The Feed 2025-04-18

AI Generated Podcast
Summarized Stories
-
Windows Process Cloning — How to dump a process without dumping the process: This article illustrates the use of the
NtCreateProcessExsyscall withPROCESS_CREATE_PROCESSto clone a process, enabling memory dumping of the clone without requiring direct read access to the original process. -
Inside Gamaredon’s PteroLNK: Dead Drop Resolvers and evasive Infrastructure: This analysis provides a technical breakdown of Gamaredon’s PteroLNK malware, focusing on its use of VBScript, dead drop resolvers for command and control, and targeting of Ukrainian entities [Inside Gamaredon’s PteroLNK: Dead Drop Resolvers and evasive Infrastructure].
-
The Definitive Guide To Process Cloning on Windows: This guide offers a detailed exploration of Windows process cloning using various APIs, highlighting the security implications for covert activities such as memory dumping [The Definitive Guide To Process Cloning on Windows].
-
Threat actors misuse Node.js to deliver malware and other malicious payloads: This blog post from Microsoft details recent campaigns starting in October 2024 where threat actors are increasingly using Node.js to deliver malware for information theft, employing techniques such as malvertising to distribute malicious installers and inline script execution.
Windows Process Cloning — How to dump a process without dumping the process
Summary
Windows Process Cloning is a technique that leverages inherent operating system functionalities to create a copy (clone) of a running process. This allows for inspection and manipulation of the cloned process’s memory and resources without directly interacting with the original target process in ways that are typically monitored by security solutions. The research highlights that by using specific process creation syscalls, particularly NtCreateProcessEx, with only PROCESS_CREATE_PROCESS access to a target process, an attacker can create a clone that inherits the target’s memory space. This cloned process can then be examined or its memory dumped, effectively bypassing security measures that focus on monitoring sensitive access rights like PROCESS_VM_READ or interactions with well-known memory dumping tools on the original process. This technique poses a significant risk for stealthy information gathering, such as credential dumping from LSASS, and circumvents certain anti-virus and anti-cheat mechanisms that rely on monitoring specific API calls and access rights to sensitive processes. The underlying principle relies on the ‘inherit by default’ behavior of the fork()-like functionality, where the programmer (in this case, the attacker) can exploit the inherited state of the cloned process.
Technical Details
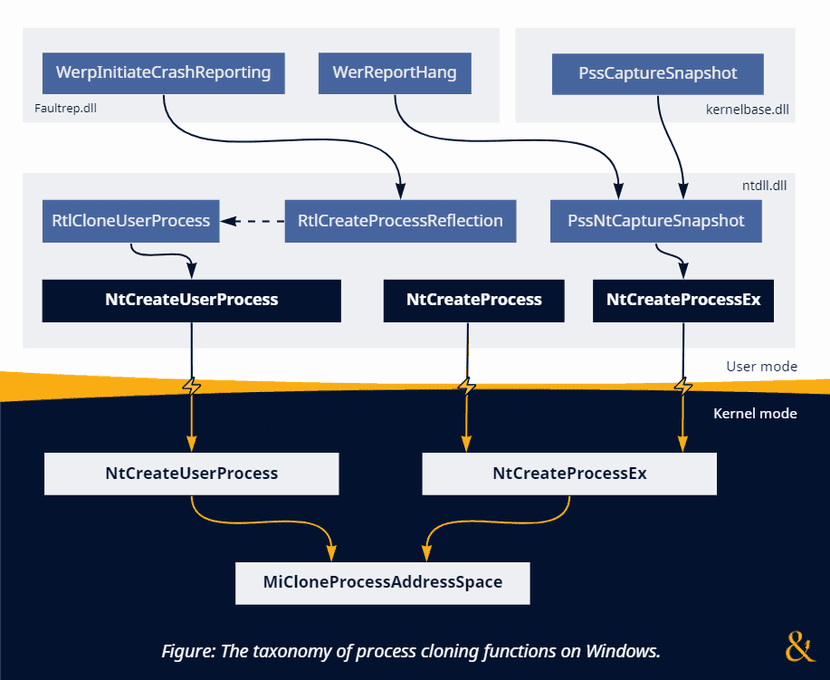
Windows offers functionalities that resemble the fork() system call found in Unix-like operating systems, primarily through the ability to clone the address space of a given process. While not widely known, this capability can be abused for offensive purposes, such as stealthy memory dumping and potentially other malicious operations.
Traditionally, accessing information about a running process requires opening a handle to it using the OpenProcess API and specifying a combination of process access rights. Common access rights associated with potentially malicious operations include PROCESS_ALL_ACCESS, PROCESS_CREATE_THREAD, PROCESS_DUP_HANDLE, PROCESS_SET_INFORMATION, PROCESS_SUSPEND_RESUME, PROCESS_TERMINATE, PROCESS_VM_OPERATION, PROCESS_VM_READ, and PROCESS_VM_WRITE. Security products often monitor attempts to open handles with these rights, especially to sensitive processes like LSASS.
However, researchers have identified that certain process access rights, such as PROCESS_CREATE_PROCESS, PROCESS_QUERY_INFORMATION, PROCESS_QUERY_LIMITED_INFORMATION, and PROCESS_SET_QUOTA, are often largely ignored by security filters. The PROCESS_CREATE_PROCESS right, which is required to create a process, can be abused in the context of process cloning.
The primary syscalls involved in process creation and cloning are NtCreateUserProcess and the legacy NtCreateProcessEx. NtCreateUserProcess is a higher-level API that understands filenames, parses executables, writes process parameters, and always creates an initial thread. Before Windows Vista, CreateProcess relied on NtCreateProcessEx, which still exists for backward compatibility. NtCreateProcessEx operates with memory projection objects (image sections) instead of filenames, is unaware of process parameters, and does not create threads.
A lesser-documented technique allows forking (cloning) of processes on Windows using the undocumented function RtlCloneUserProcess, which is a wrapper around NtCreateUserProcess. A minimal implementation of forking via NtCreateUserProcess involves calling it with NULL object attributes, process parameters, an empty create info argument, and a NULL attribute list, resulting in a clone of the current process that inherits private memory regions and inheritable handles.
A novel approach involves forking a remote process using only a PROCESS_CREATE_PROCESS handle. By using the legacy NtCreateProcess(Ex) variant and passing NULL for the SectionHandle and a PROCESS_CREATE_PROCESS handle of the target for the ParentProcess arguments, a fork of the remote process can be created. Crucially, if no threads are created in the forked process, no process creation callbacks might be triggered, allowing stealthy access to the target’s memory.
Similarly, with the modern NtCreateUserProcess variant, an attacker can achieve remote forking by using the minimal local forking implementation but passing the target process handle as a PsAttributeParentProcess in the attribute list.
The created child process inherits the virtual address space of the parent, enabling memory inspection without requiring PROCESS_VM_READ. This technique is particularly relevant for dumping sensitive process memory, such as that of LSASS, to extract credentials. Instead of directly accessing LSASS with monitored rights, an attacker can create a clone of LSASS using only PROCESS_CREATE_PROCESS and then dump the memory of the clone. The MiniDumpWriteDump API can be used on the forked child to create a memory dump.
The stealth benefits of this approach include:
- Avoiding the need for
PROCESS_VM_READandPROCESS_QUERY_INFORMATIONon the target process, which are commonly monitored. - Potentially bypassing Ps-callbacks because no new threads are created in certain implementations (e.g., when using
NtCreateProcessExwithout creating threads).
