The Feed 2025-04-09

AI Generated Podcast
Summarized Stories
-
CrushFTP CVE-2025-31161 Auth Bypass and Post-Exploitation: This blog post details the critical CVE-2025-31161 authentication bypass vulnerability affecting CrushFTP, its exploitation in the wild leading to potential admin access, and observed post-exploitation activities involving RMM tools and malware.
-
Exploitation of CLFS zero-day leads to ransomware activity: Microsoft reports on the exploitation of a zero-day elevation of privilege vulnerability in the Windows Common Log File System (CLFS) (CVE-2025-29824) by the Storm-2460 threat actor, which led to the deployment of ransomware.
-
How ToddyCat tried to hide behind AV software: Kaspersky analyzes the TCESB tool used by the ToddyCat APT group, which employs DLL proxying to evade ESET antivirus and leverages a vulnerable driver for defense evasion and payload execution.
-
Windows Remote Desktop Protocol: Remote to Rogue: Google Threat Intelligence Group describes a novel phishing campaign by UNC5837 that used signed .rdp files to leverage resource redirection and RemoteApps for espionage, potentially utilizing the PyRDP proxy tool.
-
Threat actors leverage tax season to deploy tax-themed phishing campaigns: Microsoft observed multiple tax-themed phishing campaigns designed to steal credentials and deploy various malware, including BruteRatel C4, Latrodectus, RaccoonO365, AHKBot, GuLoader, and Remcos.
CrushFTP CVE-2025-31161 Auth Bypass and Post-Exploitation
Summary
A critical severity authentication bypass vulnerability, CVE-2025-31161, affects CrushFTP managed file transfer (MFT) software versions 10.0.0 through 10.8.3 and 11.0.0 through 11.3.0, allowing unauthenticated remote attackers with knowledge of a username to impersonate that user and perform actions on their behalf, including administrative functions and data retrieval. Exploitation of this vulnerability can lead to full control of the vulnerable server. Huntress observed in-the-wild exploitation starting as early as March 30, 2025, with post-exploitation activities including the deployment of legitimate and malicious Remote Monitoring and Management (RMM) tools like MeshCentral and AnyDesk, as well as custom malware such as a Telegram bot. It is strongly recommended to patch immediately to versions 10.8.4+ or 11.3.1+. As of March 30, 2025, approximately 1,500 vulnerable CrushFTP instances were publicly exposed.
Technical Details
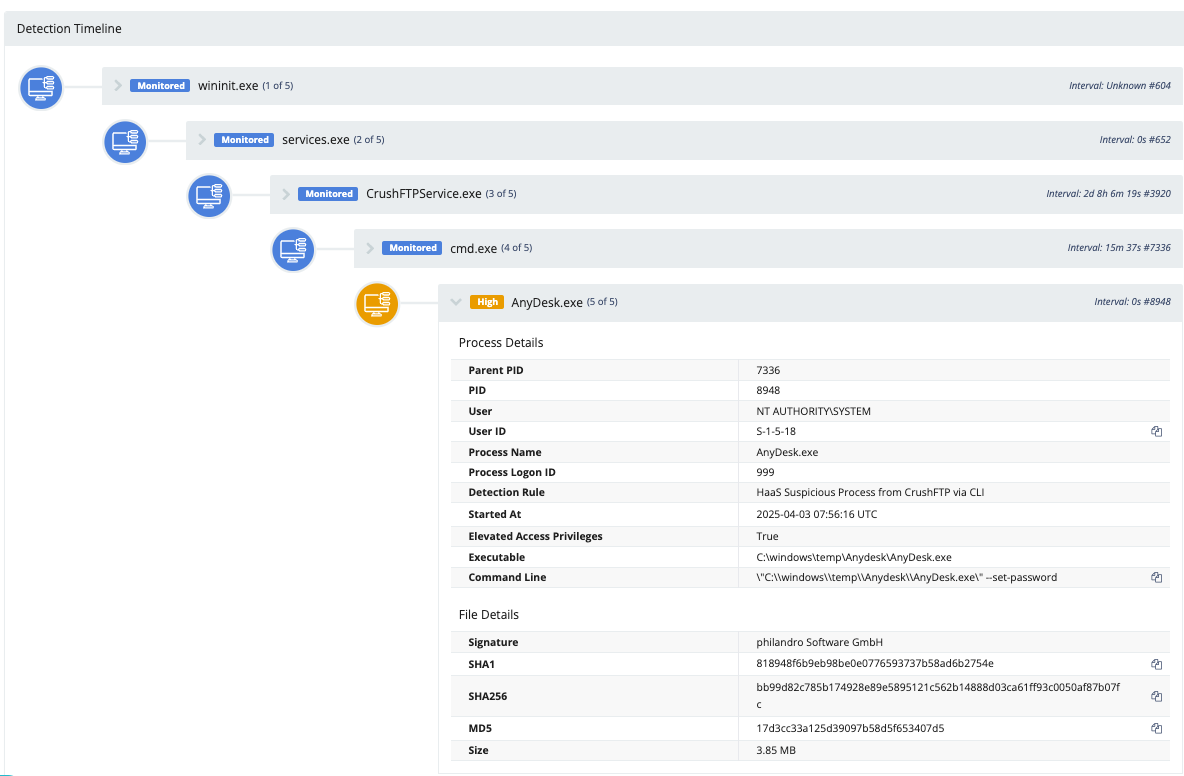
CVE-2025-31161 is located in the S3 authorization header processing of CrushFTP. The vulnerability allows an attacker to bypass authentication by sending an HTTP request with a crafted Authorization header. The Authorization header needs to have the prefix AWS4-HMAC-SHA256 and the Credential field set to a known CrushFTP username, which does not include a tilde (~) followed by a forward slash (/). The default administrator username crushadmin is commonly targeted.
The proof-of-concept (PoC) HTTP request demonstrates the bypass:
GET /WebInterface/function/?command=getUserList&serverGroup=MainUsers&c2f=1111 HTTP/1.1
Cookie: CrushAuth=1111111111_111111111111111111111111111111111
Authorization: AWS4-HMAC-SHA256 Credential=crushadmin/
Connection: close
This request can list users on the CrushFTP instance. Key components include a CrushAuth cookie (which does not need to be valid but might need to be “known” to the instance, potentially requiring a prior request) and a c2f HTTP parameter that matches the last four characters of the CrushAuth cookie.
