The Feed 2025-03-21

AI Generated Podcast
https://open.spotify.com/episode/2VWl9iVQgcawqUURCA960h?si=YbEpB3C2QQecFBaNEhwoCA
Summarized Stories
- UAT-5918 targets critical infrastructure entities in Taiwan: Cisco Talos reports on the activity of threat actor UAT-5918, which has been targeting critical infrastructure organizations in Taiwan since at least 2023, employing web shells and open-source tools for long-term access and information theft, with overlaps in TTPs and victimology with groups like Volt Typhoon and Flax Typhoon.
- BitM Up! Session Stealing in Seconds Using the Browser-in-the-Middle Technique: This blog post by Mandiant discusses Browser in the Middle (BitM) attacks as a rapid method for stealing authenticated session tokens, even bypassing MFA, and suggests defenses like hardware-based MFA and client certificates.
- By Executive Order, We Are Banning Blacklists - Domain-Level RCE in Veeam Backup & Replication (CVE-2025-23120): This watchTowr Labs post exposes new Remote Code Execution (RCE) vulnerabilities in Veeam Backup & Replication, stemming from the continued use of deserialization blacklists that can be bypassed by domain users.
- Albabat Ransomware Group Potentially Expands Targets to Multiple OS, Uses GitHub to Streamline Operations: This article from Trend Research details the discovery of new Albabat ransomware versions targeting Windows, Linux, and macOS, and their use of GitHub for operational efficiency.
- South Korean Organizations Targeted by Cobalt Strike ‘Cat’ Delivered by a Rust Beacon: Hunt researchers uncovered an intrusion campaign targeting South Korean entities, utilizing a publicly exposed server hosting a Rust-compiled loader for a modified Cobalt Strike variant known as ‘Cat’, along with open-source reconnaissance tools.
UAT-5918 targets critical infrastructure entities in Taiwan
Summary
Cisco Talos has identified a malicious campaign, tracked as UAT-5918, that has been actively targeting critical infrastructure entities in Taiwan since at least 2023. This threat actor, believed to be motivated by long-term information theft, establishes persistent access by exploiting N-day vulnerabilities and utilizes a combination of web shells and open-source tooling for post-compromise activities, including credential harvesting and lateral movement. UAT-5918’s TTPs and victimology show significant overlap with other APT groups such as Volt Typhoon, Flax Typhoon, Earth Estries, and Dalbit.
Technical Details
UAT-5918 is assessed to be an advanced persistent threat (APT) group focused on establishing long-term persistent access in Taiwanese victim environments. The group typically gains initial access by exploiting N-day vulnerabilities in unpatched web and application servers exposed to the internet. Following successful compromise, the threat actor conducts preliminary reconnaissance using standard operating system commands such as ping <IP>, net user, systeminfo, arp –a, route print, tasklist, tasklist -v, netstat -ano, whoami, ipconfig, query user, and cmd /c dir to gather information about users, domains, and system configurations. Initial credential reconnaissance involves the cmdkey /list command.
For post-compromise activities, UAT-5918 heavily relies on publicly available red-teaming tools and network scanning utilities. They frequently use web shells, including the publicly available Chopper web shell, deployed across discovered sub-domains and internet-accessible servers to create multiple entry points. The threat actor utilizes reverse proxies and tunnels such as FRP and Neo-reGeorg to access compromised endpoints via attacker-controlled remote hosts. The tools are downloaded as archives and extracted using commands like:
C:/Temp/frpc-x64[.].zip
C:\Program Files\7-Zip\7zG[.].exe x -o<C:\Temp\frpc-x64> -spe -slp- -an -ai#7zMap11476:44:7zEvent8716
and
C:\Program Files\WinRAR\WinRAR[.].exe x -iext -ow -ver -- C:\ProgramData\Neo-reGeorg-5[.].2[.]0[.].zip C:\ProgramData\Neo-reGeorg-5.2.0\
The Earthworm (ew) tool is also used for establishing proxies, executed with commands such as Run32[.].exe -s ssocksd -l 8888.
For port scanning and vulnerability scanning, UAT-5918 employs tools like FScan, capable of scanning IP ranges and specific ports. Talos observed scans targeting ports 21, 22, 80, 81, 83, 91, 135, 443, 445, 888, 808, 889, 5432, 8000, 8080, 54577, and 11211. They also heavily utilize In-Swor, another publicly available tool, for port scans across IP address ranges, scanning for ports such as 22 (SSH), 80 (HTTP), 135 (RPC), 445 (SMB), 1433 (SQL server), 1521 (Oracle DBs), 3306 (MySQL), 3389 (RDP), 4194 (Kubernetes?), 5432 (PostgreSQL), 5900 (VNC), 6379 (Redis), 10248 (?), 10250 (Kubernetes), 10255 (MongoDB). In-Swor is also used to establish proxy channels with commands like svchost[.]exe proxy -l *:22 -k 9999 and svchost[.]exe -type server -proto tcp -listen :443. PortBrute, a password brute-forcer for multiple protocols, is also used.
For additional network reconnaissance, the threat actor uses NirSoft’s CurrPorts utility and TCPView to monitor current connections, likely to discover pivot points. They also use PowerShell scripts to attempt SMB logins to identified endpoints. Netspy, a network segmentation discovery tool, is occasionally employed.
To gather local system information, commands such as wmic diskdrive get partitions /value, fsutil fsinfo drives, and wmic logicaldisk get DeviceID,VolumeName,Size,FreeSpace are executed.