However, process forking has limitations. Attackers are generally restricted to processes running at the same privilege level. Also, security solutions might attempt to remediate this by filtering or stripping PROCESS_CREATE_PROCESS handles, although this could cause compatibility issues.
The use of NtCreateProcessEx for memory dumping offers advantages over RtlCreateProcessReflection (another cloning-related API) in terms of stability and stealth, as it doesn’t intrude into the target process, works on frozen processes, relies on less-monitored rights, and doesn’t trigger Ps-callbacks.
Memory tampering is also a potential consequence. If the parent process has writable mapped memory regions, the clone can inherit these views and potentially modify the underlying storage, offering a limited PROCESS_VM_WRITE-like primitive.
Recommendations
- Security vendors should audit the usage of
PROCESS_CREATE_PROCESSwithin customer environments and consider limiting or filtering this access right for sensitive processes where appropriate. However, they should be aware of potential compatibility issues that such changes might introduce. - Organizations should monitor for anomalous process creation events, even those that do not involve typical malicious access rights like
PROCESS_VM_READ. - Endpoint Detection and Response (EDR) solutions should consider monitoring the use of
NtCreateProcessExwith a parent process handle and a NULL section handle, especially when the target process is a sensitive one like LSASS. - Investigate processes that obtain
PROCESS_CREATE_PROCESShandles to sensitive processes without requesting other commonly monitored access rights.
Hunting methods
-
Behavioral Monitoring: Look for processes that create child processes of sensitive processes (e.g., LSASS) using
NtCreateProcessExwhere the section handle is NULL and the only requested access right to the parent isPROCESS_CREATE_PROCESS. - API Call Tracing: Monitor for sequences of API calls:
OpenProcessbeing called on a sensitive process (e.g., LSASS) with onlyPROCESS_CREATE_PROCESSaccess requested.- Subsequent calls to
NtCreateProcessExwith the handle obtained in the previous step as theParentProcessargument and NULL for theSectionHandleargument. - Following this, monitor for memory dumping operations (e.g.,
MiniDumpWriteDump) where the process handle being dumped is the newly created child process rather than the original target process.
- Sigma Rule Example (Conceptual):
```sigma
detection:
selection_openprocess:
EventID: 8 # Sysmon Process Access
TargetImage: ‘C:\Windows\System32\lsass.exe’
GrantedAccess: ‘0x0010’ # PROCESS_CREATE_PROCESS
CallTrace: ‘\ntdll.dll!NtOpenProcess’
selection_createprocex:
EventID: 1 # Sysmon Process Creation
ParentProcessImage: (Image of the process that opened LSASS with PROCESS_CREATE_PROCESS)
TargetImage: ‘’
CallTrace: ‘\ntdll.dll!NtCreateProcessEx’
Details: ‘SectionHandle=NULL’
Details: ‘ParentProcessHandle=’ # Match the handle from the OpenProcess event
selection_dump:
EventID: 10 # Sysmon Process Access (for MiniDumpWriteDump on the cloned process)
TargetImage: (Image of the cloned LSASS process)
GrantedAccess: ‘0x001F0FFF’ # Access rights associated with dumping (example)
CallTrace: ‘\dbghelp.dll!MiniDumpWriteDump’
condition: selection_openprocess and selection_createprocex and selection_dump
fields:
- TargetImage
- ParentProcessImage
- GrantedAccess
- CallTrace
```
Logic: This conceptual Sigma rule attempts to detect a sequence of events where a process opens LSASS with only
PROCESS_CREATE_PROCESSrights, then usesNtCreateProcessExwith a NULL section handle and the LSASS handle as the parent, and subsequently the newly created process’s memory is dumped usingMiniDumpWriteDump. This requires correlating process creation and access events.
Original link:
- https://billdemirkapi.me/abusing-windows-implementation-of-fork-for-stealthy-memory-operations/
- https://www.huntandhackett.com/blog/the-definitive-guide-to-process-cloning-on-windows
- https://captain-woof.medium.com/windows-process-cloning-how-to-dump-a-process-without-dumping-the-process-f3101cbea2e1
Inside Black Basta: Ransomware Resilience and Evolution After the Leak
Summary
Analysis of leaked internal communications from the Black Basta ransomware group, coinciding with Microsoft Threat Intelligence’s report in Q1 2025, reveals the group’s continued operational status and adaptive nature despite the exposure of their internal workings. The leak provides unprecedented insight into their methods, which closely align with tactics, techniques, and procedures (TTPs) attributed by Microsoft to threat actors like Storm-1674, Storm-1811, and Storm-2410. Black Basta demonstrates resilience through infrastructure rotation, segmented botnets, and careful attack timing. Their methods include exploiting hybrid cloud infrastructure and leveraging social engineering at scale, particularly impersonating IT support. The observed persistence and evolution of Black Basta, even under public scrutiny, underscore the need for enhanced detection mechanisms, proactive cloud security measures, and increased awareness of social engineering threats. Despite the leak, Black Basta continues to function as a high-tier closed Ransomware-as-a-Service (RaaS) collective.
Technical Details
The Black Basta group leverages a variety of techniques for initial access, lateral movement, and payload delivery. A key aspect is the exploitation of known services and infrastructure, including Citrix and VPN portals, weak authentication on ESXi hypervisors, and compromised Jenkins instances. The chat logs reveal discussions and sharing of infrastructure specifically targeting these vulnerabilities, such as a bot identified as exploiting Citrix and direct references to ESXi servers with easily guessable passwords. Reconnaissance using tools like Shodan and FOFA is also indicated for identifying exposed Jenkins infrastructure.
Credential harvesting and reuse are significant components of their operations. The leaked chats contain substantial dumps of RDP and VPN portal credentials, as well as mentions of sslvpn_logon.shtml endpoints with administrative usernames, suggesting brute-force or credential stuffing attacks against VPNs.
Social engineering, particularly voice-based IT spoofing, is actively coordinated by the actors. This aligns with Microsoft’s attribution of fake IT helpdesk calls to Storm-2410 and Storm-1674. The group discusses making phone calls appear to originate from IT departments, indicating a focus on refining these pretexts and potentially incorporating automation or deepfakes in the future.
For command-and-control, scripting, and obfuscation, the group utilizes PowerShell-based and loader-based execution. Examples include the use of rundll32.exe to execute DLLs and VBScript downloaders. This supports Microsoft’s observations regarding Noiserv-like C2 channels and the use of both public and custom tools. They also coordinate bots and SOCKS proxies for remote access and persistence. The use of obfuscated commands via tools like PowerShell and rundll32.exe demonstrates a move towards stealthier attack delivery.
Black Basta exhibits a focus on anti-detection and operational security. Actors monitor the blacklisting of their infrastructure and deliberately throttle delivery volumes to evade detection. Discussions about rotating delivery domains and staging different botnets for specific functions further highlight their emphasis on infrastructure resilience. The careful pacing of attacks to avoid detection, especially in phishing and initial access stages, is a key operational security consideration.
Internal coordination within the group suggests a structured workflow and potential for scalability. Discussions around test windows, coordinated timings, role distribution, and infrastructure segmentation (e.g., avoiding overloading specific bot groups) indicate a sophisticated level of organization, mirroring advanced affiliate models within the RaaS ecosystem.
The observed TTPs strongly correlate with Microsoft-attributed activity:
- Storm-1674: Use of PowerShell, C2 infrastructure like Noiserv, ESXi/Citrix exploitation.
- Storm-2410: Social engineering via fake IT calls explicitly coordinated in the logs for initial access.
- Storm-1811: Shared infrastructure, with actor drop-off mirroring observed silence post-February.
