The Feed 2025-03-31

AI Generated Podcast
https://open.spotify.com/episode/2dlebPHR6x0KKhAJlzE7nR?si=oEAwup5uTh2YG9OGe7E5lQ
Summarized Stories
-
Fake Zoom Ends in BlackSuit Ransomware: This report analyzes a BlackSuit ransomware attack that began with a malicious download from a fake Zoom website, utilizing tools like Inno Setup, d3f@ck loader, and Cobalt Strike for various stages of the attack, including persistence, lateral movement, and data exfiltration.
-
Exposed Fortinet Fortigate firewall interface leads to LockBit Ransomware (CVE-2024–55591): This post includes a detection rule for potential defense evasion related to VPN SSL settings on Fortinet devices, possibly connected to the exploitation of CVE-2024–55591 leading to LockBit ransomware.
-
A Deep Dive into Water Gamayun’s Arsenal and Infrastructure: This article details the tactics, techniques, and procedures of the suspected Russian threat actor Water Gamayun, including their exploitation of a Microsoft Management Console vulnerability, custom payloads, malware arsenal like EncryptHub Stealer, DarkWisp, and SilentPrism, and command-and-control infrastructure.
-
Gamaredon campaign abuses LNK files to distribute Remcos backdoor: This article describes a Gamaredon campaign that uses war-themed LNK files to download ZIP archives containing a mix of clean and potentially abused applications, ultimately leading to the deployment of the Remcos backdoor.
-
From Contagious to ClickFake Interview: Lazarus leveraging the ClickFix tactic: This blog post examines a new campaign dubbed ClickFake Interview attributed to the Lazarus Group, which targets cryptocurrency job seekers with fake interview websites employing the ClickFix tactic to deploy the GolangGhost backdoor on Windows and macOS systems for remote control and data theft.
Fake Zoom Ends in BlackSuit Ransomware
Summmary
This report from The DFIR Report details a BlackSuit ransomware attack that originated from a fake Zoom installer downloaded from the domain zoommanager[.]com in May 2024. The initial infection chain involved the d3f@ckloader and IDAT loader to deploy the SectopRAT remote access trojan. After a dwell time of nine days, the threat actors used SectopRAT to deploy Cobalt Strike and Brute Ratel for further command and control and lateral movement. Lateral movement was achieved through various remote services and eventually RDP, facilitated by the QDoor proxy tool. The attackers used WinRAR for archiving and Bublup, a cloud SaaS application, for data exfiltration. Finally, the BlackSuit ransomware was deployed across Windows systems using PsExec. The Time to Ransomware (TTR) in this case was approximately 194 hours.
Technical Details
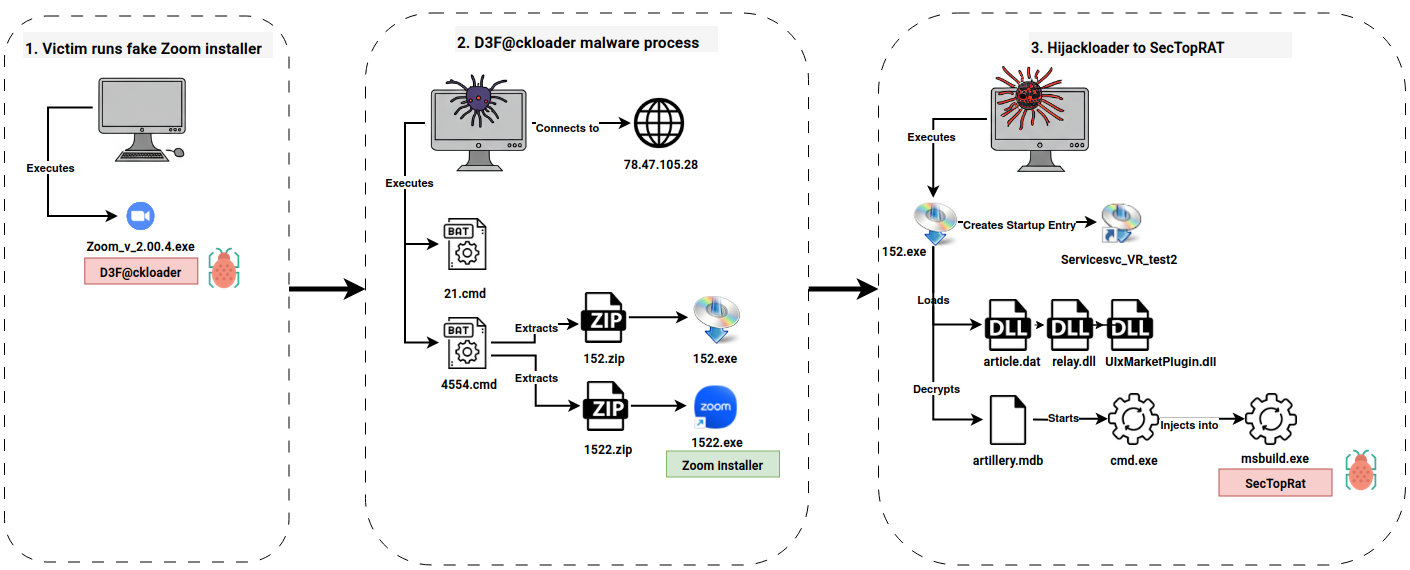 The attack began when a user visited a cloned Zoom webpage hosted on
The attack began when a user visited a cloned Zoom webpage hosted on zoommanager[.]com, likely through malvertising or access brokers. Downloading the seemingly legitimate Zoom installer (Zoom_v_2.00.4.exe) resulted in the execution of a malicious program created with Inno Setup. This installer acted as a downloader known as d3f@ckloader, built using the Pascal Scripting language. String analysis revealed embedded URLs pointing to various platforms like OneDrive, Telegram, and Steam, used to host subsequent stages of the malware.
Upon execution, d3f@ckloader launched a batch script (21.cmd) to perform defense evasion by setting the ‘hidden’ attribute to files in its directory and adding the root folder C:\ to Windows Defender’s exclusion list. The malware then connected to a Steam Community profile page (https://steamcommunity.com/profiles/76561199675758951) to retrieve the IP address 78.47.105[.]28 hosting the next-stage malware.
Using the Inno Download Plugin, two ZIP archive files (/manual/152/152.zip and /manual/1522.zip) were downloaded from this IP address. The associated User-Agent, InnoDownloadPlugin/1.5, is a distinctive characteristic. Another batch script (4554.cmd) extracted the contents of these archives. The first archive contained a benign Zoom installer (1522.exe) used as a decoy. The second archive contained the IDAT loader (152.exe), along with supporting DLL files (relay.dll, UIxMarketPlugin.dll) and an encrypted payload file (artillery.mdb).
Execution of 152.exe (IDAT loader) spawned a cmd.exe process, which then decrypted, loaded, and injected the SectopRAT payload into MSBuild.exe. The injected MSBuild.exe process then communicated with a Pastebin URL (https://pastebin.com/raw/cLika3dt) to receive its command and control (C2) configuration, resolving to the IP address 45.141.87[.]218. SectopRAT C2 traffic was observed on port 9000 and port 15647.
After eight days of inactivity, on the ninth day, SectopRAT spawned a new command shell and executed a Brute Ratel payload (2905.dll) using regsvr32.exe. Memory analysis confirmed the presence of Brute Ratel, often referred to as ‘Badger’. Another Brute Ratel Badger DLL (3004.dll) with a different C2 configuration was also dropped but not executed. The executed Brute Ratel Badger communicated with megupdate[.]com (resolving to 5.181.159[.]31) over port 443 using the URIs /procupdater.php and /callsysprocess.php.
The same process also facilitated the execution of a Cobalt Strike beacon (run32.exe) from the Windows temp directory. Memory scans confirmed this as a Cobalt Strike beacon. The Cobalt Strike beacon configuration revealed a C2 server provincial-gaiters-gw.aws-use1.cloud-ara[.]tyk.io with the URI /api/v2/login over port 443 and a fallback to 44.196.9.9:443. The HttpPostUri was /api/v2/status. Cobalt Strike was used for lateral movement using the psexec_psh jump, creating remote services with base64 encoded payloads.
For lateral movement and to facilitate RDP connections, the threat actor deployed a proxy tool known as QDoor as svhost.exe on a domain controller and a backup server using WMIC. QDoor was executed with a command-line argument to set the C2 server to 143.244.146[.]183 over port 443, which tunneled RDP traffic from their server 88.119.167[.]239 to internal hosts. The threat actor’s backend hostname DESKTOP-NT7KVK5 was leaked during RDP activity.
