The Feed 2025-02-17

AI Generated Podcast
https://open.spotify.com/episode/6KHiCCqPp9zbu7ruoUYeiy?si=d1eRpYs1T86dcvyFc6NOag
Summarized Sources
- Defying tunneling: A Wicked approach to detecting malicious network traffic: This article discusses how attackers use tunneling and dynamic DNS to hide malicious network traffic and how to detect such activity.
Original link: https://redcanary.com/blog/threat-detection/network-traffic-tunneling/
- Google Cloud Platform Data Destruction via Cloud Build: This article examines how a threat actor with minimal permissions can exploit Google Cloud Build to perform malicious actions like data destruction.
Original link: https://blog.talosintelligence.com/gcp-data-destruction-via-cloud-build/
- How to detect malicious browser extensions using Elastic: This article explains how to use osquery and the Elastic Stack to detect and manage malicious browser extensions, which are a significant threat to organizations.
Original link: https://www.elastic.co/blog/how-to-detect-malicious-browser-extensions-using-elastic
- Storm-2372 conducts device code phishing campaign: This article details a device code phishing campaign by the threat actor Storm-2372, who is likely aligned with Russian interests, that targets various organizations to steal authentication tokens.
Original link: https://www.microsoft.com/en-us/security/blog/2025/02/13/storm-2372-conducts-device-code-phishing-campaign/
- The BadPilot campaign: Seashell Blizzard subgroup conducts multiyear global access operation: This article reports on a subgroup within the Russian state actor Seashell Blizzard, which has been conducting global compromises of Internet-facing infrastructure since 2021 to persist on high-value targets.
Original link: https://www.microsoft.com/en-us/security/blog/2025/02/12/the-badpilot-campaign-seashell-blizzard-subgroup-conducts-multiyear-global-access-operation/
Defying tunneling: A Wicked approach to detecting malicious network traffic
Summary
This article discusses how adversaries use traffic tunneling and dynamic DNS hostnames to conceal malicious network traffic, making it difficult to identify and eradicate. The research focuses on the prevalence of tunneling and dynamic DNS techniques across four malware variants, highlighting the challenges in distinguishing between legitimate and malicious uses of these technologies. The article provides insights into how these techniques are used in attacks and offers recommendations for improving security posture by detecting and managing such activities. The study involved analyzing over 150,000 malware samples from VirusTotal using tools like Synapse to identify trends in tunneling and dynamic DNS usage.
Technical Details
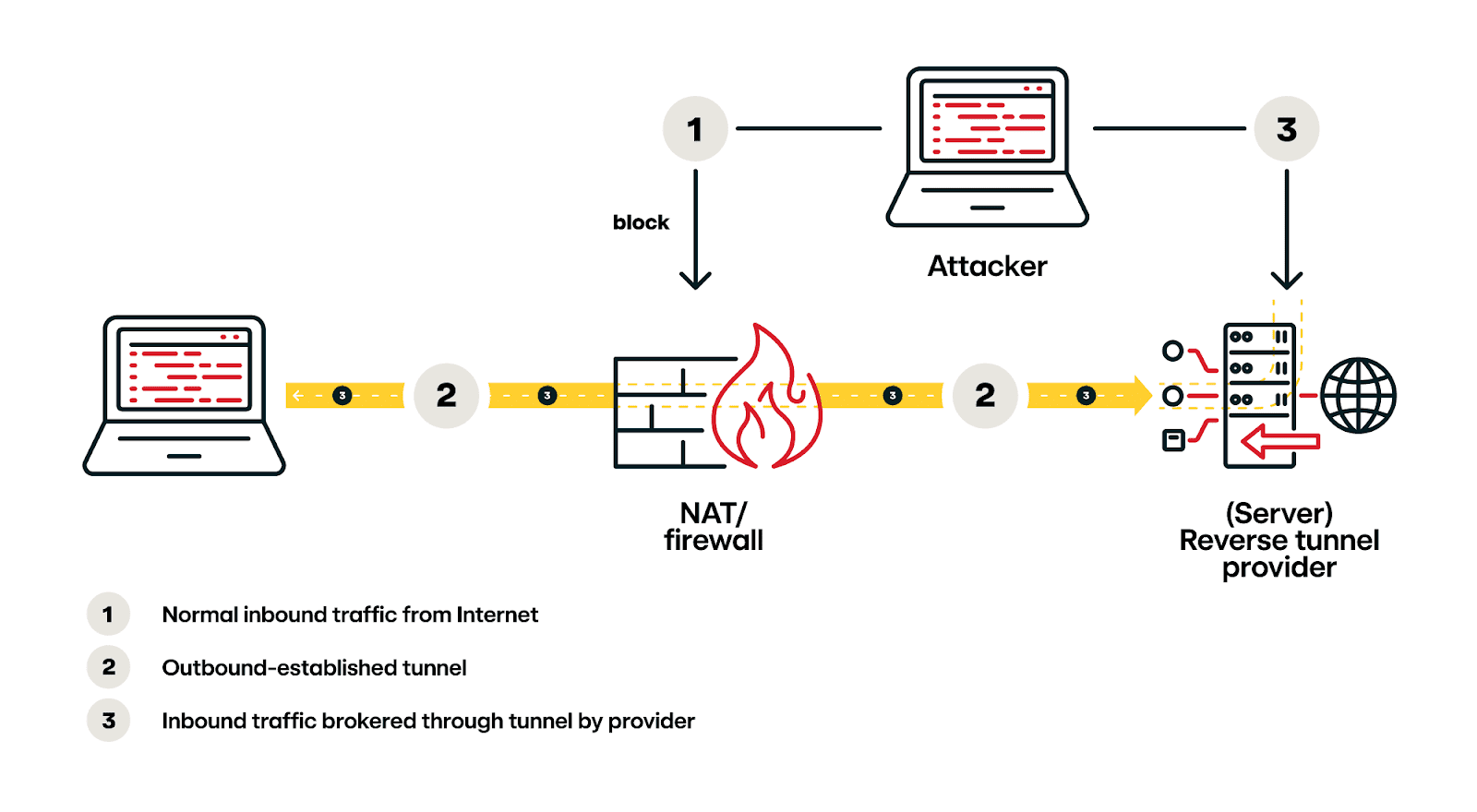 The article explains that adversaries use reverse tunneling to bypass Network Address Translation (NAT) and firewalls, establishing outbound connections from compromised endpoints to internet-based tunnel providers. This allows them to create an “inbound” path to the client system. Dynamic DNS is often used alongside tunnels to maintain a consistent hostname for systems with changing IP addresses.
The article explains that adversaries use reverse tunneling to bypass Network Address Translation (NAT) and firewalls, establishing outbound connections from compromised endpoints to internet-based tunnel providers. This allows them to create an “inbound” path to the client system. Dynamic DNS is often used alongside tunnels to maintain a consistent hostname for systems with changing IP addresses.
The research methodology involved analyzing malware configuration data from VirusTotal using the Synapse analytic tool. This allowed the researchers to pivot into a wider set of indicators, including tunneling and dynamic DNS techniques. The analysis covered four malware variants during December 2024.
The article highlights the use of Remote Access Trojans (RATs) like XWorm, AsyncRAT, DCRat and njRAT. These RATs are often installed on client systems, and adversaries use tunneling to connect back to the malware for command and control (C2).
- XWorm: Adversaries running XWorm prefer ply[.]gg domains, which are used by the Playit service that caters to gamers. The Playit service forwards traffic through a tunnel, making it appear that malicious traffic originates from Playit’s infrastructure.
