paths:
%APPDATA%\\<3-8 alphanumeric characters starting with an uppercase letter>\\<6-16 lowercase alphanumeric characters>.exe
%PROGRAMFILES%\\<3-8 alphanumeric characters starting with an uppercase letter>\\<6-16 lowercase alphanumeric characters>.exe
Registry Keys:
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\\<5-12 uppercase alphanumeric characters>
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\\<5-12 uppercase alphanumeric characters>
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run\\<5-12 uppercase alphanumeric characters>
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run\\<5-12 uppercase alphanumeric characters>
SysWOW64 Executables (examples):
SearchFilterHost.exe
Isv.exe
UserAccountControlSettings.exe
systeminfo.exe
SyncHost.exe
print.exe
sdiagnhost.exe
fixmapi.exe
msiexec.exe
takeown.exe
systray.exe
net1.exe
nslookup.exe
srdelayed.exe
makecab.exe
setx.exe
runonce.exe
auditpol.exe
notepad.exe
setupugc.exe
AtBroker.exe
RMActivate_isv.exe
mountvol.exe
dfrgui.exe
Original link: https://www.zscaler.com/blogs/security-research/technical-analysis-xloader-versions-6-and-7-part-1
Okay, here is the threat intelligence summary of the article you provided, formatted as requested:
Unmasking SparkRAT: Detection & macOS Campaign Insights
Summary
The article discusses the SparkRAT remote access trojan, detailing detection methods and a recent campaign targeting macOS users, suspected to be linked to DPRK. SparkRAT, known for its modular design and cross-platform support, uses WebSocket and HTTP for command-and-control (C2) communication. The campaign involves the use of fake meeting pages and domains to deliver SparkRAT implants. The article provides insights into identifying active SparkRAT C2 servers and analyzing the malware’s behavior on macOS systems. It emphasizes the ongoing nature of the threat and the importance of proactive monitoring and disruption.
Technical Details
- SparkRAT Overview:
- Written in Golang and uses the WebSocket protocol for initial communication with the C2 server.
- After WebSocket, it switches to HTTP, specifically a POST request to check for updates from the repository.
- The default port for the server is 8000, but this can be reconfigured.
- Employs HTTP Basic Authentication to restrict access to its C2 server panel.
- Detection Techniques:
- Checking for specific HTTP response headers on port 8000, such as “HTTP/1.1 401 Unauthorized” and “Www-Authenticate: Basic realm=Authorization Required”.
- Identifying the absence of standard header fields like Server, Content-Type, and Connection.
- Sending a POST request to the /api/client/update endpoint and analyzing the response.
-
Looking for a specific JSON response: **’{“code”:-1,”msg”:”${i18n COMMON.INVALID_PARAMETER}”}’**.
- DPRK Campaign:
- Delivers SparkRAT via fake meeting pages and domains.
- Uses infrastructure with characteristics associated with DPRK, such as UCLOUD ASN, Apache HTTPD server stack, .site and .space TLDs, and Let’s Encrypt TLS certificates.
- Utilizes open directories on servers to host SparkRAT implants and bash scripts.
- Bash scripts (dev.sh and test.sh) download client.bin (SparkRAT client) from a specified URL, set execute permissions, and run it as a background process.
- File Analysis (client.bin):
- A 64-bit Mach-O binary containing strings from the SparkRAT repository.
- Creates and drops the file com.second.startup.plist in /Users/run to establish persistence by running every 10 minutes.
- Attempts TCP connections to 51.79.218[.]159:8000, an OVH SAS server in Singapore.
- The server at 51.79.218[.]159 hosts a webpage mimicking an online gaming platform, One68, aimed at Vietnamese speakers, and features a download button for an Android APK file.
- The APK makes a GET request to http://one68[.]top/client, upgrading to a WebSocket connection.
- Observed Infrastructure:
- 152.32.138[.]108: Hosts an exposed directory at /dev containing bash scripts and SparkRAT client.
- 15.235.130[.]160: Operates as an active SparkRAT C2 server on port 8000.
- 118.194.249[.]38: Shows domain patterns that align with previously observed patterns.
Countries
- South Korea
- Singapore
- Vietnam
Industries
- Government organizations
- Online gaming
Recommendations
- Monitor network traffic for HTTP Basic Authentication requests on port 8000 without standard header fields.
- Inspect HTTP POST requests to the /api/client/update endpoint and validate the server’s JSON response.
- Monitor for unusual processes creating /Users/run/com.second.startup.plist to maintain persistence.
- Monitor network connections to the IPs associated with SparkRAT C2 servers.
- Implement detection mechanisms for bash scripts downloading and executing binaries from untrusted sources.
- Monitor for connections to gaming platforms, especially those resolving to unusual IPs.
Hunting methods
- Actively scan for RAT servers to identify infrastructure.
- Investigate for open directories containing SparkRAT implants and scripts.
- Monitor domain registration patterns such as the use of .site and .space TLDs registered under Namecheap.
IOC
IP Addresses:
152.32.138[.]108
15.235.130[.]160
118.194.249[.]38
51.79.218[.]159
Domains:
gsoonmann[.]site
gmnormails[.]site
gmoonsom[.]site
nasanecesoi[.]site
gmoocsoom[.]site
gmcomamz[.]site
namerowem[.]site
gmoosomnoem[.]site
mncomgom[.]site
ggnmcomas[.]site
remote.henh247[.]net
updatetiker[.]net
gomncomow[.]site
gooczmmnc[.]site
gnmoommle[.]space
one68[.]top
File Hashes (SHA-256):
cd313c9b706c2ba9f50d338305c456ad3392572efe387a83093b09d2cb6f1b56
52277d43d2f5e8fa8c856e1c098a1ff260a956f0598e16c8fb1b38e3a9374d15
ffe4cfde23a1ef557f7dc56f53b3713d8faa9e47ae6562b61ffa1887e5d2d56e
Original link: https://hunt.io/blog/sparkrat-server-detection-macos-activity-and-malicious-connections