Using an RDP session through the QDoor proxy to a file share server, the threat actor downloaded WinRAR using the Edge browser from https://www.win-rar.com/fileadmin/winrar-versions/winrar/th/winrar-x64-701.exe. WinRAR was then used to archive targeted file shares. The archives were exfiltrated using the SaaS project management suite Bublup (mystuff.bublup.com), which uses Amazon S3 for backend storage. Approximately 934.38 MB of data was exfiltrated.
Prior to ransomware deployment, the threat actor connected to a domain controller via RDP and again downloaded WinRAR using Edge. They then downloaded a RAR archive (BAT_COMPS.rar) from the temporary file-sharing site temp.sh. The contents of this archive were extracted using WinRAR and included 123.exe (BlackSuit ransomware), PsExec.exe, and text files containing target host IPs (comps.txt), along with batch scripts COPY.bat and EXE.bat.
A network share (\\*\share$) was created to stage the ransomware deployment files. The COPY.bat script used PsExec to copy the ransomware executable (123.exe) to remote hosts listed in the comps*.txt files. The EXE.bat script then used PsExec to execute the ransomware on the remote hosts. The ransomware, BlackSuit, used vssadmin to delete shadow copies before encrypting local files and dropping a ransom note. Finally, the threat actor used WMIC to execute the ransomware locally on the staging domain controller.
During the reconnaissance phase, the threat actor executed commands such as hostname, nltest /domain_trusts /all_trusts, net group ""domain admins"" /domain, net group ""Domain Computers"" /domain, net group /domain, systeminfo, and whoami /groups. They also attempted credential access using Cobalt Strike’s pass-the-hash module and appeared to have used or attempted to use Rubeus for credential access, based on memory YARA hits within the Brute Ratel Badger process. WMIC was used to enumerate installed AV/EDR products.
Recommendations
The report implicitly highlights the importance of:
- User awareness training to recognize and avoid fake installer websites.
- Implementing robust endpoint detection and response (EDR) solutions to detect and block malicious activities at various stages.
- Maintaining up-to-date antivirus and anti-malware solutions.
- Monitoring network traffic for suspicious activity, including connections to known malicious IPs and unusual User-Agent strings like
InnoDownloadPlugin/1.5. - Implementing and monitoring for the execution of tools commonly used by threat actors, such as PsExec, WinRAR, and command-line utilities used for reconnaissance and privilege escalation.
- Regularly backing up critical data and ensuring the backups are stored offline and are not accessible to attackers.
- Implementing strong password policies and multi-factor authentication to prevent credential compromise.
- Patching systems and applications promptly to address known vulnerabilities.
- Monitoring for the creation of new services and unusual processes, especially those spawned by legitimate applications like
MSBuild.exe. - Detecting and alerting on data exfiltration attempts to cloud storage services.
Hunting methods
The report provides several indicators and methods for threat hunting:
- Network Intrusion Detection System (NIDS) signatures for the distinctive User-Agent
InnoDownloadPlugin/1.5associated with the Inno Download Plugin. The ruleETPRO ADWARE_PUP InnoDownloadPlugin User-Agent Observedwould trigger on this activity. - YARA rules identified memory patterns consistent with Brute Ratel C4 framework, Cobalt Strike beacon, and Rubeus. Specific external YARA rules that would have triggered are listed in the report.
- Sigma rules are provided to detect various stages of the attack, including startup folder file write, DNS query by
regsvr32.exe, new process creation viawmic.exe, potential recon activity vianltest.exe, suspicious group and account reconnaissance usingnet.exe, suspicious execution ofsysteminfo, share and session enumeration usingnet.exe, Cobalt Strike service installations, PsExec tool execution, and shadow copies deletion. - Suricata rule
ET POLICY Tunneled RDP msts Handshaketo detect tunneled RDP sessions over the QDoor proxy. - Zeek logs can be used to observe RPC calls related to the creation and execution of remote services used for lateral movement.
- Monitoring for specific commands used during reconnaissance (
nltest,net,systeminfo,whoami). - Monitoring for the execution of
attribwith the+sand+hflags to hide files and directories. - Detecting network connections originating from
MSBuild.exeto external IPs, specifically45.141.87[.]218on ports 9000 and 15647, indicative of SectopRAT C2. - Monitoring for the creation of startup entries, as created by Hijackloader.
- Detecting access to the LSASS process with
PROCESS_ALL_ACCESSpermissions from processes likedllhost.exe, which is indicative of credential dumping. - Monitoring for Logon Type 9 with Authentication Type
seclogo, associated with Cobalt Strike’s pass-the-hash technique. - Detecting the download of RAR archives from
temp.sh(b8a5dde0-fb1c-466e-832e-5a9b33e59b69). - Monitoring for the execution of
wmicto enumerate antivirus products (c79b4806-b86f-4c6e-a7b8-ecdb4b73fb70ande568650b-5dcd-4658-8f34-ded0b1e13992) and to create remote processes (6df37102-c993-4133-ad3d-b12ca32e03c6and526be59f-a573-4eea-b5f7-f0973207634d). - Detecting the creation of network shares (
5142 File Shareevent). - Monitoring for the execution of
vssadmin delete shadows /all /quiet. - Detecting the creation of services with PowerShell and base64 encoded commands, related to Cobalt Strike’s
psexec_psh. The ruleET RPC DCERPC SVCCTL - Remote Service Control Manager AccessandET POLICY PsExec service createdcan help identify this.
- Specific rule IDs can be found in the original article
Suricata Rule
alert tcp $HOME_NET any -> $EXTERNAL_NET any (msg: "[ConnectWise CRU] MALWARE QDoor Heartbeat Response"; flow:established, to_server; content: "|c4 c3 c2 c1 00 00 00 01 08|"; startswith; tag:session,5,packets; classtype:command-and-control; sid:9999990; rev:2; metadata: created_at 2024_09_17, updated_at 2024_09_20, mitre_tactic_id TA0011, mitre_tactic_name Command_and_Control;)
Logic:: Тhis Suricata rule is designed to detect QDoor malware by looking for a specific byte sequence (content: "|c4 c3 c2 c1 00 00 00 01 08|") in the TCP payload of established connections to external networks from the internal network. The byte sequence is likely part of a heartbeat message sent by the malware to its command-and-control server.
YARA Rule
rule QDoor_Backdoor
{
meta:
author = "ConnectWise Research Unit"
date = "2024-09-20"
malware = "QDoor"
description = "Detects QDoor backdoor malware using unique strings or specific conditional patterns."