For maintaining persistent access, UAT-5918 deploys multiple web shells, often ASP or PHP-based, in inconspicuous directories. They also use a web shell variant of JuicyPotato (a privilege escalation tool). JuicyPotato is then used to spawn cmd[.]exe for a reverse shell, enabling arbitrary command execution. The threat actor also uses PuTTY’s pscp tool to deliver additional web shells to servers. Additionally, reverse Meterpreter shells have been observed for persistent access. Backdoored user accounts with administrative privileges are regularly created using net user and net localgroup administrators commands.
Credential extraction is a key objective, achieved through tools like Mimikatz, LaZagne, and browser credential stealers. Mimikatz is used to obtain credentials from endpoints. LaZagne is employed as an open-source credential extractor. The attackers also take registry dumps of the SAM, SECURITY, and SYSTEM hives using the reg save command. BrowserDataLite is used to extract login information, cookies, and browsing history from web browsers like Chrome, which is then accessed via notepad. SNETCracker, a .NET-based password cracker, is used for brute-forcing various services. The threat actor also searches for strings related to credentials in configuration files using findstr.
For pivoting to additional endpoints, UAT-5918 performs cyclical network reconnaissance and attempts to gain access via RDP using mstsc.exe. Impacket is frequently used for lateral movement and tool deployment, as seen in commands like:
python wmiexec[.]py Administrator:<password>@<IP> -codec big5 1> [\][\]127[.]0[.]0[.]1\ADMIN$\__<timestamp> 2>&1
and utilizing network shares with commands like net use and copy to distribute tools like fscan.exe and mimikatz.exe.
File collection and staging involve enumerating local and shared drives for data of interest, including confidential documents, database exports, backups, and application configuration files. In one instance, SQLCMD.EXE was used to create database backups for exfiltration.
Countries
Taiwan
Industries
Telecommunications
Healthcare
Information technology
Critical infrastructure sectors
Recommendations
Customers can detect and block this threat using various Cisco security products.
- Cisco Secure Endpoint (AMP for Endpoints) can prevent malware execution.
- Cisco Secure Email (formerly Cisco Email Security) can block malicious emails.
- Cisco Secure Firewall (formerly Next-Generation Firewall and Firepower NGFW) appliances can detect malicious activity.
- Cisco Secure Malware Analytics (Threat Grid) identifies malicious binaries and builds protection.
- Cisco Secure Access provides secure access based on Zero Trust principles.
- Umbrella (Cisco’s secure internet gateway) blocks connections to malicious domains, IPs, and URLs.
- Cisco Secure Web Appliance (formerly Web Security Appliance) blocks dangerous and suspicious websites.
- Firewall Management Center offers additional protections based on environment and threat data.
- Cisco Duo provides multi-factor authentication.
- Open-source Snort Subscriber Rule Set customers can update to the latest rule pack.
Hunting methods
The article does not explicitly provide specific Yara, Sigma, KQL, SPL, or other hunting queries. However, based on the TTPs described, threat hunters can develop detection rules focusing on:
- Execution of known red-teaming tools: Monitor for the execution of
frp.exe,Neo-reGeorg,ew.exe,fscan.exe,in-swor.exe,PortBruteWin.exe,cports.exe,tcpview64.exe,mimikatz.exe,LaZagne.exe,BrowserDataLite_x64.exe,SNETCracker.exe,JuicyPotato.exe,pscp.exe,SQLCMD.EXE. - Command-line activity indicative of reconnaissance: Look for sequences of commands such as
ping,net user,systeminfo,arp -a,route print,tasklist,netstat,whoami,ipconfig,query user, and multipledircommands targeting user directories. - Web shell deployment: Monitor for the creation of new ASP or PHP files in web server directories, especially within housekeeping directories.
- Persistence mechanisms: Look for the creation of new administrative user accounts using
net userand the addition of users to the “Administrators” or “Domain Admins” groups usingnet localgroupornet group. Monitor for the execution of reverse shells initiated by JuicyPotato. - Credential dumping activity: Monitor for the execution of
mimikatz.exe,LaZagne.exe, and commands involvingreg save hklm\sam,reg save hklm\security, andreg save hklm\system. Look for notepad.exe accessing files namedChrome_LoginPass.txt,Chrome_Cookies.txt, orChrome_History.txt. - Lateral movement attempts: Monitor for RDP connections using
mstsc.exeand the execution ofwmiexec.pyor other Impacket tools, especially when involving unusual network share access patterns and the copying of executables to remote hosts. - Disabling of Microsoft Defender: Look for
powershell.exe -exec bypass Add-MpPreference -ExclusionPath.
The logic behind these hunting methods is to identify processes, command-line arguments, and file system activity that are characteristic of the tools and techniques employed by UAT-5918 as described in the report.