- AsyncRAT: This RAT is more dispersed in its domain usage but shows a strong tendency to use duckdns[.]org domains. DuckDNS provides dynamic DNS functionality using Amazon AWS resources but does not provide any tunneling features.
- DCRat: Adversaries using DCRat prefer portmap[.]host dynamic DNS hosting for C2. The varied network behaviors between DCRat and AsyncRAT are useful to differentiate what may be very similar binaries due to their shared parentage.
- njRAT: This RAT provides spyware-like and surveillance functions and can spread through removable USB drives. njRAT samples show a strong preference for ply[.]gg domains and ddns[.]net domains.
The article notes that tunneling and dynamic DNS services are often used heavily by malicious actors of all kinds since these services operate on any kind of network traffic.
Industries
- Gaming (specifically mentioned in relation to Playit service).
- The article does not explicitly list targeted industries, but the general applicability of RATs suggests a wide range of potential targets.
Recommendations
- Consider blocking traffic to and from frequently used tunneling and dynamic DNS providers, but be aware that this may impact legitimate business functions.
- Implement DNS sinkhole-type controls on dynamic DNS domains that your organization does not use.
- Allowlist only the dynamic DNS providers that your organization uses and implement alerting or blocking measures on any others.
- Understand the scope of the threat and how it may affect your organization, and develop a plan that mitigates the risk without significant negative impact to your business needs.
Hunting methods
- Monitor DNS behavior using DNS and/or web proxy visibility or an endpoint-based capability.
IOC
Since the list of domains is extensive, I’m including the malware alongside the associated domain as extracted from the count per domain figures provided within the source article.
Domains (Dynamic DNS and Tunneling Providers): A good starting point is to consider implementing DNS sinkhole-type controls on dynamic DNS domains that your organization does not use. There are numerous dynamic DNS providers, and a good resource to get started is this list from MISP
Original link: https://redcanary.com/blog/threat-detection/network-traffic-tunneling/
Google Cloud Platform Data Destruction via Cloud Build
Summary
This article examines how a threat actor with minimal permissions (specifically, the cloudbuild.builds.create permission) can exploit Google Cloud Build to perform malicious actions, such as data destruction. It details how an attacker can leverage Cloud Build’s default service account (SA) and its associated permissions to execute commands and potentially destroy data within a Google Cloud Platform (GCP) environment. The research highlights that while Google provides robust security recommendations and defaults, these can be misused. The article provides recommendations for cloud administrators and security analysts to monitor for, detect, and mitigate such threats. The research uses a GitHub-to-Cloud Build execution path to demonstrate data destruction.
Technical Details
The attack vector involves exploiting the Cloud Build service, a CI/CD service in GCP, by gaining the ability to submit and run Cloud Build jobs. This can be achieved either through compromised GCP user/SA credentials (Mitre ATT&CK T1078.004) or by pushing/merging code into a repository with a configured Cloud Build pipeline (Mitre T1195.002).
Key points:
- A threat actor with cloudbuild.builds.create permission can execute any gcloud CLI command that the Cloud Build SA has permissions to perform.
- The Talos research focuses on malicious actions enabled by the storage. permission family.
- The attack uses a GitHub repository connected to Cloud Build via a trigger that starts a build when code is pushed, a pull request (PR) is created, or code is committed to an existing PR.
- The research demonstrates data destruction by deleting a Cloud Storage bucket using the gcloud storage rm –recursive gs://BUCKET_NAME command.
- To bypass “Soft Delete” protections, the attacker can immediately create a new bucket with the same name after deletion, preventing restoration. This is done by updating the Cloud Build configuration file.
- Data encryption for impact is also discussed, where an attacker encrypts objects with a customer-provided key they control if Object Versioning is not enabled. This uses the gcloud storage cp SOURCE_DATA gs://BUCKET_NAME/OBJECT_NAME –encryption-key=YOUR_ENCRYPTION_KEY command.
Attack Chain:
- Initial Access: A threat actor gains the ability to submit and run Cloud Build jobs either by compromising a GCP user or SA or by pushing malicious code into a repository with a Cloud Build pipeline.
- Execution: The attacker leverages the Cloud Build SA to execute gcloud commands.
- Data Destruction: The attacker deletes a Cloud Storage bucket using the gcloud storage rm command.
- Bypassing Soft Delete: The attacker creates a new bucket with the same name to prevent restoration.
- Data Encryption (Alternative): If object versioning is disabled, the attacker encrypts objects using a customer-provided encryption key.
Recommendations
- Apply the principle of least privilege by assigning Cloud Build a lower privileged Service Account with just the permissions needed.
- Review the configuration applied to any repositories that can trigger Cloud Build jobs.
- Require manual approval for builds triggered by Pull Requests (PRs).
- Avoid allowing anyone to directly commit code to GitHub repositories without a PR.
- Create an anomaly model-style threat detection for the default Cloud Build SA performing actions that are not standard.
- Enable “Soft Delete” to allow restoration of accidentally or maliciously deleted GCS buckets and objects.
- Consider the use of the comment “/gcbrun” on GitHub pull requests to trigger Cloud Build runs but restrict it to repository owners or collaborators.
- Enable Object Versioning to prevent irreversible encryption of objects.
- Monitor the Operations Logs events.
Hunting methods
- Monitor Google Operations Logs for the following events:
- google.devtools.cloudbuild.v1.CloudBuild.RunBuildTrigger: Logs the creation of a new build via a connection trigger. Useful for DFIR investigations.
- google.devtools.cloudbuild.v1.CloudBuild.CreateBuild: Logs the manual creation of a new build and the identity principal. Useful for DFIR investigations, especially if there are many failed events followed by a success.
- storage.buckets.delete: Logs the deletion of a GCS bucket. Worth threat hunting if the protoPayload.authenticationInfo.principalEmail is the default Cloud Build Service Account and a good candidate for an anomaly model detection.
- storage.buckets.create: While relatively uninteresting in isolation, if this event shortly follows a storage.buckets.delete event it may be indicative of an attempt to bypass the protections offered by Safe Delete.
IOC
The article focuses on techniques and does not provide traditional IOCs like IPs or domains. However, the following can be considered indicators of potential misuse:
- GCP Project IDs: Monitor for Cloud Build jobs that interact with GCS buckets in unknown or external GCP projects.
- Unusual gcloud commands: Monitor for the use of gcloud storage rm –recursive and gcloud storage buckets create commands, especially when executed by the Cloud Build SA.
- Service Account: Default Cloud Build Service Account.
- Event Pattern: storage.buckets.delete followed shortly by storage.buckets.create.
Original link: https://blog.talosintelligence.com/gcp-data-destruction-via-cloud-build/
How to detect malicious browser extensions using Elastic
Summary
This article explains how to detect malicious browser extensions using osquery and the Elastic Stack. It highlights the increasing threat of malicious browser extensions that can steal information or compromise users. The document emphasizes the challenges of managing browser extensions in an enterprise environment, especially with multiple user profiles and personal extensions on corporate workstations. It introduces osquery, an open-source agent, to query OS information, including installed browser extensions, and how to deploy and manage it via Elastic Security. The article provides methods to create a real-time inventory of browser extensions and detection rules to notify teams about compromised extensions. It also details how to build detections for known bad extensions using threat intelligence reports and indicator match rules.
Technical Details
The article focuses on using osquery and Elastic to detect malicious browser extensions.