version = "1"
md5 = "85144918f213e38993383f0745d7e41e"
strings:
$header_magic = {C4 C3 C2 C1}
$cmp1 = {0f b6 43 ?? 3c 01 75 11}
$cmp2 = {3c 07 0f 85 f7 00 00 00}
$string1 = "QClient"
$string2 = "Already exists connection with this channel id"
$string3 = "bot2world_.isNull()"
$string4 = "bot2server_.isNull()"
condition:
$header_magic and (($cmp1 and $cmp2) or (2 of ($string*)))
}
IOC
Hashes (SHA256)
c0230d748e61819d9dfad0da03fe6ec8
951154980d3ddd4101b8e09b11669cbedc86f979
3967b38f763b2e58b0679bc0178247b855c68d761187c71c2f1760b6882e473a
8477ef317b8974e18ed84ca69b9f6a08
328d5554025757e5ec8e2e9eee2ad97d0e986a59
b676dbc3e20fa7acb92c1cc0a90132798c482dbf43211793abb937bd43295d42
eae6cd02784743cde314afb8c533c5cd
a13061b229a225441f67d2b25ccda139ee21b14e
58dde623e36fefe8038aa2d579d3d1f5394b96ea3623b3125876137b4ee08d80
85144918f213e38993383f0745d7e41e
a6dcdfc8e97616c07549290950e78b145883e532
e6cfae572f777def856878e36bbacfaa82cb5662fc97c1492e2367a105dddbc9
ffb3755897b8d38ccc70b9c3baa38960
a25cfdcff675277035fb35add9d273934117e943
b594b8b91b6967e2fa6946753c8fd3f6ed3592c55c49a0ada7abd41752ae8a41
d1ba9412e78bfc98074c5d724a1a87d6
0572f98d78fb0b366b5a086c2a74cc68b771d368
cbcea8f28d8916219d1e8b0a8ca2db17e338eb812431bc4ad0cb36c06fd67f15
9bddb0e95a03fdcea4c62210f5818184
3eb042e449c6097f29fad255d21aac336fae534b
cb53118ec2d578febfd311bcda298c716f1f543b24f780f2721f45df0bda3dc3
4b22032954a12677675add0de20d7b94
5b1e0d72435da7d3a97107cddc655be71769ba53
a8a88bf91d1280ffa59536a6e50f24fe9c1ef79f68a300ef047d92eec7231d9e
9fb4770ced09aae3b437c1c6eb6d7334
fe54b31b0db8665aa5b22bed147e8295afc88a03
a05b592a971fe5011554013bcfe9a4aaf9cfc633bdd1fe3a8197f213d557b8d3
91f69fa3439f843b51c878688963e574
c5826e9e3c4b1fece4991f269fd4e5307e92bfe2
ecb0b3057163cd25c989a66683cfb47c19f122407cbbb49b1043e908c4f07ad1
27304b246c7d5b4e149124d5f93c5b01
e50d9e3bd91908e13a26b3e23edeaf577fb3a095
3337e3875b05e0bfba69ab926532e3f179e8cfbf162ebb60ce58a0281437a7ef
f91fbe09b593fb1104b30e3343afb392
41360d3eae3a71dd60c9ac34788d6863ef4e3e30
63dcff4bad9576794c3a412cf8dae83b807a138cc09c4de64485bb8ec991cd4b
5b8ebe43ded7ba460e4827206329375a
df774b96aa6f7ba914e7d6c1e3c448170e2e419e
e0f31fe28223b5bd22ce01c6bc1d3a4d3e030b9dc3c98440d11d72e67fdaa453
80110fbb81d0407340b908bb43c815d3
8d4f2aa315ce17505b8698db22ec2526805645a4
b837bec967df6748b72c3b43c254532620977d0bbe0fc23e0c178c74516baab9
d98fb34b4fa0f83d02e3272f1cb9c5fc
6c75e2c704f69aaa09cdfd455c7bdbf9336dc7fe
f34aad9a56ca9310f40ecbcb075e4be12aaf9ef60fd24893b5e8fb28934cd730
0cc25cf9f5d4f02c1a2ed014e2d4acb0d383f01c9bb1852a10b933eec17c1f20
5d2e7ed8f77bc95302e693312f9a154f0afb698a05796561e277c037deb15a9d
6d208e99cfac9b2a32df042889636db6217cd12de1980aca7d9678160bf58d4d
87db51984bfcadf9ee96183f0fe0fb5129b4cfe5a23a68c272b94299267779ea
aee7d7e05e063892f1291a77a8940a9c346c05a68588de89c2a6563ae82ae770
e491642e9c60e1e83e4c5224dac313936ac136f8821bf3f886c5129ec6b2ad87
fd2695460011f5c1a584bb8da6ac09bad30ed2c909ed2b790b3ab7e10bb53635
019f97d81d00e411d1ae48b926429947826e66e952e2218b92c7b36a3912f4a7
Domains
zoommanager[.]com
steamcommunity.com
pastebin.com
megupdate[.]com
administrative-manufacturer-gw.aws-usw2.cloud-ara.tyk[.]io
provincial-gaiters-gw.aws-use1.cloud-ara[.]tyk.io
temp.sh
mystuff.bublup.com
www.win-rar.com
www.bing.com
IP Addresses
78.47.105[.]28
45.141.87[.]218
5.181.159[.]31
88.119.167[.]239
143.244.146[.]183
44.196.9.9
Original link: https://thedfirreport.com/2025/03/31/fake-zoom-ends-in-blacksuit-ransomware/
Exposed Fortinet Fortigate firewall interface leads to LockBit Ransomware (CVE-2024–55591)
Summary
This article details an incident response investigation following a LockBit 3.0 ransomware attack. The attack began with the exploitation of CVE-2024–55591 on an internet-exposed Fortinet Fortigate firewall, allowing an initial attacker to gain super-administrator access. This initial access broker then established multiple VPN-enabled administrator accounts and configured unrestricted firewall rules. Subsequently, a second threat actor, likely a buyer of the initial access, leveraged the established VPN access to infiltrate the internal network. Due to weak network segmentation and password policies, the second attacker moved laterally, compromised critical systems including domain controllers and backup servers, stole credentials, gained cloud access, and ultimately deployed ransomware after disabling the victim’s endpoint detection and response (EDR) system and destroying backups. The lack of a robust monitoring solution and weak log retention significantly hampered the incident response efforts. The attackers did not exfiltrate a significant amount of data before encryption. The article also provides Sigma rules to detect some of the attacker’s initial activities on the Fortinet firewall.
Technical Details
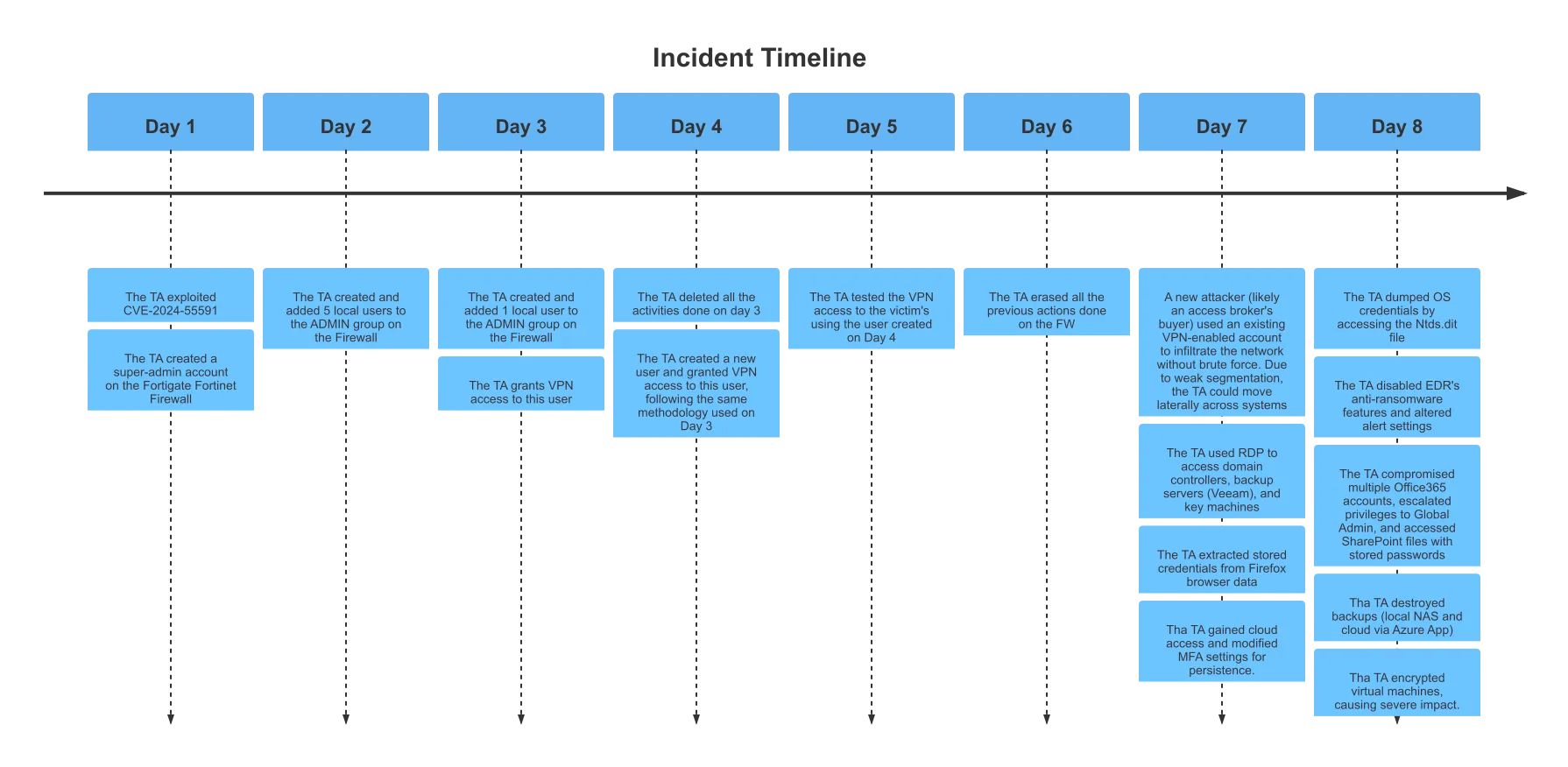
The attack unfolded in two distinct phases. The initial phase (Days 1-6) involved the exploitation of CVE-2024–55591 against an internet-exposed Fortinet Fortigate firewall. On Day 1, the threat actor exploited this authentication bypass vulnerability in the Node.js web socket module to create a new super-administrator account. This demonstrates an Exploit Public-Facing Application Tactic (TA0001) using a Valid Account sub-technique (T1078) with Cloud Accounts, Local Accounts. The specific technique involved crafting requests to the vulnerable web socket module to gain administrative privileges.