IOC
File Hashes (SHA256):
6F6F7AA6144A1CFE61AC0A80DB7AD712440BDC5730644E05794876EB8B6A41B4
BAB01D029556CF6290F6F21FEC5932E13399F93C5FDBCFFD3831006745F0EB83
F7F6D0AFB300B57C32853D49FF50650F5D1DC7CF8111AA32FF658783C038BFE5
497A326C6C207C1FB49E4DAD81D051FCF6BCBE047E0D3FE757C298EF8FE99ABA
F9EB34C34E4A91630F265F12569F70B83FEBA039C861D6BF906B74E7FB308648
DD832C8E30ED50383495D370836688EE48E95334270CBBCE41109594CB0C9FD1
F7B52EE613F8D4E55A69F0B93AA9AA5472E453B0C458C8390DB963FF8B0B769C
B994CBC1B5C905A2B731E47B30718C684521E8EC6AFB601AFECF30EF573E5153
12D4EFE2B21B5053A3A21B49F25A6A4797DC6E9A80D511F29CA67039BA361F63
2272925B1E83C7C3AB24BDEB82CE727DB84F5268C70744345CDA41B452C49E84
71EB5115E8C47FFF1AB0E7ACEBAEA7780223683259A2BB1B8DB1EB3F26878CA4
E159824448A8E53425B38BD11030AA786C460F956C9D7FC118B212E8CED4087A
7EF22BFB6B2B2D23FE026BDFD7D2304427B6B62C6F9643EFEDDB4820EBF865AF
EFC0D2C1E05E106C5C36160E17619A494676DEB136FB877C6D26F3ADF75A5777
B7690c0fc9ec32e1a54663a2e5581e6260fe9318a565a475ee8a56c0638f38d0
A774244ea5d759c4044aea75128a977e45fd6d1bb5942d9a8a1c5d7bff7e3db9
31742ab79932af3649189b9287730384215a8dccdf21db50de320da7b3e16bb4
09cea8aed5c58c446e6ef4d9bb83f7b5d7ba7b7c89d4164f397d378832722b69
D47e35baee57eb692065a2295e3e9de40e4c57dba72cb39f9acb9f564c33b421
1753fa34babeeee3b20093b72987b7f5e257270f86787c81a556790cb322c747
F4ea99dc41cb7922d01955eef9303ec3a24b88c3318138855346de1e830ed09e
5b0f8c650f54f17d002c01dcc74713a40eccb0367357d3f86490e9d17fcd71e8
3588bda890ebf6138a82ae2e4f3cd7234ec071f343c9f5db5a96a54734eeaf9f
95eee44482b4226efe3739bed3fa6ce7ae7db407c1e82e988f27cd27a31b56a6
02ab315e4e3cf71c1632c91d4914c21b9f6e0b9aa0263f2400d6381aab759a61
D1825cd7a985307c8585d88d247922c3a51835f9338dc76c10cdbad859900a03
234899dea0a0e91c67c7172204de3a92a4cbeef37cdc10f563bf78343234ad1d
8d440c5f0eca705c6d27aa4883c9cc4f8711de30fea32342d44a286b362efa9a
Ffb8db57b543ba8a5086640a0b59a5def4929ad261e9f3624b2c0a22ae380391
Original link: https://blog.talosintelligence.com/uat-5918-targets-critical-infra-in-taiwan/
BitM Up! Session Stealing in Seconds Using the Browser-in-the-Middle Technique
Summary
This article discusses the rise of Browser-in-the-Middle (BitM) attacks, which offer a streamlined approach for attackers to quickly compromise user sessions across various web applications. While multi-factor authentication (MFA) remains a crucial security measure, the article highlights that sophisticated social engineering tactics can effectively bypass it by targeting session tokens. Once a user authenticates with MFA, the application stores a session token in the browser, and stealing this token grants the attacker access without needing to perform the MFA challenge. The article contrasts BitM attacks with traditional methods like transparent proxies (e.g., Evilginx2), which require significant customization and understanding of the targeted application’s authentication mechanisms. BitM attacks, on the other hand, leverage the inherent functionalities of a web browser to deceive the victim into believing they are browsing normally, while all actions are performed on the attacker’s machine. This technique allows for rapid targeting of virtually any website with minimal configuration, making it exceptionally challenging for victims to distinguish between legitimate and fake sites. Mandiant’s internal tool, Delusion, is presented as an example of a BitM framework that simplifies session stealing by operating a legitimate site through an attacker-controlled browser. The article concludes by emphasizing the importance of robust defenses against BitM attacks, recommending the implementation of hardware-based MFA (like FIDO2) and client certificates.
Technical Details
 Browser-in-the-Middle (BitM) attacks present a significant threat by offering a rapid and less complex method for session hijacking compared to traditional techniques. Unlike transparent proxies such as Evilginx2, which intercept and modify HTTP requests and responses to capture credentials and session cookies, BitM attacks operate by controlling the entire browser session.
Browser-in-the-Middle (BitM) attacks present a significant threat by offering a rapid and less complex method for session hijacking compared to traditional techniques. Unlike transparent proxies such as Evilginx2, which intercept and modify HTTP requests and responses to capture credentials and session cookies, BitM attacks operate by controlling the entire browser session.
Traditional Transparent Proxies: These proxies, exemplified by Evilginx2, act as intermediaries between the victim and the targeted service. When a victim interacts with a phishing site hosted by the attacker, their HTTP requests are captured and forwarded to the legitimate website. The attacker’s server then modifies the responses before sending them back to the victim, replacing legitimate domain references with the phishing domain. This allows for the capture of login credentials from POST requests and the extraction of session cookies (tokens) from the server’s response headers after successful authentication, including MFA. However, deploying these transparent proxies against custom applications can be time-consuming and requires a deep understanding of the application’s session management and authentication processes. Maintaining updated templates for each targeted application also introduces significant overhead.
Browser-in-the-Middle (BitM) Attacks: In contrast, BitM attacks leverage the inherent functionalities of a web browser, essentially tricking the victim into using an attacker-controlled browser instance. The victim is convinced they are interacting with the legitimate website, while all their actions occur on the attacker’s machine. This bypasses the need for intricate proxy configurations or detailed knowledge of the target application’s authentication protocols.