The continued focus on misconfigured ESXi environments and unpatched Citrix SSL VPN instances, increased use of fake IT support, resilient payload delivery via simple scripts and multi-hosting, and increasing adversary operational security are anticipated tactical evolutions.
Recommendations
Defenders should focus on targeted detection of the TTPs observed in the Black Basta leaks. Proactive hardening of cloud and hybrid infrastructure, particularly Citrix and ESXi environments, is crucial. Heightened vigilance around social engineering threats, especially voice phishing and fake IT support scenarios, is necessary. Organizations should implement robust credential management practices and monitor for unauthorized access attempts to VPN and RDP portals. Detecting and blocking the execution of commodity malware delivery tools like PowerShell and VBScript in suspicious contexts is also recommended. Monitoring for the use of remote access tools and the deletion of shadow copies can help identify active ransomware infections. Implementing and regularly updating detection rules, such as the Sigma rules provided, is a key technical recommendation.
Hunting methods
The source provides several Sigma rules for threat hunting, which can be implemented in SIEM or EDR solutions:
1. Suspicious Citrix/VPN Portal Access:
title: Suspicious Citrix/VPN Portal Access
id: 1a2b3c4d-5e6f-7g8h-9i0j-k1l2m3n4o5p6
status: experimental
description: Detects potential unauthorized access to Citrix and VPN portals.
author: Your Name
date: 2025-04-17
logsource:
category: network
product: windows
detection:
selection:
EventID: 4625
TargetUserName|contains: ["Citrix", "VPN"]
condition: selection
fields:
- TargetUserName
- WorkstationName
- SourceNetworkAddress
- FailureReason
level: high
Logic: This rule looks for Windows security event ID 4625 (an account failed to log in) where the target username contains “Citrix” or “VPN”. This can indicate brute-force or credential stuffing attempts against these critical access points.
2. Abuse of ESXi Hypervisors:
title: Suspicious ESXi Hypervisor Access Attempts
id: 2b3c4d5e-6f7g-8h9i-0j1k-l2m3n4o5p6q7
status: experimental
description: Detects potential unauthorized access attempts to ESXi hypervisors.
author: Your Name
date: 2025-04-17
logsource:
category: network
product: linux
detection:
selection:
EventID: 4625
TargetUserName|contains: ["root", "admin"]
WorkstationName|contains: ["esxi"]
condition: selection
fields:
- TargetUserName
- WorkstationName
- SourceNetworkAddress
- FailureReason
level: high
Logic: This rule monitors for failed login attempts (EventID 4625) on Linux systems where the target username is “root” or “admin” and the workstation name contains “esxi”. This aims to detect potential brute-force attacks or unauthorized access attempts to ESXi hypervisors, often targeted with weak credentials.
3. Use of Remote Access Tools:
title: Execution of Remote Access Tools
id: 3c4d5e6f-7g8h-9i0j-1k2l-m3n4o5p6q7r8
status: experimental
description: Detects the execution of remote access tools which may indicate unauthorized access.
author: Your Name
date: 2025-04-17
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith:
- '\AnyDesk.exe'
- '\TeamViewer.exe'
- '\RemoteUtilities.exe'
condition: selection
fields:
- Image
- CommandLine
- ParentImage
- User
level: medium
Logic: This rule detects the creation of processes with image paths ending in the names of common remote access tools like AnyDesk, TeamViewer, and Remote Utilities. While these tools have legitimate uses, their execution in unexpected contexts can indicate unauthorized access.
4. Obfuscated PowerShell Commands:
title: Obfuscated PowerShell Command Execution
id: 4d5e6f7g-8h9i-0j1k-2l3m-n4o5p6q7r8s9
status: experimental
description: Detects execution of obfuscated PowerShell commands.
author: Your Name
date: 2025-04-17
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith: '\powershell.exe'
CommandLine|contains:
- 'FromBase64String'
- 'Invoke-Expression'
condition: selection
fields:
- Image
- CommandLine
- ParentImage
- User
level: high
Logic: This rule identifies PowerShell processes where the command line contains “FromBase64String” or “Invoke-Expression” (or its alias “IEX”). These keywords are often used to execute obfuscated PowerShell scripts, a common tactic for evading detection.
5. Ransom Note File Creation:
title: Ransom Note File Creation
id: 5e6f7g8h-9i0j-1k2l-3m4n-o5p6q7r8s9t0
status: experimental
description: Detects creation of ransom note files commonly used by ransomware.
author: Your Name
date: 2025-04-17
logsource:
category: file_creation
product: windows
detection:
selection:
FileName|contains:
- 'readme.txt'
- 'instructions.html'
- 'decrypt_files.txt'
condition: selection
fields:
- FileName
- FolderPath
- User
- ComputerName
level: high
Logic: This rule monitors for the creation of files with names commonly used for ransom notes, such as “readme.txt”, “instructions.html”, and “decrypt_files.txt”. The creation of such files is a strong indicator of ransomware activity.
6. CVE-2023–4966 Exploitation Attempt Citrix ADC Sensitive Information Disclosure:
title: CVE-2023-4966 Exploitation Attempt - Citrix ADC Sensitive Information Disclosure
id: ff349b81-617f-4af4-924f-dbe8ea9bab41
status: test
description: Detects potential exploitation attempt of CVE-2023-4966 via proxy logs.
author: Nasreddine Bencherchali (Nextron Systems), Michael Haag (STRT)
date: 2023-11-28
references:
- https://support.citrix.com/article/CTX579459
- https://attackerkb.com/topics/2faW2CxJgQ/cve-2023-4966
- https://www.rapid7.com/blog/post/2023/10/25/etr-cve-2023-4966-exploitation-of-citrix-netscaler-information-disclosure-vulnerability/
- https://www.assetnote.io/resources/research/citrix-bleed-leaking-session-tokens-with-cve-2023-4966
- https://github.com/assetnote/exploits/tree/main/citrix/CVE-2023-4966
tags:
- detection.emerging-threats
- attack.initial-access
- attack.t1190
- cve.2023-4966
logsource:
category: proxy
detection:
selection:
cs-method: 'GET'
cs-uri|contains: '/oauth/idp/.well-known/openid-configuration'
sc-status: 200
condition: selection
falsepositives:
- Vulnerability scanners
level: medium
Logic: This rule looks for specific HTTP GET requests to the /oauth/idp/.well-known/openid-configuration URI with a 200 OK status code in proxy logs. This pattern is indicative of an attempt to exploit CVE-2023–4966, a Citrix ADC vulnerability that allows sensitive information disclosure.
7. Remote Access Tool Services Installation:
title: Remote Access Tool Services Have Been Installed - System
id: 1a31b18a-f00c-4061-9900-f735b96c99fc
status: test
description: Detects service installation of different remote access tools software.
author: Connor Martin, Nasreddine Bencherchali
date: 2022-12-23
modified: 2023-06-22
tags:
- attack.persistence
- attack.t1543.003
- attack.t1569.002
logsource:
category: system
product: windows
detection:
selection:
ServiceName|contains:
- 'AnyDesk'
- 'TeamViewer'
- 'UltraVNC'
- 'NetSupport'
condition: selection
falsepositives:
- Legitimate installations of remote access tools
level: medium
Logic: This rule monitors system logs for the installation of services associated with known remote access tools like AnyDesk, TeamViewer, UltraVNC, and NetSupport. Installation of these services without legitimate reason can indicate malicious persistence mechanisms.