On Days 2-4, the initial threat actor focused on establishing persistent remote access. They created multiple local user accounts with VPN access and added them to the ADMIN group. These accounts followed a pattern of 6-character random strings. Additionally, they configured firewall rules to allow unrestricted access from the created VPN users to all internal network subnets across all services and ports. This involved adding new firewall address objects (object_172_all_iZ, object_10_all_iZ, object_192_all_iZ) defining internal network ranges, enabling the VPN SSL web portal with tunnel mode enabled and associating it with the newly created address objects, and adding a permissive firewall policy allowing traffic from the ssl.root interface and SSLVPN_TUNNEL_ADDR1_ to any internal destination (10_all_iZ, 172_all_iZ, 192_all_iZ) on all services. This highlights Account Manipulation (TA0003) through Local Account creation (T1136.001) and Remote Services abuse (TA0002) via VPN configuration (T1133). The subsequent deletion and recreation of these accounts and firewall rules on Days 3, 4, and 6 indicates an attempt at Defense Evasion (TA0005) by Indicator Removal (T1070) through log manipulation. On Day 5, a 2-minute VPN connection test was performed, confirming the established remote access.
The second phase (Days 7-8) involved a new threat actor who leveraged the existing VPN access established in the first phase. On Day 7, this attacker connected via VPN using an account already present on the firewall, bypassing the need for brute-force attacks. This demonstrates the continued abuse of Remote Services (TA0002) using a Valid Account (T1078). Due to weak network segmentation (all targets in the same subnet) and likely weak password policies, the attacker could move laterally across systems using Remote Desktop Protocol (RDP) (T1021.001). They accessed domain controllers, backup servers (Veeam), and key machines. The attacker then engaged in Credential Access (TA0006) by extracting stored credentials from Firefox browser data and dumping operating system credentials from the NTDS.dit file (T1003.001) on the domain controller. Accessing the NTDS.dit file likely involved leveraging Volume Shadow Copy Service (VSS) as the file was saved in a temporary directory under a VSS path. The attacker also gained access to a cloud account, modified Multi-Factor Authentication (MFA) settings for persistence (T1098.005), and manipulated password reset information.
On Day 8, the attacker continued their activities by disabling the Endpoint Detection and Response (EDR) system’s anti-ransomware features and manipulating alert settings via its web management console, demonstrating Impair Defenses (TA0005) through Disable or Modify Tools (T1562.001). They also compromised multiple Office365 accounts, escalated privileges to Global Administrator, and gained unauthorized access to SharePoint files containing stored passwords. This further highlights Credential Access (TA0006) from web browsers and potentially files. Subsequently, the attacker destroyed backups stored on local NAS devices and cloud platforms (Azure App). Finally, the attacker encrypted virtual machines (T1486), causing significant operational impact and data loss. The lack of command and control (C2) activity observed by InTheCyber suggests the attacker relied solely on the established VPN access and RDP for lateral movement and actions on objectives.
The source IPs observed during the initial exploitation and VPN access phases are 45.55.158.47, 37.19.196.65, and 154.18.187.108.
Recommendations
The article implicitly recommends several security measures:
- Implement a robust monitoring solution.
- Enforce strong log retention policies on critical systems.
- Patch internet-facing systems promptly, specifically addressing vulnerabilities like CVE-2024–55591. The reference link in the Sigma rules points to Fortiguard advisory FG-IR-24-535.
- Implement strong network segmentation to limit lateral movement.
- Enforce strong password policies.
- Secure administrative accounts and limit their exposure.
- Regularly audit and monitor firewall rules and VPN configurations.
- Implement and regularly test backup and recovery procedures, ensuring backups are stored securely and are not accessible from compromised systems or accounts.
- Implement multi-factor authentication (MFA) and monitor for unauthorized changes.
- Regularly review and secure cloud configurations, including MFA settings and application permissions.
Hunting methods
The article provides several Sigma rules to detect potentially malicious activity on Fortinet Fortigate firewalls based on the observed attack:
1. Potential Persistence via New Admin User Creation:
title: Potential Persistence via New Admin User Creation
id: cd0a4943-0edd-42cf-b50c-06f77a10d4c1
status: experimental
description: Detects the creation of an administrator on Fortinet Fortigate Firewall.
references:
- https://www.fortiguard.com/psirt/FG-IR-24-535
author: Marco Pedrinazzi @pedrinazziM (InTheCyber)
date: 2025-02-14
tags:
- attack.persistence
- attack.t1136.001
logsource:
product: fortinet
service: event
detection:
selection:
action: 'Add'
cfgpath: 'system.admin'
condition: selection
falsepositives:
- An administrator account can be created for legitimate purposes
level: medium
Logic: This rule looks for Fortinet event logs where the action is ‘Add’ and the configuration path (cfgpath) is system.admin. This indicates the creation of a new administrator account, which can be used for persistence.
2. Potential Persistence via New Local User Creation:
title: Potential Persistence via New Local User Creation
id: ddbbe845-1d74-43a8-8231-2156d180234d
status: experimental
description: |
Detects the creation of a new local user on Fortinet Fortigate Firewall. The new local user could be used for VPN connections.
references:
- https://www.fortiguard.com/psirt/FG-IR-24-535
author: Marco Pedrinazzi @pedrinazziM (InTheCyber)
date: 2025-02-14
tags:
- attack.persistence
- attack.t1136.001
logsource:
product: fortinet
service: event
detection:
selection:
action: 'Add'
cfgpath: 'user.local'
condition: selection
falsepositives:
- A local user can be created for legitimate purposes
level: medium
Logic: This rule monitors for the creation of new local users on the Fortinet firewall by looking for ‘Add’ actions with the configuration path user.local. Threat actors might create local users for unauthorized VPN access.
3. Potential Remote Services Abuse via Modification of VPN SSL Settings:
title: Potential Remote Services Abuse via Modification of VPN SSL Settings
id: 8b5dacf2-aeb7-459d-b133-678eb696d410
status: experimental
description: |
Detects the modification of VPN SSL Settings (for example, the modification of authentication rules). This behavior was observed in pair with Potential Remote Services Abuse via Addition of VPN SSL Web Portal - Fortinet Fortigate Firewall (sigma rule)
references:
- https://www.fortiguard.com/psirt/FG-IR-24-535
author: Marco Pedrinazzi @pedrinazziM (InTheCyber)
date: 2025-02-14
tags:
- attack.persistence
- attack.initial-access
- attack.t1133
logsource:
product: fortinet
service: event
detection:
selection:
action: 'Edit'
cfgpath: 'vpn.ssl.settings'
condition: selection
falsepositives:
- VPN SSL settings can be changed for legitimate purposes
level: medium
Logic: This rule detects modifications to the VPN SSL settings on the Fortinet firewall by looking for ‘Edit’ actions on the vpn.ssl.settings configuration path. Attackers might modify these settings to facilitate unauthorized access.
4. Potential Defense Evasion via Addition of Firewall Address Object:
title: Potential Defense Evasion via Addition of Firewall Address Object
id: 5c8d7b41-3812-432f-a0bb-4cfb7c31827e
status: experimental
description: Detects the addition of firewall address objects on Fortinet Fortigate Firewall.
references:
- https://www.fortiguard.com/psirt/FG-IR-24-535
author: Marco Pedrinazzi @pedrinazziM (InTheCyber)
date: 2025-02-14
tags:
- attack.defense-evasion
- attack.t1562
logsource:
product: fortinet
service: event
detection:
selection:
action: 'Add'
cfgpath: 'firewall.address'
condition: selection
falsepositives:
- An address could be added or deleted for legitimate purposes
level: medium
Logic: This rule identifies the addition of new firewall address objects by monitoring for ‘Add’ actions on the firewall.address configuration path. Attackers might add address objects to create exceptions in firewall rules for their traffic.
5. Potential Remote Services Abuse via Addition of VPN SSL Web Portal:
title: Potential Remote Services Abuse via Addition of VPN SSL Web Portal
id: 2bfb6216-0c31-4d20-8501-2629b29a3fa2
status: experimental
description: |
Detects the addition of a VPN SSL Web Portal on Fortinet Fortigate Firewall. This behavior was observed in pair with the Potential Remote Services Abuse via Modification of VPN SSL Settings - Fortinet Fortigate Firewall (sigma rule)
references:
- https://www.fortiguard.com/psirt/FG-IR-24-535
author: Marco Pedrinazzi @pedrinazziM (InTheCyber)
date: 2025-02-14
tags:
- attack.persistence
- attack.initial-access
- attack.t1133
logsource:
product: fortinet
service: event
detection:
selection:
action: 'Add'
cfgpath: 'vpn.ssl.web.portal'
condition: selection
falsepositives:
- A VPN SSL Web Portal can be added for legitimate purposes
level: medium
Logic: This rule detects the creation of a new VPN SSL web portal by looking for ‘Add’ actions on the vpn.ssl.web.portal configuration path. Attackers might create these portals for unauthorized access.