A key advantage of BitM is its rapid targeting capability, allowing attackers to target any website on the web in seconds with minimal configuration. Once a target is specified within a BitM framework, the legitimate site is served through the attacker-controlled browser. This makes detection extremely difficult for the victim as the entire browser window, including the URL and SSL certificate indicators, appears legitimate.
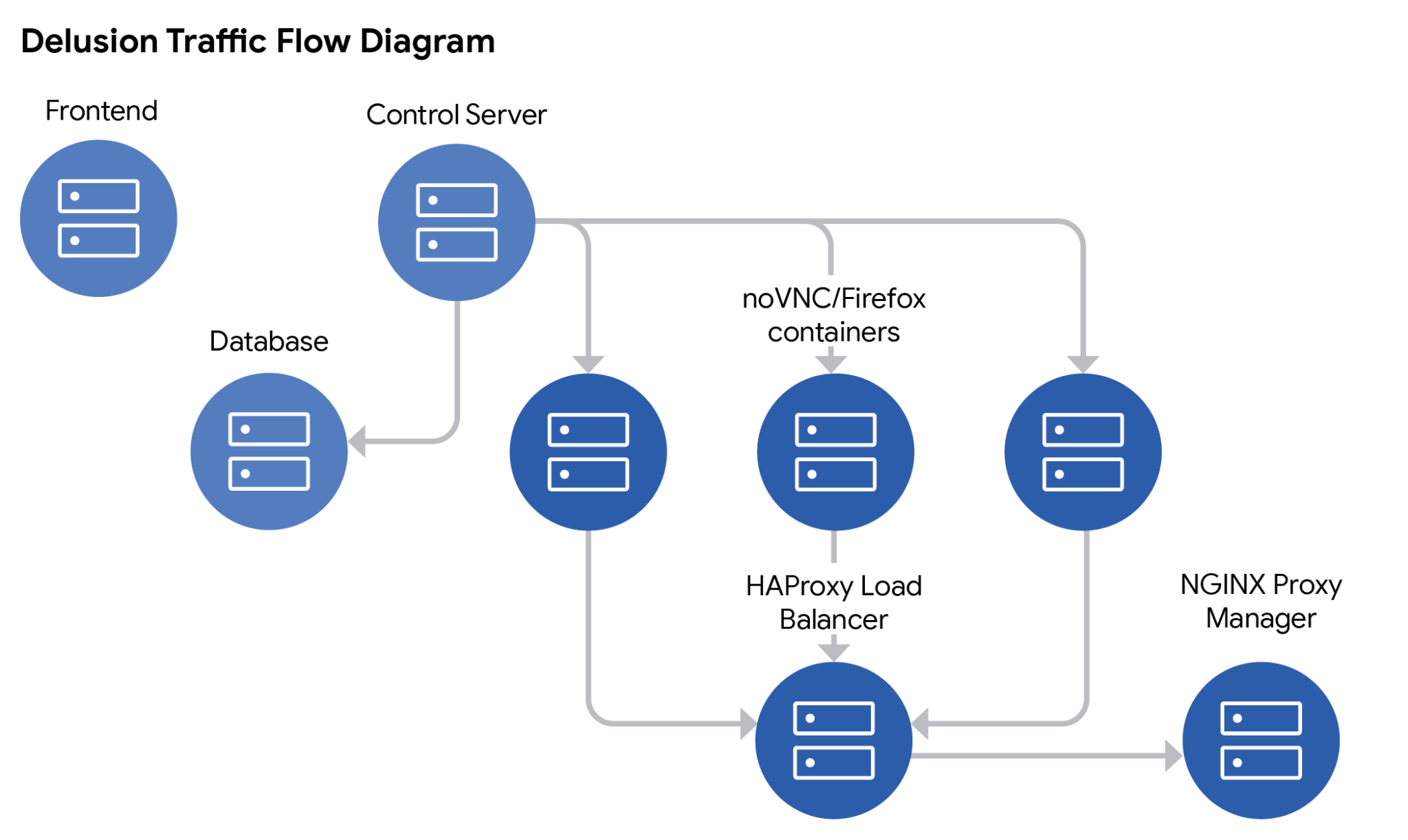
Mandiant’s Delusion Framework: This internal tool exemplifies the capabilities of BitM attacks. Delusion allows an operator to target applications without prior knowledge of their authentication protocols. Its features include:
- Firefox browser profile storage and download: This enables trivial session stealing without the need for cookie import.
- Real-time monitor page: Operators can observe and interact with the victim’s session in real time.
- Scalable container infrastructure: Delusion supports scaling containers and automatically adding them to a load balancer for large-scale phishing campaigns.
- Dual operation modes (Manual and Automatic): Designed for both vishing and phishing scenarios.
- Bookmarks: Simplifies deployment against multiple websites.
- Tagging: For campaign management.
- Session recording: For reporting purposes.
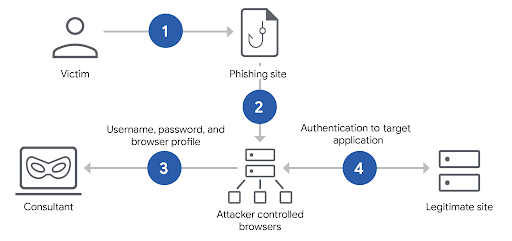
The typical BitM attack flow, as illustrated in Figure 6, involves:
- Social Engineering: The victim is lured to a malicious website via phishing, vishing, or SMS phishing (smishing).