8. Outbound Network Connection To Public IP Via Winlogon:
title: Outbound Network Connection To Public IP Via Winlogon
id: 7610a4ea-c06d-495f-a2ac-0a696abcfd3b
status: test
description: Detects a "winlogon.exe" process that initiates network communications with public IP addresses.
author: Christopher Peacock @securepeacock, SCYTHE @scythe_io
date: 2023-04-28
modified: 2024-03-12
tags:
- attack.defense-evasion
- attack.execution
- attack.command-and-control
- attack.t1218.011
logsource:
category: network_connection
product: windows
detection:
selection:
Image: 'C:\Windows\System32\winlogon.exe'
DestinationIp|cidr:
- '0.0.0.0/0'
condition: selection
falsepositives:
- Legitimate remote desktop connections
level: high
Logic: This rule identifies network connections initiated by the winlogon.exe process to public IP addresses. While winlogon.exe is a legitimate Windows process, it is not typically expected to establish direct connections to external IPs, making such activity potentially suspicious.
9. Suspicious PowerShell Execution:
title: Suspicious PowerShell Execution
id: cbd8e156-dc48-4dbf-939f-62e8c7b27b60
status: experimental
description: Detects execution of potentially malicious PowerShell commands used in ransomware attacks.
author: Abhinav Pandey
date: 2024-11-19
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith: '\powershell.exe'
CommandLine|contains:
- '-enc'
- '-e'
- 'Invoke-Expression'
- 'IEX'
condition: selection
fields:
- Image
- CommandLine
- ParentImage
- User
level: high
Logic: Similar to rule #4, this rule focuses on detecting PowerShell execution with command-line parameters like -enc or -e (for encoded commands) and Invoke-Expression or IEX, which are commonly used to execute malicious and obfuscated PowerShell code in ransomware attacks.
10. Ransomware File Extension Creation:
title: Ransomware File Extension Creation
id: 05329b66-1eb3-47fd-a8f1-c5c58e1d5ef7
status: experimental
description: Detects creation of files with extensions indicative of ransomware encryption.
author: Abhinav Pandey
date: 2024-11-19
logsource:
category: file_creation
product: windows
detection:
selection:
FileName|endswith:
- '.ransom'
- '.basta'
condition: selection
fields:
- FileName
- FolderPath
- User
- ComputerName
level: high
Logic: This rule monitors for the creation of files with specific extensions, .ransom and .basta, which are known to be used by the Black Basta ransomware to mark encrypted files.
11. Execution of Remote Access Tools:
title: Execution of Remote Access Tools
id: 8a5c8e42-39dc-4c4f-a5b6-96bf5dbd93c9
status: experimental
description: Detects execution of tools like AnyDesk, Quick Assist, or related payloads.
author: Abhinav Pandey
date: 2024-11-19
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith:
- '\AnyDesk.exe'
- '\QuickAssist.exe'
- '\AntispamAccount.exe'
- '\AntispamUpdate.exe'
- '\AntispamConnectUS.exe'
condition: selection
fields:
- Image
- CommandLine
- ParentImage
- User
level: high
Logic: This rule expands on rule #3 by also including detection for the execution of Quick Assist and other potentially malicious executables like AntispamAccount.exe, AntispamUpdate.exe, and AntispamConnectUS.exe, which have been associated with unauthorized access.
12. Shadow Copy Deletion via vssadmin:
title: Shadow Copy Deletion via vssadmin
id: 100012
status: experimental
description: Detects usage of vssadmin.exe to delete shadow copies.
author: Wazuh Team
date: 2024-11-19
logsource:
category: process_creation
product: windows
detection:
selection:
Image|endswith: '\vssadmin.exe'
CommandLine|contains:
- 'delete'
- 'shadows'
condition: selection
fields:
- Image
- CommandLine
- ParentImage
- User
level: high
Logic: This rule detects the execution of vssadmin.exe with command-line arguments “delete” and “shadows”. Ransomware often uses this command to delete shadow copies, making system recovery more difficult.
13. Creation of Ransom Note Files:
title: Creation of Ransom Note Files
id: 100013
status: experimental
description: Detects creation of ransom note files commonly used by ransomware.
author: Wazuh Team
date: 2024-11-19
logsource:
category: file_creation
product: windows
detection:
selection:
FileName|contains:
- 'readme.txt'
- 'instructions.html'
- 'decrypt_files.txt'
condition: selection
fields:
- FileName
- FolderPath
- User
- ComputerName
level: high
Logic: This rule is identical in logic to rule #5, monitoring for the creation of common ransomware note filenames.
IOC
Domains
temp.sh
send.vis.ee
IP Addresses
80.190.xxx.x
13.57.243.97
58.171.144.24
79.141.1.193
5.8.18.20
URLs (potential IOCs - for reconnaissance/access)
https://darpan.kvs.REDACTED.in/rdweb/...;KVS@DLREDACTED
https://start.elvyonline.nl/...;sdejong@elvyonline;e4256ohN
https://79.141.1.193/sslvpn_logon.shtml
http:/58.171.144.24:10002/ui/
http://temp.sh/ctGHj/downloader.vbs
Original link: https://detect.fyi/inside-black-basta-ransomware-resilience-and-evolution-after-the-leak-1fd691e7cade?source=rss—-d5fd8f494f6a—4
Inside Gamaredon’s PteroLNK: Dead Drop Resolvers and evasive Infrastructure
Summmary
This report, TRR250401, details an analysis of the Gamaredon group’s PteroLNK VBScript malware and its associated infrastructure, observed between late 2024 and mid-March 2025. The research proactively identified samples related to the Pterodo malware family, commonly attributed to the Russian-nexus Gamaredon threat actor, on a public malware analysis platform. The continued daily updates to related Gamaredon Dead Drop Resolvers (DDRs) underscore the ongoing nature of their operations. While ESET previously documented the broader Pterodo ecosystem for the 2022-2023 period, public analysis of the specific samples discussed in this report was previously unavailable. The report emphasizes Gamaredon’s consistent use of heavily obfuscated VBScripts and a modular malware structure involving downloaders and LNK droppers. The group demonstrates flexibility in their operations by easily modifying parameters like file names, persistence mechanisms, and anti-detection logic. Their infrastructure relies heavily on frequently updated Dead Drop Resolvers hosted on platforms like Telegraph and Teletype, often pointing to Cloudflare quick tunnel addresses. Victimology data suggests a focus on Ukrainian targets, aligning with Gamaredon’s well-established targeting patterns. The analysis further strengthens the attribution to Gamaredon through consistent TTPs, infrastructure usage (like REGRU-RU registrar and ntuser.dat.tmcontainer filenames), and victimology aligning with their historical campaigns and suspected ties to Russia’s FSB. The report concludes that Gamaredon remains a significant component of Russia’s cyber operations against Ukraine, leveraging adaptability and redundancy over advanced technical sophistication.
Technical Details
The analyzed PteroLNK malware employs a multi-stage execution process initiated by a heavily obfuscated VBScript file. Upon execution, the primary script dynamically constructs and deploys two additional base64-encoded VBScript payloads: a downloader and an LNK dropper. This modular structure allows for distinct functionalities in the infection chain.
The initial PteroLNK VBScript establishes persistence primarily through scheduled tasks, creating entries to execute the downloader every 3 minutes and the LNK dropper every 9 minutes. It also attempts to conceal its activities by modifying Windows Explorer settings to hide files. The script drops copies of itself to %PUBLIC%\NTUSER.DAT.TMContainer and %APPDATA%\~.drv. The downloader and LNK dropper payloads are dropped as %PUBLIC%\NTUSER.DAT.TMContainer00000000000000000001.regtrans-ms and %PUBLIC%\NTUSER.DAT.TMContainer00000000000000000002.regtrans-ms, respectively.