Successful exploitation grants the attacker access to backend functions, allowing them to perform administrative actions. Observed post-exploitation activities include:
- Creation of Backdoor Accounts: Threat actors used the
setUserItemfunction to create new administrator accounts with hidden last login times to ensure persistence. An example backdoor account name observed wasEaion6Mz. - Deployment of RMM Tools:
- MeshCentral: The MeshCentral agent (
mesch.exe) was uploaded to/Windows/Temp/and executed using commands likeC:\Windows\Temp\mesch.exe runandC:\Windows\Temp\mesch.exe -fullinstall. Base64 encoded commands were also observed to connect to specific dispatcher ports. Subsequently, a non-admin user (CrushUser) was added to the local administrators group. The use of acurrentAuthcookie in the logs alongside the MeshCentral activity suggests that attackers leveraged the authentication bypass and then potentially established a legitimate session. - AnyDesk: A malicious AnyDesk instance was installed using
CrushFTPService.exe. Commands observed include usingmsiinstall.exefor silent installation andAnyDesk.exeto register a license and set a password.
- MeshCentral: The MeshCentral agent (
- Deployment of Telegram Bot Malware: A large C++ DLL (
d3d11.dll) implementing the open-source TgBot library was uploaded to/Windows/Temp/. While execution wasn’t directly observed, analysis of the DLL and associated PDB information revealed potential use for collecting telemetry from infected hosts via a Telegram bot. Three additional related DLLs were identified on VirusTotal. - Credential Dumping: On a host where AnyDesk was deployed, the threat actor proceeded to dump the SAM and System registry hives using
reg.exeto harvest credentials.
The CrushFTP software is typically installed in its own program directory at the root of a volume (e.g., C:\CrushFTP10, C:\CrushFTP11). The CrushFTP.log file, located within this directory, is a reliable source for determining the full running version number and for identifying potential exploitation activity. Look for ACCEPT and POST requests with AWS4-HMAC-SHA256 Credential=crushadmin/ without a corresponding currentAuth cookie. Log files in the \logs\session_logs directory may also contain further details.
Recommendations
- Immediately patch all CrushFTP installations to versions 10.8.4+ or 11.3.1+.
- If your CrushFTP instance is publicly exposed to the internet, patching should be prioritized.
- Review the
CrushFTP.logfile and\logs\session_logsdirectory for any signs of exploitation, particularly activity including theAWS4-HMAC-SHA256 Credential=crushadmin/string without acurrentAuthcookie. - Look for child processes spawned by the
CrushFTPService.exeprocess, which could indicate post-exploitation activity. - Consider using a trial of Huntress for identifying any potential compromises.
Hunting methods
title: Remote Access Tool - MeshAgent Command Execution via MeshCentral
id: 74a2b202-73e0-4693-9a3a-9d36146d0775
status: experimental
description: |
Detects the use of MeshAgent to execute commands on the target host, particularly when threat actors might abuse it to execute commands directly.
MeshAgent can execute commands on the target host by leveraging win-console to obscure their activities and win-dispatcher to run malicious code through IPC with child processes.
references:
- https://github.com/Ylianst/MeshAgent
- https://github.com/Ylianst/MeshAgent/blob/52cf129ca43d64743181fbaf940e0b4ddb542a37/modules/win-dispatcher.js#L173
- https://github.com/Ylianst/MeshAgent/blob/52cf129ca43d64743181fbaf940e0b4ddb542a37/modules/win-info.js#L55
author: '@Kostastsale'
date: 2024-09-22
tags:
- attack.command-and-control
- attack.t1219
logsource:
product: windows
category: process_creation
detection:
selection:
ParentImage|endswith: '\meshagent.exe'
Image|endswith:
- '\cmd.exe'
- '\powershell.exe'
- '\pwsh.exe'
condition: selection
falsepositives:
- False positives can be found in environments using MessAgent for remote management, analysis should prioritize the grandparent process, MessAgent.exe, and scrutinize the resulting child processes triggered by any suspicious interactive commands directed at the target host.
level: medium
Logic: attackers were observed deploying MeshCentral (mesch.exe, likely a renamed meshagent.exe) after gaining initial access. This Sigma rule would be directly useful in detecting that specific post-exploitation technique where the attackers might use the installed MeshAgent to run further commands via cmd.exe or powershell.exe.
title: Remote Access Tool - AnyDesk Silent Installation
id: 114e7f1c-f137-48c8-8f54-3088c24ce4b9
status: test
description: Detects AnyDesk Remote Desktop silent installation. Which can be used by attackers to gain remote access.
references:
- https://twitter.com/TheDFIRReport/status/1423361119926816776?s=20
- https://support.anydesk.com/Automatic_Deployment
author: Ján Trenčanský
date: 2021-08-06
modified: 2023-03-05
tags:
- attack.command-and-control
- attack.t1219
logsource:
category: process_creation
product: windows
detection:
selection:
CommandLine|contains|all:
- '--install'
- '--start-with-win'
- '--silent'
condition: selection
fields:
- CommandLine
- ParentCommandLine
- CurrentDirectory
falsepositives:
- Legitimate deployment of AnyDesk
level: high
Logic: attackers were observed installing AnyDesk silently using similar command-line flags (–install, –start-with-win) after exploiting the vulnerability. This Sigma rule would be directly applicable to detecting that specific post-exploitation behavior.
IOC
IP Addresses
172.235.144[.]67
2.58.56[.]16
File Hashes (SHA256)
9036c92c3ca73cb6ec2da25035322554319288fd2f6db906413011873ad7e281 (MeshAgent Installer Binary - mesch.exe)
1ab5a915e306686a1c7bebd03563a977 (TgBot DLL - d3d11.dll)
be6cb5f80b33b9e97622d278a86a99e67b78ccab0b3e554b8430ae5969bcfc0e (Likely related TgBot DLL)
f7c8be827f3bd98b30c5a8d23c1af77f3d0324a9ebcd90104134fc1971751ff7 (Likely related TgBot DLL)
85a1bfebf2a5973ebecd6e5a58c8fab18edfead2c1680ec1e9cce902924c347e (Likely related TgBot DLL)
114c196c39c91575880a5012d06565b1 (MD5 of uploaded mesch.exe)
Other Indicators
Eaion6Mz (Backdoor Account Name)
C:\Windows\Temp\d3d11.dll (Path of Telegram Bot Malware)
C:\Windows\Temp\mesch.exe (Path of MeshAgent Installer)
Original link: https://www.huntress.com/blog/crushftp-cve-2025-31161-auth-bypass-and-post-exploitation
Exploitation of CLFS zero-day leads to ransomware activity
Summary
Microsoft Threat Intelligence Center (MSTIC) and Microsoft Security Response Center (MSRC) have reported the active post-compromise exploitation of a zero-day elevation of privilege vulnerability in the Windows Common Log File System (CLFS), tracked as CVE-2025-29824. This exploitation, attributed to the threat actor Storm-2460, involved the deployment of PipeMagic malware followed by ransomware activity. The attackers targeted a limited number of organizations across various sectors and countries. The CLFS exploit enabled threat actors to escalate privileges from an initial foothold, facilitating widespread ransomware deployment within compromised environments. Microsoft has released security updates to address this vulnerability and strongly advises immediate patching.