Key points:
- Browser Extension Threats: Threat actors are targeting browser extensions to steal information, such as usernames, passwords, and bank account information, or to compromise users by changing website content.
- Challenges in Managing Extensions: Extensions are installed per profile within the browser, making it difficult to manage across an enterprise, especially with personal and work profiles.
- osquery for Inventory: osquery is used to capture a snapshot of the current state of workstations, providing information about installed Chrome extensions. It treats the OS like a relational database with tables that can be queried.
- Elastic Integration: Elastic Security allows easy deployment and management of osquery to endpoints, with query results ingested into an Elasticsearch index for various use cases.
- Querying with osquery:
- Live Queries: Used for building and refining queries during testing or investigations.
- Query Packs: Collections of preconfigured queries scheduled to run at different intervals. The
browser_monitoringpack inventories browser extensions.
- Query Examples:
- Collecting browser extension information requires joining the
userstable to the extension table using theuidfield. - Example query:
SELECT * FROM users JOIN chrome_extensions USING (uid).
- Collecting browser extension information requires joining the
- Data Storage: Query results are stored in the
logs-osquery_manager.result*index pattern, with fields from the osquery schema table indexed with theosquery.*field name. - Key Fields:
osquery.identifier: Unique identifier of the extension.osquery.name: Name of the extension.osquery.profile: Chrome profile the extension is installed in.osquery.permissions: Permissions granted to the extension.osquery.version: Installed version of the extension.osquery.update_url: URL used to check for updates. Non-standard URLs indicate sideloaded extensions.
- Content Scripts: The
chrome_extension_content_scriptstable provides information about JavaScript files used by extensions. - Detection Strategies:
- Known Bad Extensions: Use threat intelligence reports to identify malicious extensions by their identifiers and versions.
- Elasticsearch Query: Build a large query with OR operators to look for specific extension identifiers and versions.
- Indicator Match Rule: Use threat intel feeds to create dynamic rules that alert when an installed extension matches a known bad extension.
Recommendations
- Use osquery and Elastic Stack to create a real-time inventory of browser extensions.
- Regularly run the
browser_monitoringpack to inventory all browser extensions every six hours. - Monitor
osquery.update_urlfor non-standard update paths to identify sideloaded extensions. - Build detections for known bad extensions using threat intelligence reports.
- Use indicator match rules to dynamically alert on known bad extensions based on threat intel feeds.
- Pay close attention to extensions with broad permissions, such as access to every HTTPS website (
https://*/*). - Secure Annex or crxaminer.tech reputation scores of extensions can be checked by their identifiers.
Hunting methods
- Query the
logs-osquery_manager.result*index in Elastic Stack to view browser extension data. - Use the
action_idfield to find results from scheduled pack queries (e.g.,action_id: "pack_browser-monitoring_chrome_extensions"to view results of thechrome_extensionsquery). - Investigate sideloaded extensions by monitoring the update URL (
osquery.update_url). - Examine the
chrome_extension_content_scriptstable for malicious JavaScript files and use Elastic Defend’s response action capabilities to download those files for offline analysis.
IOC
- Extension Identifiers and Versions: The article references a Cyberhaven extension compromise campaign with a list of malicious extensions with the following identifiers and versions:
- VPNCity
ID:nnpnnpemnckcfdebeekibpiijlicmpom
Version:2.0.1 - Parrot Talks
ID:kkodiihpgodmdankclfibbiphjkfdenh
Version:1.16.2 - Uvoice
ID:oaikpkmjciadfpddlpjjdapglcihgdle
Version:1.0.12 - Internxt VPN
ID:dpggmcodlahmljkhlmpgpdcffdaoccni
Version:1.1.1 - Bookmark Favicon Changer
ID:acmfnomgphggonodopogfbmkneepfgnh
Version:4.00 - Castorus
ID:mnhffkhmpnefgklngfmlndmkimimbphc
Version:4.40 - Wayin AI
ID:cedgndijpacnfbdggppddacngjfdkaca
Version:0.0.11 - Search Copilot AI Assistant for Chrome
ID:bbdnohkpnbkdkmnkddobeafboooinpla
Version:1.0.1 - VidHelper - Video Downloader
ID:egmennebgadmncfjafcemlecimkepcle
Version:2.2.7 - AI Assistant - ChatGPT and Gemini for Chrome
ID:bibjgkidgpfbblifamdlkdlhgihmfohh
Version:0.1.3 - TinaMind - The GPT-4o-powered AI Assistant!
ID:befflofjcniongenjmbkgkoljhgliihe
Version:2.13.0 - Bard AI chat
ID:pkgciiiancapdlpcbppfkmeaieppikkk
Version:1.3.7 - Reader Mode
ID:llimhhconnjiflfimocjggfjdlmlhblm
Version:1.5.7 - Primus (prev. PADO)
ID:oeiomhmbaapihbilkfkhmlajkeegnjhe
Version:3.18.0 - Tackker - online keylogger tool
ID:ekpkdmohpdnebfedjjfklhpefgpgaaji
Version:1.3 - AI Shop Buddy
ID:epikoohpebngmakjinphfiagogjcnddm
Version:2.7.3 - Sort by Oldest
ID:miglaibdlgminlepgeifekifakochlka
Version:1.4.5 - Rewards Search Automator
ID:eanofdhdfbcalhflpbdipkjjkoimeeod
Version:1.4.9 - Earny - Up to 20% Cash Back
ID:ogbhbgkiojdollpjbhbamafmedkeockb
Version:1.8.1 - ChatGPT Assistant - Smart Search
ID:bgejafhieobnfpjlpcjjggoboebonfcg
Version:1.1.1 - Keyboard History Recorder
ID:igbodamhgjohafcenbcljfegbipdfjpk
Version:2.3 - Email Hunter
ID:mbindhfolmpijhodmgkloeeppmkhpmhc
Version:1.44 - Visual Effects for Google Meet
ID:hodiladlefdpcbemnbbcpclbmknkiaem
Version:3.1.3 - Cyberhaven security extension V3
ID:pajkjnmeojmbapicmbpliphjmcekeaac
Version:24.10.4 - GraphQL Network Inspector
ID:ndlbedplllcgconngcnfmkadhokfaaln
Version:2.22.6 - GPT 4 Summary with OpenAI
ID:epdjhgbipjpbbhoccdeipghoihibnfja
Version:1.4 - Vidnoz Flex - Video recorder & Video share
ID:cplhlgabfijoiabgkigdafklbhhdkahj
Version:1.0.161 - YesCaptcha assistant
ID:jiofmdifioeejeilfkpegipdjiopiekl
Version:1.1.61 - Proxy SwitchyOmega (V3)
ID:hihblcmlaaademjlakdpicchbjnnnkbo
Version:3.0.2 - ChatGPT App
ID:lbneaaedflankmgmfbmaplggbmjjmbae
Version:1.3.8 - Web Mirror
ID:eaijffijbobmnonfhilihbejadplhddo
Version:2.4 - Hi AI
ID:hmiaoahjllhfgebflooeeefeiafpkfde
Version:1.0.0
- VPNCity
Original link: https://www.elastic.co/blog/how-to-detect-malicious-browser-extensions-using-elastic
Okay, I will summarize the article “Storm-2372 conducts device code phishing campaign” and provide operational cyber intelligence for SOC, TI, IR, and Threat Hunting, following the format you specified.