A notable aspect of the malware’s flexibility is its conditional execution logic based on the presence of the “360 Total Security” antivirus. If detected, the malware shifts its persistence mechanism to an infinite loop instead of scheduled tasks, and file concealment is disabled.
The downloader payload is designed to retrieve and deploy further malware, utilizing a modular, multi-stage structure for C2 communication. It leverages the Windows registry (HKEY_CURRENT_USER\Console\WindowsUpdates for the primary C2 and HKEY_CURRENT_USER\Console\WindowsResponby for the backup C2) to persistently store and retrieve C2 addresses across execution cycles.
Upon execution, the downloader attempts to read existing C2 addresses from these registry keys. It then generates a custom HTTP “User-Agent” string, uniquely identifying the infected machine by including the computer name and system drive serial number, spliced randomly between two predefined templates. The malware checks for internet connectivity by sending a request to a benign website. The error counter mechanism triggers different stages of C2 communication. Initially, if a backup C2 is present, a request is sent to the Ukrainian streaming service sweet.tv. Otherwise, the first request goes to the Ukrainian news site ukr.net and a hardcoded dead drop resolver (DDR) at hxxps://telegra[.]ph/Vizit-12-28. The response from the DDR is parsed using a regular expression (\<address\>\n(.*?)\<\/p\>\<\/article\>) to extract an updated C2 address.
The extracted C2 address, often a Cloudflare quick tunnel address hosted on trycloudflare[.]com (e.g., des-cinema-democrat-san.trycloudflare[.]com), is then contacted using the custom User-Agent. If a 404 status code is received, an updated C2 is extracted from the response. The domain portion is saved in the backup C2 registry key (WindowsResponby), and the URI portion is saved in the WindowsDetect registry key. If errors occur, the C2 domain is also saved in the primary C2 registry key (WindowsUpdates).
If the error counter further increases, the script tries to reach bbc.com while querying another DDR on teletype.in. This DDR address is dynamically constructed using the URI from the previous C2 tunnel response (e.g., @din3/VByOMkbbyIt) and the WindowsDetec registry key, resulting in a URL like hxxps://teletype[.]in/@din3/VByOMkbbyIt?.... A new C2 address is fetched from this DDR using Internet Explorer and parsed with a different regex pattern: \<\!--\[--\>\<\!--\]--\>\<\!--\[--\>(.*?)\<\!--\]--\>\<\/p\>\<\!--\]--\>\<\/article\>\<\!----\>. The extracted address is prepended with https:// and stored in the primary C2 registry key.
In case of further errors, the script attempts to access the Russian news site vesti.ru and uses check-host.net to resolve a hardcoded C2 domain in the format <2-digits>.mahombres[.]ru. The resolved IP address, prefixed with http://, is stored in the primary C2 registry key. On each successful C2 communication, the server response is expected to contain Base64-encoded VBScript payloads, which are decoded and executed on the infected system.
The LNK dropper payload is responsible for lateral movement and persistence within the infected environment. It propagates by replacing existing files and folders on local and network drives with malicious shortcuts while hiding the originals. These shortcuts are designed to execute the main PteroLNK VBScript (~.drv, also copied to the same folder and potentially renamed to ~.tmp or ~.ini if those exist) via mshta.exe.
The LNK dropper modifies the registry to hide hidden files and folders, extensions, and protected operating system files. It enumerates local and mapped drives, targeting .pdf, .docx, and .xlsx files in the root directory. For each targeted file type, it creates a mimicking malicious shortcut and hides the original. To ensure at least two shortcuts are present, the malware uses an array of military-themed decoy filenames in Ukrainian (and their translations) if necessary.
The behavior of the generated shortcuts differs depending on whether they replaced an existing file or were created using a decoy filename. Shortcuts replacing originals attempt to open the original document or folder before executing PteroLNK, while decoy shortcuts directly execute PteroLNK. Both types of shortcuts contain a JavaScript command that uses wscript.exe to execute the PteroLNK script.
Gamaredon’s infrastructure heavily relies on Dead Drop Resolvers (DDRs) hosted on Telegraph and Teletype, which are frequently updated. These DDRs typically point to Cloudflare quick tunnel addresses, offering anonymity and blending with legitimate traffic. The earliest identified DDR was created on December 28, 2024, while dynamic DDR generation continued until at least March 26, 2025. Notably, an early sample from December 25, 2024, directly used the check-host.net technique without initially using a DDR. The threat actor also controls several C2 domains registered via REGRU-RU and hosted on Cloudflare, some of which were flagged as “Suspected Phishing”.
Attribution to Gamaredon is further supported by the reuse of infrastructure, such as the domain nandayo[.]ru resolving to previously known Gamaredon C2 IPs and kimiga[.]ru being linked to past campaigns. The consistent use of ntuser.dat.tmcontainer as payload filenames and the custom User-Agent beacon delimiter format also align with previous Gamaredon activity.
Countries
Ukraine
Industries
Government Military Critical Infrastructure
Recommendations
The report provides actionable detection signatures, complete hashes, and infrastructure indicators for the analyzed samples, which are available on online multi-scanners and the HarfangLab GitHub repository. Security teams can leverage these indicators for detection and blocking. Monitoring for the creation of scheduled tasks related to the identified file paths and registry modifications associated with hiding files and setting C2 addresses are also recommended. Network monitoring for connections to the identified domains, hostnames, and URLs, particularly Cloudflare quick tunnels and Ukrainian websites initially contacted, can help identify potential infections. Organizations should also be vigilant for the creation of LNK files replacing existing documents and folders, especially those using the military-themed decoy filenames.
Hunting methods
Yara Rules:
rule Gamaredon_PteroLNK_VBScript {
meta:
description = "Matches Gamaredon PteroLNK VBScript samples used in early 2025"
references = "TRR250401"
hash = "d5538812b9a41b90fb9e7d83f2970f947b1e92cb68085e6d896b97ce8ebff705"
date = "2025-04-04"
author = "HarfangLab"
context = "file"
strings:
$vbs = "on error resume next" ascii wide
$a1 = "=\"b24gZXJyb3IgcmVzdW1lIG5leHQNC" ascii wide
$b1 = "\"\"%PUBLIC%\"\"" ascii wide
$b2 = "\"\"%APPDATA%\"\"" ascii wide
$b3 = "\"\"REG_DWORD\"\"" ascii wide
condition:
filesize < 400KB
and $vbs in (0..2)
and $a1
and 1 of ($b*)
}
Logic: This rule looks for VBScript files smaller than 400KB containing the string “on error resume next” (often used in malicious VBScripts), a specific base64 encoded string (“=”"b24gZXJyb3IgcmVzdW1lIG5leHQNC”), and at least one of the strings representing the %PUBLIC%, %APPDATA% environment variables, or the string REG_DWORD, all common elements observed in the analyzed PteroLNK VBScripts.
rule Gamaredon_PteroLNK_LNK {
meta:
description = "Matches Gamaredon PteroLNK-generated LNK files used in early 2025"
references = "TRR250401"
hash = "N/A"
date = "2025-04-04"
author = "HarfangLab"
context = "file"
strings:
$a1 = "javascript:eval('w=new%20ActiveXObject(\\\"\"WScript.Shell\\\"\");w.run(\\\"\"wscript.exe //e:vb\"\"+\"\"Script" ascii wide // Non-existing file lnk
$a2 = "javascript:eval('w=new%20ActiveXObject(\\\"\"WScript.Shell\\\"\");w.run(\\\"\"explorer" ascii wide // Existing file/folder lnk
$b1 = "\"\");window.close()')" ascii wide nocase
condition:
filesize < 10KB
and uint32(0) == 0x0000004C // Standard LNK signature
and uint32(4) == 0x00021401 // Expected values for LNK header
and 1 of ($a*)
and $b1
}
Logic: This rule targets LNK files (identified by the standard LNK signature 0x0000004C at the beginning of the file and the expected header value 0x00021401 at offset 4) smaller than 10KB. It looks for specific JavaScript code snippets used in the malicious shortcuts to execute the PteroLNK VBScript (either directly or after attempting to open the original file/folder) and the string ");window.close()'.