Technical Details
The observed attack chain began with an unknown initial access vector, after which the threat actor Storm-2460 utilized the certutil utility to download a malicious MSBuild file from compromised legitimate third-party websites. This MSBuild file contained an encrypted malware payload, which, upon decryption and execution via the EnumCalendarInfoA API callback, delivered the PipeMagic malware. Microsoft attributes the exploitation of the CLFS zero-day vulnerability to Storm-2460, which also used PipeMagic to deploy ransomware.
Following the deployment of PipeMagic, the attackers executed the CLFS exploit in memory from a dllhost.exe process. The exploit targeted a vulnerability within the CLFS kernel driver (CVE-2025-29824). Notably, the exploit leveraged the NtQuerySystemInformation API to leak kernel addresses to user mode. However, the report highlights that this technique is restricted in Windows 11, version 24H2, as access to certain System Information Classes requires SeDebugPrivilege, which standard user accounts do not possess. Consequently, the exploit was not effective on Windows 11, version 24H2, even if the underlying vulnerability was present.
The CLFS exploit then employed a memory corruption technique and the RtlSetAllBits API to overwrite the exploit process’s token with the value 0xFFFFFFFF, effectively granting it all privileges and enabling process injection into SYSTEM processes. As part of the exploitation process, a CLFS BLF file was created by the exploit’s dllhost.exe process at the path C:\ProgramData\SkyPDF\PDUDrv.blf.
Upon successful privilege escalation, a payload was injected into winlogon.exe. This payload subsequently injected the Sysinternals procdump.exe tool into another dllhost.exe process and executed it with the following command line to dump the memory of LSASS for credential harvesting:
C:\Windows\system32\dllhost.exe -accepteula -r -ma lsass.exe c:\programdata\[random letters].
After obtaining user credentials, the threat actors proceeded with ransomware activity on the target systems. Files were encrypted with a random extension, and a ransom note named !READ_ME_REXX2!.txt was dropped. Microsoft tracks this ransomware activity under the name Storm-2460. Although a ransomware sample was not available for analysis, the ransom notes contained two .onion domains:
- jbdg4buq6jd7ed3rd6cynqtq5abttuekjnxqrqyvk4xam5i7ld33jvqd.onion, which has been associated with the RansomEXX ransomware family.
- uyhi3ypdkfeymyf5v35pbk3pz7st3zamsbjzf47jiqbcm3zmikpwf3qd.onion.
The ransomware was launched from dllhost.exe using the command line:
C:\Windows\system32\dllhost.exe --do [path_to_ransom]
Observed ransomware behaviors included the execution of commands designed to hinder recovery and analysis, such as:
bcdedit /set {default} recoveryenabled nowbadmin delete catalog -quietwevtutil cl Application
In one instance, the threat actor also spawned notepad.exe as SYSTEM, likely as a test or indicator of successful privilege escalation.
Countries
- United States
- Venezuela
- Spain
- Saudi Arabia
Industries
- Information Technology (IT)
- Real Estate
- Financial
- Software
- Retail
Recommendations
- Apply security updates for CVE 2025-29824 as soon as possible. These updates were released on April 8, 2025.
- Organizations should prioritize patching elevation of privilege vulnerabilities to defend against ransomware attacks.
- Refer to Microsoft’s blog “Ransomware as a service: Understanding the cybercrime gig economy and how to protect yourself” for robust ransomware defense measures.
- Turn on cloud-delivered protection in Microsoft Defender Antivirus or equivalent antivirus products.
- Use device discovery to identify and onboard unmanaged devices to Microsoft Defender for Endpoint.
- Run EDR in block mode in Microsoft Defender for Endpoint.
- Enable investigation and remediation in full automated mode in Microsoft Defender for Endpoint.
- Use Microsoft Defender Vulnerability Management to assess and deploy missed updates.
- Microsoft 365 Defender customers should turn on attack surface reduction rules for advanced ransomware protection.
- Microsoft Defender XDR customers can refer to the list of applicable detections.
- Customers with provisioned access can use Microsoft Security Copilot in Microsoft Defender to investigate and respond to incidents and hunt for threats.
Hunting methods
Microsoft Sentinel (KQL) Queries:
- Search for devices having CVE-2025-29814 exposure
DeviceTvmSoftwareVulnerabilities | where CveId in ("CVE-2025-29824") | project DeviceId,DeviceName,OSPlatform,OSVersion,SoftwareVendor,SoftwareName,SoftwareVersion, CveId,VulnerabilitySeverityLevel | join kind=inner ( DeviceTvmSoftwareVulnerabilitiesKB | project CveId, CvssScore,IsExploitAvailable,VulnerabilitySeverityLevel,PublishedDate,VulnerabilityDescription,AffectedSoftware ) on CveId | project DeviceId,DeviceName,OSPlatform,OSVersion,SoftwareVendor,SoftwareName,SoftwareVersion, CveId,VulnerabilitySeverityLevel,CvssScore,IsExploitAvailable,PublishedDate,VulnerabilityDescription,AffectedSoftwareLogic: This query searches the Microsoft Defender Vulnerability Management data for devices that have an exposure to CVE-2025-29824. It joins information about the vulnerability with details about the affected software installed on devices to identify potentially vulnerable systems.
- Detect CLFS BLF file creation after exploitation of CVE 2025-29824
DeviceFileEvents | where FolderPath has "C:\\ProgramData\\SkyPDF\\" and FileName endswith ".blf"Logic: This query looks for the creation of files with the “.blf” extension within the “C:\ProgramData\SkyPDF" directory. The creation of a file at this specific path is an indicator of the CLFS exploit activity observed by Microsoft.