- Redirection: The victim’s connection to the malicious site is routed through a load balancer to an attacker-controlled proxied browser.
- Credential Capture: The victim unknowingly interacts with the proxied browser, entering their credentials and MFA tokens. The attacker gains access to the username, password, and effectively the browser profile state.
- Session Compromise: Once the attacker observes a successful login, the victim is disconnected, and their authenticated session is now under the attacker’s control. The downloaded browser profile contains all necessary information to resume the session.
BitM attacks are particularly effective against applications providing initial access to privileged networks through Virtual Desktop Infrastructure (VDI). Targeting login portals becomes a simple process of specifying the portal information and deploying the attack infrastructure.
Recommendations
To defend against BitM attacks, organizations should implement robust authentication and access-control mechanisms. The following technical recommendations are provided:
- Require client certificates for authentication: These certificates are typically bound to specific devices and cannot be easily manipulated by attackers, thus deterring BitM attacks.
- Implement hardware-based Multi-Factor Authentication (MFA) solutions like FIDO2 compatible security keys: These offer strong protection against BitM as the FIDO2 protocol ensures that authentication responses are immutably tied to the request’s origin, preventing replay attacks from the attacker’s site. Figure 7 illustrates the FIDO2 authentication flow, and Figure 8 shows how FIDO2 and certificate-based authentication can halt a BitM attack.
- Adopt a layered security approach for all applications that host sensitive data or provide access to restricted networks. This is crucial because even hardware-based MFA and client certificates are vulnerable if the device they reside on is compromised.
- Consider using compensating controls in conjunction with strong authentication methods to further enhance resilience against sophisticated threats like BitM.
Original link: https://cloud.google.com/blog/topics/threat-intelligence/session-stealing-browser-in-the-middle/
By Executive Order, We Are Banning Blacklists - Domain-Level RCE in Veeam Backup & Replication (CVE-2025-23120)
Summary
This article from watchTowr Labs details two Remote Code Execution (RCE) vulnerabilities found in Veeam Backup & Replication, tracked as CVE-2025-23120. The vulnerabilities stem from insecure deserialization due to the use of a blacklist-based security mechanism to control which .NET classes can be deserialized. Despite previous research and patches that added to the blacklist, the authors discovered two new gadget classes within the Veeam codebase itself (Veeam.Backup.EsxManager.xmlFrameworkDs and Veeam.Backup.Core.BackupSummary) that extend the .NET DataSet class, a known RCE gadget. These vulnerabilities can be exploited by any authenticated domain user if the Veeam server is joined to an Active Directory domain. The authors emphasize the inherent flaws of relying on blacklists for deserialization protection and express concern over the repeated patching approach by Veeam. The vulnerabilities affect Veeam Backup & Replication 12.3.0.310 and all earlier version 12 builds.
Technical Details
The article builds upon previous research, specifically referencing CVE-2024-40711, which involved an unauthenticated RCE vulnerability in Veeam Backup & Replication due to insecure deserialization via the .NET Remoting Channel. Veeam attempted to mitigate this by implementing a custom formatter with a blacklist to restrict deserialized classes. However, the initial blacklist was incomplete and missed the System.Runtime.Remoting.ObjRef gadget, allowing for RCE. A patch was released (Veeam KB 4693) that extended the blacklist to include ObjRef and other potentially malicious classes discovered by Sina Kheirkhah (System.CodeDom.Compiler.TempFileCollection, System.IO.DirectoryInfo).
The current research demonstrates that even with these additions, the blacklist approach remains insufficient. The authors discovered two new deserialization gadgets within the Veeam codebase itself: Veeam.Backup.EsxManager.xmlFrameworkDs and Veeam.Backup.Core.BackupSummary. Both of these classes inherit from the .NET DataSet class and are marked as Serializable. The DataSet class is a well-known gadget in .NET deserialization attacks, as its deserialization process can be leveraged to achieve RCE.
The exploitation chain involves the following steps:
- An authenticated domain user can access the Veeam .NET Remoting Channel. The Veeam Mount Service’s authorization check in the
CMountServiceAccessChecker.HasAccessmethod allows any user belonging to the local Users group to pass the check. When a machine is joined to an Active Directory domain, the Domain Users group is added to the local Users group, making this attack vector accessible to any domain user by default. - The .NET Remoting Channel exposes deserialization capabilities based on BinaryFormatter.
- Veeam’s custom formatter implements a whitelist-like mechanism initially, but one of the allowed classes, Veeam.Backup.Model.CDbCryptoKeyInfo, contains a constructor that leads to an inner deserialization mechanism controlled by a blacklist via
CProxyBinaryFormatter.DeserializeCustomandRestrictedSerializationBinder. - By deserializing the whitelisted
CDbCryptoKeyInfoclass with attacker-controlled input, the attacker can trigger the internal blacklist-protected deserialization. - The discovered gadgets, Veeam.Backup.EsxManager.xmlFrameworkDs and Veeam.Backup.Core.BackupSummary, are not on the blacklist. Since these classes extend DataSet and have the necessary characteristics for BinaryFormatter deserialization (Serializable attribute and a suitable constructor inherited from DataSet), they can be exploited.
- During the deserialization of these gadget classes, their parent class, DataSet, will be deserialized, which can be manipulated to achieve arbitrary code execution. This typically involves modifying the type and assembly names within the serialized data.