6. Potential Defense Evasion via Firewall Policy Addition:
title: Potential Defense Evasion via Firewall Policy Addition
id: f24ab7a8-f09a-4319-82c1-915586aa642b
status: experimental
description: Detects the addition of a new firewall policy on Fortinet Fortigate Firewall.
references:
- https://www.fortiguard.com/psirt/FG-IR-24-535
author: Marco Pedrinazzi @pedrinazziM (InTheCyber)
date: 2025-02-14
tags:
- attack.defense-evasion
- attack.t1562
logsource:
product: fortinet
service: event
detection:
selection:
action: 'Add'
cfgpath: 'firewall.policy'
condition: selection
falsepositives:
- A firewall policy can be added for legitimate purposes
level: medium
Logic: This rule monitors for the addition of new firewall policies by looking for ‘Add’ actions on the firewall.policy configuration path. Attackers might add permissive firewall policies to allow their malicious traffic.
7. Potential Persistence via User Group Modification:
title: Potential Persistence via User Group Modification
id: 69ffc84e-8b1a-4024-8351-e018f66b8275
status: experimental
description: Detects the modification of a user group on Fortinet Fortigate Firewall. The group could be used to grant VPN access to a network.
references:
- https://www.fortiguard.com/psirt/FG-IR-24-535
author: Marco Pedrinazzi @pedrinazziM (InTheCyber)
date: 2025-02-14
tags:
- attack.persistence
- attack.t1098.007
logsource:
product: fortinet
service: event
detection:
selection:
action: 'Edit'
cfgpath: 'user.group'
condition: selection
falsepositives:
- A group can be modified for legitimate purposes
level: medium
Logic: This rule detects modifications to user groups on the Fortinet firewall by looking for ‘Edit’ actions on the user.group configuration path. Attackers might modify groups to grant unauthorized users VPN access.
IOC
IP Addresses
45.55.158.47
37.19.196.65
154.18.187.108
Original link: https://posts.inthecyber.com/exposed-fortinet-fortigate-firewall-interface-leads-to-lockbit-ransomware-cve-2024-55591-de8fcfb6c45c
A Deep Dive into Water Gamayun’s Arsenal and Infrastructure
Summmary
Trend Research has provided an analysis of the suspected Russian threat actor Water Gamayun, also known as EncryptHub and Larva-208, and their campaign exploiting a zero-day vulnerability in the Microsoft Management Console framework (CVE-2025-26633), dubbed MSC EvilTwin. The report details Water Gamayun’s delivery methods, custom payloads, and techniques used to compromise systems and exfiltrate data, highlighting the potential for severe business impact through data theft and operational disruption. The threat actor utilizes various methods to deploy malware, including malicious provisioning packages (.ppkg), signed Microsoft Installer files (.msi), and Windows MSC files, and employs living-off-the-land binaries (LOLBins) such as the IntelliJ runnerw.exe to execute PowerShell commands. Their arsenal includes custom payloads like the EncryptHub Stealer variants and backdoors such as SilentPrism and the newly identified DarkWisp, which are used for persistence, command execution, and data exfiltration via encrypted channels to command-and-control (C&C) servers. The research provides insights into the evolution of the EncryptHub Stealer, tracing its origins to a fake WinRAR website and subsequent GitHub repository. The report also analyzes the C&C infrastructure, including active domains and server-side components, revealing the threat actor’s methods for managing compromised systems and collecting stolen data. Trend Micro’s analysis emphasizes the importance of proactive security measures, up-to-date patch management, and advanced threat detection technologies to protect against Water Gamayun’s evolving tactics.
Technical Details
Water Gamayun leverages the MSC EvilTwin zero-day vulnerability (CVE-2025-26633) for initial access and code execution. Their delivery mechanisms primarily involve malicious provisioning packages (.ppkg), signed Microsoft Installer files (.msi), and Windows MSC files. A notable technique involves the use of the IntelliJ process launcher runnerw.exe (renamed to invoker.exe in some instances) as a LOLBin to proxy the execution of PowerShell commands on infected systems. This allows for the bypassing of standard execution policies and stealthy execution of malicious scripts.
The threat actor employs various custom payloads for different stages of their attacks. The MSC EvilTwin loader exploits the CVE-2025-26633 vulnerability by creating decoy and malicious .msc files in seemingly legitimate system paths (C:\Windows \System32\ and C:\Windows \System32\en-US\ ). The malicious .msc file contains a placeholder *{htmlLoaderUrl}* which is dynamically replaced with a URL hosting PowerShell commands (https://82[.]115[.]223[.]182/encrypthub/ram/). Upon execution via Start-Process, this downloads and runs a PowerShell script, followed by a 30-second delay and cleanup of the created directories and files to minimize forensic traces.
For persistence and remote control, Water Gamayun utilizes backdoors. SilentPrism is a backdoor designed for persistence and dynamic execution of shell commands. It employs different persistence mechanisms based on user privileges: registry auto-run entries using mshta.exe and VBScript for non-administrative users, and scheduled tasks with similar execution methods for administrative users. SilentPrism communicates with its C&C server using encrypted channels (AES encryption and Base64 encoding) over HTTP, dynamically executes received commands via PowerShell (including direct execution, script block creation with Invoke-Expression, or job-based execution with Start-Job), and implements anti-analysis techniques like VM detection and randomized sleep intervals (300-700ms).
A newer backdoor, DarkWisp, is a PowerShell-based reconnaissance and remote access utility. It gathers extensive system information, including admin rights, domain membership, cryptocurrency wallet presence, VPN software, public IP, location, OS version, antivirus, and firewall status, and transmits this data to the C&C server. DarkWisp uses a dual-channel C&C communication strategy: TCP port 8080 for initial reconnaissance data, a PING mechanism for maintaining connection, and receiving Base64-encoded commands; and HTTPS port 8081 as a redundant channel for exfiltrating Base64-encoded command execution results via the /receive_result endpoint. The C&C server, managed by the handle.py Python script, can send Base64-encoded commands to clients, which are then decoded and executed using Invoke-Expression.
Water Gamayun employs several information stealers. The EncryptHub Stealer has multiple variants (A, B, and C), all modified versions of the open-source Kematian-Stealer. These stealers collect a wide range of sensitive data, including system information, Wi-Fi passwords, Windows product keys, clipboard history, session data from messaging, VPN, VNC, and FTP clients, password manager data, and files matching specific keywords and extensions. Variant A, distributed via malicious MSI packages and binary droppers, exfiltrates data over HTTP to the C&C server, unlike the original Kematian Stealer which used Discord. Variant B, found on the 82[.]115[.]223[.]182 C&C server, includes obfuscation (Base64 encoding of filenames and build type), data exfiltration over HTTPS port 8081, and Telegram notifications for the attacker. Variant C removes Telegram notifications and instead directly exfiltrates stolen data statistics via HTTPS to hxxps[:]//malwarehunterteam[.]net, while file exfiltration remains similar to Variant B.
The threat actor also utilizes known malware binaries such as Stealc and Rhadamanthys stealer. The runner.ps1 script associated with the MSC EvilTwin loader is used to download and deploy the Rhadamanthys stealer.
The C&C infrastructure is actively managed, with servers being deployed for short periods before being replaced. The domain 82[.]115[.]223[.]182 hosts various malicious payloads, collected data, and the server-side C&C infrastructure, including the handle.py script. The handle.py script manages client connections, receives commands, sends PING requests, and facilitates Telegram notifications upon successful client registration. The C&C server also provides endpoints to list infected machines (/list_all_clients, /list_clients_by_build) and stores exfiltrated data in specific directories. Hidden JavaScript code within seemingly blank HTML pages is used to download additional malicious files, including backdoors (DarkWisp), stealers (Stealc, Rhadamanthys), and remote access tools like AnyDesk.
Recommendations
Organizations can protect themselves from threats like Water Gamayun through:
- Up-to-date patch management.
- Advanced threat detection technologies.
- Staying informed about evolving threats and adopting proactive defense strategies.
- Utilizing comprehensive cybersecurity platforms like Trend Vision One™ that centralize cyber risk exposure management, security operations, and layered protection.
- Leveraging threat intelligence reports and threat insights to stay ahead of cyber threats.
- Using IOC sweeping tools to identify potential compromises.
- Implementing network security measures, such as TippingPoint Intrusion Prevention Filters, to detect and block malicious activity.
Hunting methods
Trend Vision One customers can use the following hunting queries:
- Water Gamayun Malware Arsenal:
malName: (*RHADAMANTHYS* OR *FICKLESHADE* OR *SILENTPRISM* OR *DARKWISP*) AND eventName: MALWARE_DETECTION AND LogType: detectionLogic: This query looks for malware detection events where the detected malware name contains keywords associated with Water Gamayun’s known arsenal.
- EncryptHub Stealer Module execution:
eventId:1 AND processFilePath:*powershell.exe AND processCmd:*encrypthub_steal.ps1Logic: This query searches for process creation events (eventId:1) where
powershell.exeis the executed process and the command line (processCmd) includesencrypthub_steal.ps1, indicating the potential execution of an EncryptHub Stealer variant.