- LSSASS process dumping activity
SecurityEvent | where EventID == 4688 | where CommandLine has("dllhost.exe -accepteula -r -ma lsass.exe") | extend timestamp = TimeGenerated, AccountCustomEntity = Account, HostCustomEntity = ComputerLogic: This query searches the Windows Security Event logs for Event ID 4688 (A new process has been created) where the command line contains “dllhost.exe -accepteula -r -ma lsass.exe”. This specific command line was observed being used by the threat actor to dump the LSASS process memory for credential access.
- Ransomware process activity
let cmdlines = dynamic(["C:\\Windows\\system32\\dllhost.exe --do","bcdedit /set {default} recoveryenabled no","wbadmin delete catalog -quiet","wevtutil cl Application"]); DeviceProcessEvents | where ProcessCommandLine has_any (cmdlines) | project TimeGenerated, DeviceName, ProcessCommandLine, AccountDomain, AccountNameLogic: This query looks for process execution events where the command line matches any of the commands known to be associated with the ransomware activity, including the ransomware launch command and commands to disable recovery options and clear event logs.
- PipeMagic and RansomEXX fansomware domains
let domains = dynamic(["aaaaabbbbbbb.eastus.cloudapp.azure.com","jbdg4buq6jd7ed3rd6cynqtq5abttuekjnxqrqyvk4xam5i7ld33jvqd.onion","uyhi3ypdkfeymyf5v35pbk3pz7st3zamsbjzf47jiqbcm3zmikpwf3qd.onion"]); DeviceNetworkEvents | where RemoteUrl has_any (domains) | project TimeGenerated, DeviceId, DeviceName, Protocol, LocalIP, LocalIPType, LocalPort,RemoteIP, RemoteIPType, RemotePort, RemoteUrlLogic: This query searches network connection events for any communication to the domains associated with the PipeMagic malware and the RansomEXX ransomware family found in the ransom notes.
IOC
File Paths
C:\ProgramData\SkyPDF\PDUDrv.blf
C:\Windows\system32\dllhost.exe --do
C:\programdata\[random letters] (used with procdump.exe)
!_READ_ME_REXX2_!.txt
Command Lines
C:\Windows\system32\dllhost.exe -accepteula -r -ma lsass.exe c:\programdata\[random letters]
bcdedit /set {default} recoveryenabled no
wbadmin delete catalog -quiet
wevtutil cl Application
Domains
aaaaabbbbbbb.eastus.cloudapp.azure[.]com
jbdg4buq6jd7ed3rd6cynqtq5abttuekjnxqrqyvk4xam5i7ld33jvqd.onion
uyhi3ypdkfeymyf5v35pbk3pz7st3zamsbjzf47jiqbcm3zmikpwf3qd.onion
Original link: https://www.microsoft.com/en-us/security/blog/2025/04/08/exploitation-of-clfs-zero-day-leads-to-ransomware-activity/
How ToddyCat tried to hide behind AV software
Summary
This research article details how the ToddyCat APT group attempted to evade detection on compromised Windows systems by running their malicious tool, TCESB, in the context of a legitimate security solution (ESET Command line scanner). This allowed them to bypass monitoring tools that typically trust security software. The attackers leveraged a DLL proxying technique to load their malicious code and exploited a vulnerability (CVE-2024-11859) in the ESET Command line scanner that caused it to insecurely load system libraries. The TCESB tool, based on the open-source EDRSandBlast malware, was modified to extend its capabilities, including disabling notification routines by modifying operating system kernel structures. To achieve this, TCESB determines the Windows kernel version and retrieves necessary memory offsets from either an embedded CSV file or by downloading a PDB file from Microsoft’s debug information server. The tool also employs the Bring Your Own Vulnerable Driver (BYOVD) technique by installing the vulnerable Dell DBUtilDrv2.sys driver (CVE-2021-36276). Finally, TCESB waits for an encrypted payload file in its directory, decrypts it using AES-128 with a key embedded in the payload, and executes it in memory.
Technical Details

The ToddyCat attackers employed several sophisticated techniques to achieve their goal of stealthy payload execution.
- Exploiting Security Solution Trust: The core of their strategy was to execute their malicious code within the context of a security solution, the ESET Command line scanner. This approach allowed them to operate with a higher level of trust, as monitoring tools are less likely to flag activity originating from security software.
- DLL Proxying (Hijack Execution Flow, T1574): TCESB is implemented as a 64-bit DLL named
version.dll. Static analysis revealed that this malicious DLL exports all the same functions as the legitimate Windows system fileversion.dll(Version Checking and File Installation Libraries). Instead of implementing these functions, TCESB redirects the calls to the originalversion.dll. This technique, known as DLL proxying, allows a legitimate application that expects to load the systemversion.dllto instead load the malicious TCESB DLL. The application continues to function normally, while the malicious code runs in its background. - Exploiting Insecure DLL Loading (CVE-2024-11859): Simply proxying a DLL is not sufficient to execute malware. The application loading the malicious DLL must contain insecure code that searches for dynamic library images in untrusted locations. The ESET Command line scanner (
ecls.exe) was found to have such a vulnerability. It insecurely loadsversion.dllby first checking the current directory before searching system directories. By placing the maliciousversion.dll(TCESB) in the same directory asecls.exe, the attackers could trick the vulnerable scanner into loading and executing their tool. - Leveraging Open-Source Malware (EDRSandBlast): Analysis of the strings within the TCESB DLL revealed significant overlap with the open-source malicious tool EDRSandBlast. The strings were not obfuscated, and Kaspersky products detect TCESB with verdicts associated with ToddyCat and EDRSandBlast. This indicates that ToddyCat built TCESB upon the foundation of EDRSandBlast, modifying its original code to add further malicious functionality.
- Disabling Notification Routines: One of the primary capabilities of TCESB is to modify operating system kernel structures to disable notification routines, which are used to alert security solutions about system events like process creation or driver loading.
- Kernel Memory Address Resolution: To modify these kernel structures, TCESB needs to locate them in memory. It first determines the running Windows kernel version using the
GetNtoskrnlVersion()function. It then attempts to retrieve the corresponding memory offsets from two sources:- Embedded CSV File: TCESB contains a CSV file within its resources that stores a table of kernel versions and their associated memory offsets. It searches this file for a match with the current kernel version. The content of this CSV file in TCESB matches a specific version of the CSV data from the EDRSandBlast repository from August 13, 2022.
- PDB File Download: If the required kernel version is not found in the embedded CSV, TCESB attempts to download the Program Database (PDB) file containing debug symbols for the kernel (
ntoskrnl.exe) from Microsoft’s debug information server. It constructs the download URL using the version information extracted fromC:\Windows\System32\ntoskrnl.exe. The downloaded PDB file is then used to read the necessary kernel memory offsets.