The authors provide hints on how to adapt the Proof-of-Concept (PoC) for CVE-2024-40711 to exploit these new vulnerabilities by replacing ObjRefGenerator with DataSetTypeSpoofGenerator and modifying the AssemblyName and FullTypeName to point to the newly discovered gadget classes.
The vendor’s response to these new findings was to further extend the blacklist to include Veeam.Backup.EsxManager.xmlFrameworkDs and Veeam.Backup.Core.BackupSummary. The authors criticize this reactive approach, highlighting that relying solely on blacklists is fundamentally flawed and that a more comprehensive solution is needed.
Recommendations
The authors strongly imply that moving away from blacklist-based deserialization protection is the primary recommendation. They suggest that Veeam should adopt a more robust security mechanism, such as a whitelist that explicitly allows only safe classes to be deserialized.
While not direct technical recommendations for mitigation in the interim, the article highlights the importance of prompt patching. Users of Veeam Backup & Replication version 12.3.0.310 and all earlier version 12 builds are vulnerable and should apply the necessary patches released by Veeam.
The article also implicitly recommends that organizations should be mindful of the security implications of joining their Veeam Backup & Replication server to an Active Directory domain, as this broadens the attack surface to all authenticated domain users. If feasible and without negatively impacting functionality, restricting domain user access to the Veeam server might reduce the risk. However, the core issue lies within the vulnerable software itself.
Hunting methods
The article does not provide specific hunting queries (Yara, Sigma, KQL, SPL). However, general hunting strategies based on the nature of the vulnerability could include:
- Monitoring network traffic for unusual activity related to the Veeam Backup & Replication server, particularly on the .NET Remoting channel. This might involve looking for unexpected patterns or volumes of communication.
- Analyzing Veeam Backup & Replication logs for errors or anomalies related to deserialization processes. However, successful exploitation might not leave easily detectable log entries.
- Endpoint detection and response (EDR) systems might detect suspicious processes or code execution originating from the Veeam server, especially if the RCE is used to launch further malicious activities. Hunting for such post-exploitation behavior would be relevant.
The logic behind these methods is to identify either the initial exploitation attempts (which might be challenging without specific signatures) or the subsequent actions taken by an attacker after successful RCE.
Albabat Ransomware Group Potentially Expands Targets to Multiple OS, Uses GitHub to Streamline Operations
Summary
Trend Research has identified new versions of the Albabat ransomware, indicating a potential expansion of its targeting from Windows to also include Linux and macOS devices. The research also uncovered the group’s utilization of GitHub to manage and streamline their ransomware operations. New versions, specifically 2.0.0 and 2.5, were observed, with version 2.0 targeting Windows and gathering system information on Linux and macOS. The ransomware retrieves its configuration data via the GitHub REST API using a “User-Agent” string “Awesome App”. Analysis of the configuration reveals details about the ransomware’s behavior, including ignored folders, encrypted file extensions, killed processes, and the storage location for collected data in a PostgreSQL database. Notably, version 2.5, currently under development, introduces cryptocurrency wallets for Bitcoin, Ethereum, Solana, and BNB in its configuration. The use of GitHub for configuration and potentially other components highlights an effort to streamline and potentially obfuscate their operations. Organizations are advised to remain vigilant against Albabat ransomware due to the potential for reputational damage, operational disruption, and financial losses. Mitigation strategies include strong access controls, regular system updates and patching, and proper backups.
Technical Details
The Albabat ransomware, a financially motivated threat, has shown recent activity with the emergence of new versions. While early versions were noted in late 2023 and early 2024, Trend Research encountered versions 2.0.0 and 2.5. A significant development is the potential expansion of targeted operating systems beyond Windows to include Linux and macOS, as evidenced by information gathering capabilities on these platforms in version 2.0 and the presence of platform-specific commands in the configuration.
The ransomware employs GitHub to host and deliver its configuration files. Specifically, the private repository billdev.github.io is used. The configuration is retrieved through the GitHub REST API via an HTTPS GET request to a config.json file. This communication uses a “User-Agent” string labelled “Awesome App” and requires an authentication token.
The downloaded configuration dictates various aspects of the ransomware’s operation. In version 2.0, analysis reveals a list of folders that the ransomware will ignore during encryption, including common system and application directories such as Searches, AppData, $RECYCLE.BIN, System Volume Information, windows.old, steamapps, perflogs, ansel, tmp, node_modules, cache, vendor, target, Mozilla, venv, env, Chrome, google-chrome, pypoetry, vimfiles, viminfo, site-packages, scoop, go, and temp.
The configuration also specifies a long list of file extensions that the ransomware will encrypt. This list includes various document, archive, media, database, executable, and other file types.
Furthermore, the ransomware is configured to kill a predefined set of processes, likely to ensure files are not locked and can be encrypted. These processes include task management tools (taskmgr.exe, processhacker.exe), registry editor (regedit.exe), development environments (code.exe, sublime_text.exe), Microsoft Office applications (excel.exe, powerpnt.exe, winword.exe, msaccess.exe, mspub.exe), web browsers (msedge.exe, chrome.exe), virtualization software (virtualboxvm.exe, virtualbox.exe), games and platforms (cs2.exe, steam.exe), database management tools (postgres.exe, mysqlworkbench.exe), email clients (outlook.exe), database servers (mysqld.exe), terminal applications (windowsterminal.exe, powershell.exe, cmd.exe), and image viewers (microsoft.photos.exe, photosapp.exe).