More hunting queries are available for Trend Vision One customers with Threat Insights Entitlement enabled. Trend Vision One customers can also use the Search App to match or hunt the malicious indicators mentioned in the blog post with data in their environment.
IOC
Hashes (MD5)
abaa46bc704842d6cc6f494c21546ae6
87792cf4bd370f483a293a23c4247c50
e59a025f9310d266190b91f5330fde8d
f0df469c3459a6a3b98b7b69b07bf61b
239e8a3ee1fafe452d0b59eadb32247b
99a80820ae6dc60c9e9307e6ed8ef211
42b55615cbaa014f246097bd904d7ff2
2f8bf3e5b6cbdb0c8e5935b078711867
1fbe357c26133a4b39b96fdd2c48f1ae
3371da6397159dbced2794c12aeb80c6
1c34b88280d660051b69ccb40660e71f
Hashes (SHA-1)
87c46845f57dc9ca8136b730c08b5b5916ca0ad3
a225bee48074feac53c7cb2f3929a41f7b4a71d3
ffb72adff6e099a9deb418c5d40abd8cf9b12c42
b38a0478aefa9d9d77282dd82ada51d7a47fe6f5
1377a69ae519d1cf000fa51869454e31ba92056d
2e4ae2af76c6239eb4191853221b4a40139cc122
f16e0dac597de903a4c6842184770ba5618275a0
Ca4fea2deacb9665461eb74b6422b137326c0d76
57ab6bdbb41289f3c8983d5b48fc98c08782ed1f
291ed2eb864c95ba5495ca415efd1b071362ec7b
d63a8c0a00fb1c68450da7cc19a08a6ed96791dc
Hashes (SHA-256)
cbb84155467087c4da2ec411463e4af379582bb742ce7009156756482868859c
725df91a9db2e077203d78b8bef95b8cf093e7d0ee2e7a4f55a30fe200c3bf8f
db3fe436f4eeb9c20dc206af3dfdff8454460ad80ef4bab03291528e3e0754ad
983506186590f7118cb507d29f12f163afb536a03e6d0f4fb441df8afe49ede1
0ac748baaad6017e331a8d99aae9e5449a96ba76fb7374f5d8c678ae52b7db9f
f381a3877028f29ec7865b505b5c85ce77d4947d387d3f30071159fa991f009a
d150d8d8bfa651c0e08a10323ecb0bccf346a35bd1bad19f89a5338acd8a88b3
B29e630b9c70b0daaba4f83489494444c04c7a470b9c24eb4ddffb6cd7cf05ff
677601f72181c53541f850248dd0904153ea62458489d7aa782149b93399ebd8
899d0b75e7eb3250246f709ad8aa32a8634f536153a3d2eaa3b5a9d9c2690168
49a552d3adbcad9f5ac70151b48a4edc2ae1d4094a1ea9d944785cee8b4319d7
91aa7642a301ad6f46a6e466d89b601270aac64b7b6a5661436f7f9b5d804e89
bad43a1c8ba1dacf3daf82bc30a0673f9bc2675ea6cdedd34624ffc933b959f4
724aa4d5e3fb96be0a4a01a74324e7123d3281d7e3dce0f79ae717c5a7383ef1
079b7f03c727de92c3fcb7d3b9b9fea6d1e9ffdcd60dc9a360af90ce7b4b5cc6
5752efa219c7e42cb104917f38c146e1f747d14230be0e64a5e87c20e82075bb
2a5f9198f1e563688a2081b746bdaf48d897ec0ae96dfafc15cd5cd52c25e8f2
Domains
encrypthub.(net/org)
82[.]115[.]223[.]182
hxxps[:]//encrypthub.org/main/zakrep/worker.ps1
https://82[.]115[.]223[.]182/encrypthub/ram/
hxxps[:]//malwarehunterteam[.]net
api.telegram.org
IP Addresses
82[.]115[.]223[.]182
URLs
https://www.win-rar[.]com/zx.ps1
bazaar.abuse.ch/sample/3761060....
https://github[.]com/sap3r-encrypthub/encrypthub
Unknown panel for me at: https://www.win-rar[.]com/panel/panel/login.php
https://encrypthub.org/main/zakrep/worker.ps1
https://82[.]115[.]223[.]182/encrypthub/ram/
https://82[.]115[.]223[.]182/payload/hvnc/anydesk.ps1
https://82[.]115[.]223[.]182/payload/hvnc/nthread.dll
https://82[.]115[.]223[.]182:8080/8081
https://82[.]115[.]223[.]182:8081/receive_result?result=$Base64Result
https://82[.]115[.]223[.]182/payload
https://82[.]115[.]223[.]182/encrypthub/ram/runner.ps1
hxxps[:]//encrypthub.org/main/steal/taskmaker.ps1
https://82[.]115[.]223[.]182:8081/upload_file?filename=$base64Filename&buildType=$base64BuildType
https://82[.]115[.]223[.]182/server/uploads/$build/$(Split-Path $tarFilePath -Leaf)
https://api.ipify.org
http://ipinfo.io/$IpAddress/json
https://82[.]115[.]223[.]182:8080
https://82[.]115[.]223[.]182:8081/receive_result
https://api.telegram.org/bot[API_KEY]/sendMessage
hxxps[:]//malwarehunterteam[.]net/server/send_notification?machine=$encodedParams
https://82[.]115[.]223[.]182/login.php
https://82[.]115[.]223[.]182/payload/
https://82[.]115[.]223[.]182/server/
https://82[.]115[.]223[.]182/server/uploads/encrypthub/
Original link: https://www.trendmicro.com/en_us/research/25/c/deep-dive-into-water-gamayun.html
Gamaredon Campaign Abuses LNK Files to Distribute Remcos Backdoor
Summary
A cyber espionage campaign, attributed with medium confidence to the Gamaredon threat actor group (also known as Primitive Bear, Armageddon, Shuckworm, etc.), has been actively targeting users in Ukraine since at least November 2024. The campaign utilizes malicious LNK files, often disguised as Office documents with names related to the movement of troops in Ukraine, to initiate the infection chain. These LNK files contain PowerShell code that acts as a downloader. The PowerShell downloader retrieves a second-stage ZIP file containing the Remcos backdoor from geo-fenced servers located in Russia and Germany. The Remcos payload is then executed using DLL side-loading techniques. The Gamaredon group, active since 2013, is known for espionage, data theft, and establishing long-term access, primarily targeting Ukrainian entities, including government organizations and critical infrastructure. This campaign continues the group’s trend of using the invasion of Ukraine as a theme in their phishing attacks. The threat actor likely distributes the malicious ZIP archives via phishing emails, either as direct attachments or through links to remote download hosts. Cisco Talos assesses this activity to be associated with Gamaredon based on observed tactics, techniques, and procedures, including the use of specific machines for creating LNK files previously seen in Gamaredon incidents. The campaign also employs a decoy file to mask the compromise after infection.
Technical Details
The attack begins with the delivery of LNK files, often compressed within ZIP archives and disguised as legitimate documents using file names related to the conflict in Ukraine and sometimes including names of individuals. These LNK files contain embedded PowerShell code. Upon execution, the PowerShell script downloads a ZIP archive containing the next-stage payload from command and control (C2) servers located in Russia and Germany. The PowerShell code employs the Get-Command cmdlet to indirectly execute download and execution functions, potentially as an evasion technique against string-based antivirus detection. The downloaded ZIP archive is extracted to the %TEMP% folder. The archive contains a legitimate, clean application and a malicious DLL file. The clean application is then used to load the malicious DLL using the DLL side-loading technique. Observed clean applications abused for DLL side-loading include DPMHelper.exe, DZIPR.exe, IDRBackup.exe, IUService.exe, madHcCtrl.exe, palemoon.exe, Compil32.exe, IsCabView.exe, TiVoDiag.exe, WiseTurbo.exe, Mp3tag.exe, AcroBroker.exe, SbieSvc.exe, steamerrorreporter64.exe, and vmhost.exe. An analysis of a specific sample revealed the use of TiVoDiag.exe to load the malicious mindclient.dll. This malicious DLL acts as a loader, decrypting and executing the final Remcos payload from encrypted files within the ZIP archive. The final Remcos payload is a typical backdoor that gets injected into Explorer.exe. It establishes communication with the C2 server at 146.185.233.96 on port 6856. While the communication with the servers is direct via IP addresses, some reverse DNS records for these IPs show unique and invalid entries, such as domains ending with “.poopyies” and others with seemingly random character combinations followed by “.2901”. This DNS artifact helped uncover additional IP addresses associated with the campaign. The servers involved are primarily hosted by GTHost and HyperHosting ISPs. While these servers distribute the payload and decoy document, at least one server was identified as a C2 server for the Remcos backdoor. Access to the payload servers appears to be geo-fenced, with the files being accessible from Ukraine while returning HTTP error 403 for requests originating from other locations. This suggests the threat actors restrict access to their payload delivery infrastructure. The metadata of the malicious LNK files indicates that they were created using only two machines, a characteristic previously observed in Gamaredon campaigns.