- Bring Your Own Vulnerable Driver (BYOVD, T1211): To interact with and modify kernel structures, TCESB utilizes the BYOVD technique. It installs a legitimate but vulnerable driver, Dell DBUtilDrv2.sys (vulnerable to CVE-2021-36276), into the system via the Device Manager interface using an INF file (
dbutildrv2.INF). This allows TCESB to gain the necessary privileges to manipulate kernel-level components. - Payload Execution: Once the vulnerable driver is installed and the necessary kernel offsets are resolved, TCESB enters a loop, checking every two seconds for the presence of a payload file (with names like
kesporecoreand no extension) in its current directory. This delay likely allows the operator to ensure the tool is running correctly before deploying the actual payload. When the payload file is found, TCESB reads and decrypts its contents using AES-128. The first 32 bytes of the payload file contain the decryption key, followed by the encrypted data. After decryption, the payload is loaded into memory and executed. - Logging: TCESB creates its own log file to record detailed information about its execution process.
Recommendations
The article provides the following technical recommendations for detecting similar activity:
- Monitor systems for driver installation events, especially those involving drivers with known vulnerabilities. Resources like the loldrivers project website can provide lists of such drivers.
- Monitor events related to the loading of Windows kernel debug symbols on systems where kernel debugging is not a standard practice.
- Utilize operating system tools to verify the digital signatures of all loaded system library files.
Hunting methods
The article suggests monitoring for the installation of drivers with known vulnerabilities and the loading of Windows kernel debug symbols.
IOC
Malicious Files Hashes (TCESB - version.dll)
D38E3830C8BA3A00794EF3077942AD96
008F506013456EA5151DF779D3E3FF0F
Legitimate file for DLL proxying
8795271F02B30980EBD9950FCC141304 ESET Command-line scanner (ecls)
Legitimate files for BYOVD
B87944DCC444E4C6CE9BB9FB8A9C0DEF dbutildrv2.INF
DE39EE41D03C97E37849AF90E408ABBE DBUtilDrv2.cat
DACB62578B3EA191EA37486D15F4F83C dbutildrv2.sys
Original link: https://securelist.com/toddycat-apt-exploits-vulnerability-in-eset-software-for-dll-proxying/116086/
Windows Remote Desktop Protocol: Remote to Rogue
Summary
This Google Threat Intelligence Group (GTIG) research article details a novel phishing campaign attributed to the suspected Russia-nexus espionage actor UNC5837, targeting European government and military organizations in October 2024. The campaign utilized signed .rdp file attachments to establish Remote Desktop Protocol (RDP) connections, creatively leveraging resource redirection (mapping victim file systems to attacker servers) and RemoteApps (presenting attacker-controlled applications) instead of focusing on traditional interactive RDP sessions. Evidence suggests the potential use of an RDP proxy tool like PyRDP to automate malicious activities such as file exfiltration and clipboard capture, a technique dubbed “Rogue RDP”. The primary objective appeared to be espionage and file theft. The signed nature of the .rdp files helped bypass typical security warnings.
Technical Details
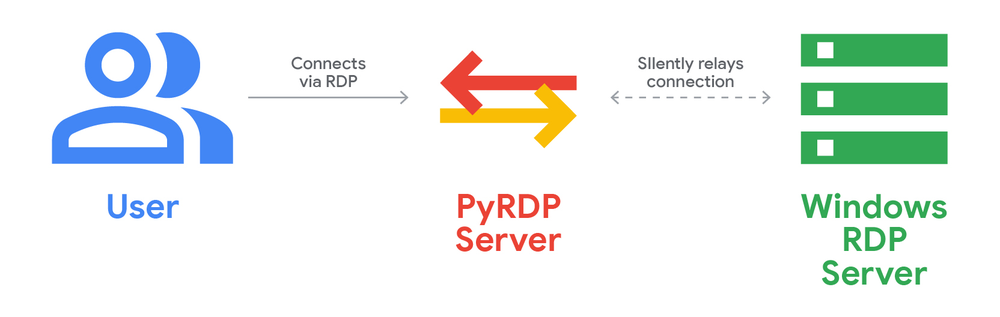
The campaign employed several notable technical details:
- Phishing with Signed .rdp Files: The attack began with widespread phishing emails containing signed .rdp file attachments. The email claimed to be part of a project involving Amazon, Microsoft, and the Ukrainian State Secure Communications and Information Security Agency. The signed nature of the .rdp file (using a Let’s Encrypt certificate tied to the attacker’s domain) likely helped bypass the typical warning banner displayed when executing unsigned .rdp files.
- .rdp Configuration Files: The executed .rdp files contained specific configurations:
- Full Address: Defined the malicious command-and-control (C2) server (e.g., eu-southeast-1-aws[.]govtr[.]cloud).
- Resource Redirection: Enabled read and write access to all victim drives (
drivestoredirect:s:*), clipboard (redirectclipboard:i:1), printers, COM ports, smart cards, WebAuthn requests, and POS devices, mapping them to the attacker’s server. - RemoteApp: Configured the session to present a server-hosted application (“AWS Secure Storage Connection Stability Test v24091285697854”) to the victim (
remoteapplicationmode:i:1,remoteapplicationname). This application, while its exact purpose is unknown, may have been used for phishing or further compromise. The icon for this application was also specified (remoteapplicationicon). - Command-Line Arguments: Windows environment variables (%USERPROFILE%, %COMPUTERNAME%, %USERDNSDOMAIN%) from the victim machine were sent as command-line arguments to the RemoteApp on the attacker’s server, facilitating initial reconnaissance (
remoteapplicationexpandcmdline:i:0,remoteapplicationcmdline). - Certificate Signature: Included an encoded signature generated using Let’s Encrypt, with the SSL certificate issued for the domain the RDP connection was established with.
- Resource Redirection Mechanism: RDP resource redirection uses “virtual channels” for communication, with protocol data packets (PDU) mirroring changes between the victim and attacker machines over encrypted streams.
- RemoteApps for Deception: RemoteApps are applications hosted on the RDP server that appear as windowed applications on the victim’s machine, masking their remote origin. They utilize the resources of the RDP server but can also access redirected victim drives.
- Potential Use of PyRDP: The report discusses PyRDP, an open-source RDP proxy tool, and its potential use in automating malicious activities. PyRDP operates as a man-in-the-middle, relaying the RDP connection while providing enhanced capabilities:
- Password Theft: Can capture NTLM hashes (with NLA enabled) or attempt to heuristically detect plaintext passwords (without NLA). The report suggests PyRDP might have been used to bypass the user authentication prompt and directly present the RemoteApp.