Storm-2372 conducts device code phishing campaign
Summary
This article details a device code phishing campaign conducted by the threat actor Storm-2372, which Microsoft assesses with medium confidence aligns with Russian interests. Active since August 2024, the campaign targets various sectors across multiple regions, including government, NGOs, IT, defense, telecommunications, health, higher education, and energy/oil and gas. The attackers use lures resembling messaging app experiences like WhatsApp, Signal, and Microsoft Teams to trick users into entering a device code on a legitimate sign-in page, granting the actors access to the user’s account. Once the user authenticates, the actor captures authentication tokens to access data and services. As of February 2025, Storm-2372 has shifted to using the specific client ID for Microsoft Authentication Broker to gain refresh tokens and register actor-controlled devices within Entra ID.
Technical Details
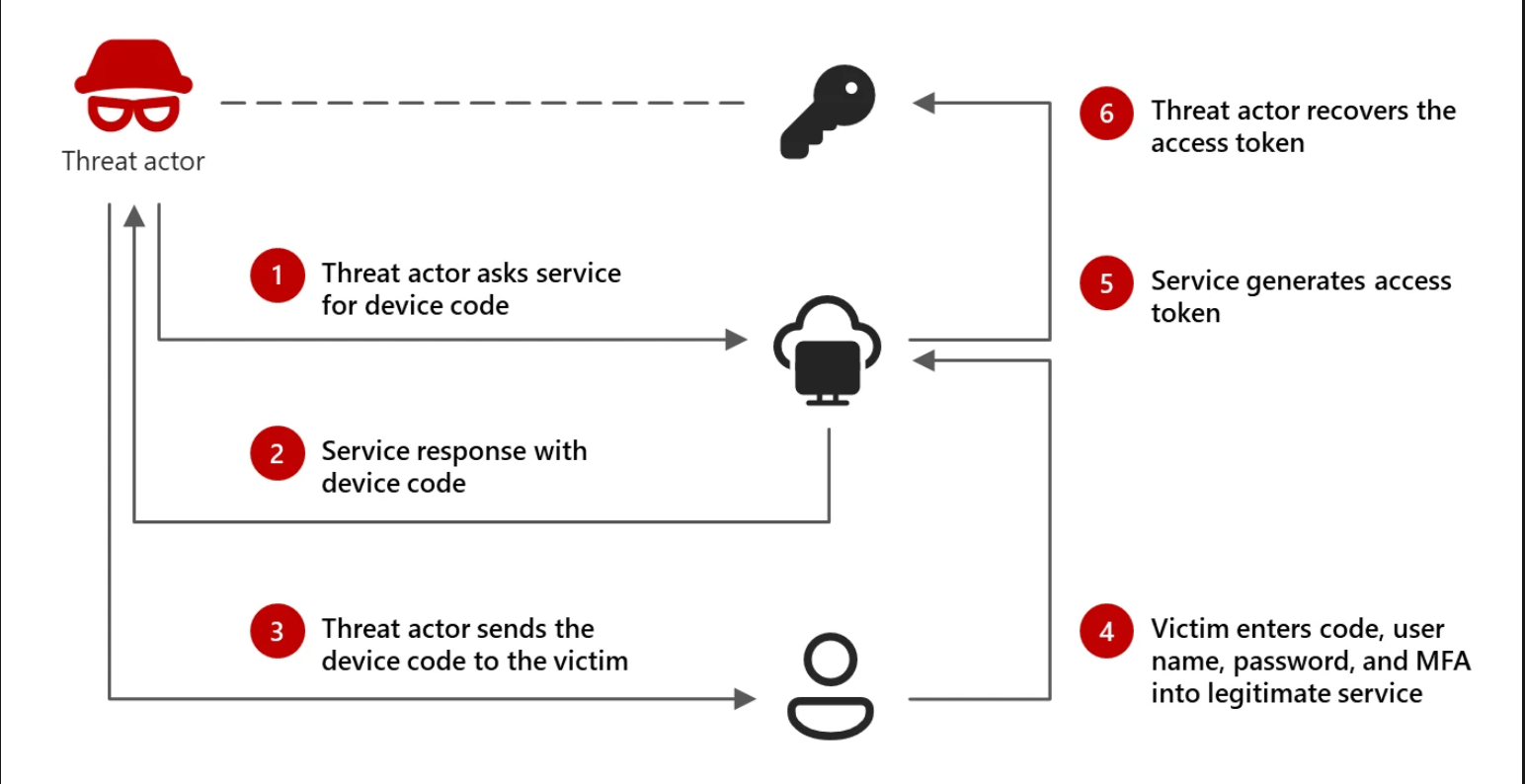 The Storm-2372 campaign employs device code phishing to compromise target accounts. The attack cycle involves several key steps:
The Storm-2372 campaign employs device code phishing to compromise target accounts. The attack cycle involves several key steps:
- Initial Contact: The actor establishes rapport with potential victims via third-party messaging services, impersonating prominent individuals.
- Phishing Email: Victims receive invitations to online events or meetings via phishing emails.
- Device Code Authentication: Victims are prompted to authenticate using a threat actor-generated device code on a legitimate Microsoft sign-in page.
- Token Capture: Upon entering the code, the actor receives valid access tokens, granting them access to the user’s accounts and data.
- Lateral Movement: The actor uses the compromised account to send further phishing messages within the organization.
- Data Exfiltration: Microsoft Graph is used to search for sensitive information such as usernames, passwords, and credentials within the compromised account’s messages.
Key TTPs:
- Device Code Phishing: Exploitation of the device code authentication flow to capture authentication tokens.
- Lure Design: Use of lures that resemble messaging app experiences, such as WhatsApp, Signal, and Microsoft Teams.
- Impersonation: Posing as prominent individuals to build trust with targets.
- Credential Harvesting: Capturing access and refresh tokens to access target accounts without needing a password.
- Lateral Movement: Sending additional phishing messages through intra-organizational emails from the compromised account.
- Data Exfiltration: Using Microsoft Graph to search and exfiltrate sensitive information from compromised accounts.
- Proxy Usage: Employing regionally appropriate proxies to conceal suspicious sign-in activity.
- Client ID Shift: Utilizing the Microsoft Authentication Broker client ID to register actor-controlled devices within Entra ID and obtain Primary Refresh Tokens (PRT).
Tools and Techniques:
- Microsoft Graph API: Used for data collection activities, such as email harvesting and searching for sensitive information.
- Microsoft Authentication Broker: Exploited by shifting to the specific client ID to receive refresh tokens and register actor-controlled devices.
- Device Registration Service: Used in conjunction with refresh tokens to register actor-controlled devices within Entra ID.
Countries
- Europe
- North America
- Africa
- Middle East
Industries
- Government
- Non-governmental organizations (NGOs)
- Information technology (IT) services and technology
- Defense
- Telecommunications
- Health
- Higher education
- Energy/oil and gas
Recommendations
- Block device code flow wherever possible. Configure Microsoft Entra ID’s device code flow in Conditional Access policies where necessary.
- Educate users about common phishing techniques, emphasizing that sign-in prompts should clearly identify the application being authenticated to.
- Revoke user refresh tokens if Storm-2372 or other device code phishing activity is suspected by calling revokeSignInSessions.
- Set a Conditional Access Policy to force re-authentication for users.
- Implement a sign-in risk policy to automate responses to risky sign-ins.
- Require multifactor authentication (MFA).
- Centralize identity management into a single platform, integrating on-premises and cloud directories.
- Secure accounts with credential hygiene, practicing the principle of least privilege and auditing privileged account activity.
- Implement enrollment restrictions to limit user permissions for enrolling devices into Microsoft Entra ID.