The collected information from infected machines, which includes system details, user information, geolocation data, encryption status, and ransom payment details, is stored in a PostgreSQL database hosted at postgres://postgres.*<username>*:*<password>*@aws-0-us-west-1.pooler.supabase[.]com:5432/postgres. This database is used to track infections and manage ransom demands.
Analysis of the configuration also reveals commands for gathering hardware and system information on Linux and macOS systems, further supporting the potential expansion of targeted operating systems.
The GitHub repository billdev1.github.io is associated with the ransomware operation. Although currently private, it was accessible via an authentication token. The repository was created on February 27, 2024, and the associated GitHub account is registered under the name “Bill Borguiann”, with the email address billdev@morke[.]org. The commit history indicates active development, with a significant increase in activity during August and September 2024, particularly between 00:00 to 04:00 UTC and 12:00 to 16:00 UTC. The most recent commit was on February 22, 2025.
A folder named 2.5.x within the private repository suggests the development of a newer ransomware version. The config.json file within this folder for version 2.5 reveals the addition of cryptocurrency wallets for Bitcoin, Ethereum, Solana, and BNB, although no transactions have been detected in these wallets yet.
Recommendations
The article provides several security best practices to mitigate the threat of Albabat ransomware:
- Implement strong access controls for sensitive data.
- Update and patch systems regularly to close exploitable vulnerabilities.
- Maintain up-to-date, secure backups of all critical data and regularly test restoration processes.
- Implement network segmentation to limit the potential spread of ransomware within the organization.
- Conduct regular user training and awareness sessions to help employees recognize phishing attempts and suspicious links.
- Organizations using Trend Vision One™ can leverage its AI-powered platform for centralized cyber risk exposure management, security operations, and layered protection.
- Trend Vision One customers can access Intelligence Reports and Threat Insights for proactive threat intelligence.
- Utilize the Trend Vision One Search App to hunt for malicious indicators mentioned in the report within their environment.
Hunting methods
Trend Vision One customers can utilize the following hunting query within the Search App to detect command-line execution for system information gathering:
eventSubId: 2 AND processCmd: /cmd.+wmic (cpu|csproduct|os|nic).+get (name|caption|displayName|MACAddress)/
Logic of the query: This query searches for command-line executions (processCmd) that contain /cmd (indicating the use of the command prompt) and invoke wmic (Windows Management Instrumentation Command-line) to query system information related to the CPU, computer system product, operating system, or network interface card. It specifically looks for commands using the get verb to retrieve properties like name, caption, displayName, or MACAddress, which are actions observed in the Albabat ransomware’s information gathering phase on Windows. The eventSubId: 2 likely refers to a specific event type within the Trend Vision One data model related to process execution.
The article also mentions that more hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled.
IOC
File Hashes (SHA1):
1cc2d1f2a991c19b7e633a92b1629641c019cdeb
c7c52fdaecf325dfaf6eda14e0603579feaed40a
8a3ea65147a156d381d8f1773e91eb8e0f6b1e40
8de54cad9d6316679580c91117b484acb493ab72
d67dc8c4232a3943a66608d62874923e9a3fb628
Domains:
api.github.com
billdev1.github.io
aws-0-us-west-1.pooler.supabase[.]com
Email Addresses:
billdev@morke[.]org
User-Agent String:
Awesome App
Cryptocurrency Wallet Addresses (Version 2.5 Configuration):
Bitcoin (btc): bc1qnv3kslqx564u6xk9xrulxeceu5zvhnp7q6mjrk
Ethereum (eth): 0x43d880e2966a062faf350a574cf3da0dc9c6c5f24
Solana (sol): 4UbaQHU3tZshBqNqBjFyFnQDbpvwNbAH2JXYv9NRjPMo
BNB (bnb): bnb14ud90wvhdnymyah360vnu0rnjht3x669z298hmw
Detection Names:
Ransom.Win64.ALBABAT.THBBEBE
Original link: https://www.trendmicro.com/en_us/research/25/c/albabat-ransomware-group.html
South Korean Organizations Targeted by Cobalt Strike ‘Cat’ Delivered by a Rust Beacon
Summary
Hunt researchers identified a cyber intrusion campaign targeting South Korean organizations, including government and commercial entities. The attackers used a publicly exposed web server to host their tools, which included a Rust-compiled Windows executable designed to deliver a modified version of the Cobalt Strike penetration testing tool, dubbed Cobalt Strike Cat (CS Cat). Alongside CS Cat, the server contained open-source tools like SQLMap, Web-SurvivalScan, and dirsearch, suggesting the attackers leveraged these for reconnaissance and exploitation of vulnerable web applications. The threat actor compiled a list of over 1,000 Korean domains, likely for targeting. The use of a Rust loader combined with a modified Cobalt Strike variant, previously seen on a Chinese-language hacking forum, provides insight into the actor’s delivery and post-exploitation strategies. Evidence of successful exploitation was found, including SQL injection activity and exfiltrated credentials. The attackers also utilized Marte beacon shellcode, delivered through Rust-compiled loaders.
Technical Details
The intrusion campaign utilized a publicly exposed web server running Python’s built-in SimpleHTTPServer. This server hosted various malicious tools and payloads accessible via an open directory. The presence of tools like SQLMap, Web-SurvivalScan, and dirsearch indicates a multi-stage attack process starting with reconnaissance and vulnerability scanning.
Reconnaissance:
- The attackers used dirsearch to brute-force directories and files on web servers, likely to discover hidden paths and resources.