Countries
Ukraine
Industries
Specifically government organizations, critical infrastructure, and entities affiliated with Ukraine’s defense, security, and law enforcement apparatus. Secondary operations include broad targeting of entities in Europe and globally, including government, military, humanitarian, and non-profit organizations.
Recommendations
Organizations should implement robust email security measures to prevent phishing emails containing malicious attachments or links from reaching users. Endpoint detection and response (EDR) solutions should be deployed and configured to detect and block the execution of suspicious LNK files and PowerShell scripts. Network security controls, such as firewalls and intrusion prevention systems, should be in place to identify and block communication with known malicious IP addresses and domains. Organizations should educate users about the risks of opening unsolicited attachments or clicking on links in emails, especially those with suspicious file names or from unknown senders. Implement multi-factor authentication to secure access to networks and critical resources. Regularly update threat intelligence feeds to incorporate the latest IOCs associated with Gamaredon and similar threat actors. Consider using secure internet gateways to block connections to known malicious infrastructure. Employ malware analysis platforms to identify and analyze suspicious files.
Hunting methods
Customers using Cisco security products can leverage the protections provided by Cisco Secure Endpoint, Cisco Secure Email, Cisco Secure Firewall/Secure IPS, Cisco Secure Malware Analytics (Threat Grid), Umbrella, and Cisco Secure Web Appliance. Cisco Secure Network/Cloud Analytics can also help detect potentially unwanted network activity. Open-source Snort Subscriber Rule Set customers can utilize the provided Snort SIDs to detect related network traffic.
Snort SIDs:
Snort 2: 64707, 64708
Snort 3: 301171
These Snort rules are designed to detect network traffic patterns associated with this Gamaredon campaign. They likely focus on specific characteristics of the network communication, such as patterns in HTTP requests to the identified malicious servers or specific content within the network packets related to the Remcos backdoor.
IOC
IP Addresses
146.185.233.96
146.185.233.101
146.185.239.45
80.66.79.91
80.66.79.195
81.19.131.95
80.66.79.159
80.66.79.200
80.66.79.155
146.185.239.51
146.185.233.90
146.185.233.97
146.185.233.98
146.185.239.47
146.185.239.56
146.185.239.33
146.185.239.60
101.233.185.146
79.233.185.146
96.233.185.146
97.233.185.146
98.233.185.146
99.233.185.146
File Names (LNK)
3079807576 (Шашило О.В)/ШАШИЛО Олександр Віталійович.docx.lnk
3151721177 (Рибак С.В)/РИБАК Станіслав Вікторович.docx.lnk
3407607951 (Жолоб В.В)/ЖОЛОБ Владислав Вікторович.docx.lnk
3710407173 (Гур'єв П.А)/ГУР'ЄВ Павло Андрійович.docx.lnk
Вероятное расположение узлов связи, установок РЭБ и расчетов БПЛА противника. ЮГ КРАСНОАРМЕЙСКА.docx.lnk
ГУР'ЄВ Павло Андрійович.docx.lnk
Координаты взлетов противника за 8 дней (Красноармейск).xlsx.lnk
Позиции противника запад и юго-запад.xlsx.lnk
РИБАК Станіслав Вікторович.docx.lnk
ШАШИЛО Олександр Віталійович.docx.lnk
Malicious DLL Filename
mindclient.dll
C2 Port
6856
Original link: https://blog.talosintelligence.com/gamaredon-campaign-distribute-remcos/
From Contagious to ClickFake Interview: Lazarus leveraging the ClickFix tactic
Summary
The Lazarus Group, a state-sponsored threat actor attributed to North Korea (DPRK), conducted a financially motivated cyber operation targeting the cryptocurrency industry, dubbed “ClickFake Interview”. This campaign, discovered in February 2025, is assessed with high confidence to be a continuation of the “Contagious Interview” campaign, which has been ongoing since at least December 2022. In March 2025, Lazarus was also attributed to the theft of $1.5 billion from the crypto exchange Bybit, marking the largest cryptocurrency heist in history. North Korea has been using cyber operations to bypass international sanctions and fund its weapons programs since at least 2014, with DPRK threat actors stealing a record $1.3 billion in cryptocurrency in 2024. The ClickFake Interview campaign uses fake job interview websites to lure job seekers in the cryptocurrency sector and deploy the GolangGhost backdoor on Windows and macOS systems using the ClickFix tactic. This campaign shows a shift in Lazarus’ targeting from decentralized finance (DeFi) to centralized finance (CeFi) entities. The fake job offers are designed to attract individuals with limited technical expertise, unlike previous campaigns that targeted software developers. The infrastructure of ClickFake Interview shares technical indicators with the Contagious Interview campaign.
Technical Details

The ClickFake Interview campaign begins by operators sending URL links via social media, inviting users to fake cryptocurrency-related job interviews hosted on specially crafted websites. These websites, analyzed in early 2025, utilize ReactJS to dynamically load their content from a single minified JavaScript file. Each website contains multiple fake job invitations with specific details like the role, company, interview questions, and test duration, all stored within a structured JSON object in the JavaScript file. This setup is designed to build user trust as they proceed through steps like filling out contact forms, answering crypto-related questions, and preparing an introductory video.
The infection chain is triggered when users are asked to enable their camera. An error message appears, prompting them to download a driver to fix the issue. This is where the ClickFix tactic is employed. Based on the user’s browser User-Agent, they are presented with specific commands to copy, paste, and run in their system’s terminal (Command Prompt on Windows, Terminal on macOS).
On Windows, the command uses curl.exe to download a ZIP archive (nvidiadrivers.zip) from a staging C2 server. This archive is then extracted using powershell.exe, and a VBS script (update.vbs) within the archive is executed using wscript.exe. This VBS script launches a NodeJS downloader (nvidia.js) which fetches another ZIP archive (nvidiawins-update.zip). The contents of this second archive are extracted, and another update.vbs script is executed. Persistence is established by creating a registry key (NvidiaDriverUpdate) under HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run that points to the update.vbs script. This second update.vbs script then executes a Batch file (go_batch.bat) that displays a decoy progress bar while silently launching the final Go backdoor, GolangGhost (named nvidiaupdate.go).
On macOS, the command uses curl to download a malicious bash script (coremedia.sh) from a staging C2 server. This script is made executable and run. The bash script downloads a ZIP archive (VCam.zip) based on the processor architecture (amd or intel) to /var/tmp/VCam.zip. It extracts the contents to /var/tmp/VCam/ and creates a plist file (/Library/LaunchAgents/com.drive.plist) to establish persistence, pointing to another bash script named cloud.sh. Before executing cloud.sh (which runs GolangGhost), the script executes a stealer application dubbed FrostyFerret (DriverPackX.app) to retrieve the user’s system password. FrostyFerret displays a fake window mimicking the macOS UI, claiming Chrome needs camera or microphone access and prompting for the system password. Regardless of the input, it reports an invalid password and exfiltrates it to Dropbox, likely to access the user’s keychain later. The cloud.sh script then starts the GolangGhost backdoor by running the interpreted Go script server.go.
GolangGhost is a Go-based malware designed for remote control and data theft, capable of running on both Windows and macOS. It includes Chrome browser stealing capabilities based on the HackBrowserData project. Upon execution, GolangGhost generates a unique random ID for each victim and stores it in a .host file in the temporary directory. It ensures only one instance is running at a time, using .store to hold the process ID and .ses for a timestamp and machine identifier. It communicates with a hardcoded C2 server via encrypted HTTP POST requests, sending data such as a unique ID, a function name, device and user names, OS name, processor architecture, and a version number (2.0.1). The data is encrypted using RC4 with a dynamically generated 128-byte key, and the transmitted data includes the key, the encrypted data, and an MD5 sum of both. GolangGhost can execute various commands received from the C2, including uploading and downloading files, executing shell commands, retrieving system information, and stealing browser data. Analysis of the malware’s source code revealed traces of previously reported malicious domains.
The ClickFix tactic used in this campaign involves the user manually copying and pasting commands into their terminal, which is a more discreet approach compared to directly executing malicious files via mshta.exe or complex PowerShell commandlets. The sequential execution of curl.exe, powershell.exe (on Windows), and wscript.exe within a short timeframe, all initiated by the user following the fake error prompt, is a key technical characteristic of this attack.
Analysis of 184 invitations from the fake interview websites revealed 14 company names used as lures, predominantly in the centralized finance (CeFi) sector, including exchanges like Bybit, Coinbase, KuCoin, and Kraken. The targeted job roles were primarily management positions in business development, asset management, product development, and DeFi, indicating a shift towards less technical profiles.