Hunting methods
Microsoft Defender XDR
The following query can help identify possible device code phishing attempts:
let suspiciousUserClicks = materialize(UrlClickEvents
| where ActionType in ("ClickAllowed", "UrlScanInProgress", "UrlErrorPage") or IsClickedThrough != "0"
| where UrlChain has_any ("microsoft.com/devicelogin", "login.microsoftonline.com/common/oauth2/deviceauth")
| extend AccountUpn = tolower(AccountUpn)
| project ClickTime = Timestamp, ActionType, UrlChain, NetworkMessageId, Url, AccountUpn);
//Check for Risky Sign-In in the short time window
let interestedUsersUpn = suspiciousUserClicks
| where isnotempty(AccountUpn)
| distinct AccountUpn;
let suspiciousSignIns = materialize(AADSignInEventsBeta
| where ErrorCode == 0
| where AccountUpn in~ (interestedUsersUpn)
| where RiskLevelDuringSignIn in (10, 50, 100)
| extend AccountUpn = tolower(AccountUpn)
| join kind=inner suspiciousUserClicks on AccountUpn
| where (Timestamp - ClickTime) between (-2min .. 7min)
| project Timestamp, ReportId, ClickTime, AccountUpn, RiskLevelDuringSignIn, SessionId, IPAddress, Url
);
//Validate errorCode 50199 followed by success in 5 minute time interval for the interested user, which suggests a pause to input the code from the phishing email
let interestedSessionUsers = suspiciousSignIns
| where isnotempty(AccountUpn)
| distinct AccountUpn;
let shortIntervalSignInAttemptUsers = materialize(AADSignInEventsBeta
| where AccountUpn in~ (interestedSessionUsers)
| where ErrorCode in (0, 50199)
| summarize ErrorCodes = make_set(ErrorCode) by AccountUpn, CorrelationId, SessionId
| where ErrorCodes has_all (0, 50199)
| distinct AccountUpn);
suspiciousSignIns
| where AccountUpn in (shortIntervalSignInAttemptUsers)
This following query from public research surfaces newly registered devices, and can be a useful in conjunction with anomalous or suspicious user or token activity:
CloudAppEvents
| where AccountDisplayName == "Device Registration Service"
| extend ApplicationId_ = tostring(ActivityObjects[0].ApplicationId)
| extend ServiceName_ = tostring(ActivityObjects[0].Name)
| extend DeviceName = tostring(parse_json(tostring(RawEventData.ModifiedProperties))[1].NewValue)
| extend DeviceId = tostring(parse_json(tostring(parse_json(tostring(RawEventData.ModifiedProperties))[6].NewValue))[0])
| extend DeviceObjectId_ = tostring(parse_json(tostring(RawEventData.ModifiedProperties))[0].NewValue)
| extend UserPrincipalName = tostring(RawEventData.ObjectId)
| project TimeGenerated, ServiceName_, DeviceName, DeviceId, DeviceObjectId_
- Monitor for anomalous token or PRT activity surrounding close-in-time device registrations.
- Use Risky sign-in reports to surface attempted and successful user access activities where the legitimate owner might not have performed the sign-in.
-
Azure Sentinel Queries
- Campaign with suspicious keywords
- Determine Successfully Delivered Phishing Emails to Inbox/Junk folder.
- Successful Signin from Phishing Link
- Phishing link click observed in Network Traffic
- Suspicious URL clicked
- Anomaly of MailItemAccess by GraphAPI
- OAuth Apps accessing user mail via GraphAPI
- OAuth Apps reading mail both via GraphAPI and directly
- OAuth Apps reading mail via GraphAPI anomaly
Original link: https://www.microsoft.com/en-us/security/blog/2025/02/13/storm-2372-conducts-device-code-phishing-campaign/
Okay, I will summarize the article “The BadPilot campaign: Seashell Blizzard subgroup conducts multiyear global access operation” and provide operational cyber intelligence for SOC, TI, IR, and Threat Hunting, following the format you specified.
The BadPilot campaign: Seashell Blizzard subgroup conducts multiyear global access operation
Summary
This article details the activities of a subgroup within the Russian state actor Seashell Blizzard (linked to Russian Military Intelligence Unit 74455 (GRU)), known as the “BadPilot campaign,” which has been active since at least 2021. This subgroup focuses on gaining initial access to Internet-facing infrastructure globally to enable Seashell Blizzard to persist on high-value targets and support tailored network operations. The subgroup uses opportunistic access techniques and stealthy persistence methods to collect credentials and achieve command execution, sometimes leading to significant regional network compromises. They target various sectors, including energy, oil and gas, telecommunications, shipping, arms manufacturing, and international governments. Since early 2024, the subgroup has expanded its access to include targets in the United States and United Kingdom. Microsoft assesses that the compromises made by this subgroup offer Seashell Blizzard options when responding to Russia’s evolving strategic objectives, particularly concerning organizations providing support to Ukraine. Despite the commodity nature of the subgroup’s exploitation patterns, shifts in their post-compromise tradecraft have been observed.
Technical Details
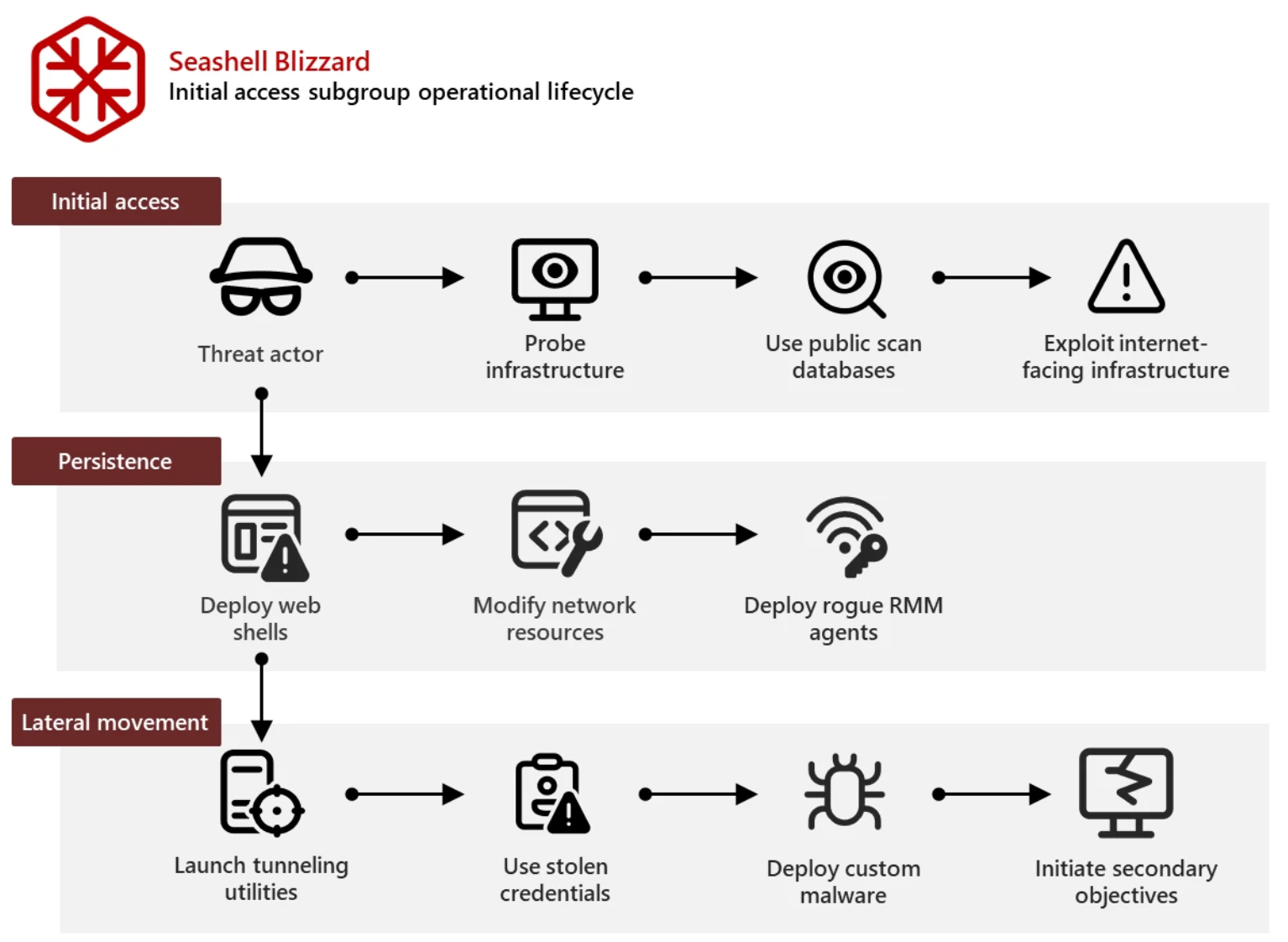
The Seashell Blizzard initial access subgroup employs a consistent operational lifecycle after exploiting vulnerable Internet-facing infrastructure. This involves a set of tactics, techniques, and procedures (TTPs) to maintain persistence and facilitate lateral movement, which have evolved to become more evasive.