- Command Execution: Allows execution of commands (cmd.exe, PowerShell, PowerShell scripts) on the RDP server, though not directly on the victim machine, by temporarily freezing the user session. This could be used to plant malicious files on redirected drives.
- Clipboard Capture: Automatically captures the victim’s clipboard data.
- File System Scraping/Browsing: Can crawl and save victim files (if
--crawloption is used) or allow browsing and downloading of accessed files via the PyRDP-player GUI. - Session Streaming/Capture/Intercept: Can record RDP sessions and stream them live, allowing for potential interaction and takeover of the RDP server.
- Limited Direct Victim Control: The campaign did not involve direct command execution on victim machines. The attacker’s control over the victim was primarily through resource redirection and the presented RemoteApp.
Countries
European government and military organizations were targeted. CERT-UA (Ukraine) also reported this campaign.
Industries
Government and Military sectors were targeted.
Recommendations
The article provides the following recommendations for defenders:
- System Hardening:
- Implement network-level blocking of outgoing RDP traffic to public IP addresses.
- Disable resource redirection via the registry by setting
HKEY_LOCAL_MACHINE\Software\Microsoft\Terminal Server Client\DisableDriveRedirection(REG_DWORD) to1. - Configure granular RDP policies via Group Policy (Computer Configuration -> Administrative Templates -> Windows Components -> Remote Desktop Services -> Remote Desktop Connection Client and Remote Desktop Session Host) to:
- Disable execution of .rdp files from unknown publishers (“Allow .rdp files from unknown publishers”).
- Specify trusted .rdp publishers by their certificate SHA1 thumbprints.
- Manage resource redirection, clipboard redirection.
- Force Network Level Authentication.
- Set time limits for active/idle connections.
- Block the
.rdpfile extension as email attachments.
Hunting methods
- Log Artifact Analysis:
- Monitor for the creation of specific registry keys (
HKU\...\Microsoft\Terminal Server Client\Servers\<attacker_IP_Address>andHKU\...\Microsoft\Terminal Server Client\Servers\<attacker_server>\UsernameHint) that log attacker server addresses and usernames. - Analyze Windows Event Logs (Microsoft-Windows-TerminalServices-RDPClient/Operational) for Event ID 1102 (attacker server IP), Event ID 1027 (attacker server domain), and Event ID 1029 (base64-encoded SHA256 hash of the username).
- With enhanced logging (Sysmon, advanced audit logging), monitor for file write activity originating from
C:\Windows\system32\mstsc.exe, excluding known benign patterns like_TS[A-Z0-9]{4}\.tmpin%APPDATA%/Local/Tempand file operations in%APPDATA%/Local\Microsoft\Terminal Server Client. - Consider enabling and cautiously monitoring
mstsc.exe-originating file read activity. - Monitor for the execution of .rdp files directly from Outlook email attachments using the provided regex patterns:
/\\AppData\\Local\\Microsoft\\Windows\\(INetCache|Temporary Internet Files) \\Content\.Outlook\\[A-Z0-9]{8}\\[^\\]{1,255}\.rdp$/ /\\AppData\\Local\\Packages\\Microsoft\.Outlook_[a-zA-Z0-9]{1,50}\\.{0,120} \\[^\\]{1,80}\.rdp$/ /\\AppData\\Local\\Microsoft\\Olk\\Attachments\\([^\\]{1,50}\\){0,5}[^\\] {1,80}\.rdp$/The article provides the following YARA rules to detect suspicious RDP configuration files:
- Monitor for the creation of specific registry keys (
- Detect RDP config files utilizing RemoteApp and ResourceRedirection:
/* Detect RDP config files utilizing RemoteApp and ResourceRedirection */ rule G_Hunting_RDP_File_RemoteApp_ResourceRedir_1 { meta: author = "Google Threat Intelligence Group" description = "Detect RDP config files utilizing RemoteApp and resource redirection" strings: $rdp_param1 = "remoteapplicationmode:i:1" wide $rdp_param2 = "drivestoredirect:s:" wide $rdp_param3 = "remoteapplicationprogram:s:" wide $rdp_param4 = "remoteapplicationname:s:" wide condition: filesize < 20KB and (2 of ($rdp_param*)) }Logic: This rule looks for
.rdpfiles smaller than 20KB that contain at least two of the following strings:remoteapplicationmode:i:1(indicating RemoteApp mode),drivestoredirect:s:(indicating drive redirection),remoteapplicationprogram:s:(specifying a remote application program), andremoteapplicationname:s:(specifying the name of the remote application). The presence of these parameters suggests the.rdpfile is configured to utilize both RemoteApps and resource redirection. - Detect RDP config files with a base64 LetsEncrypt certificate:
/* Detect RDP config files with a base64 LetsEncrypt certificate */ rule G_Hunting_RDP_File_LetsEncrypt_Signed_1 { meta: author = "Google Threat Intelligence Group" description = "Detects signed RDP configuration files that contain a base64 encoded LetsEncrypt certificate" strings: $rdp_param1 = "full address" wide $rdp_param2 = "redirectclipboard" wide $rdp_param3 = "remoteapplicationmode" wide $rdp_param4 = "compression" wide $rdp_param5 = "remoteapplicationexpandcmdline" wide $rdp_param6 = "promptcredentialonce" wide $rdp_param7 = "allow font smoothing" wide $rdp_param8 = "desktopheight" wide $rdp_param9 = "screen mode id" wide $rdp_param10 = "videoplaybackmode" wide $lets_encrypt_1 = "Let's Encrypt" base64wide $lets_encrypt_2 = "lencr.org" base64wide condition: filesize < 20KB and (any of ($lets_encrypt_*)) and (2 of ($rdp_param*)) }Logic: This rule searches for
.rdpfiles smaller than 20KB that contain either of the base64-encoded strings “Let’s Encrypt” or “lencr.org” (indicating a Let’s Encrypt certificate) and at least two other common RDP parameters (likefull address,redirectclipboard,remoteapplicationmode, etc.). This rule aims to detect signed.rdpfiles using certificates from Let’s Encrypt, which was observed in the campaign.