- Web-SurvivalScan, a subdomain enumeration tool, was employed to identify active subdomains within the targeted environments. A file named targ.txt containing over 1,000 Korean domains associated with government, municipalities, and private businesses was found, likely used as input for Web-SurvivalScan.
- A Python script (urls.py) with Simplified Chinese comments was used to process the output of Web-SurvivalScan (found in res.txt), organizing identified subdomains into a structured CSV file. This automation likely streamlined further analysis and exploitation efforts.
Initial Access and Exploitation:
- The sqli subfolder contained output from SQLMap, documenting SQL injection attempts and successful exploitation against multiple South Korean websites. Files (1.txt to 4.txt) contained extracted database entries, and bbs_admin.csv held exfiltrated user credentials from a South Korean bulletin board system. This demonstrates the use of SQL injection as an initial access vector.
Payload Delivery and Post-Exploitation:
- The primary payload was Cobalt Strike Cat (CS Cat), a modified version of the Cobalt Strike penetration testing tool. The bash history on the server showed the operator extracting CS Cat project files from a password-protected zip archive named 123.zip, which aligns with previous findings of CS Cat being distributed on a Chinese-language hacking forum.
- A Rust-compiled Windows executable acted as a loader for the CS Cat beacon. Several Rust-compiled executables (88.txt, 882.txt, 888.txt) were identified as Cobalt Strike Cat beacon loaders. These used an intermediate execution layer, decoding and running Marte beacon shellcode extracted using the FLOSS tool.
- Other files, ma.exe and 0101.txt, were MinGW-compiled Cobalt Strike beacons. These beacons used a watermark of 100000000, indicative of cracked or leaked Cobalt Strike builds. Interestingly, these beacons exhibited unusual network behavior, with initial requests to a seemingly benign jQuery file resulting in an HTTP 301 redirect to the official CIA website, likely as an environment check or a diversion tactic. Follow-on requests led to an ‘unsupported browser’ page on the same domain.
- Attack logs in events.log revealed the attacker using Scripted Web Delivery (PowerShell) to stage a payload. Victim machines successfully established Cobalt Strike beacons, with payloads (123.exe and ma.exe) running under LOCAL SERVICE and Admin privileges. The attacker was seen logging into the command-and-control server with Google 2FA enabled, indicating an attempt at operational security despite the exposed directory. The C2 server configuration in CatServer.properties provided details about the malicious infrastructure.
Countries
South Korea.
Industries
Government agencies, local municipalities, and private businesses across multiple industries in South Korea were targeted.
Recommendations
- Monitor for unusual network traffic over uncommon ports.
- Monitor for irregular HTTP requests mimicking benign web traffic.
- Monitor for repeated connections to external infrastructure.
- Given the attacker’s use of SQL injection for initial access, organizations should enforce input validation.
- Apply security patches for web applications to address known vulnerabilities.
- Log database queries for signs of exploitation attempts.
Hunting methods
The article mentions that Hunt researchers used their AttackCapture™ system to scan and automatically download files from open directories. Files with specific extensions were submitted to Hatching Triage for analysis. The use of these automated analysis platforms aided in identifying the malware and its behavior.
No specific Yara, Sigma, KQL, SPL, or other explicit hunting queries are provided in the article. However, based on the TTPs, the following hunting logic can be applied:
- Network Traffic Analysis: Look for connections originating from internal networks to the identified IP addresses (144.48.4[.]219 and 104.167.222[.]106) on unusual ports or via suspicious protocols. Analyze HTTP traffic for unusual user-agent strings or patterns that might indicate Cobalt Strike beacons or the open-source tools used. Investigate any HTTP requests to
/jquery-3.3.1.min.jsfollowed by redirects tohttps[:]//www.cia[.]gov. - Endpoint Detection and Response (EDR): Search for the execution of files with the identified SHA256 hashes. Monitor for processes initiated by unusual parent processes, especially those involving PowerShell executing commands to download files from external IPs. Look for the execution of
sqlmap,dirsearch, or processes related to web vulnerability scanning. Investigate processes running with LOCAL SERVICE or administrative privileges that initiate network connections to external, untrusted IPs. - Web Server Logs: Examine web server logs for suspicious activity indicative of directory brute-forcing (multiple requests for non-existent files), SQL injection attempts (unusual characters or keywords in URL parameters), and access to the exposed directory at
144.48.4[.]219:8000.
IOC
IP Addresses:
144.48.4[.]219:8000
104.167.222[.]106
File Hashes (SHA256):
f635f424b967e3df6bec0e6bd4643d5b19bb6e3e3d9c925d91124b80f85e8d1b (ma.exe)
4b00b7ef72db51bd3c40366e283fc4eed7d613b410fdebaf451bf926fdd427fd (0101.txt)
97536e893cbd37b535911d36b284de01325f3a6cd7213e4e82536cef1d85c3aa (88.txt)
8212f3c18f5c875e5543e08389798edb8cdace8446211cedb0baee70e0e37d97 (882.txt)
bbb6542d8602dfe0b66073266a3606e6804f5b2c67d64266b0ef245220ccc3cc (888.txt)
36ca817200204eae59263031e64971e18a8f1d187c81e858d21e4567885e3040 (Marte Shellcode)
cb884be5f579e4e4917de5d9ae0a9cd3d9c80397b9a1519a8bb1fd5eeb6b882b (123.zip)
Original link: https://hunt.io/blog/rust-beacon-cobalt-strike-cat-south-korea