Exploitation Patterns:
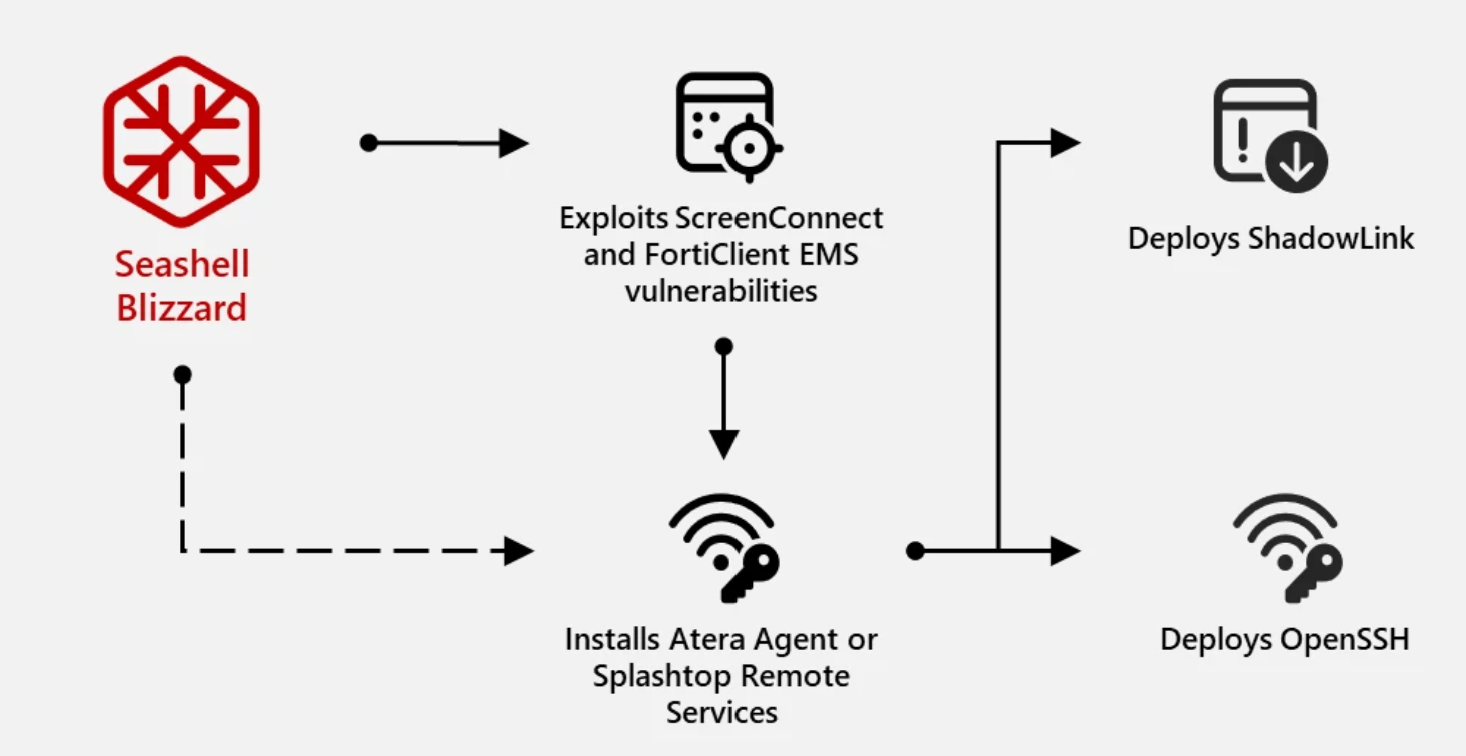
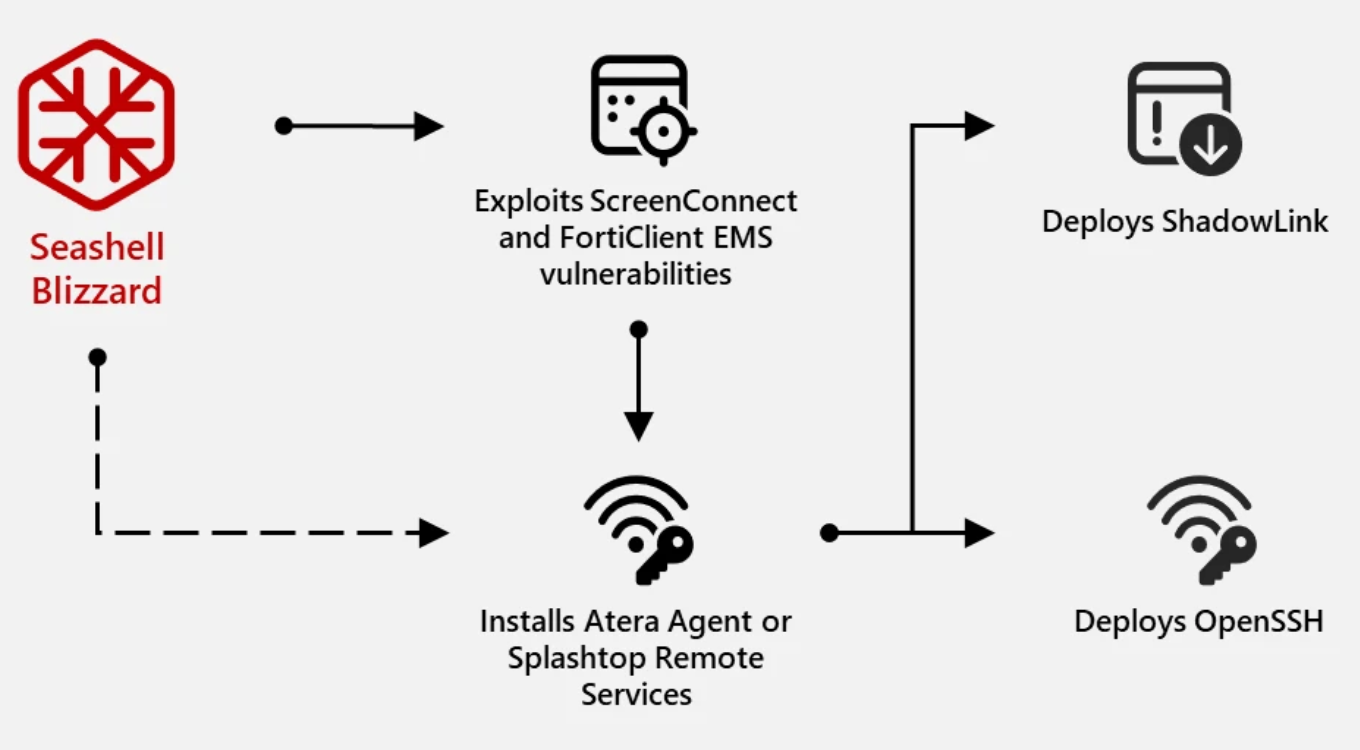
- RMM Suites Exploitation: In early 2024, the subgroup began exploiting vulnerabilities in ConnectWise ScreenConnect (CVE-2024-1709) and Fortinet FortiClient EMS (CVE-2023-48788) to deploy Remote Management and Monitoring (RMM) software like Atera Agent and Splashtop Remote Services. This allowed them to retain command and control (C2) functions while masquerading as legitimate utilities.