IOC
Domains
eu-southeast-1-aws[.]govtr[.]cloud
eu-north-1-aws.ua-gov.cloud
govtr.cloud
ua-gov.cloud
Original link: https://cloud.google.com/blog/topics/threat-intelligence/windows-rogue-remote-desktop-protocol/
Threat actors leverage tax season to deploy tax-themed phishing campaigns
Summmary
As Tax Day in the United States approaches, Microsoft has observed a surge in tax-themed phishing campaigns designed for social engineering. These campaigns employ various redirection techniques, including URL shorteners and QR codes embedded in malicious attachments, and abuse legitimate services like file-hosting and business profile pages to evade detection. The primary objectives of these campaigns are to steal user credentials and deploy malware, leading to potential identity theft and financial losses. Threat actors utilize well-established social engineering tactics, highlighting the need for advanced anti-phishing solutions and comprehensive user awareness training within organizations. Microsoft has identified multiple distinct campaigns delivering a range of malware, including the RaccoonO365 phishing-as-a-service platform, remote access trojans like Remcos, red-teaming tools such as BruteRatel C4, and other malware such as Latrodectus, AHKBot, and GuLoader. These campaigns underscore the persistent threat posed by cybercriminals during tax season and the importance of proactive defense measures.
Technical Details
Observed tax-themed phishing campaigns leveraged several distinct technical approaches and delivered various malicious payloads.
One campaign, observed around February 6, 2025, and attributed to the access broker Storm-0249, involved thousands of emails with subjects like “Notice: IRS Has Flagged Issues with Your Tax Filing” and attached PDFs such as “lrs_Verification_Form_1773.pdf”. These PDFs contained embedded DoubleClick URLs that redirected victims through a Rebrandly URL shortener to a fake DocuSign landing page hosted on a lookalike domain (slgndocline[.]onlxtg[.]com). Upon clicking a “Download” button on this fake page, the outcome was conditional. If the victim’s system and IP address met the threat actor’s criteria, a JavaScript file was downloaded from Firebase. Execution of this JavaScript file then downloaded a Microsoft Software Installer (MSI) containing the BruteRatel C4 (BRc4) malware, which subsequently installed Latrodectus. If access was restricted, a benign PDF from royalegroupnyc[.]com was served as a decoy.
Latrodectus is a loader malware used for initial access and payload delivery. The observed version, Latrodectus 1.9 (first seen in February 2025), featured dynamic command-and-control (C2) configurations, anti-analysis features like process count and network adapter checks, and C2 check-in behavior that split POST data. This version also reintroduced scheduled tasks for persistence and the ability to execute Windows commands via the command prompt.
BruteRatel C4 (BRc4) is an advanced red-teaming framework capable of bypassing modern security defenses. Threat actors are exploiting it for post-exploitation activities and C2 operations. The campaign attributed to Storm-0249 used BRc4 for these purposes, with C2 infrastructure including domains like cronoze[.]com and muuxxu[.]com.
Another campaign, active between February 12 and 28, 2025, targeted over 2,300 organizations, primarily in the engineering, IT, and consulting sectors in the United States. These emails had empty bodies but contained unique PDF attachments with QR codes. The QR codes redirected to a hyperlink associated with the RaccoonO365 phishing-as-a-service (PhaaS) platform, specifically to a domain like shareddocumentso365cloudauthstorage[.]com. The URL contained the recipient’s email as a query string parameter, suggesting a targeted credential phishing attack mimicking Microsoft 365 sign-in pages. The emails used various display names to appear legitimate, such as “EMPLOYEE TAX REFUND REPORT” and “Client Contract Negotiation Service Agreement”.
A third campaign, observed on February 13, 2025, utilized an IRS-themed email with the subject “IRS Refund Eligibility Notification”. The email, purportedly from jessicalee@eboxsystems[.]com, contained a hyperlink that abused an open redirector on a Google Business page to direct users to a malicious Excel file (Tax_Refund_Eligibility_Document[.]xlsm) hosted on the likely compromised domain historyofpia[.]com. If the user opened the Excel file and enabled macros, a malicious MSI file was downloaded and executed from hxxps://acusense[.]ae/umbrella/. This MSI file contained a legitimate copy of AutoNotify.exe (used for AutoHotKey scripts) and a malicious AutoNotify.ahk script, which is an AHKBot Looper. The AHKBot Looper is designed to receive and run additional AutoHotKey scripts, and in this instance, it downloaded the Screenshotter module, enabling the capture of screenshots from the compromised device. Both the Looper and Screenshotter communicated with the C2 IP address 181.49.105[.]59.
A fourth campaign, observed on March 3, 2025, targeted CPAs and accountants in the United States with tax-themed phishing emails designed to deliver GuLoader and Remcos malware. This campaign employed a two-stage approach, beginning with a benign “rapport-building” email from a fake persona requesting tax filing services. If the recipient replied, a second email containing a malicious PDF attachment was sent. The malicious PDF contained an embedded URL that, when clicked, downloaded a ZIP file from Dropbox. This ZIP file contained various .lnk files disguised as tax documents. If launched, these .lnk files used PowerShell to download a PDF and a .bat file. The .bat file then downloaded the GuLoader executable, which subsequently installed the Remcos RAT.
GuLoader is an evasive malware downloader known for using encrypted shellcode, process injection, and cloud-based hosting for delivering payloads. It incorporates anti-analysis techniques like sandbox detection and API obfuscation. Remcos is a RAT that grants attackers comprehensive control over infected systems through keylogging, screen capturing, and process manipulation, while also employing stealth techniques to avoid detection. The Remcos campaign utilized a C2 domain of newsbloger1.duckdns[.]org.
Countries
United States
Industries
Engineering IT Consulting CPAs and accountants
Recommendations
- Educate users about protecting personal and business information on social media, filtering unsolicited communication, identifying lure links in phishing emails, and reporting suspicious activity.
- Turn on Zero-hour auto purge (ZAP) in Defender for Office 365 to quarantine sent mail based on new threat intelligence.
- Pilot and deploy phishing-resistant authentication methods.
- Enforce multifactor authentication (MFA) on all accounts and devices.
- Implement Entra ID Conditional Access authentication strength to require phishing-resistant authentication for critical apps.
- Encourage users to use web browsers with Microsoft Defender SmartScreen enabled.
- Educate users on validating browser URLs.
- Enable network protection to block access to malicious domains.
- Configure Microsoft Defender for Office 365 to recheck links on click using Safe Links.
- Turn on cloud-delivered protection in Microsoft Defender Antivirus or equivalent antivirus products.
- Enable investigation and remediation in full automated mode in Defender for Endpoint.
- Run endpoint detection and response (EDR) in block mode.