IOC
Hashes (SHA-256)
0cec5ca5d2fe9616a275b54ca37f45248e1ed6e15f627d6bffb566ffd6295208
913e2001d1b13711728ff63fa44b720e5a6d464a68be2e3e72a091bd6c245de1
d0b6e053a967db89cd6492beb5202be67b7fd7be8f7eb1d60905310a4bfb9ea8
1bd6df231f94053b33ae6becb9e49894236a123b82e62eaedf566e8d2572e018
1c32b8ee9442e7e6d0e2e61fb15d3beea9db2fe77d2f70b38ce05eab7c6933f6
5062ca28db713d36e2523f0a041ccde2ea563e3d20c436197e8d33ec3025f3be
28166ea98915ce5c07108bae1ae116d7eeab3fceb64d9564dd2d483cdc2c5e1c
d5538812b9a41b90fb9e7d83f2970f947b1e92cb68085e6d896b97ce8ebff705
582075b7d84fd7233359ede009ae5ccd9c05d06087e4eebf2fcde86286a67938
ab7b9e5025b9095a4fcf76dfa5becc12bd219de84bd2a300371cc303af4463f4
A38399ECB70B504573CE708C7A26C306
09958DEBBD3336D374892D92C8939D75
File paths
%PUBLIC%\NTUSER.DAT.TMContainer00000000000000000001.regtrans-ms
%PUBLIC%\NTUSER.DAT.TMContainer00000000000000000002.regtrans-ms
%PUBLIC%\NTUSER.DAT.TMContainer
%APPDATA%\~.drv
Scheduled tasks
\Windows\DeviceDirectoryClient\RegisterUserDevice
\Windows\DeviceDirectoryClient\RegisterDeviceConnectedToNetwork
Registry keys
HKEY_CURRENT_USER\Console\WindowsUpdates
HKEY_CURRENT_USER\Console\WindowsResponby
HKEY_CURRENT_USER\Console\WindowsDetect
Domains
tienes[.]ru
mahombres[.]ru
kimiga[.]ru
areyouall[.]ru
nandayo[.]ru
Hostnames
des-cinema-democrat-san.trycloudflare[.]com
satin-adams-writings-idol.trycloudflare[.]com
such-bad-magnet-dealer.trycloudflare[.]com
chaos-forces-bears-sent.trycloudflare[.]com
cups-technologies-knock-posts.trycloudflare[.]com
cables-encounter-chem-stranger.trycloudflare[.]com
asset-advised-jane-disc.trycloudflare[.]com
recreational-bosnia-granny-interventions.trycloudflare[.]com
governmental-rocket-hourly-blair.trycloudflare[.]com
silence-modems-france-fact.trycloudflare[.]com
extend-terrorism-nowhere-two.trycloudflare[.]com
taking-hl-kerry-pet.trycloudflare[.]com
horizon-fee-calendar-seek.trycloudflare[.]com
rows-slideshow-toll-dsl.trycloudflare[.]com
blowing-traveling-looks-appropriations.trycloudflare[.]com
making-toys-sn-kijiji.trycloudflare[.]com
checklist-digital-proved-labels.trycloudflare[.]com
im-trend-naturally-administrator.trycloudflare[.]com
dressed-emissions-councils-storage.trycloudflare[.]com
sand-northeast-consumers-sells.trycloudflare[.]com
architect-reverse-poster-failed.trycloudflare[.]com
mailed-this-chemical-thermal.trycloudflare[.]com
adjustable-za-creativity-copper.trycloudflare[.]com
amenities-minus-judges-clearly.trycloudflare[.]com
zambia-relate-highlights-tasks.trycloudflare[.]com
adventures-worked-exposure-maui.trycloudflare[.]com
asks-ribbon-nearest-traveler.trycloudflare[.]com
relax-spas-miss-feeling.trycloudflare[.]com
sized-professionals-expertise-reveals.trycloudflare[.]com
sat-mapping-metadata-instrumentation.trycloudflare[.]com
dimensions-incorporated-citysearch-quotes.trycloudflare[.]com
funky-honduras-drives-statutory.trycloudflare[.]com
outputs-sam-come-bosnia.trycloudflare[.]com
efficiently-noble-pubs-armed.trycloudflare[.]com
place-experiencing-teen-kitty.trycloudflare[.]com
cat-pop-injuries-gallery.trycloudflare[.]com
compact-egypt-meal-imagination.trycloudflare[.]com
stockholm-align-closed-far.trycloudflare[.]com
cope-senator-european-texas.trycloudflare[.]com
playstation-look-became-circles.trycloudflare[.]com
fixtures-bracelet-anatomy-jon.trycloudflare[.]com
engineering-moreover-packages-shareholders.trycloudflare[.]com
applicant-approx-vatican-senators.trycloudflare[.]com
wallpaper-duplicate-agents-exports.trycloudflare[.]com
advisors-commission-burn-valuation.trycloudflare[.]com
wto-ls-stocks-pie.trycloudflare[.]com
forces-details-round-gates.trycloudflare[.]com
spectrum-maldives-literally-garcia.trycloudflare[.]com
performances-look-humidity-pie.trycloudflare[.]com
unlike-processes-saskatchewan-prepared.trycloudflare[.]com
URLs
[hxxps://telegra[.]ph/Vizit-12-28](hxxps://telegra.ph/Vizit-12-28)
[hxxps://telegra[.]ph/Post-12-20-7](hxxps://telegra.ph/Post-12-20-7)
[hxxps://graph[.]org/LifeNews-02-20](hxxps://graph.org/LifeNews-02-20)
[hxxps://telegra[.]ph/VectorsWar-03-06](hxxps://telegra.ph/VectorsWar-03-06)
[hxxps://telegra[.]ph/mark-01-20-5](hxxps://telegra.ph/mark-01-20-5)
[hxxps://telegra[.]ph/Leons-01-13](hxxps://telegra.ph/Leons-01-13)
[hxxps://telegra[.]ph/Kasiopeya-01-09](hxxps://telegra.ph/Kasiopeya-01-09)
[hxxps://teletype[.]in/@dc1/p9G48lhQVjw](hxxps://teletype.in/@dc1/p9G48lhQVjw)
[hxxps://teletype[.]in/@din3/VByOMkbbyIt](hxxps://teletype.in/@din3/VByOMkbbyIt)
[hxxps://teletype[.]in/@mew31/y4JyD2Rpb41](hxxps://teletype.in/@mew31/y4JyD2Rpb41)
[hxxps://telegra[.]ph/Simphoniya-03-07](hxxps://telegra.ph/Simphoniya-03-07)
[hxxps://des-cinema-democrat-san.trycloudflare[.]com/comp/](hxxps://des-cinema-democrat-san.trycloudflare.com/comp/)
[hxxps://ukr.net](hxxps://ukr.net)
[hxxps://sweet.tv](hxxps://sweet.tv)
[hxxps://bbc.com](hxxps://bbc.com)
[hxxps://vesti.ru](hxxps://vesti.ru)
[hxxp://<2-digits>.mahombres[.]ru](hxxp://<2-digits>.mahombres.ru)
[hxxps://nandayo[.]ru/srgssdfsf](hxxps://nandayo.ru/srgssdfsf)
[hxxps://kimiga[.]ru](hxxps://kimiga.ru)
Original link: https://harfanglab.io/insidethelab/gamaredons-pterolnk-analysis/
Threat actors misuse Node.js to deliver malware and other malicious payloads
Summmary
Threat actors are increasingly leveraging Node.js, a cross-platform JavaScript runtime environment, to deliver malware and conduct malicious activities, leading to information theft and data exfiltration. While traditional scripting languages remain popular, the use of compiled JavaScript or direct script execution via Node.js indicates an evolving threat landscape. Attack campaigns observed since October 2024 utilize Node.js to bypass security controls and persist in compromised environments. A notable and active malvertising campaign as of April 2025, related to cryptocurrency trading, lures users to download malicious installers disguised as legitimate software. These attacks employ techniques such as malvertising, social engineering, and inline script execution to deliver various payloads. Organizations should be aware of this emerging threat and implement recommended mitigations to reduce their risk.