- Following exploitation, the subgroup used two methods of payload retrieval to install RMM agents:
- Retrieval of Atera Agent installers from legitimate agent endpoints
- Retrieval of Atera Agent from actor-controlled infrastructure
- After installing RMM software, Seashell Blizzard uses the native functionality of the agents to deploy secondary tools for credential acquisition, data exfiltration, and uploading custom utilities.
- Credential access is achieved through registry-based access, renamed procdump, and potentially via Taskmanager UI by LSASS process dumping.
- rclone.exe is deployed for data exfiltration using an actor-supplied configuration file.
- For durable persistence and direct access, OpenSSH is deployed with a unique public key, and ShadowLink is used.
- ShadowLink facilitates persistent remote access by configuring a compromised system as a Tor hidden service, using Tor service binaries and a unique Tor configuration file (torrc). It redirects inbound connections to the Tor hidden service address to ports for RDP (3389).
- Following exploitation, the subgroup used two methods of payload retrieval to install RMM agents:
- Web Shell Deployment: Since late 2021, the subgroup has deployed web shells following successful exploitation to maintain footholds and execute commands for deploying secondary tooling. This is often achieved by exploiting vulnerabilities in Microsoft Exchange (CVE-2021-34473) and Zimbra (CVE-2022-41352). The web shells are retrieved from actor-controlled infrastructure.
- LocalOlive is a web shell exclusive to this subgroup, written in ASPX supporting C#, and used for C2 and deploying additional utilities. It supports uploading/downloading files, running shell commands, and opening a port.
- Tunneling Utilities: When strategic targets are identified, the subgroup deploys tunneling utilities like Chisel, plink, and rsockstun to establish dedicated conduits into affected network segments.
- Chisel is often named MsChSoft.exe, MsNan.exe, Msoft.exe, Chisel.exe, Win.exe, MsChs.exe, MicrosoftExchange32.exe, Desk.exe, or Sys.exe.
- Rsockstun is often named Sc.exe.
- Reverse tunnels are established to exclusive VPS actor-owned infrastructure.
- Network Resource Modification: The subgroup modifies network resources, including Outlook Web Access (OWA) sign-in pages and DNS configurations, to gather network credentials.
- Rogue JavaScript is inserted into legitimate sign-in portals to collect clear text usernames and passwords.
- DNS A record configurations are modified, possibly to intercept credentials from critical authentication services.
Tools and Techniques:
- Exploitation of Vulnerabilities: Exploiting vulnerabilities in Internet-facing infrastructure such as ConnectWise ScreenConnect (CVE-2024-1709), Fortinet FortiClient EMS (CVE-2023-48788), Microsoft Exchange (CVE-2021-34473), and Zimbra (CVE-2022-41352).
- Remote Management and Monitoring (RMM) Software: Deploying Atera Agent and Splashtop Remote Services for command and control.
- Web Shells: Using web shells like LocalOlive for command execution and deploying additional utilities.
- Tunneling Utilities: Employing Chisel, plink, and rsockstun for establishing dedicated conduits into affected network segments.
- Credential Access: Obtaining credentials through registry-based access, renamed procdump, Taskmanager UI, and modification of OWA sign-in pages.
- Data Exfiltration: Using rclone.exe to exfiltrate data.
- ShadowLink: Utilizing Tor hidden services for persistent remote access.
Countries
- Ukraine
- United States
- United Kingdom
- Europe
- Central Asia
- Middle East
- Canada
- Australia
Industries
- Energy
- Oil and gas
- Telecommunications
- Shipping
- Arms manufacturing
- International governments
- Retail
- Education
- Consulting
- Agriculture
Recommendations
- Utilize a vulnerability management system.
- Require multifactor authentication (MFA).
- Implement Entra ID Conditional Access authentication strength.
- Encourage users to use web browsers that support Microsoft Defender SmartScreen.
- Use Microsoft Defender External Attack Surface Management (EASM).
- Enable Network Level Authentication for Remote Desktop Service connections.
- Enable AppLocker to restrict specific software tools.
- Ensure that tamper protection is enabled in Microsoft Defender for Endpoint.
- Enable network protection in Microsoft Defender for Endpoint.
- Turn on web protection.
- Run endpoint detection and response (EDR) in block mode.
- Configure investigation and remediation in full automated mode.
- Turn on Safe Links and Safe Attachments in Microsoft Defender for Office 365.
- Enable Zero-hour auto purge (ZAP) in Microsoft Defender for Office 365.
- Invest in advanced anti-phishing solutions.
- Configure Microsoft Defender for Office 365 to recheck links on click.
- Use the Attack Simulator in Microsoft Defender for Office 365.
- Block executable content from email client and webmail.
- Block executable files from running unless they meet a prevalence, age, or trusted list criterion.
- Block execution of potentially obfuscated scripts.
- Block JavaScript or VBScript from launching downloaded executable content.
- Block process creations originating from PSExec and WMI commands.
Hunting methods
ScreenConnect
Surface the possible exploitation of ScreenConnect to launch suspicious commands.