Countries
While the report doesn’t explicitly state the targeted countries, the focus on the cryptocurrency industry suggests a potentially global target base. However, the attribution to a North Korean threat actor implies motivations related to bypassing international sanctions, suggesting that entities dealing with international finance and cryptocurrency might be of particular interest.
Industries
Cryptocurrency, particularly centralized finance (CeFi) entities such as exchanges and lending platforms.
Recommendations
Organizations in the cryptocurrency industry should educate their employees, especially those in non-technical roles, about the risks of social engineering attacks involving fake job interviews. Emphasize the importance of verifying the legitimacy of job offers and interview requests through official channels. Implement strict policies regarding the execution of commands provided during online interviews, especially those related to system or driver updates. Deploy and maintain robust endpoint detection and response (EDR) solutions to detect and block suspicious activities, including the execution of unusual command sequences involving curl, powershell, wscript, NodeJS, and bash scripts. Implement strong web filtering and reputation services to block access to known malicious domains and IP addresses associated with Lazarus Group staging and command and control infrastructure. Regularly update operating systems and software to patch known vulnerabilities that threat actors like Lazarus might exploit. Monitor network traffic for connections to the IOCs listed below. Implement multi-factor authentication for all critical accounts to mitigate the impact of stolen credentials obtained by FrostyFerret.
Hunting methods
Detection of ClickFake Interview activity can be achieved by correlating specific process execution events within a short timeframe using a Security Information and Event Management (SIEM) system. Create individual detection rules for curl.exe downloading files from suspicious domains, powershell.exe decompressing archives from temporary locations, and wscript.exe executing scripts from temporary folders. Correlate these events based on the hostname and parent process ID within a 2-minute time frame.
Sigma Rules:
name: curl_download_clickfake
detection:
selection:
process.name: 'curl.exe'
process.command_line|contains|all:
- '-k'
- '-o'
- 'temp'
process.parent.pid: '*'
condition: selection
---
name: powershell_unzip_clickfake
detection:
selection:
process.name: 'powershell.exe'
process.command_line|contains|all:
- 'Expand-Archive'
- 'temp'
- 'force'
process.parent.pid: '*'
condition: selection
---
name: wscript_execute_clickfake
detection:
selection:
process.name: 'wscript.exe'
process.command_line|contains: 'temp'
process.parent.pid: '*'
condition: selection
---
action: correlation
type: temporal
rule:
- curl_download_clickfake
- powershell_unzip_clickfake
- wscript_execute_clickfake
group-by:
- host.name
- process.parent.pid
timespan: 2m
ordered: true
Explanation: These Sigma rules aim to detect the specific sequence of commands used in the Windows infection chain of the ClickFake Interview campaign. The first rule identifies curl.exe downloading a file to a temporary location. The second rule detects powershell.exe being used to extract an archive from a temporary location. The third rule looks for wscript.exe executing a script from a temporary location. The correlation rule then combines these individual detections, requiring all three to occur within a 2-minute timeframe with the same parent process ID and hostname, indicating the ClickFix attack flow.
Sekoia Operating Language (SOL) Hunting Query:
events | where timestamp >= ago(7d) | where process.command_line contains~ "temp" | where process.name in ["curl.exe", "powershell.exe", "wscript.exe"] | aggregate cmd_line = make_set(process.command_line) by host.name, process.parent.pid
Explanation: This SOL query searches for events within the last 7 days where the process command line contains “temp” and the process name is one of curl.exe, powershell.exe, or wscript.exe. It then aggregates the unique command lines executed by the same parent process on the same host, allowing threat hunters to identify suspicious sequences of commands indicative of the ClickFake Interview attack.
Monitoring the RunMRU registry key for the execution of cmd.exe after a user is instructed to open the Run dialog (Win+R) can also be a potential detection method, although it might generate more false positives.
YARA rules have also been created to detect various components of the ClickFake Interview campaign, including the macOS installer, FrostyFerret, JavaScript code used in the fake websites, ZIP files containing GolangGhost, the NodeJS downloader, and strings within the GolangGhost backdoor itself. These rules use specific file characteristics and string content to identify malicious files associated with the campaign.
IOC
Domains (ClickFake Interview Websites)
vid-crypto-assess[.]com
assessiohq[.]com
blockassess[.]com
blockchainjobassessment[.]com
blockchainjobhub[.]com
candidateinsightinfo[.]com
coinbase-walet[.]biz
coinbase-walet[.]me
competency-core[.]com
devchallengehq[.]com
evalassesso[.]com
evalswift[.]com
quickskill-review[.]com
jobinterview360[.]com
livehirehub[.]com
talenthiring360[.]com
quickassessio[.]com
quickhire360[.]com
quickinterview360[.]com
skillprof[.]com
evalvidz[.]com
intervwolf[.]com
vidcruiterinterview[.]com
vidcruitermaster[.]com
vidintermaster[.]com
skillhiretrack[.]com
skillprooflab[.]com
talentcheck[.]pro
talentsnaptest[.]com
talentview360[.]com
test-wolf[.]com
toptalentassess[.]com
ugethired360[.]com
vidassess360[.]com
vidassesspro[.]com
videorecruitpro[.]com
vidhirehub[.]com
zenspiretech[.]com
Domains (Staging C2)
api.camdriverhub[.]cloud
api.camdrivers[.]cloud
api.camdriverstore[.]cloud
api.drivercamhub[.]cloud
api.driversnap[.]cloud
api.driverstream[.]cloud
api.provideodrivers[.]cloud
api.smartdriverfix[.]cloud
api.vcamdriverupdate[.]cloud
api.videocarddrivers[.]cloud
api.videodriverzone[.]cloud
api.videotechdrivers[.]cloud
api.vidtechhub[.]cloud
api.webcamdrivers[.]cloud
api.webcamwizard[.]cloud
api.camdriversupport[.]com
api.camera-drive[.]org
api.camtechdrivers[.]com
api.drivercams[.]cloud
api.drive-release[.]cloud
api.nvidia-drive[.]cloud
api.nvidia-release[.]org
api.nvidia-release[.]us
api.smartdriverfix[.]cloud
api.web-cam[.]cloud
Domains (GolangGhost C2)
38.134.148[.]218:8080
154.62.226[.]22:8080
72.5.42[.]93:8080
Hashes (SHA256)
e88700d069a856e1a16c0da317a6f18fa626dd2d46dcbee1a7403d2e2d9ed097 (nvidiaupdate.zip - Windows ZIP 1st stage)
bfac94bfb53b4c0ac346706b06296353462a26fa3bb09fbfc99e3ca090ec127e (update.vbs - Windows ZIP 1st stage)
887189269c3594e1a851eb22f7c174a7c28618114b7dbaab6b645f34bd809f5a (nvidia.js - NodeJS loader)
e88700d069a856e1a16c0da317a6f18fa626dd2d46dcbee1a7403d2e2d9ed097 (nvidiadrivers.zip - Windows ZIP 2nd stage)
6289ef57b1772d78da0e54ba4730b6fc79f5ec1620ff63c3abaebea70190eba9 (update.vbs - Windows ZIP 2nd stage)
0cbbf7b2b15b561d47e927c37f6e9339fe418badf49fa5f6fc5c49f0dc981100 (go_batch.bat - GolangGhost Windows)
ef9f49f14149bed09ca9f590d33e07f3a749e1971a31cb19a035da8d84f97aa0 (nvidiaupdate.go - GolangGhost Windows)
3fec701b5e8486081c7062590f4ff947fcf51246cb067f951e90eb43dad930b4 (mediadriver.sh - MacOS 1st stage)
f4b4411e403dd5094eef9c8946522fc9a99cf1676c8de5926b3c343264b126e6 (VCam-amd.zip - MacOS 1st stage)
d00ca82a32b5e8063492f27dfec225b0888cd6135db3e2af65be3782bbfa16e5 (VCam-intel.zip - MacOS 1st stage)
6e186ada6371f5b970b25c78f38511af8d10faaeaed61042271892a327099925 (cloud.sh - GolangGhost MacOS)
ba81429101a558418c80857781099e299c351b09c8c8ad47df2494634a5332dc (server.go - GolangGhost MacOS)
b7b9e7637a42b5db746f1876a2ecb19330403ecb4ec6f5575db4d94df8ec79e8 (RDriverUpdate or DriverPackX.app - FrostyFerret)
a803c043e12a5dac467fae092b75aa08b461b8e9dd4c769cea375ff87287a361 (mediadriver.jpg - Dummy content)
e52118fc7fc9b14e5a8d9f61dfae8b140488ae6ec6f01f41d9e16782febad5f2 (uvcupdate.zip - Dummy content)
Original link: https://blog.sekoia.io/clickfake-interview-campaign-by-lazarus/