Technical Details
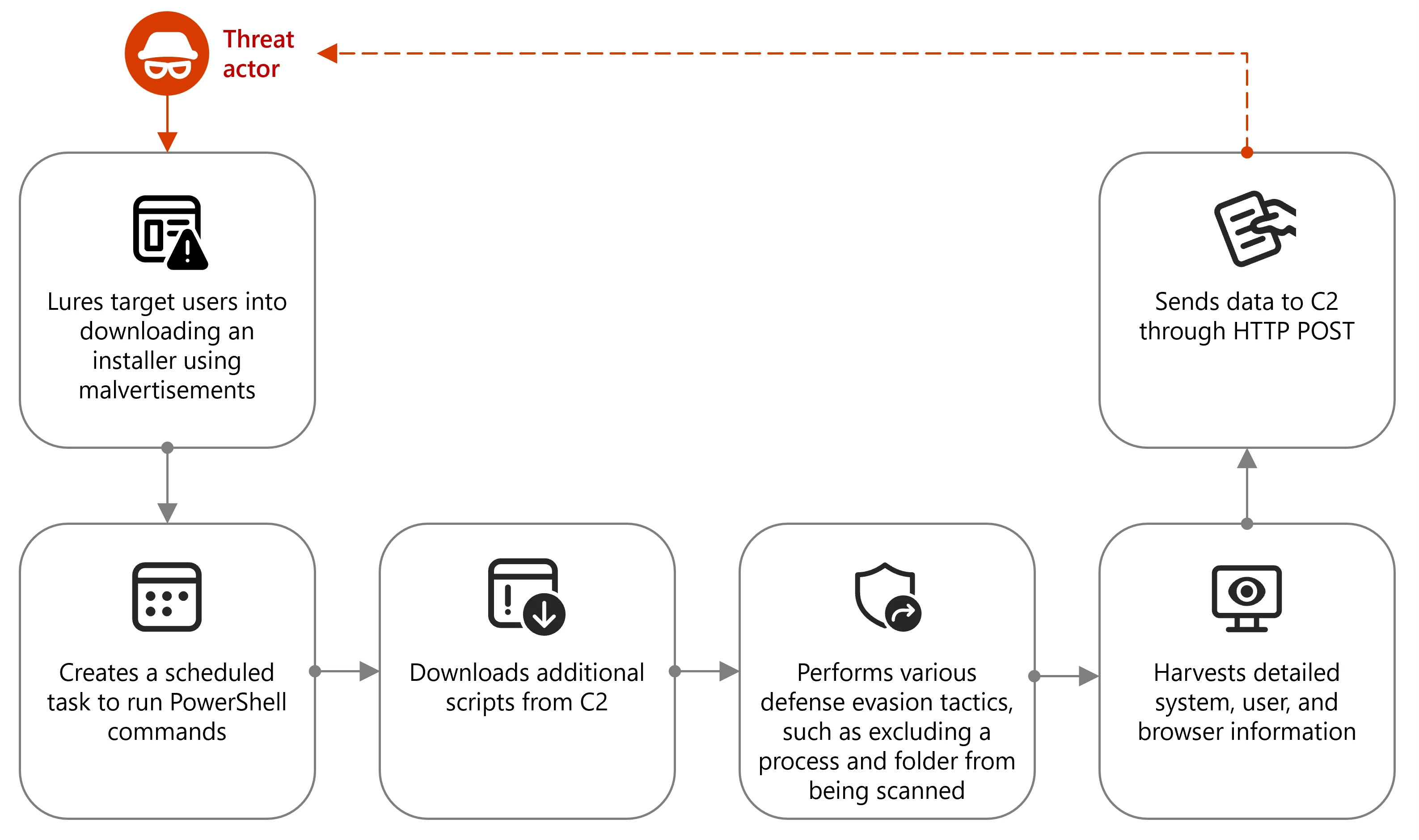
The observed attack chain often begins with malvertising campaigns, where threat actors lure targets to fraudulent websites using themes like financial services or software updates, particularly related to cryptocurrency trading platforms like Binance or TradingView. Users are tricked into downloading a malicious installer, often a Wix-built package containing a malicious DLL (e.g., CustomActions.dll). Upon execution, this DLL gathers basic system information using Windows Management Instrumentation (WMI) queries and establishes persistence by creating a scheduled task that runs a PowerShell command. Simultaneously, a decoy is launched, typically an msedge_proxy window displaying a legitimate cryptocurrency trading website, to deceive the victim.
For defense evasion, the created scheduled task executes PowerShell commands to exclude both the PowerShell process and the current directory from Microsoft Defender for Endpoint scans, allowing subsequent malicious PowerShell activities to proceed without detection.
Following the evasion tactics, an obfuscated PowerShell command, executed via the scheduled task, continuously fetches and runs scripts from remote URLs. These scripts are designed for detailed system reconnaissance, collecting a wide range of information, including Windows information (registered owner, system root, installed software, email addresses), BIOS information (manufacturer, name, release date, version), system information (name, domain, manufacturer, model, domain membership, memory, logical processors, GPUs, processors, network adapters), and operating system information (name, version, locale, UAC settings, country, language, time zone, install date). This collected data is then structured into a nested hash table, converted to JSON format, and exfiltrated to the attacker’s command-and-control (C2) server using HTTP POST requests.
After successful data exfiltration, another PowerShell script is launched to deliver the main payload. This involves downloading an archive file from the C2 server and extracting its contents. The archive typically includes the node.exe (Node.js runtime), a JSC file (JavaScript compiled file), and supporting library files/modules. The script also disables proxy settings in the Windows registry before launching the JSC file, which initiates the next stage of the attack.
The node.exe executable then executes the downloaded JSC file, which performs several malicious routines. These include loading various library modules, establishing network connections, adding certificates to the device, and reading and potentially exfiltrating sensitive browser information. These actions suggest potential follow-on activities such as credential theft, further evasion, or the deployment of secondary payloads, consistent with other Node.js-based malware campaigns. The command line used to launch the JSC file typically involves the Node.js executable followed by the JSC file name (e.g., "C:\Users\Public\node.exe" "C:\Users\Public\update.jsc").