DeviceProcessEvents
| where InitiatingProcessParentFileName endswith "ScreenConnect.ClientService.exe"
| where (FileName in~ ("powershell.exe", "powershell_ise.exe", "cmd.exe") and
ProcessCommandLine has_any ("System.DirectoryServices.ActiveDirectory.Domain", "hidden -encodedcommand", "export-registry", "compress-archive", "wget -uri", "curl -Uri", "curl -sko", "ipconfig /all", "& start /B", "start msiexec /q /i", "whoami", "net user", "net group", "localgroup administrators", "dsquery", "samaccountname=", "query session", "adscredentials", "o365accountconfiguration", "-dumpmode", "-ssh", "o or (FileName =~ "wget.exe" and ProcessCommandLine contains "http")
or (FileName =~ "mshta.exe" and ProcessCommandLine contains "http")
or (FileName =~ "curl.exe" and ProcessCommandLine contains "http")
or ProcessCommandLine has_all ("powershell", "-command", "curl")
or ProcessCommandLine has_any ("E:jscript", "e:vbscript", "start msiexec /q /i")
or ProcessCommandLine has_all ("reg add", "DisableAntiSpyware", @"\Microsoft\Windows Defender")
or ProcessCommandLine has_all ("reg add", "DisableRestrictedAdmin", @"CurrentControlSet\Control\Lsa")
or ProcessCommandLine has_all ("vssadmin", "delete", "shadows")
or ProcessCommandLine has_all ("vssadmin", "list", "shadows")
or ProcessCommandLine has_all ("wmic", "process call create")
or ProcessCommandLine has_all ("wmic", "delete", "shadowcopy")
or ProcessCommandLine has_all ("wmic", "shadowcopy", "call create")
or ProcessCommandLine has_all ("wbadmin", "delete", "catalog")
or ProcessCommandLine has_all ("ntdsutil", "create full")
or (ProcessCommandLine has_all ("schtasks", "/create") and not(ProcessCommandLine has "shutdown"))
or (ProcessCommandLine has "nltest" and ProcessCommandLine has_any ("domain_trusts", "dclist", "all_trusts"))
or (ProcessCommandLine has "lsass" and ProcessCommandLine has_any ("procdump", "tasklist", "findstr"))
or FileName in~ ("tasklist.exe", "ssh.exe", "icacls.exe", "certutil.exe", "calc.exe", "bitsadmin.exe", "accesschk.exe", "mshta.exe",
"winrm.exe", "dsquery.exe", "makecab.exe", "hh.exe", "pcalua.exe", "regsvr32.exe",
"cmstp.exe", "esentutl.exe", "dnscmd.exe", "gpscript.exe", "msdt.exe", "msra.exe", "odbcconf.exe")
| where not(ProcessCommandLine has_any ("servicedesk.atera.com", "support.csolve.net", "lt.tech-keys.com", "certutil -hashfile"))
FortiClient EMS log capture
If you believe your FortiClient has been exploited before patching, this query may help with further investigation.
According to Horizon3 research, the C:\Program Files (x86)\Fortinet\FortiClientEMS\logs log file can be examined to identify malicious activity. Run the following query to surface devices with this log file for further investigation.
DeviceFileEvents
| where FileName contains @"C:\Program Files (x86)\Fortinet\FortiClientEMS\logs"
| distinct DeviceName
Additionally, Horizon3 noted that this SQL vulnerability could allow for remote code execution (RCE) using the xp_cmdshell functionality of Microsoft SQL Server. The SQL logs can also be examined for evidence of xp_cmdshell being leveraged to spawn a Windows command shell.
According to Microsoft research, the following query could help surface exploitation activity related to this vulnerability.
DeviceProcessEvents
| where InitiatingProcessFileName == "sqlservr.exe"
| where FileName =~ "cmd.exe"
| where ProcessCommandLine has_any ("webclient", "downloadstring", "http", "https", "downloadfile")
| where InitiatingProcessCommandLine has_all ("sqlservr.exe", "-sFCEMS")
Tor service
Find services associated with Tor.
DeviceEvents
| where ActionType == 'ServiceInstalled'
| extend JSON = parse_json(AdditionalFields)
| where JSON.ServiceName has 'tor'
YARA rule
Use the following Yara rule to find malicious JavaScript inserted into OWA sign-in pages.
rule injected_cred_logger_owa {
strings:
$owa = "<!-- OwaPa"
$jq = "jquery"
$ajax = ".ajax"
$keypress = ".keypress"
$which = "e.which == 13"
$encoding1 = "btoa"
$encoding2 = "unescape"
$encoding3 = "encodeURIComponent"
$m1 = "GET"
$m2 = "POST"
condition:
$owa and $jq and $ajax and $keypress and $which and (2 of ($encoding*)) and (1 of ($m*))
}
- Microsoft Defender Antivirus detections:
- Seashell Blizzard activity group
- Microsoft Defender for Endpoint alerts:
- Possible Seashell Blizzard activity
- Suspicious Atera installation via ScreenConnect
- Suspicious command execution via ScreenConnect
- Suspicious sequence of exploration activities
- CredentialDumpingViaEsentutlDetector
- Suspicious behavior by cmd.exe was observed
- SQL Server login using xp_cmdshell
- Suspicious port scan activity within an RDP session
- Suspicious connection to remote service
- Suspicious usage of remote management software
- New local admin added using Net commands
- Sensitive data was extracted from registry
- Suspicious Scheduled Task Process Launched
- Potential human-operated malicious activity
- Compromised account conducting hands-on-keyboard attack
- Sensitive file access for possible data exfiltration or encryption
- Possible Fortinet FortiClientEMS vulnerability exploitation
- Possible target of NTLM credential theft
- Possible exploitation of ProxyShell vulnerabilities
- Possibly malicious use of proxy or tunneling tool
- Hidden dual-use tool launch attempt
- KQL Queries:
- ScreenConnect exploitation
- FortiClient EMS log capture
- Tor service detection
- ScreenConnect network connection
- Normalized Network Session events using the ASIM unifying parser _Im_NetworkSession for IOCs
- Normalized Web Session events using the ASIM unifying parser _Im_WebSession for IOCs
- YARA Rule:
- Detection of malicious JavaScript inserted into OWA sign-in pages
- Microsoft Sentinel TI Mapping analytics
IOC
File Hashes:
LocalOlive web shell:
c7379b2472b71ea0a2ba63cb7178769d27b27e1d00785bfadac0ae311cc88d8b
b38f1906680c80e1606181b3ccb8539dab5af2a7222165c53cdd68d09ec8abb0
9f3d8252e8f3169751a705151bdf675ac194bfd8457cbe08e1f3c17d7e9e9be2
68c7aab670ee9d7461a4a8f06333994f251dc79813934166421091e2f1fa145c
636e04f0618dd578d107f440b1cf6c910502d160130adae5e415b2dd2b36abcb
cab97e837a3fc095bf59703574cbfa7e60fb10991101ba9bfc9bbf294c18fd97
Chisel:
b9ef2e948a9b49a6930fc190b22cbdb3571579d37a4de56564e41a2ef736767b
File Names:
def.aspx (LocalOlive web shell)
MsChSoft.exe (Chisel tunneling utility)
MsNan.exe (Chisel tunneling utility)
Msoft.exe (Chisel tunneling utility)
Chisel.exe (Chisel tunneling utility)
Win.exe (Chisel tunneling utility)
MsChs.exe (Chisel tunneling utility)
MicrosoftExchange32.exe (Chisel tunneling utility)
Desk.exe (Chisel tunneling utility)
Sys.exe (Chisel tunneling utility)
Sc.exe (Rocstun tunneling utility)
Email Addresses (Actor-controlled):
akfcjweiopgjebvh@proton.me
ohipfdpoih@proton.me
miccraftsor@outlook.com
amymackenzie147@protonmail.ch
ehklsjkhvhbjl@proton.me
MirrowSimps@outlook.com
Infrastructure (Seashell Blizzard):
103.201.129[.]130
104.160.6[.]2
195.26.87[.]209
hwupdates[.]com
cloud-sync[.]org
148.251.53[.]222
89.149.200[.]91
17738a27bb307b3cb7bd571934a398223e170842005f1725c46c7075f14e90fe
Original link: https://www.microsoft.com/en-us/security/blog/2025/02/12/the-badpilot-campaign-seashell-blizzard-subgroup-conducts-multiyear-global-access-operation/