- Microsoft Defender XDR customers can refer to the list of applicable detections.
- Customers with provisioned access can use Microsoft Security Copilot for investigation and response.
Hunting methods
Microsoft Sentinel Hunting Queries:
- Hunt normalized Network Session events using the ASIM unifying parser
_Im_NetworkSessionfor IOCs:let lookback = 7d; let ioc_ip_addr = dynamic(["181.49.105.59 "]); _Im_NetworkSession(starttime=todatetime(ago(lookback)), endtime=now()) | where DstIpAddr in (ioc_ip_addr) | summarize imNWS_mintime=min(TimeGenerated), imNWS_maxtime=max(TimeGenerated), EventCount=count() by SrcIpAddr, DstIpAddr, DstDomain, Dvc, EventProduct, EventVendorLogic: This query searches network session logs within the last 7 days for connections where the destination IP address matches the AHKBot C2 IP address (
181.49.105[.]59). It summarizes the findings by source IP, destination IP, destination domain, device, event product, and vendor, providing a count of events and the first and last time the IOC was observed. - Hunt normalized File events using the ASIM unifying parser
imFileEventfor IOCs:let ioc_sha_hashes=dynamic(["fe0b2e0fe7ce26ae398fe6c36dae551cb635696c927761738f040b581e4ed422","bb3b6262a288610df46f785c57d7f1fa0ebc75178c625eaabf087c7ec3fccb6a","9728b7c73ef25566cba2599cb86d87c360db7cafec003616f09ef70962f0f6fc", "3c482415979debc041d7e4c41a8f1a35ca0850b9e392fecbdef3d3bc0ac69960","165896fb5761596c6f6d80323e4b5804e4ad448370ceaf9b525db30b2452f7f5","a31ea11c98a398f4709d52e202f3f2d1698569b7b6878572fc891b8de56e1ff7", "a1b4db93eb72a520878ad338d66313fbaeab3634000fb7c69b1c34c9f3e17727","0b22a0d84afb8bc4426ac3882a5ecd2e93818a2ea62d4d5cbae36d942552a36a","4d5839d70f16e8f4f7980d0ae1758bb5a88b061fd723ea4bf32b4b474c222bec","9bffe9add38808b3f6021e6d07084a06300347dd5d4b7e159d97e949735cff1e"]); imFileEvent | where SrcFileSHA256 in (ioc_sha_hashes) or TargetFileSHA256 in (ioc_sha_hashes) | extend AccountName = tostring(split(User, @'\')), AccountNTDomain = tostring(split(User, @'\')) | extend AlgorithmType = "SHA256"Logic: This query searches file event logs for any events where the source or target file’s SHA-256 hash matches any of the provided malicious file hashes associated with the campaigns (including PDFs, JavaScript, MSI, and Excel files). It also extracts account and domain information and specifies the hash algorithm.
- Hunt normalized Web Session events using the ASIM unifying parser
_Im_WebSessionfor IOCs:let lookback = 7d; let ioc_domains = dynamic(["slgndocline.onlxtg.com ", "cronoze.com ", "muuxxu.com ", "proliforetka.com ", "porelinofigoventa.com ", "shareddocumentso365cloudauthstorage.com", "newsbloger1.duckdns.org"]); _Im_WebSession (starttime=ago(lookback), eventresult='Success', url_has_any=ioc_domains) | summarize imWS_mintime=min(TimeGenerated), imWS_maxtime=max(TimeGenerated), EventCount=count() by SrcIpAddr, DstIpAddr, Url, Dvc, EventProduct, EventVendorLogic: This query searches web session logs within the last 7 days for successful web requests (
eventresult='Success') where the URL contains any of the listed malicious domains associated with the various phishing campaigns (fake DocuSign, BRc4 C2, Latrodectus C2, RaccoonO365, Remcos C2). It summarizes the findings by source IP, destination IP, full URL, device, event product, and vendor. - Phishing link click observed in Network Traffic (Query not provided, but the title indicates a potential hunting method).
- Email Link Execution with Alert Correlation (Query not provided, but the title indicates a potential hunting method).
IOC
Hashes
9bffe9add38808b3f6021e6d07084a06300347dd5d4b7e159d97e949735cff1e
0b22a0d84afb8bc4426ac3882a5ecd2e93818a2ea62d4d5cbae36d942552a36a
4d5839d70f16e8f4f7980d0ae1758bb5a88b061fd723ea4bf32b4b474c222bec
a1b4db93eb72a520878ad338d66313fbaeab3634000fb7c69b1c34c9f3e17727
a31ea11c98a398f4709d52e202f3f2d1698569b7b6878572fc891b8de56e1ff7
165896fb5761596c6f6d80323e4b5804e4ad448370ceaf9b525db30b2452f7f5
3c482415979debc041d7e4c41a8f1a35ca0850b9e392fecbdef3d3bc0ac69960
9728b7c73ef25566cba2599cb86d87c360db7cafec003616f09ef70962f0f6fc
bb3b6262a288610df46f785c57d7f1fa0ebc75178c625eaabf087c7ec3fccb6a
fe0b2e0fe7ce26ae398fe6c36dae551cb635696c927761738f040b581e4ed422
Domains
rebrand[.]ly
slgndocline[.]onlxtg[.]com
cronoze[.]com
muuxxu[.]com
proliforetka[.]com
porelinofigoventa[.]com
shareddocumentso365cloudauthstorage[.]com
historyofpia[.]com
acusense[.]ae
dropbox[.]com
newsbloger1.duckdns[.]org
royalegroupnyc[.]com
URLs
hxxp://rebrand[.]ly/243eaa
hxxp://slgndocline[.]onlxtg[.]com/87300038978/
hxxps://rosenbaum[.]live/bars.php
hxxps://business.google[.]com/website_shared/launch_bw[.]html?f=hxxps://historyofpia[.]com/Tax_Refund_Eligibility_Document[.]xlsm
hxxps://historyofpia[.]com/Tax_Refund_Eligibility_Document[.]xlsm
hxxps://acusense[.]ae/umbrella/
hxxps://www.dropbox[.]com/scl/fi/ox2fv884k4mhzv05lf4g1/2024-Tax-Document.zip?rlkey=fjtynsx5c5ow59l4zc1nsslfi&st=gvfamzw3&dl=1
IP Addresses
181.49.105[.]59
Original link: https://www.microsoft.com/en-us/security/blog/2025/04/03/threat-actors-leverage-tax-season-to-deploy-tax-themed-phishing-campaigns/