Beyond the delivery of compiled executables, threat actors are also employing inline JavaScript execution via Node.js. One observed method involves a ClickFix social engineering attack that tricks users into executing a malicious PowerShell command. This command downloads and installs several components, including the node.exe binary and necessary modules. Once these are set up, the PowerShell script utilizes the Node.js environment to execute JavaScript code directly in the command line, without needing to run it from a separate file. This inline JavaScript further performs network discovery by executing commands to map the domain structure and identify valuable assets. It also attempts to conceal C2 traffic by mimicking legitimate Cloudflare activity and achieves persistence by modifying registry run keys.
The MITRE ATT&CK tactics and techniques observed in these campaigns include Initial Access via Drive-by Compromise (T1189) through malicious websites, Persistence using Scheduled Task/Job: Scheduled Task (T1053.005), Defense Evasion through Hide Artifacts: Hidden Files and Directories (T1564.001), Obfuscated Files or Information (T1027), and Virtualization/Sandbox Evasion: Time Based Evasion (T1497.003), Discovery via System Information Discovery (T1082), Credential Access through OS Credential Dumping (T1003), Collection of Data from Local System (T1005) and System Information Discovery (T1082), Command and Control using Application Layer Protocol: Web Protocols (T1071.001) and Ingress Tool Transfer (T1105), and Exfiltration Over C2 Channel (T1041).
Countries
Targeted Countries: Not explicitly mentioned in the sources.
Industries
Targeted Industries: While the lure used a cryptocurrency trading theme, the attacks are not necessarily limited to the cryptocurrency industry.
Recommendations
Organizations can mitigate the risks associated with Node.js misuse by implementing the following technical recommendations:
- Educate users about the dangers of downloading software from unverified sources.
- Monitor Node.js execution and flag any unauthorized node.exe processes.
- Enforce PowerShell logging by enabling script block logging to track obfuscated commands.
- Implement endpoint protection by ensuring Endpoint Detection and Response (EDR) or Extended Detection and Response (XDR) solutions are actively monitoring script execution.
- Restrict outbound C2 communications by implementing firewall rules to block suspicious domains.
- Turn on cloud-delivered protection in Microsoft Defender Antivirus or equivalent antivirus products.
- Run EDR in block mode to enable the blocking of malicious artifacts.
- Allow investigation and remediation in full automated mode in Microsoft Defender for Endpoint.
- Understand and use PowerShell’s execution policies.
- Turn on and monitor comprehensive PowerShell logging, including script block logging, module logging, and transcription.
- Turn on tamper protection features and combine them with the DisableLocalAdminMerge setting.
- Utilize attack surface reduction rules in Microsoft Defender XDR to block common attack techniques such as blocking executable files from untrusted paths, potentially obfuscated scripts, and JavaScript/VBScript launching downloaded executables.
Hunting methods
Microsoft provides the following hunting queries for Microsoft Defender XDR and Microsoft Sentinel to identify related activity:
Microsoft Defender XDR Queries:
- Suspicious JSC file:
DeviceProcessEvents | where isnotempty(DeviceId) | where ProcessVersionInfoOriginalFileName == 'node.exe' | where (ProcessCommandLine has_all (".jsc", ".js") and ProcessCommandLine matches regex @"\\\w*.jsc")Logic: This query searches for process execution events where the original file name of the process is
node.exeand the command line arguments include both.jscor.jsand a regular expression matching a.jscfile path. This aims to detect the execution of compiled JavaScript files via Node.js. - Suspicious inline JavaScript execution:
DeviceProcessEvents | where isnotempty(DeviceId) | where ProcessVersionInfoOriginalFileName == 'node.exe' | where ProcessCommandLine has_all ('http', 'execSync', 'spawn', 'fs', 'path', 'zlib')Logic: This query looks for
node.exeprocesses with command lines containing keywords commonly used in malicious inline JavaScript for network communication (http), executing system commands (execSync,spawn), file system operations (fs,path), and data compression/decompression (zlib). The presence of these keywords together might indicate suspicious direct JavaScript execution. - Node.js-based infostealer activity:
DeviceEvents | where isnotempty(DeviceId) | where EtwEventId == 16385 | where InitiatingProcessParentFileName endswith "powershell.exe" | where InitiatingProcessFileName =~ "node.exe" | where InitiatingProcessCommandLine has_all ("-r", ".js") and InitiatingProcessCommandLine endswith ".jsc"Logic: This query detects potential malicious access to sensitive credentials using Windows Data Protection API (DPAPI) events (EtwEventId == 16385). It filters for events where the initiating process’s parent is
powershell.exeand the initiating process file name matchesnode.exe, with a command line containing-rand.jsand ending with.jsc. This aims to identify Node.js processes launched by PowerShell potentially involved in credential theft.
Microsoft Sentinel Queries (using ASIM):
-
Scheduled Task Creation: (No specific query provided in the excerpt, but monitoring for unusual scheduled task creation, especially those involving PowerShell with exclusion parameters or Node.js execution, is recommended.)
-
Detect network indicators of compromise communication to C2 servers:
let selectedTimestamp = datetime(2025-04-15T00:00:00.0000000Z); let ip = dynamic(['216.245.184.181', '212.237.217.182', '168.119.96.41']); let url = dynamic(['sublime-forecasts-pale-scored.trycloudflare.com', 'washing-cartridges-watts-flags.trycloudflare.com', 'investigators-boxing-trademark-threatened.trycloudflare.com', 'fotos-phillips-princess-baker.com', 'casting-advisors-older-invitations.com', 'complement-parliamentary-chairs-hc.com']); search in (AlertEvidence,BehaviorEntities,CommonSecurityLog,DeviceInfo,DeviceNetworkEvents,DeviceNetworkInfo,DnsEvents,SecurityEvent,VMConnection,WindowsFirewall) TimeGenerated between ((selectedTimestamp - 1m) .. (selectedTimestamp + 90d)) // from April 15th runs the search for last 90 days, change the above selectedTimestamp or 90d accordingly. and (RemoteIP in (ip) or DestinationIP in (ip) or DeviceCustomIPv6Address1 in (ip) or DeviceCustomIPv6Address2 in (ip) or DeviceCustomIPv6Address3 in (ip) or DeviceCustomIPv6Address4 in (ip) or MaliciousIP in (ip) or SourceIP in (ip) or PublicIP in (ip) or LocalIPType in (ip) or RemoteIPType in (ip) or IPAddresses in (ip) or IPv4Dhcp in (ip) or IPv6Dhcp in (ip) or IpAddress in (ip) or NASIPv4Address in (ip) or NASIPv6Address in (ip) or RemoteIpAddress in (ip) or RemoteUrl in (url))Logic: This query searches across various security logs for network communication involving a predefined list of IPs and URLs associated with the observed campaign’s C2 infrastructure. The
selectedTimestampvariable allows defining a timeframe for the search, and the query checks for the presence of the defined IPs in various IP address fields and the defined URLs in relevant URL fields across different log sources.
Microsoft Sentinel also provides TI Mapping analytics to automatically match malicious domain indicators with data in the workspace and recommends installing the Threat Intelligence solution from the Content Hub if the TI Map analytics are not deployed.
IOC
IP Addresses
216.245.184.181
212.237.217.182
168.119.96.41
Domains
sublime-forecasts-pale-scored.trycloudflare.com
washing-cartridges-watts-flags.trycloudflare.com
investigators-boxing-trademark-threatened.trycloudflare.com
fotos-phillips-princess-baker.com
casting-advisors-older-invitations.com
complement-parliamentary-chairs-hc.com
Original link: https://www.microsoft.com/en-us/security/blog/2025/04/15/threat-actors-misuse-node-js-to-deliver-malware-and-other-malicious-payloads/